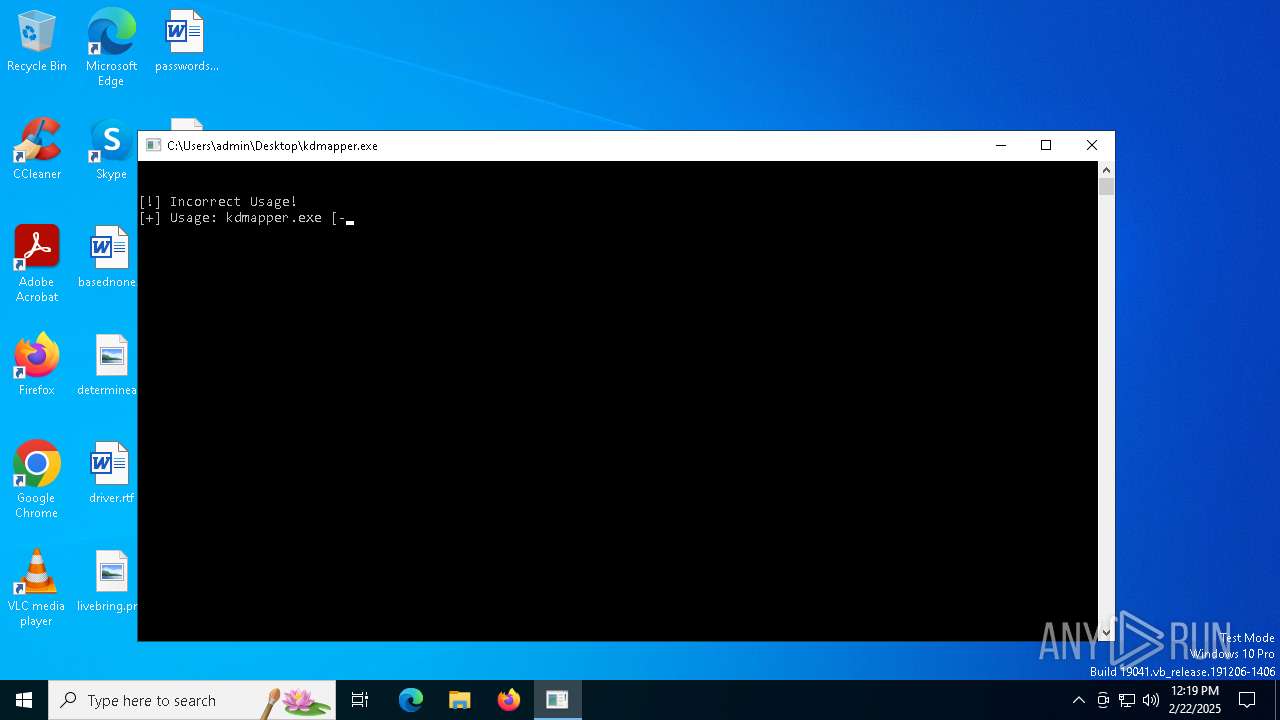
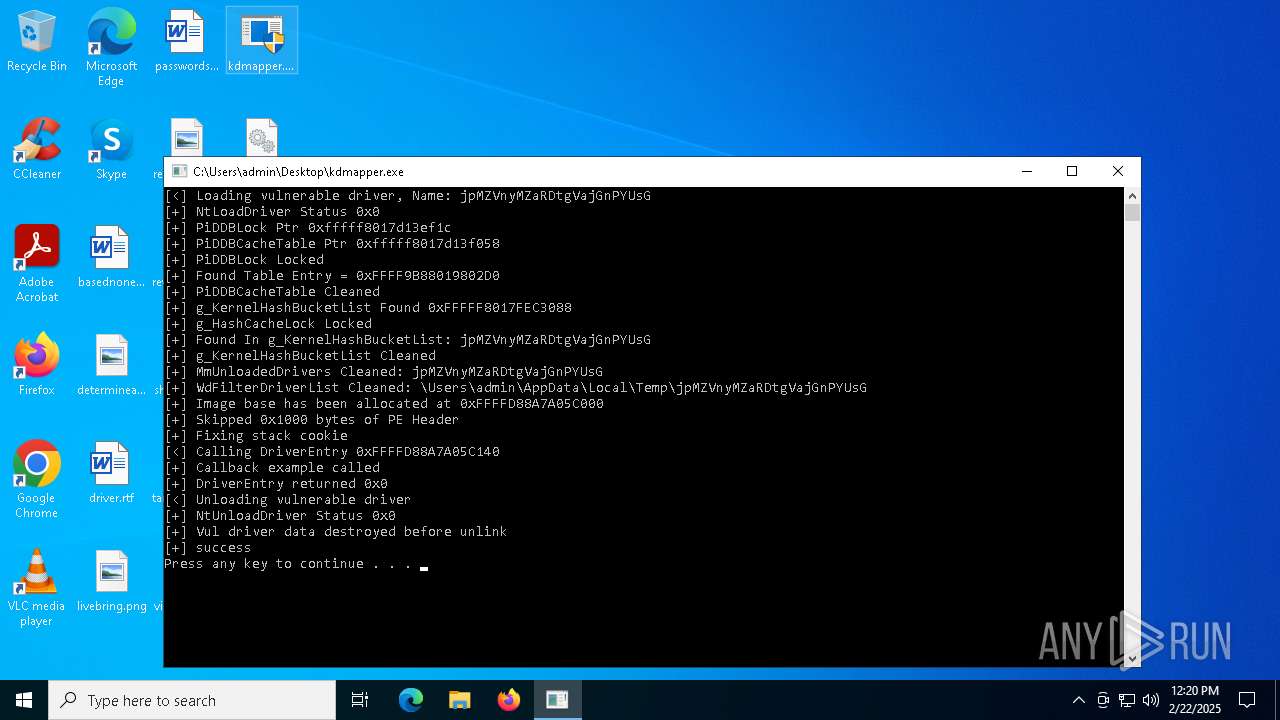
| File name: | kdmapper.exe |
| Full analysis: | https://app.any.run/tasks/6a1c6ca0-978e-4c98-909c-7b01264c0730 |
| Verdict: | Malicious activity |
| Analysis date: | February 22, 2025, 12:19:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | ED463D82261453BF71C3A7D6F14808BD |
| SHA1: | 26E8A4E098920E624F2D892BDF49C4DE5EE29041 |
| SHA256: | DD10FA10E1785219BAFF248BAD74FDF6F5152534ACEA58EAB64938102EF30C8D |
| SSDEEP: | 3072:EF1Ov2XtacME4Pfs0iycvxAkMMo/WDQajkA6hQfAMMI:EF1Ov2XwcBEfs0iyRYQUkAga |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts CMD.EXE for commands execution
- kdmapper.exe (PID: 6568)
- kdmapper.exe (PID: 6536)
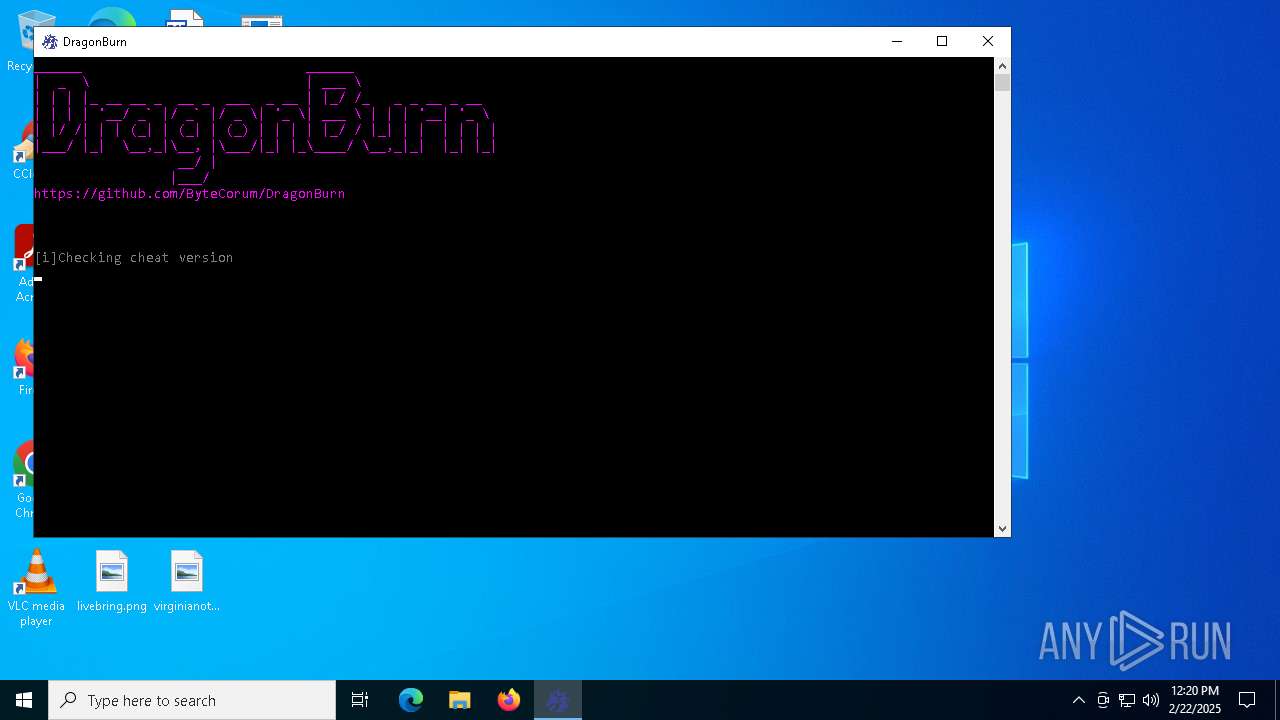
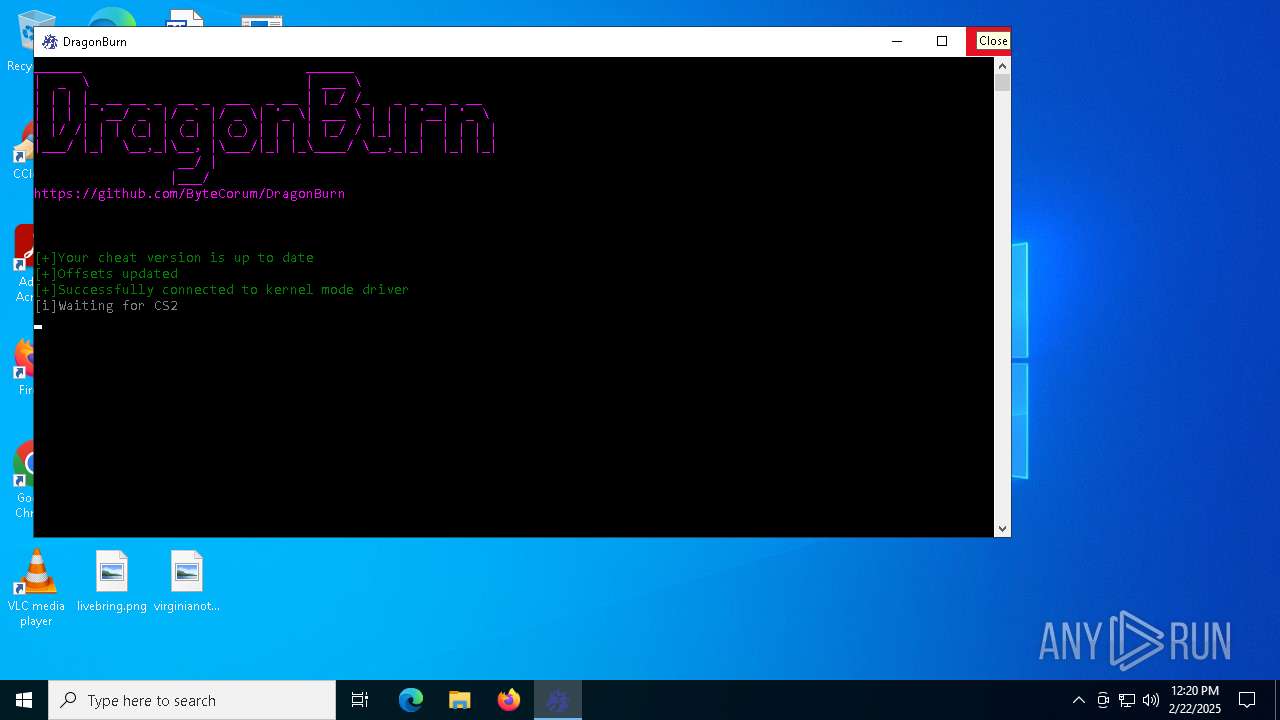
- DragonBurn.exe (PID: 3612)
Executable content was dropped or overwritten
- kdmapper.exe (PID: 6536)
Creates or modifies Windows services
- kdmapper.exe (PID: 6536)
Hides command output
- cmd.exe (PID: 3508)
- cmd.exe (PID: 5472)
Execution of CURL command
- DragonBurn.exe (PID: 3612)
INFO
Checks supported languages
- kdmapper.exe (PID: 6568)
- DragonBurn.exe (PID: 3612)
- kdmapper.exe (PID: 6536)
- curl.exe (PID: 5640)
- curl.exe (PID: 5544)
- curl.exe (PID: 6136)
- curl.exe (PID: 3808)
Manual execution by a user
- kdmapper.exe (PID: 6380)
- kdmapper.exe (PID: 6536)
- DragonBurn.exe (PID: 3612)
- DragonBurn.exe (PID: 6684)
The sample compiled with english language support
- kdmapper.exe (PID: 6536)
Create files in a temporary directory
- kdmapper.exe (PID: 6536)
Execution of CURL command
- cmd.exe (PID: 5240)
- cmd.exe (PID: 2796)
- cmd.exe (PID: 3840)
- cmd.exe (PID: 5028)
Reads the computer name
- curl.exe (PID: 5640)
- curl.exe (PID: 6136)
- curl.exe (PID: 3808)
- curl.exe (PID: 5544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:12:03 16:01:25+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.41 |
| CodeSize: | 63488 |
| InitializedDataSize: | 77312 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xf258 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
151
Monitored processes
23
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1876 | C:\WINDOWS\system32\cmd.exe /c pause | C:\Windows\System32\cmd.exe | — | kdmapper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2796 | C:\WINDOWS\system32\cmd.exe /c curl -s -X GET https://raw.githubusercontent.com/a2x/cs2-dumper/main/output/offsets.json | C:\Windows\System32\cmd.exe | — | DragonBurn.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3508 | C:\WINDOWS\system32\cmd.exe /c ping google.com > nul | C:\Windows\System32\cmd.exe | — | DragonBurn.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3608 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | DragonBurn.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
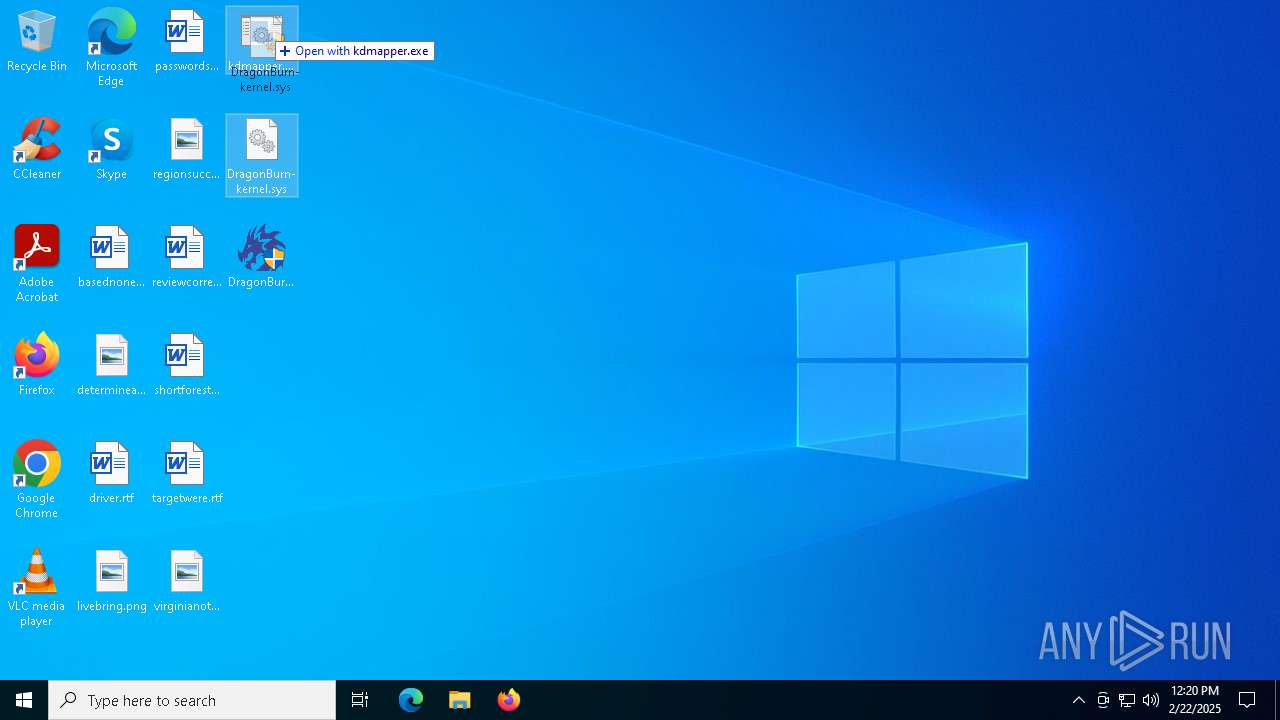
| 3612 | "C:\Users\admin\Desktop\DragonBurn.exe" | C:\Users\admin\Desktop\DragonBurn.exe | explorer.exe | ||||||||||||
User: admin Company: ByteCorum Integrity Level: HIGH Description: DragonBurn is one of the best CS2 kernel mode read only external cheats. Undetected by all anti-cheats except faceit. Exit code: 3221225547 Version: 2.0.4.0 Modules
| |||||||||||||||
| 3808 | curl -s -X GET https://raw.githubusercontent.com/a2x/cs2-dumper/main/output/buttons.json | C:\Windows\System32\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: HIGH Description: The curl executable Exit code: 0 Version: 8.4.0 Modules
| |||||||||||||||
| 3840 | C:\WINDOWS\system32\cmd.exe /c curl -s -X GET https://raw.githubusercontent.com/a2x/cs2-dumper/main/output/buttons.json | C:\Windows\System32\cmd.exe | — | DragonBurn.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4244 | ping google.com | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5028 | C:\WINDOWS\system32\cmd.exe /c curl -s -X GET https://raw.githubusercontent.com/a2x/cs2-dumper/main/output/client_dll.json | C:\Windows\System32\cmd.exe | — | DragonBurn.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5240 | C:\WINDOWS\system32\cmd.exe /c curl -s -X GET https://raw.githubusercontent.com/ByteCorum/DragonBurn/data/version | C:\Windows\System32\cmd.exe | — | DragonBurn.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 911
Read events
1 908
Write events
2
Delete events
1
Modification events
| (PID) Process: | (6536) kdmapper.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\jpMZVnyMZaRDtgVajGnPYUsG |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6536) kdmapper.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\jpMZVnyMZaRDtgVajGnPYUsG |
| Operation: | write | Name: | ImagePath |
Value: \??\C:\Users\admin\AppData\Local\Temp\jpMZVnyMZaRDtgVajGnPYUsG | |||
| (PID) Process: | (6536) kdmapper.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\jpMZVnyMZaRDtgVajGnPYUsG |
| Operation: | write | Name: | Type |
Value: 1 | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6536 | kdmapper.exe | C:\Users\admin\AppData\Local\Temp\jpMZVnyMZaRDtgVajGnPYUsG | executable | |
MD5:1898CEDA3247213C084F43637EF163B3 | SHA256:4429F32DB1CC70567919D7D47B844A91CF1329A6CD116F582305F3B7B60CD60B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
36
DNS requests
20
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.186:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
760 | lsass.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | — | — | whitelisted |
6824 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6288 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6288 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4308 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6092 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.186:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.38.73.129:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.86.251.22:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3976 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |