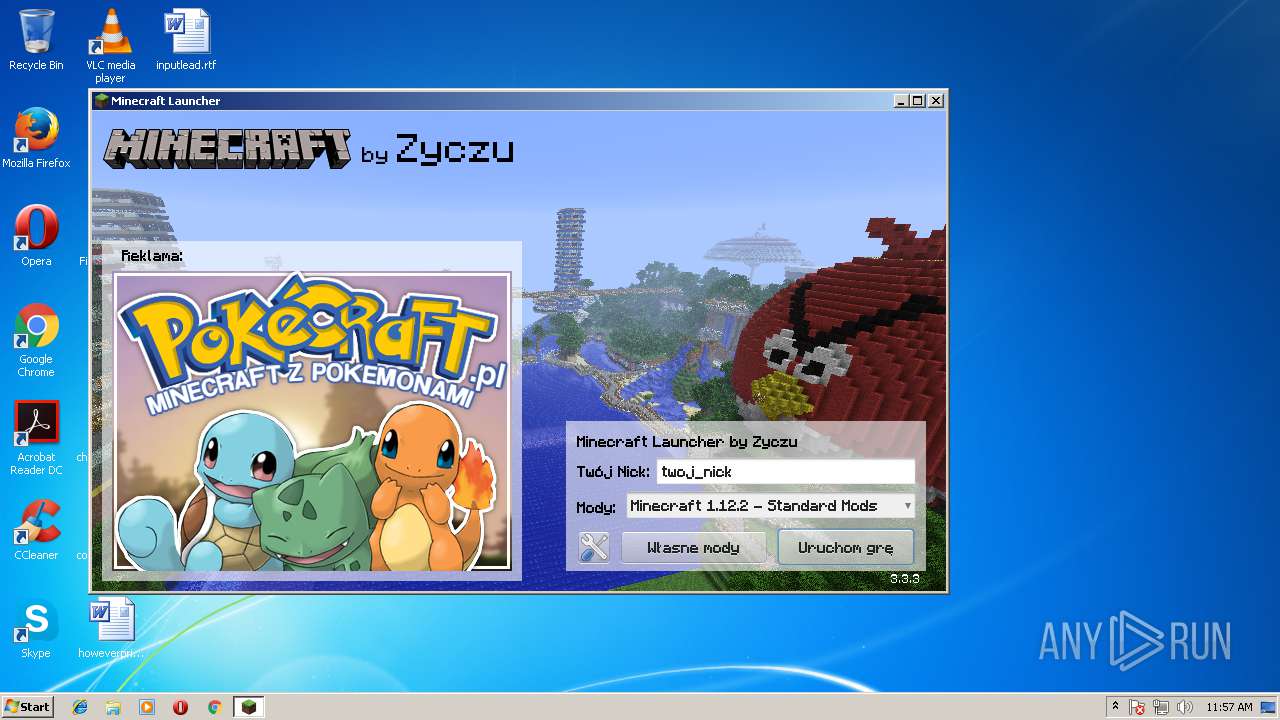
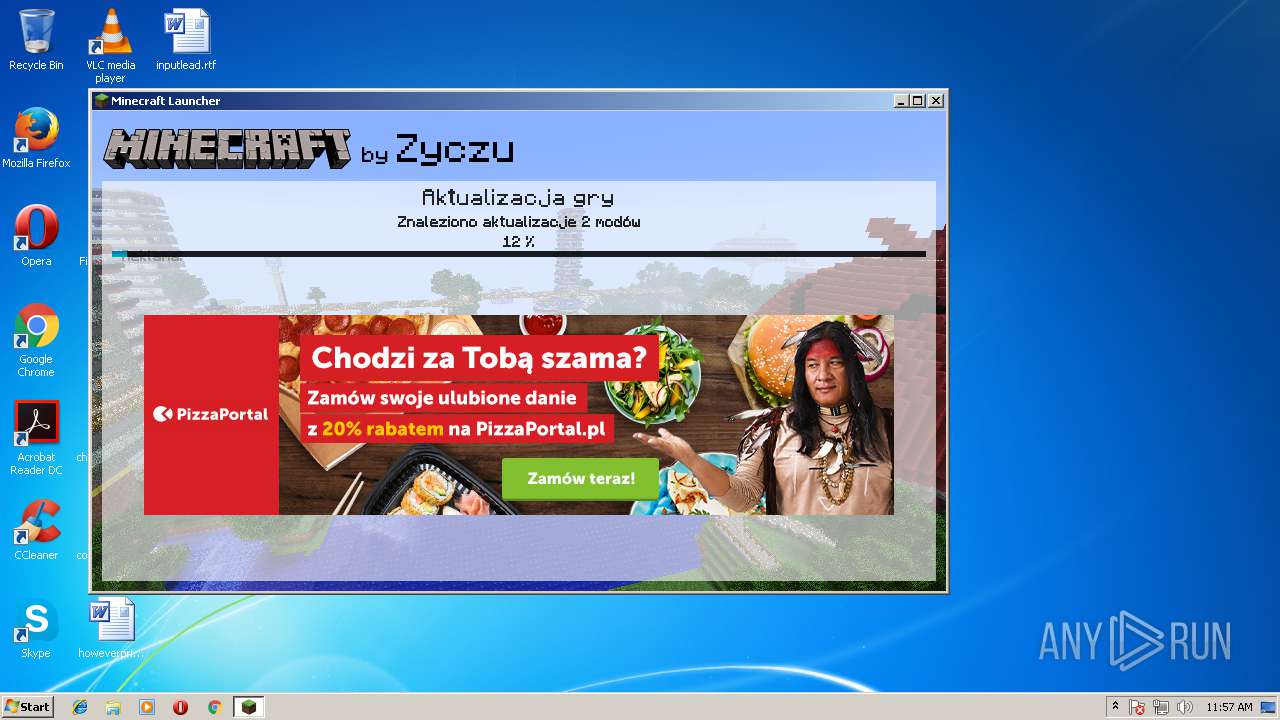
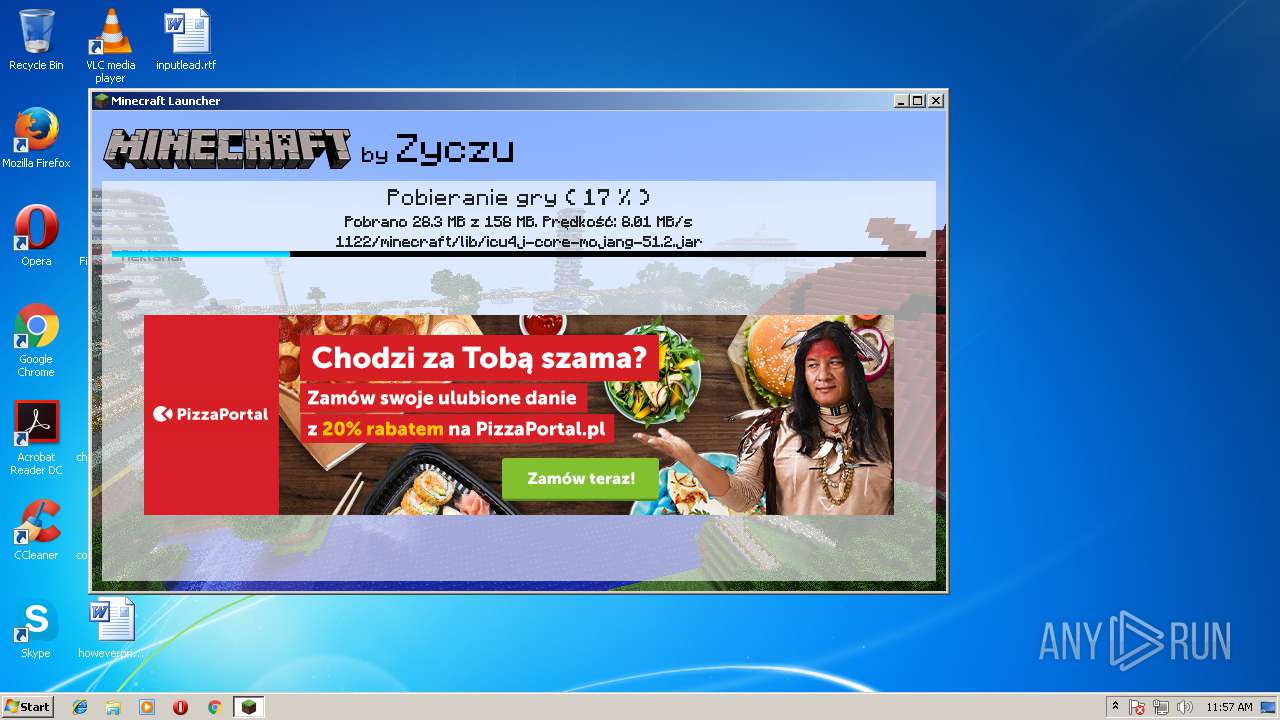
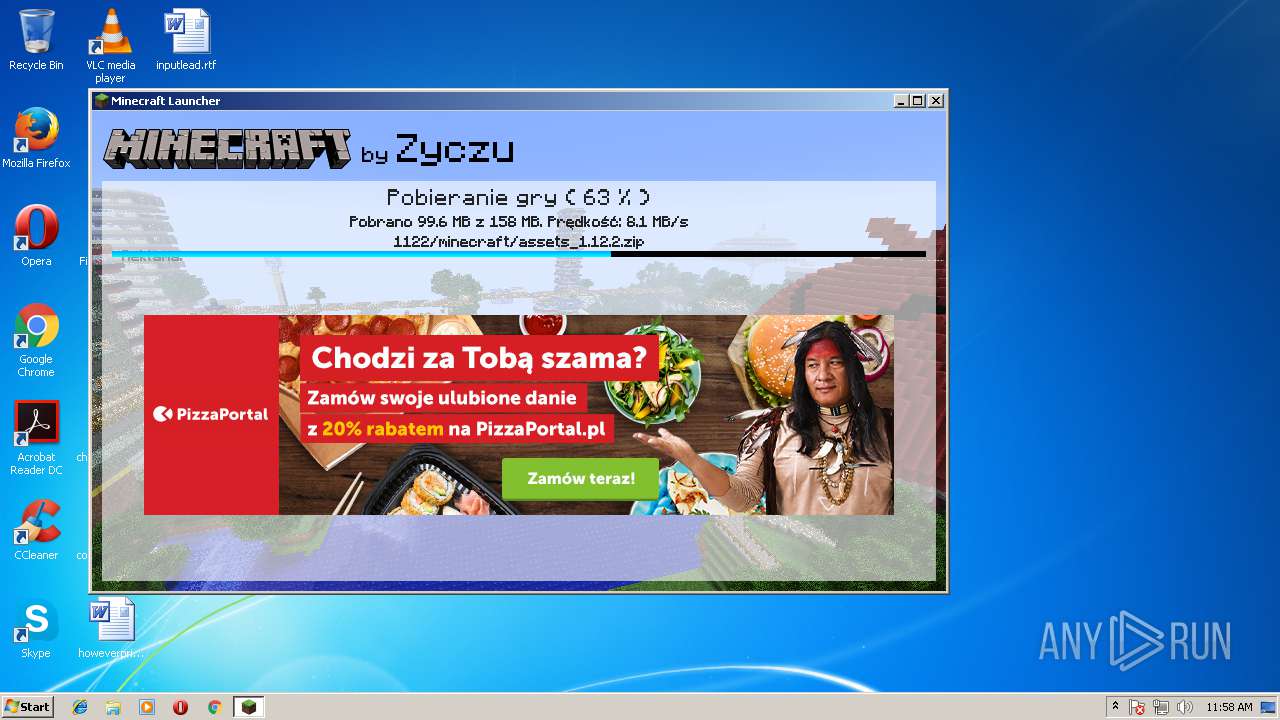
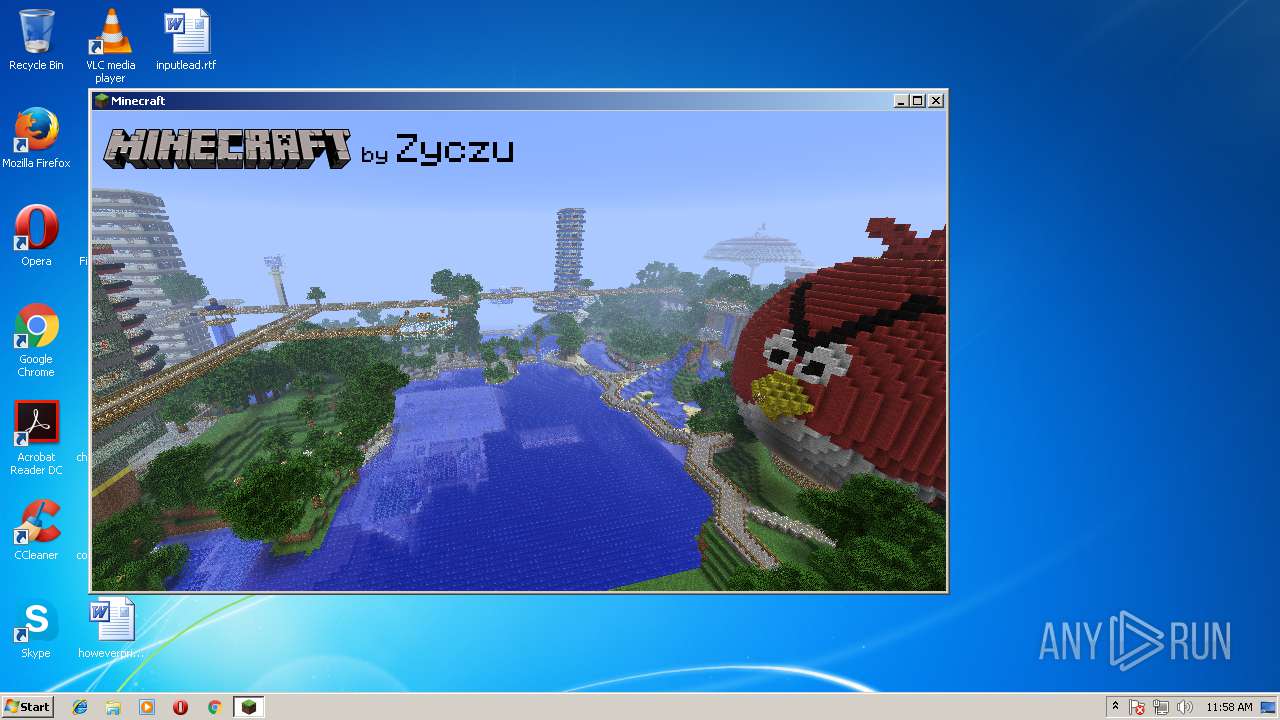
| File name: | zyczu-mc.jar |
| Full analysis: | https://app.any.run/tasks/2b8e1869-1984-4161-86d0-f011c2b968d0 |
| Verdict: | Malicious activity |
| Analysis date: | March 30, 2018, 10:57:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/java-archive |
| File info: | Java archive data (JAR) |
| MD5: | 483CF59AD76CCBCD95FE6C80796DD172 |
| SHA1: | 8F6AB62822C1042C09314D09097629B4CB63350A |
| SHA256: | DC1F5E79ECADFCEE517E1CD6FD69FFF9E90593952A2920C6AE5CAA6CA9A18E1D |
| SSDEEP: | 49152:rXX1S9lmEKTsv9QaYBSRiTysqBwf5rczXRFqXpRPGW+v0aT15FjTGrA1Vbf1b1hM:illQ5dTys+M5rczzpvbTFPL91pu |
MALICIOUS
Application loaded dropped or rewritten executable
- javaw.exe (PID: 2168)
- javaw.exe (PID: 932)
SUSPICIOUS
Creates files in the user directory
- javaw.exe (PID: 2168)
- javaw.exe (PID: 932)
Executes JAVA applets
- javaw.exe (PID: 2168)
Application launched itself
- javaw.exe (PID: 2168)
INFO
Dropped object may contain URL's
- javaw.exe (PID: 932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2013:07:03 12:31:12 |
| ZipCRC: | 0x6a4f50f3 |
| ZipCompressedSize: | 198 |
| ZipUncompressedSize: | 388 |
| ZipFileName: | META-INF/MANIFEST.MF |
Total processes
32
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 932 | javaw -Xms512m -Xmx1024m -classpath /C:/Users/admin/AppData/Local/Temp/zyczu-mc.jar net.minecraft.LauncherFrame | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | javaw.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 4294967295 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2168 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\AppData\Local\Temp\zyczu-mc.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
Total events
41
Read events
38
Write events
3
Delete events
0
Modification events
| (PID) Process: | (2168) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: javaw.exe | |||
| (PID) Process: | (932) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: javaw.exe | |||
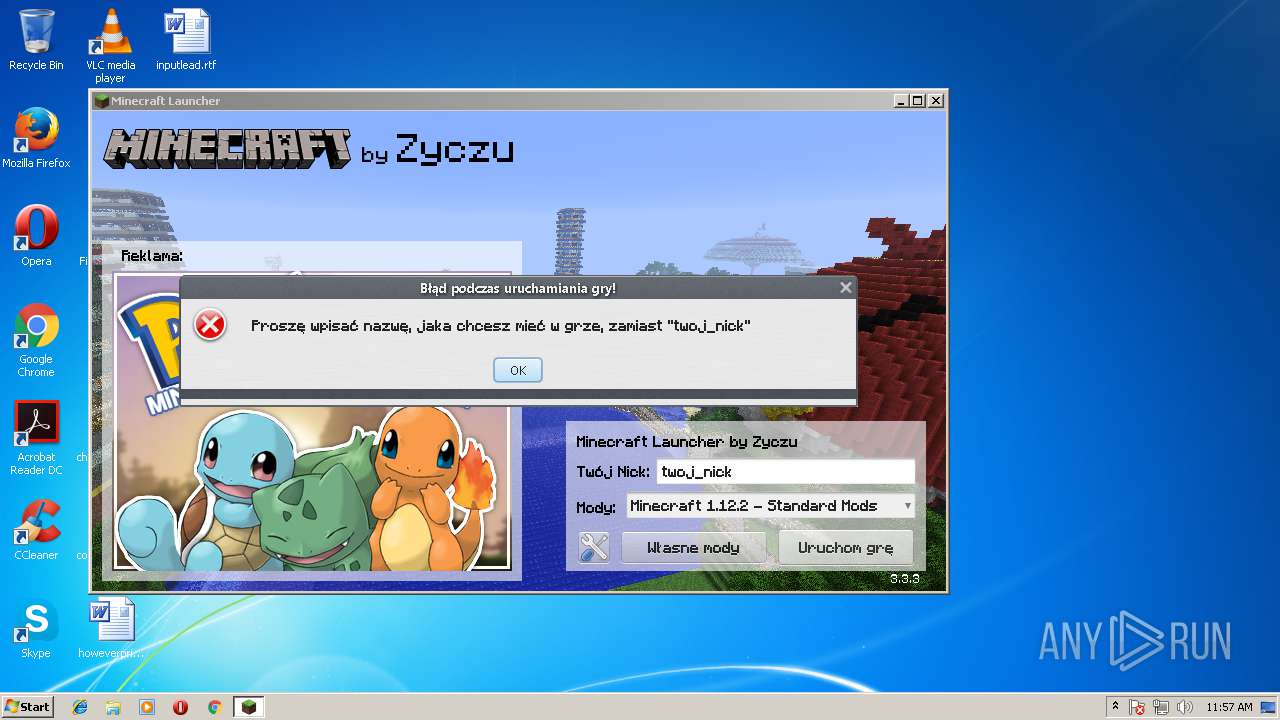
| (PID) Process: | (932) javaw.exe | Key: | HKEY_CURRENT_USER\Software\JavaSoft\Prefs\zyczu |
| Operation: | write | Name: | nick |
Value: twoj_nicks | |||
Executable files
2
Suspicious files
63
Text files
101
Unknown types
496
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2168 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio8857441259504874495.tmp | — | |
MD5:— | SHA256:— | |||
| 932 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio3620103039172164112.tmp | — | |
MD5:— | SHA256:— | |||
| 932 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio3462948871503252318.tmp | — | |
MD5:— | SHA256:— | |||
| 932 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio5235360272948312685.tmp | — | |
MD5:— | SHA256:— | |||
| 932 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio2340148175969838264.tmp | — | |
MD5:— | SHA256:— | |||
| 932 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio4213342240585325948.tmp | — | |
MD5:— | SHA256:— | |||
| 932 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio6256311931365124448.tmp | — | |
MD5:— | SHA256:— | |||
| 932 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio8877798562776491742.tmp | — | |
MD5:— | SHA256:— | |||
| 932 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio9116915338004097337.tmp | — | |
MD5:— | SHA256:— | |||
| 932 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio7143329653598461072.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
50
TCP/UDP connections
16
DNS requests
2
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
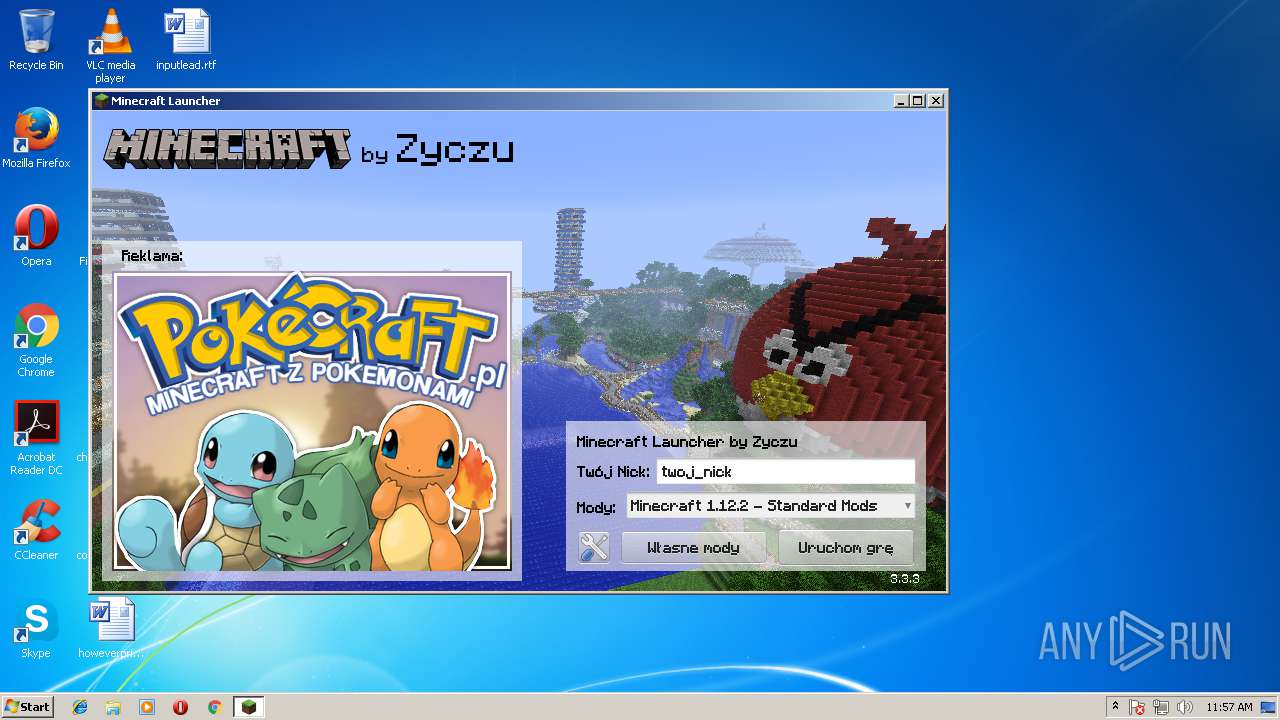
— | — | GET | 200 | 192.166.218.216:80 | http://l7.minecraft.zyczu.pl/reklama.php | PL | text | 183 b | suspicious |
— | — | GET | 200 | 192.166.218.216:80 | http://l7.minecraft.zyczu.pl/images/pizza.png | PL | image | 284 Kb | suspicious |
— | — | GET | 200 | 192.166.218.216:80 | http://l7.minecraft.zyczu.pl/images/reklama.png | PL | image | 190 Kb | suspicious |
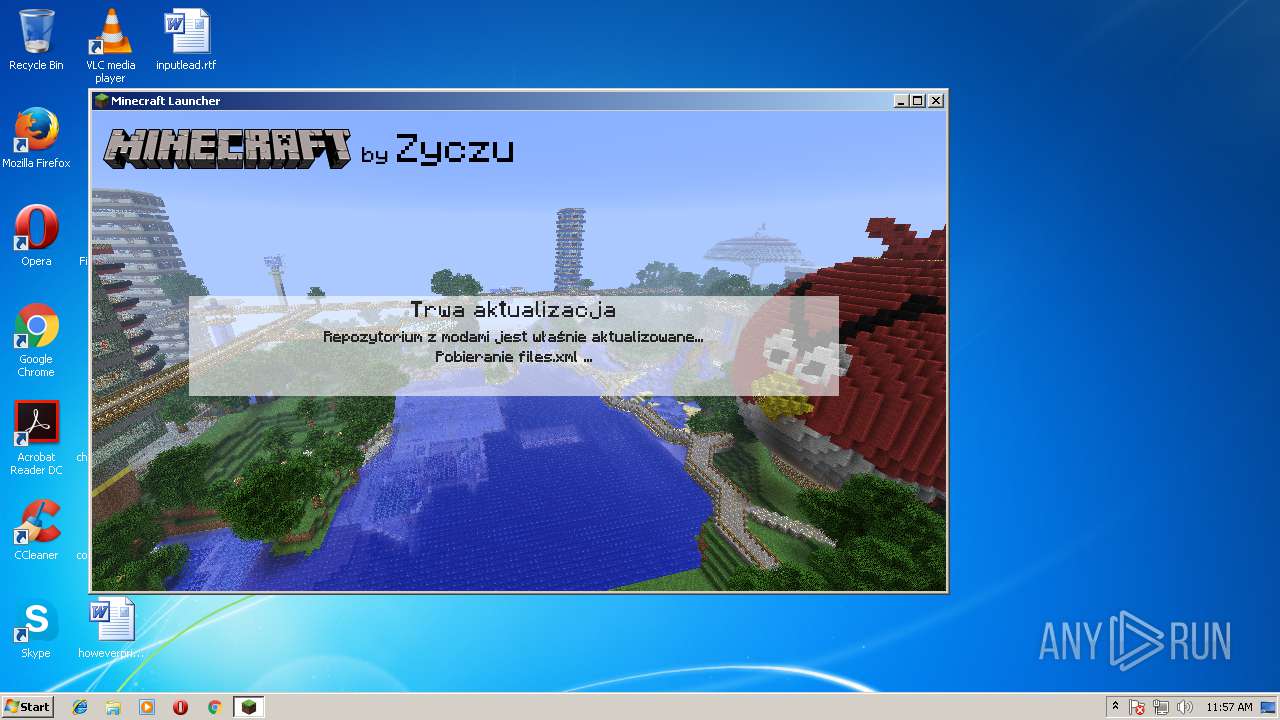
— | — | GET | 200 | 192.166.218.216:80 | http://l7.minecraft.zyczu.pl/update.php?version=10 | PL | text | 347 b | suspicious |
— | — | GET | 200 | 192.166.218.216:80 | http://l7.minecraft.zyczu.pl/repo.xml | PL | xml | 1.77 Kb | suspicious |
— | — | GET | 200 | 192.166.218.216:80 | http://l7.minecraft.zyczu.pl/repo.xml | PL | xml | 1.77 Kb | suspicious |
— | — | GET | 200 | 192.166.218.216:80 | http://l7.minecraft.zyczu.pl/files.xml | PL | xml | 185 Kb | suspicious |
— | — | GET | 200 | 192.166.218.216:80 | http://l7.minecraft.zyczu.pl/repo.xml | PL | xml | 1.77 Kb | suspicious |
— | — | POST | 200 | 192.166.218.216:80 | http://l7.minecraft.zyczu.pl/size.php | PL | text | 2.02 Kb | suspicious |
— | — | GET | 200 | 192.166.218.216:80 | http://l7.minecraft.zyczu.pl/repo.xml | PL | xml | 1.77 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.166.218.216:80 | l7.minecraft.zyczu.pl | Iwacom Sp. Z O.o. | PL | suspicious |
— | — | 151.80.109.154:80 | oldforum.pokecraft.pl | OVH SAS | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
l7.minecraft.zyczu.pl |
| suspicious |
oldforum.pokecraft.pl |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 256 |