| File name: | 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer |
| Full analysis: | https://app.any.run/tasks/c131e2e3-f491-4099-8c46-3968a48b3b19 |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 04:07:18 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | 24DE73F7FF5C18405BDDD4AAE6BE79AD |
| SHA1: | E97C448BB559523AFBB061E8C0F9EB7EA4C28C18 |
| SHA256: | DC9465F1EAFBA7CC7941D7836F62373A1A71DCDE18E6FECFC074571C8412A8A7 |
| SSDEEP: | 98304:0ftOC2wtuy0QwrKRjhOOCqUBWsMS+aF/MuncM6TXnodOrFksOe1eo8YqZwNqg13e:wh/9ZS |
MALICIOUS
NESHTA mutex has been found
- FileCoAuth.exe (PID: 3268)
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4380)
Executing a file with an untrusted certificate
- FileCoAuth.exe (PID: 904)
SUSPICIOUS
Reads security settings of Internet Explorer
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4988)
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4380)
- FileCoAuth.exe (PID: 3268)
Process drops legitimate windows executable
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4988)
- FileCoAuth.exe (PID: 3268)
Executable content was dropped or overwritten
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4380)
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4988)
- FileCoAuth.exe (PID: 3268)
There is functionality for taking screenshot (YARA)
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4380)
Reads the Windows owner or organization settings
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4988)
Mutex name with non-standard characters
- FileCoAuth.exe (PID: 3268)
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4380)
Starts a Microsoft application from unusual location
- FileCoAuth.exe (PID: 904)
ADVANCEDINSTALLER mutex has been found
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4988)
INFO
The sample compiled with english language support
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4380)
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4988)
- FileCoAuth.exe (PID: 3268)
Reads the computer name
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4380)
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4988)
- msiexec.exe (PID: 2284)
- msiexec.exe (PID: 4892)
- FileCoAuth.exe (PID: 904)
Create files in a temporary directory
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4380)
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4988)
- FileCoAuth.exe (PID: 904)
Checks proxy server information
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4988)
Reads the machine GUID from the registry
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4988)
- FileCoAuth.exe (PID: 904)
Checks supported languages
- msiexec.exe (PID: 2284)
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4988)
- msiexec.exe (PID: 4892)
- FileCoAuth.exe (PID: 904)
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4380)
Process checks computer location settings
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4380)
- FileCoAuth.exe (PID: 3268)
Reads Environment values
- msiexec.exe (PID: 4892)
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4988)
Reads the software policy settings
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4988)
Creates files or folders in the user directory
- FileCoAuth.exe (PID: 904)
Creates files in the program directory
- 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe (PID: 4988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Borland Delphi 6 (85.5) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (4.6) |
| .scr | | | Windows screen saver (4.2) |
| .dll | | | Win32 Dynamic Link Library (generic) (2.1) |
| .exe | | | Win32 Executable (generic) (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 29696 |
| InitializedDataSize: | 10752 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x8178 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
129
Monitored processes
7
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 904 | "C:\Users\admin\AppData\Local\Temp\3582-490\FileCoAuth.exe" -Embedding | C:\Users\admin\AppData\Local\Temp\3582-490\FileCoAuth.exe | — | FileCoAuth.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneDriveFile Co-Authoring Executable Exit code: 0 Version: 19.043.0304.0013 Modules
| |||||||||||||||
| 2284 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3268 | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe -Embedding | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4380 | "C:\Users\admin\Desktop\2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe" | C:\Users\admin\Desktop\2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4892 | C:\Windows\syswow64\MsiExec.exe -Embedding EFC9591ABB358AA26CFD9BB8F30E4E38 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
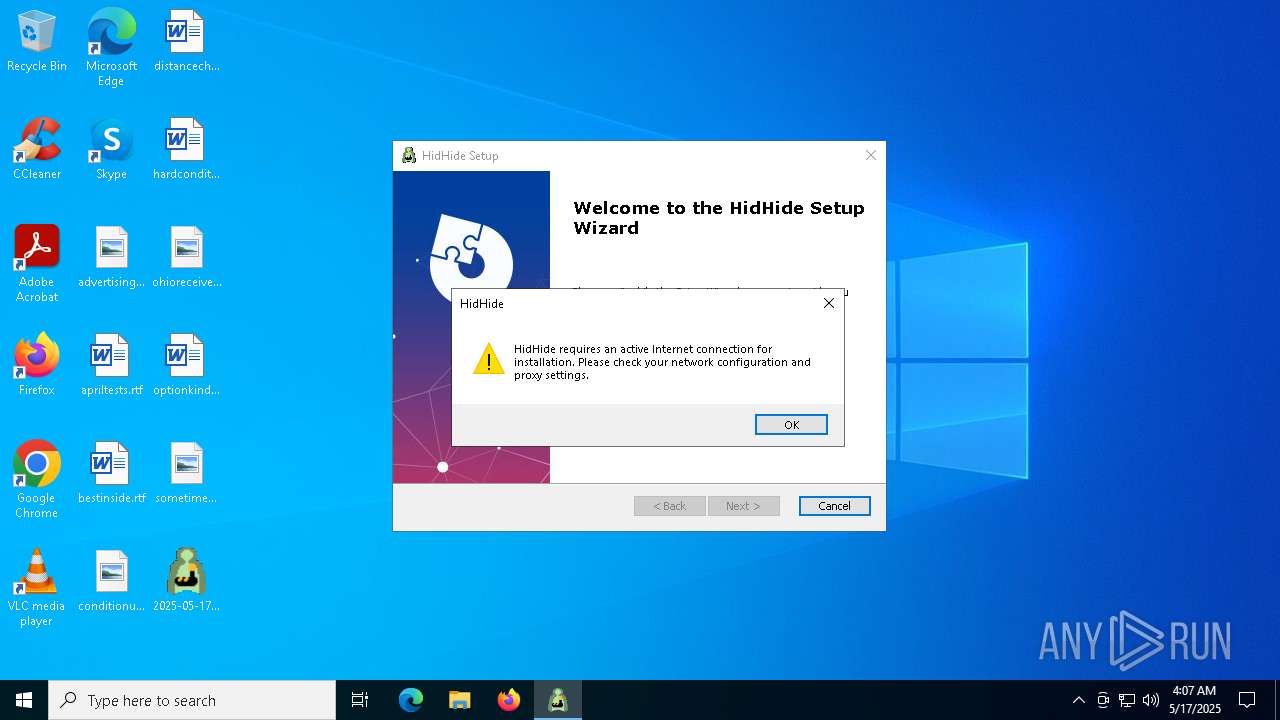
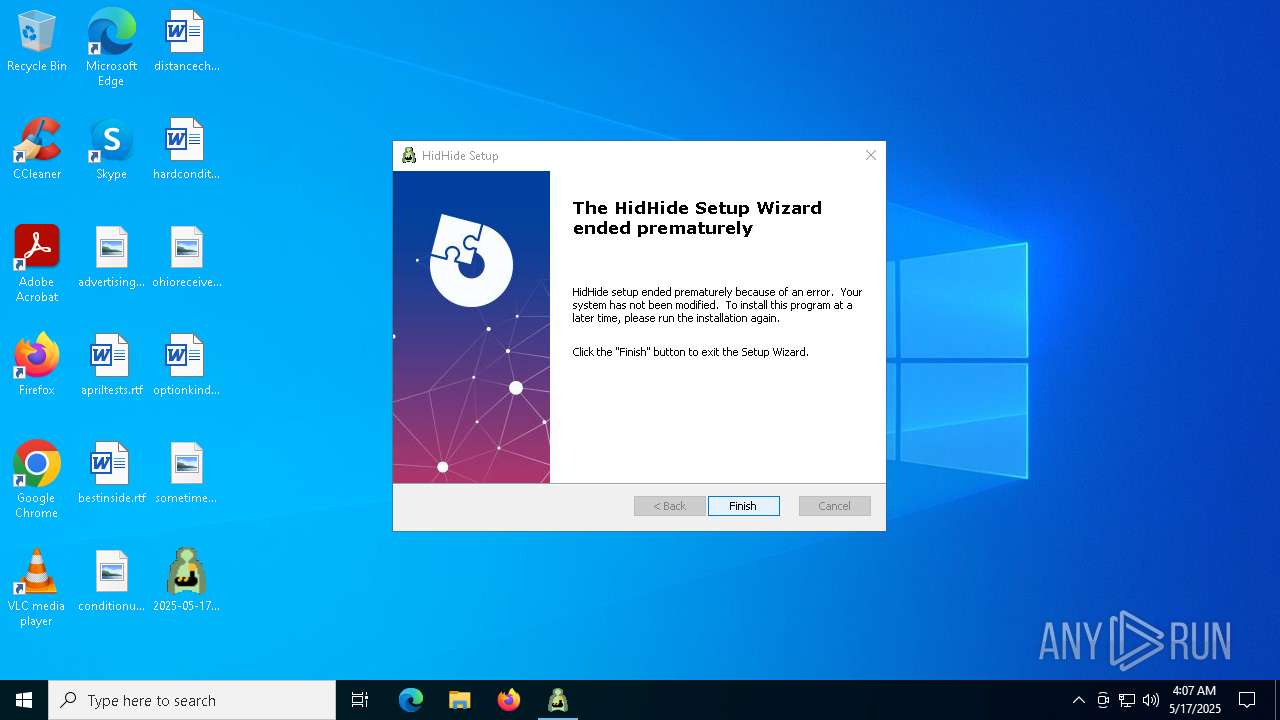
| 4988 | "C:\Users\admin\AppData\Local\Temp\3582-490\2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe" | C:\Users\admin\AppData\Local\Temp\3582-490\2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | ||||||||||||
User: admin Company: Nefarius Software Solutions e.U. Integrity Level: MEDIUM Description: HidHide Installer Exit code: 1602 Version: 1.2.98 Modules
| |||||||||||||||
| 6644 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 696
Read events
7 690
Write events
0
Delete events
6
Modification events
| (PID) Process: | (4988) 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\AiTemp |
| Operation: | delete value | Name: | C__Users_admin_AppData_Local_Temp_3582-490_2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe |
Value: | |||
| (PID) Process: | (4988) 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\AiTemp |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4988) 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | delete value | Name: | C__Users_admin_AppData_Local_Temp_3582-490_2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe |
Value: | |||
| (PID) Process: | (4892) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Nefarius Software Solutions e.U. AiTemp |
| Operation: | delete value | Name: | {27AF679E-48DB-4B49-A689-1D6A3A52C472} |
Value: | |||
| (PID) Process: | (4892) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Nefarius Software Solutions e.U. AiTemp |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4892) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | delete value | Name: | {27AF679E-48DB-4B49-A689-1D6A3A52C472} |
Value: | |||
Executable files
23
Suspicious files
5
Text files
22
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4988 | 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | C:\ProgramData\Nefarius Software Solutions\HidHide 1.2.98\install\decoder.dll | executable | |
MD5:5C6B9CB41F88B5750C6124CBCF14FB0E | SHA256:E015F8396AADD7C7734E1A95999ECA5943402E8205D1F20B56D1AEB1A2FE0971 | |||
| 4988 | 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | C:\Users\admin\AppData\Local\Temp\MSID40C.tmp | executable | |
MD5:822EC3C1B42FFDF6DB9A15936F4512CF | SHA256:94CC96B889D32F8DF13878F3CE538A741FA2D48444285C5C36849A817FC25597 | |||
| 4988 | 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | C:\ProgramData\Nefarius Software Solutions\HidHide 1.2.98\install\A52C472\HidHide.msi | executable | |
MD5:A0184DF710D6897FEF5F88E32B6AD548 | SHA256:9516C25CDD0E83C824CBAE02C998DAB71CDC00FCC8393D63D03898B962012CF8 | |||
| 4988 | 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | C:\Users\admin\AppData\Local\Temp\shiD38E.tmp | executable | |
MD5:84A34BF3486F7B9B7035DB78D78BDD1E | SHA256:F85911C910B660E528D2CF291BAA40A92D09961996D6D84E7A53A7095C7CD96E | |||
| 4380 | 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe | executable | |
MD5:21DA59CE25A2391BD3B0032B2CACDA60 | SHA256:25A12C3598CFE9705928B3110FA40E36E885BEDEEB51F405B063E806D3A4FA4B | |||
| 4380 | 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileSyncConfig.exe | executable | |
MD5:62B17C396323A05211FCB806947C9A73 | SHA256:ADD9754D24558AD5692521CFE97E9F1E71144F41E4E99D984BEE71F697D25F55 | |||
| 4988 | 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | C:\Users\admin\AppData\Local\Temp\MSID578.tmp | executable | |
MD5:822EC3C1B42FFDF6DB9A15936F4512CF | SHA256:94CC96B889D32F8DF13878F3CE538A741FA2D48444285C5C36849A817FC25597 | |||
| 4988 | 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | C:\ProgramData\Nefarius Software Solutions\HidHide 1.2.98\install\holder0.aiph | binary | |
MD5:40953FDAC7A00D2837465350EB838AE5 | SHA256:19419A7AF58591CBA0208A7A1A30119CFC51CE4FF3F7665EAF2694B4361C9940 | |||
| 4380 | 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | C:\Users\admin\AppData\Local\Temp\3582-490\2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | executable | |
MD5:713BE41FC23A881B16FB7888F20B9051 | SHA256:22731E1BC9B3BD95AF32711D51CB5CFDAFF9F5247D8CBC5D6B90F66667F1231D | |||
| 4988 | 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | C:\Users\admin\AppData\Local\Temp\MSID538.tmp | executable | |
MD5:822EC3C1B42FFDF6DB9A15936F4512CF | SHA256:94CC96B889D32F8DF13878F3CE538A741FA2D48444285C5C36849A817FC25597 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
26
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4988 | 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | GET | — | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEA%2B4p0C5FY0DUUO8WdnwQCk%3D | unknown | — | — | whitelisted |
4988 | 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | GET | — | 2.17.190.73:80 | http://crl3.digicert.com/DigiCertGlobalRootG3.crl | unknown | — | — | whitelisted |
4988 | 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | GET | — | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSE67Nbq3jfQQg8yXEpbmqLTNn7XwQUm1%2BwNrqdBq4ZJ73AoCLAi4s4d%2B0CEAZrLNkSHqdrn7DTOKxZ2QU%3D | unknown | — | — | whitelisted |
4988 | 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | GET | — | 2.17.190.73:80 | http://crl3.digicert.com/DigiCertGlobalG3CodeSigningECCSHA3842021CA1.crl | unknown | — | — | whitelisted |
4988 | 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | GET | — | 2.17.190.73:80 | http://crl4.digicert.com/DigiCertGlobalG3CodeSigningECCSHA3842021CA1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4988 | 2025-05-17_24de73f7ff5c18405bddd4aae6be79ad_amadey_black-basta_darkgate_elex_gcleaner_hijackloader_luca-stealer.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1616 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6644 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |