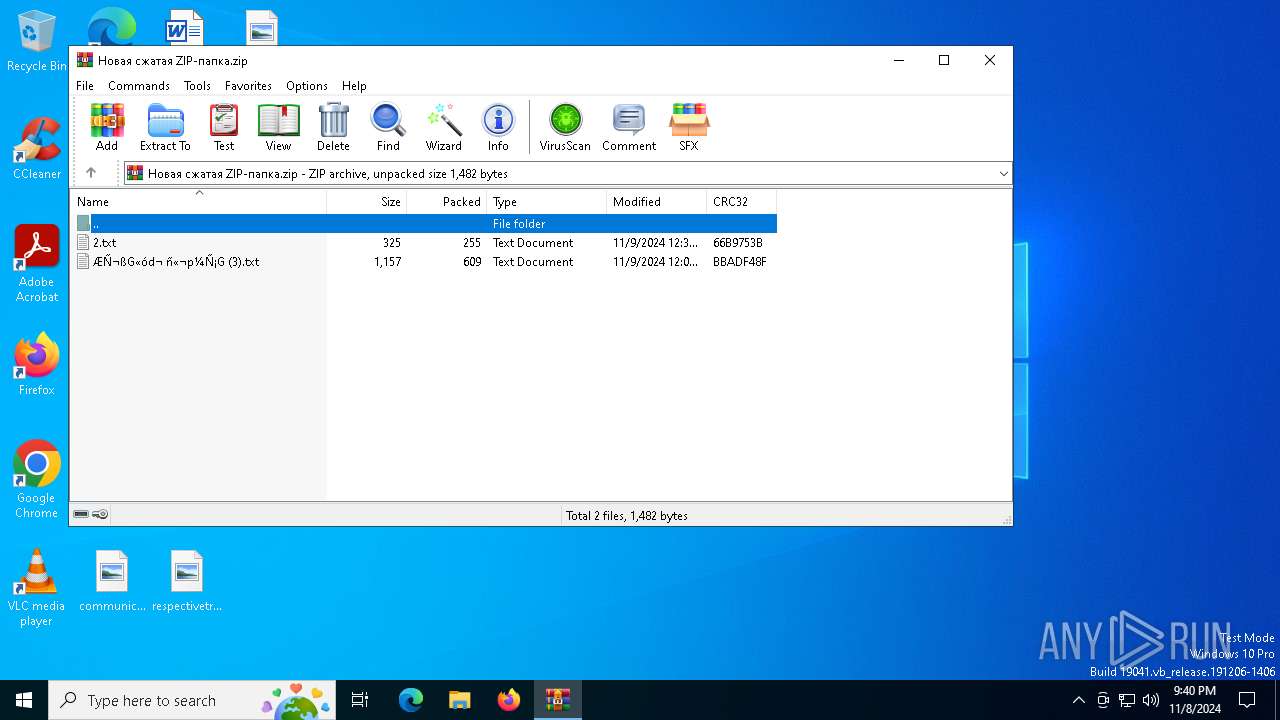
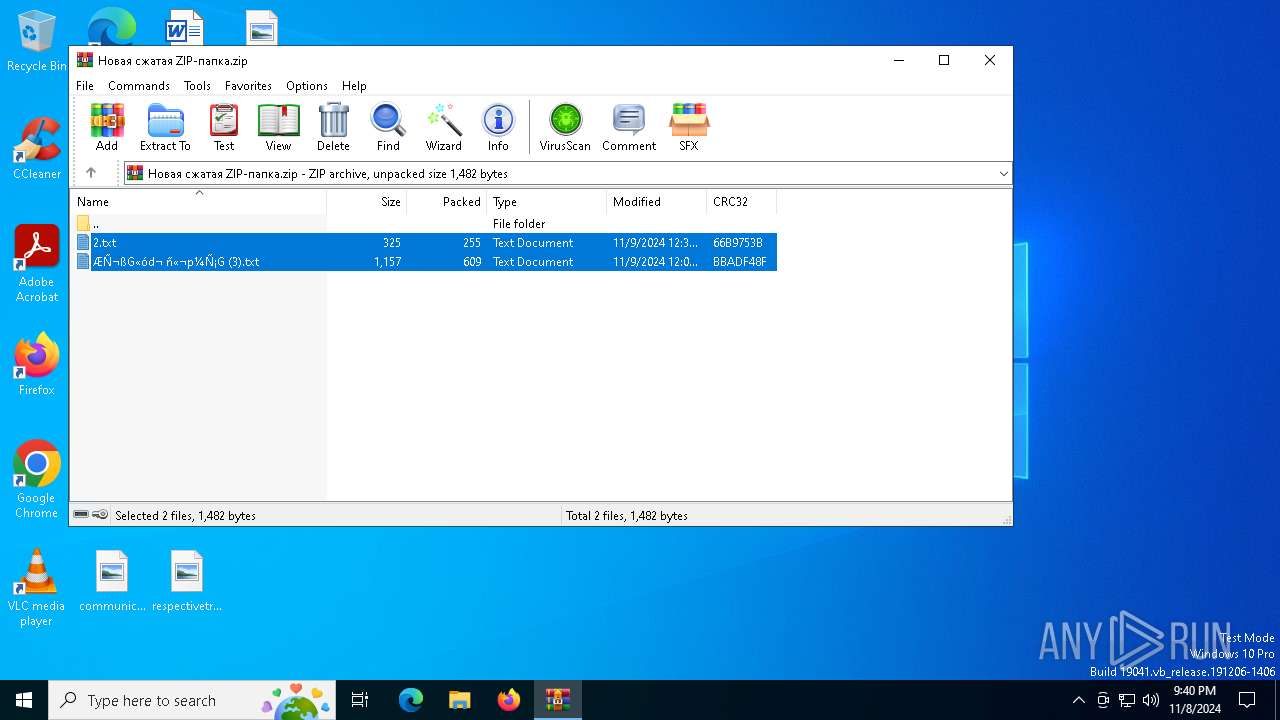
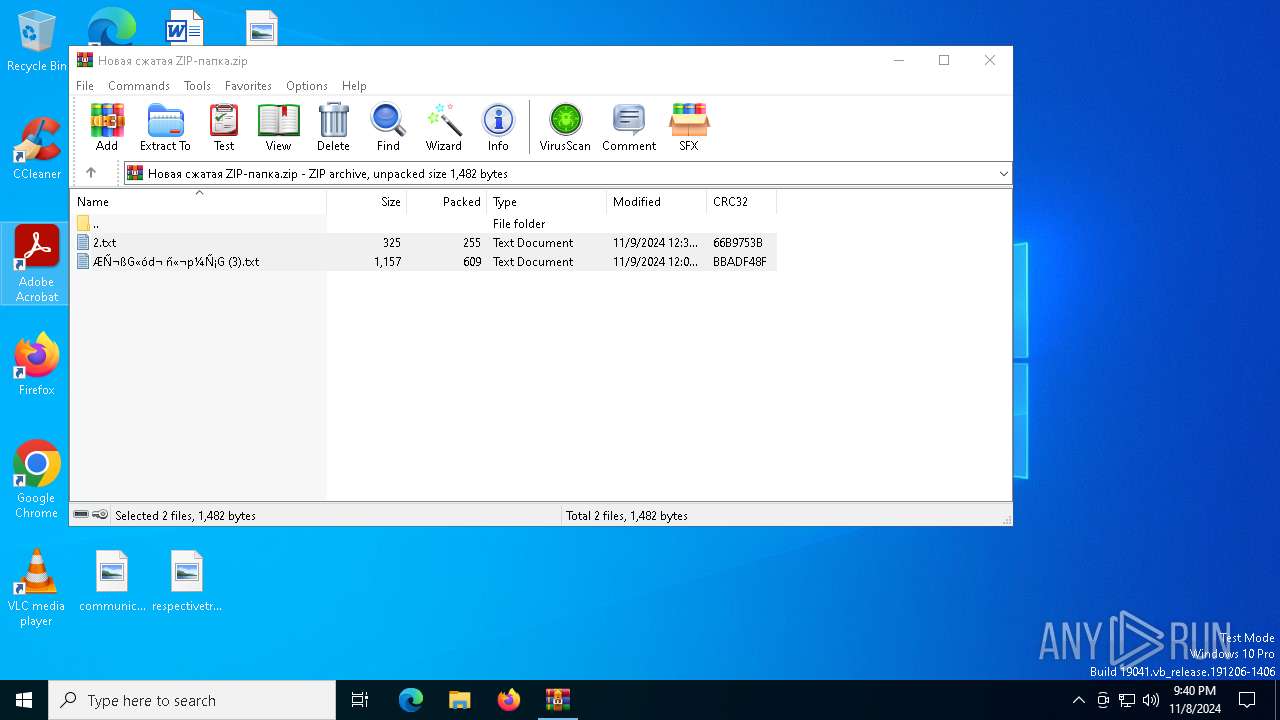
| File name: | Новая сжатая ZIP-папка.zip |
| Full analysis: | https://app.any.run/tasks/89bf32af-7242-4a9f-ae89-59107c17c8d3 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2024, 21:40:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 4E3C574EF3DE68021062D5F22564A859 |
| SHA1: | 80C7D4A351EDC915FF585FA10860ABF2CA6CBEC0 |
| SHA256: | DC334DF203CF3CC22AD64C2A389039029B20A8825AC8EFC537984D8EB6C24D86 |
| SSDEEP: | 24:9AjhiYV4ysYT9u6GFNVBgLHgzABrQli/uoSM3NHJVhEupaRyakjhm:9ShXsdBwLHgEBrQJoT3BJVhEiICm |
MALICIOUS
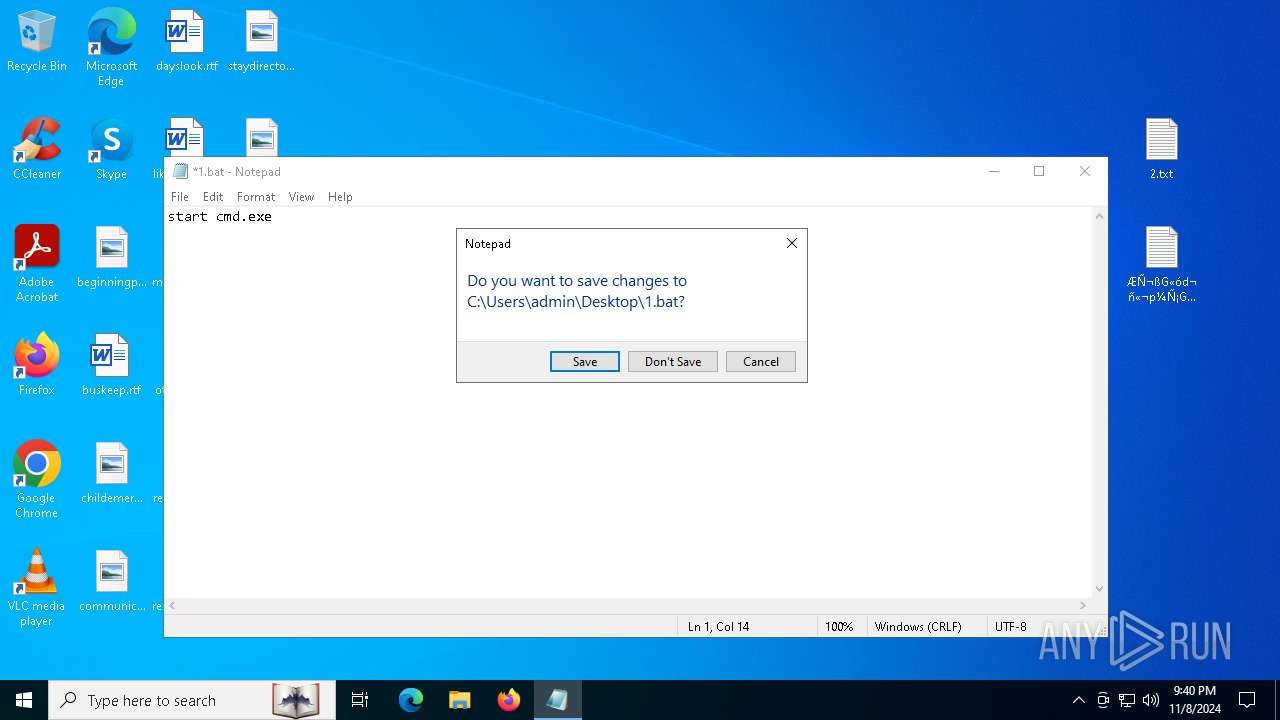
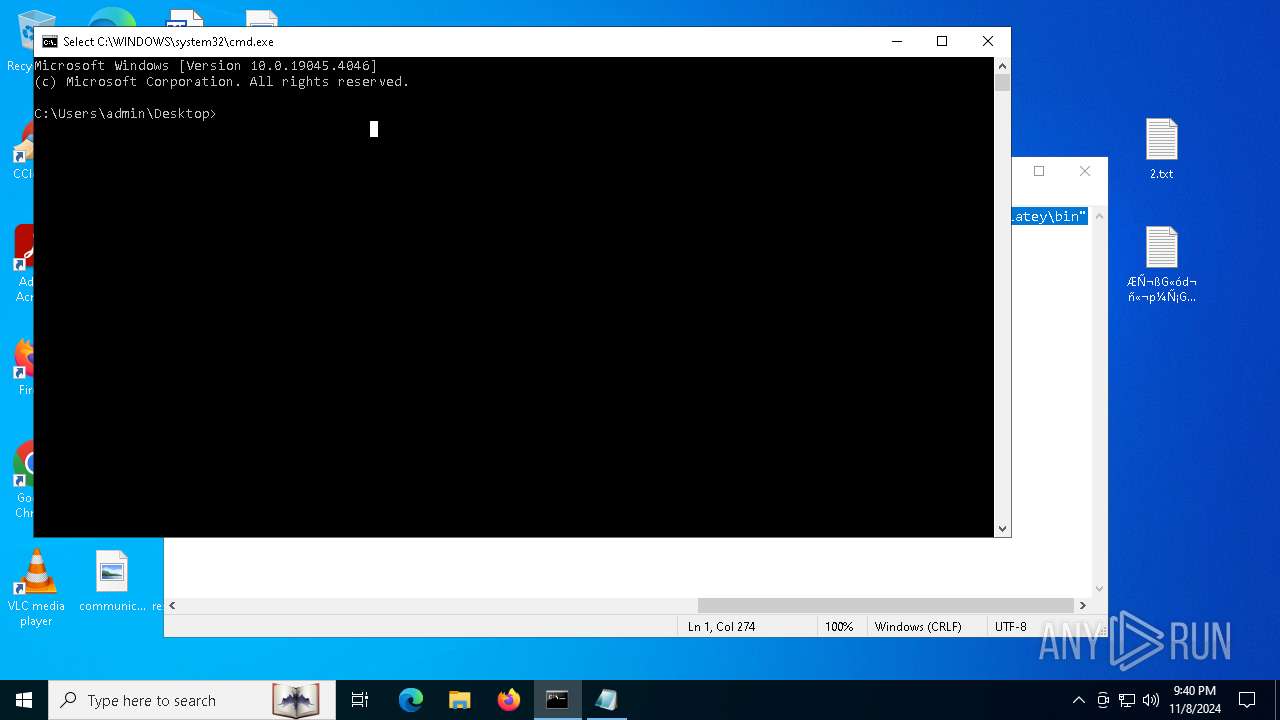
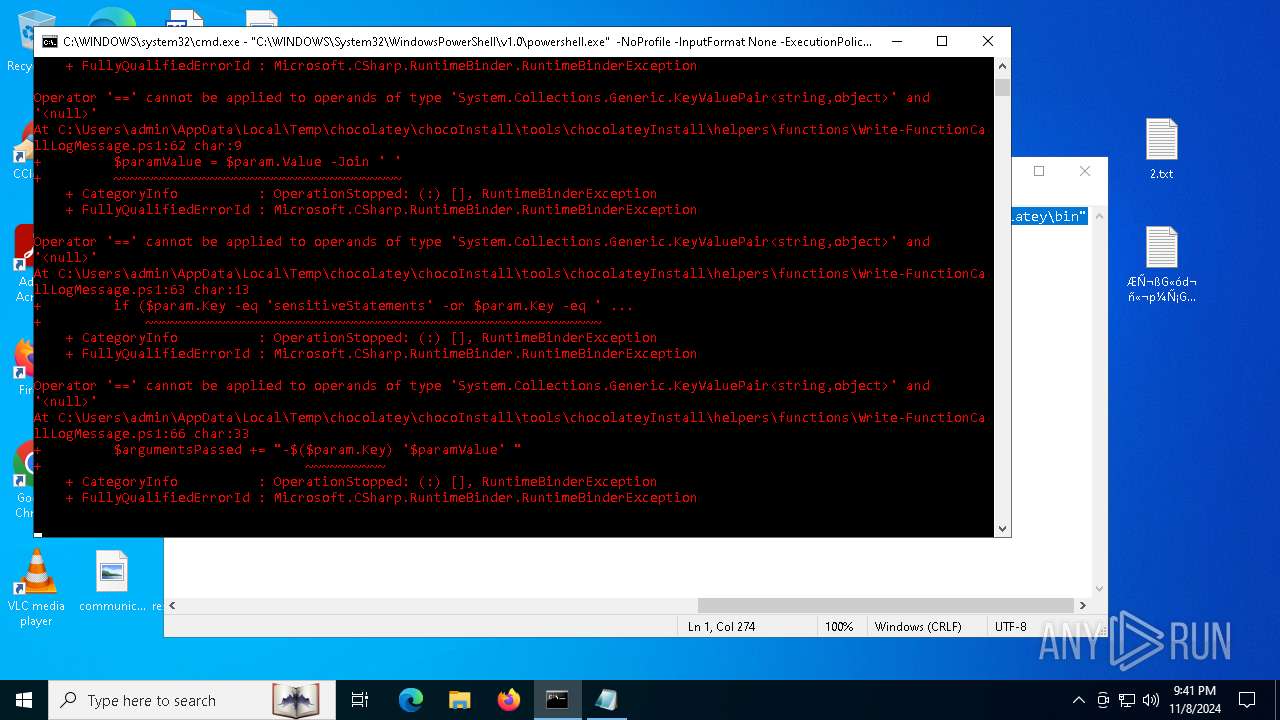
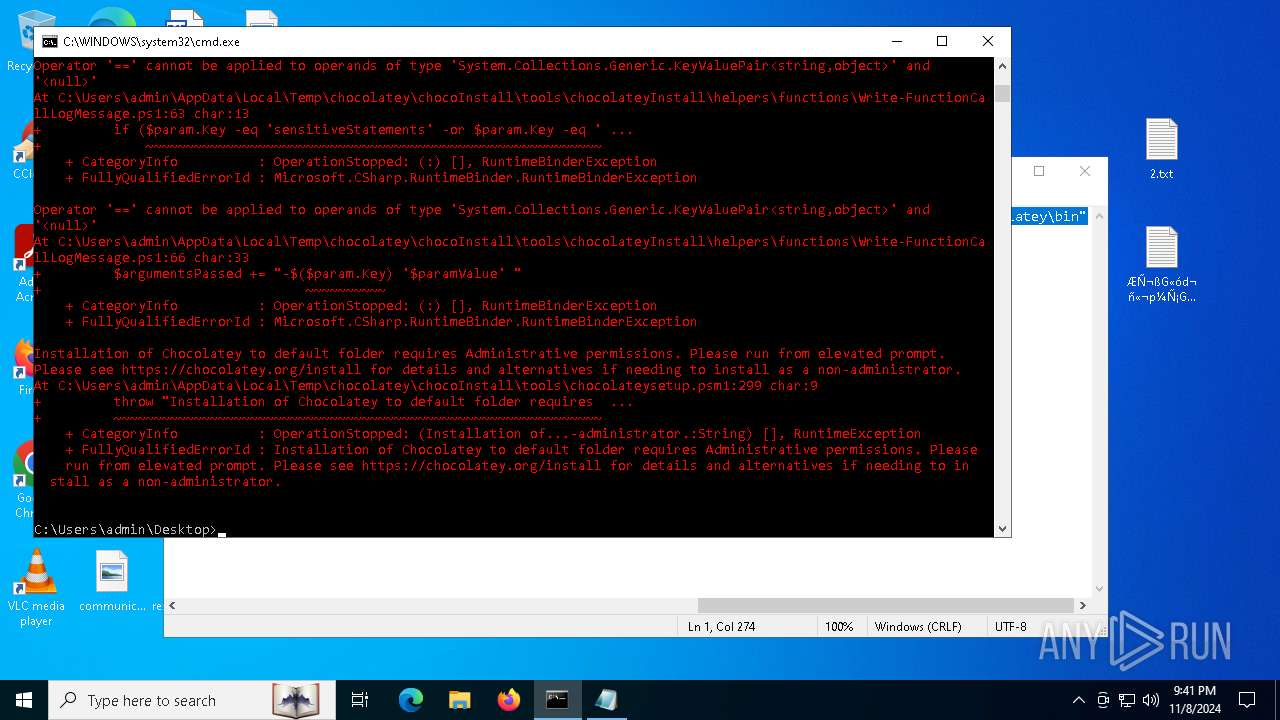
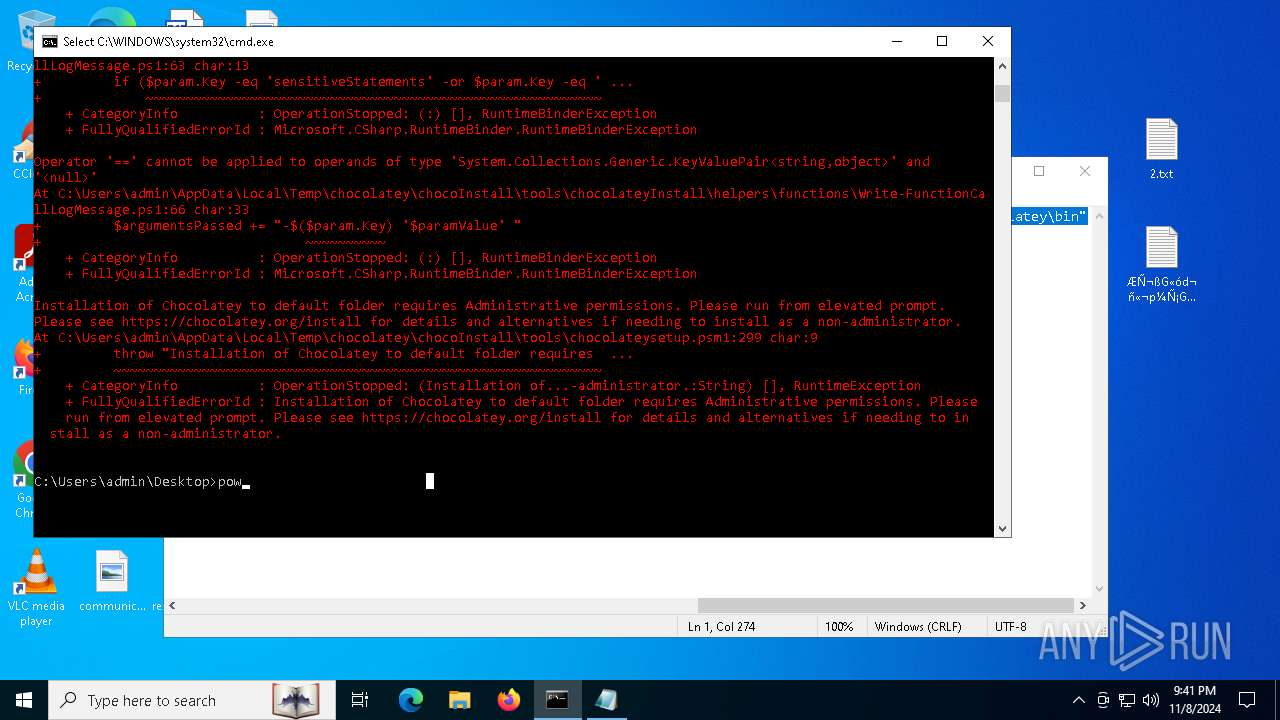
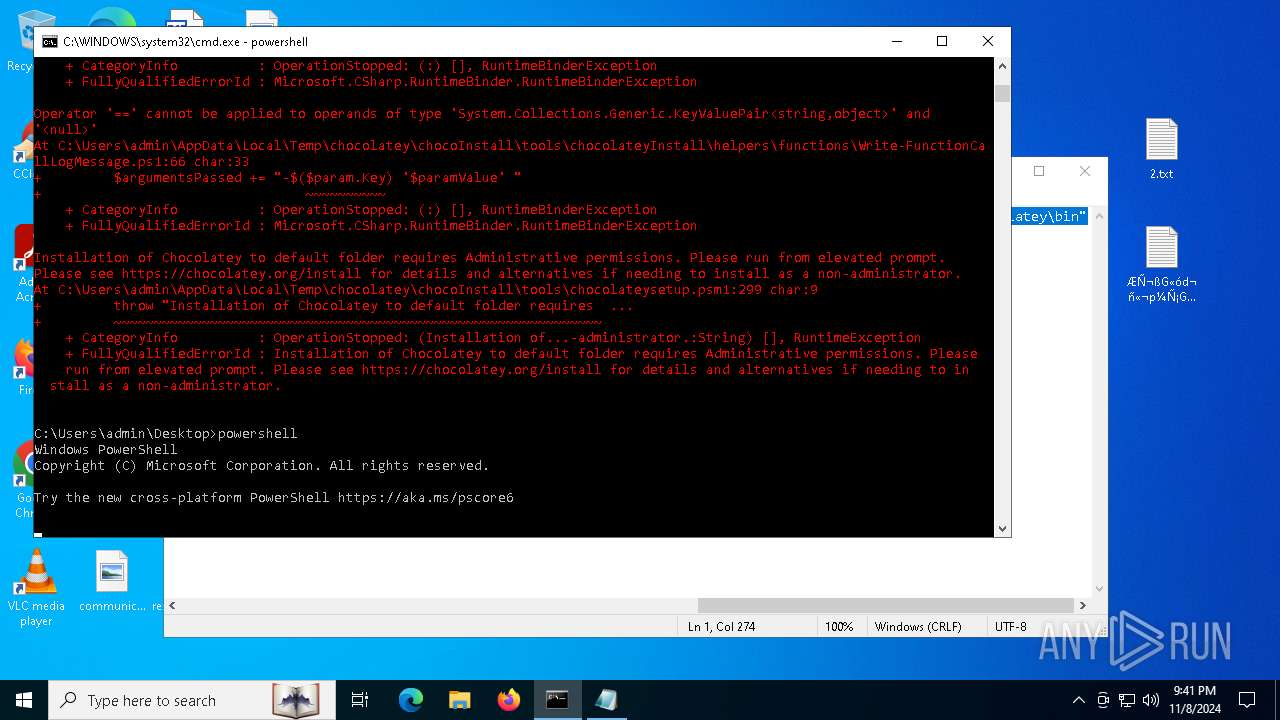
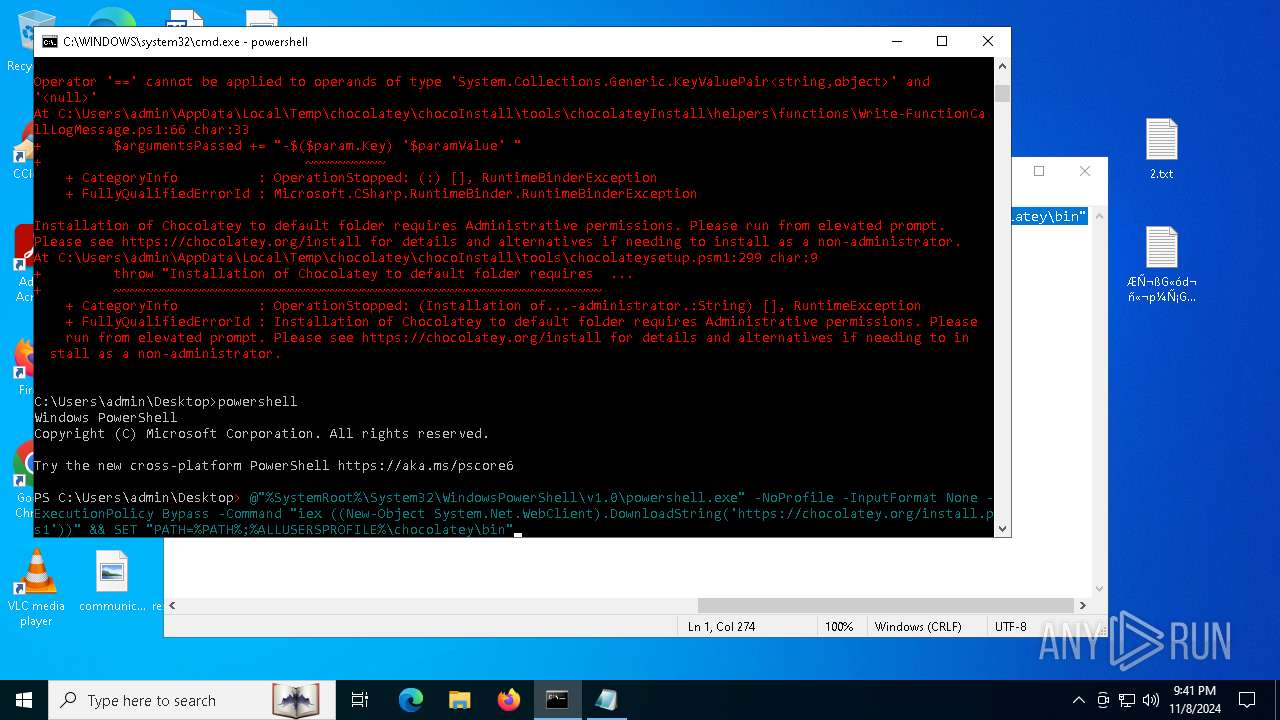
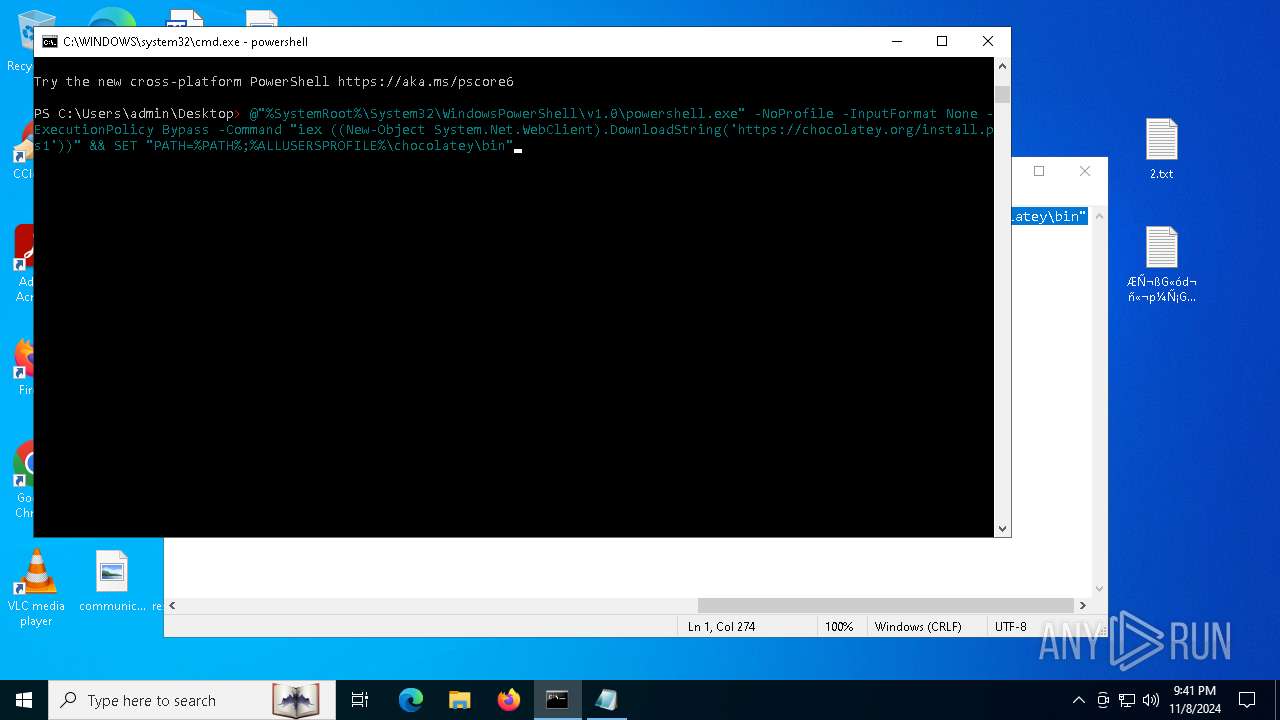
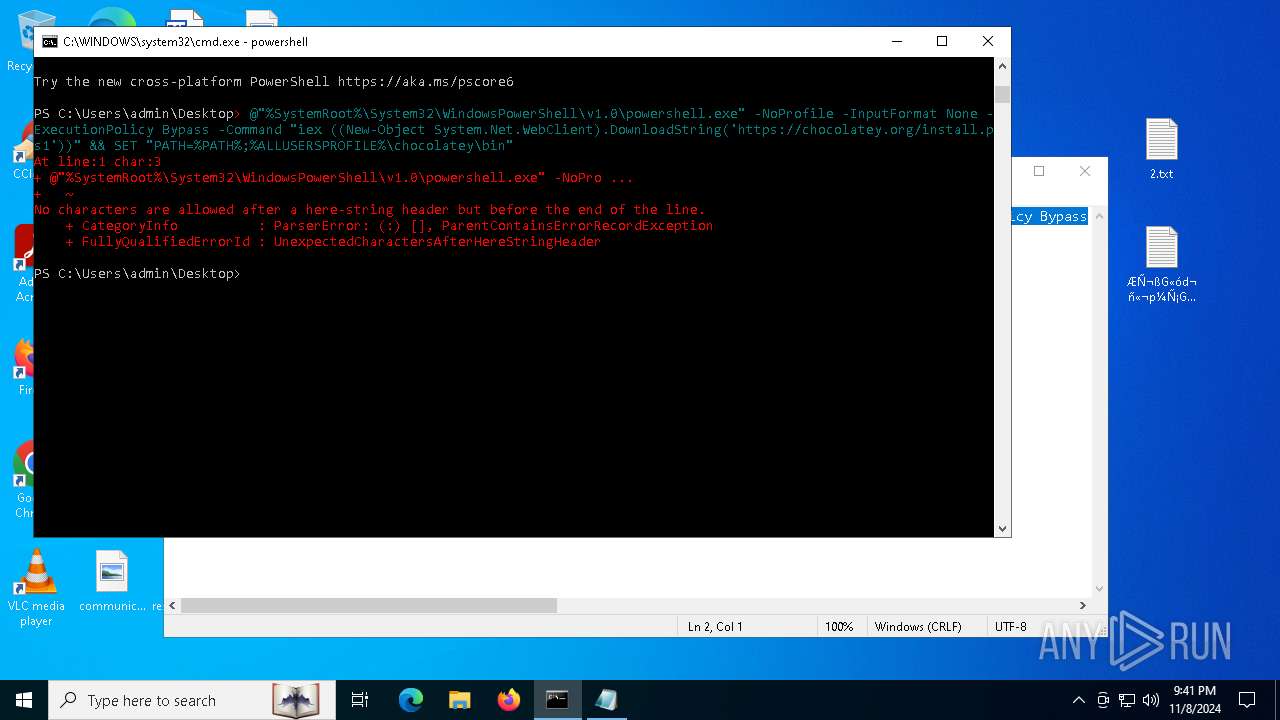
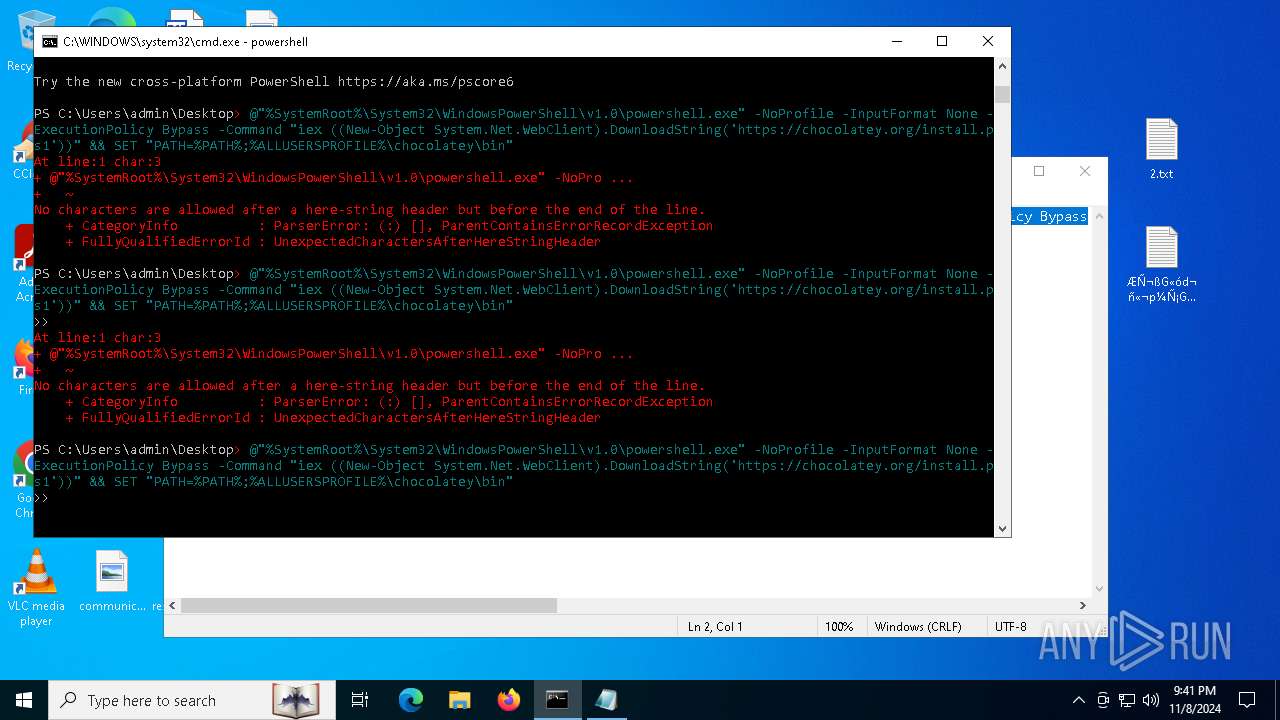
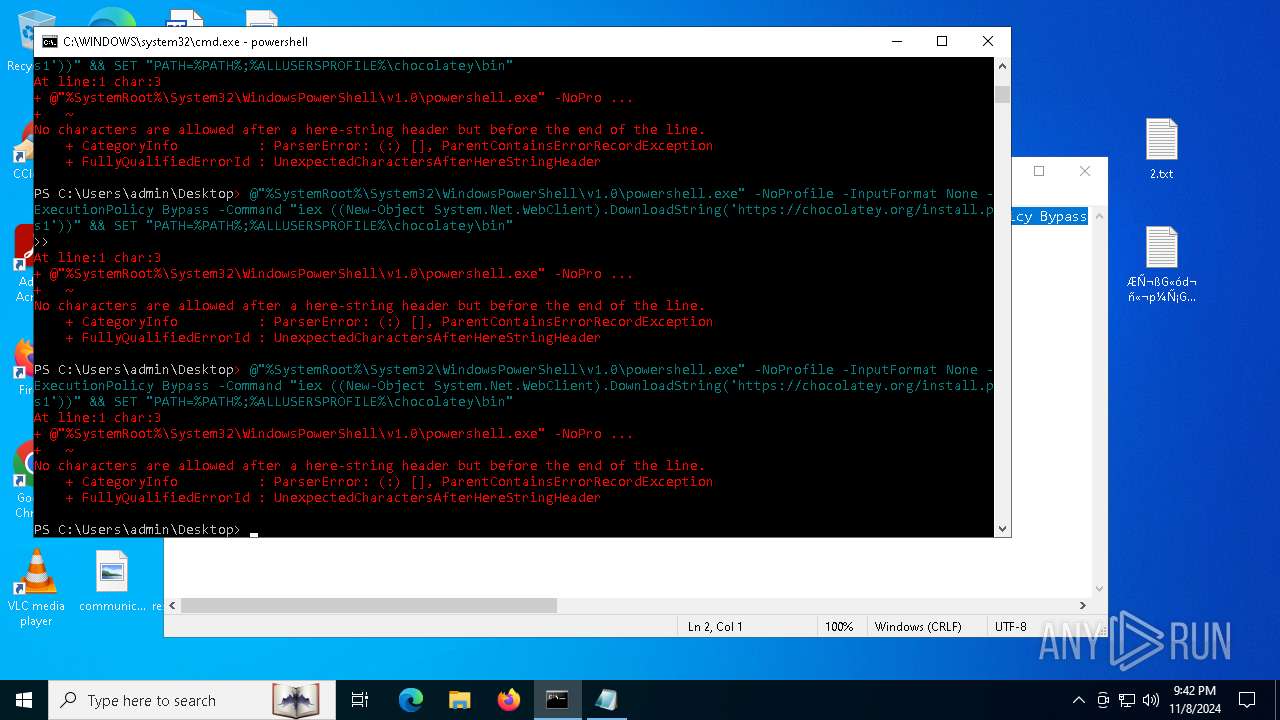
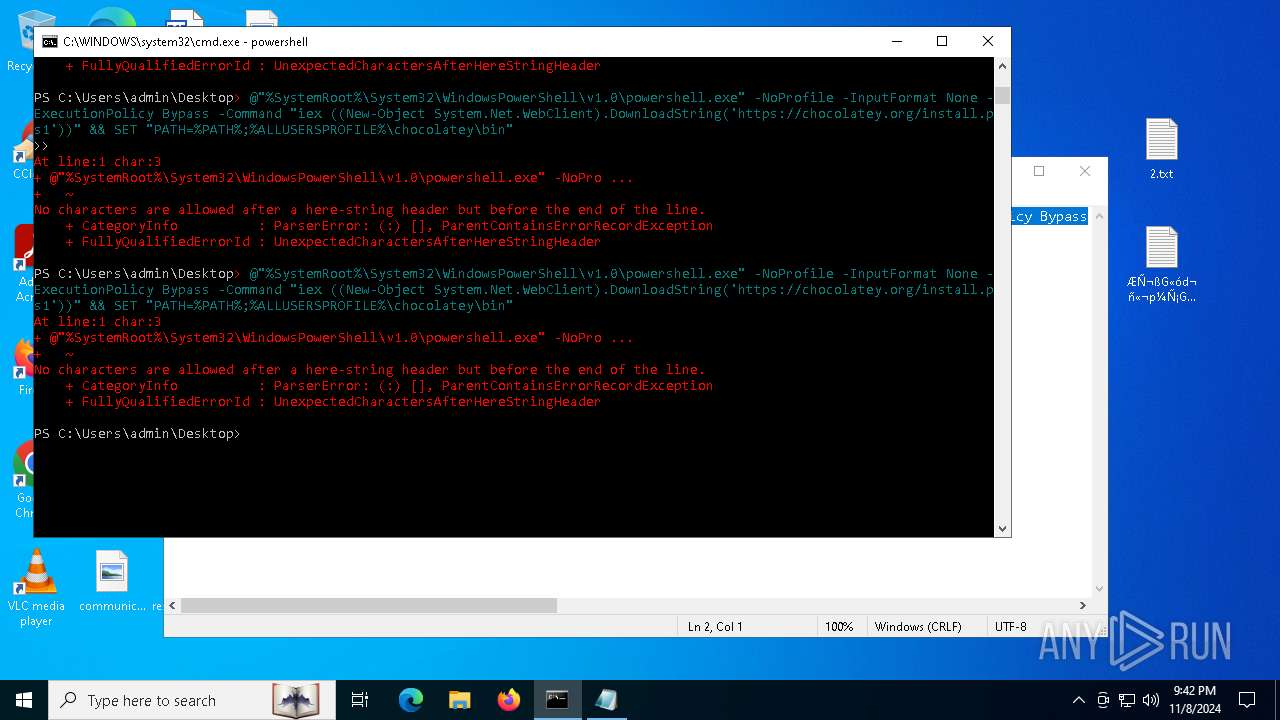
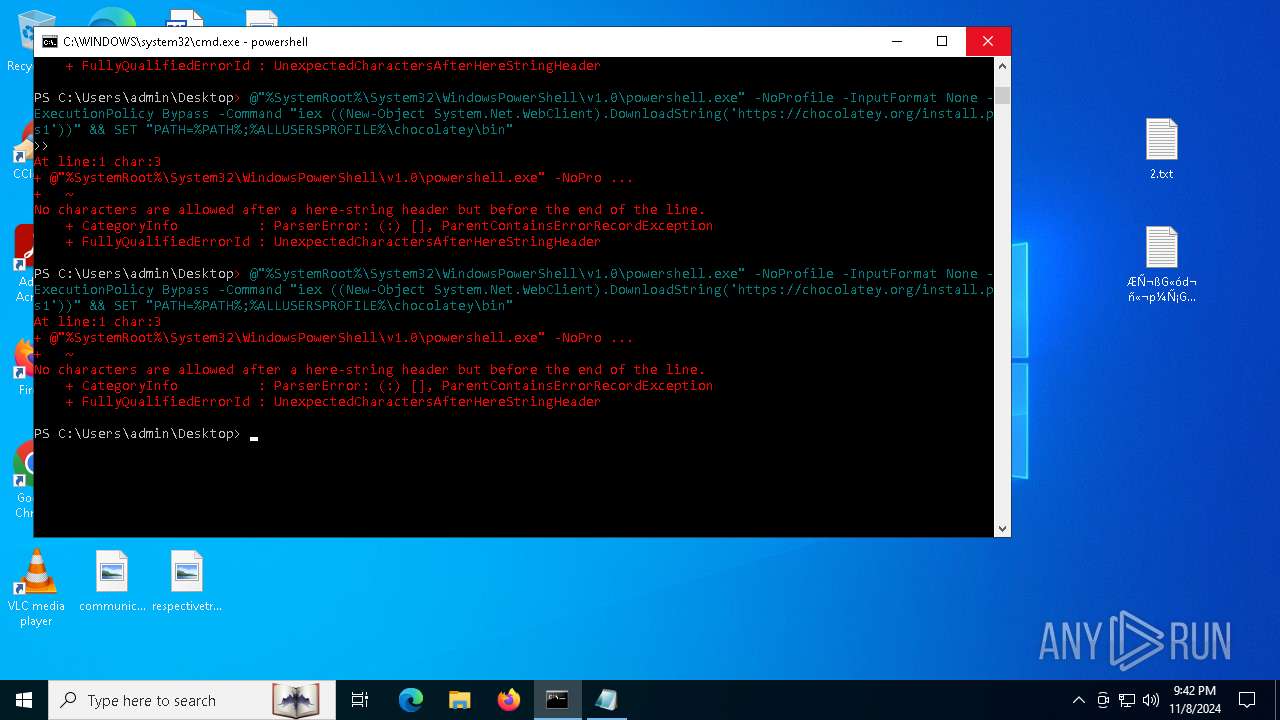
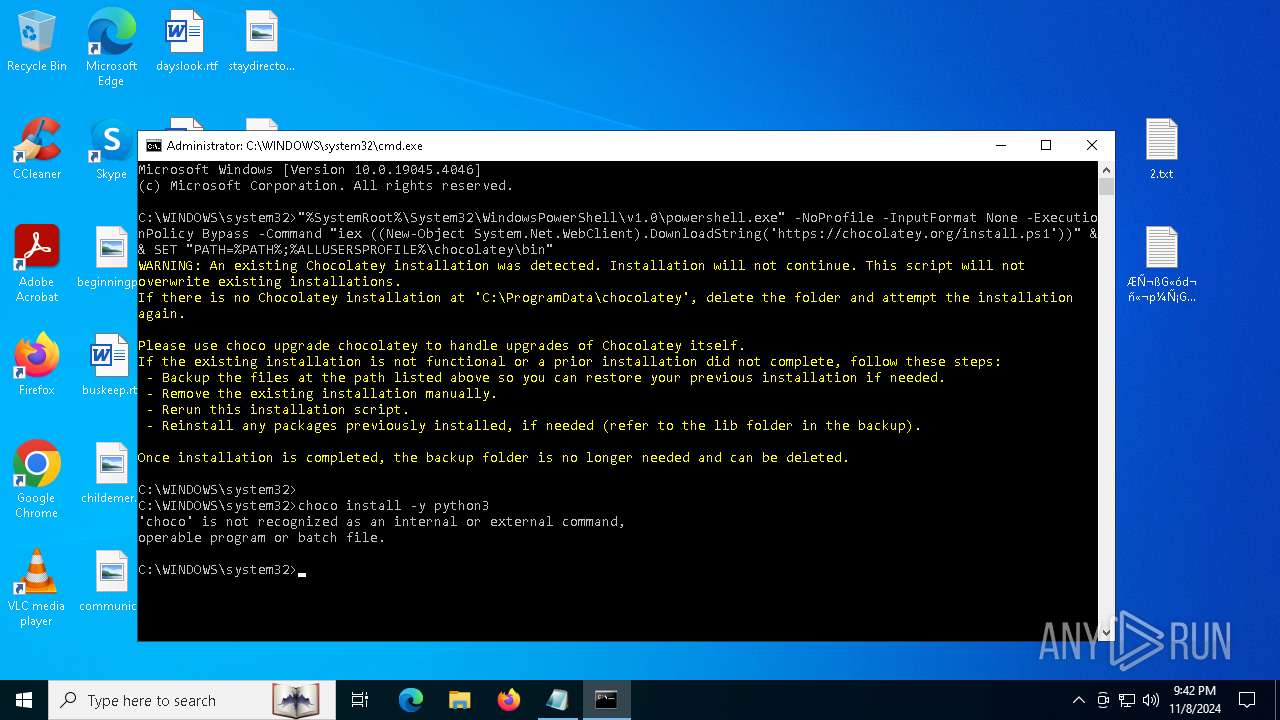
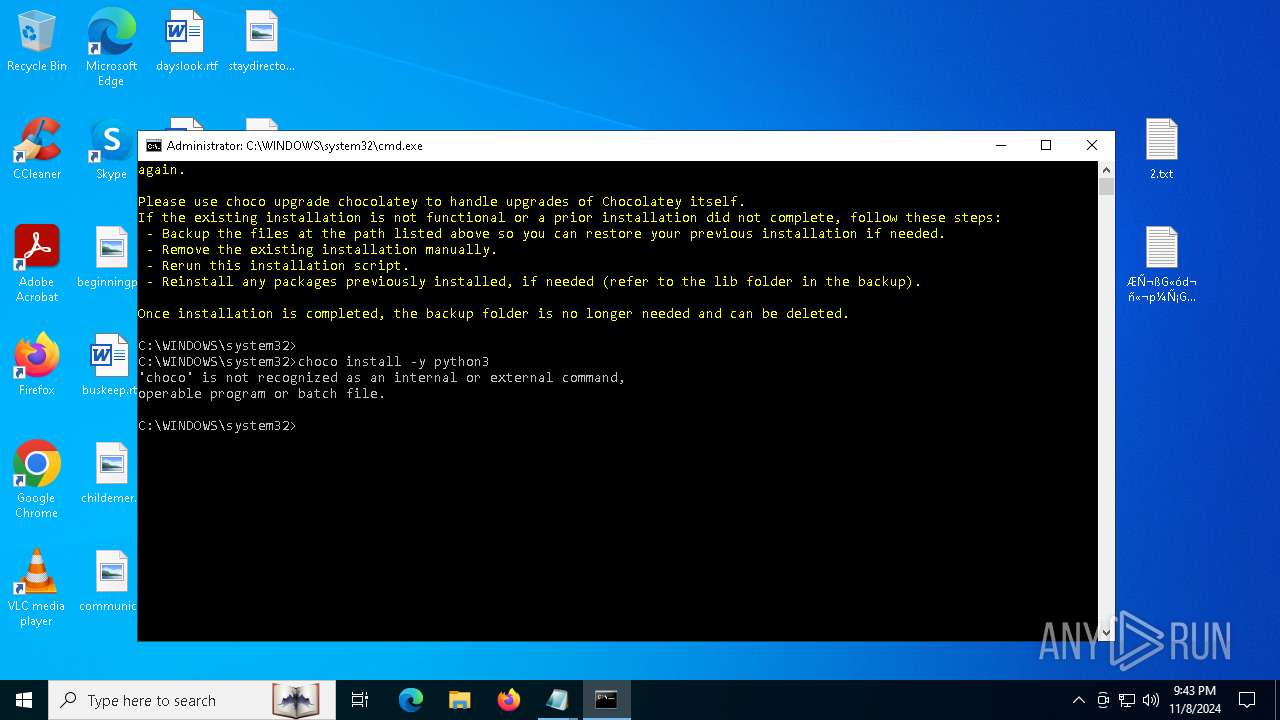
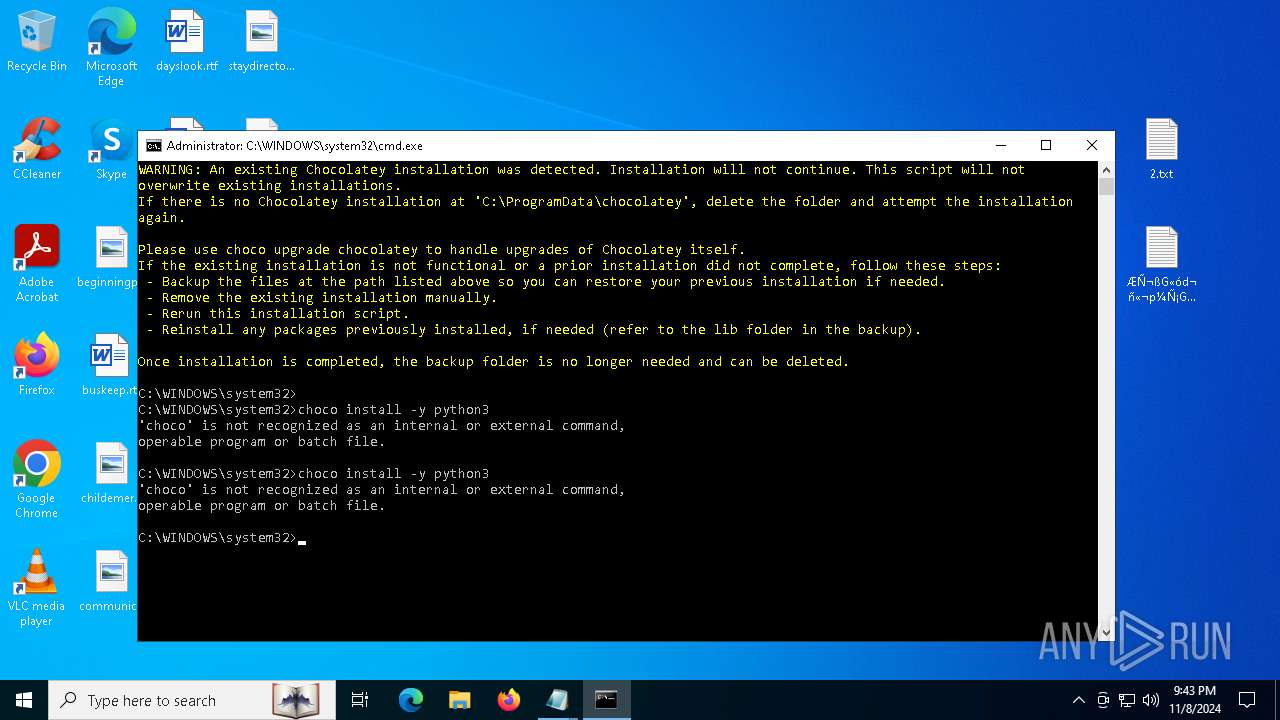
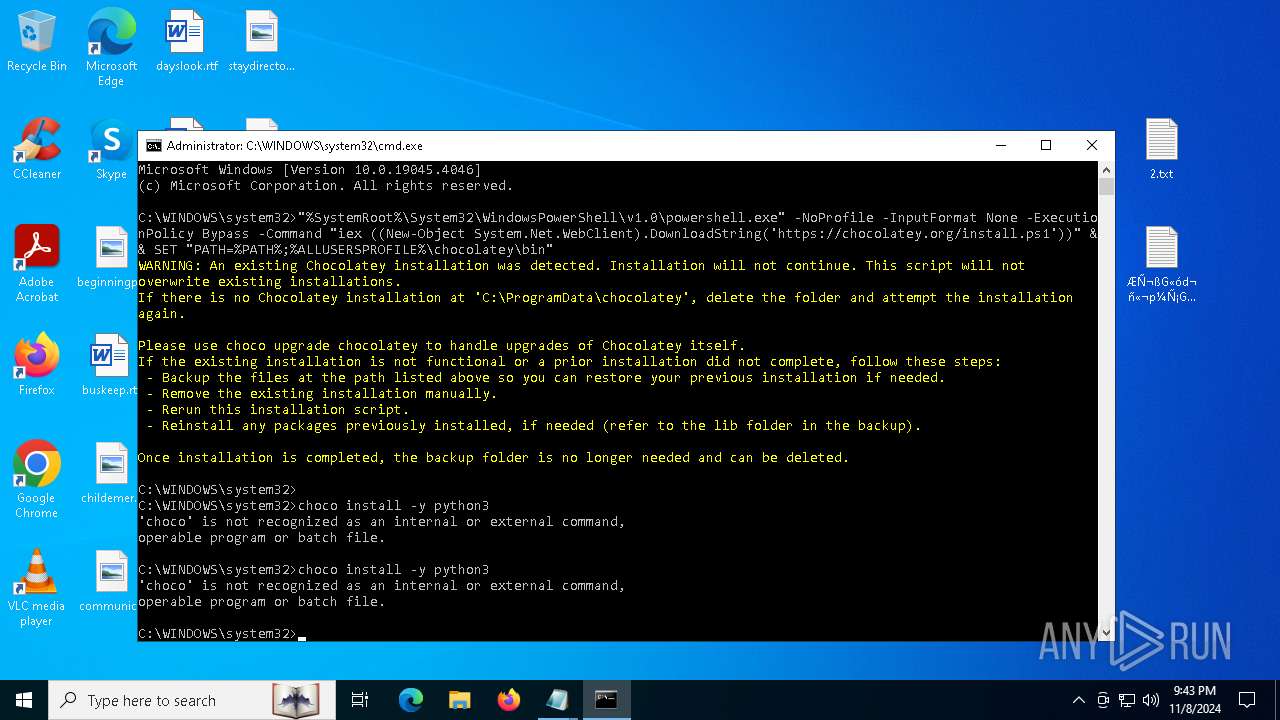
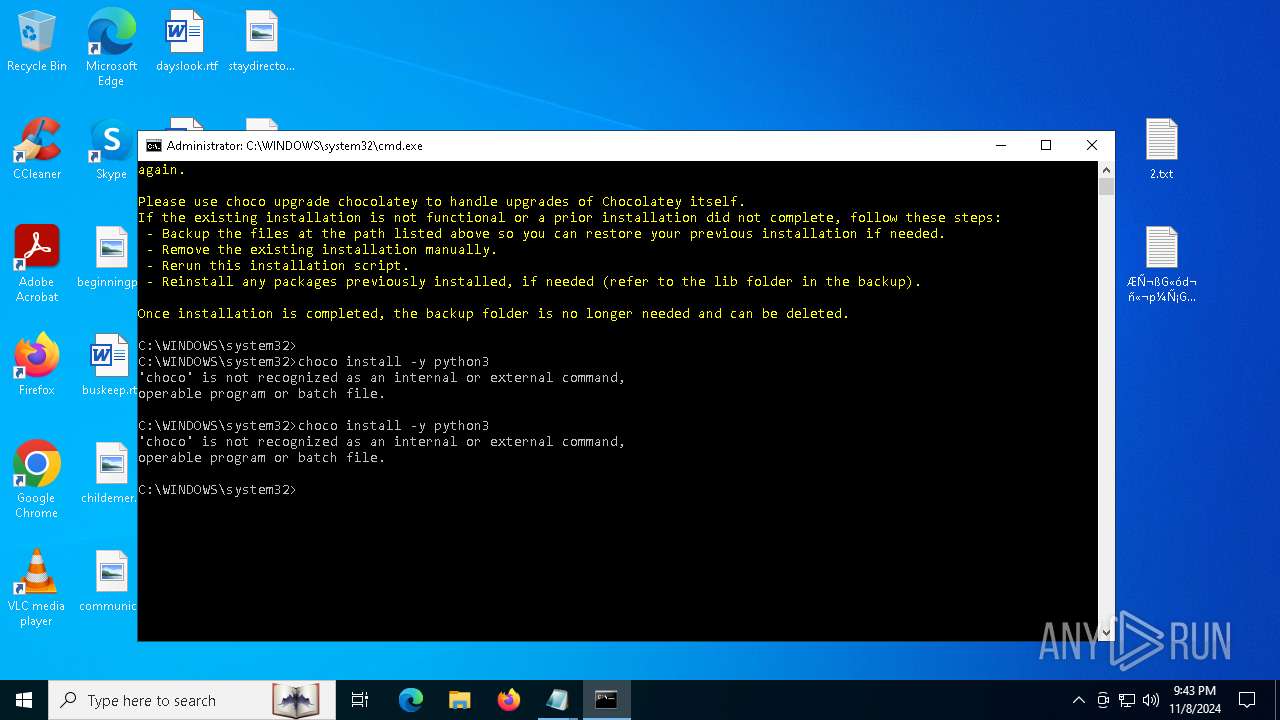
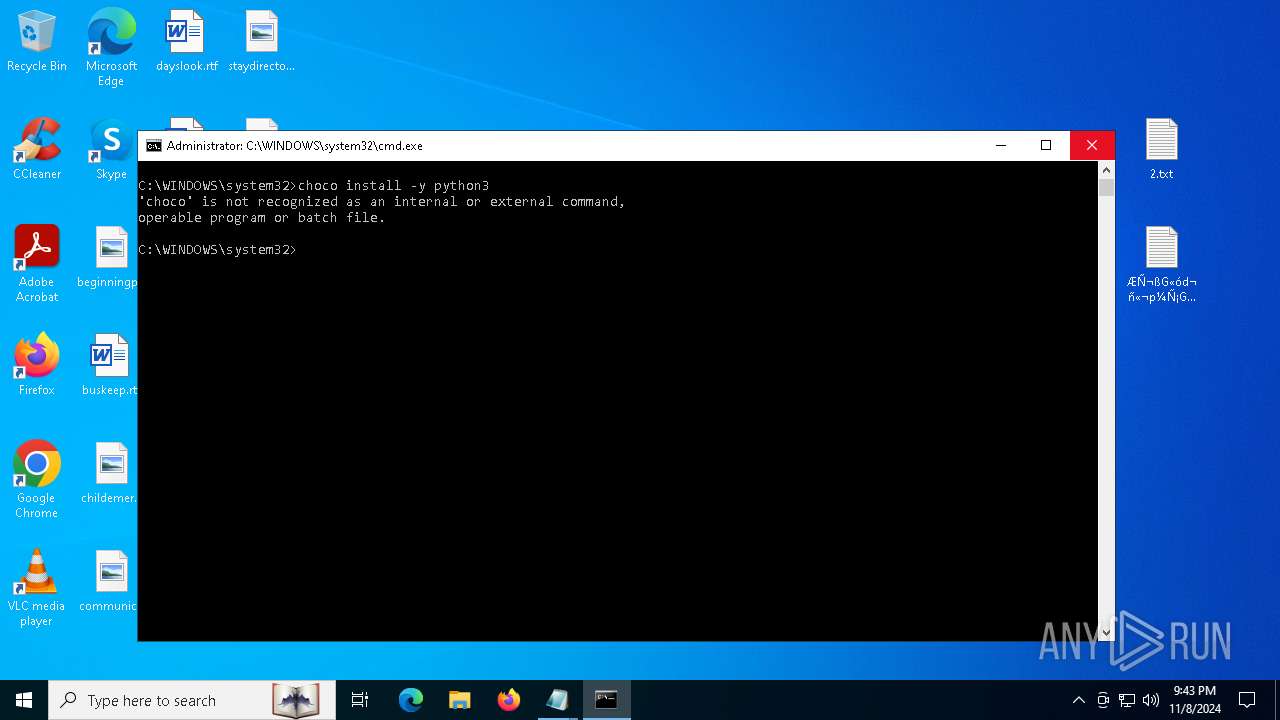
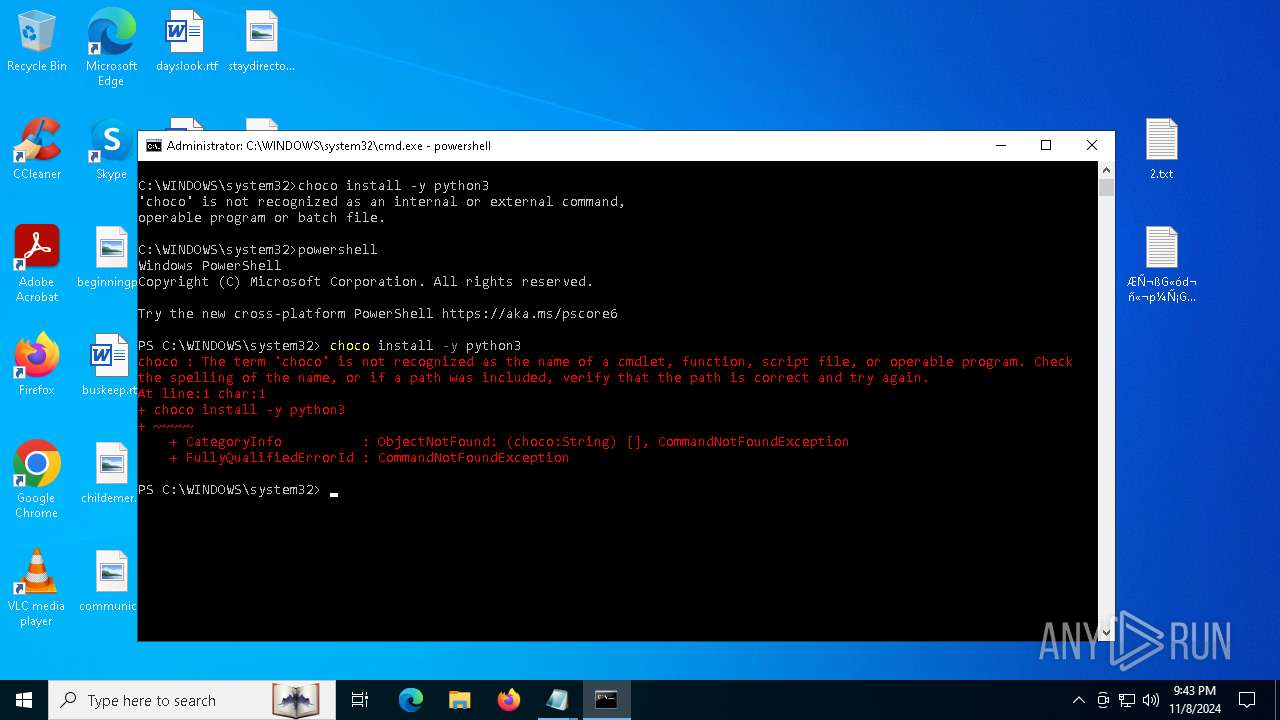
Bypass execution policy to execute commands
- powershell.exe (PID: 5852)
- powershell.exe (PID: 6100)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 6316)
- cmd.exe (PID: 3156)
SUSPICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6436)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6384)
- cmd.exe (PID: 1500)
- cmd.exe (PID: 1028)
Application launched itself
- cmd.exe (PID: 6384)
- cmd.exe (PID: 1500)
- cmd.exe (PID: 1028)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 6316)
- cmd.exe (PID: 3156)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6316)
- cmd.exe (PID: 3156)
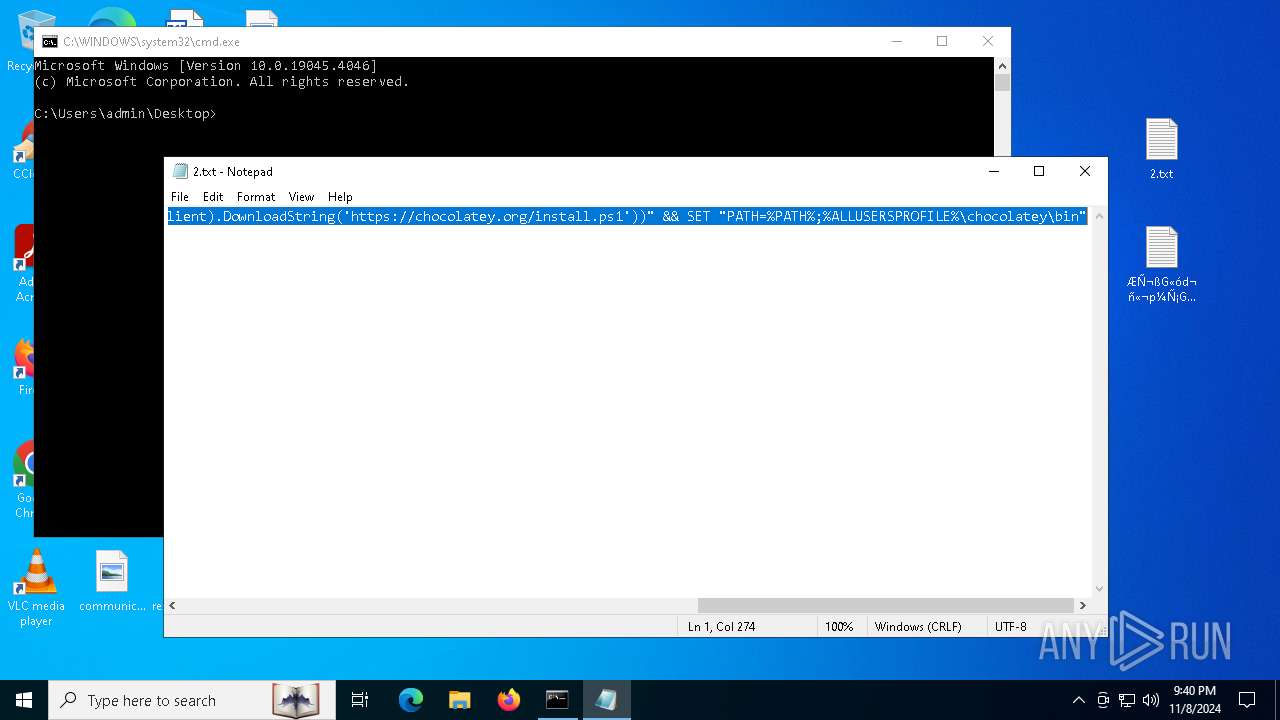
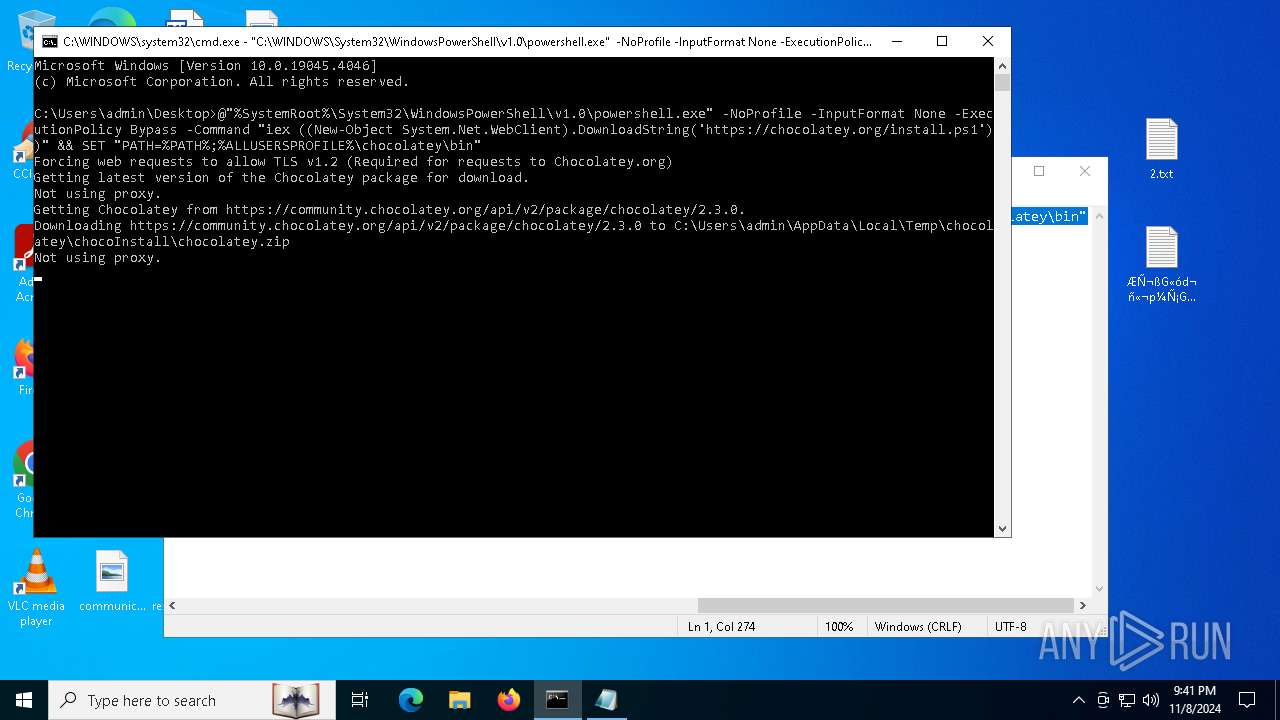
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 6316)
- cmd.exe (PID: 3156)
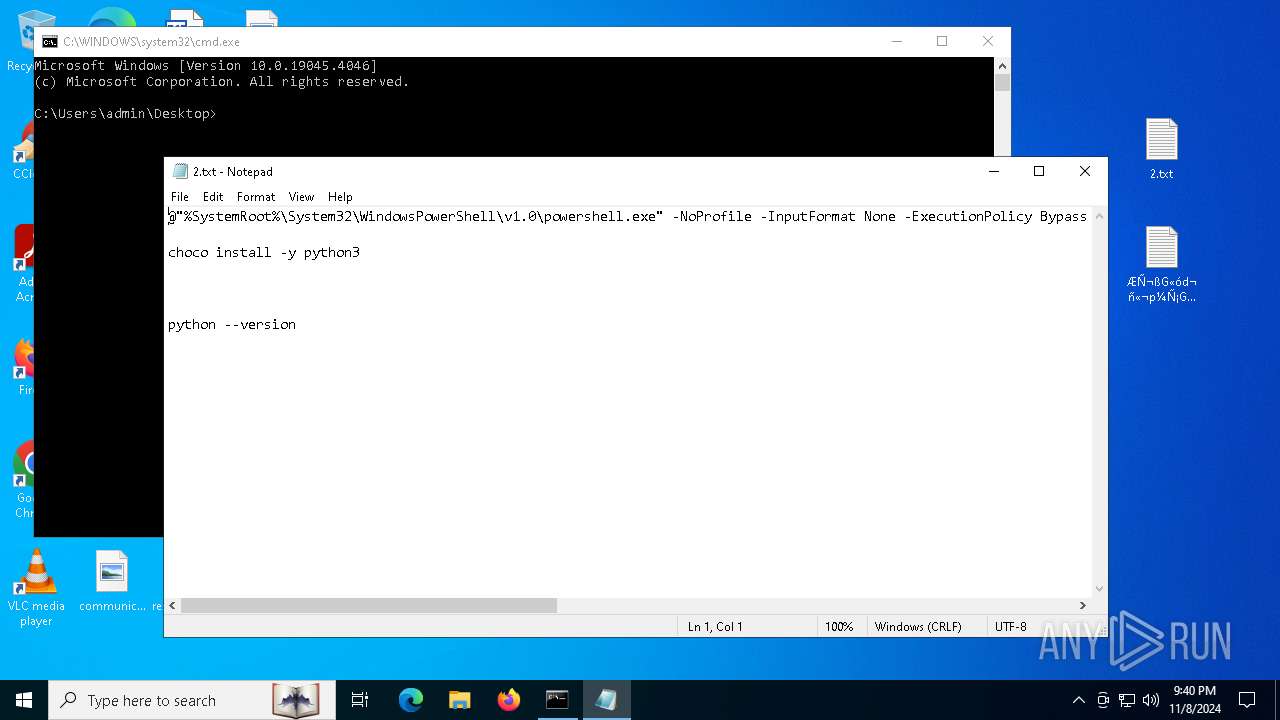
Probably download files using WebClient
- cmd.exe (PID: 6316)
- cmd.exe (PID: 3156)
The process executes Powershell scripts
- cmd.exe (PID: 6316)
- cmd.exe (PID: 3156)
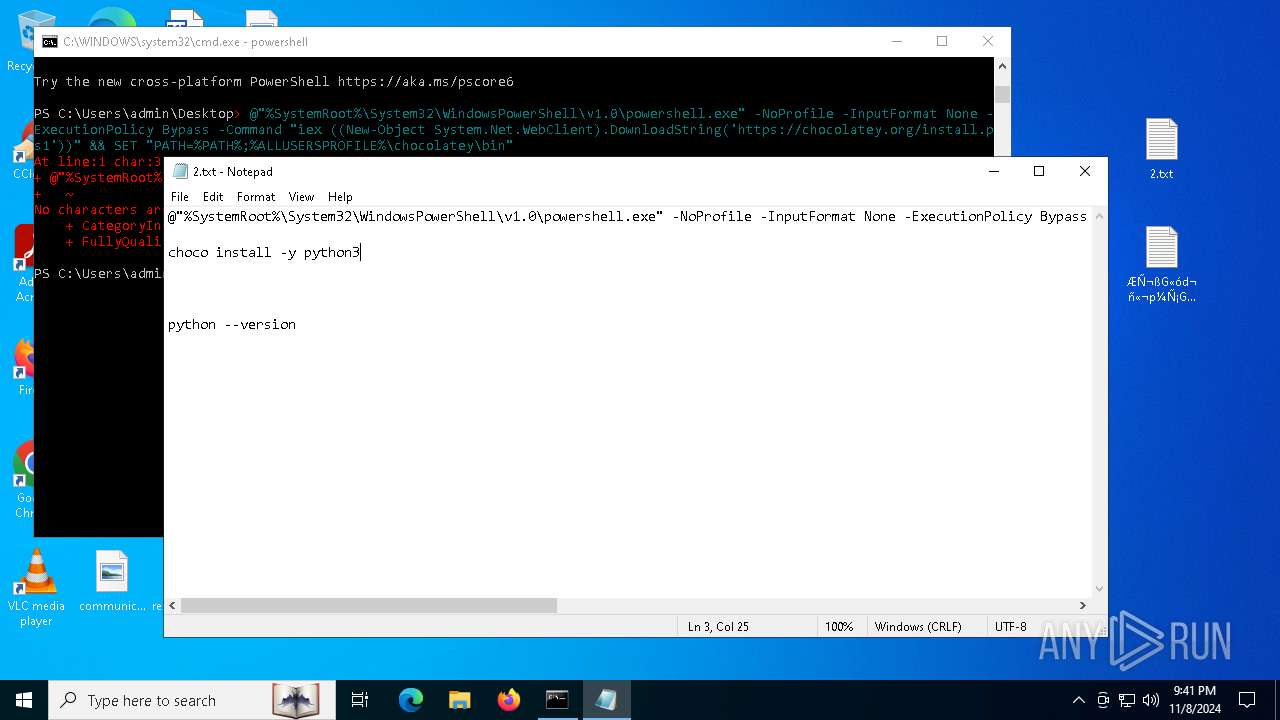
Executable content was dropped or overwritten
- powershell.exe (PID: 5852)
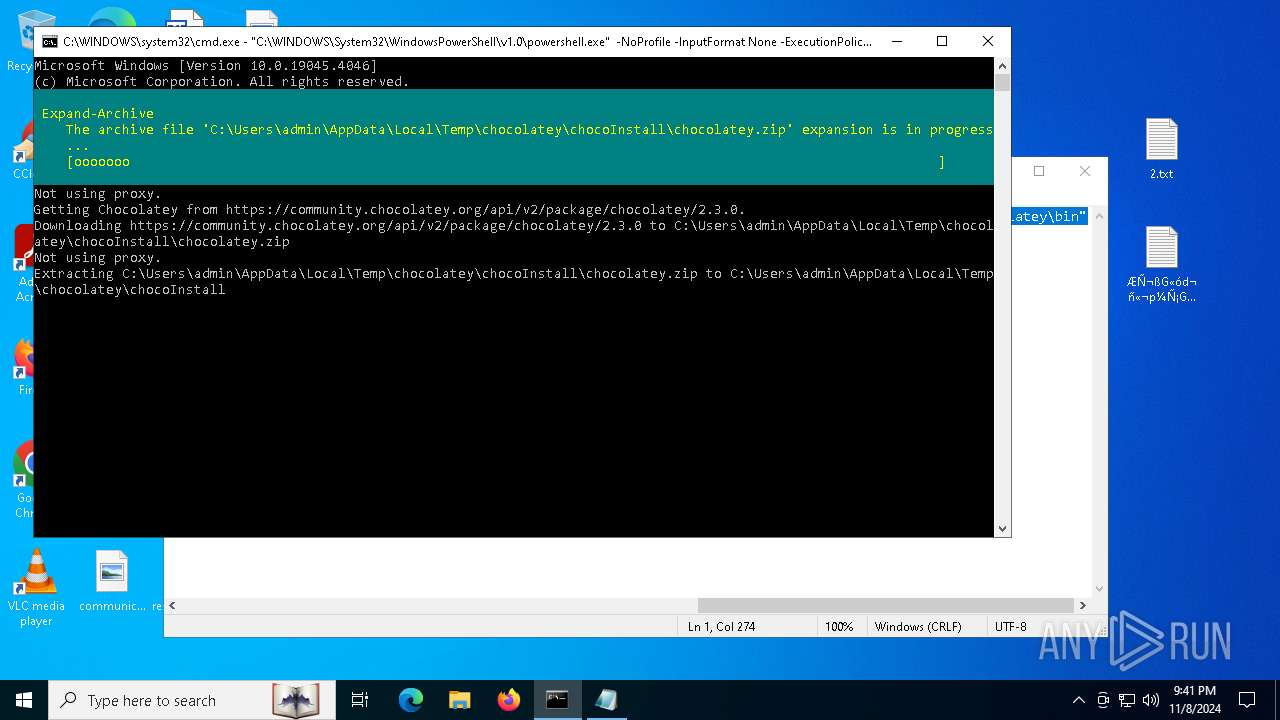
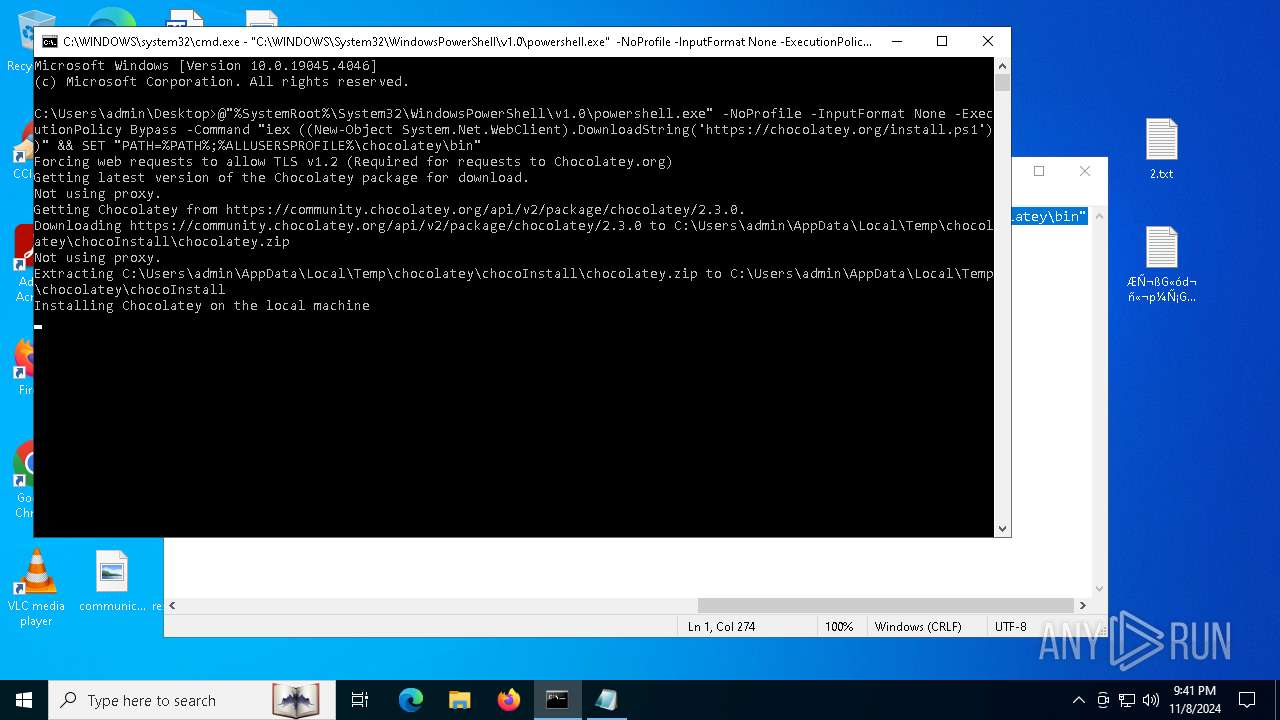
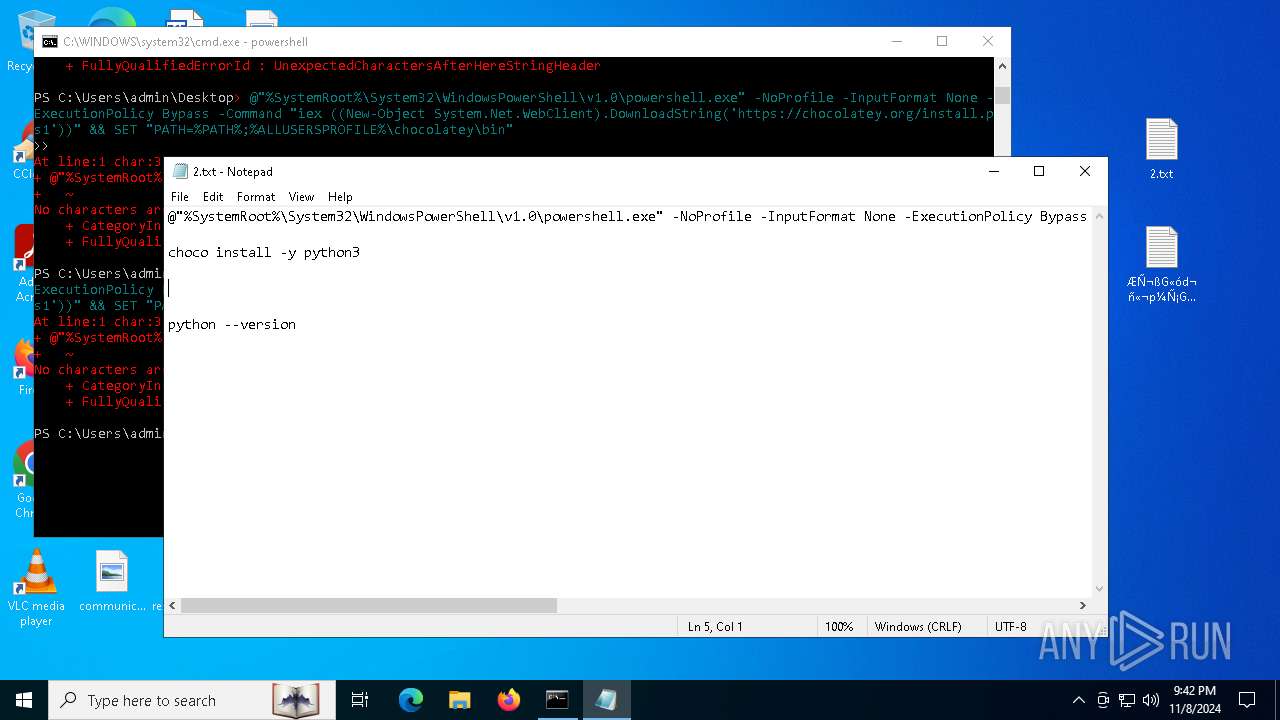
Drops 7-zip archiver for unpacking
- powershell.exe (PID: 5852)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 6436)
Manual execution by a user
- notepad.exe (PID: 1452)
- notepad.exe (PID: 1576)
- cmd.exe (PID: 6384)
- cmd.exe (PID: 1500)
- cmd.exe (PID: 1028)
- notepad.exe (PID: 1184)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:11:09 00:04:14 |
| ZipCRC: | 0xbbadf48f |
| ZipCompressedSize: | 609 |
| ZipUncompressedSize: | 1157 |
| ZipFileName: | ????⮢?? ???㬥?? (3).txt |
Total processes
160
Monitored processes
25
Malicious processes
0
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1028 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Users\admin\Desktop\1.cmd" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
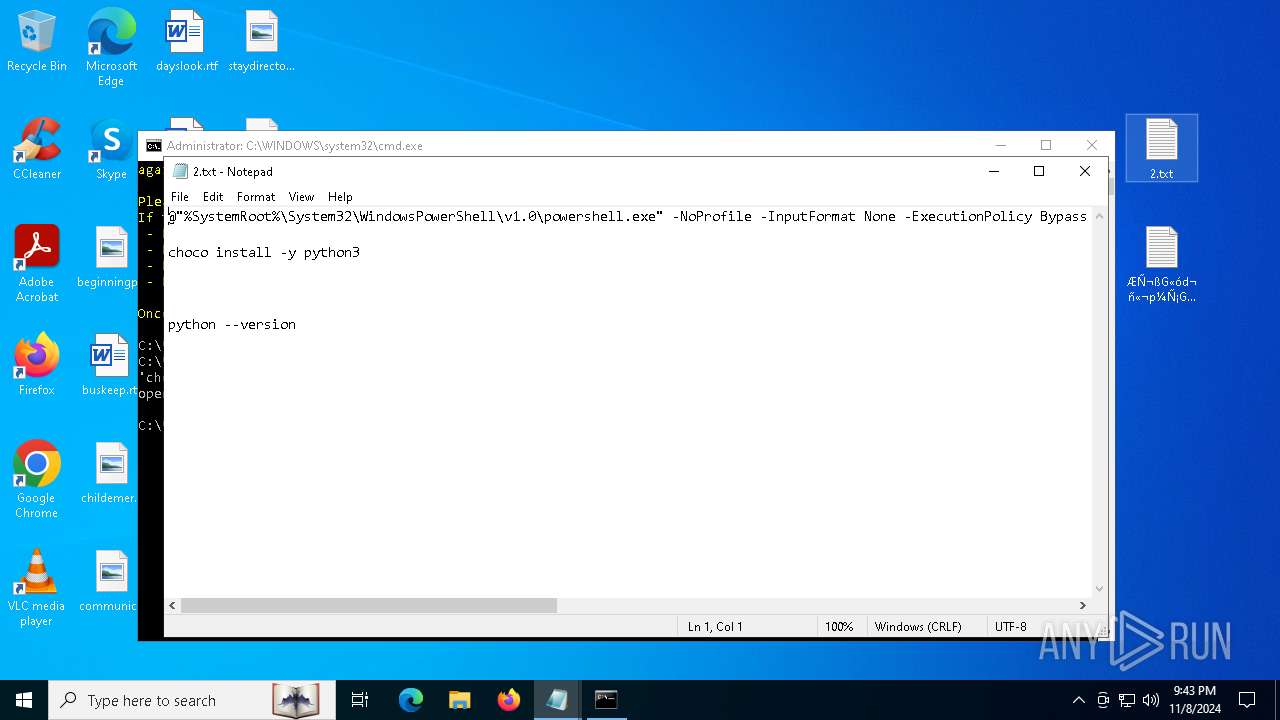
| 1184 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\2.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1452 | "C:\WINDOWS\System32\NOTEPAD.EXE" C:\Users\admin\Desktop\1.bat | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1500 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\1.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1576 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\2.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2784 | powershell | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2808 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3004 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3076 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3156 | cmd.exe | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
27 532
Read events
27 512
Write events
19
Delete events
1
Modification events
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Новая сжатая ZIP-папка.zip | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6436) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
7
Suspicious files
3
Text files
77
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5852 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_53ye1hlw.w4l.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6436.33674\ÆѬßG«ód¬ ñ«¬p¼Ñ¡G (3).txt | text | |
MD5:A65B452E83C8150C88C8F1D96BE7CC3F | SHA256:9F899583F8C53E545210B70D773EC4722C51A54F6872026A25C1DAB3F643A9A8 | |||
| 5852 | powershell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\tools\init.ps1 | text | |
MD5:534EDDF59B2A518F5475B44362D9FFF6 | SHA256:71C2606BF144C5D697B85BB170D063892D484A87F9F7FB146356BDE827D4264E | |||
| 5852 | powershell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\tools\chocolateyInstall\choco.exe | executable | |
MD5:76D8FE544353FB6DFC258FCFBE9264D9 | SHA256:9A058764417A634DCB53AF74C50F9552AF3BC0B873A562F383AF36FEEFC1496E | |||
| 5852 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zwbyzcrt.4rr.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5852 | powershell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\tools\chocolateyInstall\CREDITS.txt | text | |
MD5:7677758586925BAF4E9D7573BF12F273 | SHA256:4387F7836591FD9B384D5A11C22685D5441ED8F56A15DD962C28174F60D1B35B | |||
| 5852 | powershell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\tools\VERIFICATION.txt | text | |
MD5:F5BA42804D762840BBDA4CB2AE6824E7 | SHA256:75595E484E5BC5283398D878E882A234E4F0C1556FA5D41E8770336881E1C4FE | |||
| 5852 | powershell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\tools\chocolateyInstall\helpers\Chocolatey.PowerShell.dll-help.xml | xml | |
MD5:B01CE7945B984A7D4577948805BDC514 | SHA256:6CFE6AAF300B0447EABAD6F801DCC38461B0802F75F433DDE2C642E52BC9D36B | |||
| 5852 | powershell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\chocolatey.nuspec | xml | |
MD5:6F1D1A607FCF498C306BA60F4C49E0BB | SHA256:A2B9463494ED831C3A388C1867043FDA6D7B308125F1CE33E52C914DE5D35B99 | |||
| 5852 | powershell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\chocolatey.zip | compressed | |
MD5:95231E41829F1C3A5AE890B71BCEF1FA | SHA256:C73D4EDA9AB5CA89583EF90838C4B819A304C9AC5A8AD5A89DCB7EDB15AB5FCF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
55
DNS requests
25
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3772 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1552 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3772 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6516 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1248 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 92.123.104.32:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1552 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1552 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4360 | SearchApp.exe | 92.123.104.63:443 | th.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5852 | powershell.exe | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |
6100 | powershell.exe | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |