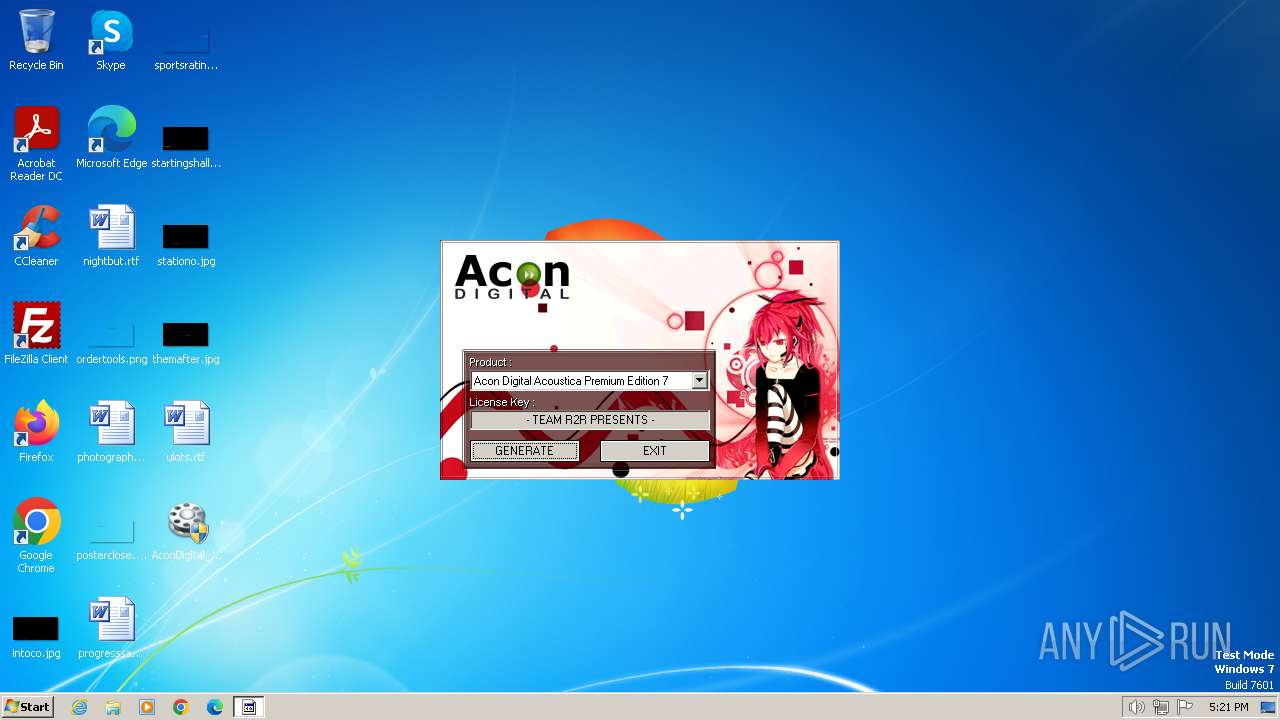
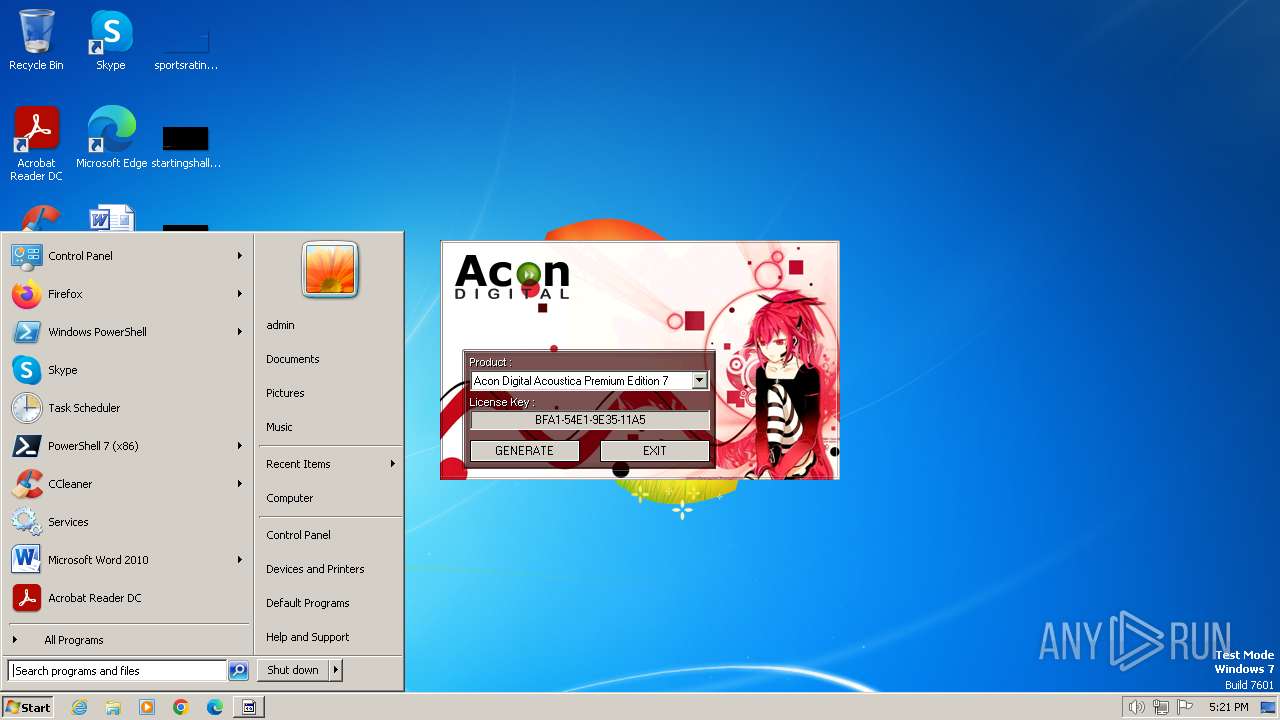
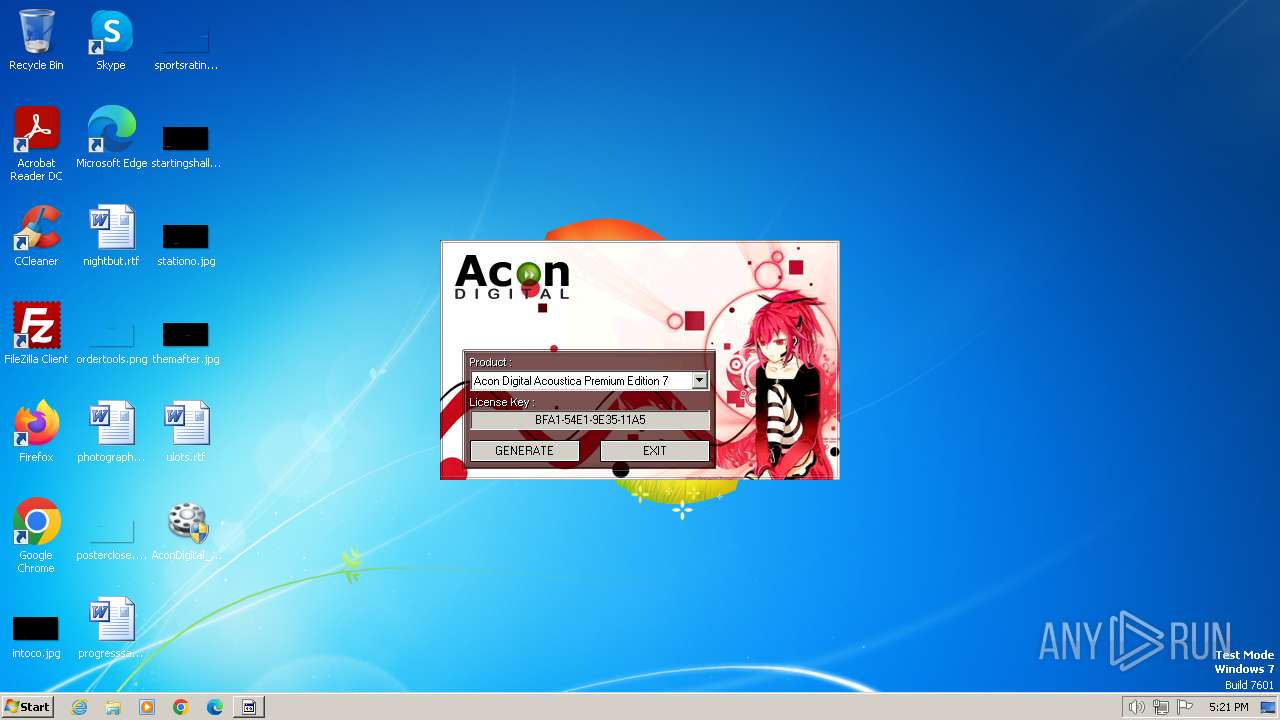
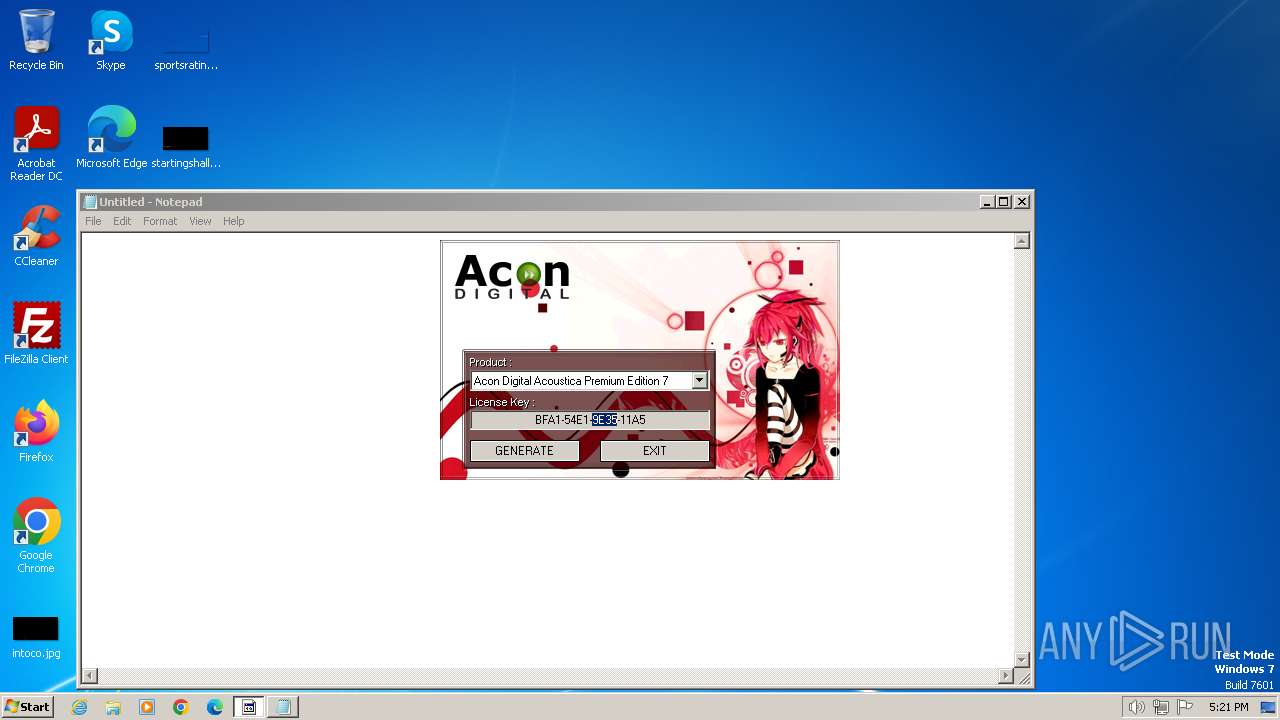
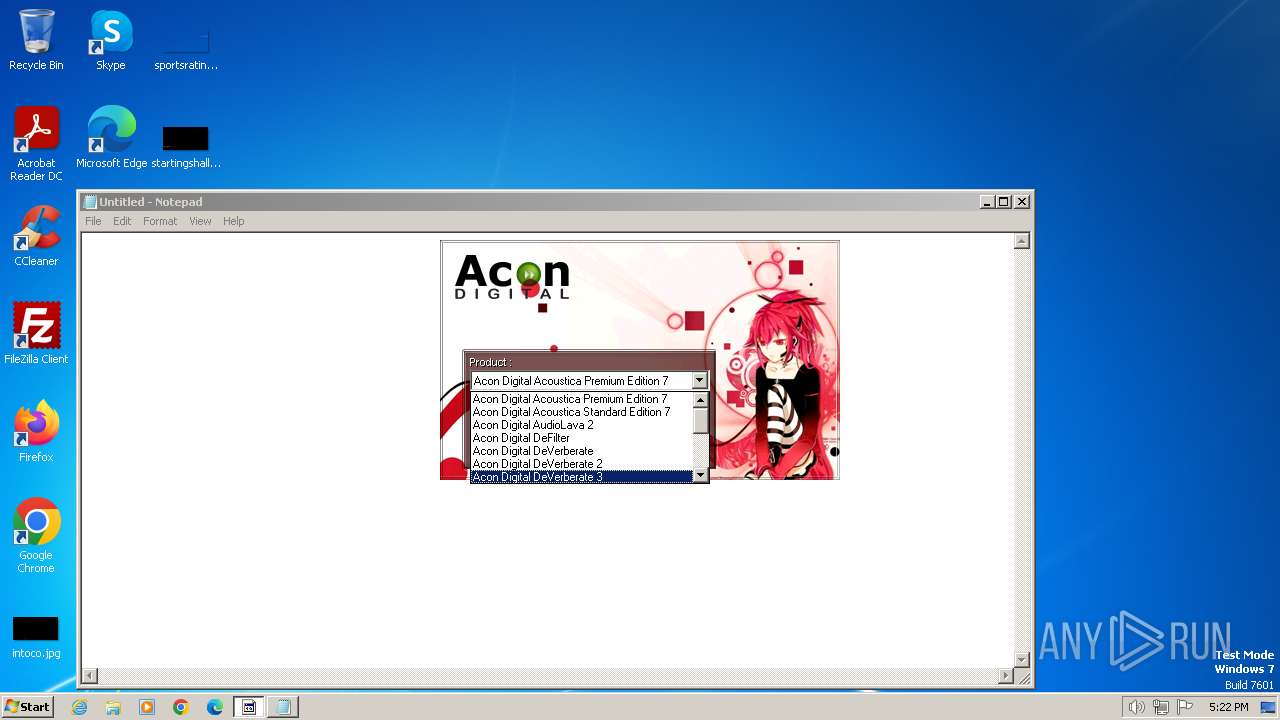
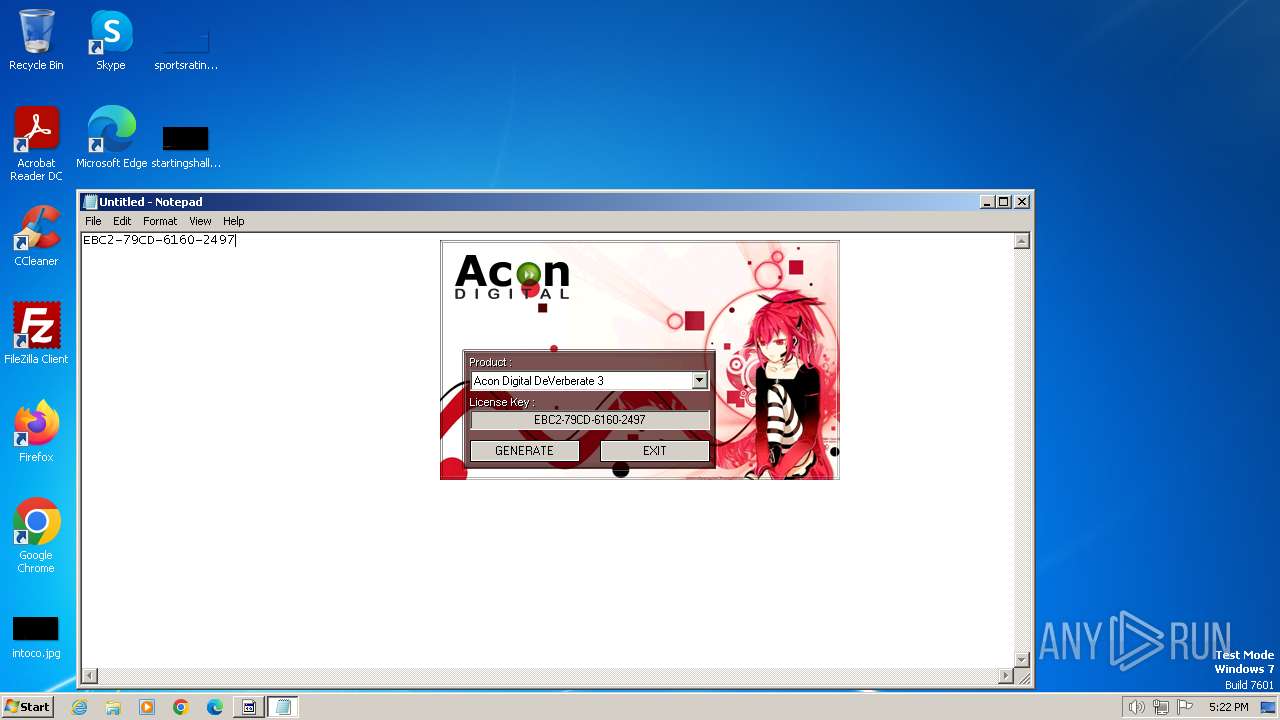
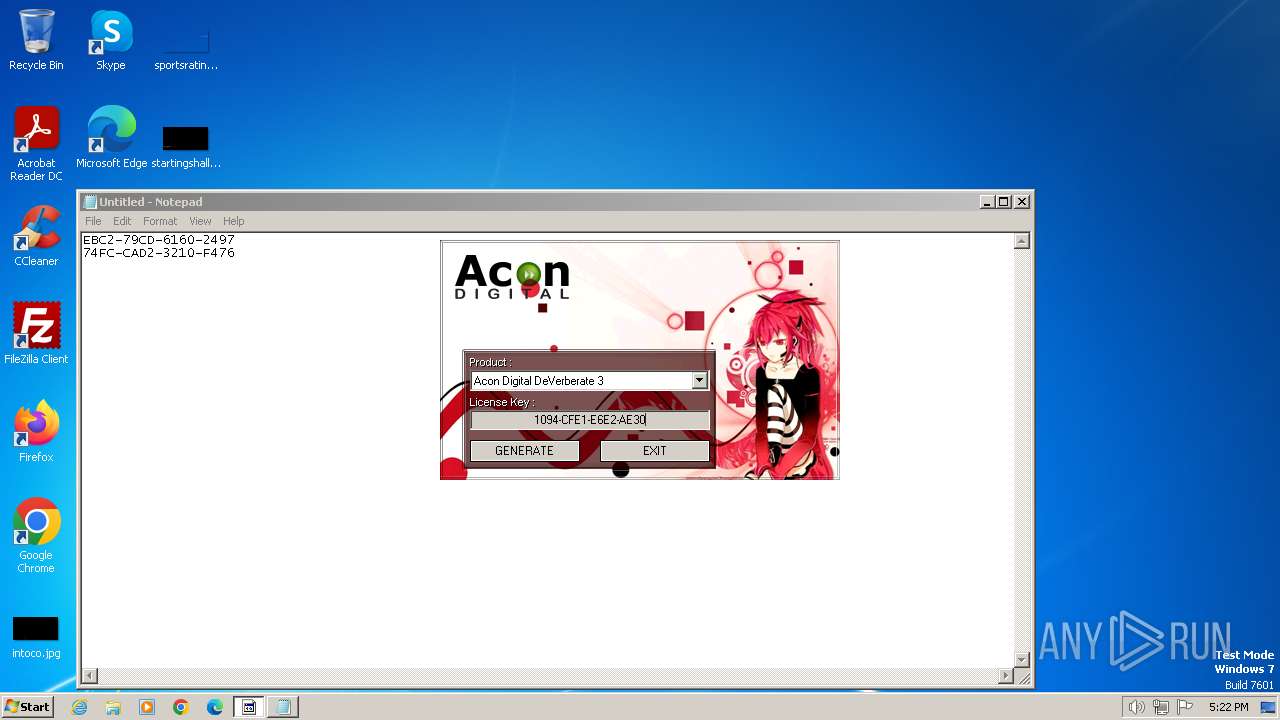
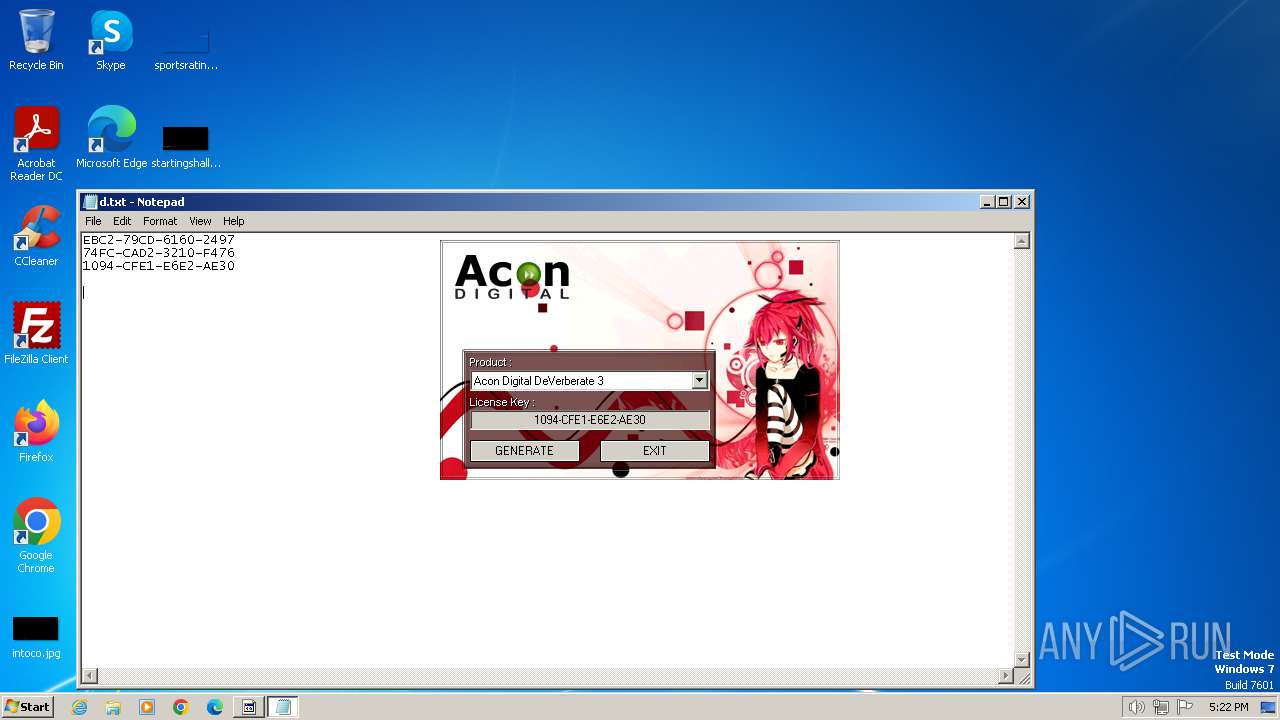
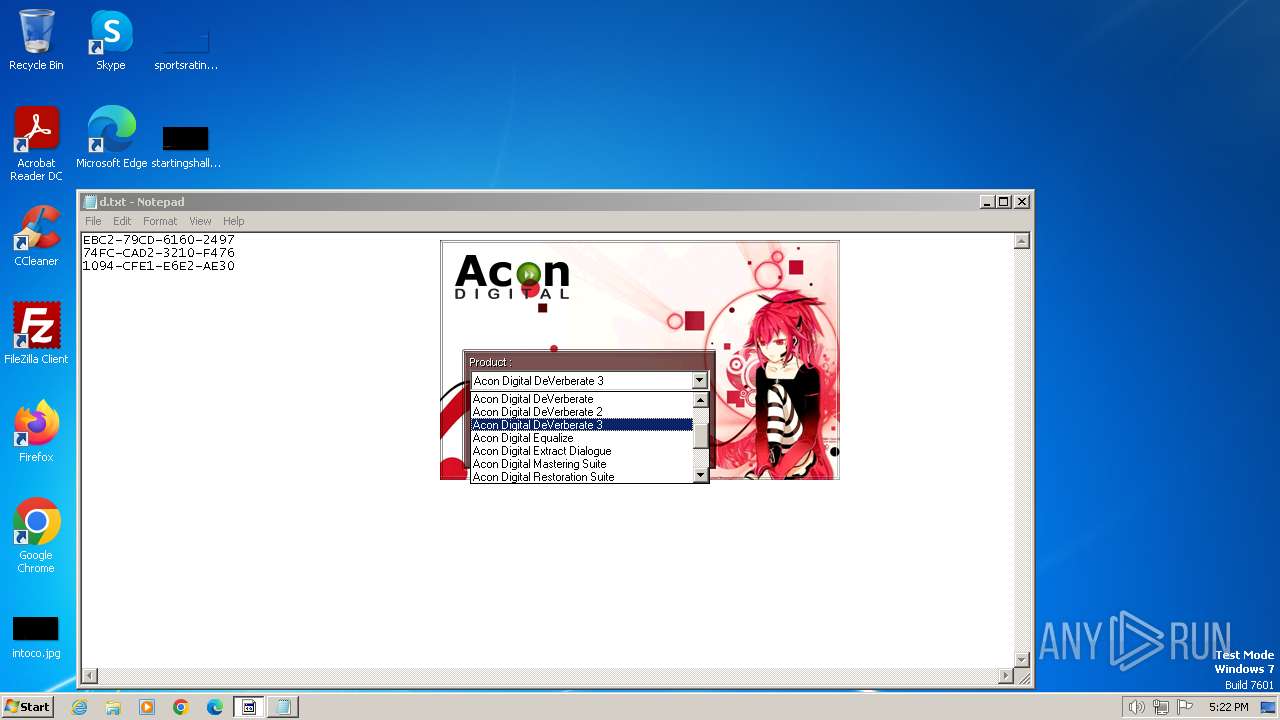
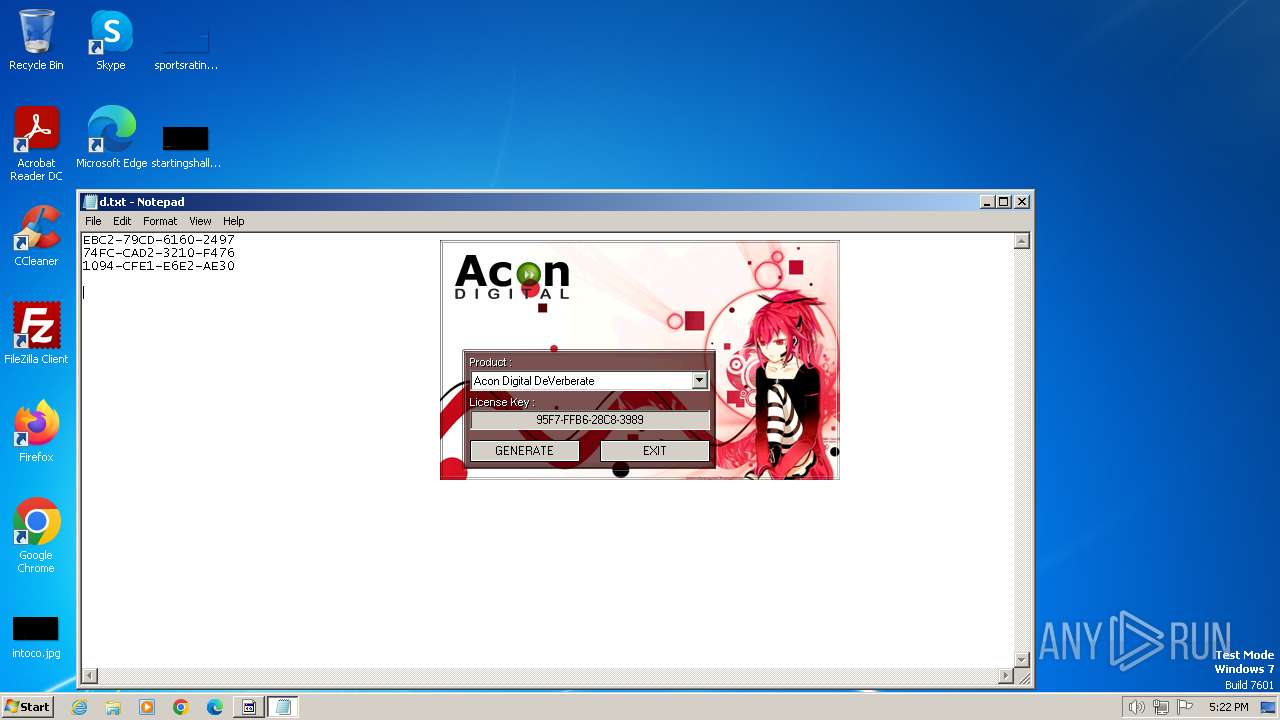
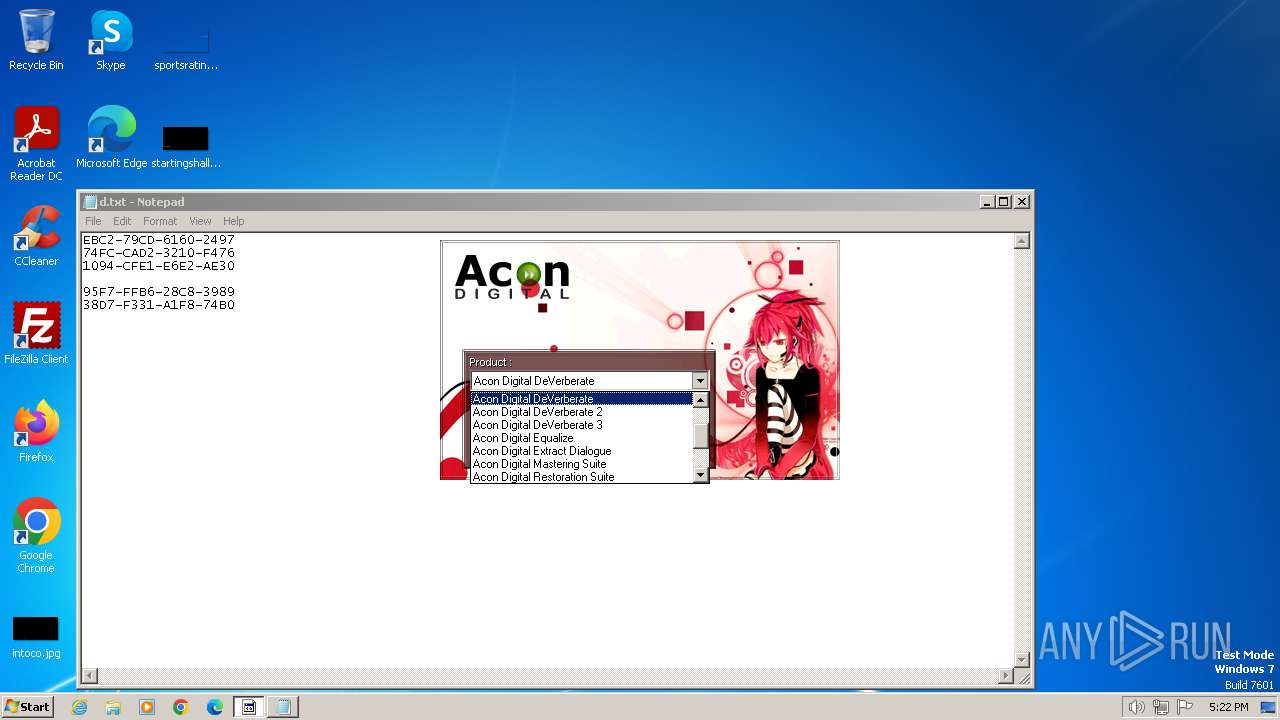
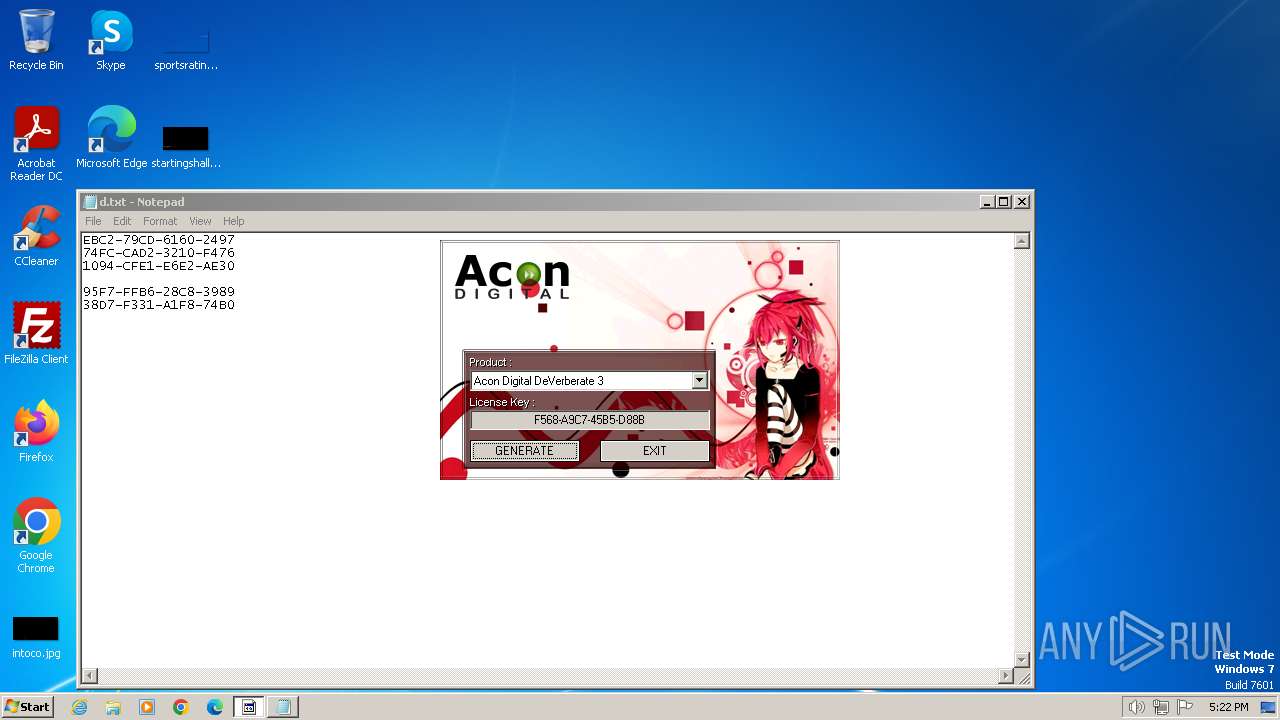
| File name: | AconDigital_KeyGen.exe |
| Full analysis: | https://app.any.run/tasks/96450737-cd9f-4b65-8b11-8a4114f8f014 |
| Verdict: | Malicious activity |
| Analysis date: | January 31, 2024, 17:21:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | C4D6E2B94972F38F1A16EAA64E2BD9FD |
| SHA1: | 7CCFFC960E639BE9578DABD006A663BBDB3D3E25 |
| SHA256: | DBB5832B400E97492A73C8A563B10A1AF9951FA9BB4A92003D4E63CC2195F1C6 |
| SSDEEP: | 12288:S3s9g9kCUWVVVVVVVVvfuRoDeQRrgPUGND7XBVBP5DG/iAnOiONfs:S3sUkCLuRoDeCrgPUGND7bBxDvZiONfs |
MALICIOUS
Drops the executable file immediately after the start
- AconDigital_KeyGen.exe (PID: 584)
SUSPICIOUS
Executable content was dropped or overwritten
- AconDigital_KeyGen.exe (PID: 584)
Reads the Internet Settings
- notepad.exe (PID: 3048)
INFO
Checks supported languages
- AconDigital_KeyGen.exe (PID: 584)
- keygen.exe (PID: 2204)
Reads the computer name
- AconDigital_KeyGen.exe (PID: 584)
- keygen.exe (PID: 2204)
Create files in a temporary directory
- keygen.exe (PID: 2204)
- AconDigital_KeyGen.exe (PID: 584)
Reads the machine GUID from the registry
- keygen.exe (PID: 2204)
Manual execution by a user
- notepad.exe (PID: 3048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:04:02 05:20:09+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24064 |
| InitializedDataSize: | 120320 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x326c |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
43
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 584 | "C:\Users\admin\Desktop\AconDigital_KeyGen.exe" | C:\Users\admin\Desktop\AconDigital_KeyGen.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1044 | "C:\Users\admin\Desktop\AconDigital_KeyGen.exe" | C:\Users\admin\Desktop\AconDigital_KeyGen.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2204 | C:\Users\admin\AppData\Local\Temp\keygen.exe | C:\Users\admin\AppData\Local\Temp\keygen.exe | — | AconDigital_KeyGen.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3048 | "C:\Windows\system32\notepad.exe" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 629
Read events
1 599
Write events
28
Delete events
2
Modification events
| (PID) Process: | (3048) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3048) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 010000000200000006000000000000000B000000070000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3048) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 020000000100000006000000000000000B000000070000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3048) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (3048) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (3048) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
| (PID) Process: | (3048) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3048) notepad.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRU |
| Operation: | write | Name: | MRUListEx |
Value: 000000000200000001000000FFFFFFFF | |||
| (PID) Process: | (3048) notepad.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\* |
| Operation: | write | Name: | MRUListEx |
Value: 0C0000000B0000000A00000009000000080000000700000006000000050000000400000003000000020000000100000000000000FFFFFFFF | |||
| (PID) Process: | (3048) notepad.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | delete value | Name: | 4 |
Value: 6E006F00740065007000610064002E00650078006500000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000000000000 | |||
Executable files
3
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 584 | AconDigital_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\R2RACON.dll | executable | |
MD5:E8CDEC2C2624357CD4CA4504AB732C54 | SHA256:369FDBFF93FAD7182147F679C83BC65030EF909DE4B4DEA886BF4D8E9E2C4390 | |||
| 584 | AconDigital_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\BASSMOD.dll | executable | |
MD5:E4EC57E8508C5C4040383EBE6D367928 | SHA256:8AD9E47693E292F381DA42DDC13724A3063040E51C26F4CA8E1F8E2F1DDD547F | |||
| 584 | AconDigital_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\keygen.exe | executable | |
MD5:022BE806370A5B74021A73799B43A2BC | SHA256:1D2AF1ED7134DFFD8812163D8B04225E6BCD7D0B31E8FD860924D84CFB43311B | |||
| 584 | AconDigital_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\bgm.xm | binary | |
MD5:57E69663CAE5500F16F5EEFDDDAC7EF3 | SHA256:48FEB65FD3126F0CADE08A999FE1A93E06F435D1CAB775E73195FB711D22FD35 | |||
| 3048 | notepad.exe | C:\Users\admin\Documents\d.txt | text | |
MD5:59E2903516CDB2D0A930C4ED91845504 | SHA256:03CD184331508C9675676CD073C7547C3A6FA2CECF9A4A97962709FFBDC04367 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |