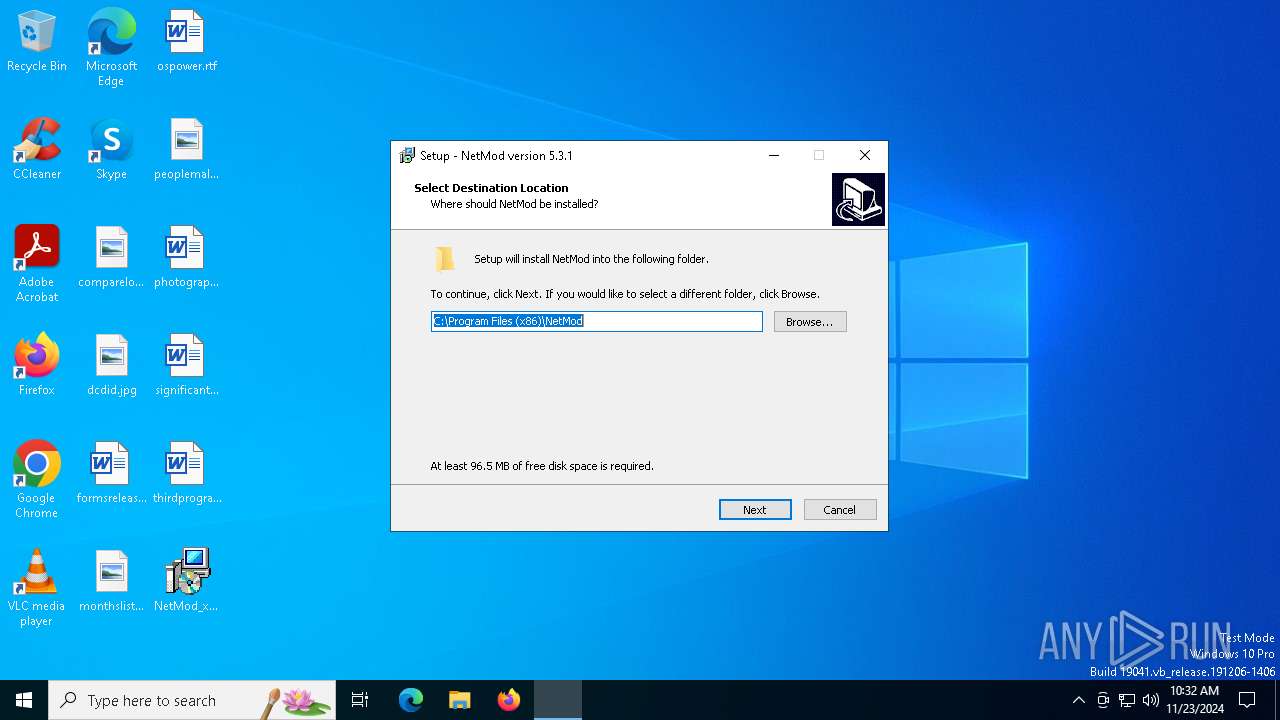
| File name: | NetMod_x86Latest.exe |
| Full analysis: | https://app.any.run/tasks/ae5e5c76-0509-45b4-8e9e-d3c59a071fcd |
| Verdict: | Malicious activity |
| Analysis date: | November 23, 2024, 10:32:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 10 sections |
| MD5: | 88A66FAFD730625FFE48117E3D7C3784 |
| SHA1: | 05EAEF97993B7CA9265F106398A54967F0F3FF65 |
| SHA256: | DC2A558D13DEC94E232CCFCD5542EF4F07CD537BA07D9D773774A2F7F5B035BB |
| SSDEEP: | 393216:DRv2HMsmNZQJSV0QAQO9SC6eiRQmRpZV2g:lvi+HQ5UOuzRRpv2g |
MALICIOUS
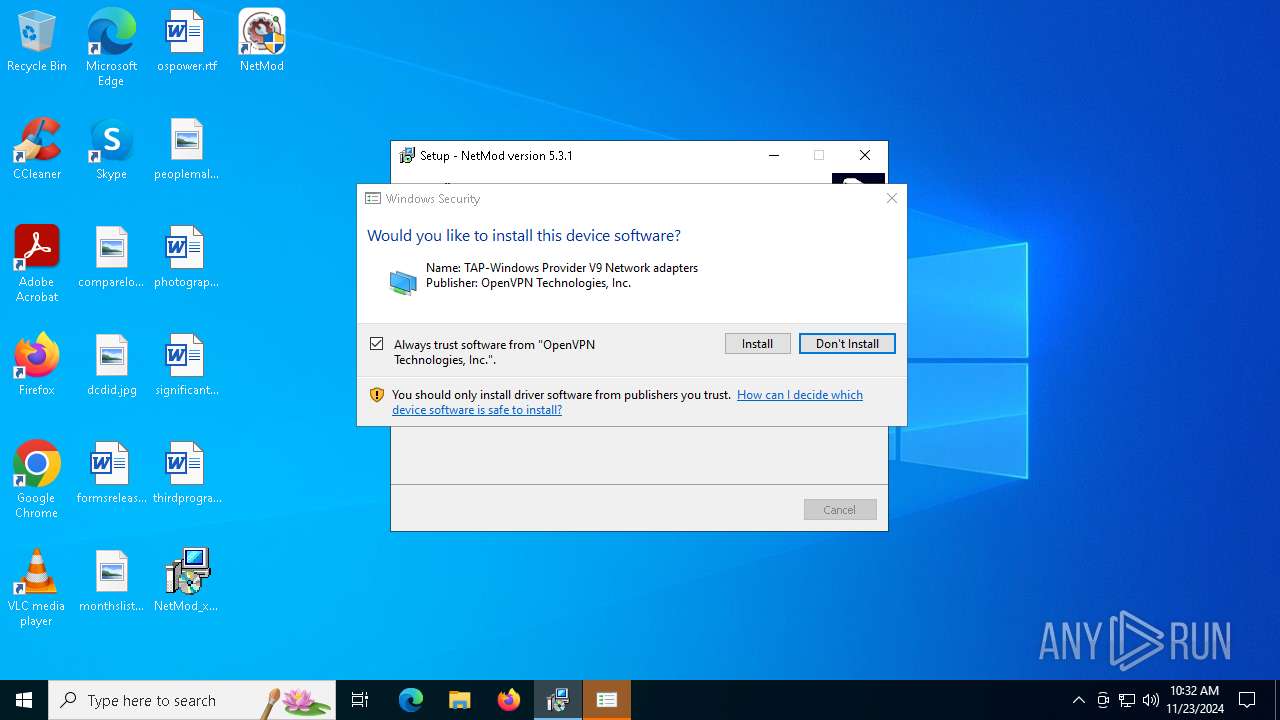
Executing a file with an untrusted certificate
- NetMod_x86Latest.exe (PID: 5728)
SUSPICIOUS
Executable content was dropped or overwritten
- NetMod_x86Latest.exe (PID: 5728)
- NetMod_x86Latest.exe (PID: 5432)
- drvinst.exe (PID: 4144)
- drvinst.exe (PID: 3736)
- tapinstall.exe (PID: 4052)
- NetMod_x86Latest.tmp (PID: 1488)
Reads security settings of Internet Explorer
- NetMod_x86Latest.tmp (PID: 6004)
- tapinstall.exe (PID: 4052)
Reads the Windows owner or organization settings
- NetMod_x86Latest.tmp (PID: 1488)
The process drops C-runtime libraries
- NetMod_x86Latest.tmp (PID: 1488)
Executing commands from a ".bat" file
- NetMod_x86Latest.tmp (PID: 1488)
Application launched itself
- cmd.exe (PID: 5968)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5968)
Checks Windows Trust Settings
- tapinstall.exe (PID: 4052)
- drvinst.exe (PID: 4144)
Starts CMD.EXE for commands execution
- NetMod_x86Latest.tmp (PID: 1488)
- cmd.exe (PID: 5968)
Drops a system driver (possible attempt to evade defenses)
- tapinstall.exe (PID: 4052)
- drvinst.exe (PID: 4144)
- drvinst.exe (PID: 3736)
- NetMod_x86Latest.tmp (PID: 1488)
Creates files in the driver directory
- drvinst.exe (PID: 4144)
Process drops legitimate windows executable
- NetMod_x86Latest.tmp (PID: 1488)
INFO
Checks supported languages
- NetMod_x86Latest.tmp (PID: 6004)
- NetMod_x86Latest.exe (PID: 5728)
- NetMod_x86Latest.exe (PID: 5432)
- NetMod_x86Latest.tmp (PID: 1488)
- tapinstall.exe (PID: 4052)
- tapinstall.exe (PID: 3736)
- drvinst.exe (PID: 4144)
Create files in a temporary directory
- NetMod_x86Latest.exe (PID: 5728)
- NetMod_x86Latest.exe (PID: 5432)
- NetMod_x86Latest.tmp (PID: 1488)
- tapinstall.exe (PID: 4052)
Reads the computer name
- NetMod_x86Latest.tmp (PID: 6004)
- NetMod_x86Latest.tmp (PID: 1488)
- tapinstall.exe (PID: 4052)
Process checks computer location settings
- NetMod_x86Latest.tmp (PID: 6004)
Creates a software uninstall entry
- NetMod_x86Latest.tmp (PID: 1488)
Reads the software policy settings
- tapinstall.exe (PID: 4052)
- pnputil.exe (PID: 3680)
- drvinst.exe (PID: 4144)
Reads security settings of Internet Explorer
- pnputil.exe (PID: 3680)
Reads the machine GUID from the registry
- tapinstall.exe (PID: 4052)
- drvinst.exe (PID: 4144)
Creates files in the program directory
- NetMod_x86Latest.tmp (PID: 1488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:11:15 09:48:30+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741376 |
| InitializedDataSize: | 38400 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Henry G. |
| FileDescription: | NetMod Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | NetMod |
| ProductVersion: | 5.3.1 |
Total processes
254
Monitored processes
138
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 396 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo "Signer name : Unknown" " | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 396 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo "Signer name : Microsoft Windows Hardware Compatibility Publisher" " | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 448 | findstr /R "Driver package provider" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | findstr /r /c:"TAP-Windows Provider V9" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 624 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo "Signer name : Microsoft Windows" " | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 768 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo "Driver date and version : 11/29/2016 16.0.7629.4000" " | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 836 | findstr /R "Published name" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 836 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo "Signer name : Microsoft Windows" " | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 880 | findstr /R "Published name" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo "Driver date and version : 06/19/2009 6.0.1.6305" " | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 526
Read events
15 449
Write events
69
Delete events
8
Modification events
| (PID) Process: | (1488) NetMod_x86Latest.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers |
| Operation: | write | Name: | C:\Program Files (x86)\NetMod\NetMod.exe |
Value: RUNASADMIN | |||
| (PID) Process: | (1488) NetMod_x86Latest.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{45FDF669-5B62-42EE-8DFB-5726B20293AE}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.1.2 | |||
| (PID) Process: | (1488) NetMod_x86Latest.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{45FDF669-5B62-42EE-8DFB-5726B20293AE}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files (x86)\NetMod | |||
| (PID) Process: | (1488) NetMod_x86Latest.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{45FDF669-5B62-42EE-8DFB-5726B20293AE}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\NetMod\ | |||
| (PID) Process: | (1488) NetMod_x86Latest.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{45FDF669-5B62-42EE-8DFB-5726B20293AE}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: NetMod | |||
| (PID) Process: | (1488) NetMod_x86Latest.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{45FDF669-5B62-42EE-8DFB-5726B20293AE}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (1488) NetMod_x86Latest.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{45FDF669-5B62-42EE-8DFB-5726B20293AE}_is1 |
| Operation: | write | Name: | Inno Setup: Language |
Value: english | |||
| (PID) Process: | (1488) NetMod_x86Latest.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{45FDF669-5B62-42EE-8DFB-5726B20293AE}_is1 |
| Operation: | write | Name: | DisplayName |
Value: NetMod version 5.3.1 | |||
| (PID) Process: | (1488) NetMod_x86Latest.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{45FDF669-5B62-42EE-8DFB-5726B20293AE}_is1 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files (x86)\NetMod\NetMod.exe | |||
| (PID) Process: | (1488) NetMod_x86Latest.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{45FDF669-5B62-42EE-8DFB-5726B20293AE}_is1 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files (x86)\NetMod\unins000.exe" | |||
Executable files
182
Suspicious files
22
Text files
7
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1488 | NetMod_x86Latest.tmp | C:\Users\admin\AppData\Local\Temp\is-9F32P.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 1488 | NetMod_x86Latest.tmp | C:\Program Files (x86)\NetMod\unins000.exe | executable | |
MD5:9393C076B11820AD848E6ECCAFA0ADD7 | SHA256:119AE51BCD5431BED1BDF63573F9E5EC5DB6942AA8388DF0F5D4785F358F1B69 | |||
| 5728 | NetMod_x86Latest.exe | C:\Users\admin\AppData\Local\Temp\is-0ST0Q.tmp\NetMod_x86Latest.tmp | executable | |
MD5:9393C076B11820AD848E6ECCAFA0ADD7 | SHA256:119AE51BCD5431BED1BDF63573F9E5EC5DB6942AA8388DF0F5D4785F358F1B69 | |||
| 1488 | NetMod_x86Latest.tmp | C:\Program Files (x86)\NetMod\is-JLCQD.tmp | executable | |
MD5:9393C076B11820AD848E6ECCAFA0ADD7 | SHA256:119AE51BCD5431BED1BDF63573F9E5EC5DB6942AA8388DF0F5D4785F358F1B69 | |||
| 1488 | NetMod_x86Latest.tmp | C:\Program Files (x86)\NetMod\is-9179L.tmp | executable | |
MD5:FFDCF232D0BB2FFF78721FB347641A76 | SHA256:FF42BCA704605E187ABB45523868B15128D6AF1C28AD40A4579D507D34A953B2 | |||
| 1488 | NetMod_x86Latest.tmp | C:\Program Files (x86)\NetMod\is-VS31U.tmp | executable | |
MD5:4A2D8937CBBDA859CB2C14D9A270A98F | SHA256:D97B1384452165C67BD72B84217C3E93D3BD902E3B29AF32659332D0B7A1467A | |||
| 1488 | NetMod_x86Latest.tmp | C:\Program Files (x86)\NetMod\is-A0IBB.tmp | executable | |
MD5:597FEB155915568EF98DDBD4D4ED6FA9 | SHA256:A93FDC30467A4847C21285B0B5386B8F90EA843D47F8B27542629E408448053E | |||
| 1488 | NetMod_x86Latest.tmp | C:\Program Files (x86)\NetMod\NetMod.exe | executable | |
MD5:4A2D8937CBBDA859CB2C14D9A270A98F | SHA256:D97B1384452165C67BD72B84217C3E93D3BD902E3B29AF32659332D0B7A1467A | |||
| 1488 | NetMod_x86Latest.tmp | C:\Program Files (x86)\NetMod\redist\VC_redist.x86.exe | executable | |
MD5:DD0232EE751164EAAD2FE0DE7158D77D | SHA256:4C6C420CF4CBF2C9C9ED476E96580AE92A97B2822C21329A2E49E8439AC5AD30 | |||
| 1488 | NetMod_x86Latest.tmp | C:\Program Files (x86)\NetMod\README.txt | text | |
MD5:4346862BA268FA5B9EEF30D04B05EB5E | SHA256:41EAE6D1C7AA61159B5A1ED8A730F501128C3DF7A26A1EEA099253A5F41DE4DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
20
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5156 | RUXIMICS.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1468 | svchost.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1468 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5156 | RUXIMICS.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 204 | 2.16.106.196:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5156 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5156 | RUXIMICS.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
1468 | svchost.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5156 | RUXIMICS.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1468 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |