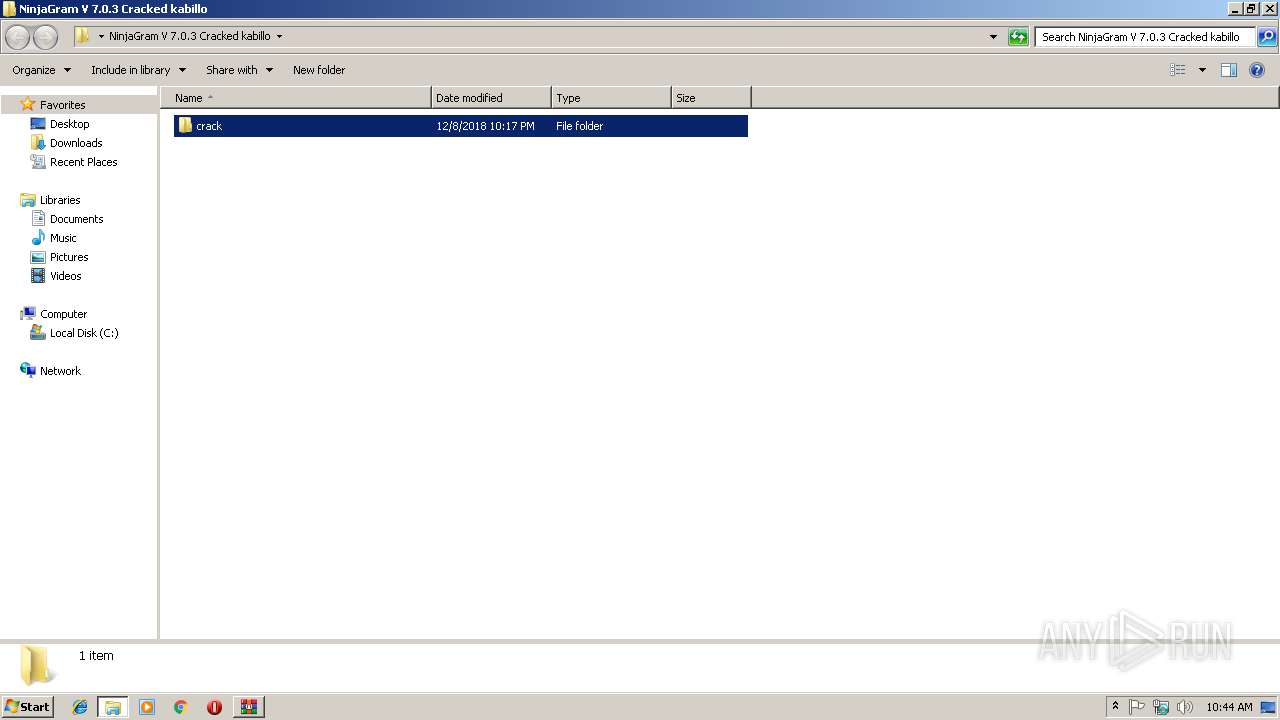
| File name: | NinjaGram V 7.0.3 Cracked kabillo.rar |
| Full analysis: | https://app.any.run/tasks/3774f7be-7630-48e4-9779-826563947046 |
| Verdict: | Malicious activity |
| Analysis date: | December 11, 2018, 10:43:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | D75CD31C01354AF03B2283EA21EA553D |
| SHA1: | 8E1924ABE2DFCB4A549B6D36C4F761E93E58C5BD |
| SHA256: | DC347B03F98949EC9417EC49E57238976700B7A1A984C427463F6F171294F568 |
| SSDEEP: | 24576:rSZVXDZ4yp+MigexDa5yfqlP6ZLqPEdDwjVIJ6dxux5+sPJ:2VxPigexD0yfqsNqPIEyJ6ux5+sB |
MALICIOUS
Application was dropped or rewritten from another process
- NinjaGram.exe (PID: 3892)
- NinjaGram.exe (PID: 2952)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 996)
- NinjaGram.exe (PID: 2952)
SUSPICIOUS
Executable content was dropped or overwritten
- NinjaGram.exe (PID: 3892)
- WinRAR.exe (PID: 2968)
Creates files in the Windows directory
- NinjaGram.exe (PID: 3892)
Modifies the open verb of a shell class
- NinjaGram.exe (PID: 3892)
INFO
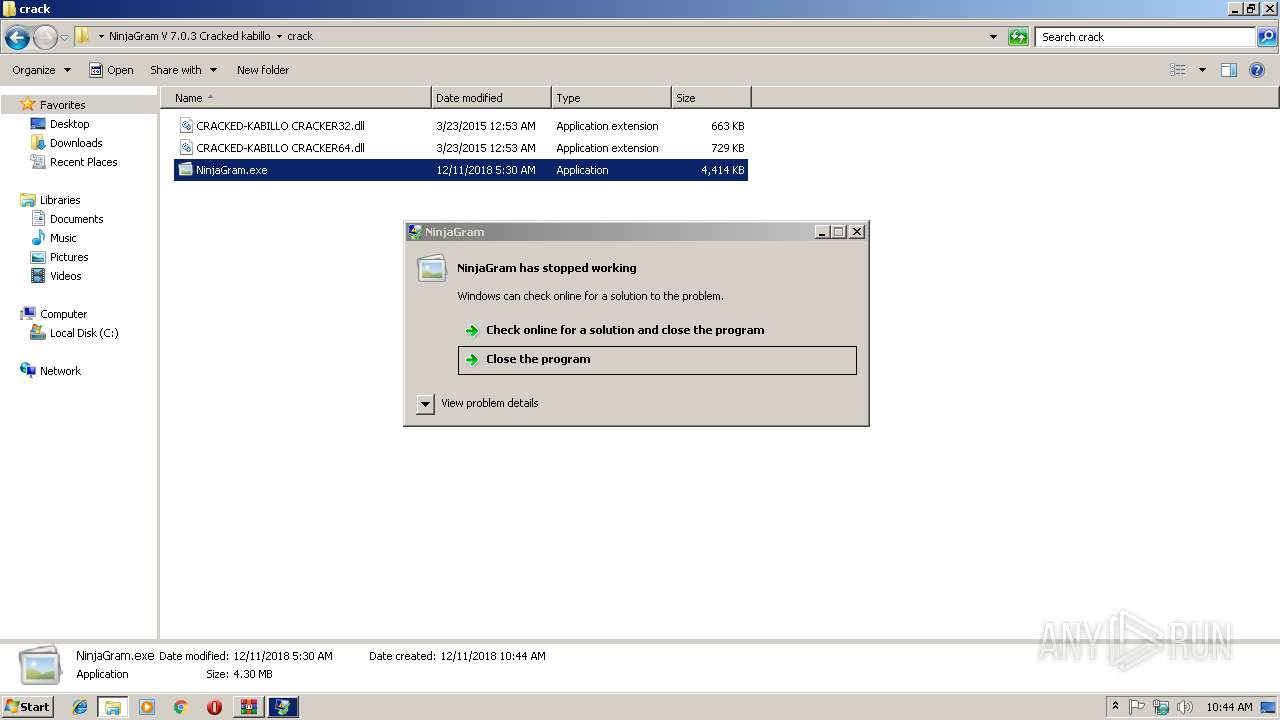
Application was crashed
- NinjaGram.exe (PID: 2952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
39
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 996 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2952 | "C:\Users\admin\AppData\Local\Temp\3582-490\NinjaGram.exe" | C:\Users\admin\AppData\Local\Temp\3582-490\NinjaGram.exe | NinjaGram.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: NinjaGram Exit code: 0 Version: 7.0.3.0 Modules
| |||||||||||||||
| 2968 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\NinjaGram V 7.0.3 Cracked kabillo.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
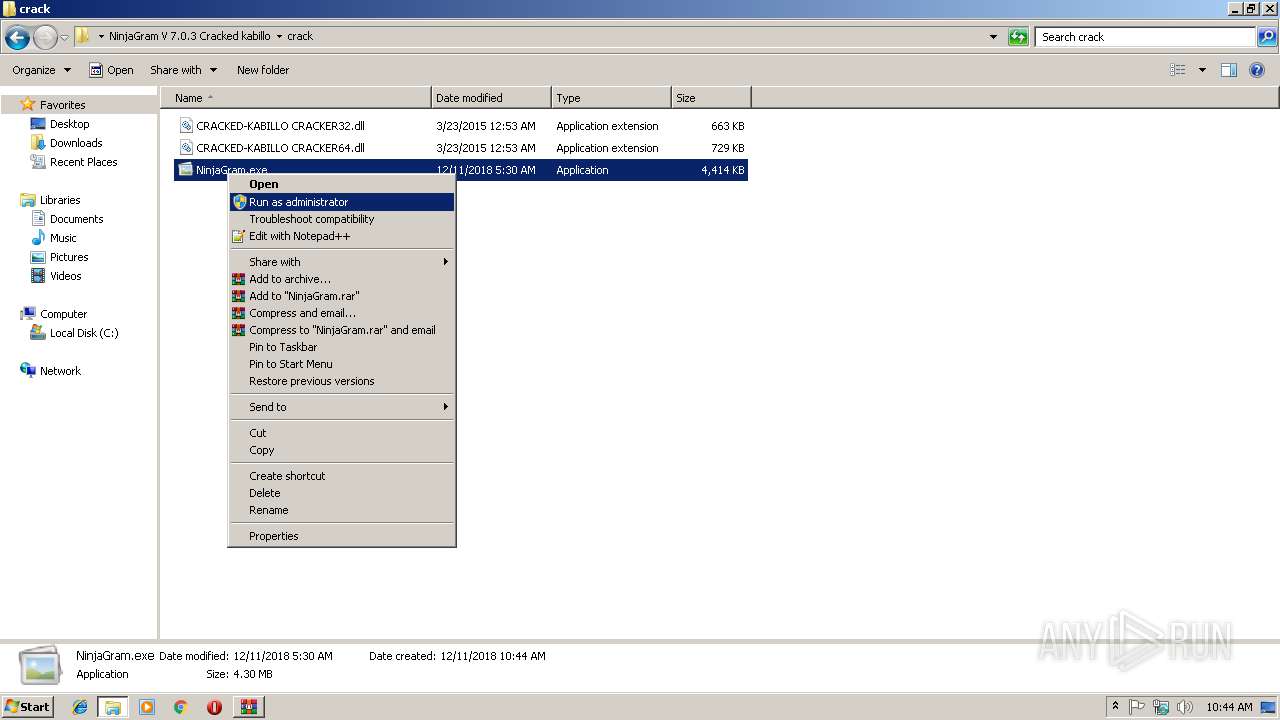
| 3892 | "C:\Users\admin\Desktop\NinjaGram V 7.0.3 Cracked kabillo\crack\NinjaGram.exe" | C:\Users\admin\Desktop\NinjaGram V 7.0.3 Cracked kabillo\crack\NinjaGram.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
1 114
Read events
1 097
Write events
17
Delete events
0
Modification events
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\NinjaGram V 7.0.3 Cracked kabillo.rar | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3892) NinjaGram.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3892) NinjaGram.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
12
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3892 | NinjaGram.exe | C:\Users\admin\AppData\Local\Temp\3582-490\NinjaGram.exe | executable | |
MD5:— | SHA256:— | |||
| 2968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2968.5635\NinjaGram V 7.0.3 Cracked kabillo\crack\NinjaGram.exe | executable | |
MD5:— | SHA256:— | |||
| 3892 | NinjaGram.exe | C:\ProgramData\Package Cache\{7e9fae12-5bbf-47fb-b944-09c49e75c061}\VC_redist.x86.exe | executable | |
MD5:— | SHA256:— | |||
| 3892 | NinjaGram.exe | C:\MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\DW20.EXE | executable | |
MD5:02EE6A3424782531461FB2F10713D3C1 | SHA256:EAD58C483CB20BCD57464F8A4929079539D634F469B213054BF737D227C026DC | |||
| 3892 | NinjaGram.exe | C:\MSOCache\All Users\{90140000-003D-0000-0000-0000000FF1CE}-C\setup.exe | executable | |
MD5:566ED4F62FDC96F175AFEDD811FA0370 | SHA256:E17CD94C08FC0E001A49F43A0801CEA4625FB9AEE211B6DFEBEBEC446C21F460 | |||
| 3892 | NinjaGram.exe | C:\ProgramData\Package Cache\{f65db027-aff3-4070-886a-0d87064aabb1}\vcredist_x86.exe | executable | |
MD5:4B27661E864382B71FFD26D67125A9D0 | SHA256:78E085875002746CBC6F4AF5DC7D15157409FE94B23D89FC1BD58E9E1242302B | |||
| 2968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2968.5635\NinjaGram V 7.0.3 Cracked kabillo\crack\CRACKED-KABILLO CRACKER64.dll | executable | |
MD5:08DFAD3A22E42E17A3BF8F4EE43A67F5 | SHA256:B3710DE17D2C2F84DEF83C8F3093DF0DBE1664F34AB4A3ADB72F1085E71C773C | |||
| 3892 | NinjaGram.exe | C:\Windows\svchost.com | executable | |
MD5:— | SHA256:— | |||
| 2968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2968.5635\NinjaGram V 7.0.3 Cracked kabillo\crack\CRACKED-KABILLO CRACKER32.dll | executable | |
MD5:7D723A8EB4D7E494EA488C13510B97B6 | SHA256:B695AC865A5DF23E45FF991BF26B71E4F879C89A1A6FDE0BA92F31904BEACA5C | |||
| 3892 | NinjaGram.exe | C:\Users\admin\AppData\Local\Temp\tmp5023.tmp | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report