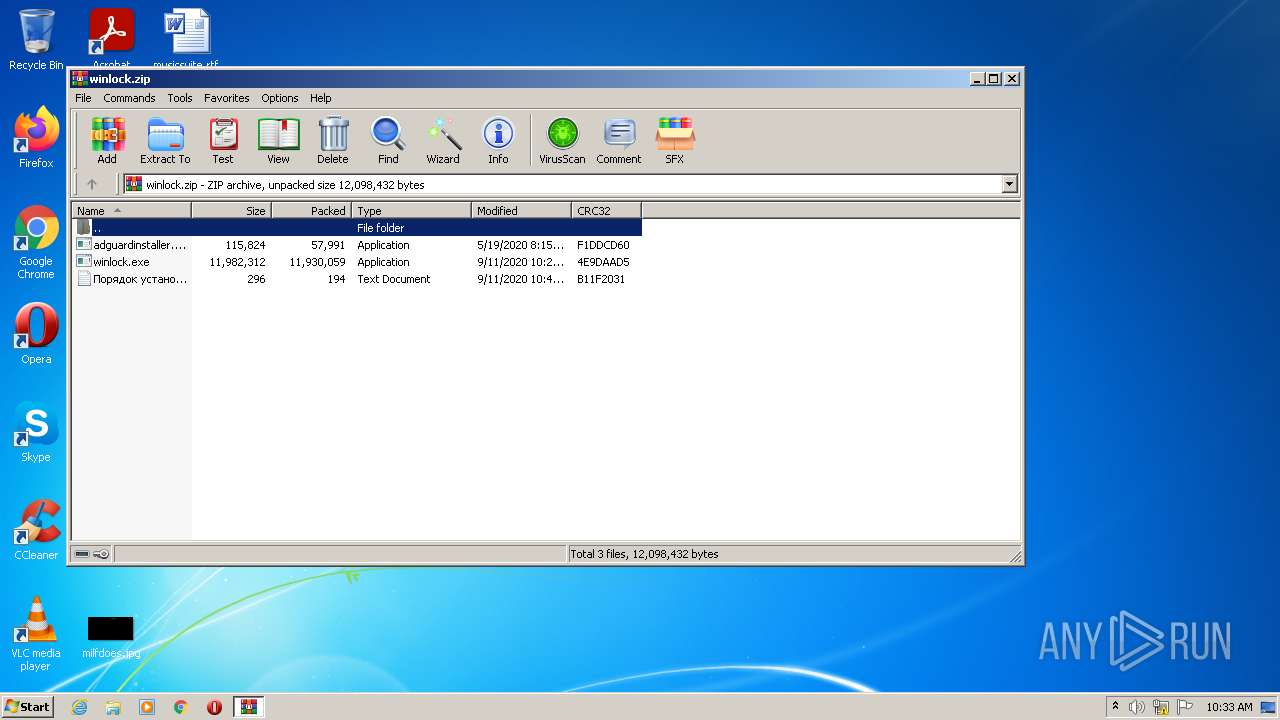
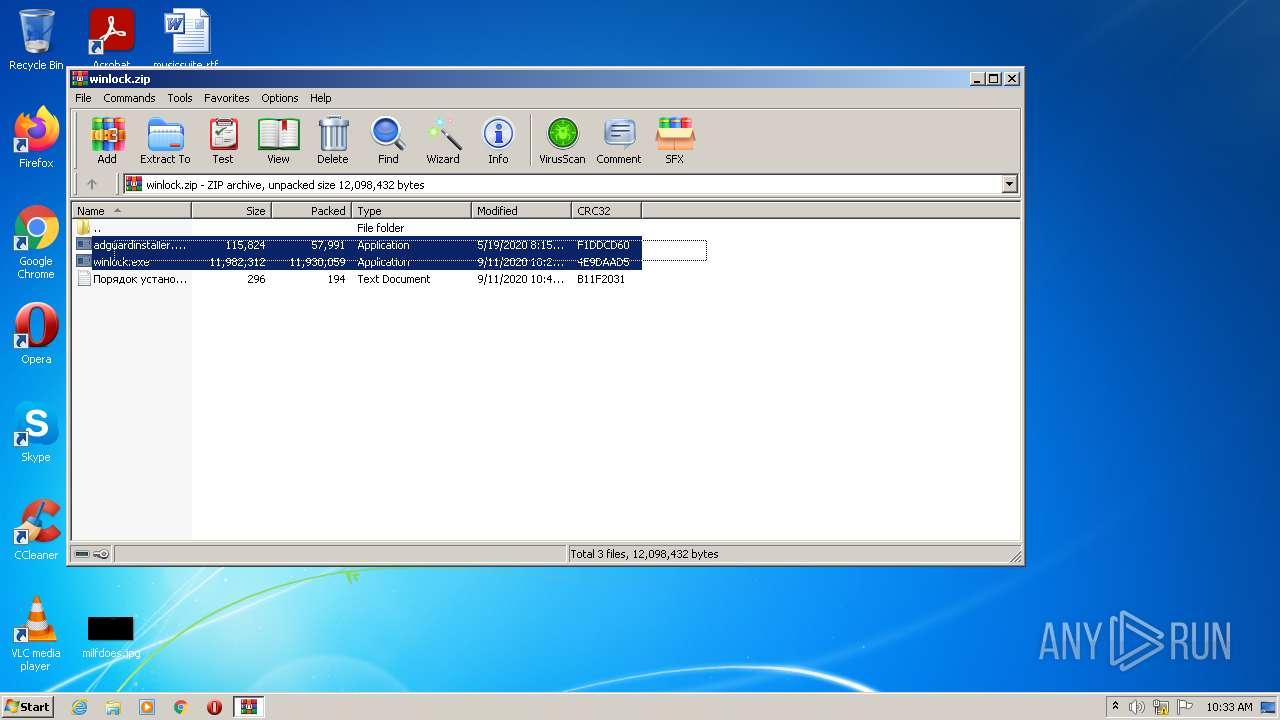
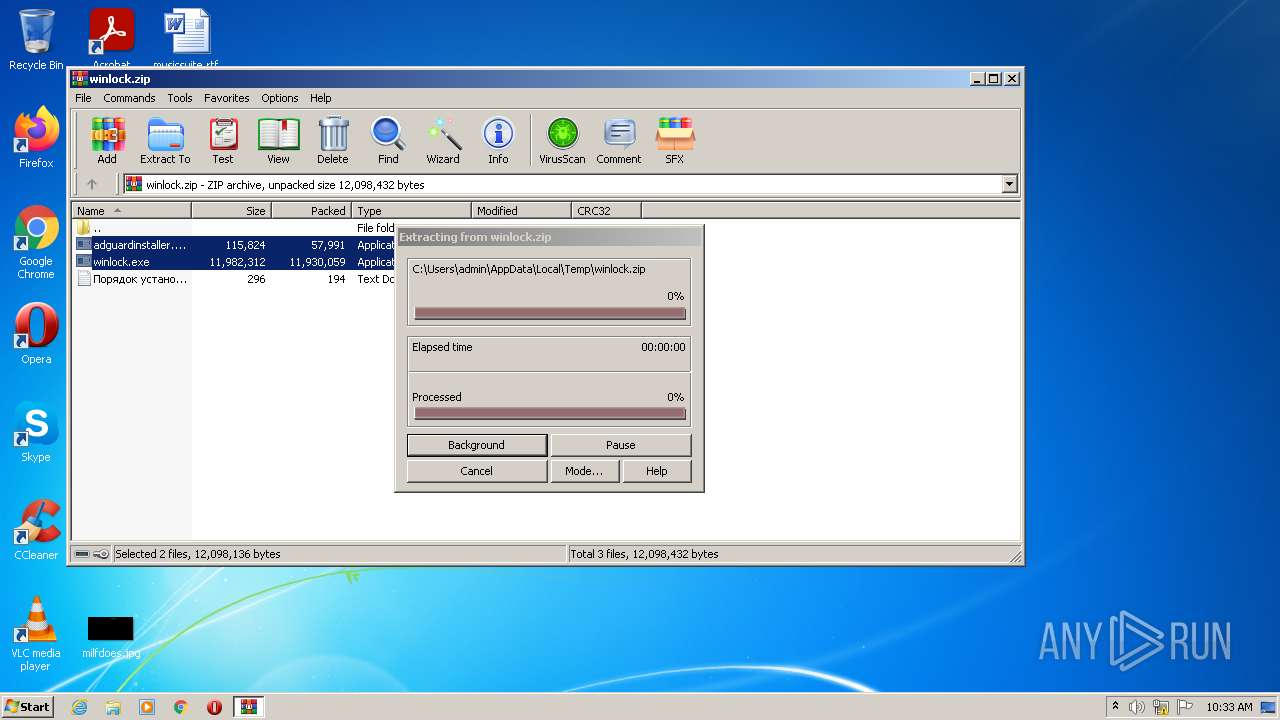
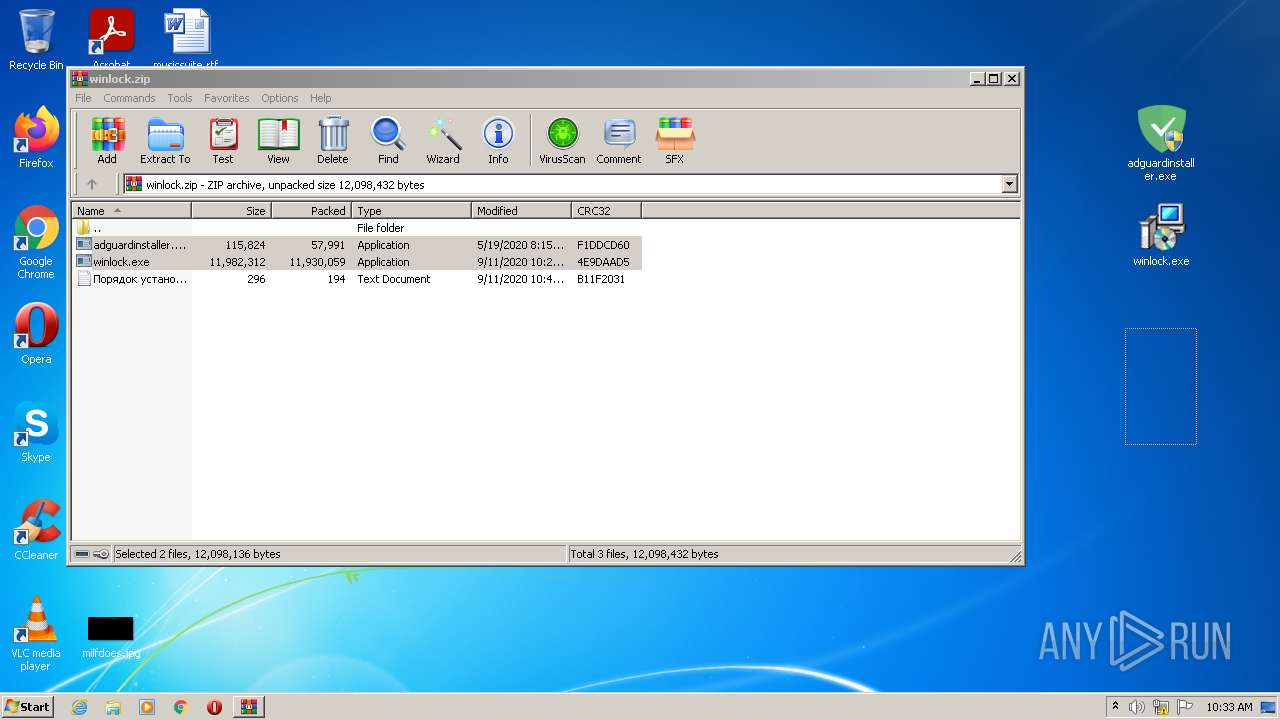
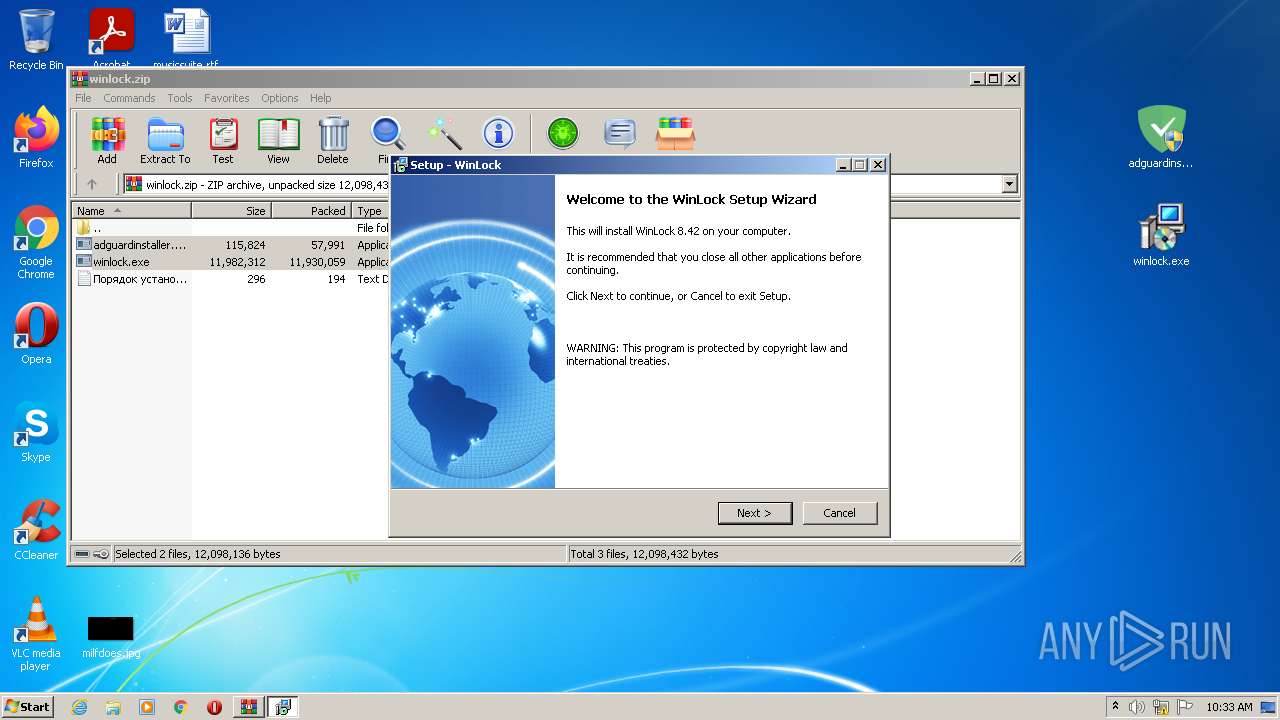
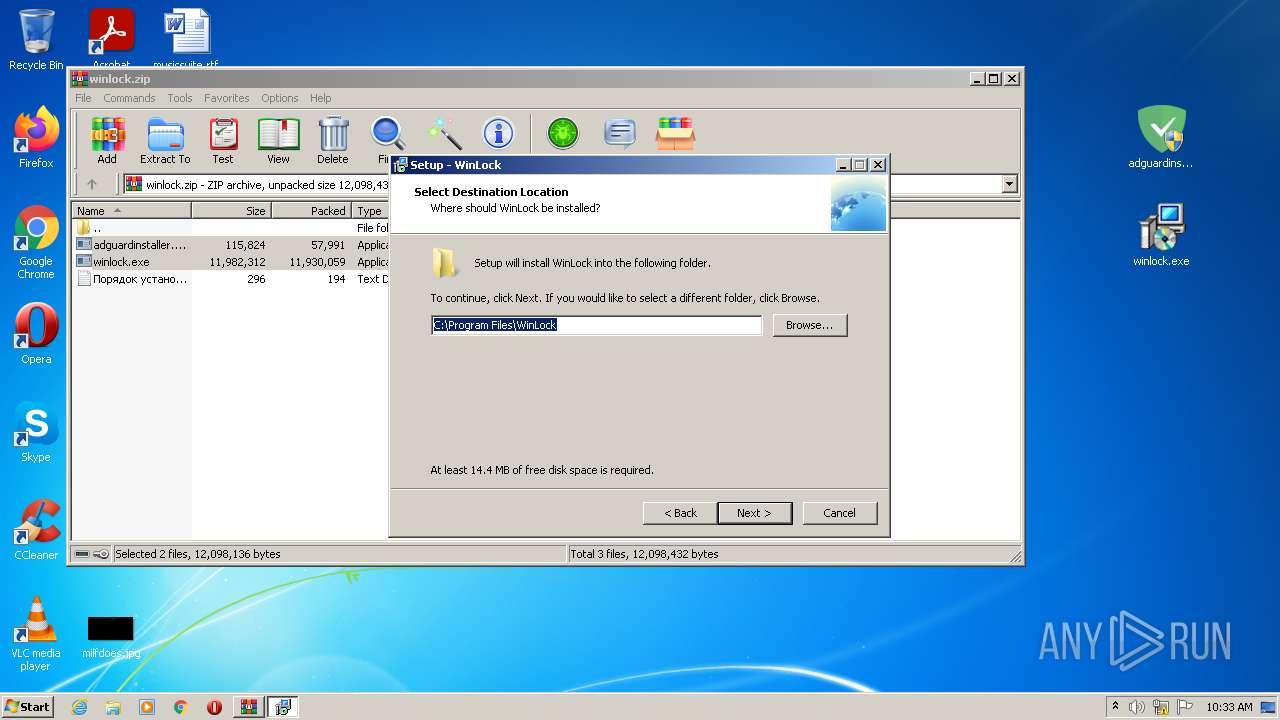
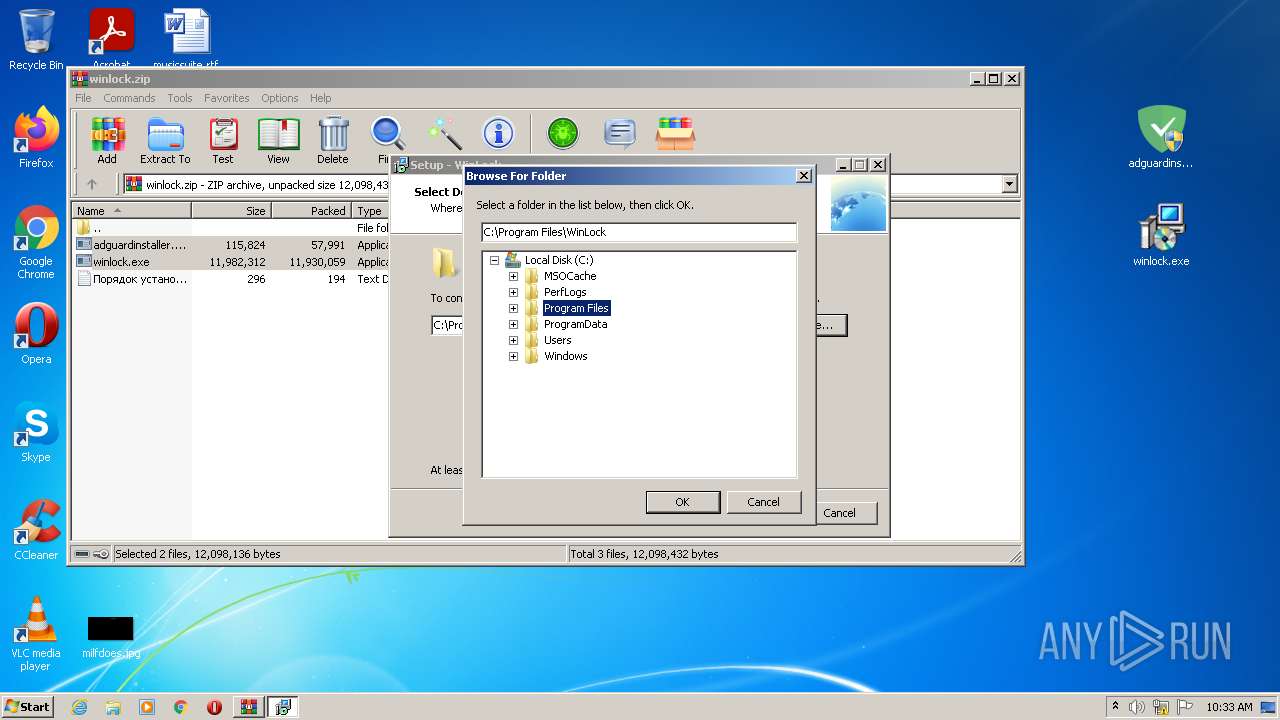
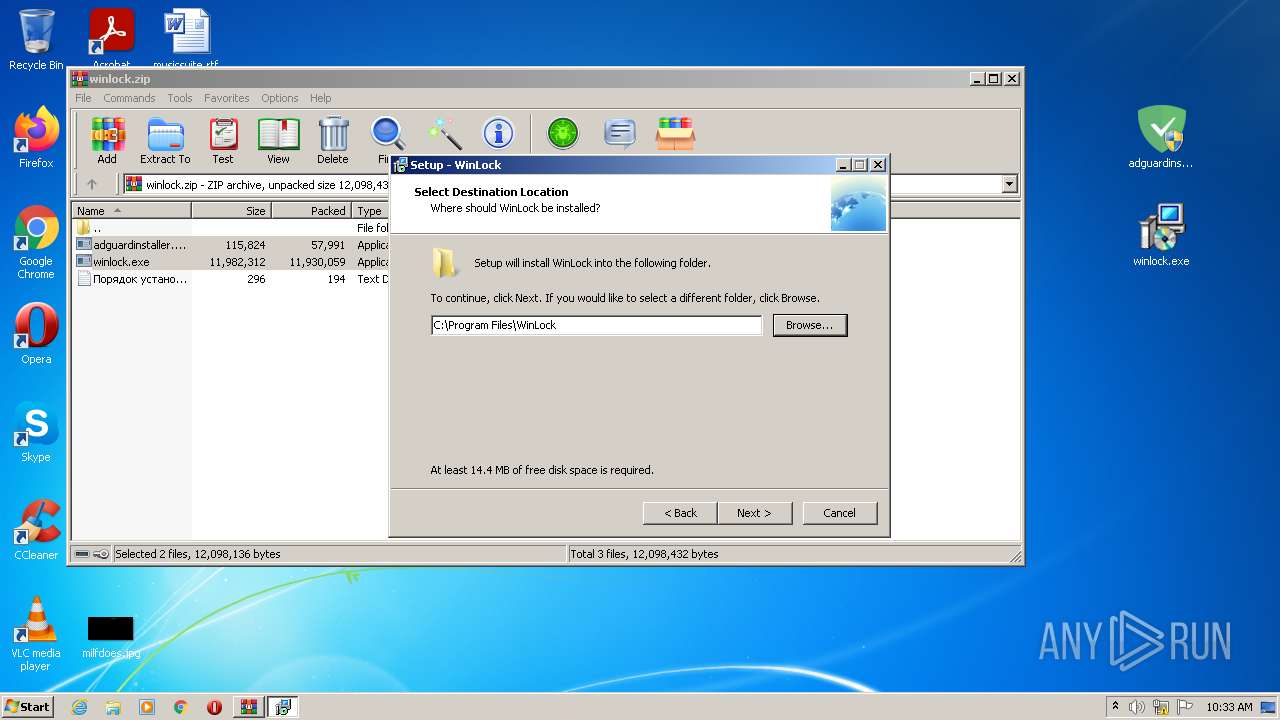
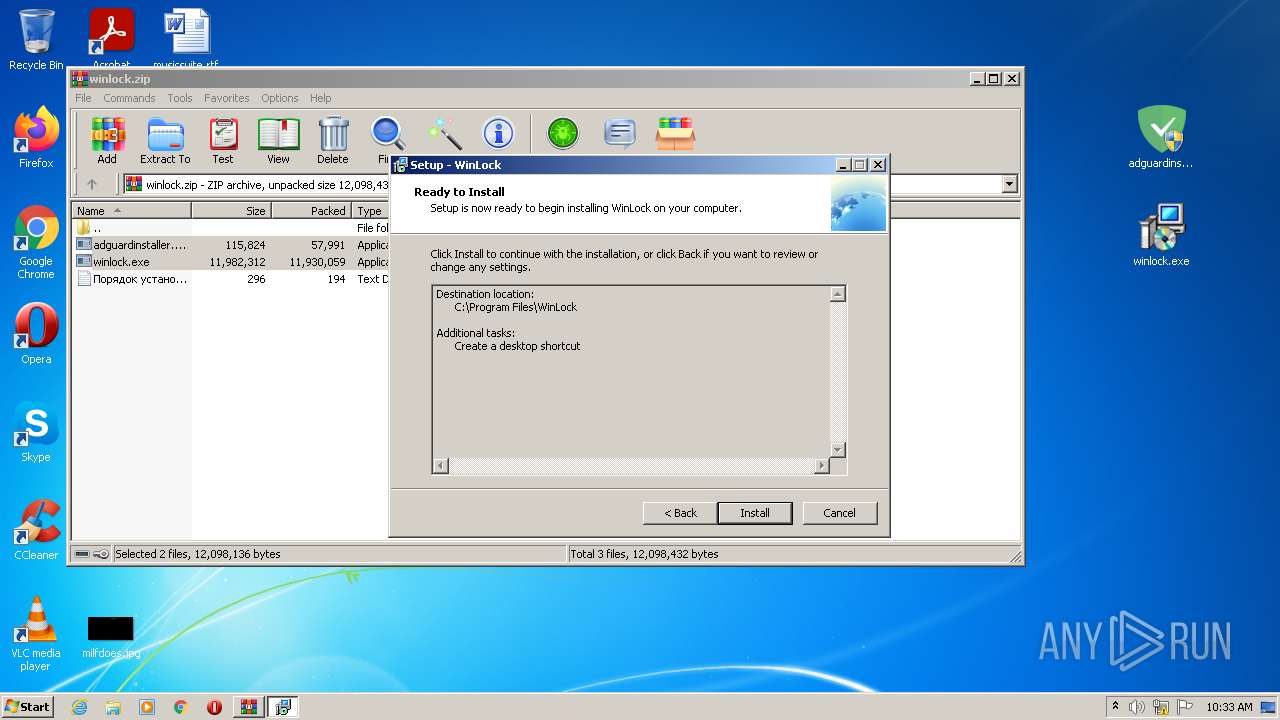
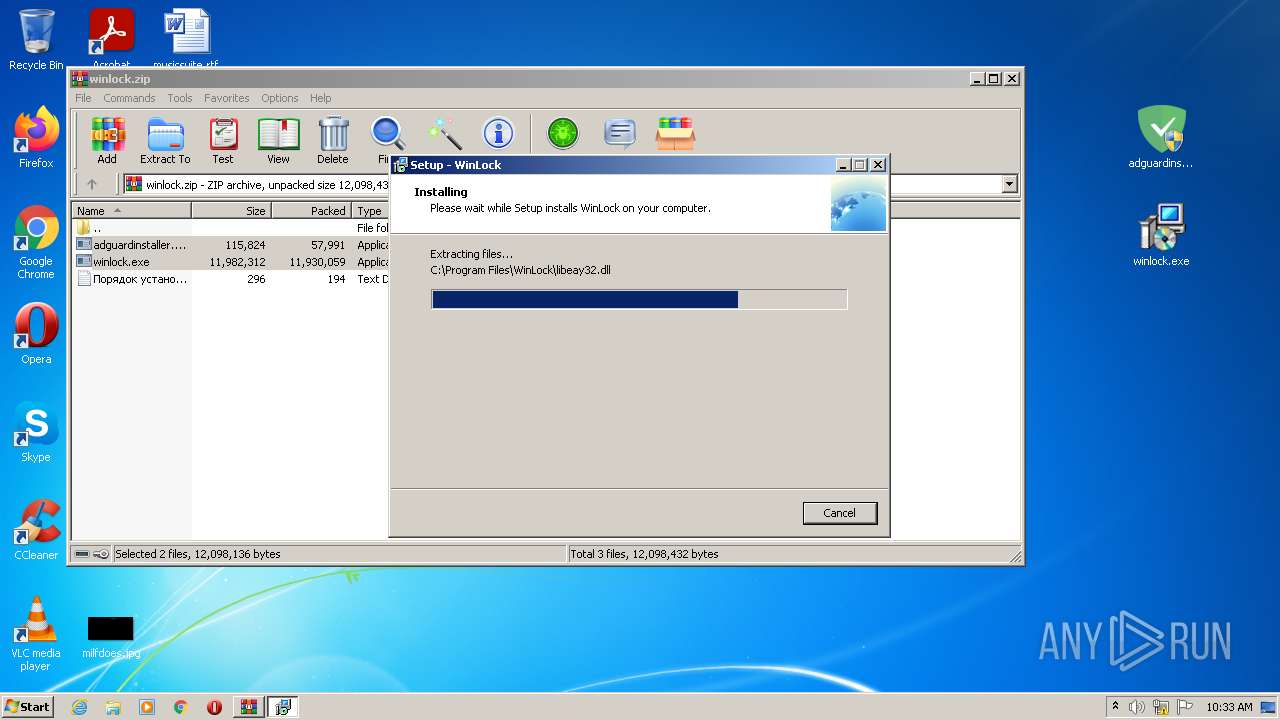
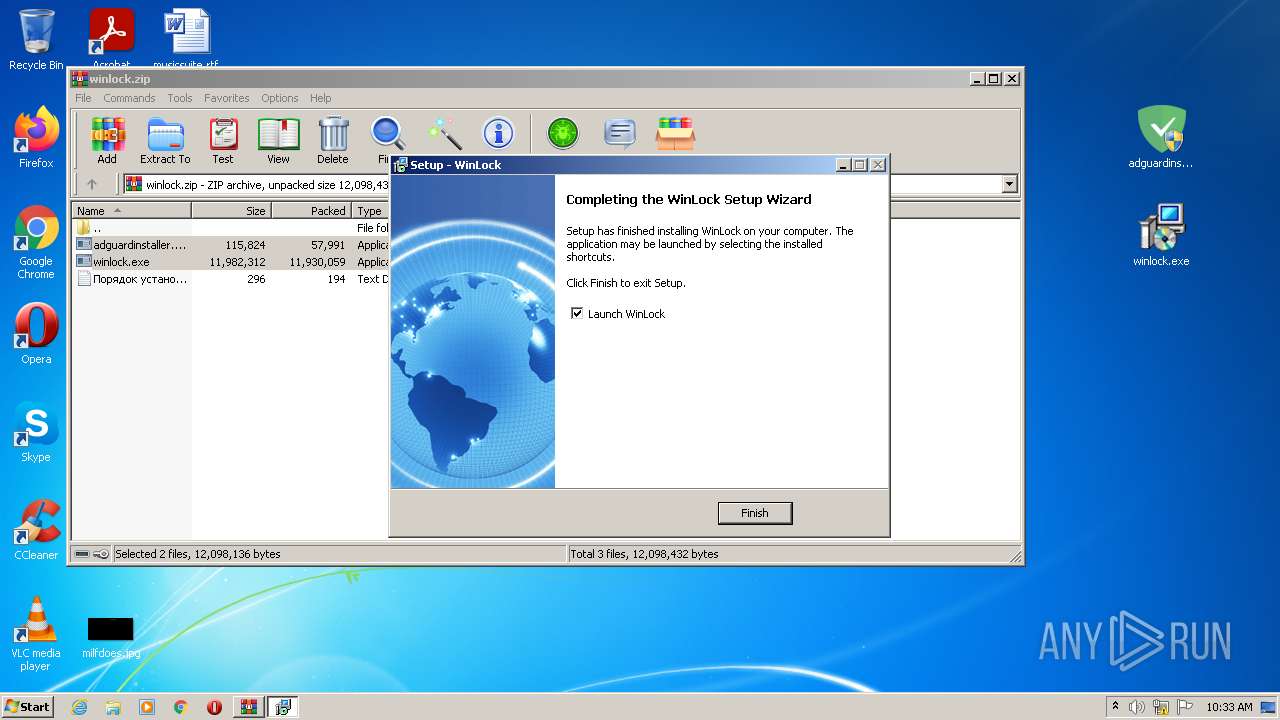
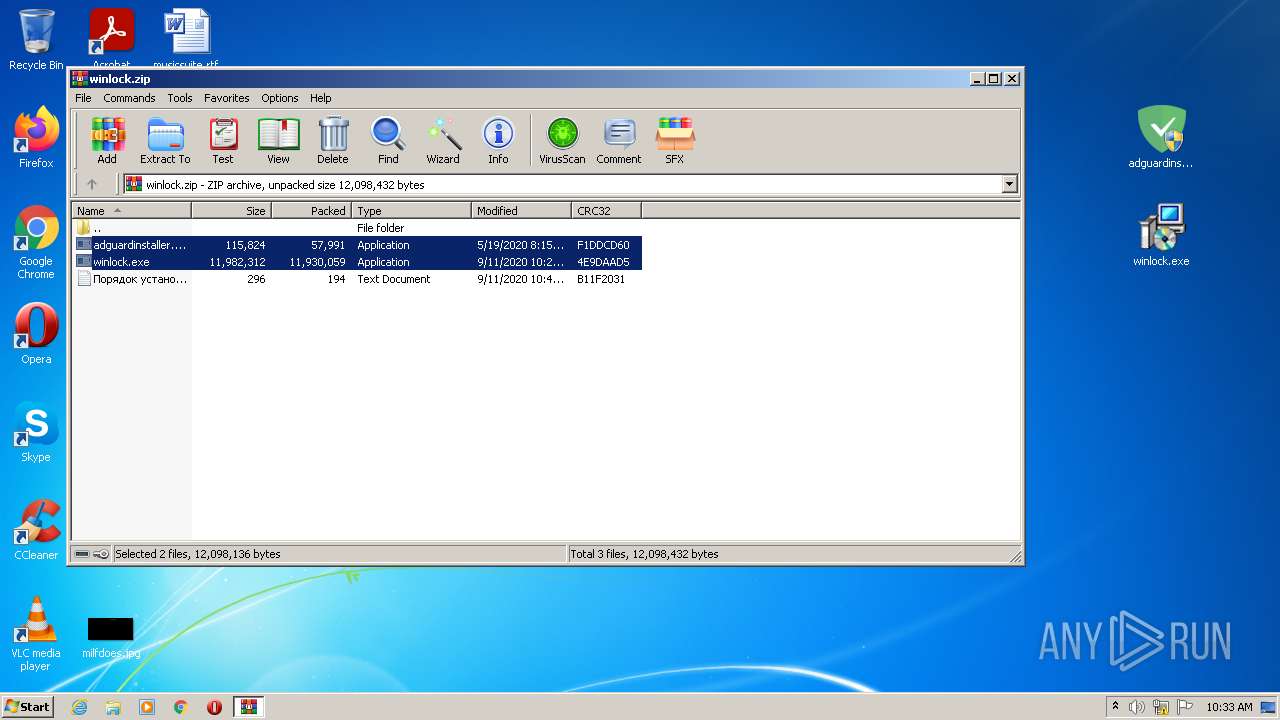
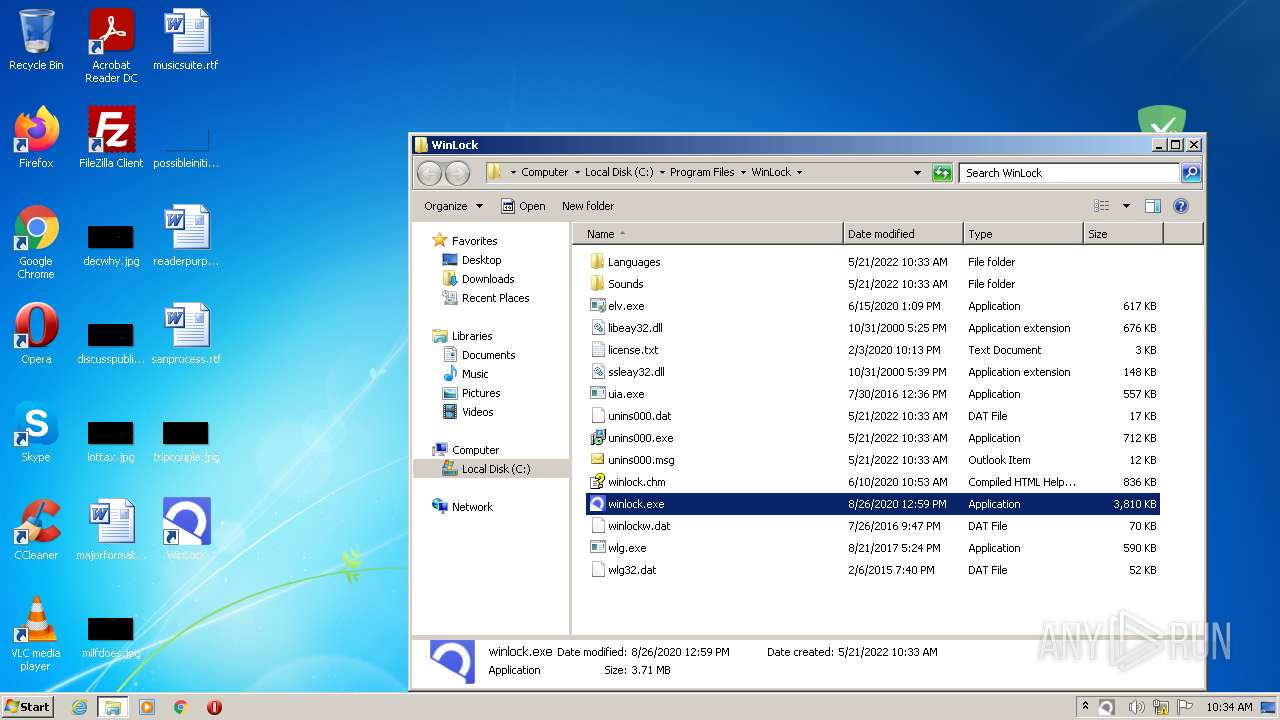
| File name: | winlock.zip |
| Full analysis: | https://app.any.run/tasks/867d3bf9-cf8c-4508-8013-459aee3547bf |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2022, 09:33:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | F1643CC4AAC7DD15CFF9E5A87CD9E94D |
| SHA1: | 900E3FCFF5EC7B31243C3521ECAFC12262EB9339 |
| SHA256: | DCC88485E6CB3380EE0E5768498FAE0D45338A3E06CAA1F8CF09E7C7B97458FE |
| SSDEEP: | 196608:vO0d1w14Oq24+LBfa+543b76JmzwFtbVP3CFwAVjOra3GW0HBqJ9:20Xw15LhaeOOJLfB3CFJVSFkX |
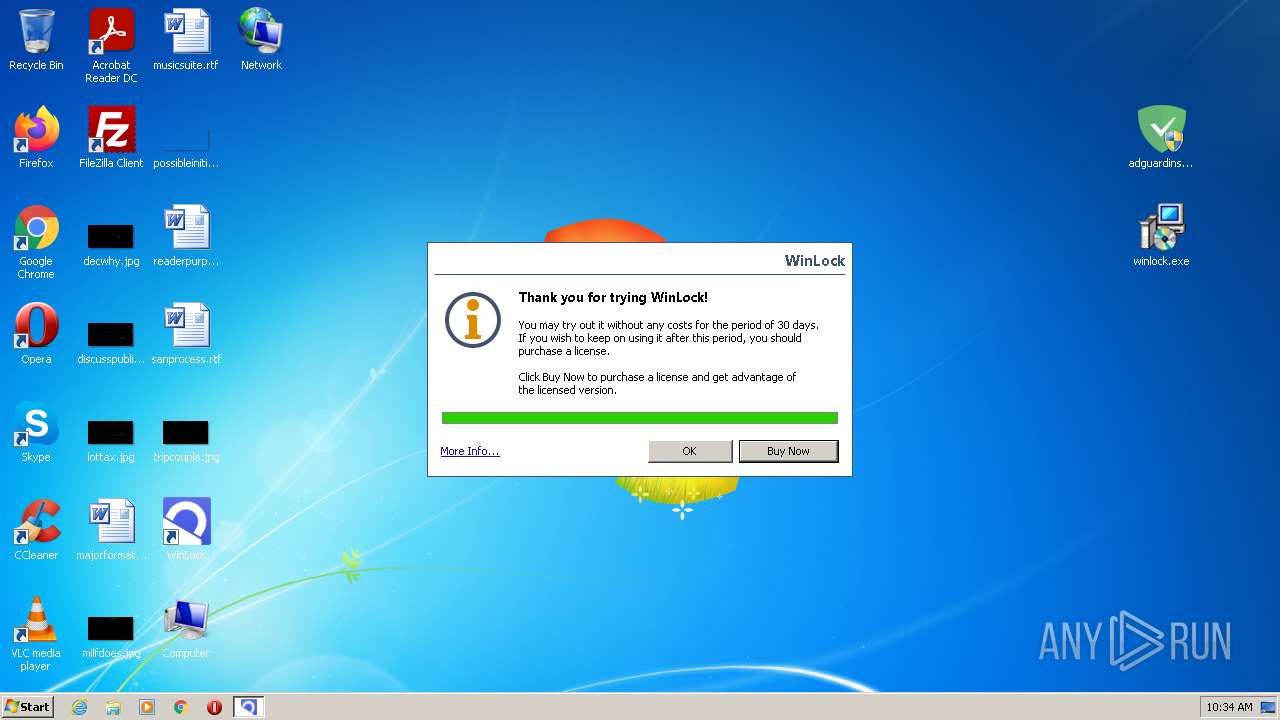
MALICIOUS
Drops executable file immediately after starts
- WinRAR.exe (PID: 3788)
- winlock.tmp (PID: 1652)
- winlock.exe (PID: 3548)
Application was dropped or rewritten from another process
- winlock.exe (PID: 3548)
- uia.exe (PID: 1808)
- winlock.exe (PID: 2488)
- uia.exe (PID: 3360)
- winlock.exe (PID: 2044)
Adds new firewall rule via NETSH.EXE
- winlock.tmp (PID: 1652)
Changes the autorun value in the registry
- winlock.tmp (PID: 1652)
Loads dropped or rewritten executable
- winlock.exe (PID: 2488)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3788)
- winlock.exe (PID: 3548)
- winlock.tmp (PID: 1652)
- winlock.exe (PID: 2488)
- winlock.exe (PID: 2044)
- uia.exe (PID: 1808)
Creates a directory in Program Files
- winlock.tmp (PID: 1652)
Executable content was dropped or overwritten
- winlock.tmp (PID: 1652)
- WinRAR.exe (PID: 3788)
- winlock.exe (PID: 3548)
Reads the computer name
- WinRAR.exe (PID: 3788)
- winlock.exe (PID: 2488)
- winlock.tmp (PID: 1652)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3788)
- winlock.exe (PID: 3548)
- winlock.tmp (PID: 1652)
Uses NETSH.EXE for network configuration
- winlock.tmp (PID: 1652)
Reads Environment values
- netsh.exe (PID: 2764)
Reads the Windows organization settings
- winlock.tmp (PID: 1652)
Reads Windows owner or organization settings
- winlock.tmp (PID: 1652)
INFO
Manual execution by user
- winlock.exe (PID: 3548)
- winlock.exe (PID: 2488)
- winlock.exe (PID: 2044)
Creates a software uninstall entry
- winlock.tmp (PID: 1652)
Reads the computer name
- netsh.exe (PID: 2764)
Checks supported languages
- netsh.exe (PID: 2764)
Application was dropped or rewritten from another process
- winlock.tmp (PID: 1652)
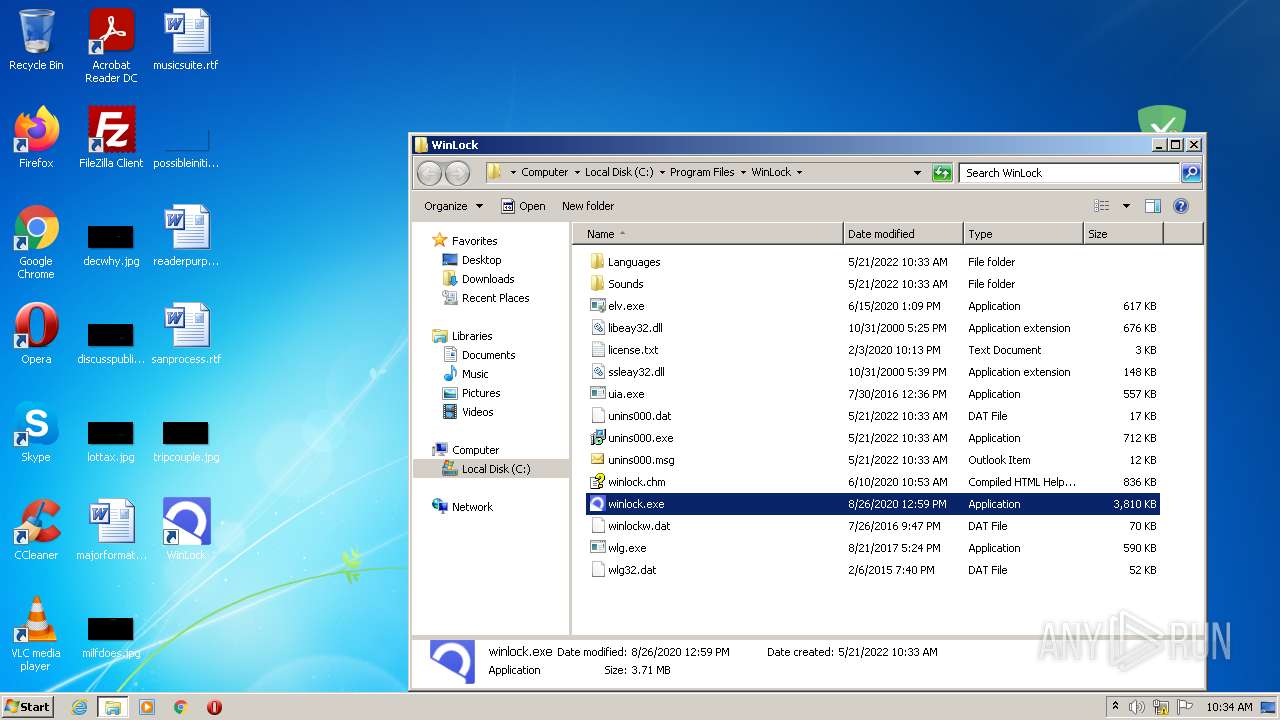
Creates files in the program directory
- winlock.tmp (PID: 1652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | ???冷? ??⠭????.txt |
|---|---|
| ZipUncompressedSize: | 296 |
| ZipCompressedSize: | 194 |
| ZipCRC: | 0xb11f2031 |
| ZipModifyDate: | 2020:09:11 12:42:00 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
50
Monitored processes
8
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1652 | "C:\Users\admin\AppData\Local\Temp\is-UA4C5.tmp\winlock.tmp" /SL5="$5017A,11624009,57856,C:\Users\admin\Desktop\winlock.exe" | C:\Users\admin\AppData\Local\Temp\is-UA4C5.tmp\winlock.tmp | winlock.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 1808 | "C:\Program Files\WinLock\uia.exe" | C:\Program Files\WinLock\uia.exe | winlock.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2044 | "C:\Program Files\WinLock\winlock.exe" | C:\Program Files\WinLock\winlock.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Crystal Office Systems Integrity Level: MEDIUM Description: WinLock Exit code: 0 Version: 8.4.2.0 Modules
| |||||||||||||||
| 2488 | "C:\Program Files\WinLock\winlock.exe" | C:\Program Files\WinLock\winlock.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Crystal Office Systems Integrity Level: MEDIUM Description: WinLock Exit code: 1073807364 Version: 8.4.2.0 Modules
| |||||||||||||||
| 2764 | "netsh.exe" advfirewall firewall add rule name="WinLock" dir=in program="C:\Program Files\WinLock\winlock.exe" action=allow | C:\Windows\system32\netsh.exe | — | winlock.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3360 | "C:\Program Files\WinLock\uia.exe" | C:\Program Files\WinLock\uia.exe | — | winlock.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
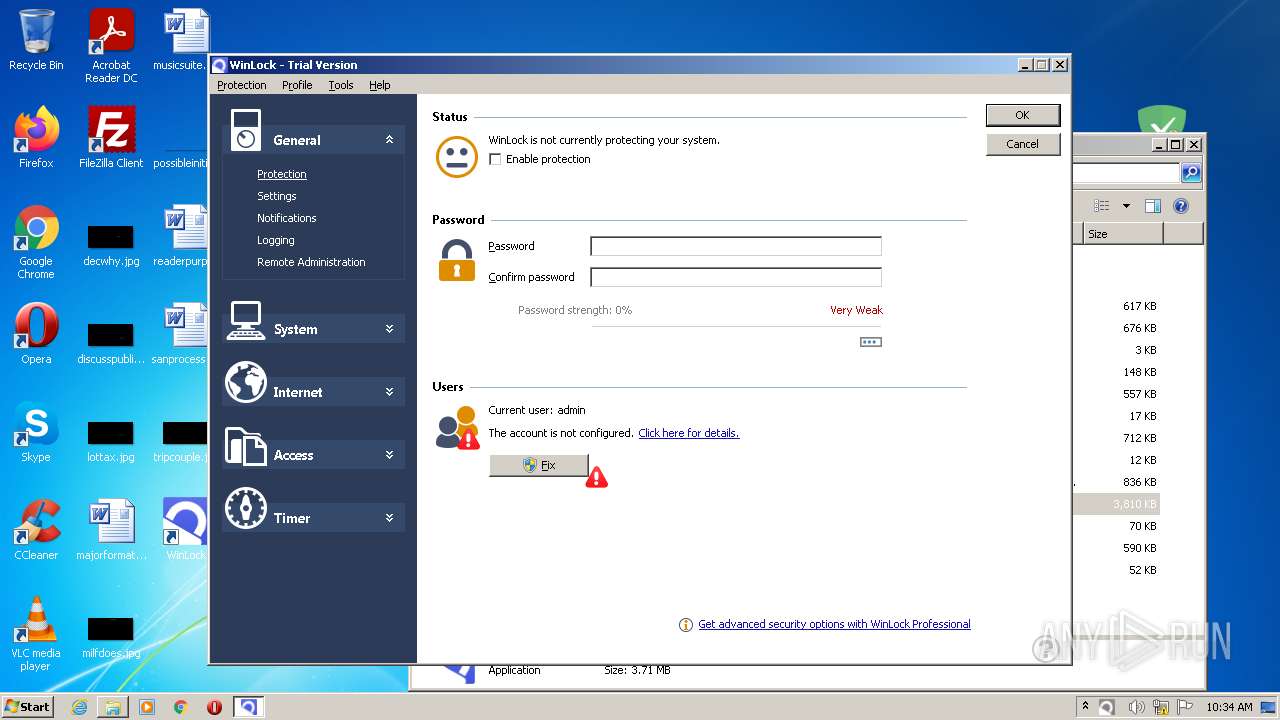
| 3548 | "C:\Users\admin\Desktop\winlock.exe" | C:\Users\admin\Desktop\winlock.exe | Explorer.EXE | ||||||||||||
User: admin Company: Crystal Office Systems Integrity Level: HIGH Description: WinLock Installation Exit code: 0 Version: 8.42 Modules
| |||||||||||||||
| 3788 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\winlock.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
2 892
Read events
2 711
Write events
174
Delete events
7
Modification events
| (PID) Process: | (3788) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3788) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3788) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3788) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3788) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3788) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\winlock.zip | |||
| (PID) Process: | (3788) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3788) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3788) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3788) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
21
Suspicious files
1
Text files
56
Unknown types
31
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1652 | winlock.tmp | C:\ProgramData\Crystal Office\WL\is-43D52.tmp | — | |
MD5:— | SHA256:— | |||
| 1652 | winlock.tmp | C:\ProgramData\Crystal Office\WL\winlockl.dat | — | |
MD5:— | SHA256:— | |||
| 3788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3788.27073\adguardinstaller.exe | executable | |
MD5:— | SHA256:— | |||
| 1652 | winlock.tmp | C:\Program Files\WinLock\is-C058P.tmp | executable | |
MD5:— | SHA256:— | |||
| 3788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3788.27073\winlock.exe | executable | |
MD5:— | SHA256:— | |||
| 3548 | winlock.exe | C:\Users\admin\AppData\Local\Temp\is-UA4C5.tmp\winlock.tmp | executable | |
MD5:— | SHA256:— | |||
| 1652 | winlock.tmp | C:\Program Files\WinLock\is-LR028.tmp | executable | |
MD5:— | SHA256:— | |||
| 1652 | winlock.tmp | C:\Program Files\WinLock\unins000.exe | executable | |
MD5:— | SHA256:— | |||
| 1652 | winlock.tmp | C:\Program Files\WinLock\elv.exe | executable | |
MD5:— | SHA256:— | |||
| 1652 | winlock.tmp | C:\Program Files\WinLock\wlg32.dat | executable | |
MD5:150B29B89FF77889EF4A59EF3AAC3BD7 | SHA256:A62ED0A37DF0644B367DD679E8AF2570F9C5CE3397B75EA84346382FF64CAF7E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 23.205.225.13:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=132976028961320000 | NL | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 23.205.225.13:80 | query.prod.cms.rt.microsoft.com | GTT Communications Inc. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
query.prod.cms.rt.microsoft.com |
| whitelisted |