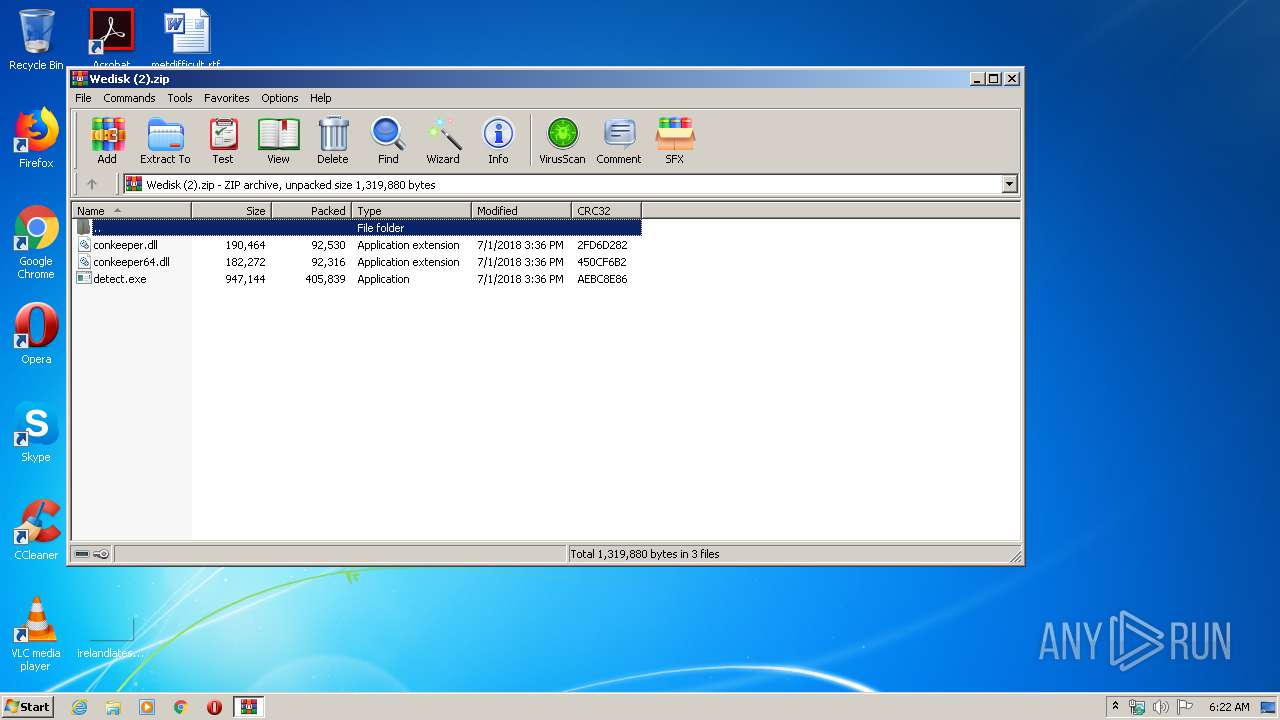
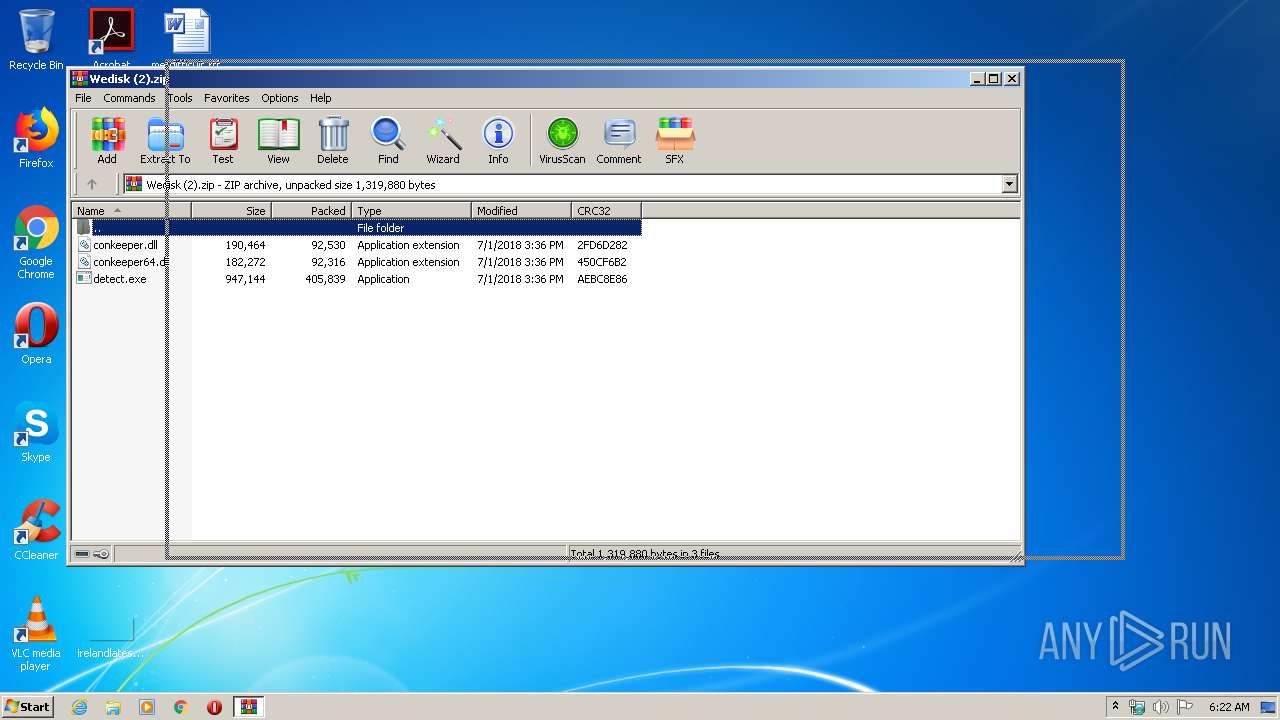
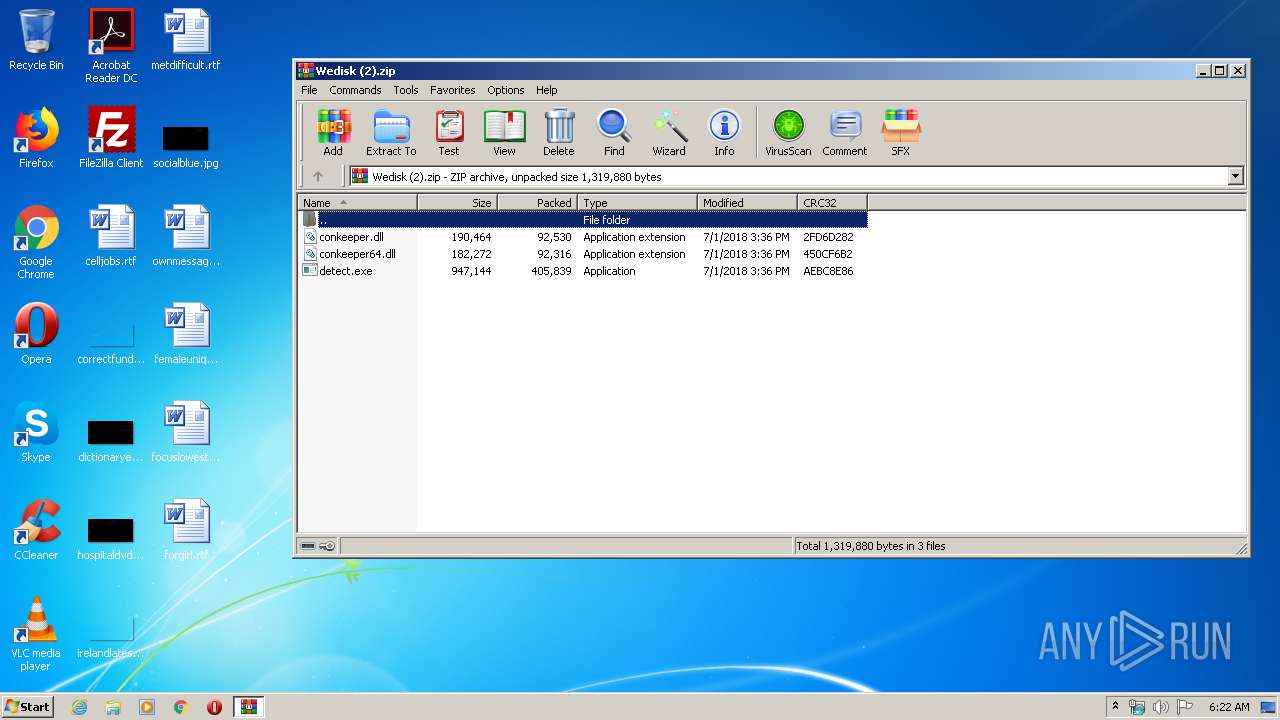
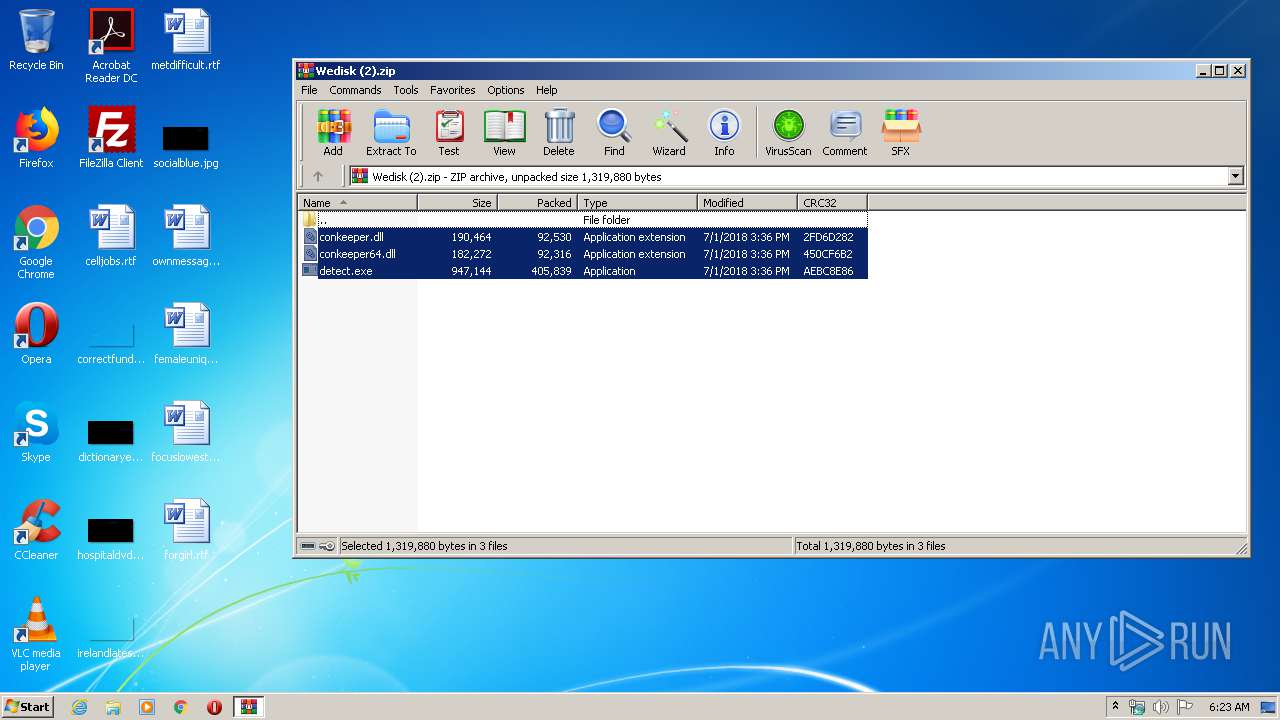
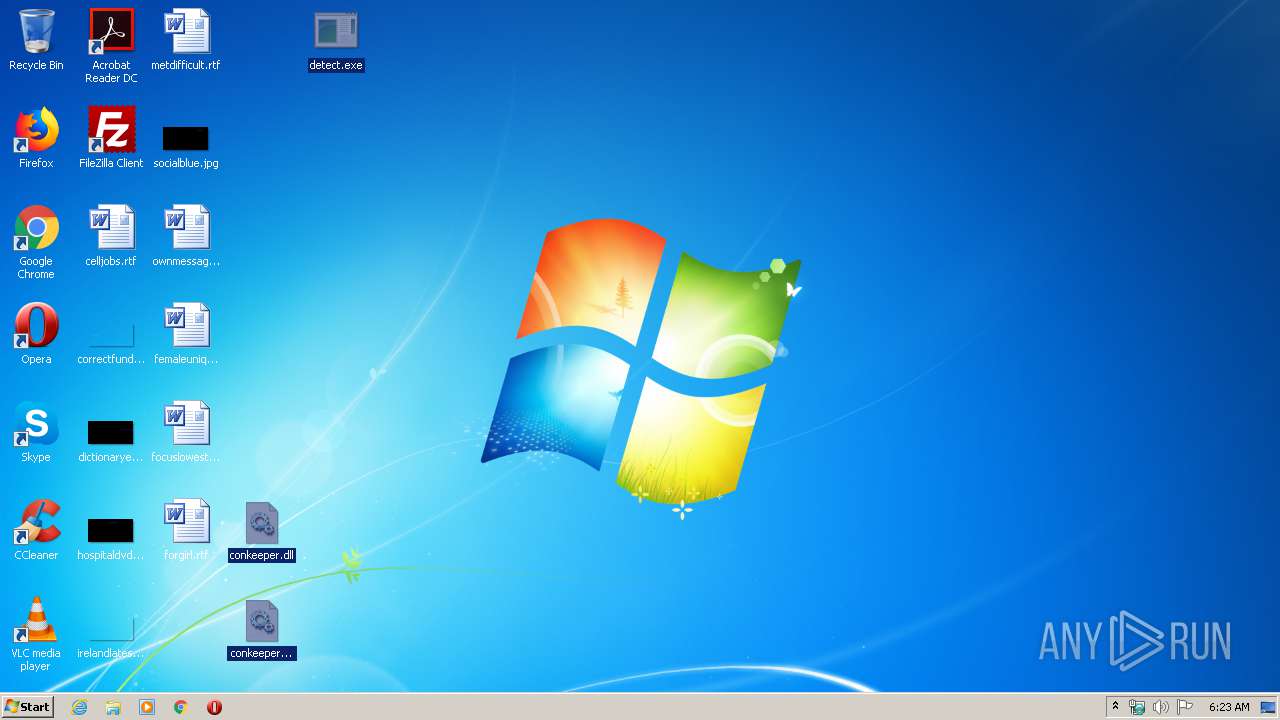
| File name: | Wedisk (2).zip |
| Full analysis: | https://app.any.run/tasks/96ae0278-c4d9-4c09-91bc-ea94d01d466d |
| Verdict: | Malicious activity |
| Analysis date: | April 07, 2020, 05:22:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | BE04716A2718DD387220592959235455 |
| SHA1: | 266F72070447ACC18A00199AA28135877A332861 |
| SHA256: | DBDD8FC2774ADBF7105042EF93E888ADEAE2BD63E3A15E62D9A3E7BECF8D6A67 |
| SSDEEP: | 12288:sTYAIOIHnBeFbK9AggtY3FuV5sG5k5EE7YEFW2qb:sTTSnoFPgVEKwa7YEUdb |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2460)
Application was dropped or rewritten from another process
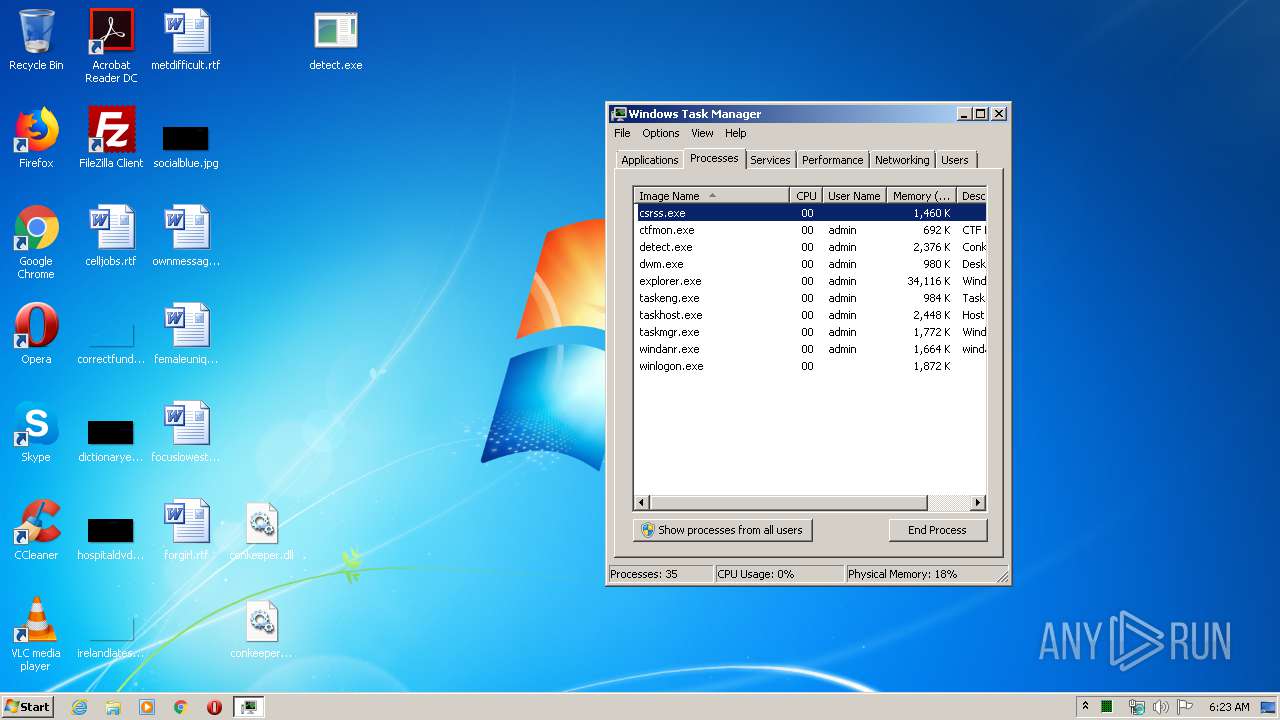
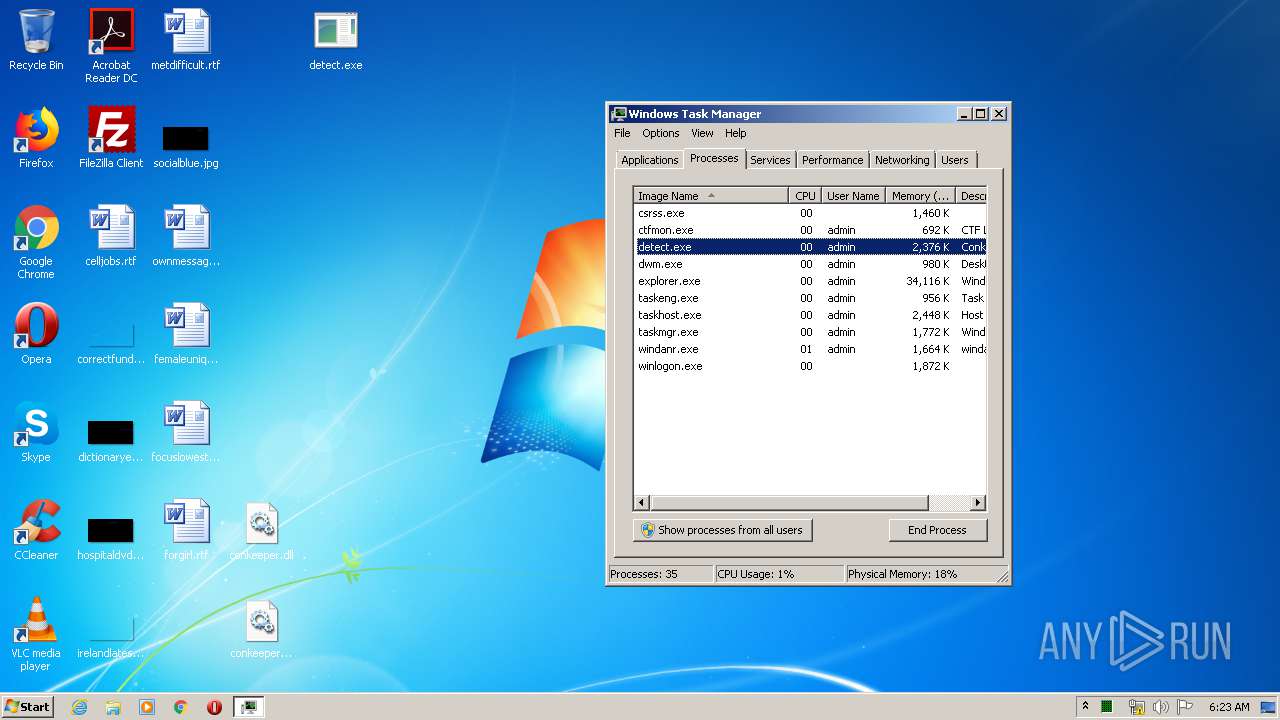
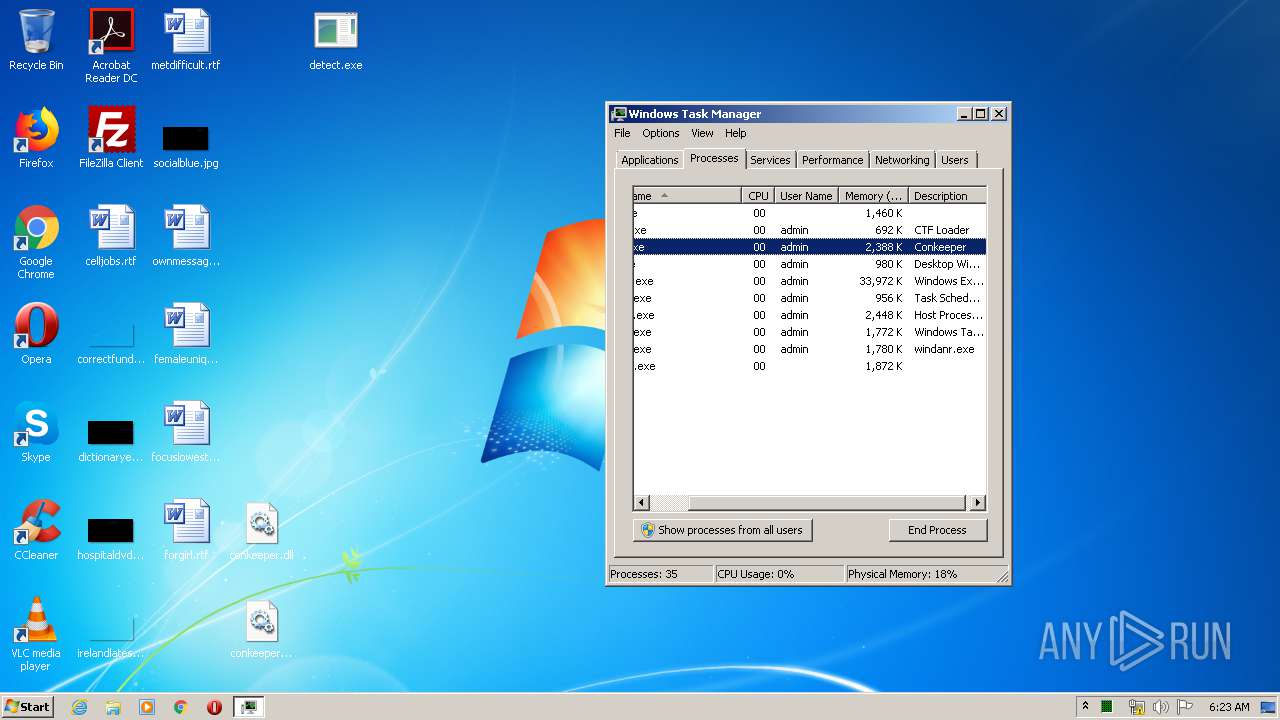
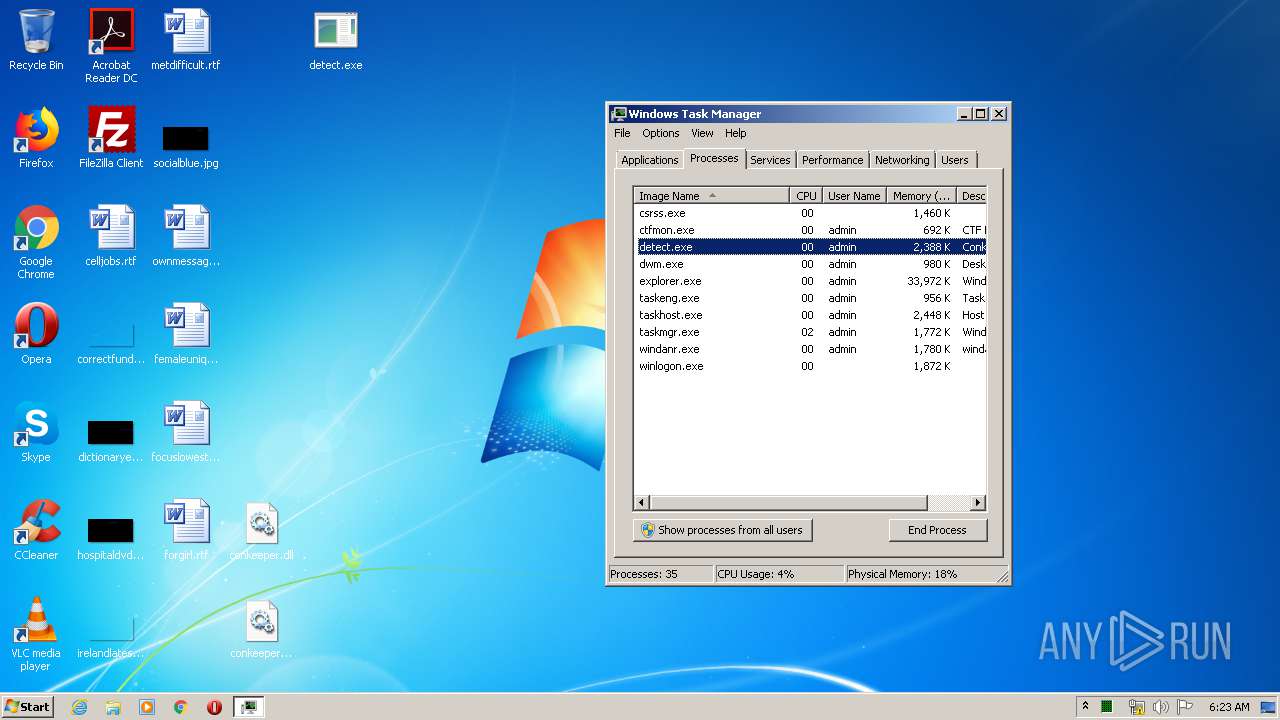
- detect.exe (PID: 1744)
SUSPICIOUS
No suspicious indicators.INFO
Manual execution by user
- taskmgr.exe (PID: 1944)
- detect.exe (PID: 1744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:07:01 23:36:25 |
| ZipCRC: | 0x2fd6d282 |
| ZipCompressedSize: | 92530 |
| ZipUncompressedSize: | 190464 |
| ZipFileName: | conkeeper.dll |
Total processes
40
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1744 | "C:\Users\admin\Desktop\detect.exe" | C:\Users\admin\Desktop\detect.exe | explorer.exe | ||||||||||||
User: admin Company: iMBC Integrity Level: HIGH Description: Conkeeper Exit code: 0 Version: 1.0.0.7 Modules
| |||||||||||||||
| 1944 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2460 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3840 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Wedisk (2).zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
487
Read events
466
Write events
21
Delete events
0
Modification events
| (PID) Process: | (3840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3840) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Wedisk (2).zip | |||
| (PID) Process: | (3840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF240100003A000000E40400002F020000 | |||
| (PID) Process: | (3840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
0
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3840 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3840.31128\conkeeper.dll | — | |
MD5:— | SHA256:— | |||
| 3840 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3840.31128\conkeeper64.dll | — | |
MD5:— | SHA256:— | |||
| 3840 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3840.31128\detect.exe | — | |
MD5:— | SHA256:— | |||
| 1744 | detect.exe | C:\Users\admin\AppData\Local\Conkeeper\chk.dat | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
2
Threats
6
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1744 | detect.exe | 211.233.27.53:443 | fil.conkeeper.co.kr | LG DACOM Corporation | KR | suspicious |
1744 | detect.exe | 211.233.27.57:443 | fil.conkeeper.co.kr | LG DACOM Corporation | KR | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fil.conkeeper.co.kr |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1744 | detect.exe | Potential Corporate Privacy Violation | ET POLICY Self Signed SSL Certificate (SomeOrganizationalUnit) |
1744 | detect.exe | Potential Corporate Privacy Violation | ET POLICY Self Signed SSL Certificate (SomeOrganizationalUnit) |
1744 | detect.exe | Potential Corporate Privacy Violation | ET POLICY Self Signed SSL Certificate (SomeOrganizationalUnit) |
1744 | detect.exe | Potential Corporate Privacy Violation | ET POLICY Self Signed SSL Certificate (SomeOrganizationalUnit) |
1744 | detect.exe | Potential Corporate Privacy Violation | ET POLICY Self Signed SSL Certificate (SomeOrganizationalUnit) |
1744 | detect.exe | Potential Corporate Privacy Violation | ET POLICY Self Signed SSL Certificate (SomeOrganizationalUnit) |