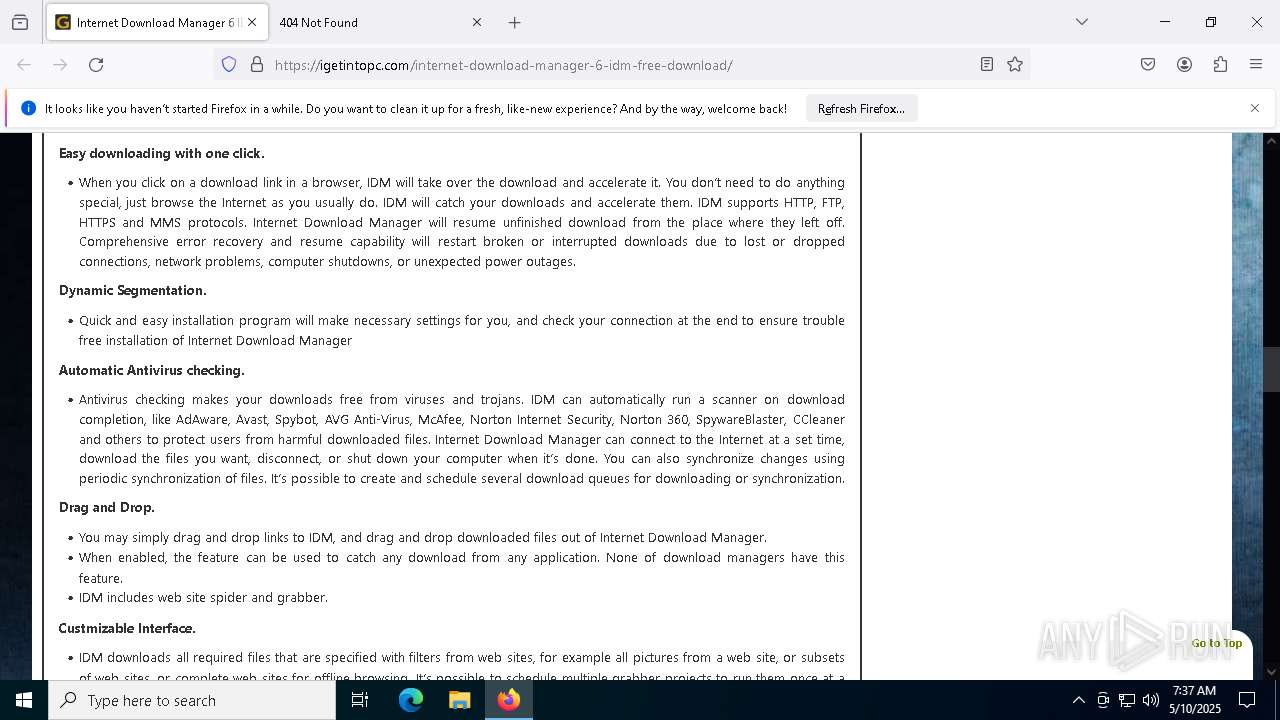
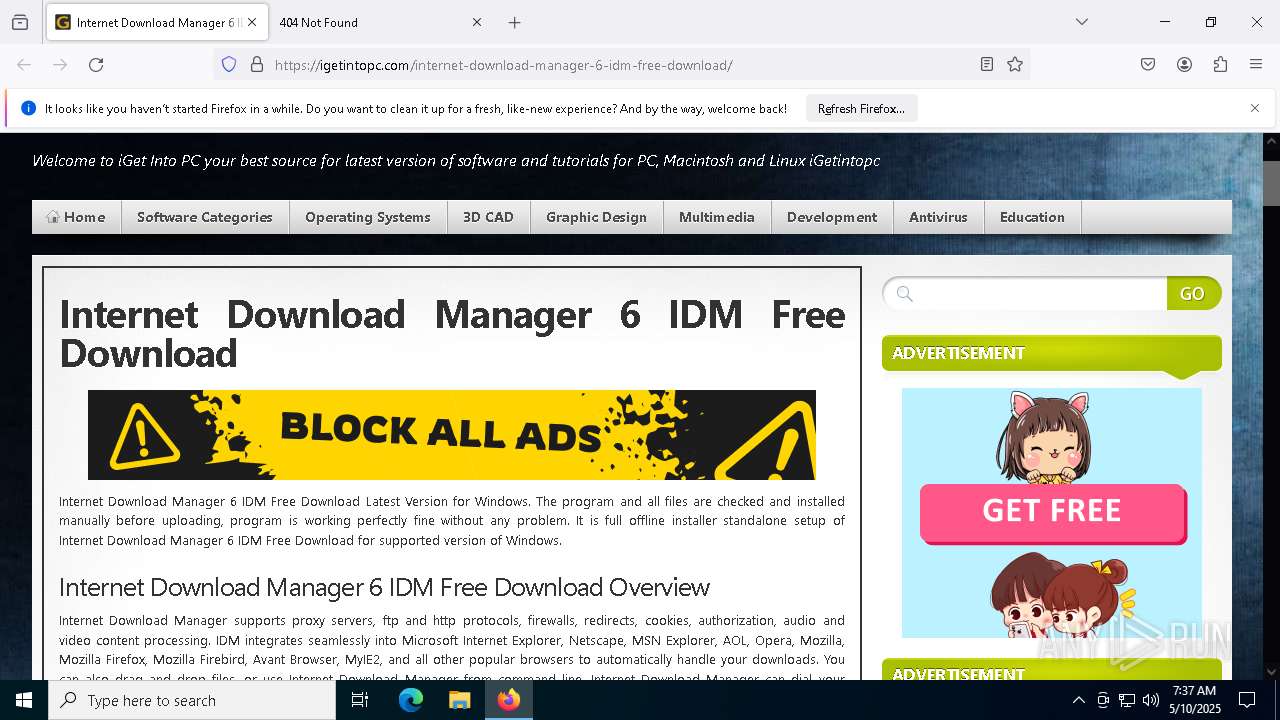
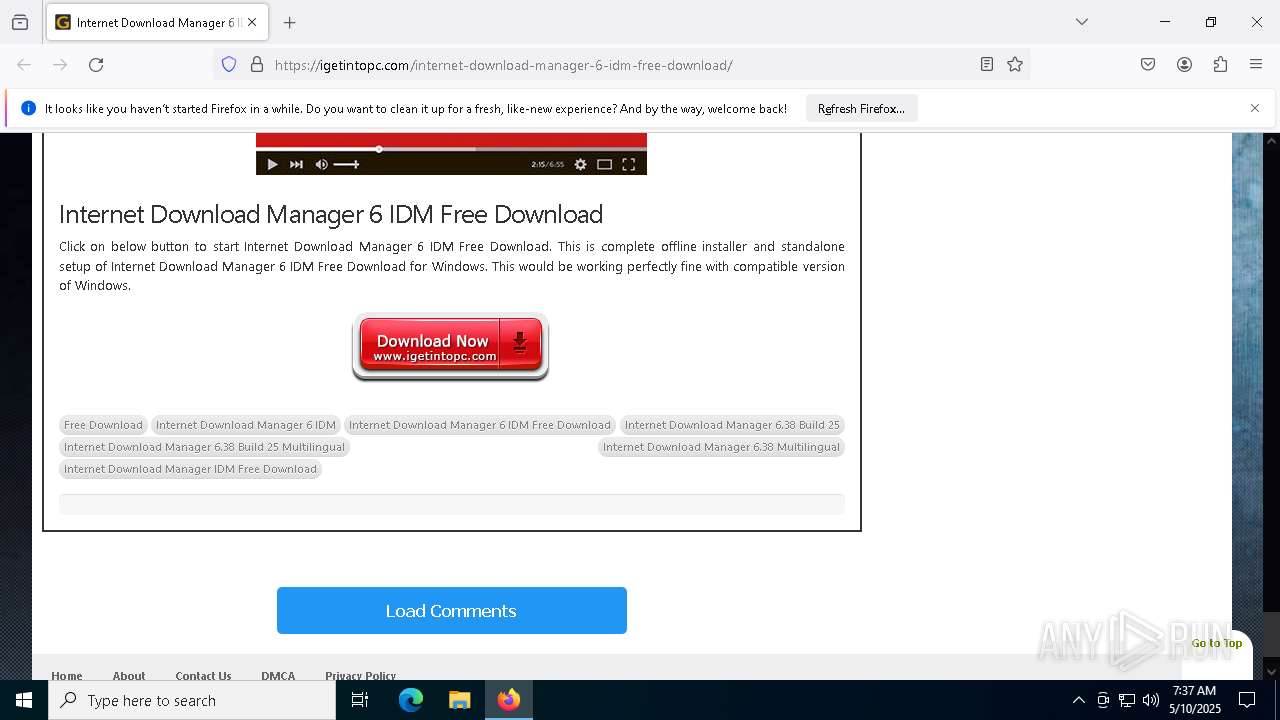
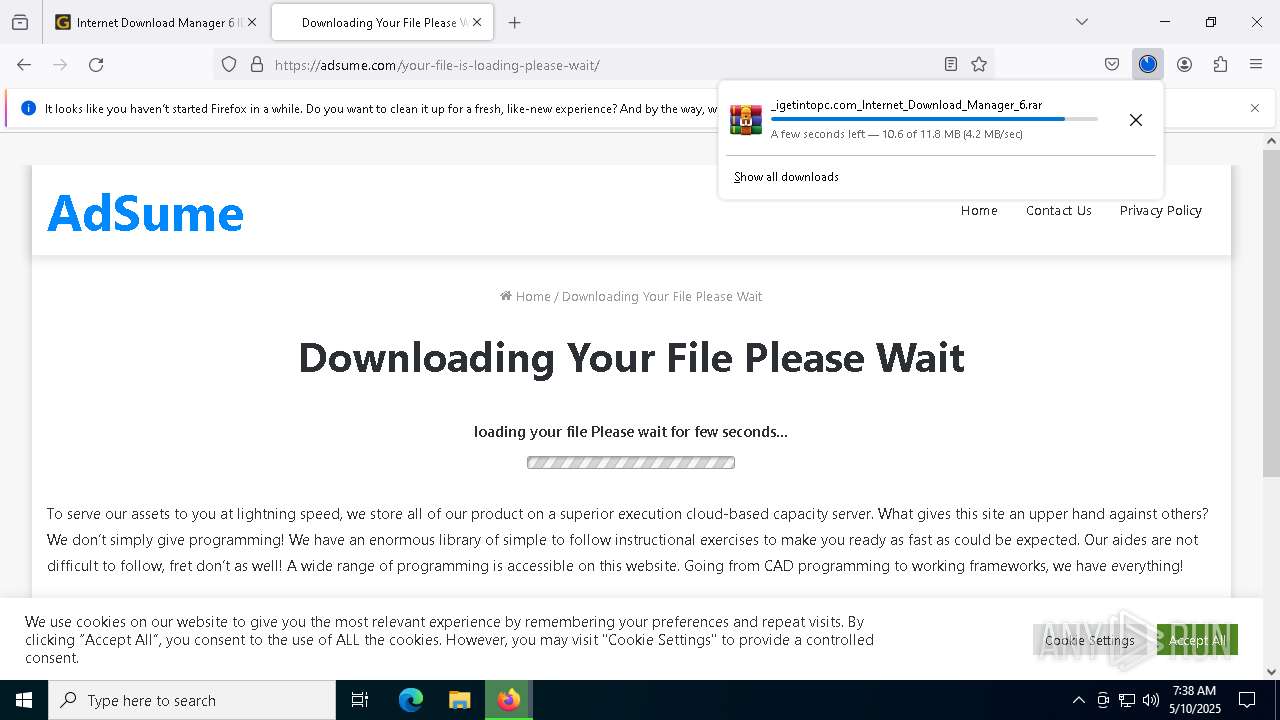
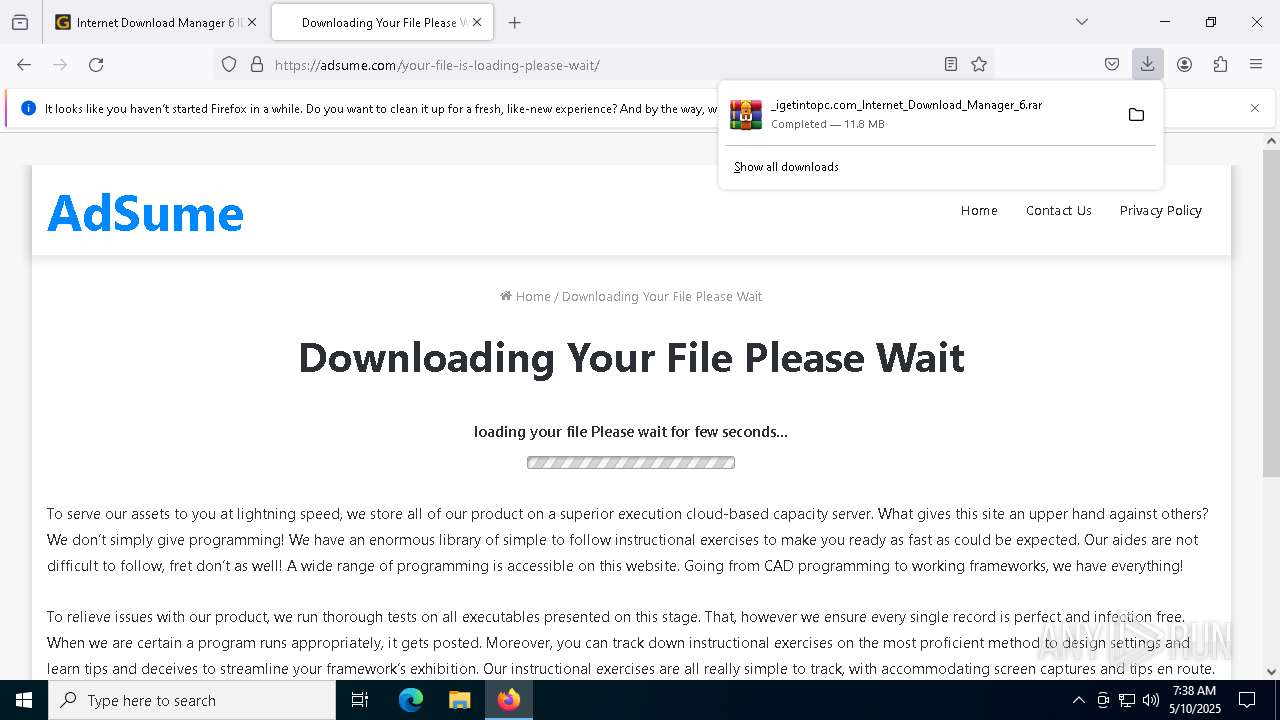
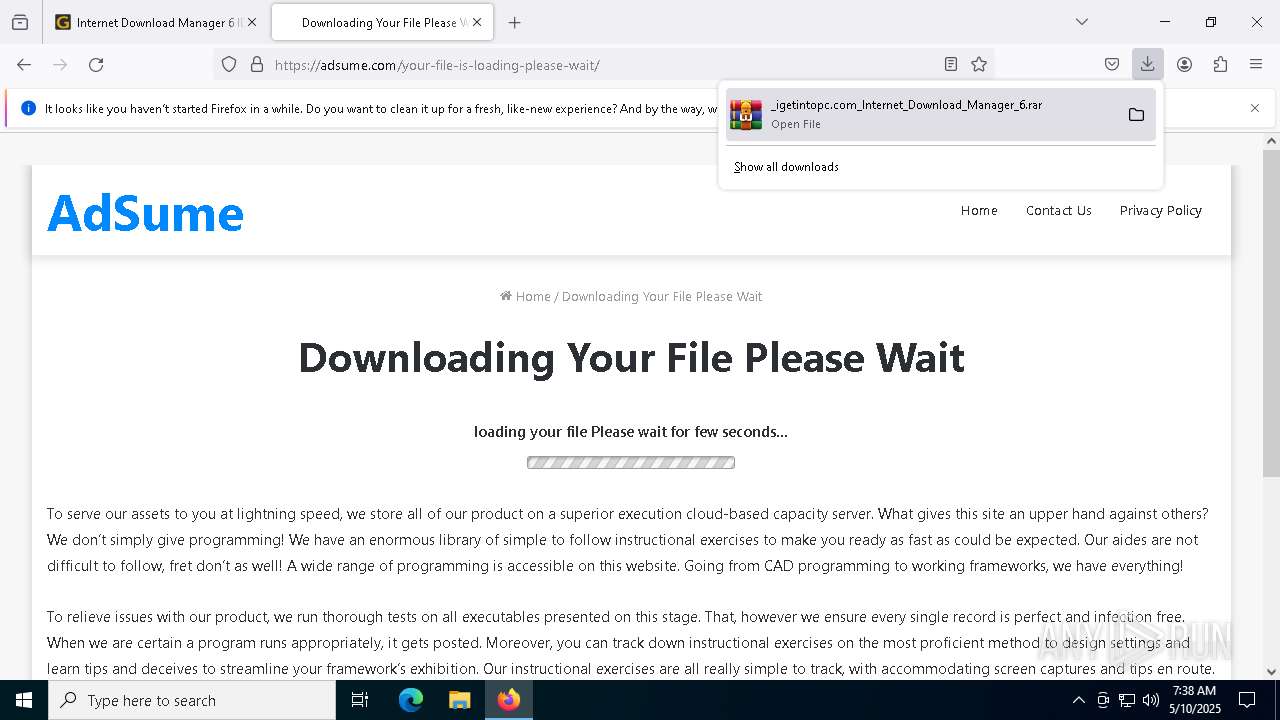
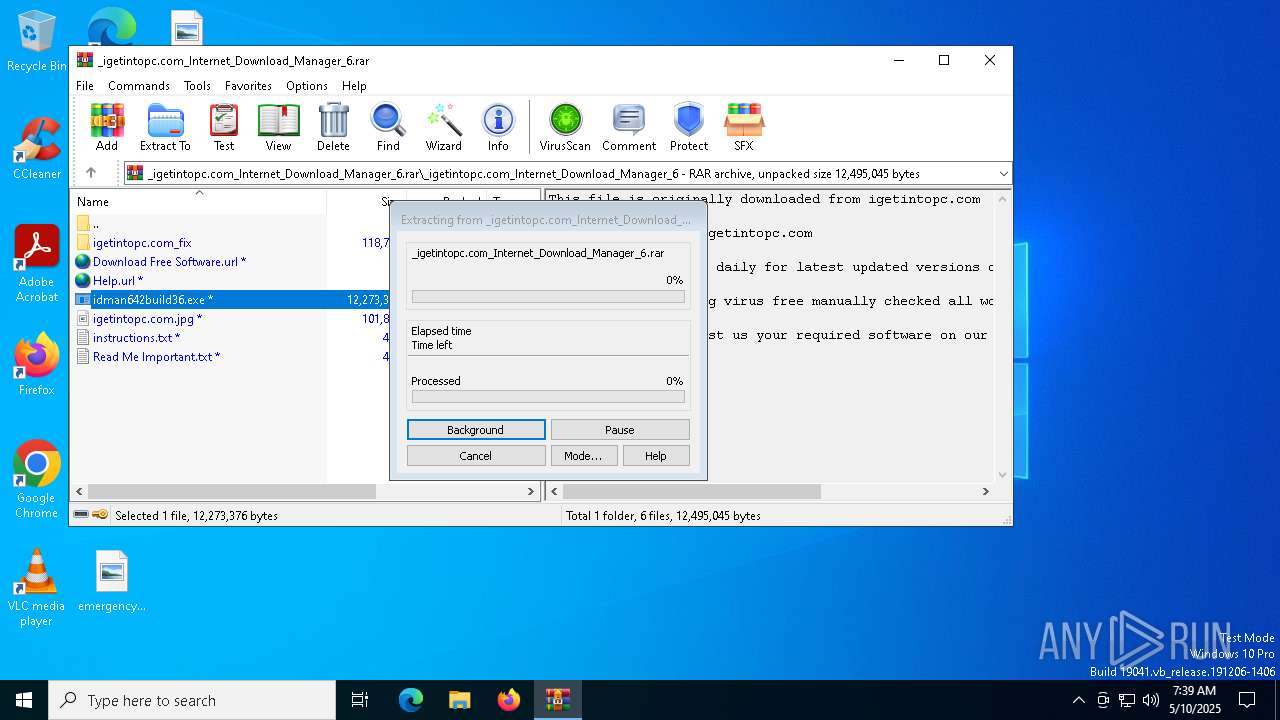
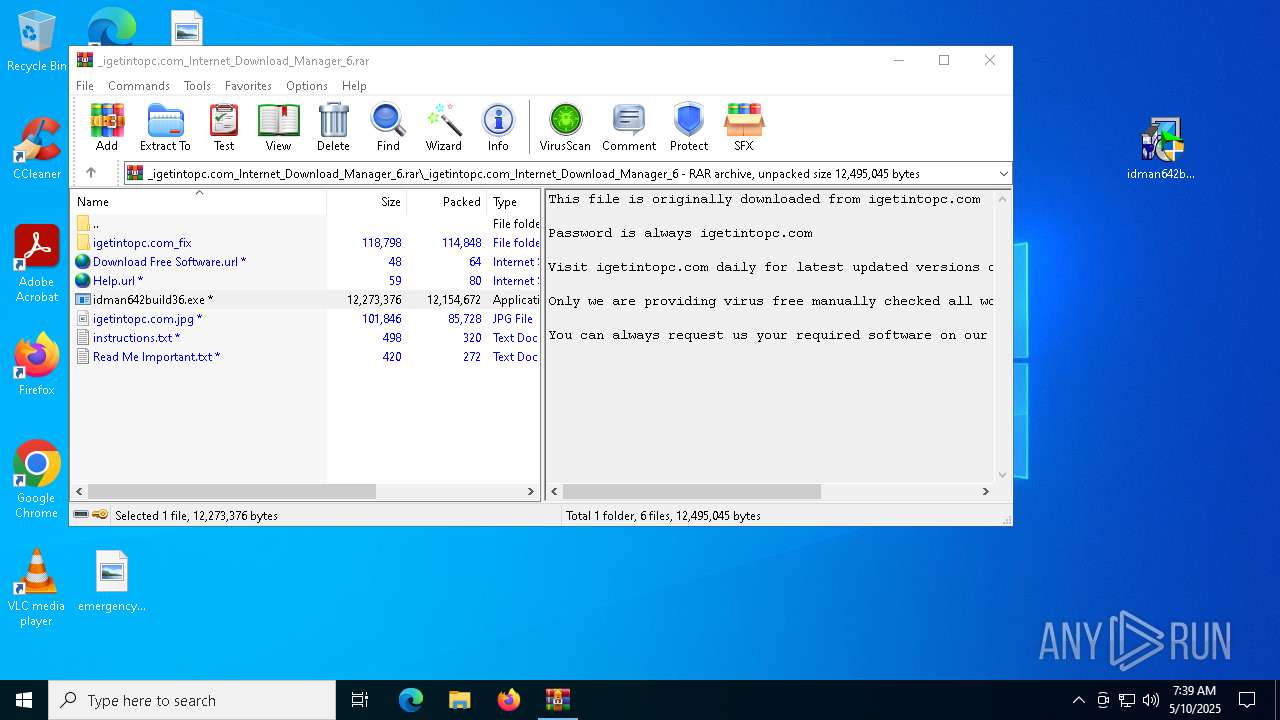
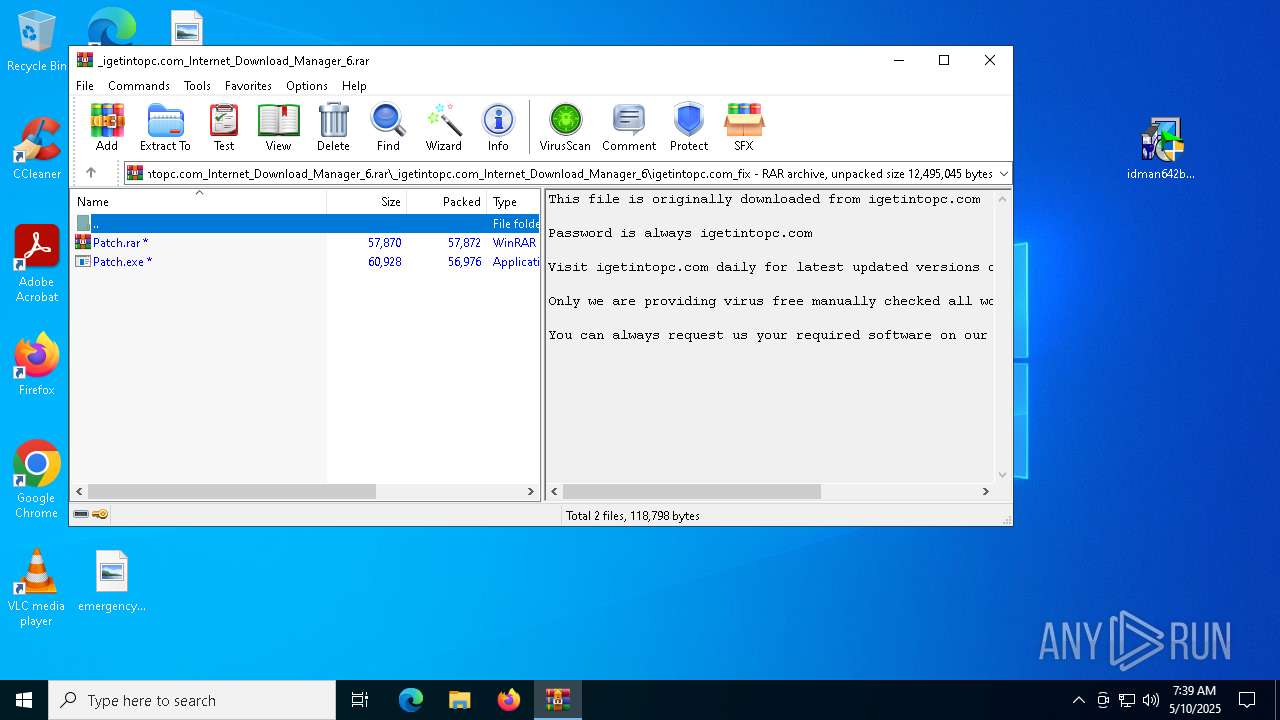
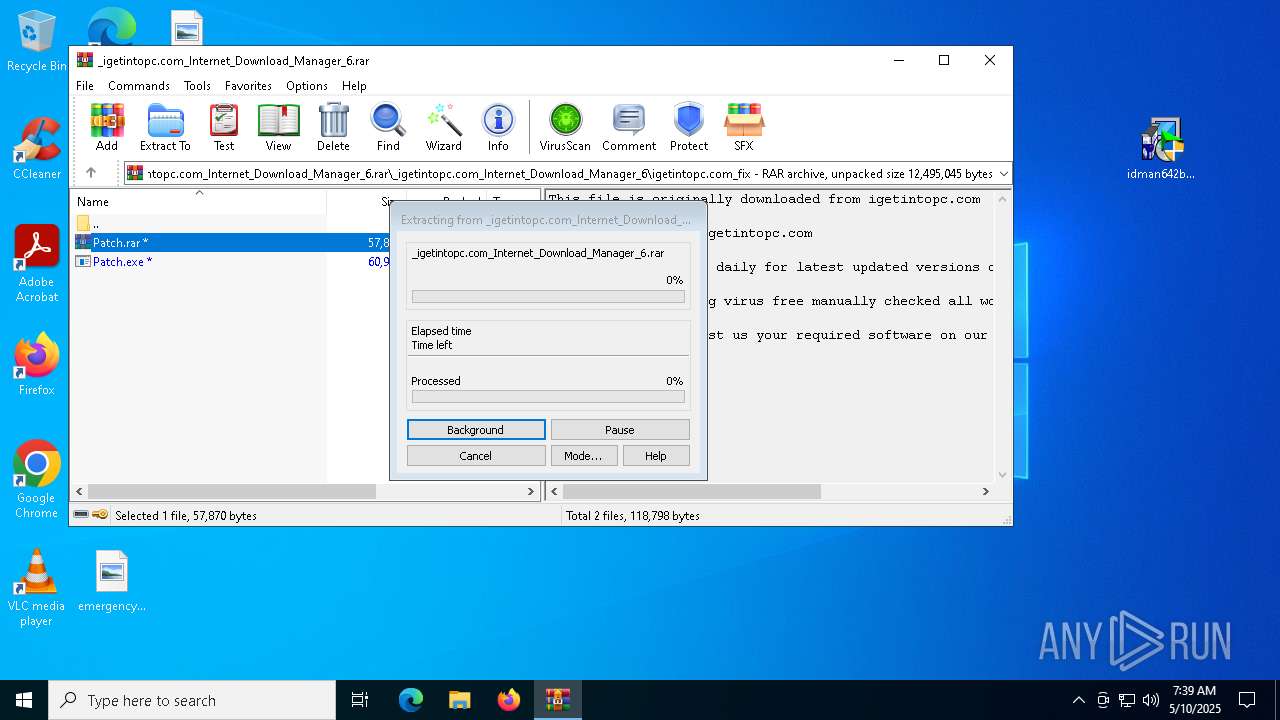
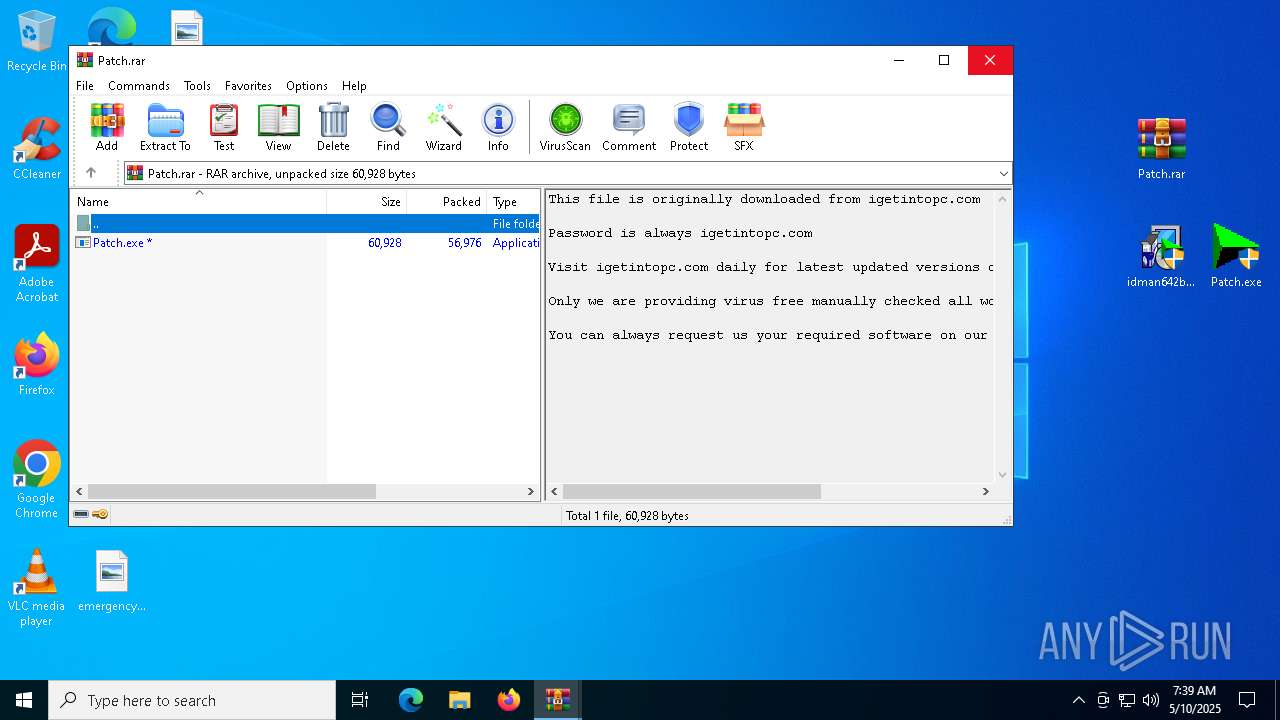
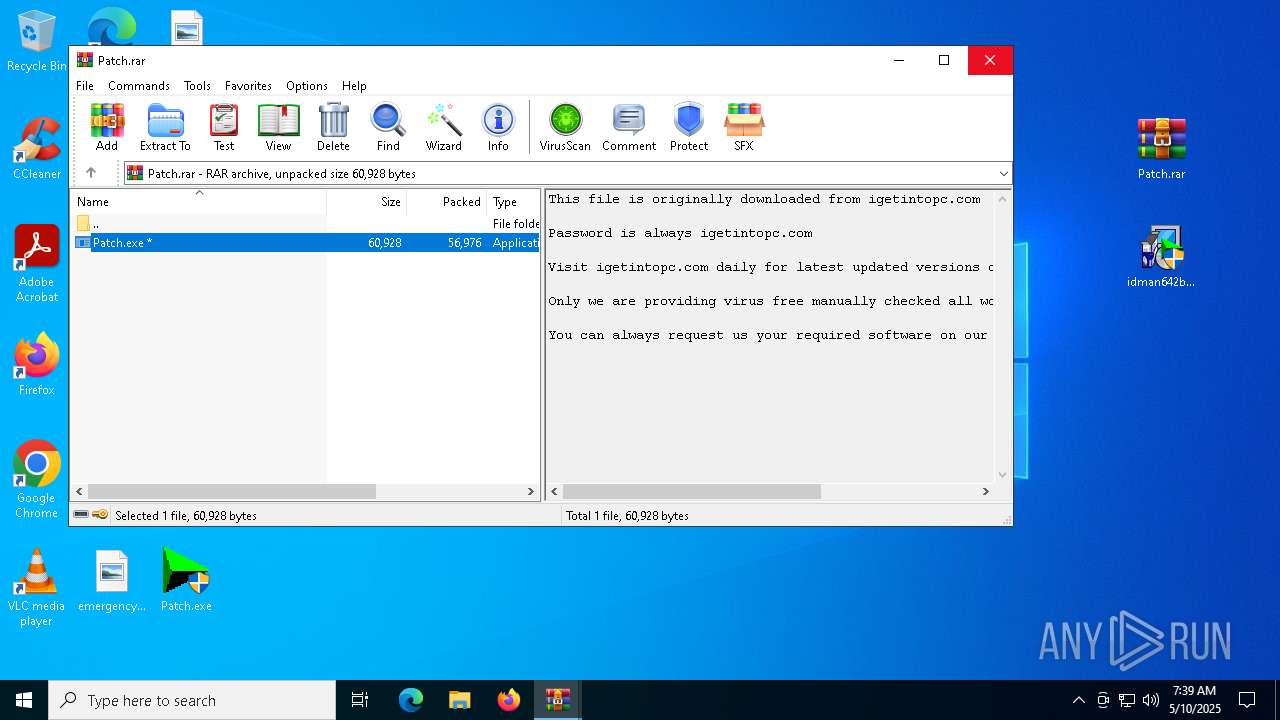
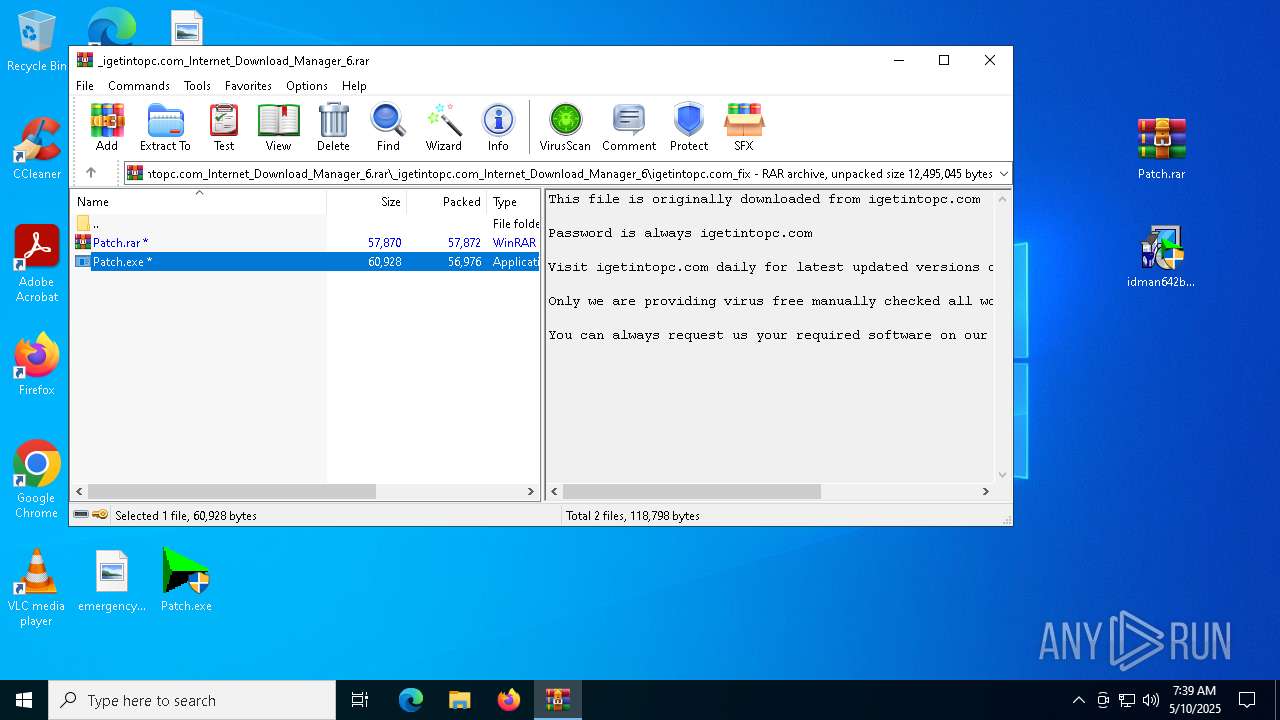
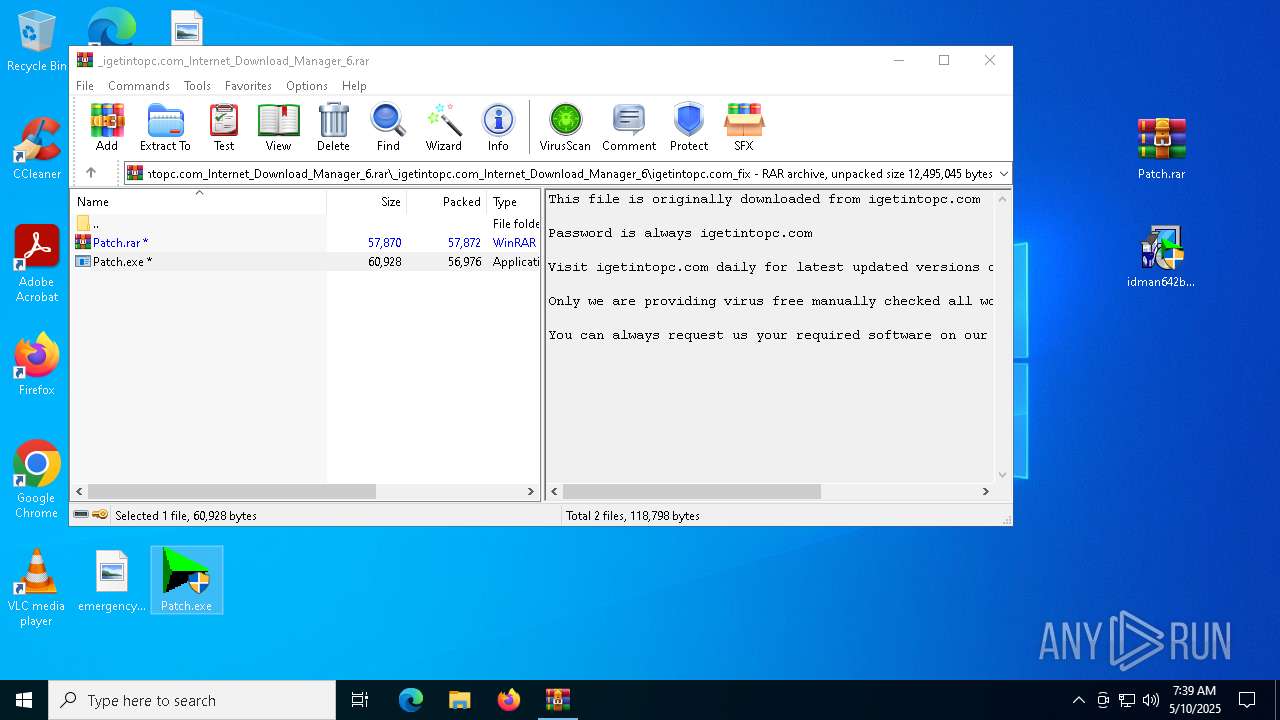
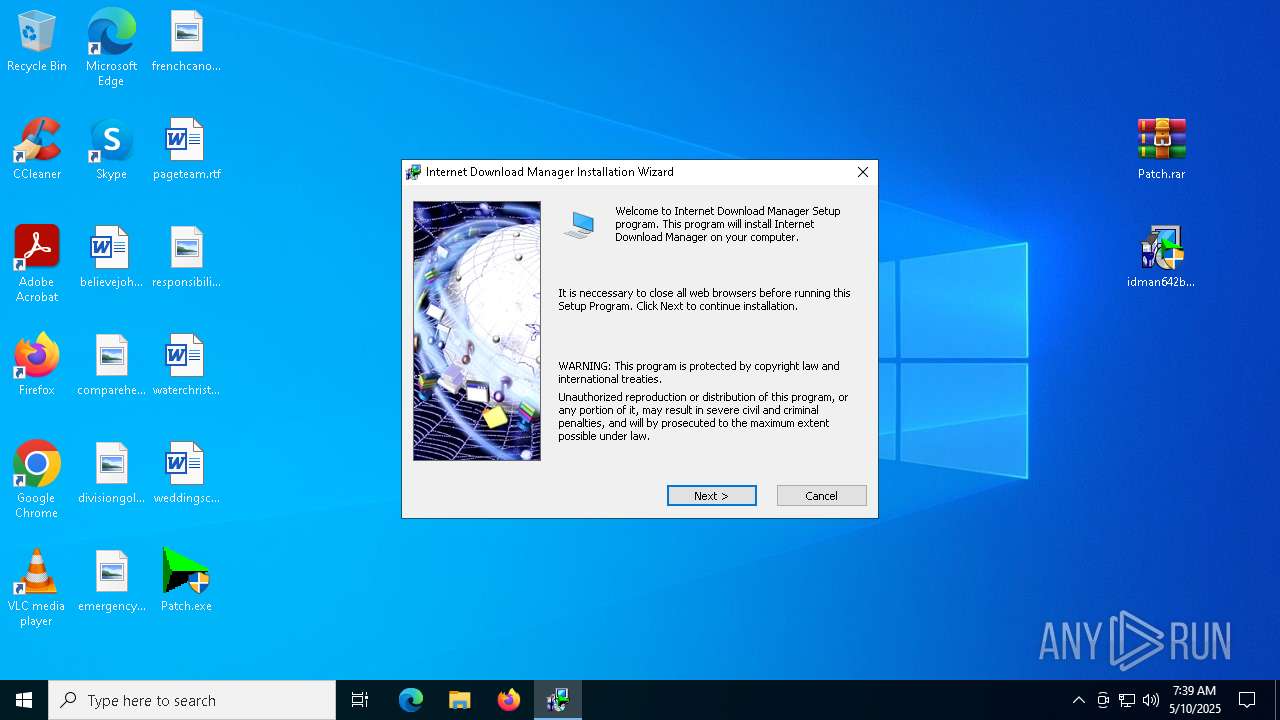
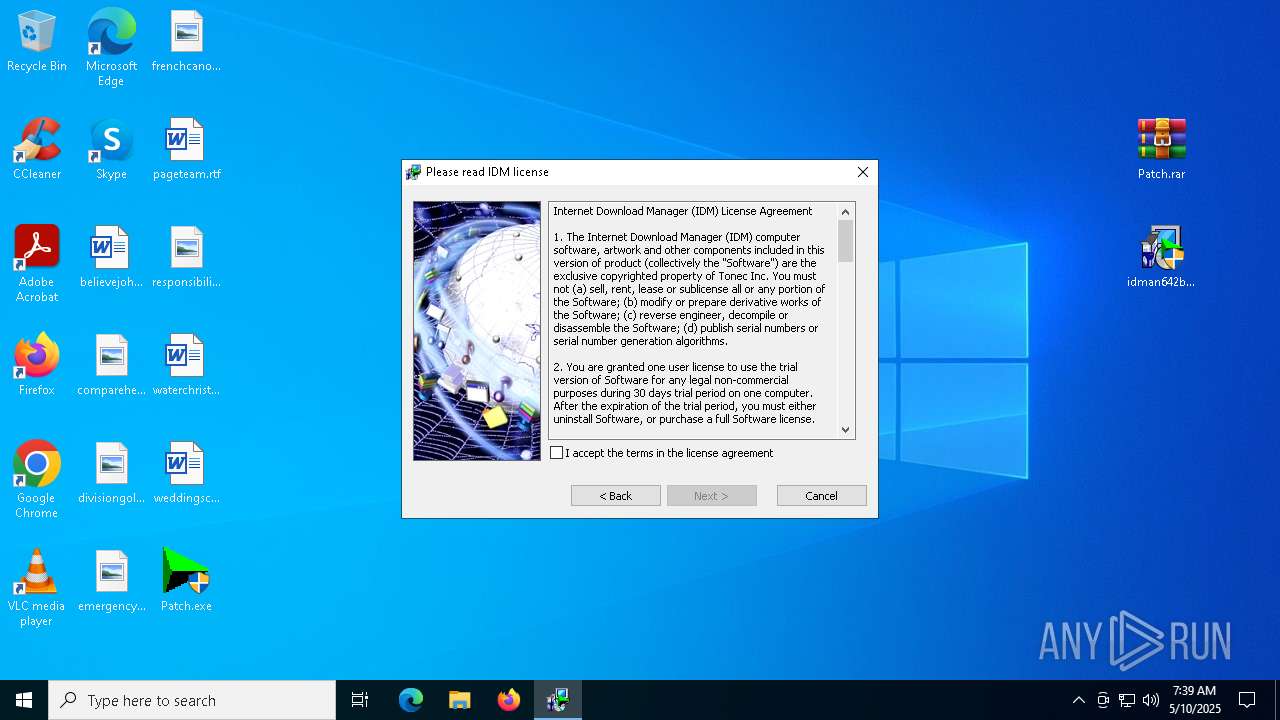
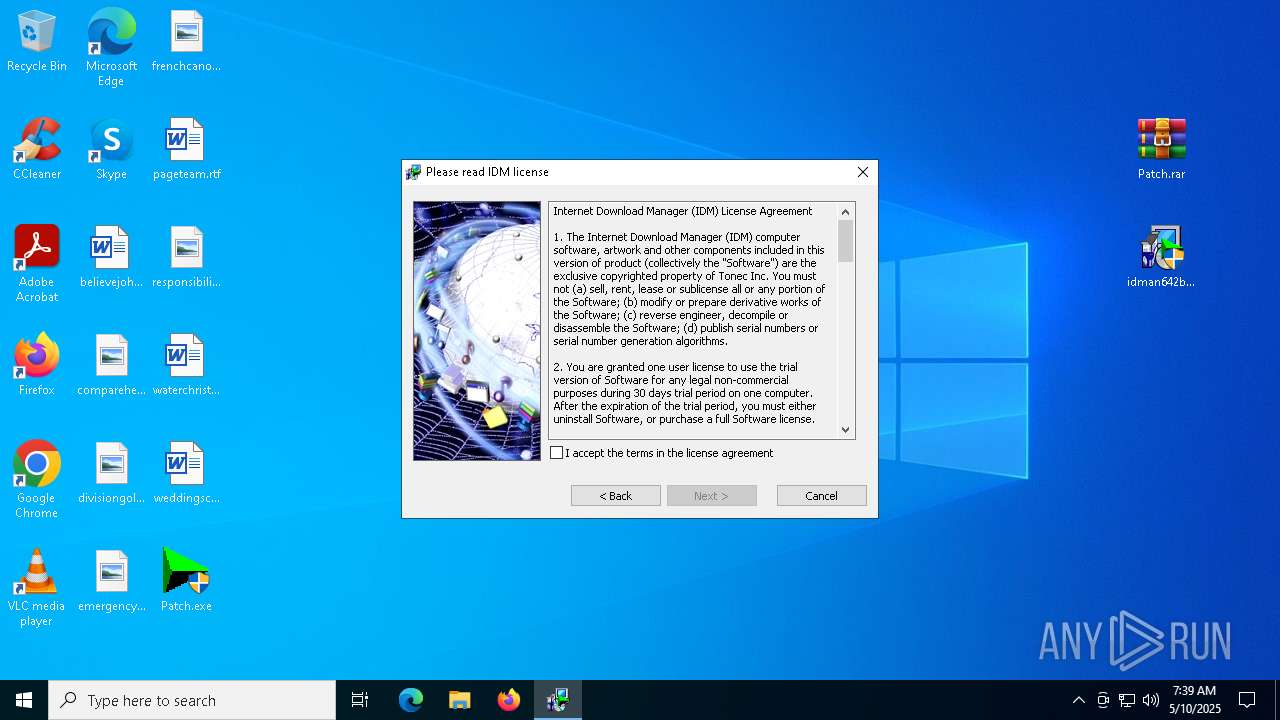
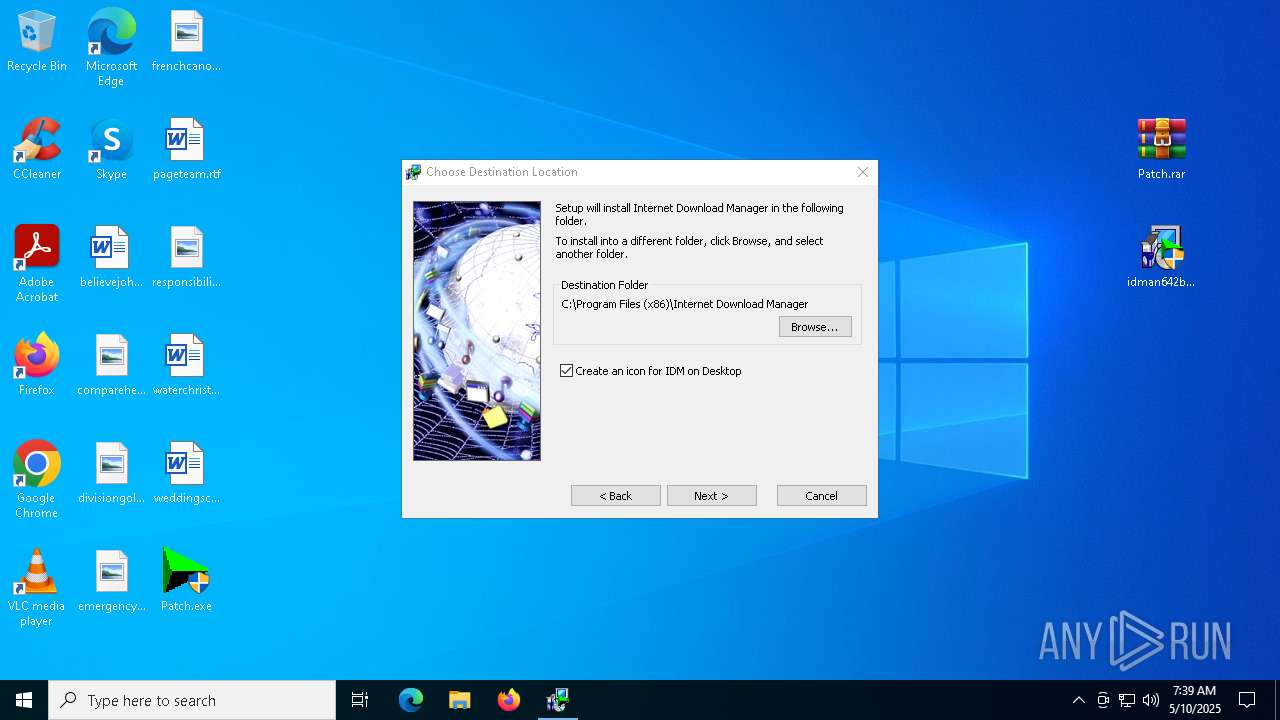
| URL: | https://igetintopc.com/internet-download-manager-6-idm-free-download/ |
| Full analysis: | https://app.any.run/tasks/874d1122-a077-456c-83a8-c0f9f817e829 |
| Verdict: | Malicious activity |
| Analysis date: | May 10, 2025, 07:36:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MD5: | 3A93F5315C8940C9256867660075269D |
| SHA1: | 311CBF59A8DA4F67106EF695306DB442DDA196C5 |
| SHA256: | DBCB7EB279ECDD34D52F4E575C75CB301B991DCD56C40C6B2C23678F7DB35568 |
| SSDEEP: | 3:N8LjLdIKuEmIDXuVLSBFmn:2L5uGDXuVW2 |
MALICIOUS
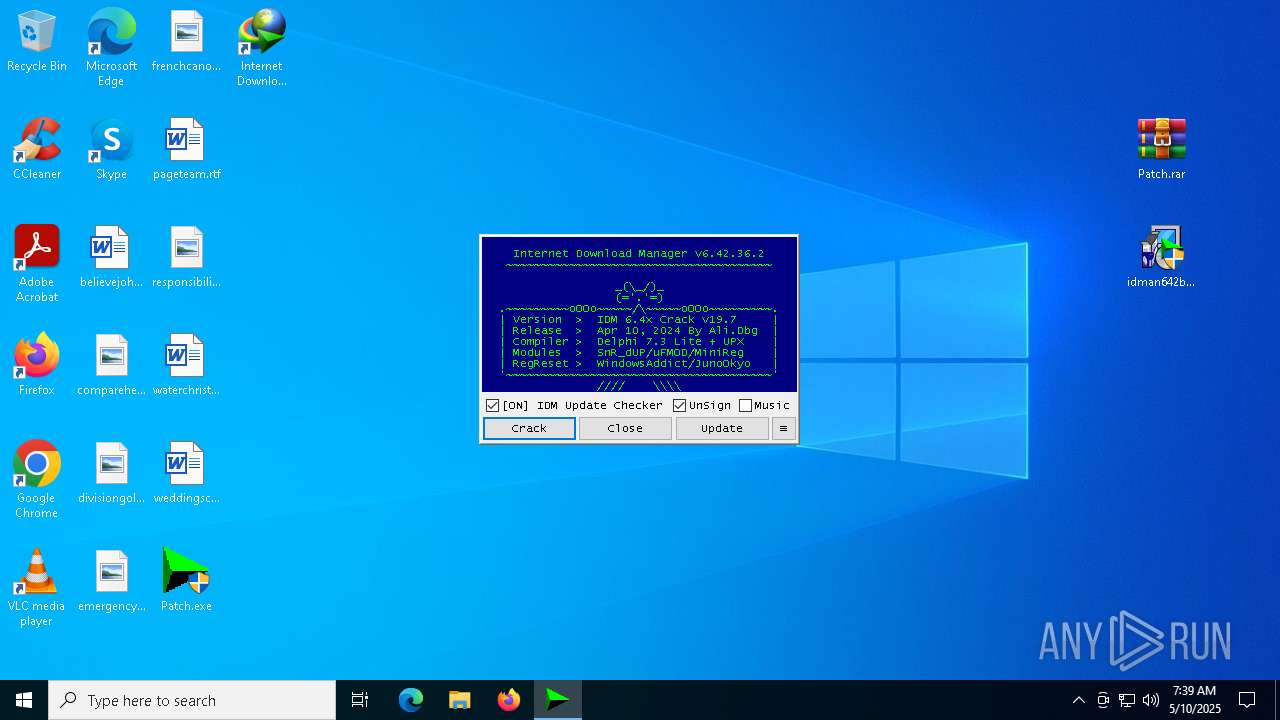
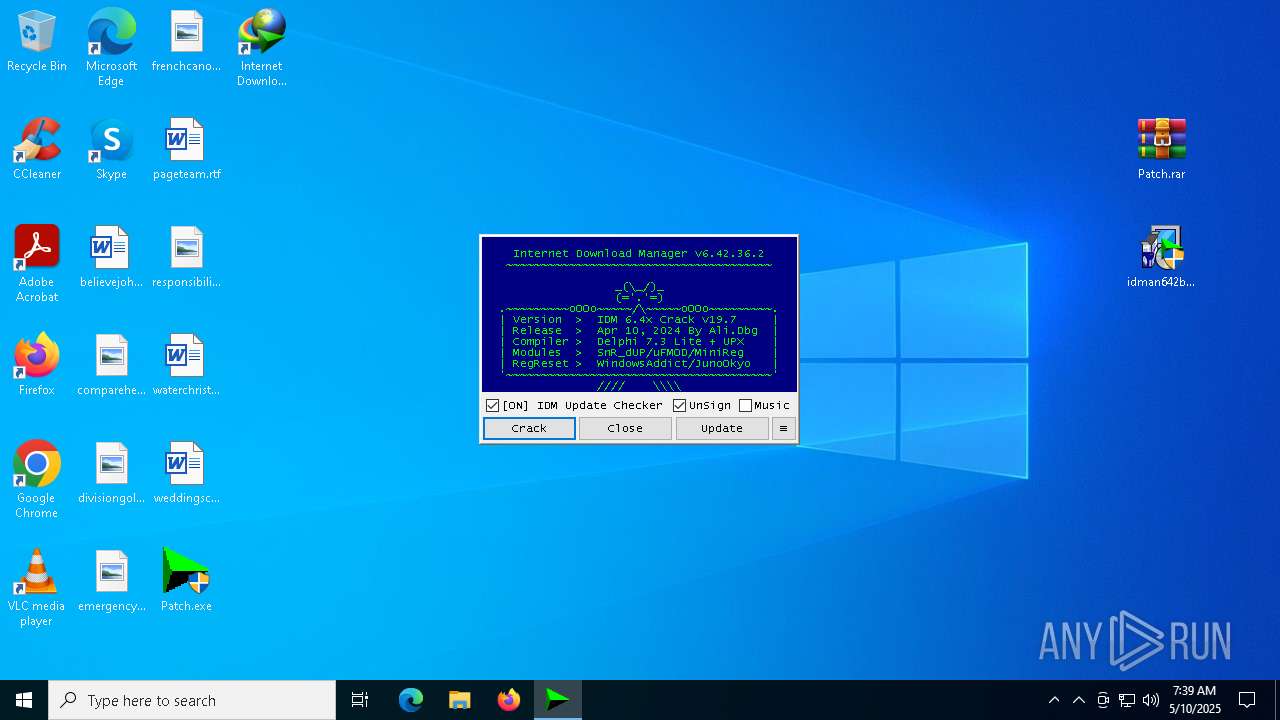
Registers / Runs the DLL via REGSVR32.EXE
- IDM1.tmp (PID: 4464)
- IDMan.exe (PID: 2136)
- IDMan.exe (PID: 680)
- Uninstall.exe (PID: 8816)
Starts NET.EXE for service management
- net.exe (PID: 8772)
- Uninstall.exe (PID: 8816)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 9036)
Starts application with an unusual extension
- idman642build36.exe (PID: 5360)
- cmd.exe (PID: 4880)
Executable content was dropped or overwritten
- Patch.exe (PID: 5668)
- IDMan.exe (PID: 2136)
- drvinst.exe (PID: 7864)
- rundll32.exe (PID: 6876)
Uses RUNDLL32.EXE to load library
- Uninstall.exe (PID: 8816)
Drops a system driver (possible attempt to evade defenses)
- rundll32.exe (PID: 6876)
- drvinst.exe (PID: 7864)
Executing commands from a ".bat" file
- Patch.exe (PID: 5668)
- cmd.exe (PID: 4880)
Uses REG/REGEDIT.EXE to modify registry
- Patch.exe (PID: 5668)
- cmd.exe (PID: 4880)
- cmd.exe (PID: 4068)
Starts CMD.EXE for commands execution
- Patch.exe (PID: 5668)
- cmd.exe (PID: 4880)
- cmd.exe (PID: 664)
Application launched itself
- cmd.exe (PID: 4880)
- cmd.exe (PID: 664)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4880)
- cmd.exe (PID: 7628)
- cmd.exe (PID: 1184)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 4880)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 4880)
Hides command output
- cmd.exe (PID: 1184)
- cmd.exe (PID: 4068)
INFO
Application launched itself
- firefox.exe (PID: 1512)
- firefox.exe (PID: 2516)
- firefox.exe (PID: 6824)
- firefox.exe (PID: 8788)
Reads the software policy settings
- slui.exe (PID: 7748)
Connects to unusual port
- firefox.exe (PID: 2516)
- firefox.exe (PID: 8788)
Local mutex for internet shortcut management
- WinRAR.exe (PID: 9036)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 9036)
- WinRAR.exe (PID: 5024)
The sample compiled with english language support
- WinRAR.exe (PID: 9036)
- Patch.exe (PID: 5668)
- IDMan.exe (PID: 2136)
- rundll32.exe (PID: 6876)
- drvinst.exe (PID: 7864)
Manual execution by a user
- WinRAR.exe (PID: 9036)
- WinRAR.exe (PID: 5024)
- idman642build36.exe (PID: 1852)
- idman642build36.exe (PID: 5360)
- Patch.exe (PID: 8604)
- Patch.exe (PID: 5668)
- firefox.exe (PID: 6824)
- IDMan.exe (PID: 6436)
Checks operating system version
- cmd.exe (PID: 4880)
Changes the display of characters in the console
- cmd.exe (PID: 4880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
264
Monitored processes
128
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | reg query "HKCU\Software\DownloadManager" "/v" "tvfrdt" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | reg export HKCU\Software\Classes\Wow6432Node\CLSID "C:\WINDOWS\Temp\_Backup_HKCU_CLSID_20250510-074011115.reg" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | REG ADD "HKLM\Software\Internet Download Manager" /v "AdvIntDriverEnabled2" /t REG_DWORD /d "1" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 664 | C:\WINDOWS\system32\cmd.exe /c echo prompt $E | cmd | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | "C:\Program Files (x86)\Internet Download Manager\IDMan.exe" -Embedding | C:\Program Files (x86)\Internet Download Manager\IDMan.exe | — | svchost.exe | |||||||||||
User: admin Company: Tonec Inc. Integrity Level: MEDIUM Description: Internet Download Manager (IDM) Exit code: 0 Version: 6, 42, 36, 2 Modules
| |||||||||||||||
| 856 | /s "C:\Program Files (x86)\Internet Download Manager\IDMGetAll64.dll" | C:\Windows\System32\regsvr32.exe | — | regsvr32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | "C:\Windows\System32\regsvr32.exe" /s "C:\Program Files (x86)\Internet Download Manager\IDMShellExt64.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | IDMan.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 976 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5240 -childID 5 -isForBrowser -prefsHandle 5160 -prefMapHandle 5180 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1292 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {af88c415-c310-4279-95dc-97cbcec520e4} 2516 "\\.\pipe\gecko-crash-server-pipe.2516" 1e1e5770a10 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1184 | C:\WINDOWS\system32\cmd.exe /c powershell.exe "([System.Security.Principal.NTAccount](Get-WmiObject -Class Win32_ComputerSystem).UserName).Translate([System.Security.Principal.SecurityIdentifier]).Value" 2>nul | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | reg query HKU\S-1-5-21-1693682860-607145093-2874071422-1001\Software\Classes\Wow6432Node\CLSID\IAS_TEST | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
83 167
Read events
82 416
Write events
579
Delete events
172
Modification events
| (PID) Process: | (2516) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (9036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (9036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (9036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (9036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (9036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\_igetintopc.com_Internet_Download_Manager_6.rar | |||
| (PID) Process: | (9036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (9036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (9036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (9036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
19
Suspicious files
286
Text files
52
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2516 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 2516 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 2516 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\protections.sqlite-journal | binary | |
MD5:0AE8A8603477AE2F14FA32C32BE5BDBB | SHA256:1625A691C3BBA5BE631B8C59D377E6BA4640017DFEB9CA522822BD04608667F2 | |||
| 2516 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 2516 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 2516 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 2516 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2516 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:BAD406480E50FEC8956978F7FE331991 | SHA256:AA07E227121171B851F7202696A0C00ACB3390A7B8FC222EC81D44FAAD5B9F2C | |||
| 2516 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2516 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
75
TCP/UDP connections
295
DNS requests
302
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2516 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2516 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
2516 | firefox.exe | POST | 200 | 184.24.77.52:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
2516 | firefox.exe | POST | — | 184.24.77.52:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
2516 | firefox.exe | POST | 200 | 184.24.77.52:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
2516 | firefox.exe | POST | 200 | 216.58.206.67:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2516 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | — | — | whitelisted |
2516 | firefox.exe | 142.250.186.138:443 | safebrowsing.googleapis.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
igetintopc.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
ipv4only.arpa |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO CMS Hosting Domain in DNS Lookup (storyblok .com) |
2196 | svchost.exe | Misc activity | ET INFO CMS Hosting Domain in DNS Lookup (storyblok .com) |
2516 | firefox.exe | Misc activity | ET INFO CMS Hosting Domain in TLS SNI (storyblok .com) |
2516 | firefox.exe | Misc activity | ET INFO CMS Hosting Domain in TLS SNI (storyblok .com) |
2516 | firefox.exe | Misc activity | ET INFO CMS Hosting Domain in TLS SNI (storyblok .com) |
2516 | firefox.exe | Misc activity | ET INFO CMS Hosting Domain in TLS SNI (storyblok .com) |
2516 | firefox.exe | Misc activity | ET INFO CMS Hosting Domain in TLS SNI (storyblok .com) |
2516 | firefox.exe | Misc activity | ET INFO CMS Hosting Domain in TLS SNI (storyblok .com) |
2196 | svchost.exe | Misc activity | ET INFO CMS Hosting Domain in DNS Lookup (storyblok .com) |
2516 | firefox.exe | Misc activity | ET INFO CMS Hosting Domain in TLS SNI (storyblok .com) |