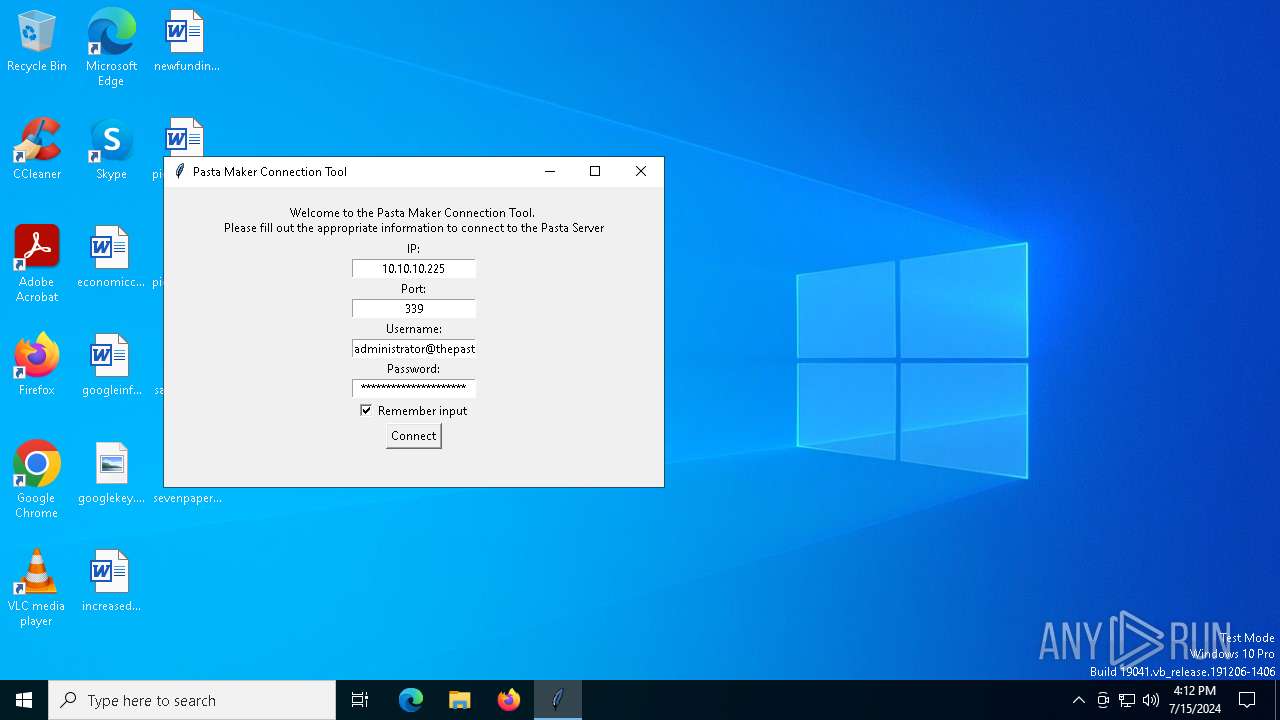
| File name: | pmcon.exe |
| Full analysis: | https://app.any.run/tasks/e336234f-15eb-4bde-8ce8-06fa7a24deb5 |
| Verdict: | Malicious activity |
| Analysis date: | July 15, 2024, 16:11:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 01032406518002A917A91076B7DE6C9A |
| SHA1: | 2494BF74D7B631E648EADFCEEC6FB71E0D908A3F |
| SHA256: | DD17EF0CB2D392DDA24FD265F54EB6AD84BCB559B82C1B16DD99797A198ED34C |
| SSDEEP: | 196608:HQP6SCsXDjpf/2WliXYrHW1B48RmU/3ZlsPvywTvN8Cfq70H:wPPCEJ2ciIrHWTtN3ZWywTY4H |
MALICIOUS
Drops the executable file immediately after the start
- pmcon.exe (PID: 3152)
SUSPICIOUS
Process drops legitimate windows executable
- pmcon.exe (PID: 3152)
The process drops C-runtime libraries
- pmcon.exe (PID: 3152)
Executable content was dropped or overwritten
- pmcon.exe (PID: 3152)
Process drops python dynamic module
- pmcon.exe (PID: 3152)
Loads Python modules
- pmcon.exe (PID: 6956)
Application launched itself
- pmcon.exe (PID: 3152)
Connects to unusual port
- pmcon.exe (PID: 6956)
INFO
Reads the computer name
- pmcon.exe (PID: 3152)
- pmcon.exe (PID: 6956)
Checks supported languages
- pmcon.exe (PID: 3152)
- pmcon.exe (PID: 6956)
Create files in a temporary directory
- pmcon.exe (PID: 3152)
Reads the machine GUID from the registry
- pmcon.exe (PID: 6956)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2022:12:22 19:51:47+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.32 |
| CodeSize: | 165888 |
| InitializedDataSize: | 154624 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xafb0 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
130
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3152 | "C:\Users\admin\AppData\Local\Temp\pmcon.exe" | C:\Users\admin\AppData\Local\Temp\pmcon.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6492 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6524 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6956 | "C:\Users\admin\AppData\Local\Temp\pmcon.exe" | C:\Users\admin\AppData\Local\Temp\pmcon.exe | pmcon.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
491
Read events
491
Write events
0
Delete events
0
Modification events
Executable files
15
Suspicious files
3
Text files
915
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3152 | pmcon.exe | C:\Users\admin\AppData\Local\Temp\_MEI31522\VCRUNTIME140.dll | executable | |
MD5:18049F6811FC0F94547189A9E104F5D2 | SHA256:C865C3366A98431EC3A5959CB5AC3966081A43B82DFCD8BFEFAFE0146B1508DB | |||
| 3152 | pmcon.exe | C:\Users\admin\AppData\Local\Temp\_MEI31522\_tkinter.pyd | executable | |
MD5:DF830D3061AA2524EEEC14ED02F7AD65 | SHA256:1B4D93153D06BCDBFF02CE3A68F6A620CCBE4BA163BAF78698D5FBA3F54D4357 | |||
| 3152 | pmcon.exe | C:\Users\admin\AppData\Local\Temp\_MEI31522\_bz2.pyd | executable | |
MD5:A991152FD5B8F2A0EB6C34582ADF7111 | SHA256:7301FC2447E7E6D599472D2C52116FBE318A9FF9259B8A85981C419BFD20E3EF | |||
| 3152 | pmcon.exe | C:\Users\admin\AppData\Local\Temp\_MEI31522\_hashlib.pyd | executable | |
MD5:88E2BF0A590791891FB5125FFCF5A318 | SHA256:E7AECB61A54DCC77B6D9CAFE9A51FD1F8D78B2194CC3BAF6304BBD1EDFD0AEE6 | |||
| 3152 | pmcon.exe | C:\Users\admin\AppData\Local\Temp\_MEI31522\_decimal.pyd | executable | |
MD5:3CCE2CA89817962AEA5B6A98891EEA1C | SHA256:0809DE4A8DEE3B6CF6DDC40A10C52D53867EE47BF5A6769D16027F2AB766B5CF | |||
| 3152 | pmcon.exe | C:\Users\admin\AppData\Local\Temp\_MEI31522\_socket.pyd | executable | |
MD5:478ABD499EEFEBA3E50CFC4FF50EC49D | SHA256:FDB14859EFEE35E105F21A64F7AFDF50C399FFA0FA8B7FCC76DAE4B345D946CB | |||
| 3152 | pmcon.exe | C:\Users\admin\AppData\Local\Temp\_MEI31522\libcrypto-1_1.dll | executable | |
MD5:89511DF61678BEFA2F62F5025C8C8448 | SHA256:296426E7CE11BC3D1CFA9F2AEB42F60C974DA4AF3B3EFBEB0BA40E92E5299FDF | |||
| 3152 | pmcon.exe | C:\Users\admin\AppData\Local\Temp\_MEI31522\_ssl.pyd | executable | |
MD5:CF7886B3AC590D2EA1A6EFE4EE47DC20 | SHA256:3D183C1B3A24D634387CCE3835F58B8E1322BF96AB03F9FE9F02658FB17D1F8C | |||
| 3152 | pmcon.exe | C:\Users\admin\AppData\Local\Temp\_MEI31522\_lzma.pyd | executable | |
MD5:CDD13B537DAD6A910CB9CBB932770DC9 | SHA256:638CD8C336F90629A6260E67827833143939497D542838846F4FC94B2475BB3E | |||
| 3152 | pmcon.exe | C:\Users\admin\AppData\Local\Temp\_MEI31522\python39.dll | executable | |
MD5:1D5E4C20A20740F38F061BDF48AACA4F | SHA256:F8172151D11BCF934F2A7518CD0D834E3F079BD980391E9DA147CE4CFF72C366 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
70
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1776 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.43:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1776 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3656 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4020 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5908 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6816 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6816 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2252 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2448 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1776 | MoUsoCoreWorker.exe | 2.16.164.43:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1776 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4656 | SearchApp.exe | 92.123.104.60:443 | www.bing.com | Akamai International B.V. | DE | unknown |
3656 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |