| File name: | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil |
| Full analysis: | https://app.any.run/tasks/5435c04d-5de6-4380-9ebe-aa23e1f22540 |
| Verdict: | Malicious activity |
| Analysis date: | May 19, 2025, 08:29:07 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 7 sections |
| MD5: | 14FBEDED3CAA1A5605E8C38F4B2797C6 |
| SHA1: | EC05441D83540FED97F34DC59780CA1AEE53734A |
| SHA256: | DBD6A6861C9ED2887648937B746532BE093A20915F3B34ABEF588A7EC7C64613 |
| SSDEEP: | 98304:3/NlZ50ywanr0y+ck0u+QG3g1SHAaN0/xjGS6w6KxLQyUg5sAO4Xm6NevZMKKVju:r8h4Co |
MALICIOUS
BITTORRENT has been detected (SURICATA)
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
Connects to the CnC server
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
SUSPICIOUS
Contacting a server suspected of hosting an CnC
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
Process drops legitimate windows executable
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
Reads Internet Explorer settings
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
Reads Microsoft Outlook installation path
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
Executable content was dropped or overwritten
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
Reads security settings of Internet Explorer
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
Potential Corporate Privacy Violation
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
There is functionality for taking screenshot (YARA)
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
INFO
Checks supported languages
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
- identity_helper.exe (PID: 7672)
Create files in a temporary directory
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
Reads the software policy settings
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
The sample compiled with english language support
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
Failed to create an executable file in Windows directory
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
Reads the computer name
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
- identity_helper.exe (PID: 7672)
Checks proxy server information
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
Creates files or folders in the user directory
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
Reads the machine GUID from the registry
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
Reads CPU info
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
Process checks computer location settings
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 5964)
- OpenWith.exe (PID: 8140)
- OpenWith.exe (PID: 7216)
- OpenWith.exe (PID: 7832)
- OpenWith.exe (PID: 7828)
- OpenWith.exe (PID: 7400)
- OpenWith.exe (PID: 7432)
- OpenWith.exe (PID: 7684)
- OpenWith.exe (PID: 5344)
- OpenWith.exe (PID: 472)
Manual execution by a user
- OpenWith.exe (PID: 8140)
- OpenWith.exe (PID: 5964)
- msedge.exe (PID: 8088)
- OpenWith.exe (PID: 7216)
- OpenWith.exe (PID: 7832)
- OpenWith.exe (PID: 472)
- OpenWith.exe (PID: 7828)
- OpenWith.exe (PID: 7432)
- OpenWith.exe (PID: 7684)
- OpenWith.exe (PID: 5344)
- OpenWith.exe (PID: 7504)
- OpenWith.exe (PID: 6824)
- OpenWith.exe (PID: 7400)
Application launched itself
- msedge.exe (PID: 6584)
- Acrobat.exe (PID: 4180)
- AcroCEF.exe (PID: 2516)
Reads Environment values
- identity_helper.exe (PID: 7672)
UPX packer has been detected
- 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe (PID: 2904)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 7400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (24) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (3.7) |
| .exe | | | Win32 Executable (generic) (2.6) |
| .exe | | | Generic Win/DOS Executable (1.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:01:17 07:12:12+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 8433664 |
| InitializedDataSize: | 5752320 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x451f3f |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.45.1.17 |
| ProductVersionNumber: | 1.45.1.17 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | www.BitComet.com |
| FileDescription: | BitComet - a BitTorrent Client |
| FileVersion: | 1.45 |
| InternalName: | BitComet.exe |
| LegalCopyright: | Copyright(C) 2003-2016 All Rights Reserved. |
| ProductName: | BitComet |
| ProductVersion: | 1.45 |
Total processes
187
Monitored processes
64
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
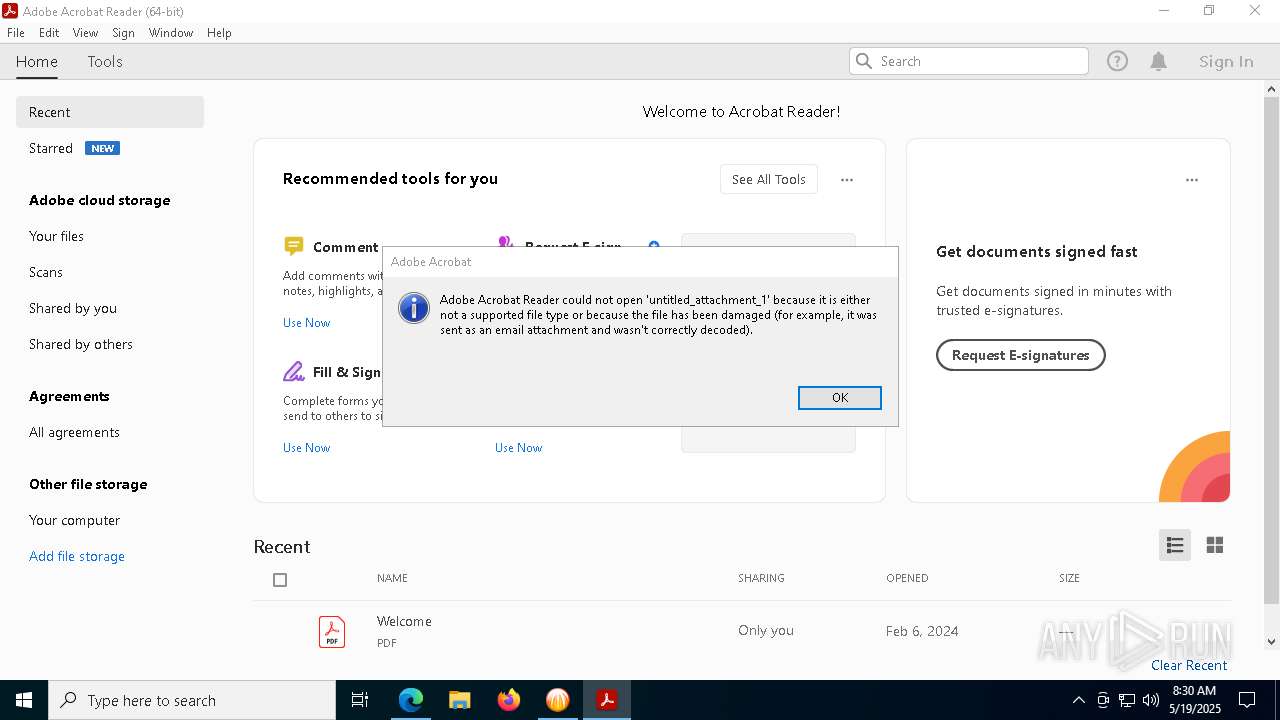
| 472 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\untitled_attachment_0 | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --no-appcompat-clear --mojo-platform-channel-handle=3680 --field-trial-handle=2440,i,14123274991439134233,14774706477078454781,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1132 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2768 --field-trial-handle=2440,i,14123274991439134233,14774706477078454781,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2340 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2584 --field-trial-handle=2440,i,14123274991439134233,14774706477078454781,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2516 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2644 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2904 --field-trial-handle=1616,i,6948450287174761107,5934598072214693527,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2904 | "C:\Users\admin\Desktop\2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe" | C:\Users\admin\Desktop\2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | explorer.exe | ||||||||||||
User: admin Company: www.BitComet.com Integrity Level: MEDIUM Description: BitComet - a BitTorrent Client Version: 1.45 Modules
| |||||||||||||||
| 3020 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=1372 --field-trial-handle=2440,i,14123274991439134233,14774706477078454781,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3268 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6772 --field-trial-handle=2440,i,14123274991439134233,14774706477078454781,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
35 299
Read events
35 154
Write events
139
Delete events
6
Modification events
| (PID) Process: | (2904) 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2904) 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2904) 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2904) 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\BitComet\BitComet |
| Operation: | write | Name: | CaptureIEDownload |
Value: 1 | |||
| (PID) Process: | (2904) 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\BitComet\BitComet |
| Operation: | write | Name: | IEMoniterFileExt |
Value: .zip;.rar;.iso;.exe;.asf;.avi;.mp3;.mpg;.rm;.rmvb;.wmv;.wma;.msi | |||
| (PID) Process: | (2904) 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\MenuExt\&D&ownload &with BitComet |
| Operation: | write | Name: | contexts |
Value: 34 | |||
| (PID) Process: | (2904) 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\MenuExt\&D&ownload &with BitComet |
| Operation: | write | Name: | BitCometCreated |
Value: 1 | |||
| (PID) Process: | (2904) 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\MenuExt\&D&ownload &with BitComet |
| Operation: | write | Name: | MenuID |
Value: ID_DOWNLOAD_LINK | |||
| (PID) Process: | (2904) 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\MenuExt\&D&ownload all with BitComet |
| Operation: | write | Name: | contexts |
Value: 243 | |||
| (PID) Process: | (2904) 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\MenuExt\&D&ownload all with BitComet |
| Operation: | write | Name: | BitCometCreated |
Value: 1 | |||
Executable files
10
Suspicious files
261
Text files
55
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | C:\Users\admin\AppData\Roaming\BitComet\fav\passport_info_zh_CN.mht | binary | |
MD5:FC6590DB6D1F50291804E70D8883C436 | SHA256:0C1B05A2B9BA99BF4E862C175C5D554E800130C254EA01947BAF96911914DAC4 | |||
| 2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\17ea251bb40e52f.customDestinations-ms | binary | |
MD5:43AE50921DD3891F73B534BB06453AE3 | SHA256:A210BAF1553AA73FE3FC4E139962E47CADDAD5E96A0CDE5C6648B3192A6B2437 | |||
| 2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | C:\Users\admin\AppData\Local\Temp\A1D26E2\D4594CCB58.tmp | executable | |
MD5:3A081EF04B92D90D621E9E7F1288A412 | SHA256:7828AD15CEDFB8431EC377730F16CAF4CB13E4272ED9C91860423B9AD7F77A9B | |||
| 2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | C:\Users\admin\AppData\Roaming\BitComet\fav\passport_login_zh_CN.mht | binary | |
MD5:6E99A0B0A9C54E9653B3A467D43C190D | SHA256:013815C6EBF911C7B4B5645659685F36BBD1BECE26DD701C2A33BB4F3AF5EC63 | |||
| 2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | C:\Users\admin\AppData\Roaming\BitComet\fav\passport_info_en_US.mht | binary | |
MD5:1522A605F1EF6AB932AA62825D55A42D | SHA256:7874727953375A578EC58B9B02A56C4C1D6A191CCF38B4B1F22B6F8F9671E64C | |||
| 2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | C:\Users\admin\AppData\Roaming\BitComet\fav\passport_login_en_US.mht | binary | |
MD5:444A95F84BB23D8C84F15E053C08075C | SHA256:9ABFC3F7D1C1FB8AB71F8787D2DBA8CCC588D6DAE582493E78BD167531899FB6 | |||
| 2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\login_7.gif | image | |
MD5:D3D7E9F65FB43D0496AD19E4CB275B7A | SHA256:50207EFA8ACEC9A590F7B9D8727DDB586DE9E770DA13D092DA38D1E33EE73CB0 | |||
| 2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | C:\Users\admin\Desktop\BitComet.xml | xml | |
MD5:586FA1032CADE52B414C474E47121399 | SHA256:7A5A5060E211ACDB0B8DC1C9838C8AC503E45673BE0D8EB0C84154CE2EEB363D | |||
| 2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | C:\Users\admin\Desktop\cache\post_info.db-journal | binary | |
MD5:A8F0AD187DB2111FB9E530AF57361E4C | SHA256:A2E421BB5C338BDADD0D19658188419322AE9AA3CFFB1B5F9AFC8B50F6480316 | |||
| 2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\7LFXWVHVYCC6R9JFTDFF.temp | binary | |
MD5:43AE50921DD3891F73B534BB06453AE3 | SHA256:A210BAF1553AA73FE3FC4E139962E47CADDAD5E96A0CDE5C6648B3192A6B2437 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
109
DNS requests
78
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | GET | 403 | 72.14.178.174:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | GET | 200 | 138.199.168.42:80 | http://inside.bitcomet.com/start/en_us/1.45/ | unknown | — | — | unknown |
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | GET | 403 | 72.14.178.174:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | GET | 200 | 138.199.168.42:80 | http://update.bitcomet.com/client/bitcomet/passport/v0.89-v1.52/passport_login_en_us.mht | unknown | — | — | unknown |
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | GET | 200 | 138.199.168.42:80 | http://update.bitcomet.com/client/bitcomet/passport/v0.89-v1.52/passport_info_en_us.mht | unknown | — | — | unknown |
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | GET | 200 | 138.199.168.42:80 | http://update.bitcomet.com/client/bitcomet/?ver=1.45&intl=en_us&osintl=en_us&cid=5ff00f6c9607d73131b97d4810f09606&btcnt=0&httpcnt=0&p=x86 | unknown | — | — | unknown |
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | GET | 200 | 138.199.168.42:80 | http://update.bitcomet.com/client/bitcomet/fav/v1.05-v1.40/fav_en_us.xml | unknown | — | — | unknown |
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | GET | 404 | 34.89.91.10:80 | http://tracker.p2pcache.org/issupported | unknown | — | — | unknown |
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | GET | 403 | 72.14.178.174:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | GET | 403 | 72.14.178.174:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | 72.14.178.174:80 | www.aieov.com | Linode, LLC | US | malicious |
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | 67.215.246.10:6881 | router.bittorrent.com | — | — | whitelisted |
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | 138.199.168.42:80 | inside.bitcomet.com | — | DE | suspicious |
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | 142.250.185.72:443 | www.googletagmanager.com | GOOGLE | US | whitelisted |
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | 95.111.225.211:443 | apphit.com | Contabo GmbH | DE | unknown |
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | 34.89.91.10:80 | tracker.p2pcache.org | GOOGLE-CLOUD-PLATFORM | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
5isohu.com |
| whitelisted |
www.aieov.com |
| malicious |
router.bittorrent.com |
| whitelisted |
router.bitcomet.net |
| unknown |
inside.bitcomet.com |
| unknown |
www.googletagmanager.com |
| whitelisted |
apphit.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | Malware Command and Control Activity Detected | MALWARE [ANY.RUN] Possible Floxif CnC Communication |
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | Misc activity | INFO [ANY.RUN] P2P BitTorrent Protocol |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | Malware Command and Control Activity Detected | MALWARE [ANY.RUN] Possible Floxif CnC Communication |
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | Potential Corporate Privacy Violation | ET INFO Unsupported/Fake Windows NT Version 5.0 |
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | Potential Corporate Privacy Violation | ET INFO Unsupported/Fake Windows NT Version 5.0 |
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | Malware Command and Control Activity Detected | MALWARE [ANY.RUN] Possible Floxif CnC Communication |
2340 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2340 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2904 | 2025-05-19_14fbeded3caa1a5605e8c38f4b2797c6_black-basta_darkgate_elex_floxif_luca-stealer_poet-rat_remcos_revil.exe | Malware Command and Control Activity Detected | MALWARE [ANY.RUN] Possible Floxif CnC Communication |