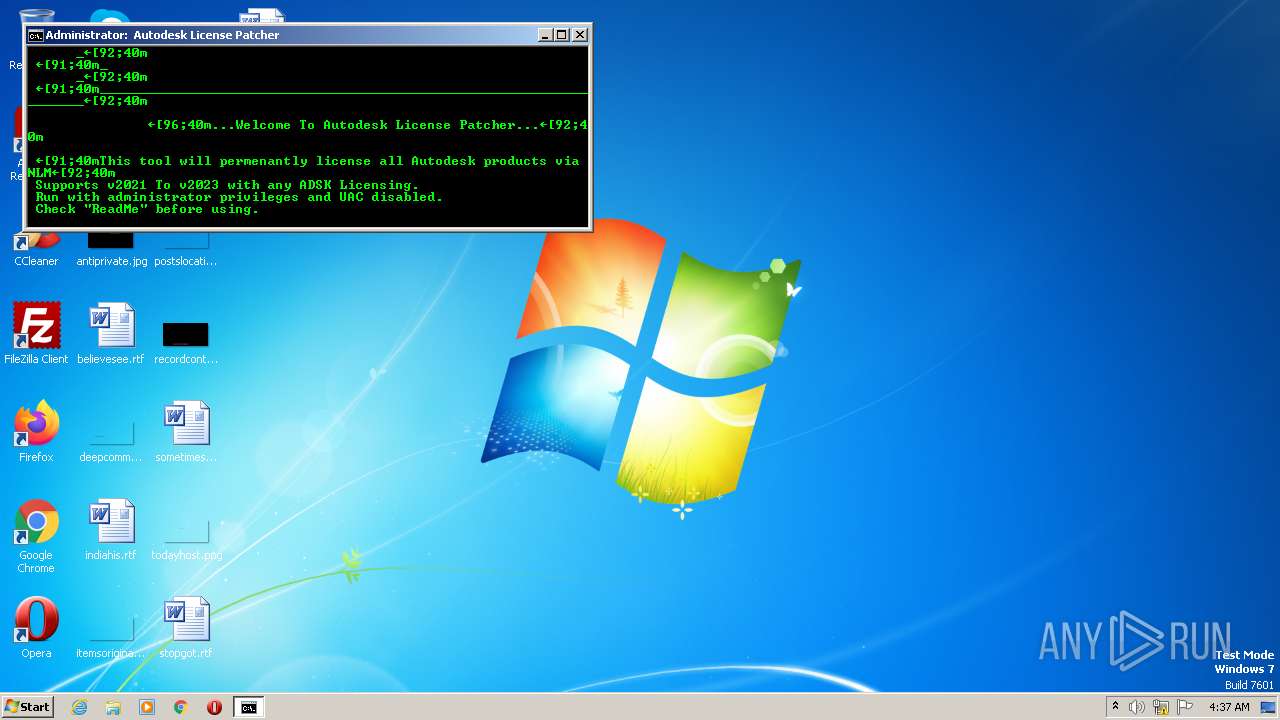
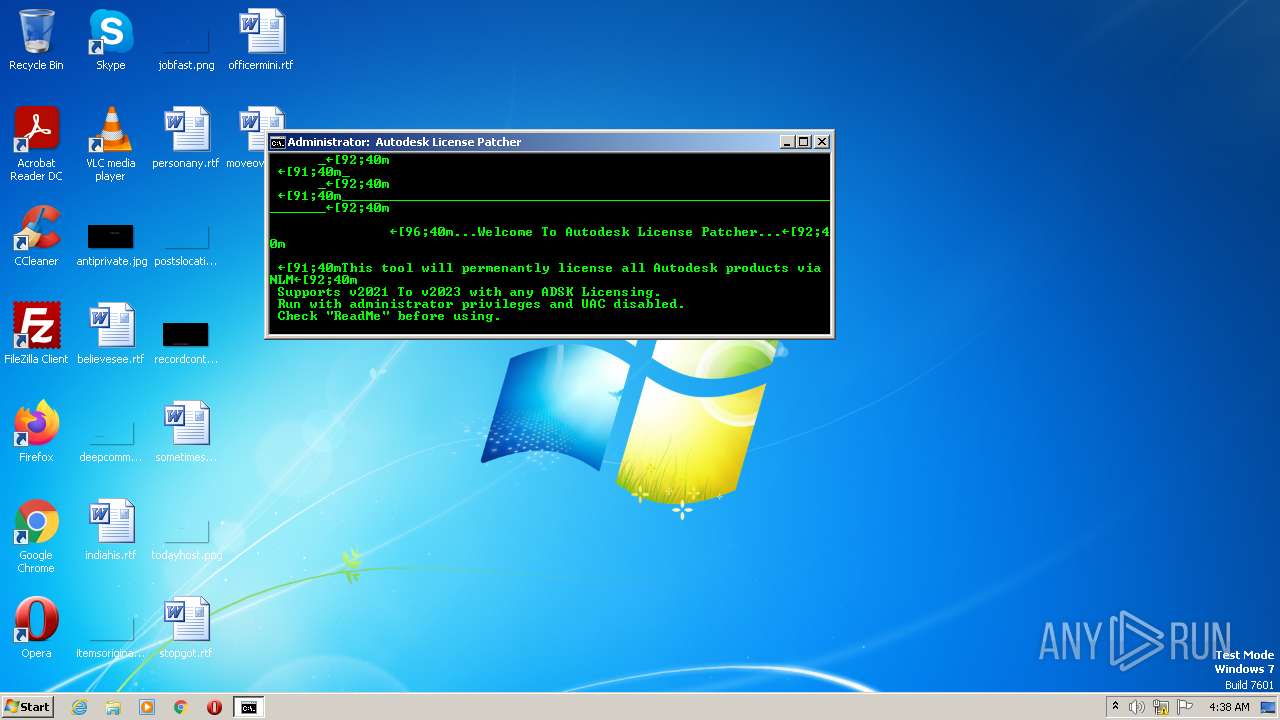
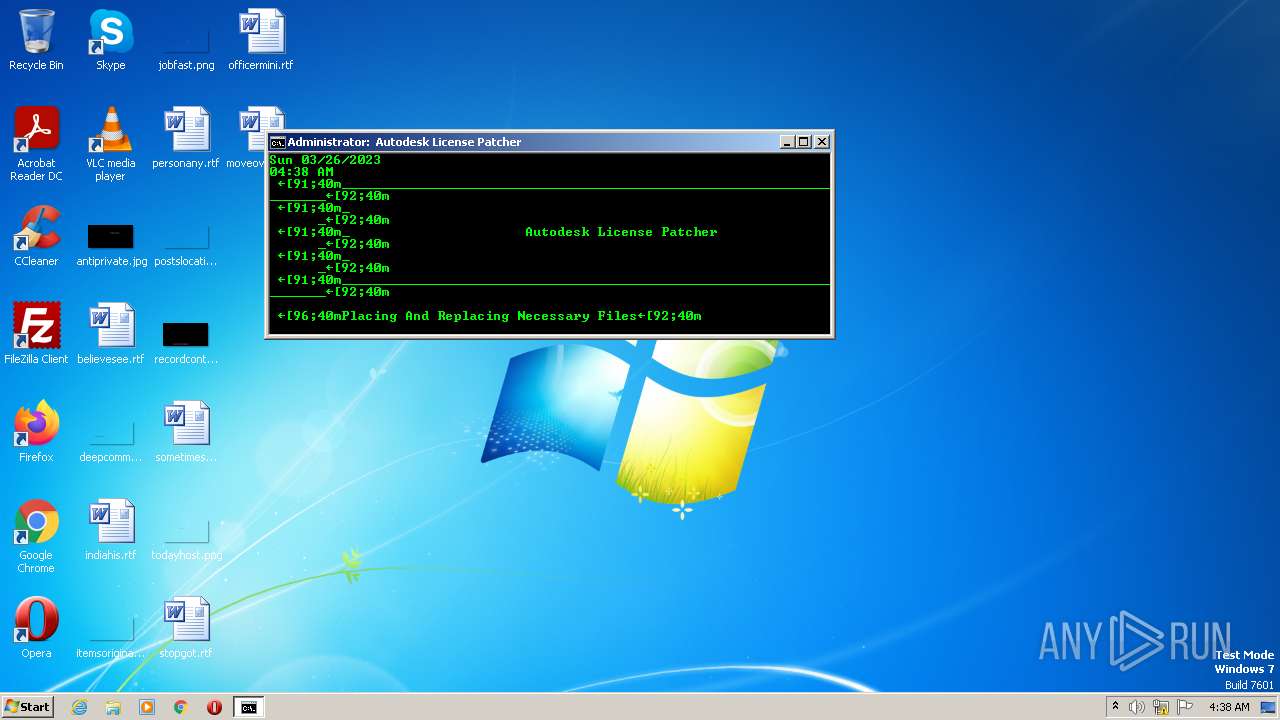
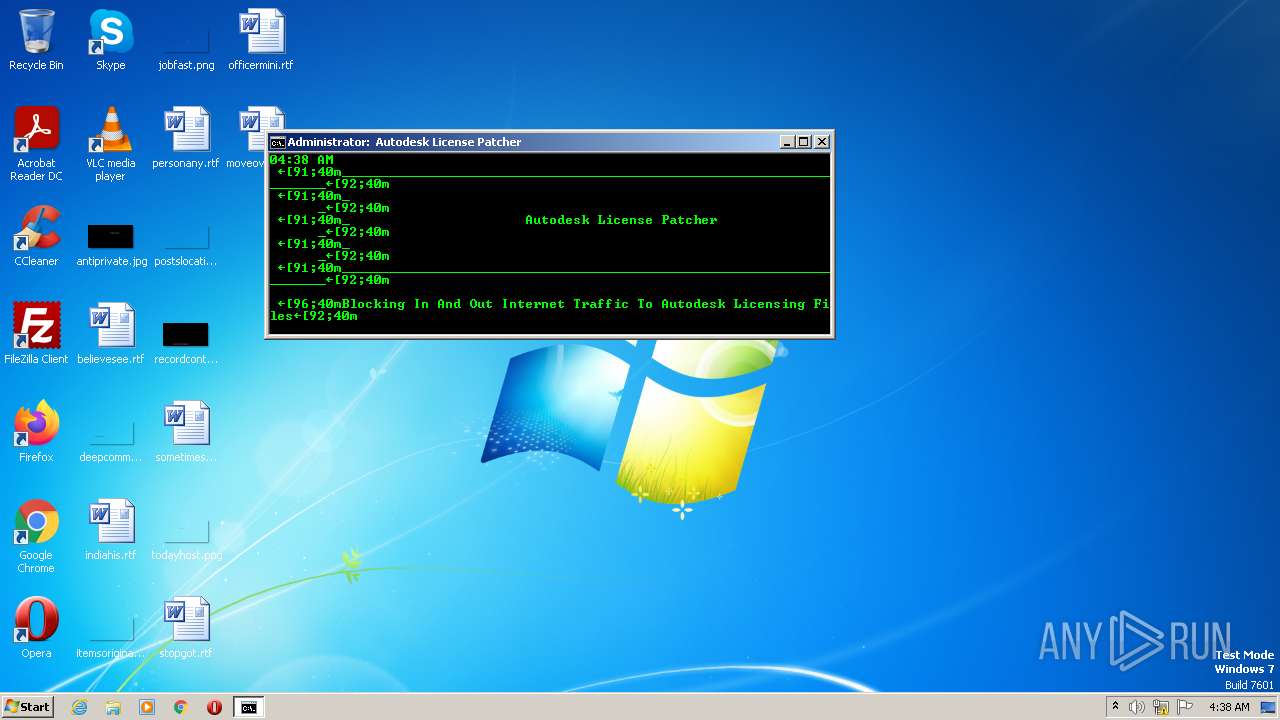
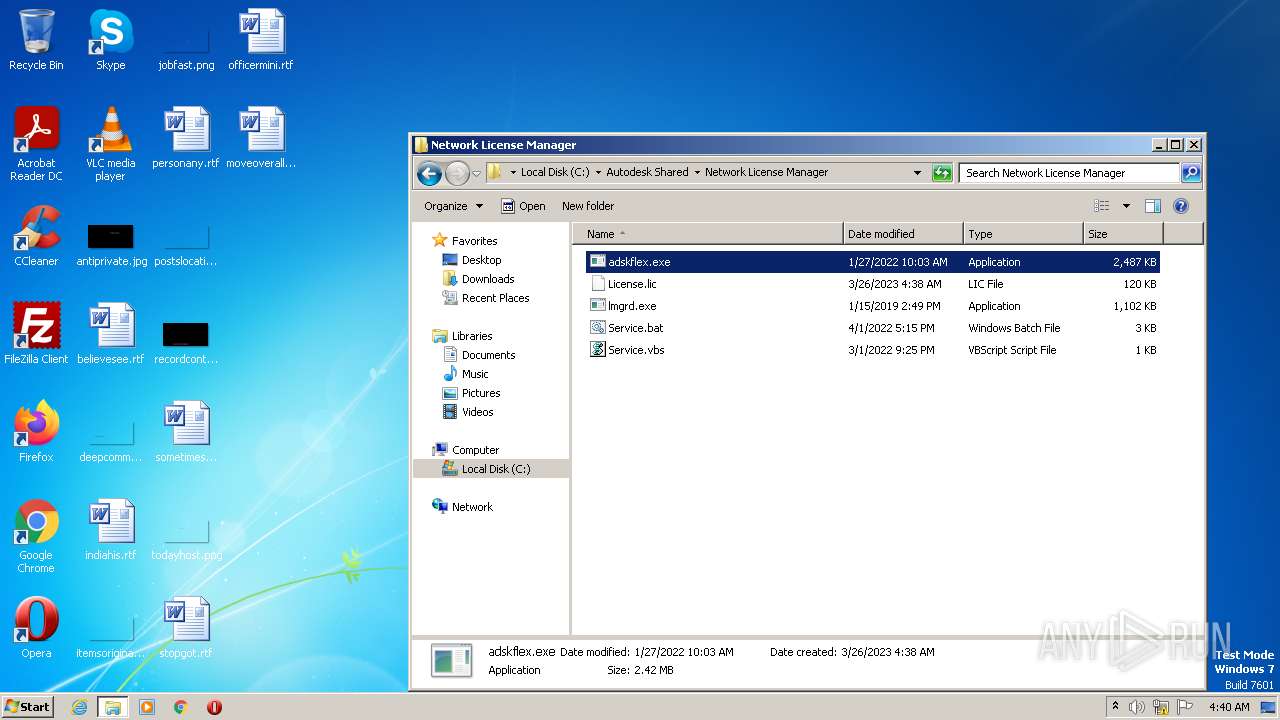
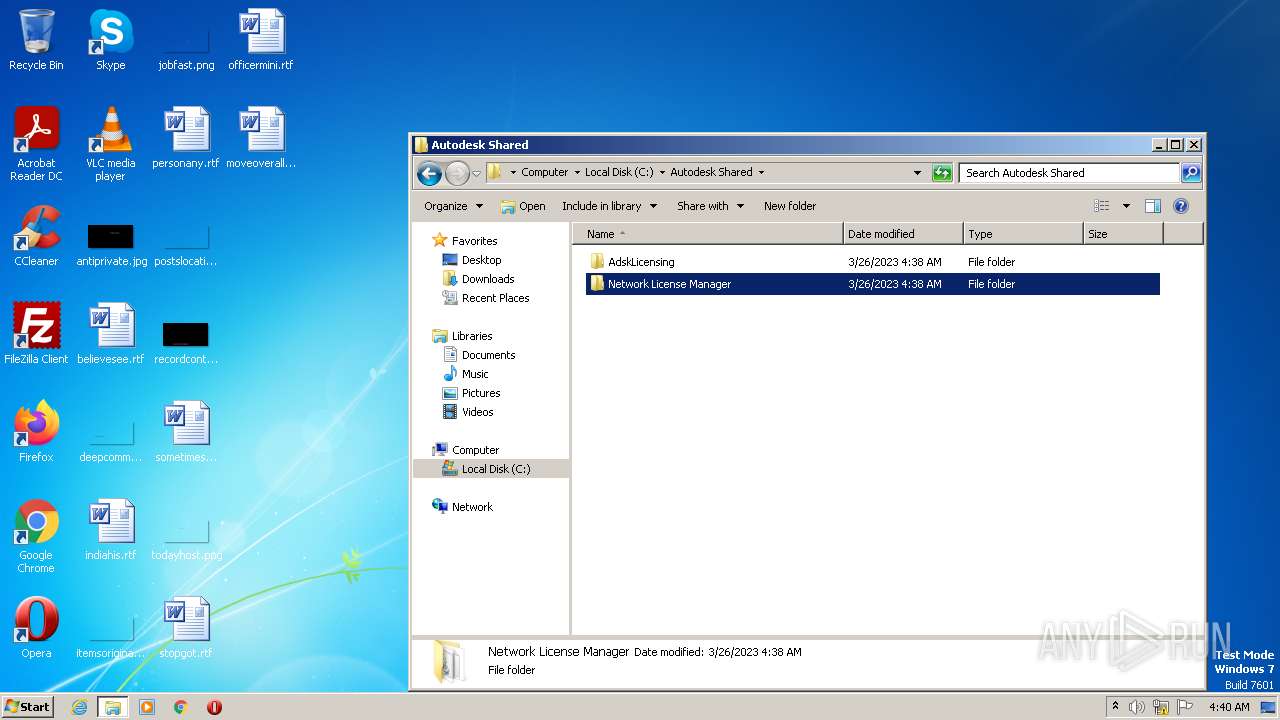
| File name: | Autodesk License Patcher Installer.exe |
| Full analysis: | https://app.any.run/tasks/023ba752-e53e-4e0c-9f95-4623489597d4 |
| Verdict: | Malicious activity |
| Analysis date: | March 26, 2023, 03:37:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | A5203927A840CD75BD807BC80A5F5C64 |
| SHA1: | B1C91369066608F4B97D82B677EBBB517F1DEF65 |
| SHA256: | DCA748FD092CAE601888CAD7CAEB986A79853EAD5471DE96689E1C54AE9CB6E1 |
| SSDEEP: | 24576:Lrr/9w9JpeSkiOMs25mI2rDc30x5tUewSFYndCfeI+GajylnGhj9EirjI:LH2LUSkOp50zxbUJndWeMln8Frc |
MALICIOUS
Starts NET.EXE for service management
- net.exe (PID: 3504)
- cmd.exe (PID: 1596)
- net.exe (PID: 2912)
- net.exe (PID: 3888)
- cmd.exe (PID: 1788)
- net.exe (PID: 1876)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 1596)
SUSPICIOUS
Executing commands from a ".bat" file
- Autodesk License Patcher Installer.exe (PID: 2572)
- cmd.exe (PID: 3156)
- wscript.exe (PID: 3580)
Starts CMD.EXE for commands execution
- Autodesk License Patcher Installer.exe (PID: 2572)
- cmd.exe (PID: 3156)
- cmd.exe (PID: 1596)
- wscript.exe (PID: 3580)
Executable content was dropped or overwritten
- Autodesk License Patcher Installer.exe (PID: 2572)
- xcopy.exe (PID: 2404)
- xcopy.exe (PID: 2420)
- xcopy.exe (PID: 3004)
Reads the Internet Settings
- Autodesk License Patcher Installer.exe (PID: 2572)
- WMIC.exe (PID: 1208)
- WMIC.exe (PID: 3296)
- wscript.exe (PID: 3580)
Starts application with an unusual extension
- cmd.exe (PID: 3156)
- cmd.exe (PID: 1596)
- cmd.exe (PID: 1788)
Uses REG/REGEDIT.EXE to modify register
- cmd.exe (PID: 3156)
- cmd.exe (PID: 1596)
- cmd.exe (PID: 1788)
Application launched itself
- cmd.exe (PID: 3156)
- cmd.exe (PID: 1596)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1596)
- cmd.exe (PID: 1788)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 1596)
- cmd.exe (PID: 1788)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1596)
- cmd.exe (PID: 1788)
Starts SC.EXE for service management
- cmd.exe (PID: 1596)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 1596)
Uses WMIC.EXE
- cmd.exe (PID: 2960)
- cmd.exe (PID: 3160)
The process executes VB scripts
- cmd.exe (PID: 1596)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 1596)
INFO
Reads the computer name
- Autodesk License Patcher Installer.exe (PID: 2572)
The process checks LSA protection
- Autodesk License Patcher Installer.exe (PID: 2572)
- cmd.exe (PID: 3156)
- taskkill.exe (PID: 1540)
- taskkill.exe (PID: 3604)
- taskkill.exe (PID: 2036)
- taskkill.exe (PID: 2844)
- msiexec.exe (PID: 908)
- powershell.exe (PID: 3860)
- taskkill.exe (PID: 2472)
- taskkill.exe (PID: 556)
- taskkill.exe (PID: 3440)
- taskkill.exe (PID: 3600)
- msiexec.exe (PID: 3864)
- taskkill.exe (PID: 3212)
- powershell.exe (PID: 556)
- WMIC.exe (PID: 3296)
- netsh.exe (PID: 2588)
- netsh.exe (PID: 2300)
- netsh.exe (PID: 3448)
- netsh.exe (PID: 2828)
- WMIC.exe (PID: 1208)
- netsh.exe (PID: 1488)
- netsh.exe (PID: 1012)
- netsh.exe (PID: 3632)
- netsh.exe (PID: 2420)
- netsh.exe (PID: 2984)
- netsh.exe (PID: 2080)
- netsh.exe (PID: 1864)
- netsh.exe (PID: 2696)
- taskkill.exe (PID: 2624)
- taskkill.exe (PID: 4084)
- taskkill.exe (PID: 2868)
- taskkill.exe (PID: 3212)
- taskkill.exe (PID: 312)
- taskkill.exe (PID: 1660)
- powershell.exe (PID: 3348)
- explorer.exe (PID: 3272)
- taskkill.exe (PID: 3364)
- taskkill.exe (PID: 3812)
- taskkill.exe (PID: 3704)
Checks supported languages
- chcp.com (PID: 3288)
- Autodesk License Patcher Installer.exe (PID: 2572)
- mode.com (PID: 3316)
- chcp.com (PID: 2792)
- mode.com (PID: 2844)
- chcp.com (PID: 2220)
- mode.com (PID: 2180)
Create files in a temporary directory
- cmd.exe (PID: 3156)
- powershell.exe (PID: 3860)
- powershell.exe (PID: 556)
- powershell.exe (PID: 3348)
[YARA] Firewall manipulation strings were found
- cmd.exe (PID: 1596)
Reads security settings of Internet Explorer
- powershell.exe (PID: 3860)
- powershell.exe (PID: 556)
- powershell.exe (PID: 3348)
Manual execution by a user
- explorer.exe (PID: 3272)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| SpecialBuild: | - |
|---|---|
| PrivateBuild: | - |
| Comments: | - |
| ProductVersion: | - |
| FileVersion: | - |
| OriginalFileName: | - |
| ProductName: | - |
| InternalName: | - |
| LegalTrademarks: | - |
| LegalCopyright: | - |
| FileDescription: | - |
| CompanyName: | - |
| CharacterSet: | Unicode |
| LanguageCode: | Russian |
| FileSubtype: | - |
| ObjectFileType: | Unknown |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x0000 |
| ProductVersionNumber: | 0.0.0.0 |
| FileVersionNumber: | 0.0.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 4 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x4cf60 |
| UninitializedDataSize: | 258048 |
| InitializedDataSize: | 176128 |
| CodeSize: | 57344 |
| LinkerVersion: | 8 |
| PEType: | PE32 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| TimeStamp: | 2012:12:31 00:38:38+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 31-Dec-2012 00:38:38 |
| Detected languages: |
|
| CompanyName: | - |
| FileDescription: | - |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| InternalName: | - |
| ProductName: | - |
| OriginalFilename: | - |
| FileVersion: | - |
| ProductVersion: | - |
| Comments: | - |
| PrivateBuild: | - |
| SpecialBuild: | - |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0060 |
| Pages in file: | 0x0001 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000060 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 31-Dec-2012 00:38:38 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
UPX0 | 0x00001000 | 0x0003F000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
UPX1 | 0x00040000 | 0x0000E000 | 0x0000DC00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.97814 |
.rsrc | 0x0004E000 | 0x0002B000 | 0x0002A200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.32227 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.23138 | 838 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 0 | 744 | Latin 1 / Western European | Russian - Russia | RT_ICON |
3 | 1.83036 | 488 | Latin 1 / Western European | Russian - Russia | RT_ICON |
4 | 2.2763 | 296 | Latin 1 / Western European | Russian - Russia | RT_ICON |
50 | 7.90594 | 7553 | Latin 1 / Western European | Russian - Russia | RT_ICON |
51 | 2.54785 | 67624 | Latin 1 / Western European | Russian - Russia | RT_ICON |
52 | 2.87378 | 38056 | Latin 1 / Western European | Russian - Russia | RT_ICON |
53 | 2.86285 | 21640 | Latin 1 / Western European | Russian - Russia | RT_ICON |
54 | 2.77144 | 16936 | Latin 1 / Western European | Russian - Russia | RT_ICON |
55 | 3.12417 | 9640 | Latin 1 / Western European | Russian - Russia | RT_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.DLL |
MSVCRT.dll |
OLEAUT32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
135
Monitored processes
90
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 312 | taskkill /F /IM "AdskLicensingInstHelper.exe" | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
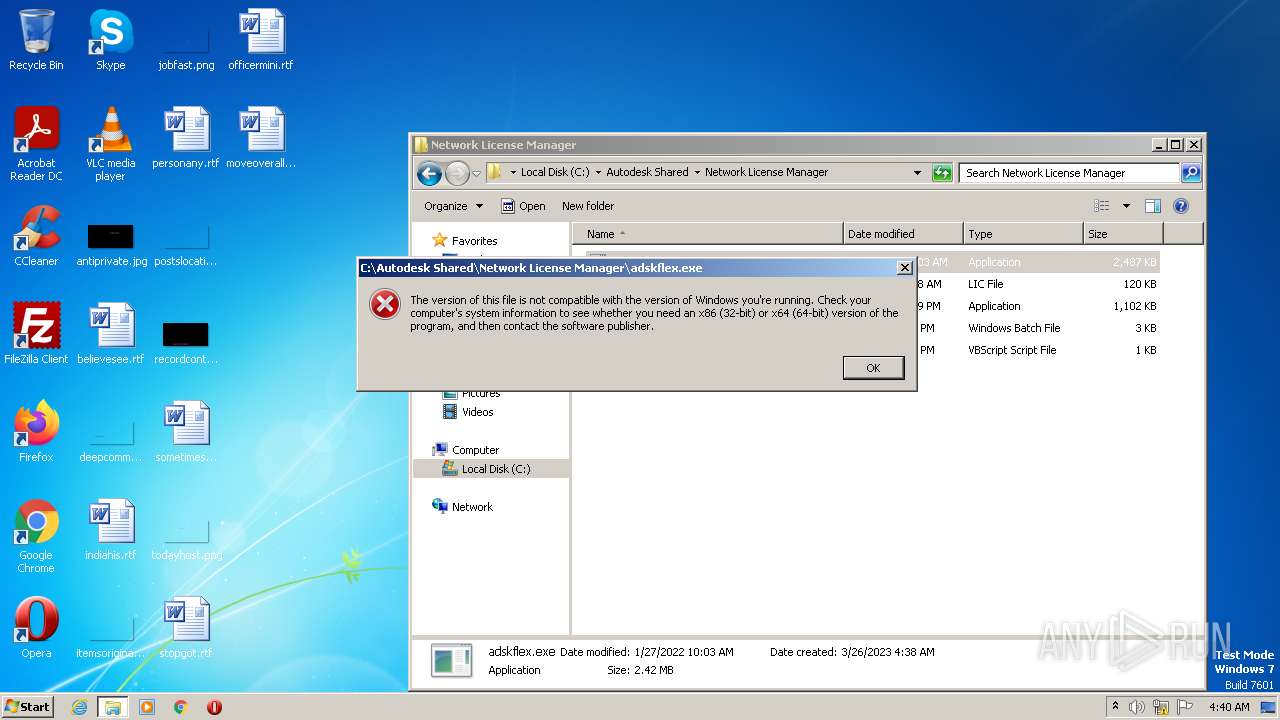
| 556 | taskkill /F /IM "adskflex.exe" | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 556 | powershell -Command "(gc License.lic) -replace 'MAC', '12A9866C77DE ' -replace 'HOSTNAME', 'User-PC' | Out-File -encoding ASCII License.lic" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 908 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1012 | netsh advfirewall firewall delete rule name="Allowed C:\Autodesk Shared\Network License Manager\lmgrd.exe" | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1184 | ping 127.0.0.1 -n 5 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1208 | wmic path Win32_NetworkAdapter where "PNPDeviceID like '%%USB%%' AND AdapterTypeID='0'" get MacAddress,AdapterType | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1384 | schtasks.exe /Delete /tn "\Microsoft\Windows\Autodesk\Autodesk" /f | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1488 | netsh advfirewall firewall add rule name="Blocked C:\Autodesk Shared\Network License Manager\adskflex.exe" dir=in action=block profile=any program="C:\Autodesk Shared\Network License Manager\adskflex.exe" | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1540 | taskkill /F /IM "AdskLicensingAgent.exe" | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
23 752
Read events
22 610
Write events
1 142
Delete events
0
Modification events
| (PID) Process: | (2572) Autodesk License Patcher Installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2572) Autodesk License Patcher Installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2572) Autodesk License Patcher Installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2572) Autodesk License Patcher Installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3536) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion |
| Operation: | write | Name: | RegisteredOwner |
Value: admin | |||
| (PID) Process: | (2588) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2300) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3448) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2828) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2420) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
12
Suspicious files
12
Text files
16
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2572 | Autodesk License Patcher Installer.exe | C:\AutodeskLicensePatcherInstaller\AutodeskLicensePatcherInstaller.bat | text | |
MD5:8C6A12F0931B1C1BEBDFFD415406523A | SHA256:70C6544BFBDE92D697CF76543104EAF42629B7823B29AC759BEF670F89BE4E82 | |||
| 2572 | Autodesk License Patcher Installer.exe | C:\AutodeskLicensePatcherInstaller\Files\NetworkLicenseManager\License.lic | text | |
MD5:4D062EA9E3D37E764E986913DB4CAAA2 | SHA256:72C545208818C062C13A3423771AD1453C8D07659E516632E4596E4DDBE093DE | |||
| 2572 | Autodesk License Patcher Installer.exe | C:\AutodeskLicensePatcherInstaller\Files\NetworkLicenseManager\lmgrd.exe | executable | |
MD5:219F8CEBEF26F1373062357B2F4A8489 | SHA256:CF025ECFB3556E334DDE501B95485998DE9E1B6A06CCBD56FFA1345D6B5A3973 | |||
| 2572 | Autodesk License Patcher Installer.exe | C:\AutodeskLicensePatcherInstaller\Files\Service\Service.vbs | text | |
MD5:BDCEE93AFA90EC55B9DEDDB3014E2269 | SHA256:9212E1A3E7D690BE3574A5252C3435E2602B3BB742993A416F483105ED53BF61 | |||
| 2572 | Autodesk License Patcher Installer.exe | C:\AutodeskLicensePatcherInstaller\Files\Task\Autodesk.xml | xml | |
MD5:53067581F721F8C3659FED0EBE619E79 | SHA256:35C8E66648CCC4A10689B7DCB78345CC857A03140CC91084679736E03798F624 | |||
| 2572 | Autodesk License Patcher Installer.exe | C:\AutodeskLicensePatcherInstaller\Files\Service\Service.bat | text | |
MD5:D0D4F5CD24C63A74C68A03B2B3A8786D | SHA256:62B915D1E0E26F72700C519534F181AC9728FFF9252D21298667FB85ECC3B702 | |||
| 3244 | xcopy.exe | C:\Autodesk Shared\Network License Manager\Service.vbs | text | |
MD5:BDCEE93AFA90EC55B9DEDDB3014E2269 | SHA256:9212E1A3E7D690BE3574A5252C3435E2602B3BB742993A416F483105ED53BF61 | |||
| 556 | powershell.exe | C:\Users\admin\AppData\Local\Temp\bk1nhavo.pij.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2420 | xcopy.exe | C:\Autodesk Shared\Network License Manager\adskflex.exe | executable | |
MD5:C00B8B7B1C084718EC5D63A53AEFB1EB | SHA256:05B24756D46CE216C84878DDDC97EF9E2EEB6ECA8EC12C97E780C4D0EEF63731 | |||
| 3004 | xcopy.exe | C:\Autodesk Shared\AdskLicensing\Current\AdskLicensingAgent\version.dll | executable | |
MD5:51F0E19B4CF164ECBA9A006C4CF3B2A5 | SHA256:6F13E52D797A732435C8BB456BE08C64D0B6FADEA29F85486F4B44559D6CC95F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report