| download: | bdcamsetup.exe |
| Full analysis: | https://app.any.run/tasks/d66dc15e-9774-4157-9eec-16d5b5640202 |
| Verdict: | Malicious activity |
| Analysis date: | April 21, 2020, 20:57:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 4081D775C5380AD6E61CAE175C2517AE |
| SHA1: | 23E937CADF132DE71FEC3A37CB0B28DC00542597 |
| SHA256: | DCD940767267E743D1255F217D7059F90AE4BB5B5492C3C78D2E5E1FCAD7FCA9 |
| SSDEEP: | 393216:ttmKzC8/KKrUidPz7W46r/RNLbu1bcuuKh9xEpEGyu51qWqFGzmoRd643hPuXHv6:DmKzFyfLR1bOTuKh9e7eZ430PYNr/h4U |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- BDMPEG1SETUP.EXE (PID: 1232)
Loads dropped or rewritten executable
- bdcamsetup.exe (PID: 2512)
- BDMPEG1SETUP.EXE (PID: 1232)
- rundll32.exe (PID: 3308)
- bdcam.exe (PID: 1168)
Application was dropped or rewritten from another process
- BDMPEG1SETUP.EXE (PID: 1232)
- bdcam.exe (PID: 1168)
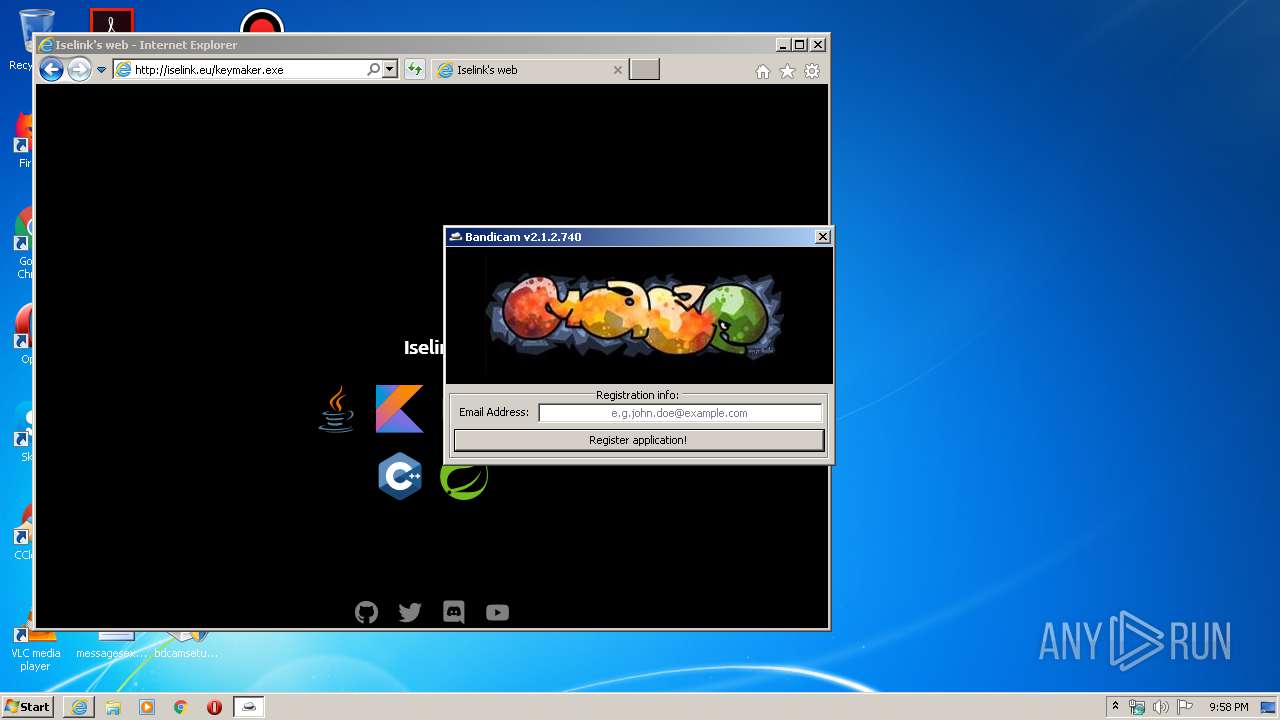
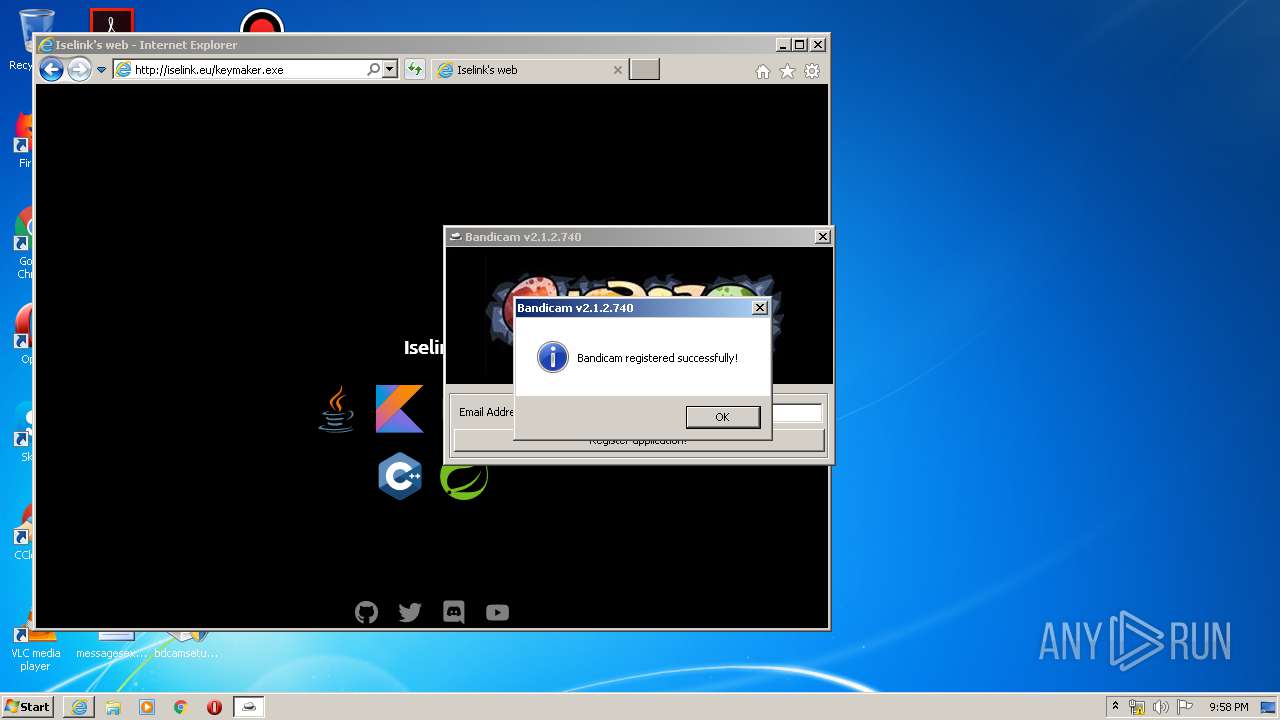
- keymaker.exe (PID: 2052)
- bdcam.exe (PID: 3360)
SUSPICIOUS
Executable content was dropped or overwritten
- bdcamsetup.exe (PID: 2512)
- BDMPEG1SETUP.EXE (PID: 1232)
- iexplore.exe (PID: 1720)
- iexplore.exe (PID: 2068)
Creates COM task schedule object
- BDMPEG1SETUP.EXE (PID: 1232)
Creates files in the program directory
- BDMPEG1SETUP.EXE (PID: 1232)
- bdcamsetup.exe (PID: 2512)
Modifies the open verb of a shell class
- bdcam.exe (PID: 1168)
Creates files in the Windows directory
- BDMPEG1SETUP.EXE (PID: 1232)
Creates a software uninstall entry
- BDMPEG1SETUP.EXE (PID: 1232)
- bdcamsetup.exe (PID: 2512)
Changes IE settings (feature browser emulation)
- bdcamsetup.exe (PID: 2512)
Uses RUNDLL32.EXE to load library
- bdcam.exe (PID: 1168)
Starts Internet Explorer
- bdcamsetup.exe (PID: 2512)
Reads Internet Cache Settings
- bdcamsetup.exe (PID: 2512)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2068)
- iexplore.exe (PID: 1720)
Changes internet zones settings
- iexplore.exe (PID: 2068)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2068)
Reads internet explorer settings
- iexplore.exe (PID: 1720)
Creates files in the user directory
- iexplore.exe (PID: 1720)
Manual execution by user
- bdcam.exe (PID: 3360)
Reads settings of System Certificates
- iexplore.exe (PID: 1720)
Changes settings of System certificates
- iexplore.exe (PID: 1720)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1720)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:12:11 22:50:41+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 25088 |
| InitializedDataSize: | 141824 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x32fe |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.5.8.1673 |
| ProductVersionNumber: | 4.5.8.1673 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Arabic |
| CharacterSet: | Windows, Arabic |
| Comments: | Bandicam Setup File (2020-04-03 오전 3:59:43) |
| CompanyName: | Bandicam Company |
| FileDescription: | Bandicam Setup File |
| FileVersion: | 4.5.8.1673 |
| LegalCopyright: | Copyright(C) 2009-2020 Bandicam.com, All rights reserved. |
| ProductName: | Bandicam |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 11-Dec-2016 21:50:41 |
| Detected languages: |
|
| Comments: | Bandicam Setup File (2020-04-03 오전 3:59:43) |
| CompanyName: | Bandicam Company |
| FileDescription: | Bandicam Setup File |
| FileVersion: | 4.5.8.1673 |
| LegalCopyright: | Copyright(C) 2009-2020 Bandicam.com, All rights reserved. |
| ProductName: | Bandicam |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000C8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 11-Dec-2016 21:50:41 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0000608D | 0x00006200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.4239 |
.rdata | 0x00008000 | 0x000013A4 | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.16231 |
.data | 0x0000A000 | 0x000202F8 | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.89813 |
.ndata | 0x0002B000 | 0x00017000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x00042000 | 0x00019968 | 0x00019A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.83261 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.28813 | 1070 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 4.67767 | 9640 | UNKNOWN | English - United States | RT_ICON |
3 | 5.31734 | 4264 | UNKNOWN | English - United States | RT_ICON |
4 | 5.28764 | 3752 | UNKNOWN | English - United States | RT_ICON |
5 | 5.66571 | 2216 | UNKNOWN | English - United States | RT_ICON |
6 | 5.26475 | 1384 | UNKNOWN | English - United States | RT_ICON |
7 | 5.82212 | 1128 | UNKNOWN | English - United States | RT_ICON |
102 | 2.72924 | 180 | UNKNOWN | English - United States | RT_DIALOG |
103 | 2.71858 | 104 | UNKNOWN | English - United States | RT_GROUP_ICON |
104 | 2.6693 | 280 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
52
Monitored processes
10
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 880 | "C:\Users\admin\Desktop\bdcamsetup.exe" | C:\Users\admin\Desktop\bdcamsetup.exe | — | explorer.exe | |||||||||||
User: admin Company: Bandicam Company Integrity Level: MEDIUM Description: Bandicam Setup File Exit code: 3221226540 Version: 4.5.8.1673 Modules
| |||||||||||||||
| 1168 | "C:\Program Files\Bandicam\bdcam.exe" /install | C:\Program Files\Bandicam\bdcam.exe | — | bdcamsetup.exe | |||||||||||
User: admin Company: Bandicam Company Integrity Level: HIGH Description: Bandicam - bdcam.exe Exit code: 0 Version: 4.5.8.1673 Modules
| |||||||||||||||
| 1232 | "C:\Users\admin\AppData\Local\Temp\BDMPEG1SETUP.EXE" /S | C:\Users\admin\AppData\Local\Temp\BDMPEG1SETUP.EXE | bdcamsetup.exe | ||||||||||||
User: admin Company: Bandicam Company Integrity Level: HIGH Description: Bandicam MPEG-1 Decoder Setup File Exit code: 0 Version: V1.0.5.17 Modules
| |||||||||||||||
| 1720 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2068 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2052 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\keymaker.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\keymaker.exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2068 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.bandicam.com/f.php?id=eng_app_complete_install&v=2&lang=en | C:\Program Files\Internet Explorer\iexplore.exe | bdcamsetup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2512 | "C:\Users\admin\Desktop\bdcamsetup.exe" | C:\Users\admin\Desktop\bdcamsetup.exe | explorer.exe | ||||||||||||
User: admin Company: Bandicam Company Integrity Level: HIGH Description: Bandicam Setup File Exit code: 0 Version: 4.5.8.1673 Modules
| |||||||||||||||
| 2796 | "regsvr32" /s "C:\Program Files\BandiMPEG1\bdfilters64.dll" | C:\Windows\system32\regsvr32.exe | — | BDMPEG1SETUP.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3308 | "C:\Windows\system32\rundll32.exe" "C:\Program Files\Bandicam\bdcamvk32.dll",RegDll | C:\Windows\system32\rundll32.exe | — | bdcam.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3360 | "C:\Program Files\Bandicam\bdcam.exe" | C:\Program Files\Bandicam\bdcam.exe | — | explorer.exe | |||||||||||
User: admin Company: Bandicam Company Integrity Level: MEDIUM Description: Bandicam - bdcam.exe Exit code: 3221226540 Version: 4.5.8.1673 | |||||||||||||||
Total events
3 497
Read events
1 652
Write events
1 845
Delete events
0
Modification events
| (PID) Process: | (1232) BDMPEG1SETUP.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{89C4B786-A490-4A3E-AA70-E6A8C61D3689} |
| Operation: | write | Name: | |
Value: Bandicam MPEG-1 Video Decoder | |||
| (PID) Process: | (1232) BDMPEG1SETUP.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{89C4B786-A490-4A3E-AA70-E6A8C61D3689}\InprocServer32 |
| Operation: | write | Name: | |
Value: C:\Program Files\BandiMPEG1\bdfilters.dll | |||
| (PID) Process: | (1232) BDMPEG1SETUP.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{89C4B786-A490-4A3E-AA70-E6A8C61D3689}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Both | |||
| (PID) Process: | (1232) BDMPEG1SETUP.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{A1C6833E-A3EC-4397-9FA9-151792F3408F} |
| Operation: | write | Name: | |
Value: Bandicam MPEG-1 Video Property | |||
| (PID) Process: | (1232) BDMPEG1SETUP.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{A1C6833E-A3EC-4397-9FA9-151792F3408F}\InprocServer32 |
| Operation: | write | Name: | |
Value: C:\Program Files\BandiMPEG1\bdfilters.dll | |||
| (PID) Process: | (1232) BDMPEG1SETUP.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{A1C6833E-A3EC-4397-9FA9-151792F3408F}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Both | |||
| (PID) Process: | (1232) BDMPEG1SETUP.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{E2E7539A-CECF-4A6A-B187-939943ECEF05} |
| Operation: | write | Name: | |
Value: Bandicam MPEG-1 Audio Decoder | |||
| (PID) Process: | (1232) BDMPEG1SETUP.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{E2E7539A-CECF-4A6A-B187-939943ECEF05}\InprocServer32 |
| Operation: | write | Name: | |
Value: C:\Program Files\BandiMPEG1\bdfilters.dll | |||
| (PID) Process: | (1232) BDMPEG1SETUP.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{E2E7539A-CECF-4A6A-B187-939943ECEF05}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Both | |||
| (PID) Process: | (1232) BDMPEG1SETUP.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{F4F5C9E9-CFCC-4C65-A8BD-0423A338F188} |
| Operation: | write | Name: | |
Value: Bandicam MPEG-1 Audio Property | |||
Executable files
27
Suspicious files
27
Text files
137
Unknown types
33
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1232 | BDMPEG1SETUP.EXE | C:\Users\admin\AppData\Local\Temp\nsj1CB5.tmp\System.dll | — | |
MD5:— | SHA256:— | |||
| 1232 | BDMPEG1SETUP.EXE | C:\Users\admin\AppData\Local\Temp\nss1A33.tmp | — | |
MD5:— | SHA256:— | |||
| 2512 | bdcamsetup.exe | C:\Users\admin\AppData\Local\Temp\nss11D.tmp\ioSpecial.ini | text | |
MD5:— | SHA256:— | |||
| 2512 | bdcamsetup.exe | C:\Users\admin\AppData\Local\Temp\nss11D.tmp\modern-wizard.bmp | image | |
MD5:DF49E245ECA7BB28691FAF396C32B934 | SHA256:B751FA1A1A2291BA1282D49936CD641C4E4340794F475294ABD5E4817952A41E | |||
| 1232 | BDMPEG1SETUP.EXE | C:\Users\Administrator\AppData\Local\Microsoft\Windows\UsrClass.dat | hiv | |
MD5:— | SHA256:— | |||
| 1232 | BDMPEG1SETUP.EXE | C:\Users\Administrator\AppData\Local\Microsoft\Windows\UsrClass.dat.LOG1 | log | |
MD5:— | SHA256:— | |||
| 1232 | BDMPEG1SETUP.EXE | C:\Users\Administrator\NTUSER.DAT | hiv | |
MD5:— | SHA256:— | |||
| 2512 | bdcamsetup.exe | C:\Program Files\Bandicam\bdcam.exe | executable | |
MD5:— | SHA256:— | |||
| 1232 | BDMPEG1SETUP.EXE | C:\Users\Administrator\NTUSER.DAT.LOG1 | log | |
MD5:— | SHA256:— | |||
| 1232 | BDMPEG1SETUP.EXE | C:\Users\admin\AppData\Local\Temp\bdfilters.dll | executable | |
MD5:ED730387FDCD684B756601B863C47417 | SHA256:9CBC29696AD2D582E251BF9C4BE5CCE618753FA43551D2474E1AE5CC5E1245E5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
41
TCP/UDP connections
34
DNS requests
19
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1720 | iexplore.exe | GET | — | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=isel&maxwidth=398&rowheight=20§ionHeight=160&FORM=IE11SS&market=en-US | US | — | — | whitelisted |
1720 | iexplore.exe | GET | — | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=iselink.eu&maxwidth=398&rowheight=20§ionHeight=160&FORM=IE11SS&market=en-US | US | — | — | whitelisted |
1720 | iexplore.exe | GET | 200 | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=iselin&maxwidth=398&rowheight=20§ionHeight=160&FORM=IE11SS&market=en-US | US | xml | 233 b | whitelisted |
1720 | iexplore.exe | GET | 200 | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=iseli&maxwidth=398&rowheight=20§ionHeight=160&FORM=IE11SS&market=en-US | US | xml | 228 b | whitelisted |
1720 | iexplore.exe | GET | 200 | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=iselink.e&maxwidth=398&rowheight=20§ionHeight=160&FORM=IE11SS&market=en-US | US | xml | 238 b | whitelisted |
1720 | iexplore.exe | GET | 200 | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=ise&maxwidth=32765&rowheight=20§ionHeight=160&FORM=IE11SS&market=en-US | US | xml | 223 b | whitelisted |
1720 | iexplore.exe | GET | 200 | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=iselink.eu%3Fke&maxwidth=398&rowheight=20§ionHeight=160&FORM=IE11SS&market=en-US | US | xml | 168 b | whitelisted |
1720 | iexplore.exe | GET | 200 | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=iselink&maxwidth=398&rowheight=20§ionHeight=160&FORM=IE11SS&market=en-US | US | xml | 222 b | whitelisted |
1720 | iexplore.exe | GET | 200 | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=iselink.eu%3Fkeymak&maxwidth=398&rowheight=20§ionHeight=160&FORM=IE11SS&market=en-US | US | xml | 169 b | whitelisted |
1720 | iexplore.exe | GET | 200 | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=iselink.eu%3Fkeym&maxwidth=398&rowheight=20§ionHeight=160&FORM=IE11SS&market=en-US | US | xml | 170 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1720 | iexplore.exe | 151.101.2.217:443 | www.bandicam.com | Fastly | US | suspicious |
1720 | iexplore.exe | 13.107.5.80:80 | api.bing.com | Microsoft Corporation | US | whitelisted |
2068 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1720 | iexplore.exe | 104.18.21.226:80 | ocsp.globalsign.com | Cloudflare Inc | US | shared |
1720 | iexplore.exe | 104.18.20.226:80 | ocsp.globalsign.com | Cloudflare Inc | US | shared |
1720 | iexplore.exe | 172.217.22.99:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
1720 | iexplore.exe | 172.217.21.227:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
1720 | iexplore.exe | 172.217.22.8:443 | www.googletagmanager.com | Google Inc. | US | whitelisted |
1720 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1720 | iexplore.exe | 172.217.18.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bandicam.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
static.bandicam.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
iselink.eu |
| suspicious |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1720 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |