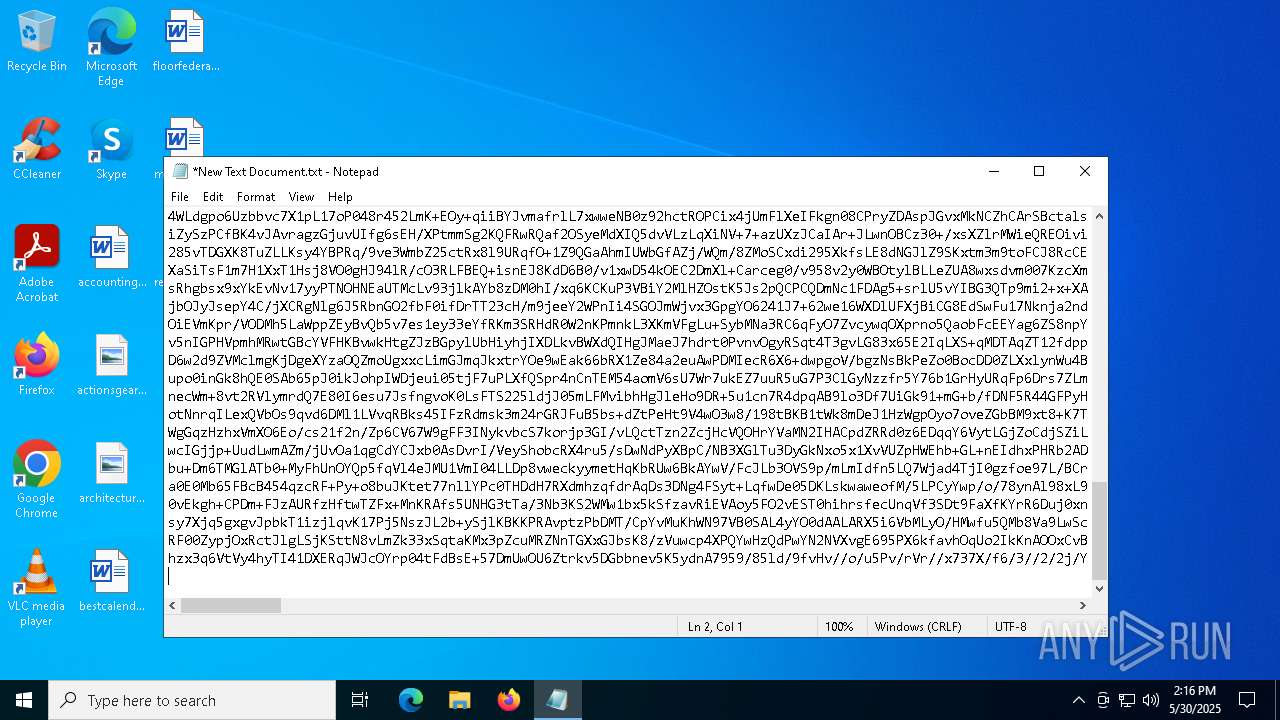
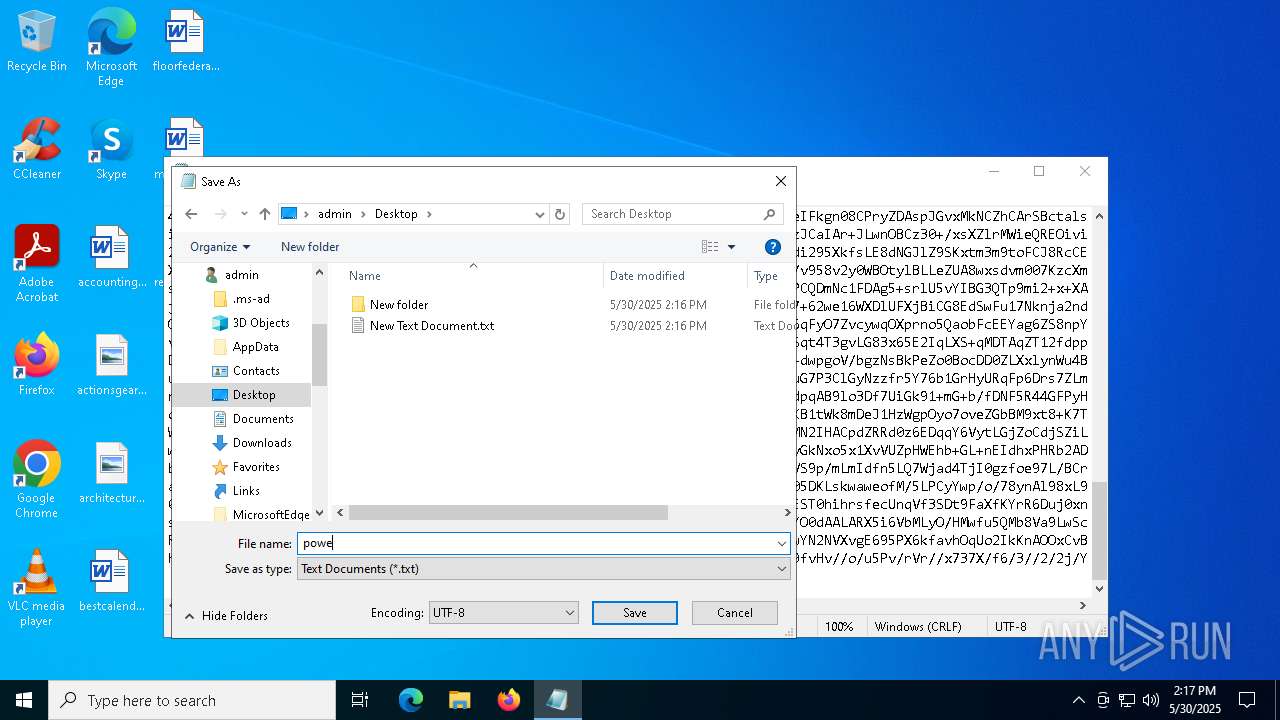
| File name: | message.txt |
| Full analysis: | https://app.any.run/tasks/d23d7345-bcfc-40f7-aa45-2932a0c62e57 |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2025, 14:15:22 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (65536), with no line terminators |
| MD5: | 5F4F173CBD0F0E7D2BF991D2A7058547 |
| SHA1: | F9ADBB0CE435E095DF049DD0B2C2CD45268C8C98 |
| SHA256: | DC2E27DF05C46E0D3F50F2BC91FCB7C7B60744C48BCB7B246CC24B2C549F6B5F |
| SSDEEP: | 1536:fsIEKDh8HuaaNWm/piJo8J0XR9OcLm/CbBf2JGaMnCcy2uQleR5EE+4skt0:UIE2h8HTm/H8J0Xv1L4CbBfmMJLuQlLv |
MALICIOUS
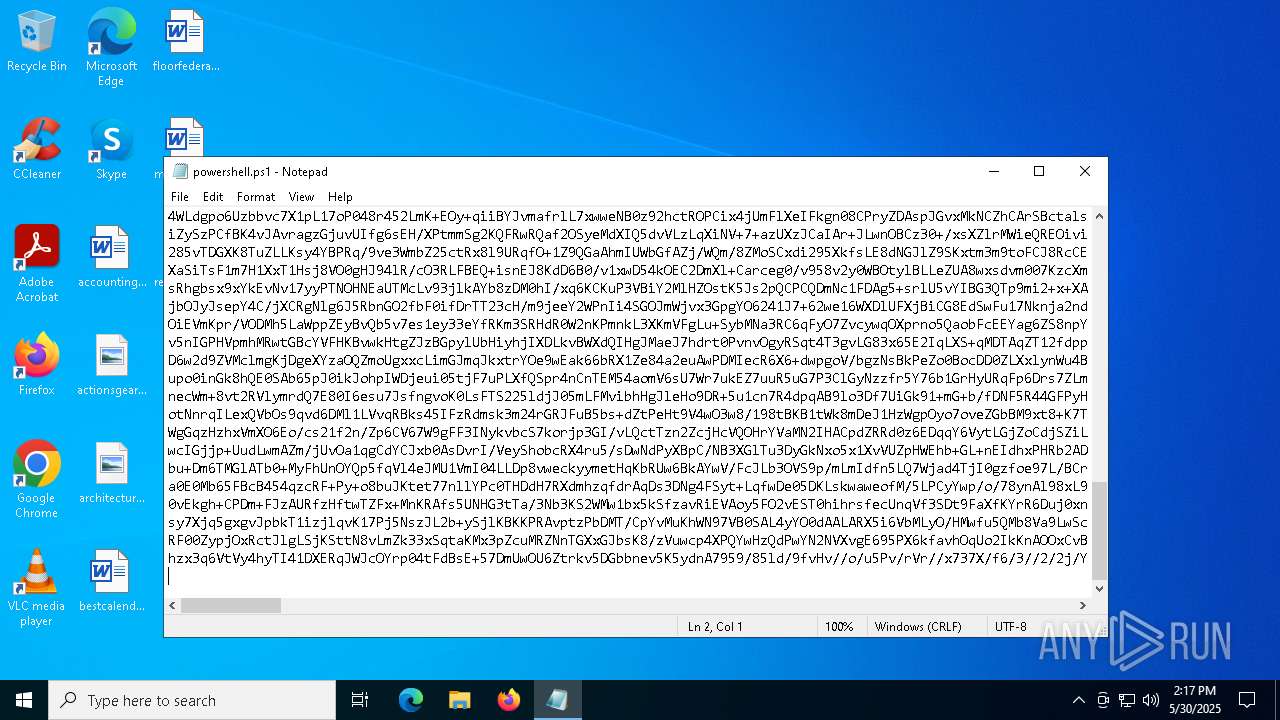
Bypass execution policy to execute commands
- powershell.exe (PID: 7312)
- powershell.exe (PID: 6244)
SUSPICIOUS
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7312)
- powershell.exe (PID: 6244)
CSC.EXE is used to compile C# code
- csc.exe (PID: 7936)
- csc.exe (PID: 1056)
Executable content was dropped or overwritten
- csc.exe (PID: 7936)
- csc.exe (PID: 1056)
INFO
Reads the machine GUID from the registry
- csc.exe (PID: 7936)
- csc.exe (PID: 1056)
Create files in a temporary directory
- cvtres.exe (PID: 7964)
- csc.exe (PID: 7936)
- csc.exe (PID: 1056)
- cvtres.exe (PID: 5640)
Checks supported languages
- cvtres.exe (PID: 7964)
- csc.exe (PID: 7936)
- csc.exe (PID: 1056)
- cvtres.exe (PID: 5640)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7312)
- powershell.exe (PID: 6244)
Manual execution by a user
- notepad.exe (PID: 896)
- powershell.exe (PID: 6244)
Reads security settings of Internet Explorer
- notepad.exe (PID: 896)
Reads the software policy settings
- slui.exe (PID: 7528)
- slui.exe (PID: 2140)
Checks proxy server information
- slui.exe (PID: 2140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
143
Monitored processes
12
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 896 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\New Text Document.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\d12xdrnx.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2140 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4008 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5640 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES7373.tmp" "c:\Users\admin\AppData\Local\Temp\CSC3FE30BE0CA6E4646A71FECE75153E395.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 6244 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass "C:\Users\admin\Desktop\powershell.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7312 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\AppData\Local\Temp\message.txt.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7320 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7496 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7528 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 105
Read events
16 037
Write events
65
Delete events
3
Modification events
| (PID) Process: | (896) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (896) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 04000000030000000E00000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (896) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 010000000000000004000000050000000200000003000000FFFFFFFF | |||
| (PID) Process: | (896) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\34\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Generic | |||
| (PID) Process: | (896) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 114 | |||
| (PID) Process: | (896) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0E000000040000000300000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (896) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 040000000E0000000300000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (896) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\34\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (896) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\34\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (896) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\34\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | FFlags |
Value: | |||
Executable files
2
Suspicious files
7
Text files
11
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 896 | notepad.exe | C:\Users\admin\Desktop\powershell.ps1 | text | |
MD5:0038F9ED78C7E04AC5BA2DB9CDE8E31D | SHA256:6AE49982B7A47FE561D3BE973FE2D15F0B81D11AAB282D67626F1623B28802F5 | |||
| 7312 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\UM4PQ03QXTJWDV73PP4N.temp | binary | |
MD5:B307A0DE2CBC1B725AB7E73308783380 | SHA256:BF95FA0985A134FAF8623B6E940381565BDCB2FE7145F0E790F629BE3A28510B | |||
| 7312 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:B307A0DE2CBC1B725AB7E73308783380 | SHA256:BF95FA0985A134FAF8623B6E940381565BDCB2FE7145F0E790F629BE3A28510B | |||
| 7312 | powershell.exe | C:\Users\admin\AppData\Local\Temp\kxl3m0cv.cmdline | text | |
MD5:750CA36EFC37DB7CBB0EE088C21250EE | SHA256:9FA8F4539AEB91473989EF902EDFBF480B4163A64CE5F5505F1E069DD702DB5F | |||
| 7312 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_42nafuqa.1vj.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7936 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC55E83FC245054BFD9DD0C12950DD6681.TMP | res | |
MD5:5D8D975E5078A885FD071DE7E5A14EBF | SHA256:8948D3C36E786B62818CEC73807CBE2B0AB1F2525D6AD2D14FEF3F20751ECCB1 | |||
| 7312 | powershell.exe | C:\Users\admin\AppData\Local\Temp\kxl3m0cv.0.cs | text | |
MD5:029A251DB8736D1C039890283DDAFD0D | SHA256:D1B97CAC79D2B968A2D80DF52AB40E480540F81040A825C5ABA1192C72DB2B0C | |||
| 7312 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF10b538.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 7312 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:46F2A0C56F11F4D0051E9BE4D3808490 | SHA256:B14EA5216E943B6D4FB13F6BBFB2E66F235124C56628DF8D985F0F257406C5B1 | |||
| 6244 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\LK1O0953HDN50EK3YMWF.temp | binary | |
MD5:06583E7D203ABD4ABE3BC049A11F3F41 | SHA256:82554D0624EDB39262D5DABA6F44E67535B4C63E10F31D241F420A159FC6280E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
27
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8188 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8188 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |