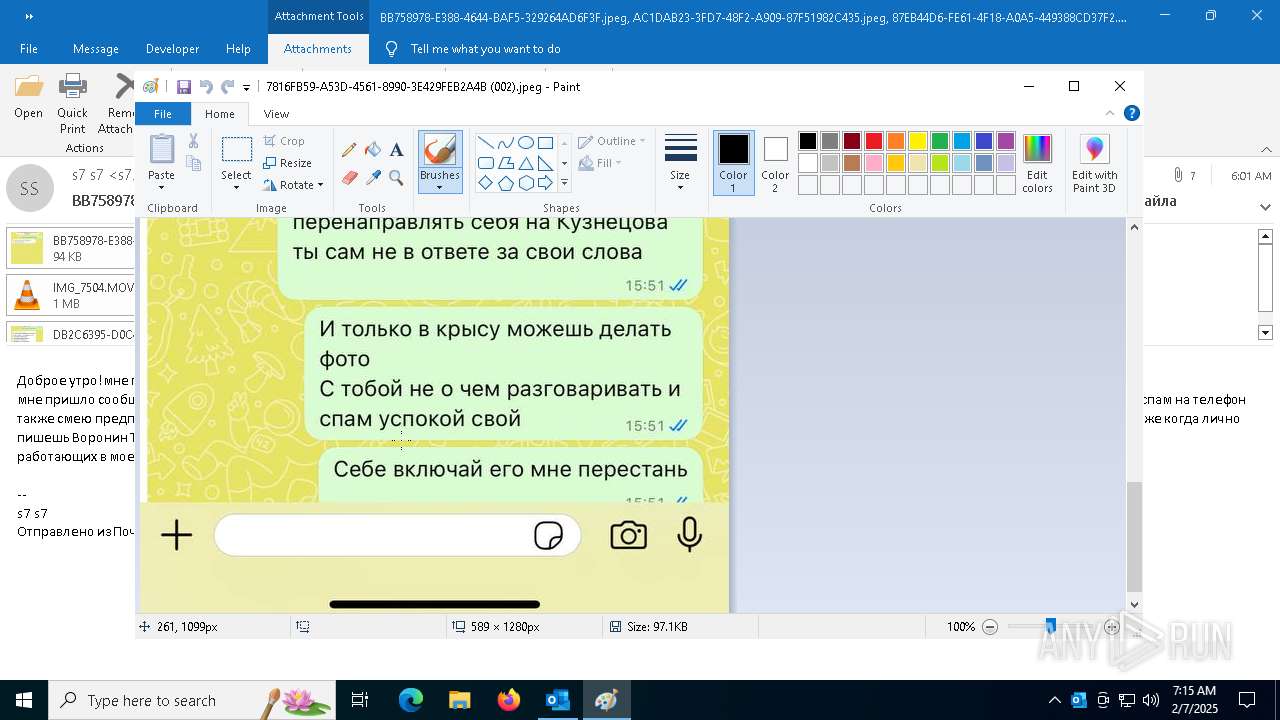
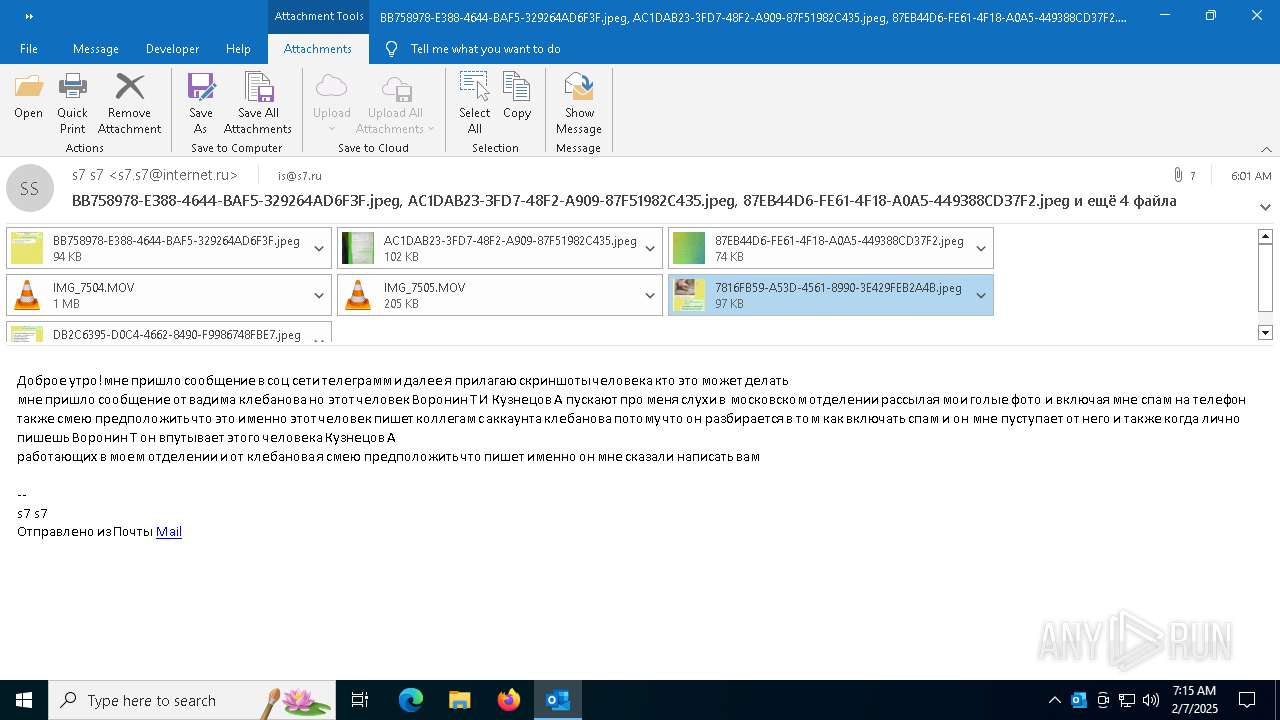
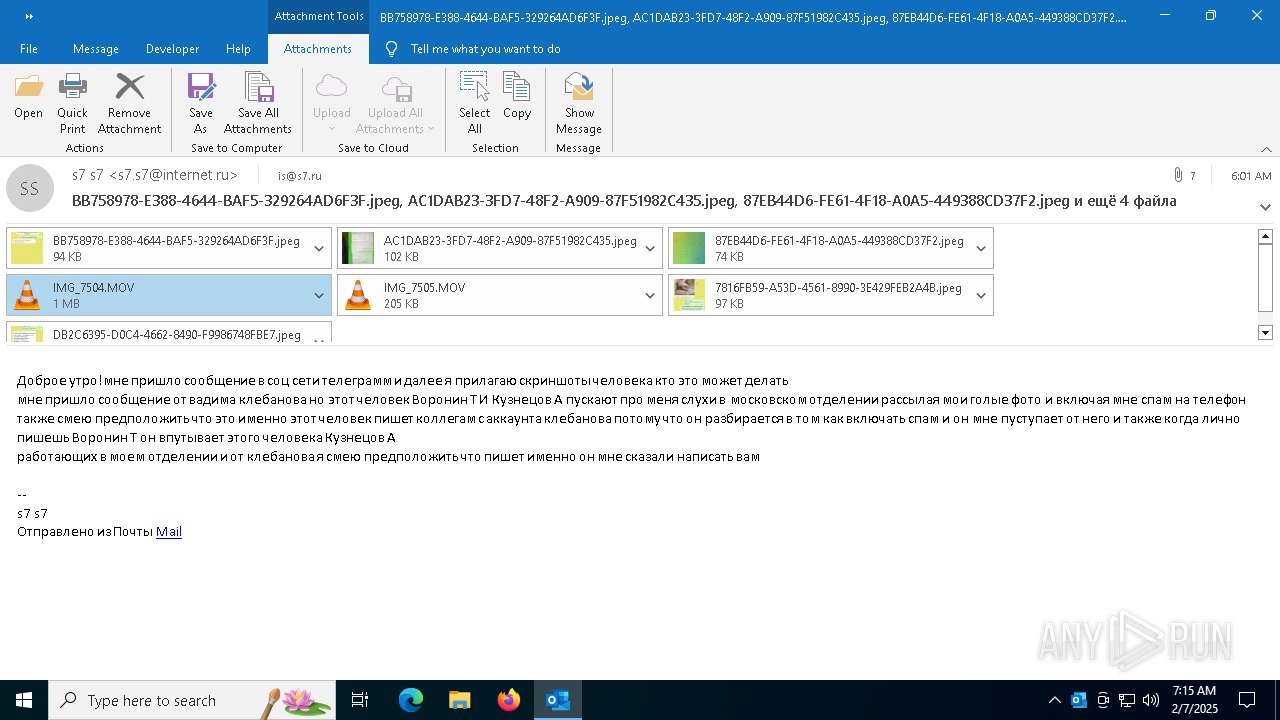
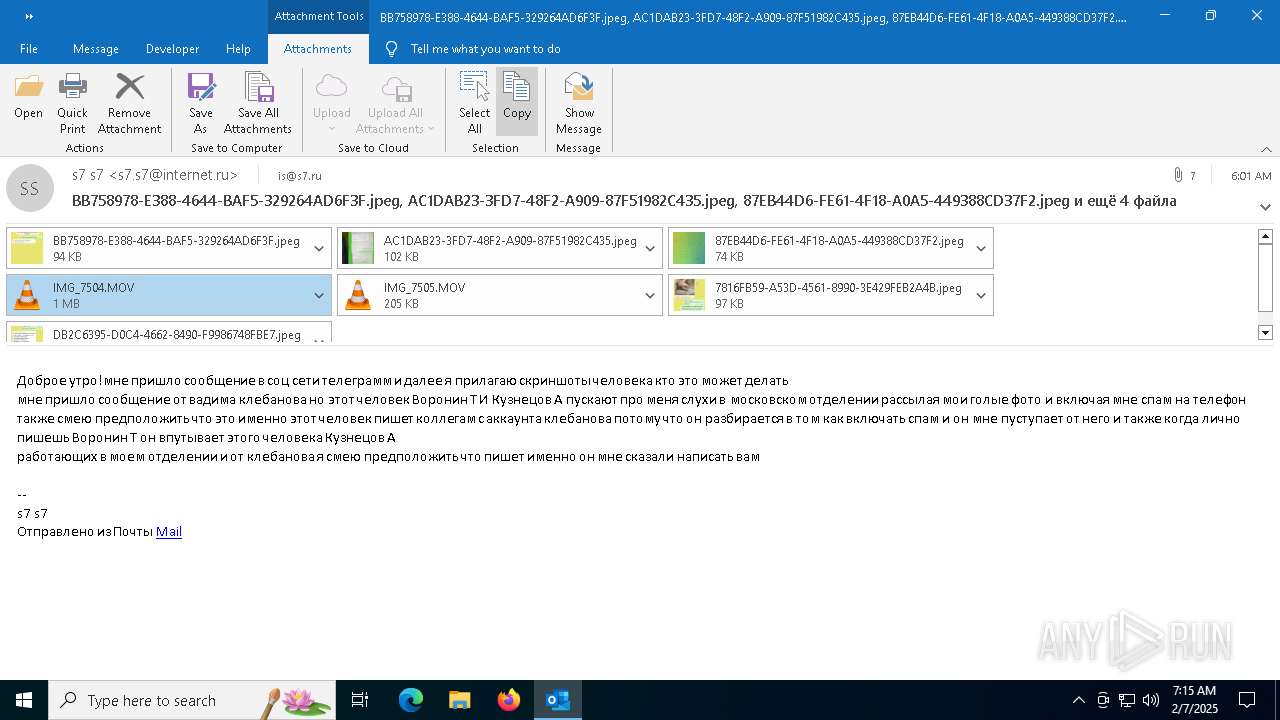
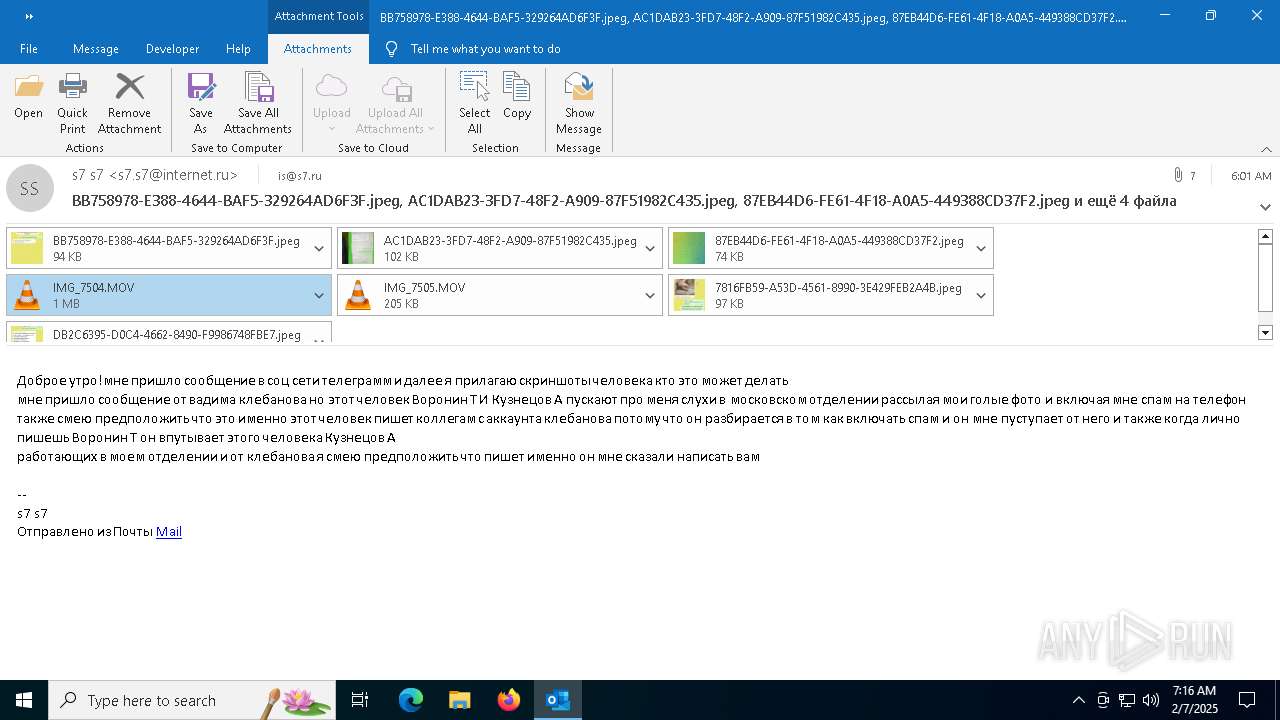
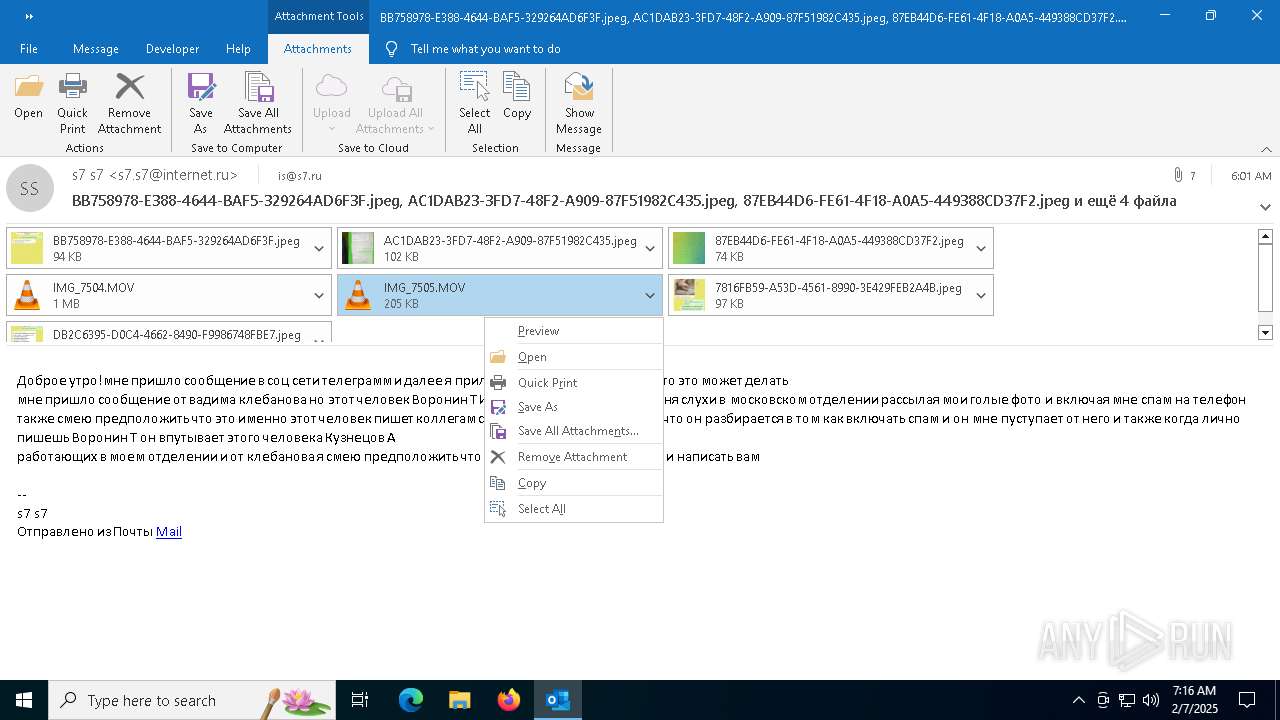
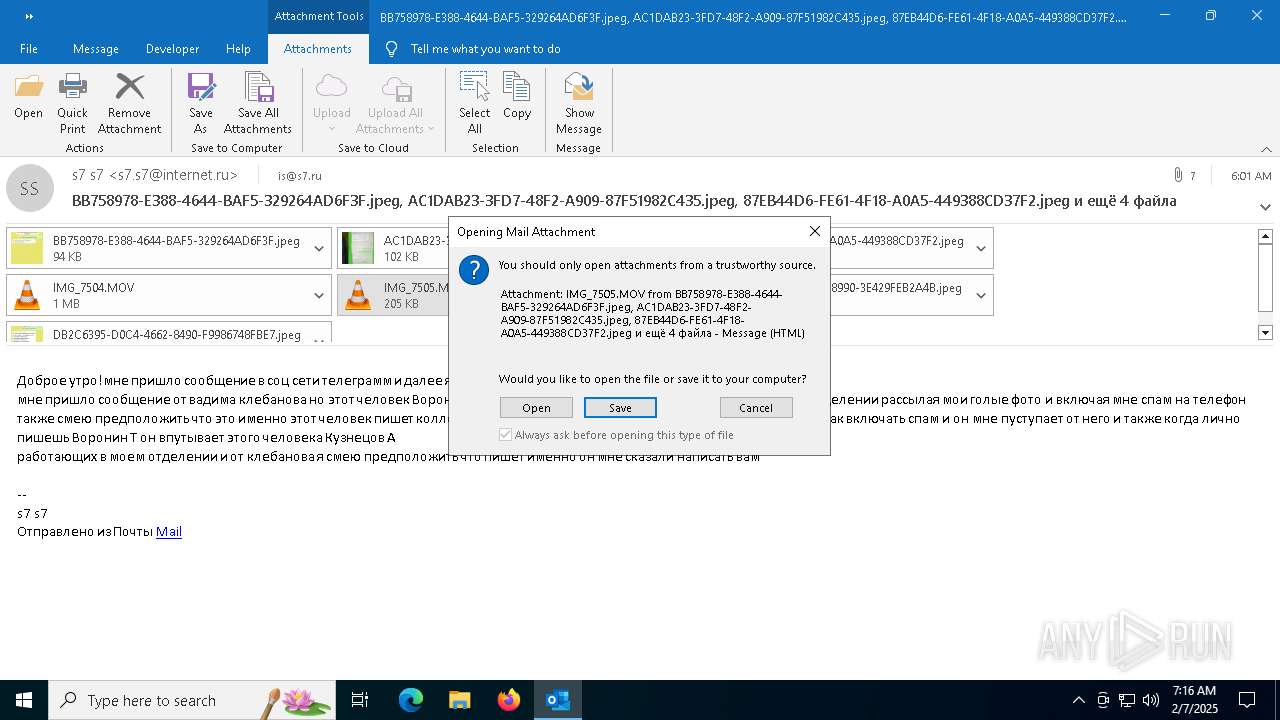
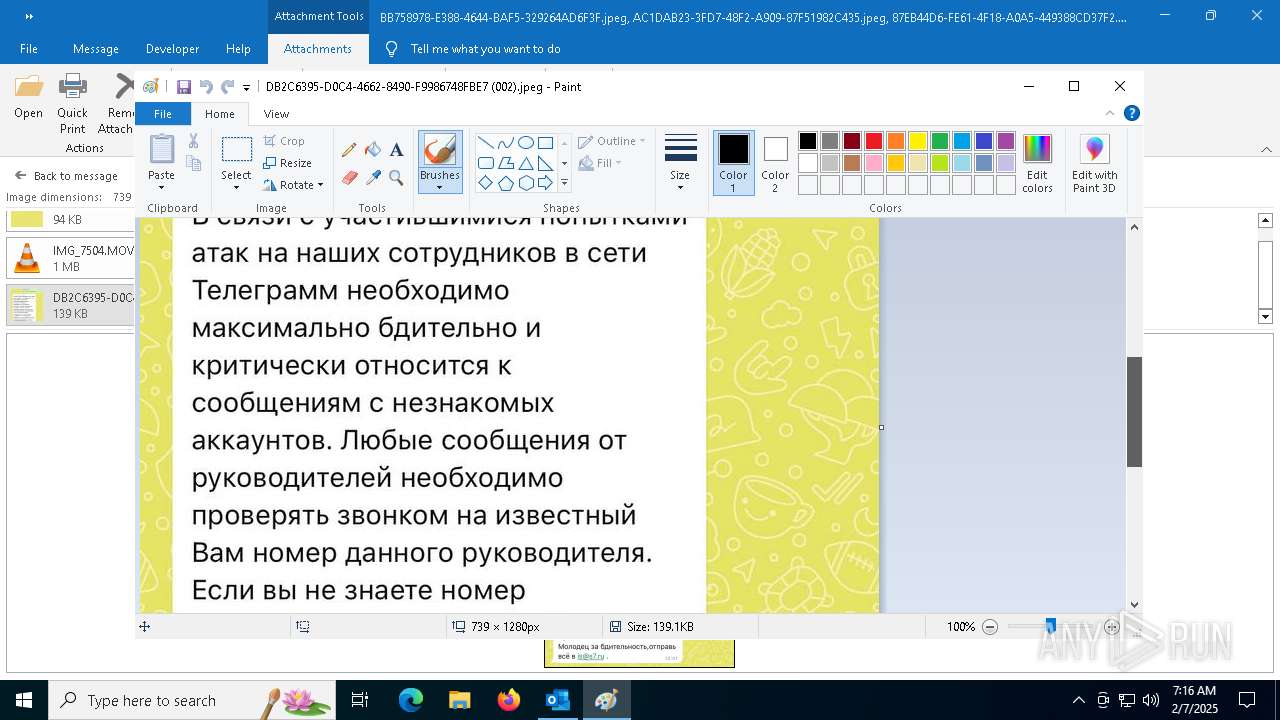
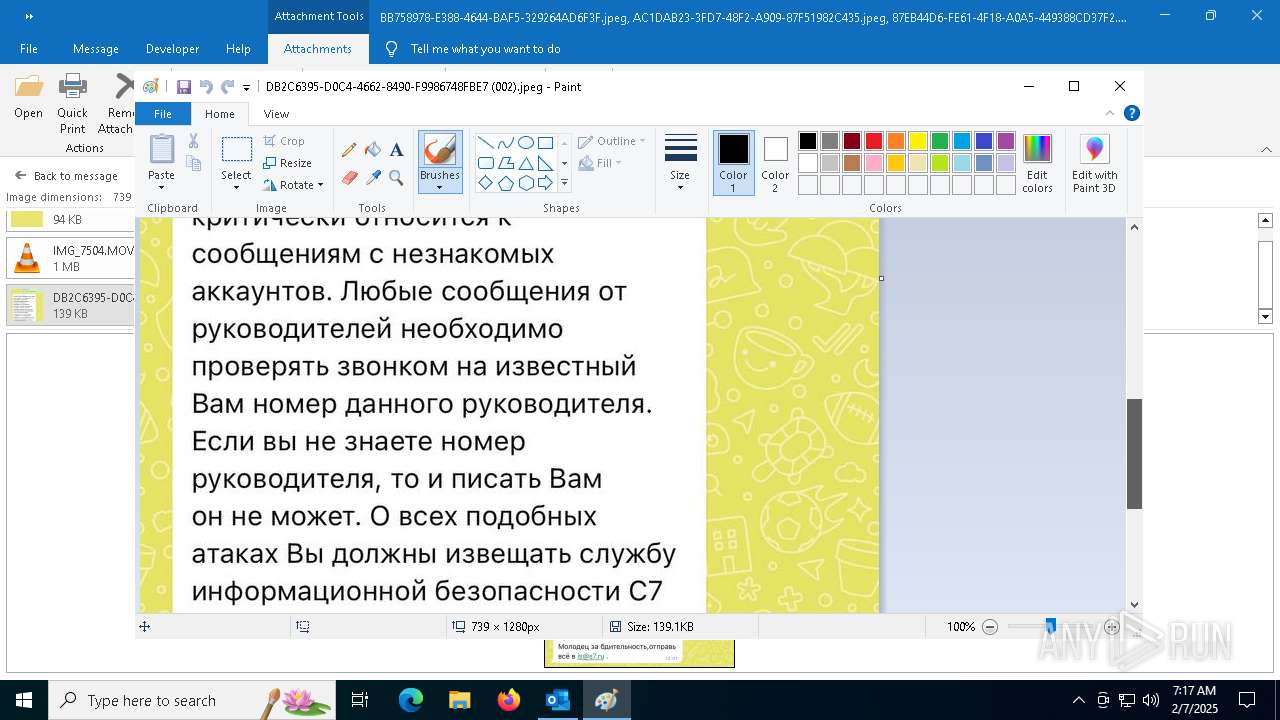
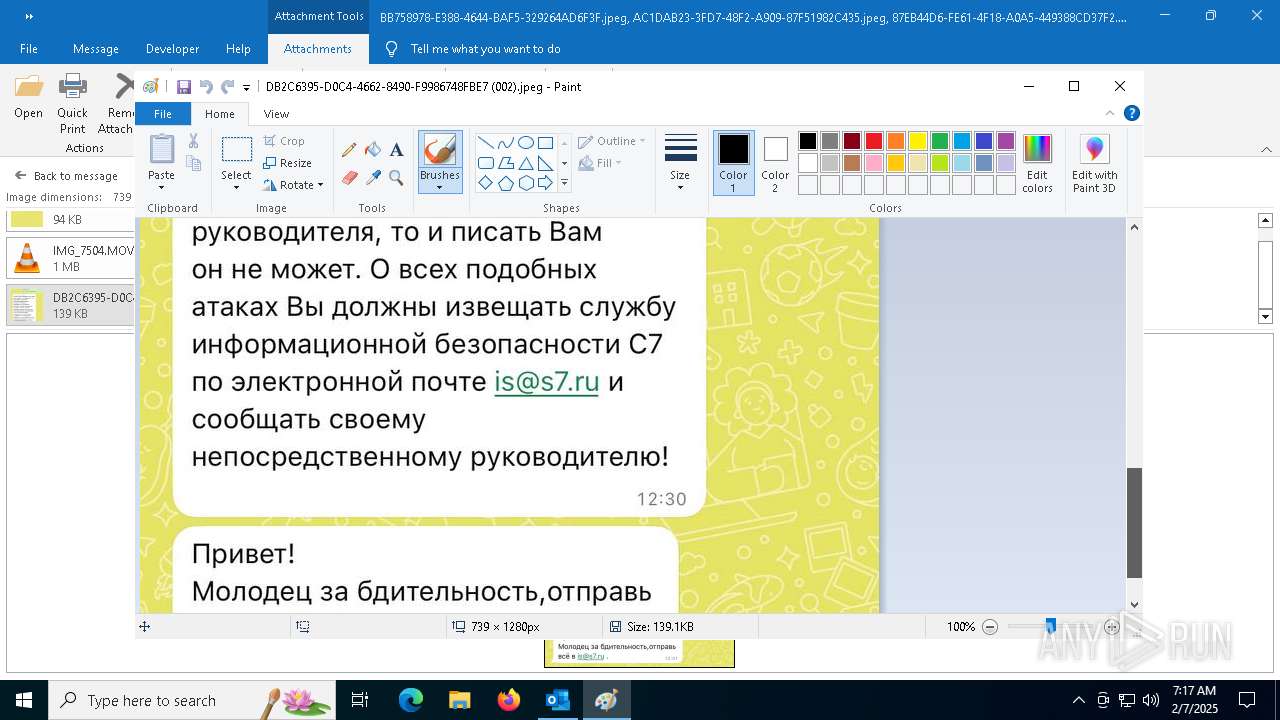
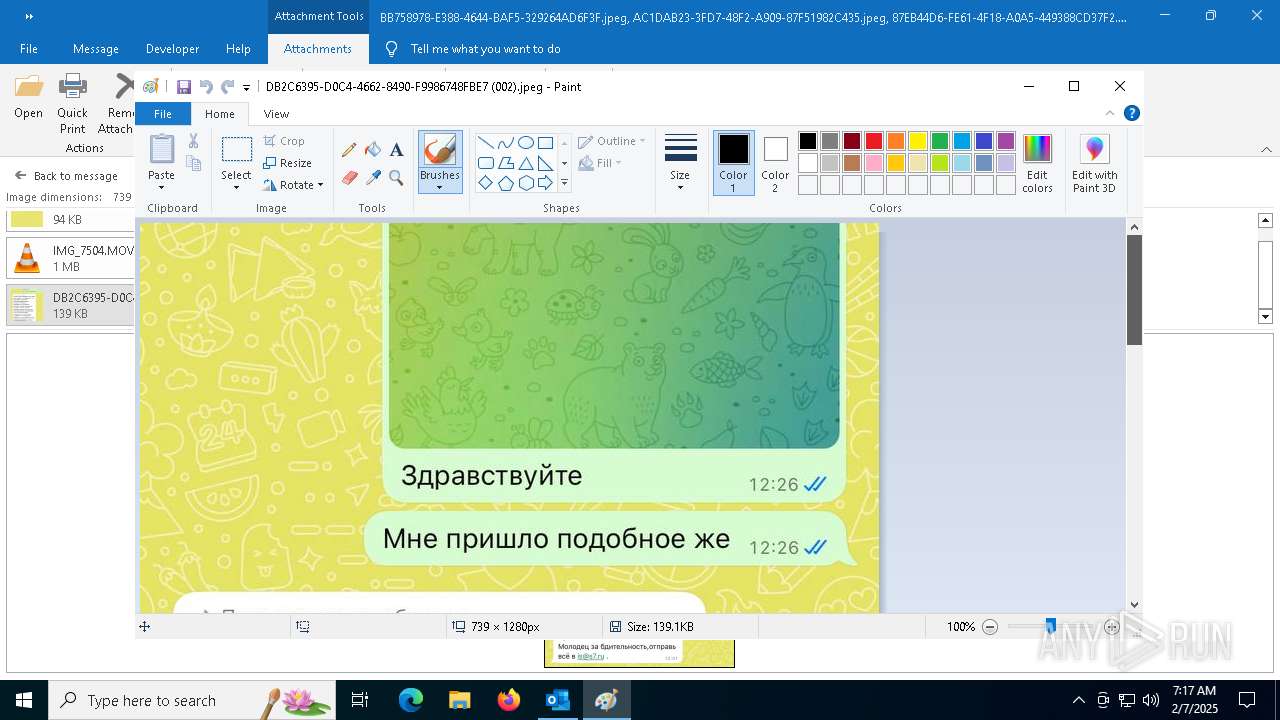
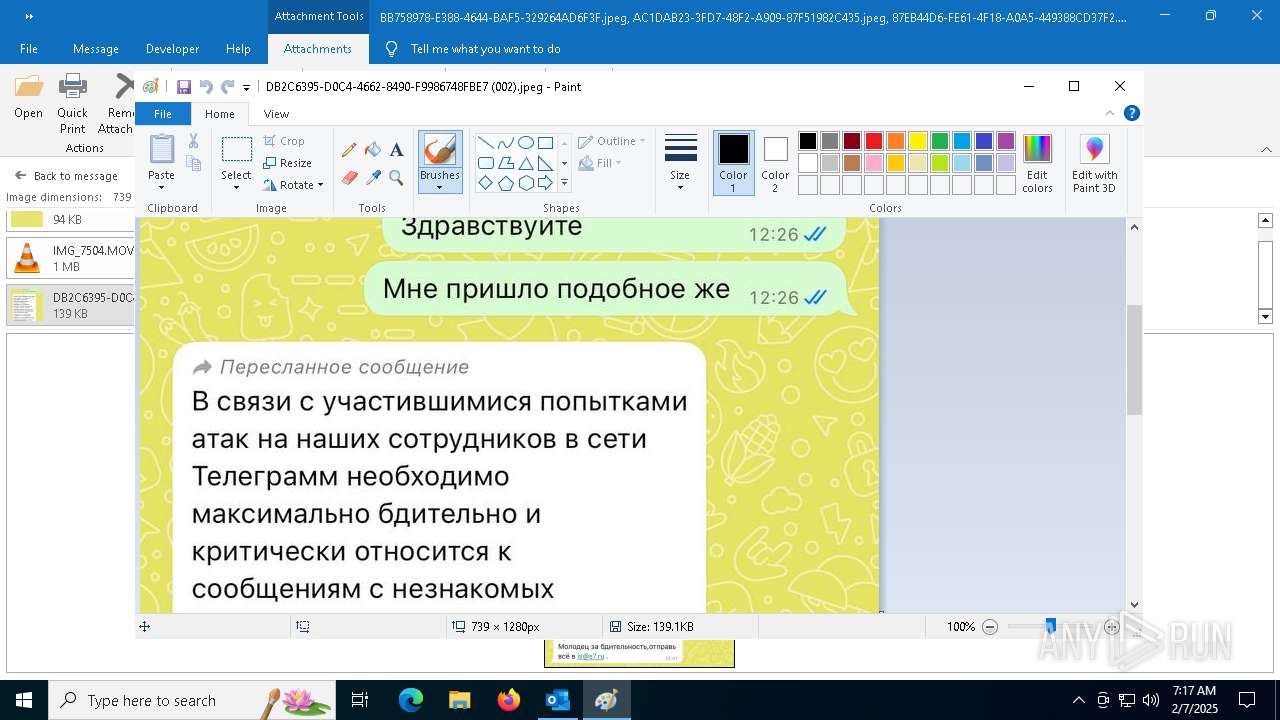
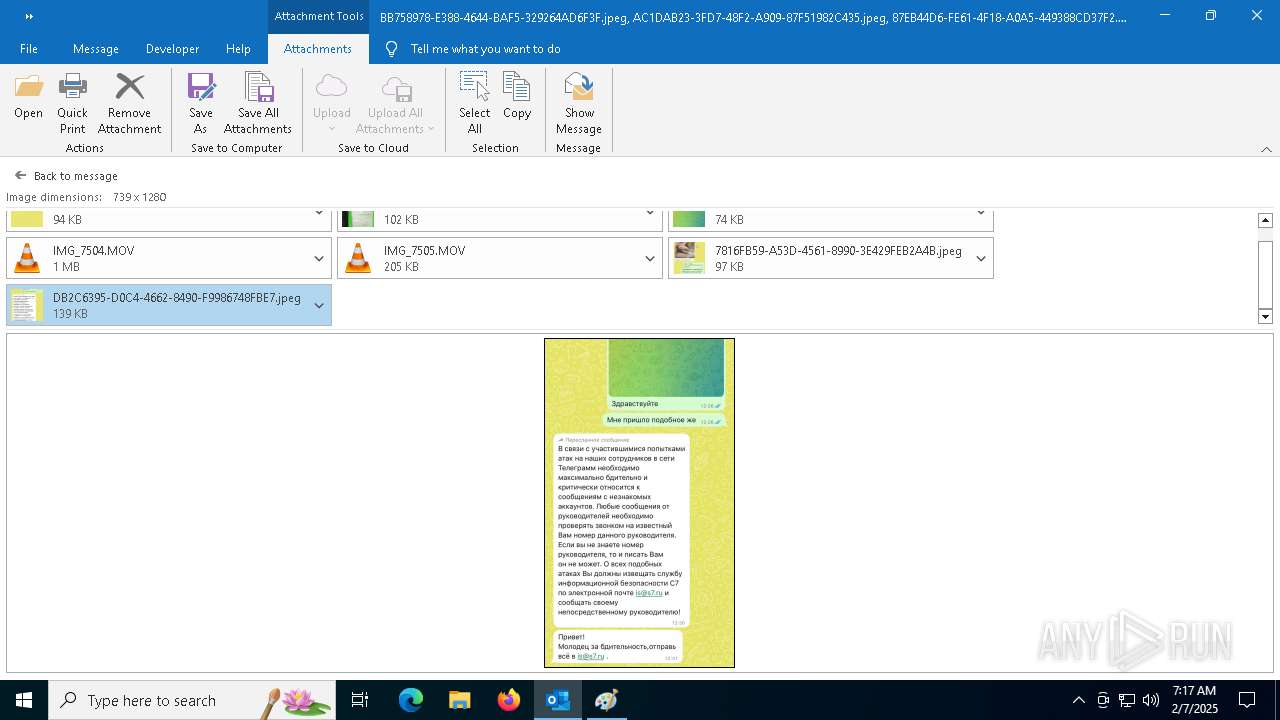
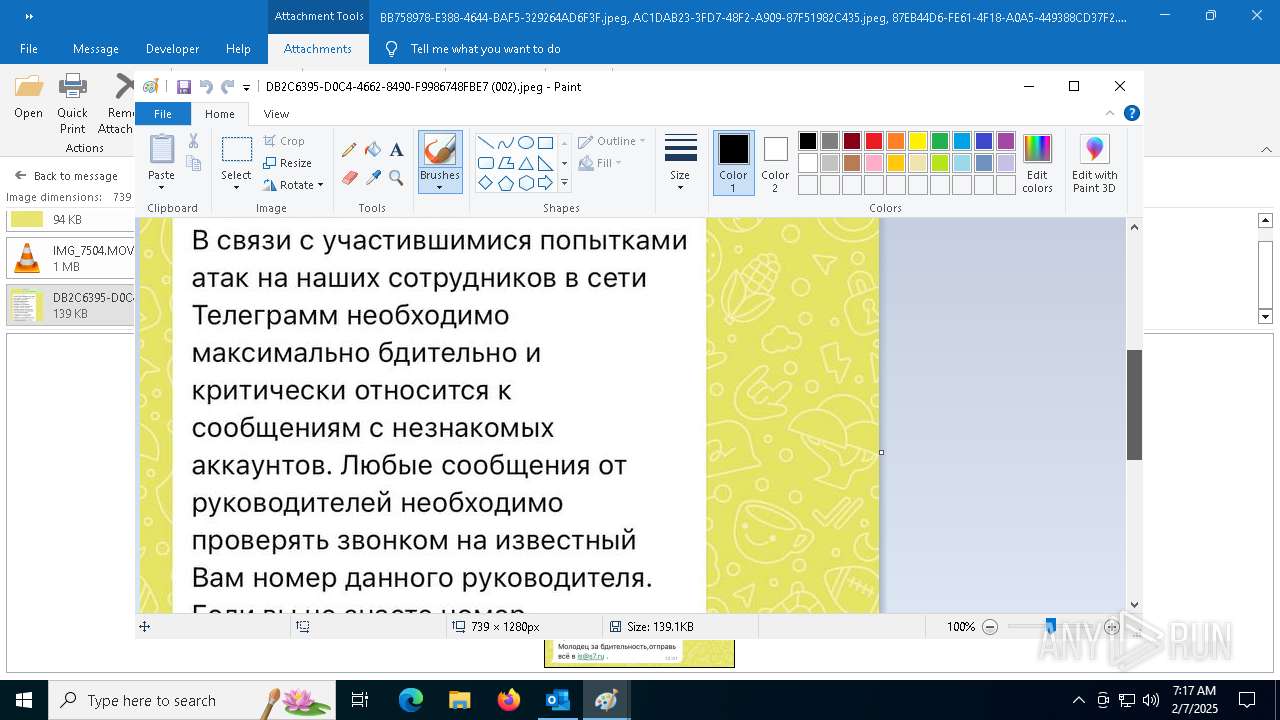
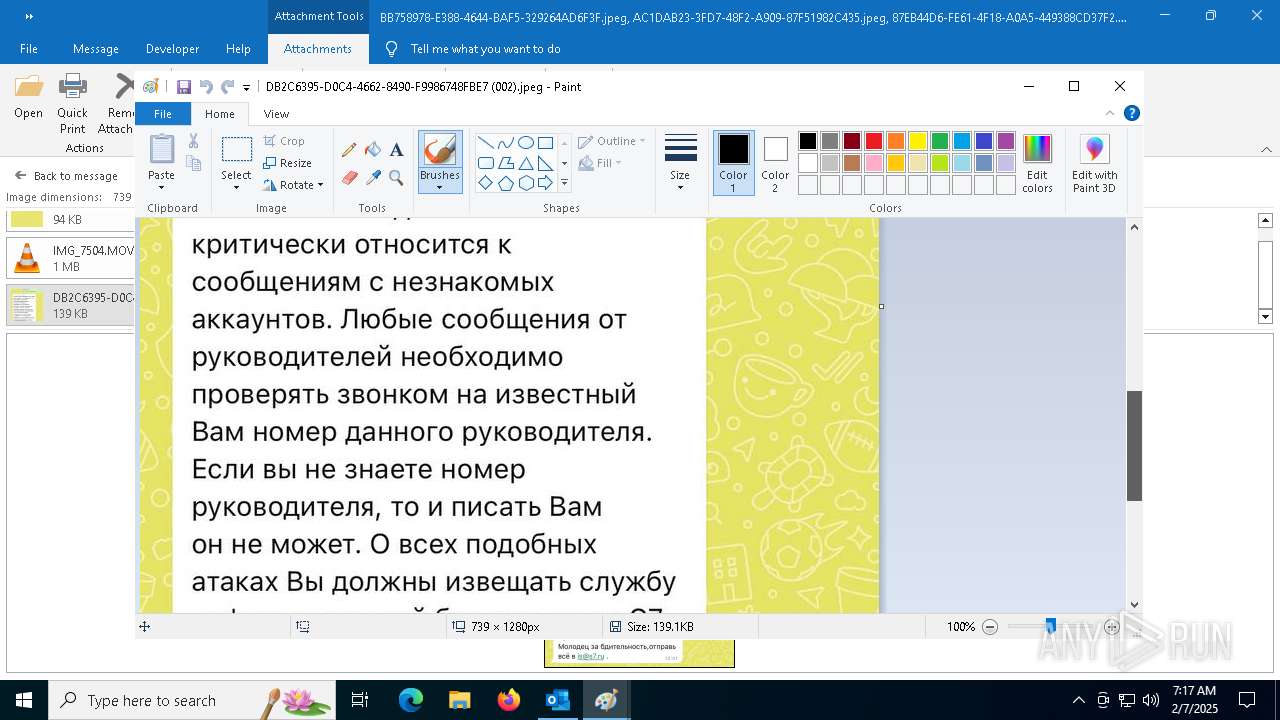
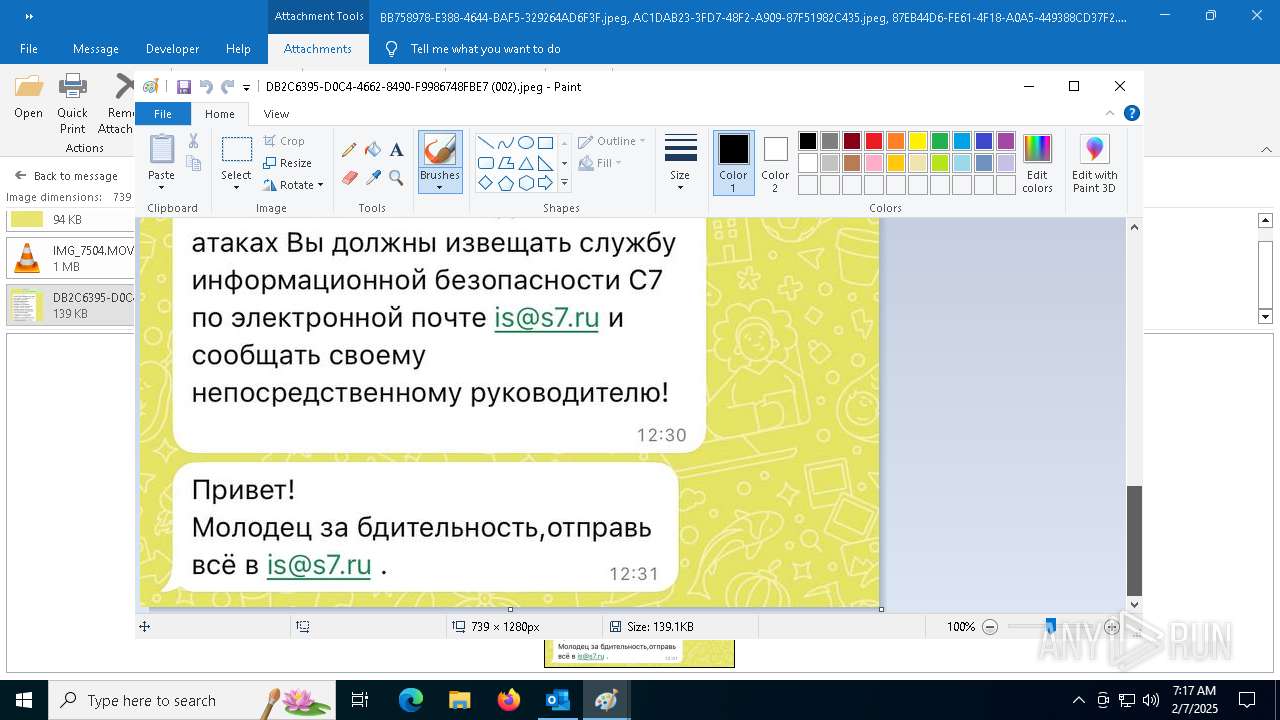
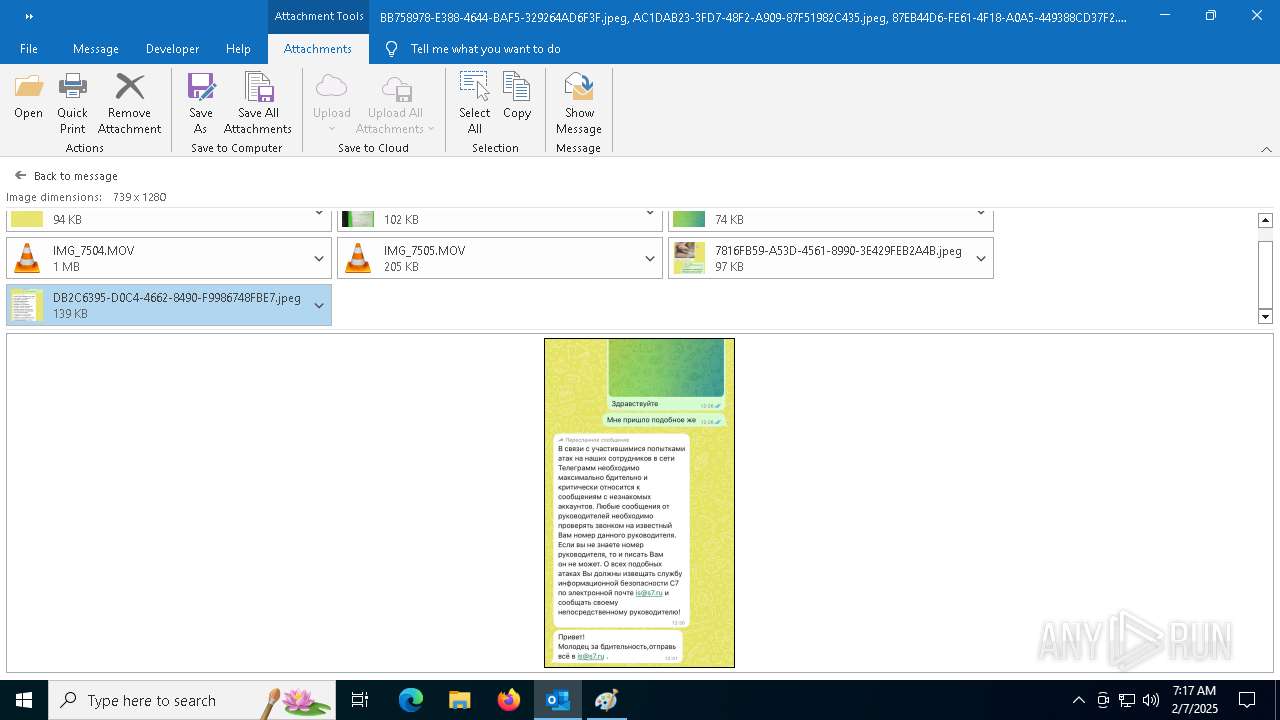
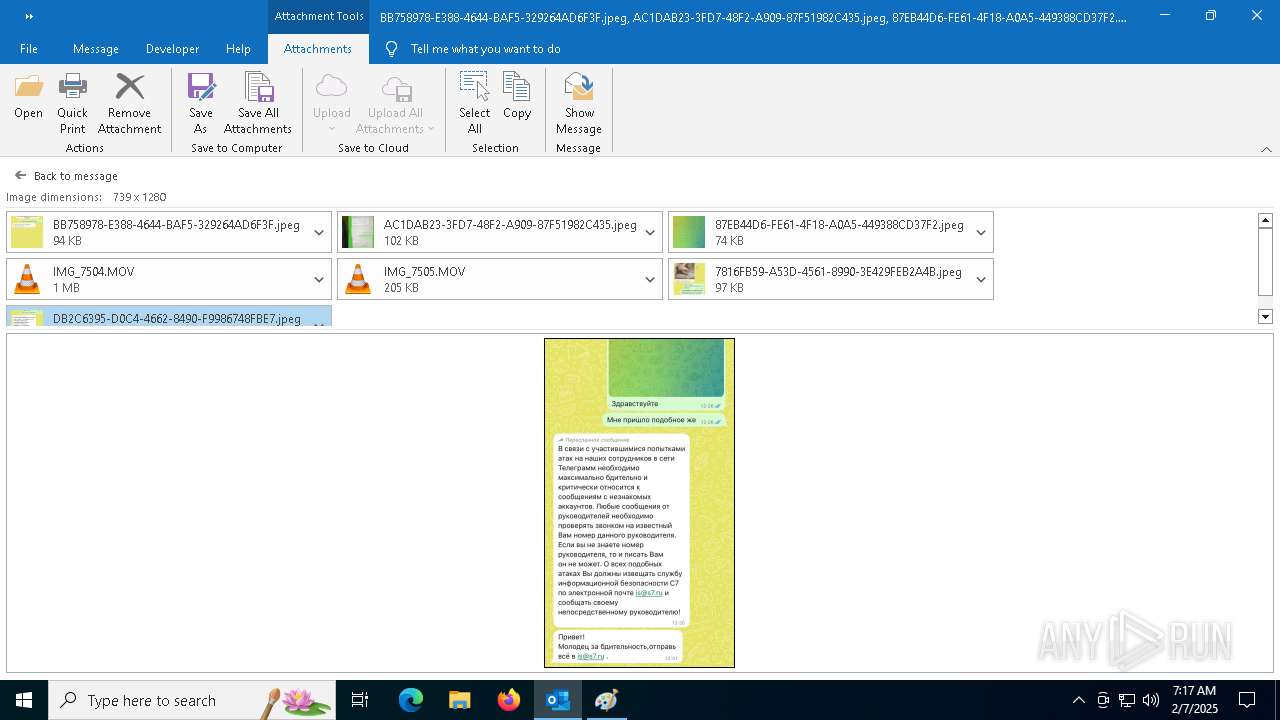
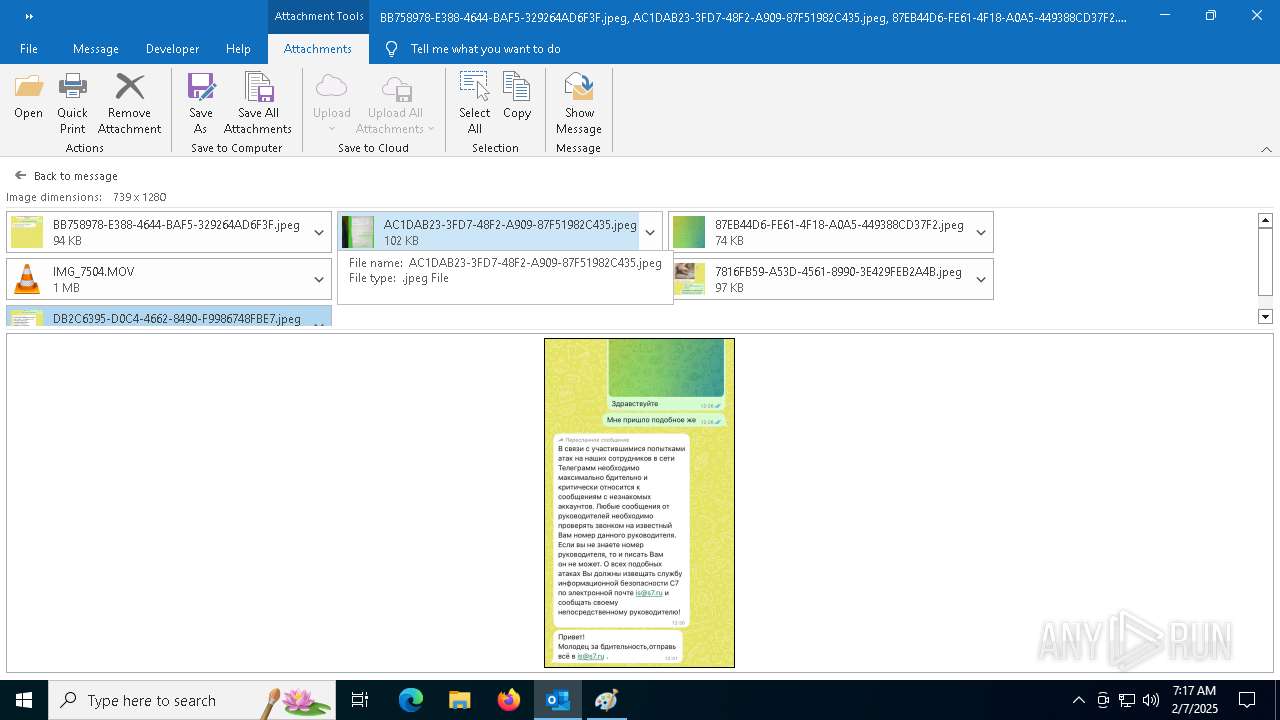
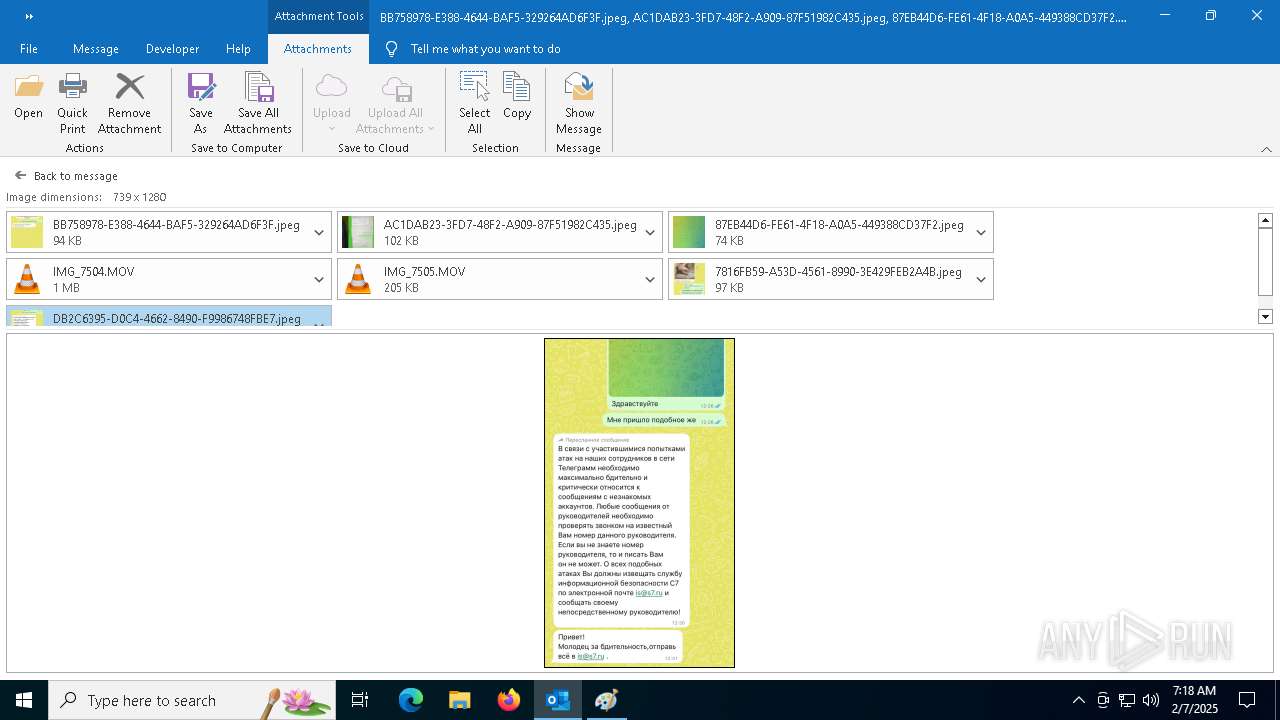
| File name: | f5726f64-db44-4d0b-8158-a637a8462b79 |
| Full analysis: | https://app.any.run/tasks/49fb05fd-d16f-47bc-a51f-0f8a841a7341 |
| Verdict: | Malicious activity |
| Analysis date: | February 07, 2025, 07:14:23 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines (908), with CRLF line terminators |
| MD5: | 774F7FE1CA40B11598C408A7C6A38B48 |
| SHA1: | 4DF442EAAA1353A8789976ED3D8303D502598CC5 |
| SHA256: | DCA8B92F97378D8E12CB155444520D546CAD418584694982FEE0C36FFFD65246 |
| SSDEEP: | 49152:mF8IF3SDS98K3G0rssSwenf7lNdYGRQjsKwHVzI:S |
MALICIOUS
Suspicious URL found
- OUTLOOK.EXE (PID: 6356)
SUSPICIOUS
Unnecessary Base64 encoding in Email Subject
- OUTLOOK.EXE (PID: 6356)
INFO
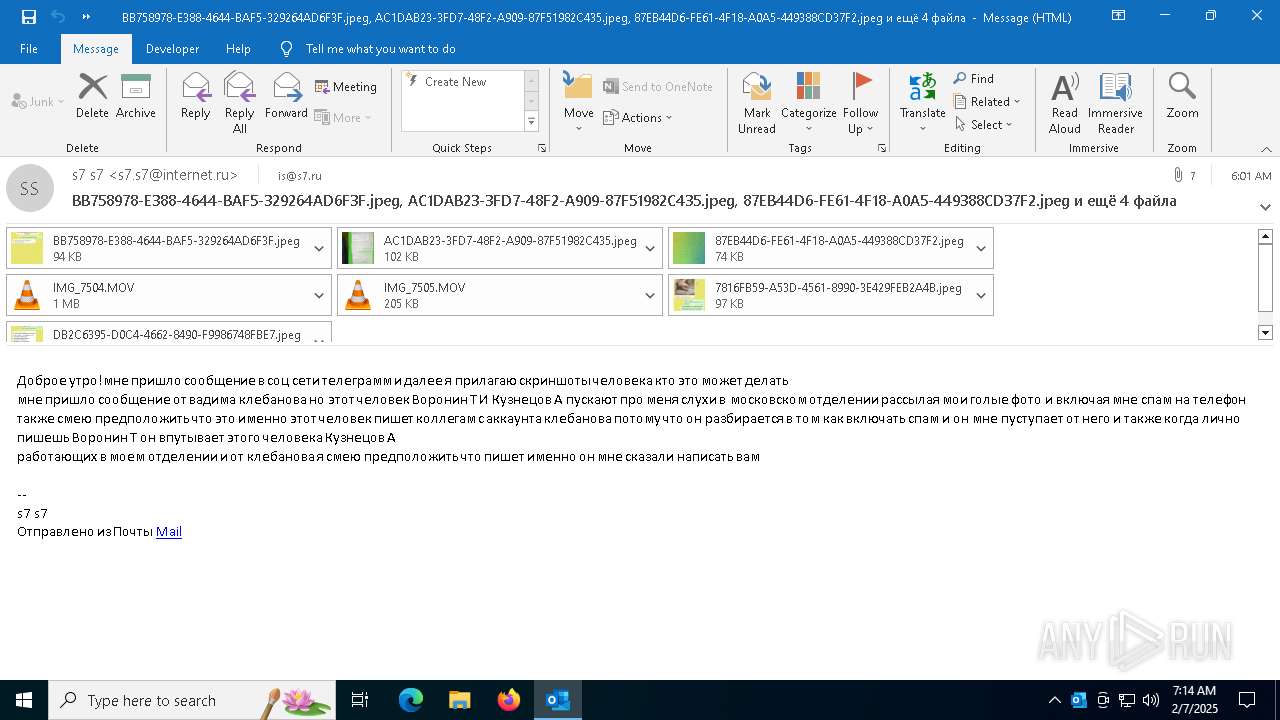
Email with attachments
- OUTLOOK.EXE (PID: 6356)
Reads the computer name
- vlc.exe (PID: 6676)
- vlc.exe (PID: 1668)
- vlc.exe (PID: 4264)
Checks supported languages
- vlc.exe (PID: 6676)
- vlc.exe (PID: 4264)
- vlc.exe (PID: 1668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
141
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
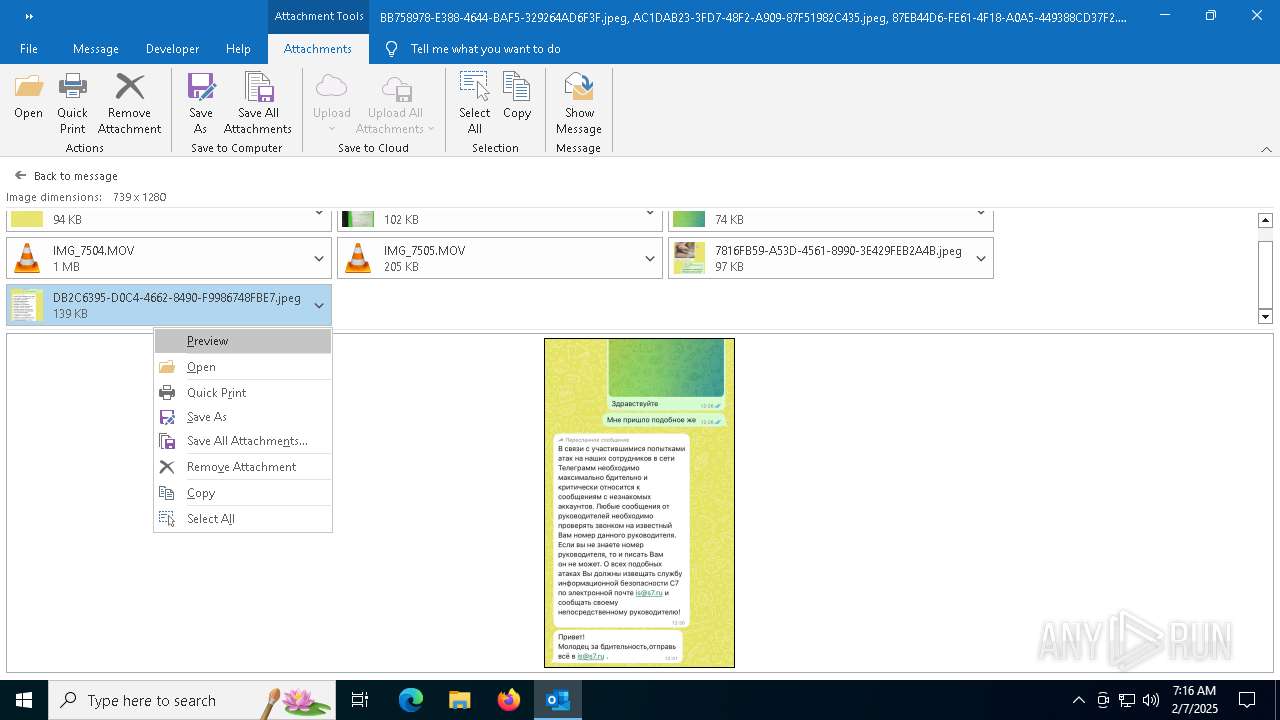
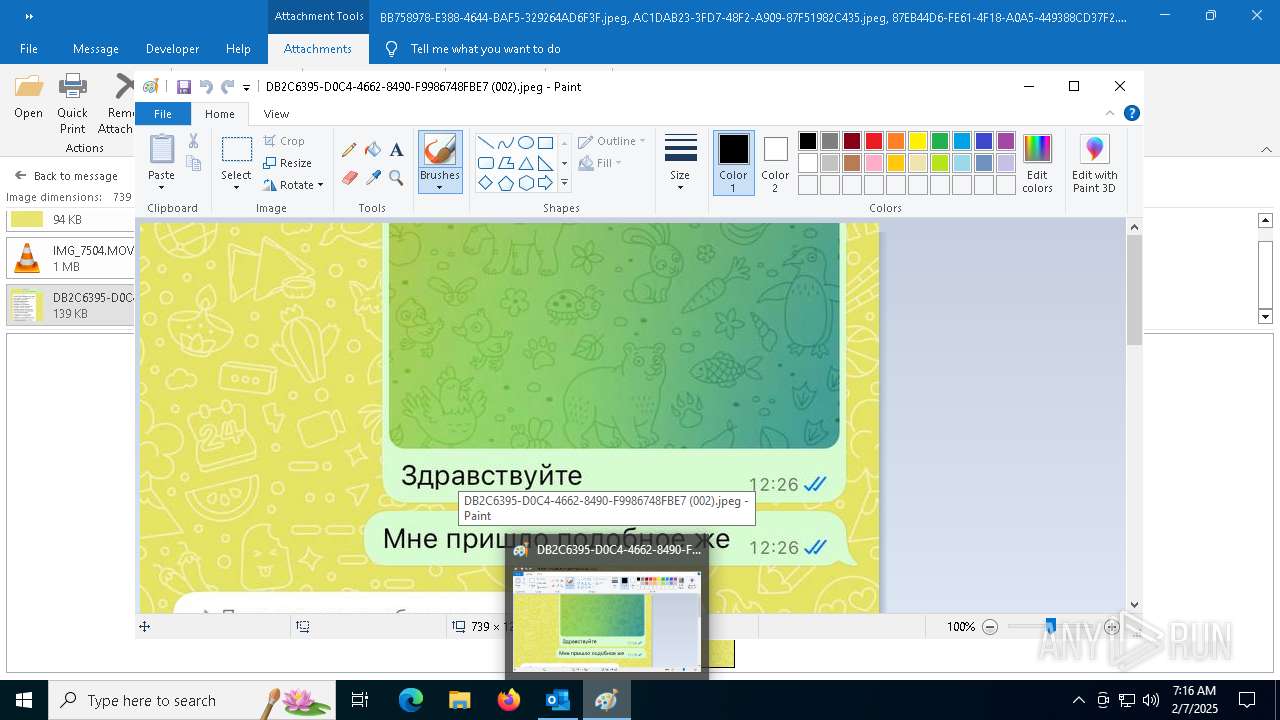
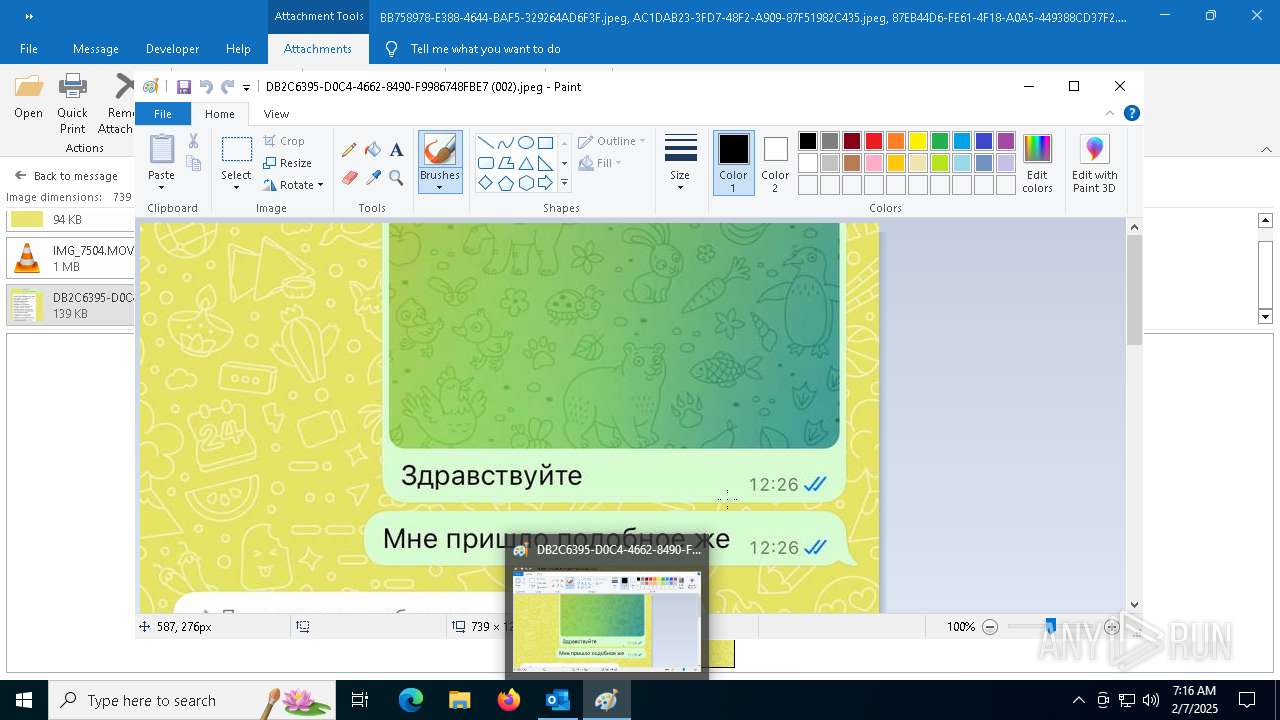
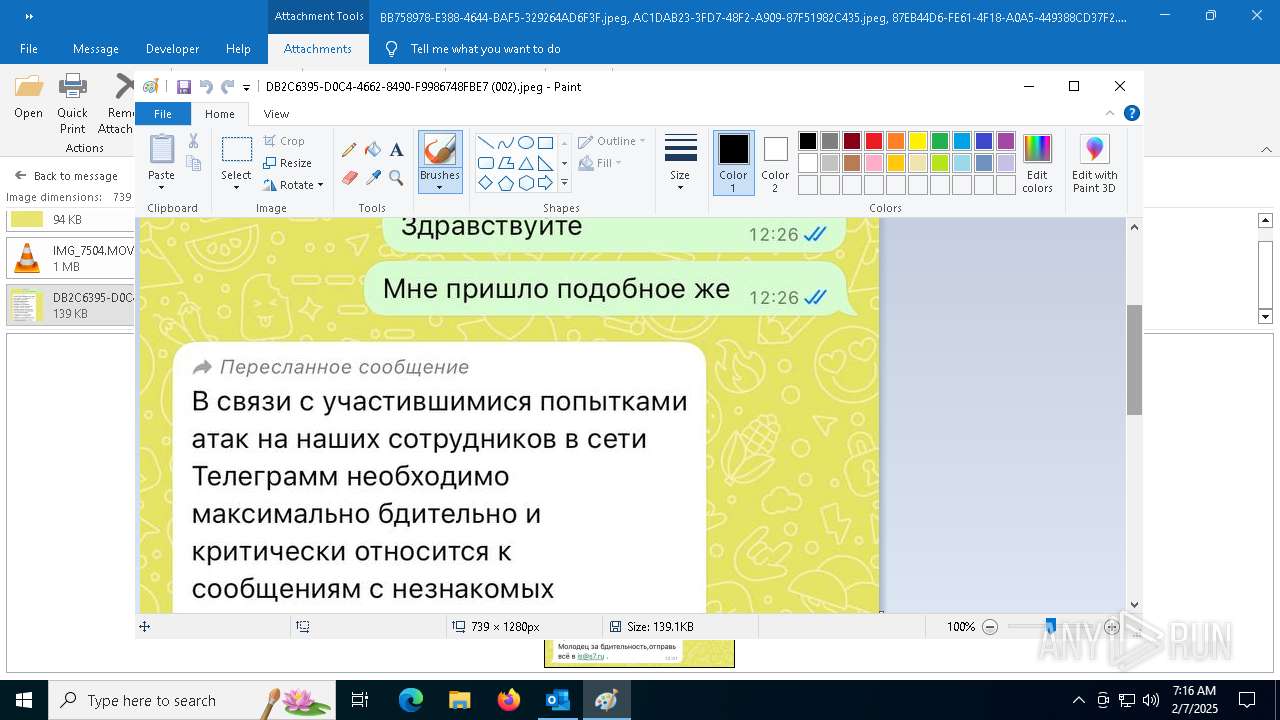
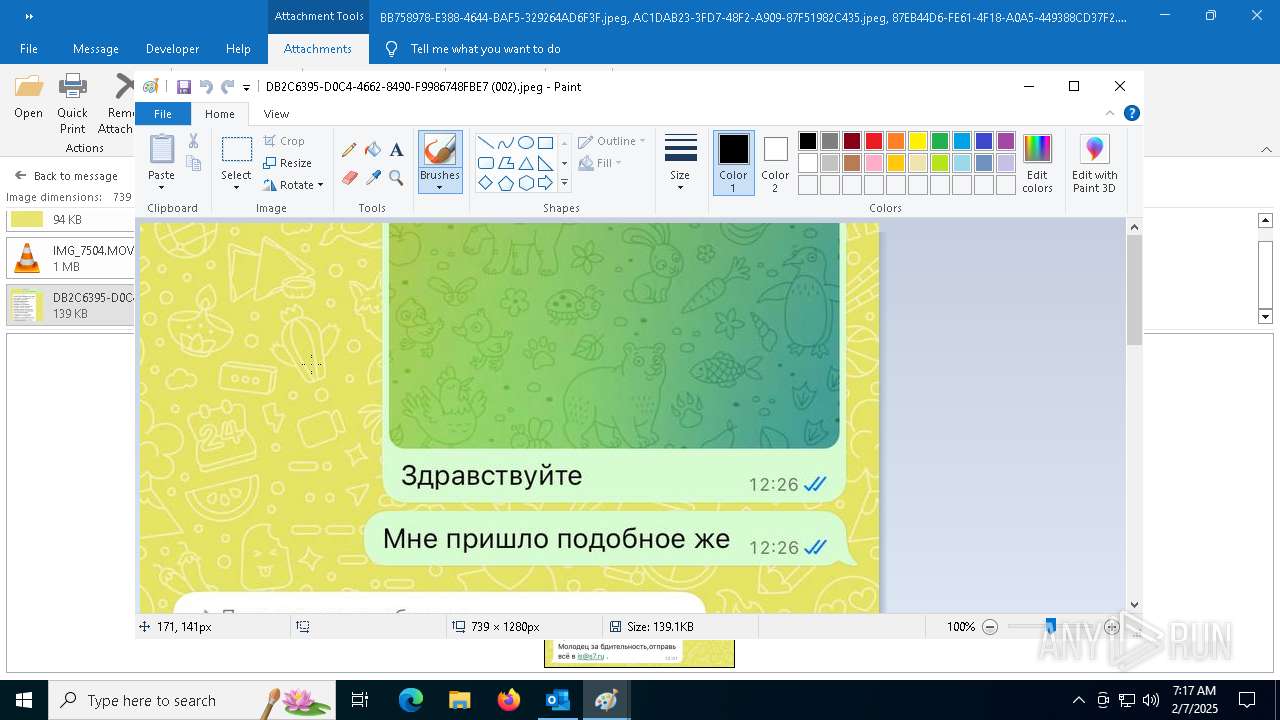
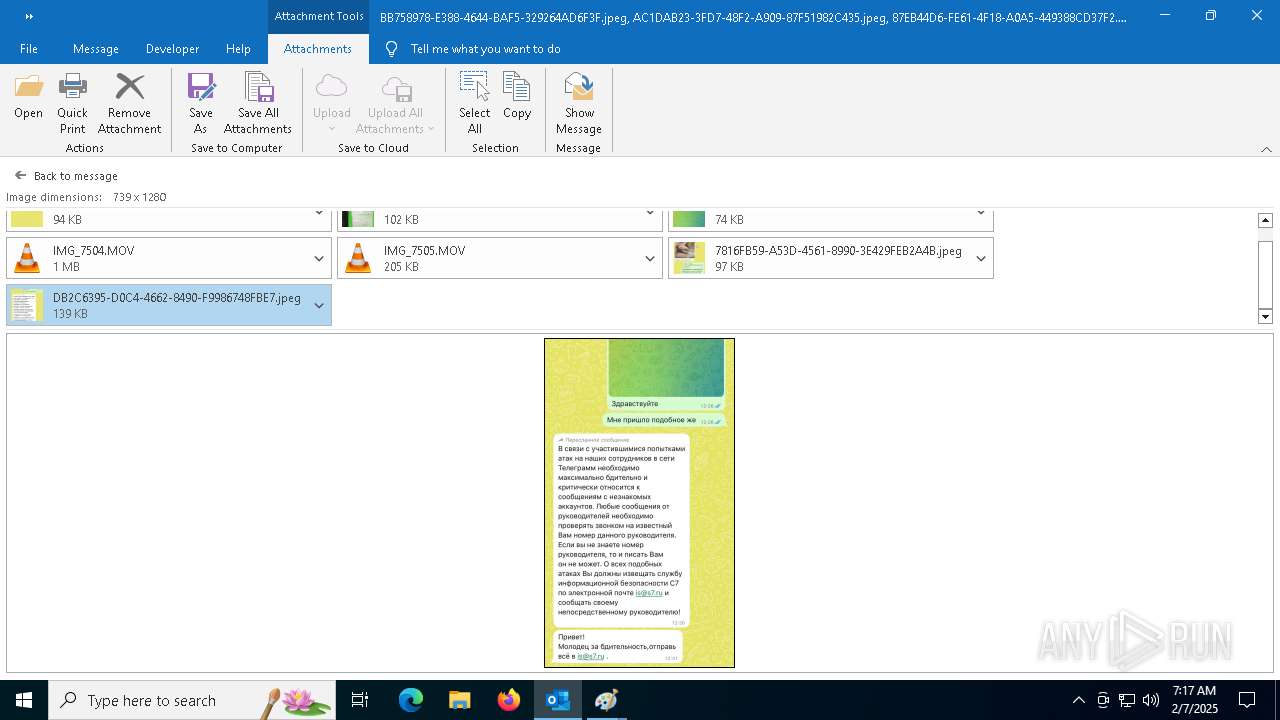
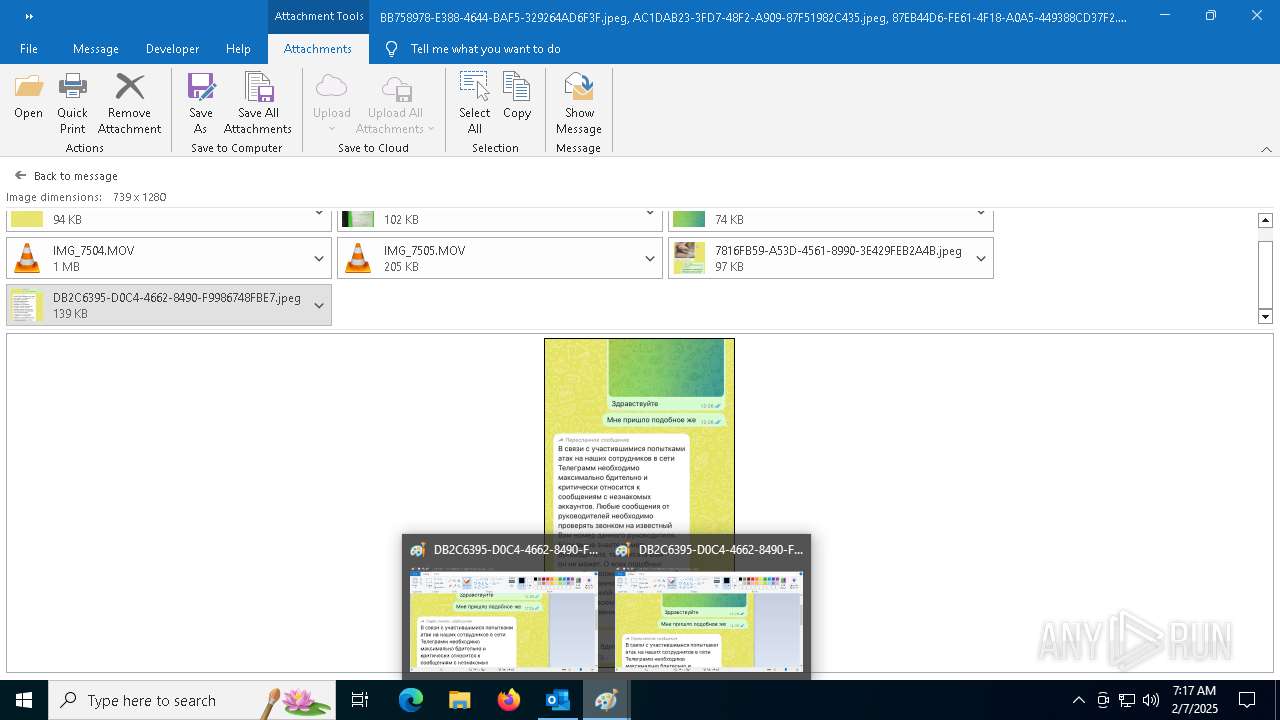
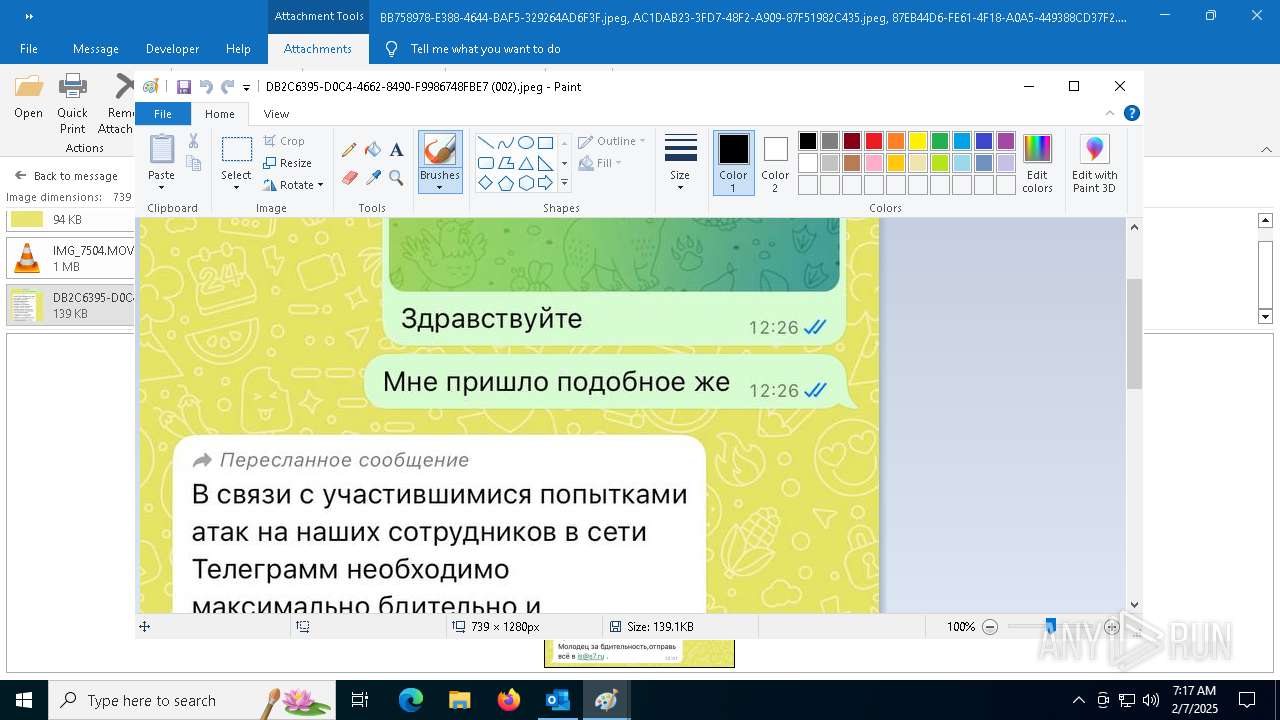
| 372 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\AAYW2787\DB2C6395-D0C4-4662-8490-F9986748FBE7 (002).jpeg" | C:\Windows\System32\mspaint.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
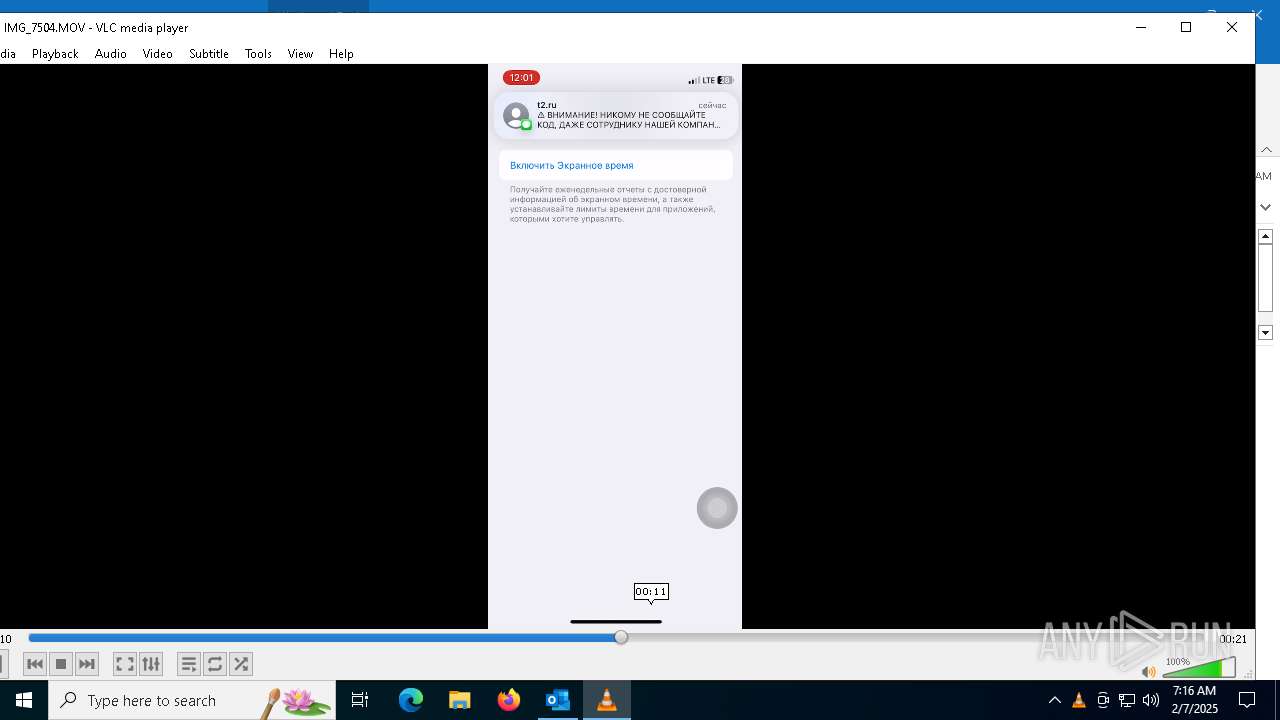
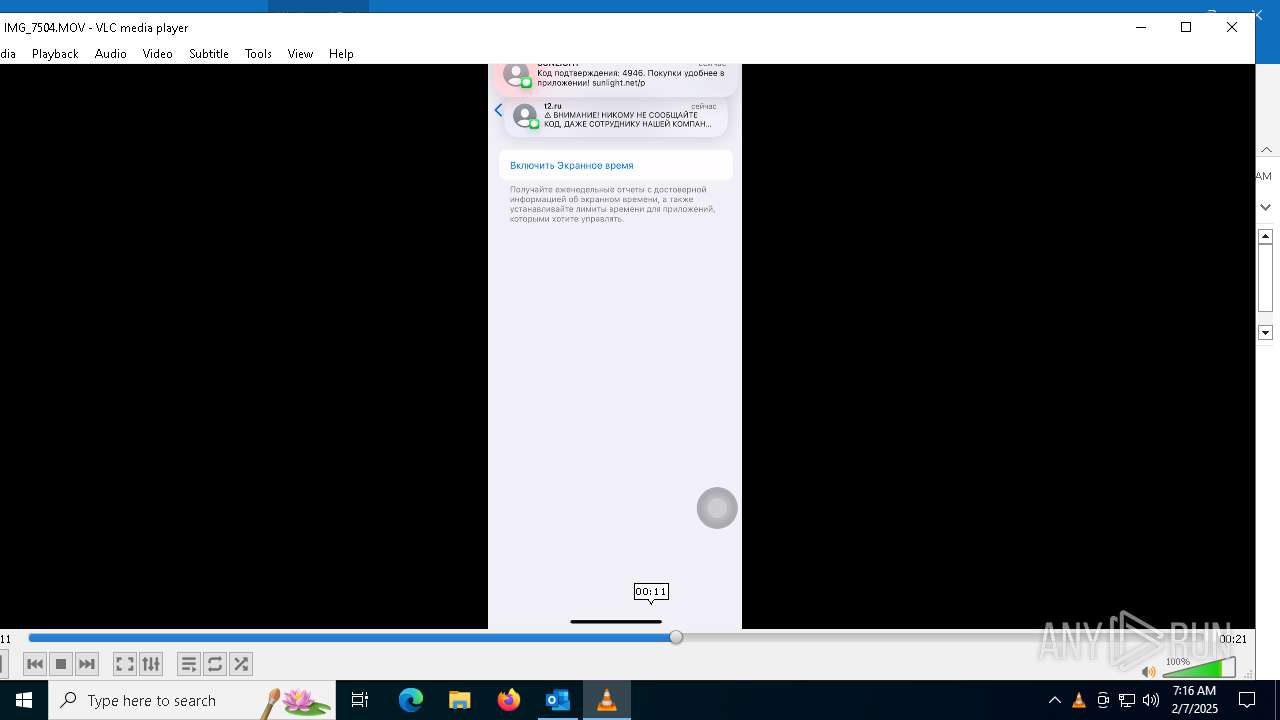
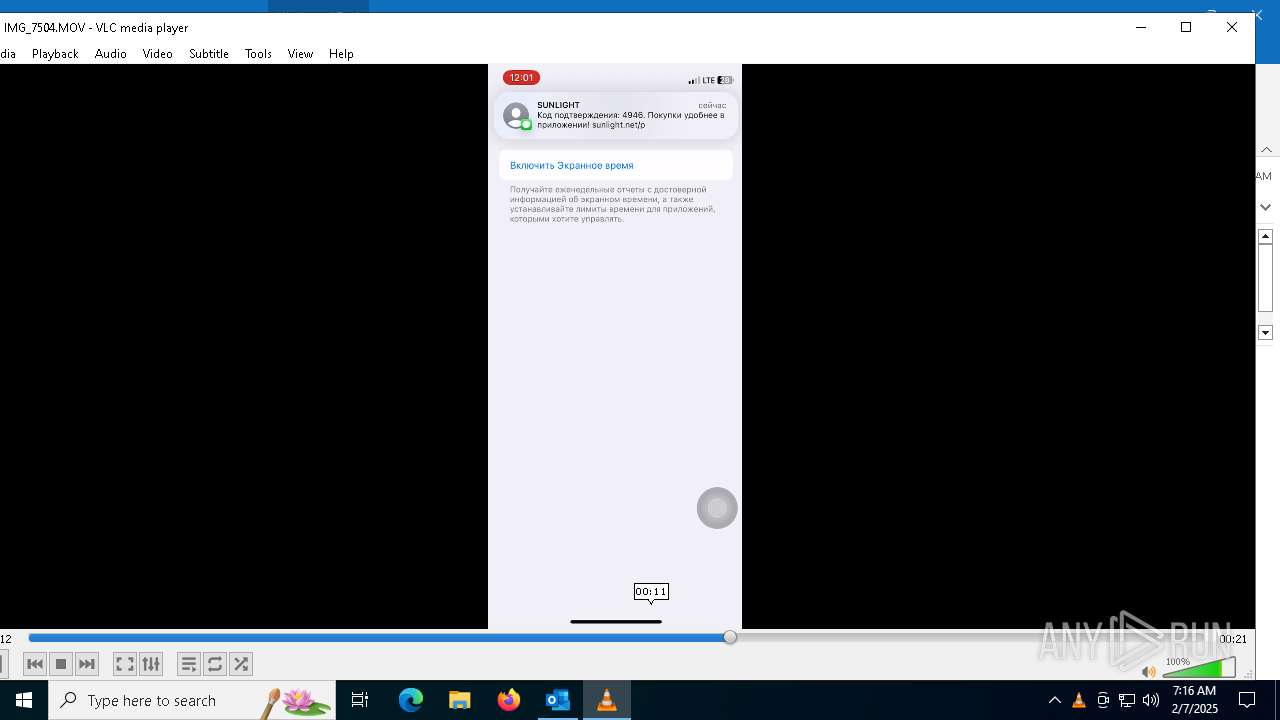
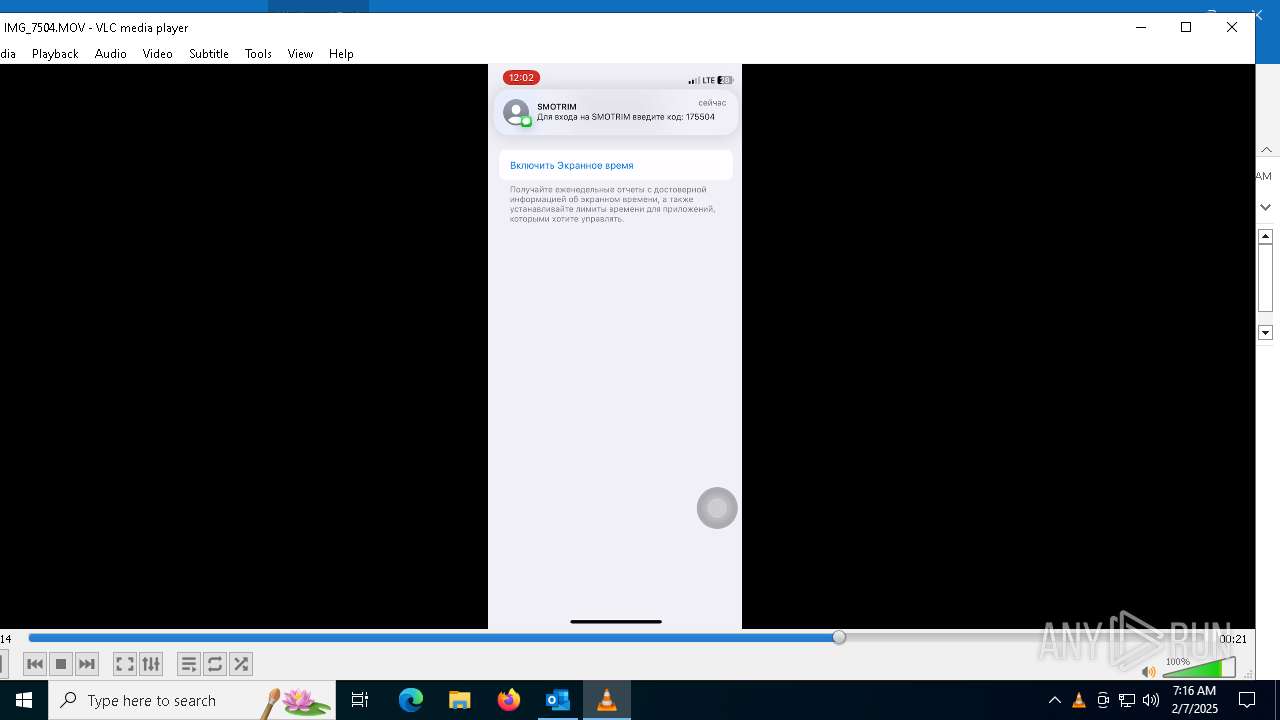
| 1668 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\AAYW2787\IMG_7505.MOV" | C:\Program Files\VideoLAN\VLC\vlc.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 3.0.11 Modules
| |||||||||||||||
| 4264 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\AAYW2787\IMG_7504.MOV" | C:\Program Files\VideoLAN\VLC\vlc.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 3.0.11 Modules
| |||||||||||||||
| 6004 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\AAYW2787\7816FB59-A53D-4561-8990-3E429FEB2A4B (002).jpeg" | C:\Windows\System32\mspaint.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6356 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml C:\Users\admin\Desktop\f5726f64-db44-4d0b-8158-a637a8462b79.eml | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6676 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\AAYW2787\IMG_7504.MOV" | C:\Program Files\VideoLAN\VLC\vlc.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 3.0.11 Modules
| |||||||||||||||
| 6956 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\AAYW2787\DB2C6395-D0C4-4662-8490-F9986748FBE7 (002).jpeg" | C:\Windows\System32\mspaint.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7100 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "7B2A1346-F0E8-4130-9C36-01F104924D00" "C55092B2-EC00-49B3-9A0A-1FD248472081" "6356" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
Total events
20 358
Read events
19 052
Write events
1 149
Delete events
157
Modification events
| (PID) Process: | (6356) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (6356) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\6356 |
| Operation: | write | Name: | 0 |
Value: 0B0E1086B9DF2C5000FC43A5A1093867C190F7230046B2EBC998FFA5DEED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511D431D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6356) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (6356) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (6356) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6356) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (6356) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (6356) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (6356) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (6356) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
12
Suspicious files
14
Text files
32
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6356 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 6356 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olk9EA4.tmp | binary | |
MD5:8C1A00D7925DA98CC88071DB57324A7A | SHA256:FBEAF57AC07D1AA897159C8397FBA971830536533BDFAC4C5134F37EA4EAA015 | |||
| 6356 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olk9F13.tmp | binary | |
MD5:82DE7C72F37A9F767ECCAF35CC06FE0A | SHA256:F6F6BE036F2FA813301DA8BE5196F2E544AD31BA95647E40E003641546474D35 | |||
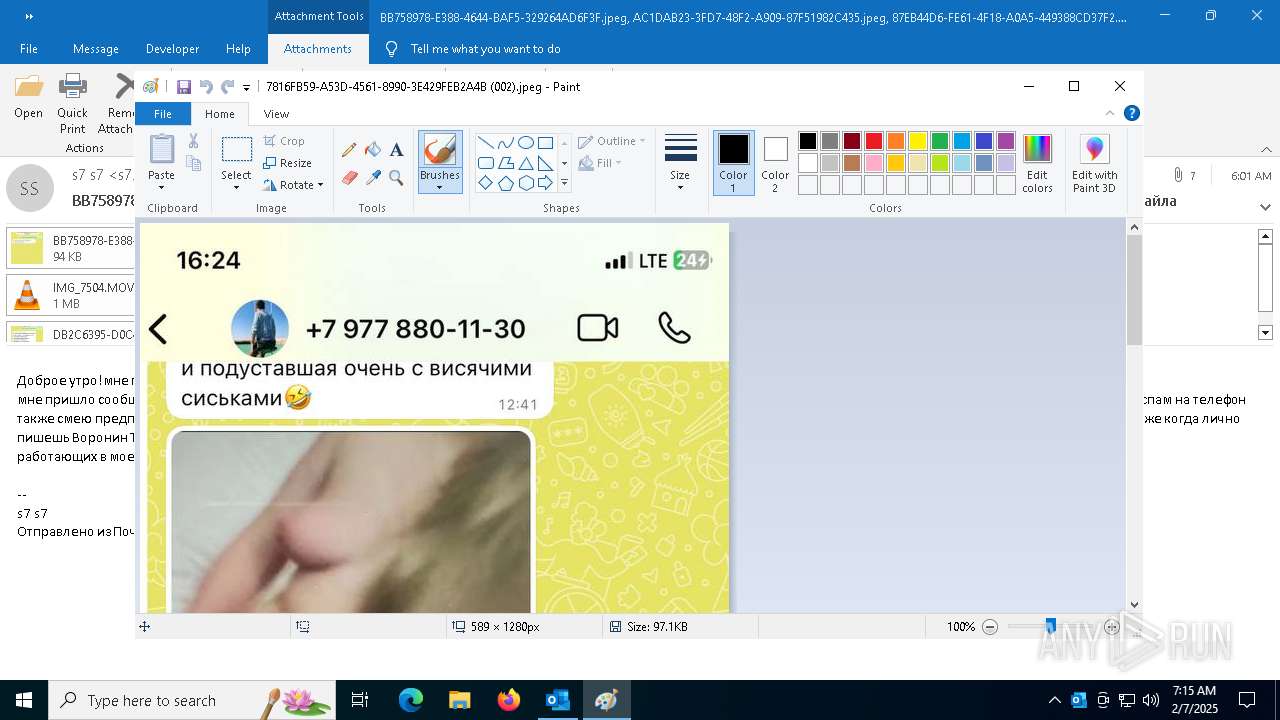
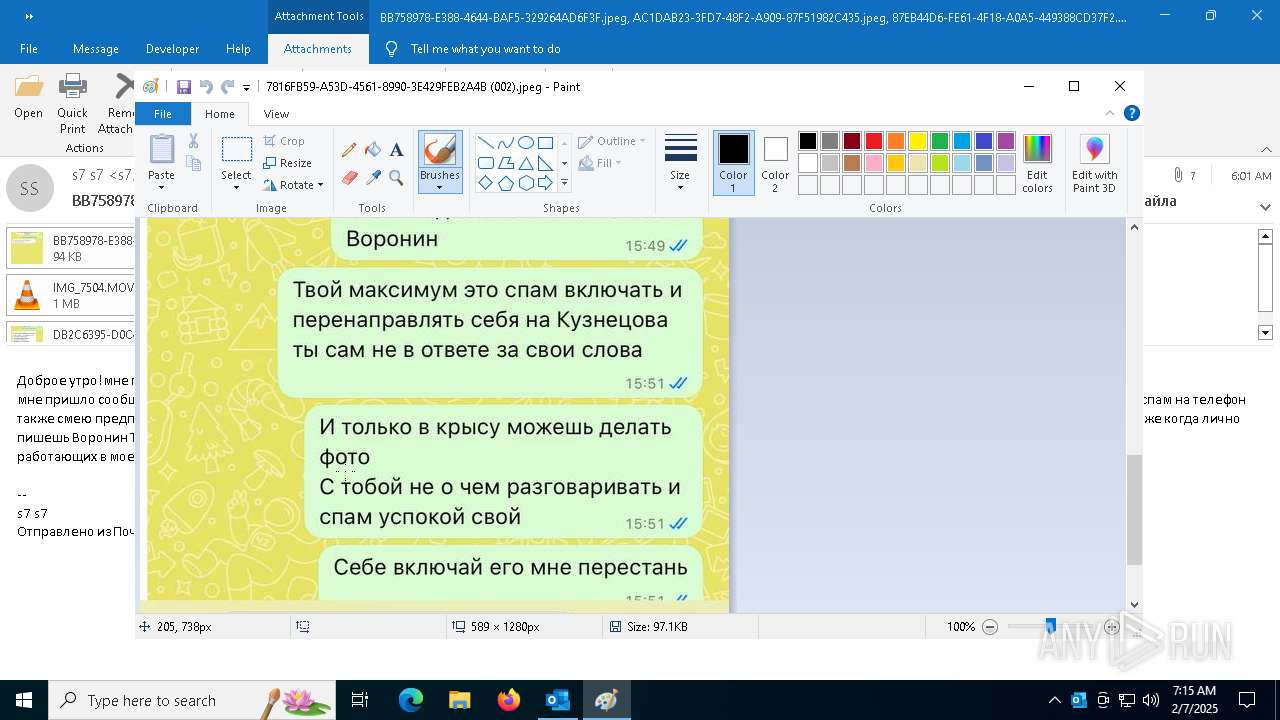
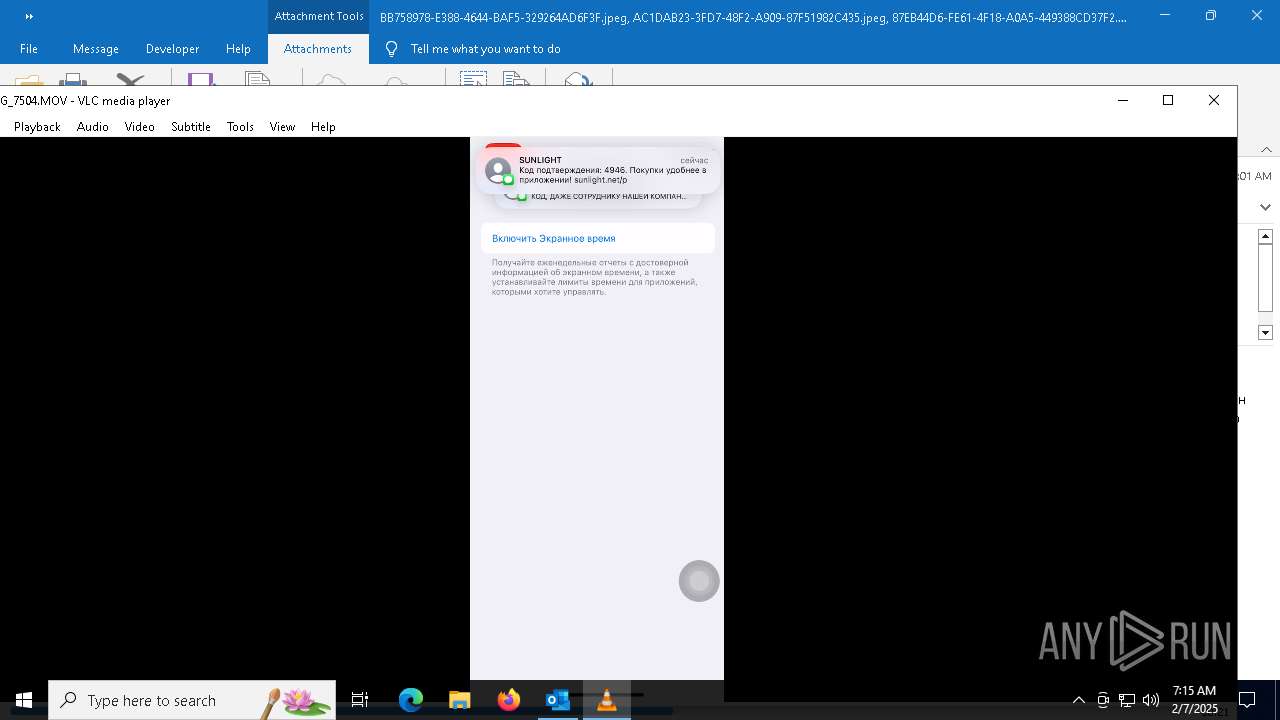
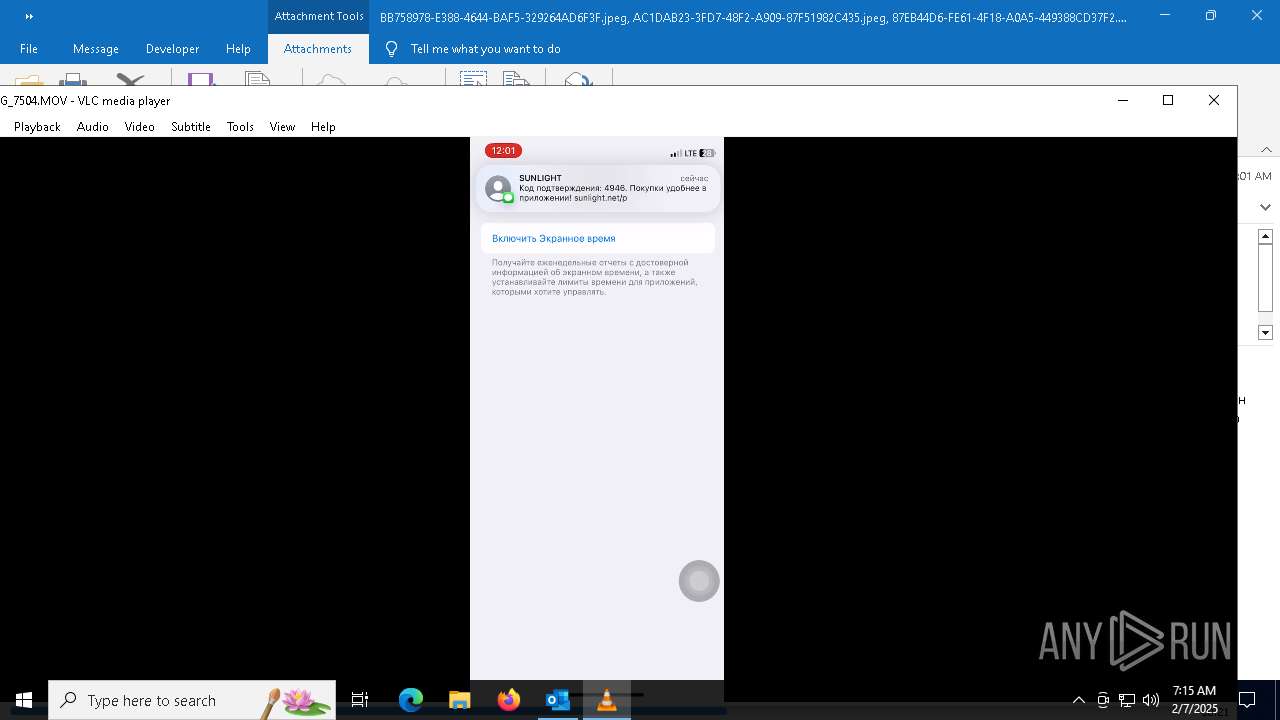
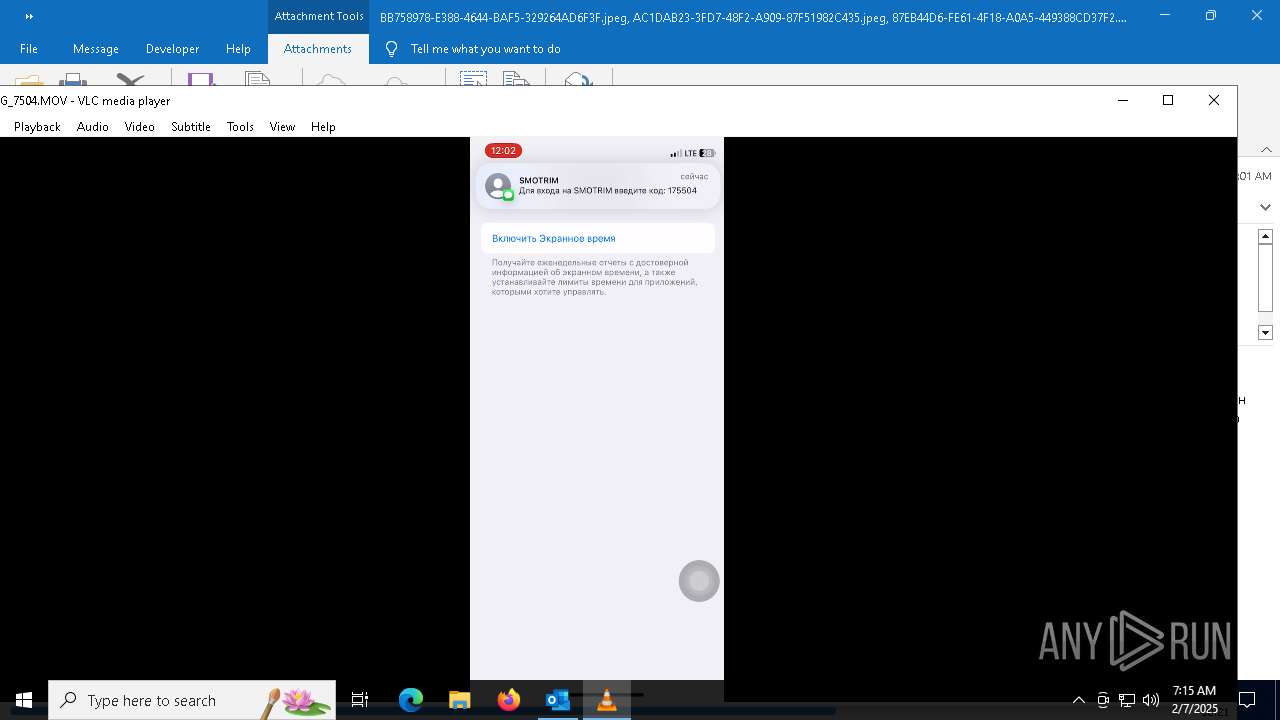
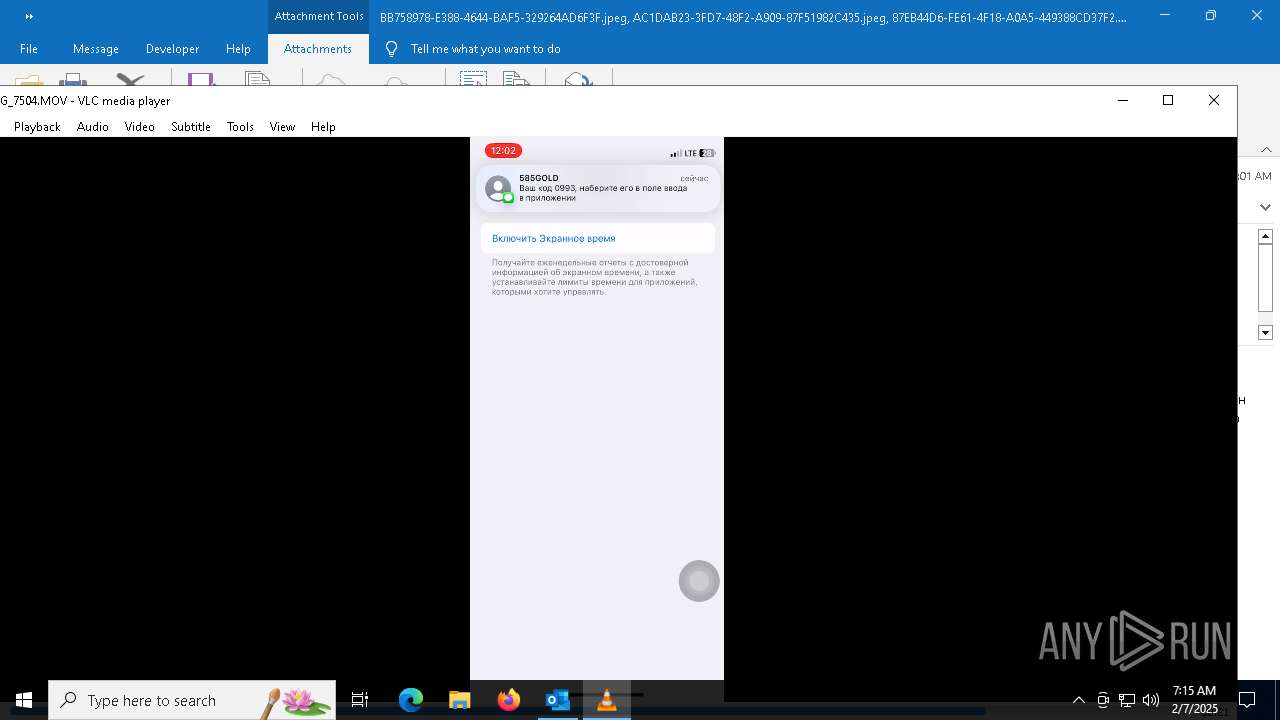
| 6356 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\AAYW2787\BB758978-E388-4644-BAF5-329264AD6F3F.jpeg | image | |
MD5:DC7D7A2C5D03A0E1385EA8F60E11076F | SHA256:A0C6D4B9FA6582E22B5A0715DD9B9F36BBDE5C6034DC533E65E07821110CF535 | |||
| 6356 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:760F1FA820896BA831800B4378630A04 | SHA256:7460F3790CEEC2BFD0BFD63DA91F8430CE544EDD18F3353BD98748BD10AA1B04 | |||
| 6356 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\CFA5360B-882B-48B1-AD47-281315731944 | xml | |
MD5:0AC76C78B74C2635D510DEA6313B26FD | SHA256:57F8E25B379F2F5EE73584D3D7EFA1A0DB80238B8EE971801B24F6E556C15B28 | |||
| 6356 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:739A97DABC8018D3F5A8F0526B74DEF0 | SHA256:1AA85D93C60B1F4CBE628F0BD0FBA00A923B8C4D971B45055326FCBB449EEB07 | |||
| 6356 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\AAYW2787\7816FB59-A53D-4561-8990-3E429FEB2A4B.jpeg | image | |
MD5:1F33A375EAF7BB5772D0378CB0561095 | SHA256:C35E1E3C98ED7022B3FB89DF6214ED5BB8AE2B778D61D6A98AC6E92615A4D919 | |||
| 6356 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:40B794CCE2BFD76BD117B325DE72C23C | SHA256:C0ABDDB73D50978E5D7A899D7FB7934D14C4F8A982ADBA29A46CA43EF081A960 | |||
| 6356 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\AAYW2787\AC1DAB23-3FD7-48F2-A909-87F51982C435.jpeg | image | |
MD5:3C469DEB512C92ACFCFF761A449F5D1A | SHA256:74227652531579FCEFAA6C81D8E25A634F3A5AAEDBDFA3CF016097CD1C6A356C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
43
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2144 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2144 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6356 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4996 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4996 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6356 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2144 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2144 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 92.123.104.19:443 | — | Akamai International B.V. | DE | unknown |
5064 | SearchApp.exe | 92.123.104.26:443 | — | Akamai International B.V. | DE | unknown |
6356 | OUTLOOK.EXE | 52.109.89.18:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
6356 | OUTLOOK.EXE | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1176 | svchost.exe | 40.126.31.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
Threats
Process | Message |
|---|---|
vlc.exe | main libvlc debug: min period: 1 ms, max period: 1000000 ms
|
vlc.exe | main libvlc debug: VLC media player - 3.0.11 Vetinari
|
vlc.exe | main libvlc debug: revision 3.0.11-0-gdc0c5ced72
|
vlc.exe | main libvlc debug: Copyright © 1996-2020 the VideoLAN team
|
vlc.exe | main libvlc debug: using multimedia timers as clock source
|
vlc.exe | main libvlc debug: configured with ../extras/package/win32/../../../configure '--enable-update-check' '--enable-lua' '--enable-faad' '--enable-flac' '--enable-theora' '--enable-avcodec' '--enable-merge-ffmpeg' '--enable-dca' '--enable-mpc' '--enable-libass' '--enable-schroedinger' '--enable-realrtsp' '--enable-live555' '--enable-dvdread' '--enable-shout' '--enable-goom' '--enable-caca' '--enable-qt' '--enable-skins2' '--enable-sse' '--enable-mmx' '--enable-libcddb' '--enable-zvbi' '--disable-telx' '--enable-nls' '--host=x86_64-w64-mingw32' '--with-breakpad=https://win.crashes.videolan.org' 'host_alias=x86_64-w64-mingw32' 'PKG_CONFIG_LIBDIR=/home/jenkins/workspace/vlc-release/windows/vlc-release-win32-x64/contrib/x86_64-w64-mingw32/lib/pkgconfig'
|
vlc.exe | main libvlc debug: searching plug-in modules
|
vlc.exe | main libvlc debug: loading plugins cache file C:\Program Files\VideoLAN\VLC\plugins\plugins.dat
|
vlc.exe | main libvlc debug: recursively browsing `C:\Program Files\VideoLAN\VLC\plugins'
|
vlc.exe | main libvlc debug: opening config file (C:\Users\admin\AppData\Roaming\vlc\vlcrc)
|