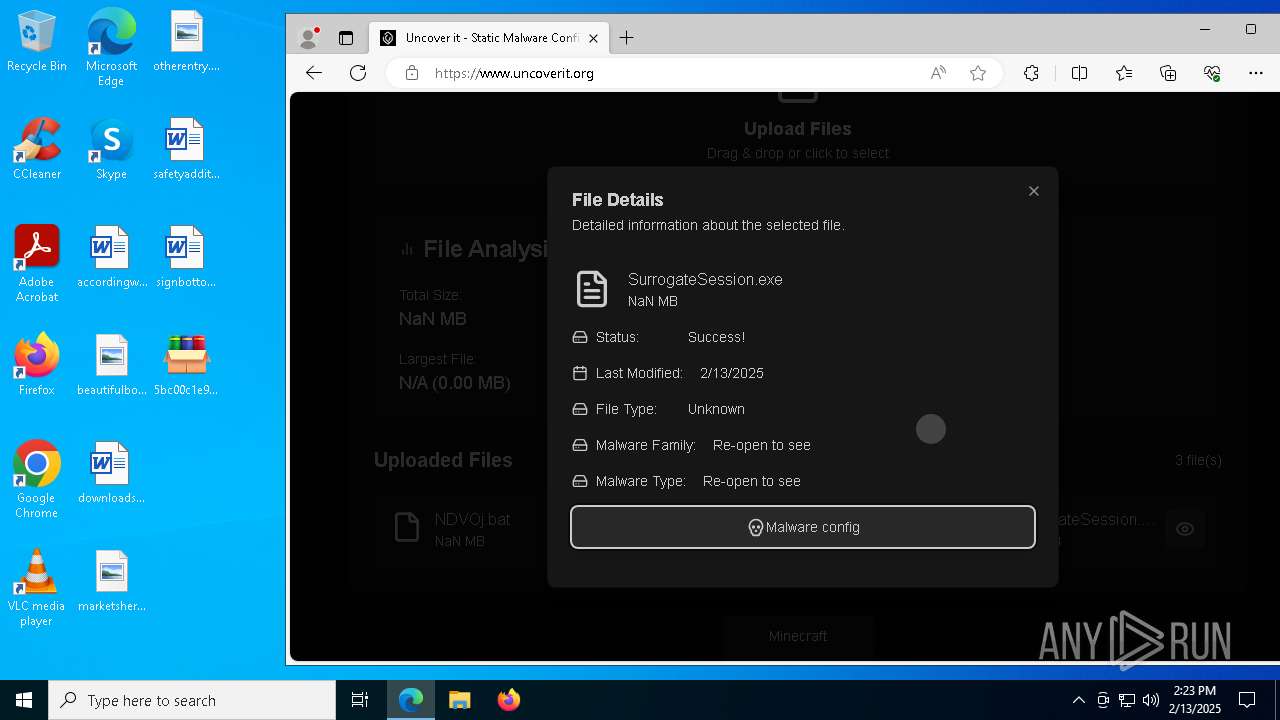
| File name: | 5bc00c1e901c395996034d839e6756f1.exe |
| Full analysis: | https://app.any.run/tasks/e1cae85a-6345-406f-8ff4-853cd95731f2 |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | February 13, 2025, 14:22:54 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 5BC00C1E901C395996034D839E6756F1 |
| SHA1: | 6CCA337F7282DFACC3635F5B4295C8775BDC8FD8 |
| SHA256: | DD136A5EE26D6914C08E9D2890F5FA43B0C920CA230FBDC54BB065982C77CA3F |
| SSDEEP: | 49152:HFrKj5G0lvhjPBuTE9vMmbVJh7CX0Z5EYJAKnRU6s4c9F:HFrKdVVttC+5EJQW6st3 |
MALICIOUS
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 6220)
DCRAT mutex has been found
- SurrogateSession.exe (PID: 6752)
- wininit.exe (PID: 6996)
Changes the autorun value in the registry
- SurrogateSession.exe (PID: 6752)
Actions looks like stealing of personal data
- wininit.exe (PID: 6996)
DCRAT has been detected (YARA)
- wininit.exe (PID: 6996)
SUSPICIOUS
Reads security settings of Internet Explorer
- 5bc00c1e901c395996034d839e6756f1.exe (PID: 2124)
- SurrogateSession.exe (PID: 6752)
Executable content was dropped or overwritten
- 5bc00c1e901c395996034d839e6756f1.exe (PID: 2124)
- SurrogateSession.exe (PID: 6752)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 6220)
- SurrogateSession.exe (PID: 6752)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6220)
Executing commands from a ".bat" file
- wscript.exe (PID: 6220)
- SurrogateSession.exe (PID: 6752)
The executable file from the user directory is run by the CMD process
- SurrogateSession.exe (PID: 6752)
Executed via WMI
- schtasks.exe (PID: 6900)
- schtasks.exe (PID: 6920)
- schtasks.exe (PID: 6936)
- schtasks.exe (PID: 6968)
- schtasks.exe (PID: 7048)
- schtasks.exe (PID: 7004)
- schtasks.exe (PID: 6984)
- schtasks.exe (PID: 7032)
- schtasks.exe (PID: 7064)
- schtasks.exe (PID: 7108)
- schtasks.exe (PID: 7128)
- schtasks.exe (PID: 7092)
- schtasks.exe (PID: 7160)
- schtasks.exe (PID: 848)
- schtasks.exe (PID: 6180)
- schtasks.exe (PID: 3208)
- schtasks.exe (PID: 5968)
- schtasks.exe (PID: 5404)
- schtasks.exe (PID: 1752)
- schtasks.exe (PID: 644)
- schtasks.exe (PID: 6168)
- schtasks.exe (PID: 436)
- schtasks.exe (PID: 3280)
- schtasks.exe (PID: 1416)
- schtasks.exe (PID: 3836)
- schtasks.exe (PID: 6092)
- schtasks.exe (PID: 4076)
- schtasks.exe (PID: 6264)
- schtasks.exe (PID: 6272)
- schtasks.exe (PID: 1732)
- schtasks.exe (PID: 1864)
- schtasks.exe (PID: 2972)
- schtasks.exe (PID: 4132)
- schtasks.exe (PID: 2212)
- schtasks.exe (PID: 624)
- schtasks.exe (PID: 5320)
- schtasks.exe (PID: 5256)
- schtasks.exe (PID: 3620)
- schtasks.exe (PID: 5244)
- schtasks.exe (PID: 3420)
- schtasks.exe (PID: 3792)
- schtasks.exe (PID: 4764)
- schtasks.exe (PID: 6244)
- schtasks.exe (PID: 2796)
- schtasks.exe (PID: 6548)
Likely accesses (executes) a file from the Public directory
- schtasks.exe (PID: 6984)
- schtasks.exe (PID: 6968)
- schtasks.exe (PID: 7032)
- schtasks.exe (PID: 7004)
- schtasks.exe (PID: 7048)
- schtasks.exe (PID: 7064)
- schtasks.exe (PID: 5404)
- schtasks.exe (PID: 6180)
- schtasks.exe (PID: 848)
- schtasks.exe (PID: 3208)
- schtasks.exe (PID: 5968)
- schtasks.exe (PID: 7160)
- schtasks.exe (PID: 1752)
- schtasks.exe (PID: 644)
- schtasks.exe (PID: 6168)
- schtasks.exe (PID: 1864)
- schtasks.exe (PID: 6272)
- schtasks.exe (PID: 6264)
- schtasks.exe (PID: 2212)
- schtasks.exe (PID: 5320)
- schtasks.exe (PID: 624)
- schtasks.exe (PID: 3620)
- schtasks.exe (PID: 3420)
- schtasks.exe (PID: 4764)
- wininit.exe (PID: 6996)
The process creates files with name similar to system file names
- SurrogateSession.exe (PID: 6752)
Reads the date of Windows installation
- SurrogateSession.exe (PID: 6752)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 1540)
There is functionality for taking screenshot (YARA)
- wininit.exe (PID: 6996)
INFO
Checks supported languages
- 5bc00c1e901c395996034d839e6756f1.exe (PID: 2124)
- SurrogateSession.exe (PID: 6752)
- wininit.exe (PID: 6996)
- identity_helper.exe (PID: 7192)
Create files in a temporary directory
- 5bc00c1e901c395996034d839e6756f1.exe (PID: 2124)
- SurrogateSession.exe (PID: 6752)
Reads the computer name
- 5bc00c1e901c395996034d839e6756f1.exe (PID: 2124)
- SurrogateSession.exe (PID: 6752)
- wininit.exe (PID: 6996)
- identity_helper.exe (PID: 7192)
The sample compiled with english language support
- 5bc00c1e901c395996034d839e6756f1.exe (PID: 2124)
- SurrogateSession.exe (PID: 6752)
- msedge.exe (PID: 7636)
Process checks computer location settings
- 5bc00c1e901c395996034d839e6756f1.exe (PID: 2124)
- SurrogateSession.exe (PID: 6752)
Drops encrypted VBS script (Microsoft Script Encoder)
- 5bc00c1e901c395996034d839e6756f1.exe (PID: 2124)
Reads the machine GUID from the registry
- SurrogateSession.exe (PID: 6752)
- wininit.exe (PID: 6996)
Reads Environment values
- SurrogateSession.exe (PID: 6752)
- identity_helper.exe (PID: 7192)
- wininit.exe (PID: 6996)
Failed to create an executable file in Windows directory
- SurrogateSession.exe (PID: 6752)
Creates files or folders in the user directory
- SurrogateSession.exe (PID: 6752)
Manual execution by a user
- msedge.exe (PID: 7016)
Application launched itself
- msedge.exe (PID: 7016)
Disables trace logs
- wininit.exe (PID: 6996)
.NET Reactor protector has been detected
- wininit.exe (PID: 6996)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- wininit.exe (PID: 6996)
Found Base64 encoded reference to WMI classes (YARA)
- wininit.exe (PID: 6996)
Checks proxy server information
- wininit.exe (PID: 6996)
Executable content was dropped or overwritten
- msedge.exe (PID: 7636)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
DcRat
(PID) Process(6996) wininit.exe
C2 (1)http://cy10907.tw1.ru/8bf75526
Options
MutexDCR_MUTEX-feGXLH0fsLims2NDFKCk
searchpath%UsersFolder% - Fast
Targetals
C2 (1)http://cy10907.tw1.ru/8bf75526
Options
Version4.5.32
SleepTimeout5
ServerTypeC#
MutexDCR_MUTEX-feGXLH0fsLims2NDFKCk
Debugfalse
ServerConfigReplacementTable
0|
1
3&
5>
8)
9.
A@
T<
S;
Q!
d(
n%
Y*
U~
a#
l_
i,
h^
k-
b$
O`
PluginConfigReplacementTable
0@
4!
9$
Q*
U~
m&
Y.
d
O(
q%
R_
Z|
J<
B;
V#
p>
F,
T-
N)
b`
a^
GetWebcamsfalse
InactivityTimeout2
CacheStorageRegistry
AutoRunFull
StealerConfig
searchpath%UsersFolder% - Fast
StealerEnabledfalse
StealerOptionsfalse
SelfDeletefalse
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:12:01 18:00:55+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 201216 |
| InitializedDataSize: | 255488 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1ec40 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
238
Monitored processes
108
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 244 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3596 --field-trial-handle=2360,i,12518951561774434707,13492607845340433213,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 436 | schtasks.exe /create /tn "dwmd" /sc MINUTE /mo 7 /tr "'C:\Users\Default\Documents\My Pictures\dwm.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 448 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2712 --field-trial-handle=2360,i,12518951561774434707,13492607845340433213,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 624 | schtasks.exe /create /tn "winlogonw" /sc MINUTE /mo 12 /tr "'C:\Users\Public\AccountPictures\winlogon.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | schtasks.exe /create /tn "dllhost" /sc ONLOGON /tr "'C:\Users\Public\Videos\dllhost.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=3164 --field-trial-handle=2360,i,12518951561774434707,13492607845340433213,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 848 | schtasks.exe /create /tn "RegistryR" /sc MINUTE /mo 12 /tr "'C:\Users\Public\Music\Registry.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1416 | schtasks.exe /create /tn "dwmd" /sc MINUTE /mo 8 /tr "'C:\Users\Default\Documents\My Pictures\dwm.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1540 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\4DxSH5DWAf.bat" " | C:\Windows\System32\cmd.exe | — | SurrogateSession.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1732 | schtasks.exe /create /tn "backgroundTaskHost" /sc ONLOGON /tr "'C:\Users\admin\Downloads\backgroundTaskHost.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
21 740
Read events
21 532
Write events
204
Delete events
4
Modification events
| (PID) Process: | (2124) 5bc00c1e901c395996034d839e6756f1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbe\OpenWithProgids |
| Operation: | write | Name: | VBEFile |
Value: | |||
| (PID) Process: | (6752) SurrogateSession.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MoUsoCoreWorker |
Value: "C:\Users\admin\PrintHood\MoUsoCoreWorker.exe" | |||
| (PID) Process: | (6752) SurrogateSession.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | dasHost |
Value: "C:\Users\Public\Libraries\dasHost.exe" | |||
| (PID) Process: | (6752) SurrogateSession.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | sihost |
Value: "C:\Users\Public\Pictures\sihost.exe" | |||
| (PID) Process: | (6752) SurrogateSession.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | csrss |
Value: "C:\Users\admin\MicrosoftEdgeBackups\backups\csrss.exe" | |||
| (PID) Process: | (6752) SurrogateSession.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | wininit |
Value: "C:\Users\Public\Videos\wininit.exe" | |||
| (PID) Process: | (6752) SurrogateSession.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Registry |
Value: "C:\Users\Public\Music\Registry.exe" | |||
| (PID) Process: | (6752) SurrogateSession.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | ctfmon |
Value: "C:\Users\Public\Pictures\ctfmon.exe" | |||
| (PID) Process: | (6752) SurrogateSession.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | winlogon |
Value: "C:\Users\Public\AccountPictures\winlogon.exe" | |||
| (PID) Process: | (6752) SurrogateSession.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | dllhost |
Value: "C:\Users\Public\Videos\dllhost.exe" | |||
Executable files
61
Suspicious files
851
Text files
145
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2124 | 5bc00c1e901c395996034d839e6756f1.exe | C:\Users\admin\AppData\Local\Temp\containerBrowserperfDhcp\NDVOj.bat | text | |
MD5:B597E9270D7BF0192234E1E92EA93921 | SHA256:52C94A2C617C046F579F064A5C7776C6B84FFAD2F28B7BC8ADBC8A91046F8ABC | |||
| 6752 | SurrogateSession.exe | C:\Users\Public\Videos\5940a34987c991 | text | |
MD5:AFC848122A2AF62E0298EBBF572E0846 | SHA256:095ABBBCD497B01875FD67E0145C551636256FE69BBD6414E2AB04977E136F3D | |||
| 6752 | SurrogateSession.exe | C:\Users\Public\Videos\wininit.exe | executable | |
MD5:24D5BE2365EB059FAE5140F8C5A02B05 | SHA256:B714B2E3ECA766E59C828FD11E8D904B0692302D64F334D16C7D2B78A0F29193 | |||
| 6752 | SurrogateSession.exe | C:\Users\Public\Libraries\21b1a557fd31cc | text | |
MD5:4BF6F1D07C8C6DBFBFF17EB7F6DE752D | SHA256:9576EE092217F5C84218F7F2292896EA05DA1B7E2BC0209CB653EC17F0EF3B1B | |||
| 2124 | 5bc00c1e901c395996034d839e6756f1.exe | C:\Users\admin\AppData\Local\Temp\containerBrowserperfDhcp\jxOJKrJl.vbe | binary | |
MD5:120B8191AE211FDE7EC6E858312ED3C7 | SHA256:9612D2C2B748335E46FDCEF81197F1BA6DD150AF2538A678E35618C19F072180 | |||
| 6752 | SurrogateSession.exe | C:\Users\Public\Music\ee2ad38f3d4382 | text | |
MD5:96742E6493208264834D6209613BA5AE | SHA256:4E548A3C061A5746AC1B92816940377D3140408A67A431EF177E73E7A3E13A67 | |||
| 6752 | SurrogateSession.exe | C:\Users\Public\Pictures\sihost.exe | executable | |
MD5:24D5BE2365EB059FAE5140F8C5A02B05 | SHA256:B714B2E3ECA766E59C828FD11E8D904B0692302D64F334D16C7D2B78A0F29193 | |||
| 6752 | SurrogateSession.exe | C:\Users\Default\Pictures\6cb0b6c459d5d3 | text | |
MD5:33B3E792F12CE04E04201C1D3025F995 | SHA256:2046604593FE6A848A07C75C9B8E5422EC714EF6385F6AFBD6A4B3348E6AA317 | |||
| 6752 | SurrogateSession.exe | C:\Users\Public\Music\Registry.exe | executable | |
MD5:24D5BE2365EB059FAE5140F8C5A02B05 | SHA256:B714B2E3ECA766E59C828FD11E8D904B0692302D64F334D16C7D2B78A0F29193 | |||
| 6752 | SurrogateSession.exe | C:\Users\Public\Pictures\ctfmon.exe | executable | |
MD5:24D5BE2365EB059FAE5140F8C5A02B05 | SHA256:B714B2E3ECA766E59C828FD11E8D904B0692302D64F334D16C7D2B78A0F29193 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
159
TCP/UDP connections
149
DNS requests
165
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.198.82:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2736 | svchost.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 23.40.158.218:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6996 | wininit.exe | GET | 200 | 94.198.223.74:80 | http://cy10907.tw1.ru/8bf75526.php?m8gxGXCVv2=scSV9HzuSwMCjdTswbhT&RDrNbKAEY3sTBn6jEsDoIMfa=7UwoQ3Nj2bYlHh7zq43dti0XJstdpl&1fce299c0295ad6ce432a5a1e31cbff3=ce4b6083f7c7e7fec98d87a8123da61f&76c0182a073030aa172379f90ef42c58=gMhRGMkRGZwQWOzYDN3QDO2IDN0AjM4kzY3ImNhlzMiVWMyADNwgzY&m8gxGXCVv2=scSV9HzuSwMCjdTswbhT&RDrNbKAEY3sTBn6jEsDoIMfa=7UwoQ3Nj2bYlHh7zq43dti0XJstdpl | unknown | — | — | whitelisted |
5968 | msedge.exe | GET | 304 | 23.40.158.218:80 | http://cacerts.digicert.com/DigiCertGlobalRootG2.crt | unknown | — | — | whitelisted |
6996 | wininit.exe | GET | 200 | 94.198.223.74:80 | http://cy10907.tw1.ru/8bf75526.php?ez9hdN8pp1=atoFHp7EJxALtCplarj6&qs8041Oe7oRYFP=SNtlz7OeeoQ&ylh7F5MuBqONytkLJ=wnwVTM87GbbOdMoVZ2ZrLd3&2ee72ac3762d12911a3ca2abb8ec7973=wIjZ4EzY3I2MyUzMiNWM3QGZ4MzYlNTZxYDZkNjM1kzMlBjN1QzNzgzM3YTMxEDM2IDN1gTO&76c0182a073030aa172379f90ef42c58=gM3IzYhJTZ4U2MzEzNwIWMhNGZ0EDMzIDOlhTZxYjY5gDMlZDMlZTY&e357e36dfa065d6c353471a83e897770=0VfiIiOigDZ1ITZmZzYidTNwEjM3AjN0QmY3EDMmNWM5MmMwcjZiwiIlJWYmJTNiVWY0EzM3ITZ2M2MwYmMzQzYwQGZxM2NjRWNjVDOmZ2N4IiOiQWNzYWYiN2NwATYjBjZ0MWNzQmZ4UDZmRDN5UTNwQjNiwiI1MmYzM2YkFTMlhjMihDM0UWZ4EGO4ADMkRGN2YmN3kjY0IGNlNGZxIiOiQzNiZzY1QDM5YWM0MDN2AjYzITY5UDNmN2YjZmZiFTOis3W | unknown | — | — | whitelisted |
5968 | msedge.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/certs/Microsoft%20Azure%20RSA%20TLS%20Issuing%20CA%2007%20-%20xsign.crt | unknown | — | — | whitelisted |
6996 | wininit.exe | GET | 200 | 94.198.223.74:80 | http://cy10907.tw1.ru/8bf75526.php?ez9hdN8pp1=atoFHp7EJxALtCplarj6&qs8041Oe7oRYFP=SNtlz7OeeoQ&ylh7F5MuBqONytkLJ=wnwVTM87GbbOdMoVZ2ZrLd3&2ee72ac3762d12911a3ca2abb8ec7973=wIjZ4EzY3I2MyUzMiNWM3QGZ4MzYlNTZxYDZkNjM1kzMlBjN1QzNzgzM3YTMxEDM2IDN1gTO&76c0182a073030aa172379f90ef42c58=gM3IzYhJTZ4U2MzEzNwIWMhNGZ0EDMzIDOlhTZxYjY5gDMlZDMlZTY&0b2ee1683d6a209b00bc843434e4ceca=d1nI2MDMyETOwQDZwEjY1IWYwETN0gTNxMjNiJWO0MmMyMGN2YmNkNmY0IiOiQWNzYWYiN2NwATYjBjZ0MWNzQmZ4UDZmRDN5UTNwQjNiwiI1MmYzM2YkFTMlhjMihDM0UWZ4EGO4ADMkRGN2YmN3kjY0IGNlNGZxIiOiQzNiZzY1QDM5YWM0MDN2AjYzITY5UDNmN2YjZmZiFTOis3W&e357e36dfa065d6c353471a83e897770=QX9JiI6ICOkVjMlZmNjJ2N1ATMycDM2QDZidTMwY2YxkzYyAzNmJCLiYzMwITM5ADNkBTMiVjYhBTM1QDO1EzM2ImY5QzYyIzY0YjZ2Q2YiRjI6ICZ1MjZhJ2Y3ADMhNGMmRzY1MDZmhTNkZGN0kTN1ADN2ICLiUzYiNzYjRWMxUGOyIGOwQTZlhTY4gDMwQGZ0YjZ2cTOiRjY0U2YkFjI6ICN3ImNjVDNwkjZxQzM0YDMiNjMhlTN0Y2YjNmZmJWM5Iyes0nI5YlaPlWUYRmdWdlYwJlRjxmVHJGVKNETpVVbkBnUzklQKl2Tp1EWkBjRHRGVshEZwpFWhBjTXFVa3lWSsR2RaZkQ5lWQL9EZtljMjZnSzkFcxUUS0F0UNdWVHJGcaJjY5JkRJRXQplFaShUSzYVbUl2bql0M5ckW1xmMWVlTVFVa3lWSPpUaPlGMXllaKdlWY5EWhl2dplkWKl2TpVVbiZHaHNmdKNTWwFDMjBnSDxUarlmYzkTbiJXNXZ1bBlmYzkTbiJXNXZVavpWSsFzVZ9kVGVFRKNETptWaiNTOtJmc1clVvFUaiNTOtJmc1clVp9maJxWMXl1TWZUVIp0QMlGNrlkNJlmYwFzRaJkTYFWa3lWSp9maJhkRFZVa3lWSwwWbRdWUq50ZVJzYwpESjlnVHRWdWVUS3VERJpHZzI2a1cVYYpUaPlWSYp1V1cVYYp0QMljSTpFd50WV2V1RjZnSYRmRKl2TpVVbiZHcYpFdsdEZpdXaJdXQE10dBRUTp9maJNnRHRme5c0YpdXaJVDeXlFMsVUS0F0QaxGbtpFcOdlW35ESJBTOtRVavpWSup0Mil2dplkMFpnT5RzQOh3dT9EMRR0T1FEROl2bqlka5ckYpdXaJVFbrlkNJNVZ5JlbiFTOykVa3lWS6Z1RidnRtRVavpWS1lzVh5mVtNWa3lWS6Z1RidnRtRVavpWS1IFWhpmSDxUaZpGTy0kaMhXRqxEeRRVTp9maJdHbtl0NwpWS2pVbipkQYNVa3lWS1x2VitmRtlkNJNlW0ZUbUlnVyMmVKNETpFVRUtEeFRFSwVFTRlTRWxkTWJVRKl2TpV1VihWNwEVUKNETplkeNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOigDZ1ITZmZzYidTNwEjM3AjN0QmY3EDMmNWM5MmMwcjZiwiI0UjZkdjM4EDO1ADZwEDN1QzM1cjZiV2Y4gjYjRWOkBDN2IzNyITYzIiOiQWNzYWYiN2NwATYjBjZ0MWNzQmZ4UDZmRDN5UTNwQjNiwiI1MmYzM2YkFTMlhjMihDM0UWZ4EGO4ADMkRGN2YmN3kjY0IGNlNGZxIiOiQzNiZzY1QDM5YWM0MDN2AjYzITY5UDNmN2YjZmZiFTOis3W | unknown | — | — | whitelisted |
6996 | wininit.exe | GET | 200 | 94.198.223.74:80 | http://cy10907.tw1.ru/8bf75526.php?ez9hdN8pp1=atoFHp7EJxALtCplarj6&qs8041Oe7oRYFP=SNtlz7OeeoQ&ylh7F5MuBqONytkLJ=wnwVTM87GbbOdMoVZ2ZrLd3&2ee72ac3762d12911a3ca2abb8ec7973=wIjZ4EzY3I2MyUzMiNWM3QGZ4MzYlNTZxYDZkNjM1kzMlBjN1QzNzgzM3YTMxEDM2IDN1gTO&76c0182a073030aa172379f90ef42c58=gM3IzYhJTZ4U2MzEzNwIWMhNGZ0EDMzIDOlhTZxYjY5gDMlZDMlZTY&b0d5e0c4474d176d94867ffdc35d68ec=0VfiElZp10MixmUXF2V4ZEWqx2RilmVIV1Y4FzY5ZlMjZFeGhlNNtWS2k0QhBjRHVVa3lWS1R2MiVHdtJmVKl2Tpd2RkhmQGpVe5ITW6x2RSl2dplUavpWSvJFWZFVMXlVekdlWzZ1RWl2dplUavpWS6JESjJUMXlFbSNTVpdXaJVHZzIWd01mYWpUaPlWUVNVeWJzYWFzVZxmUzUVa3lWS1R2MiVHdtJmVKl2TplEWapnVWJGaWdEZUp0QMlGNyQmd1ITY1ZFbJZTS5pVdGdEV0Z0VaBjTsl0cJlmYzkTbiJXNXZVavpWSvJFWZFVMXlFbSNTVpdXaJZHbHpVMGVUSzsmeKRkRFlkcWdEZzZ0VaNlQTxUenNUS1xWRJxWNXFWT1cEW5hnVkJkQ55UNjlXUCJUehxmUIJGaW1WVnBTaN9WQTpVd5cUY3lTbjpGbXRVavpWS6ZVbiZHaHNmdKNTWwFzaJNXSplkNJl3Y0ZkMZlmVyYVa3lWS1hHbjNmRUdlQ4VUVUxWRSNGesx0Y4ZEWjpUaPlWTuJGbW12Yq5EbJNXS5tEN0MkTp9maJVXOXFmeKhlWXRXbjZHZYpFdG12YHpUelJiOigDZ1ITZmZzYidTNwEjM3AjN0QmY3EDMmNWM5MmMwcjZiwiIlJWYmJTNiVWY0EzM3ITZ2M2MwYmMzQzYwQGZxM2NjRWNjVDOmZ2N4IiOiQWNzYWYiN2NwATYjBjZ0MWNzQmZ4UDZmRDN5UTNwQjNiwiI1MmYzM2YkFTMlhjMihDM0UWZ4EGO4ADMkRGN2YmN3kjY0IGNlNGZxIiOiQzNiZzY1QDM5YWM0MDN2AjYzITY5UDNmN2YjZmZiFTOis3W | unknown | — | — | whitelisted |
6996 | wininit.exe | GET | 200 | 94.198.223.74:80 | http://cy10907.tw1.ru/8bf75526.php?ez9hdN8pp1=atoFHp7EJxALtCplarj6&qs8041Oe7oRYFP=SNtlz7OeeoQ&ylh7F5MuBqONytkLJ=wnwVTM87GbbOdMoVZ2ZrLd3&2ee72ac3762d12911a3ca2abb8ec7973=wIjZ4EzY3I2MyUzMiNWM3QGZ4MzYlNTZxYDZkNjM1kzMlBjN1QzNzgzM3YTMxEDM2IDN1gTO&76c0182a073030aa172379f90ef42c58=gM3IzYhJTZ4U2MzEzNwIWMhNGZ0EDMzIDOlhTZxYjY5gDMlZDMlZTY&0b2ee1683d6a209b00bc843434e4ceca=d1nI2MDMyETOwQDZwEjY1IWYwETN0gTNxMjNiJWO0MmMyMGN2YmNkNmY0IiOiQWNzYWYiN2NwATYjBjZ0MWNzQmZ4UDZmRDN5UTNwQjNiwiI1MmYzM2YkFTMlhjMihDM0UWZ4EGO4ADMkRGN2YmN3kjY0IGNlNGZxIiOiQzNiZzY1QDM5YWM0MDN2AjYzITY5UDNmN2YjZmZiFTOis3W&e357e36dfa065d6c353471a83e897770=QX9JiI6ICOkVjMlZmNjJ2N1ATMycDM2QDZidTMwY2YxkzYyAzNmJCLiYzMwITM5ADNkBTMiVjYhBTM1QDO1EzM2ImY5QzYyIzY0YjZ2Q2YiRjI6ICZ1MjZhJ2Y3ADMhNGMmRzY1MDZmhTNkZGN0kTN1ADN2ICLiUzYiNzYjRWMxUGOyIGOwQTZlhTY4gDMwQGZ0YjZ2cTOiRjY0U2YkFjI6ICN3ImNjVDNwkjZxQzM0YDMiNjMhlTN0Y2YjNmZmJWM5Iyes0nI5YlaPlWUYRmdWdlYwJlRjxmVHJGVKNETpVVbkBnUzklQKl2Tp1EWkBjRHRGVshEZwpFWhBjTXFVa3lWSsR2RaZkQ5lWQL9EZtljMjZnSzkFcxUUS0F0UNdWVHJGcaJjY5JkRJRXQplFaShUSzYVbUl2bql0M5ckW1xmMWVlTVFVa3lWSPpUaPlGMXllaKdlWY5EWhl2dplkWKl2TpVVbiZHaHNmdKNTWwFDMjBnSDxUarlmYzkTbiJXNXZ1bBlmYzkTbiJXNXZVavpWSsFzVZ9kVGVFRKNETptWaiNTOtJmc1clVvFUaiNTOtJmc1clVp9maJxWMXl1TWZUVIp0QMlGNrlkNJlmYwFzRaJkTYFWa3lWSp9maJhkRFZVa3lWSwwWbRdWUq50ZVJzYwpESjlnVHRWdWVUS3VERJpHZzI2a1cVYYpUaPlWSYp1V1cVYYp0QMljSTpFd50WV2V1RjZnSYRmRKl2TpVVbiZHcYpFdsdEZpdXaJdXQE10dBRUTp9maJNnRHRme5c0YpdXaJVDeXlFMsVUS0F0QaxGbtpFcOdlW35ESJBTOtRVavpWSup0Mil2dplkMFpnT5RzQOh3dT9EMRR0T1FEROl2bqlka5ckYpdXaJVFbrlkNJNVZ5JlbiFTOykVa3lWS6Z1RidnRtRVavpWS1lzVh5mVtNWa3lWS6Z1RidnRtRVavpWS1IFWhpmSDxUaZpGTy0kaMhXRqxEeRRVTp9maJdHbtl0NwpWS2pVbipkQYNVa3lWS1x2VitmRtlkNJNlW0ZUbUlnVyMmVKNETpFVRUtEeFRFSwVFTRlTRWxkTWJVRKl2TpV1VihWNwEVUKNETplkeNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOigDZ1ITZmZzYidTNwEjM3AjN0QmY3EDMmNWM5MmMwcjZiwiI0UjZkdjM4EDO1ADZwEDN1QzM1cjZiV2Y4gjYjRWOkBDN2IzNyITYzIiOiQWNzYWYiN2NwATYjBjZ0MWNzQmZ4UDZmRDN5UTNwQjNiwiI1MmYzM2YkFTMlhjMihDM0UWZ4EGO4ADMkRGN2YmN3kjY0IGNlNGZxIiOiQzNiZzY1QDM5YWM0MDN2AjYzITY5UDNmN2YjZmZiFTOis3W | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.19.198.82:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2736 | svchost.exe | 2.19.198.82:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2736 | svchost.exe | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
732 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2736 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.16.204.161:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
ntp.msn.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5968 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
5968 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
5968 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
5968 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
5968 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
5968 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |