| File name: | bot.exe |
| Full analysis: | https://app.any.run/tasks/b1888973-2e4a-4ddf-8aba-d50b0b5251ac |
| Verdict: | Malicious activity |
| Analysis date: | May 31, 2025, 12:57:38 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 8 sections |
| MD5: | 98DE832A90793DDF4B4FC398BC11F15A |
| SHA1: | 4502E46737FD2949215CA29CF3D49E378FA7FF45 |
| SHA256: | DBA6CFFCD27E7BA102FC0B1EA35D5506D57111FA785478EC4811284306CA14B6 |
| SSDEEP: | 98304:FyiHpTj35Flfa61c1WjycuJHH82FaOhvS3oXS2nFhKq47gYpukrVATGNCZSC: |
MALICIOUS
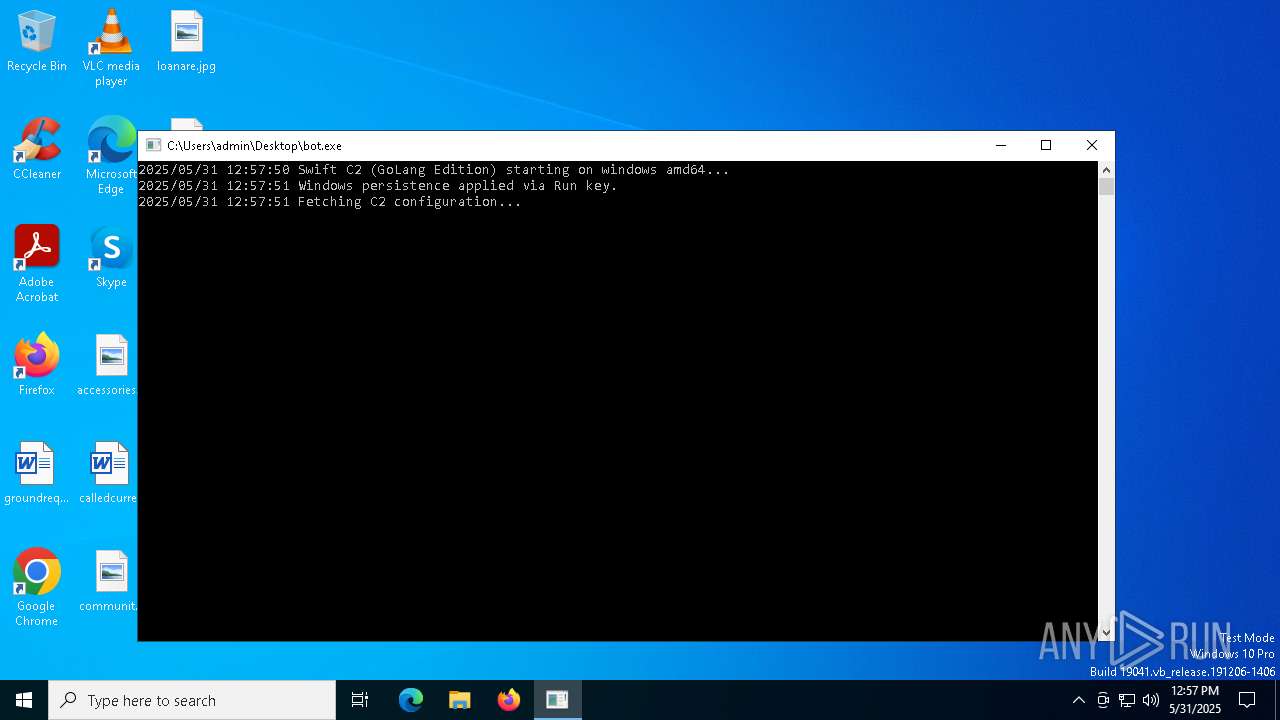
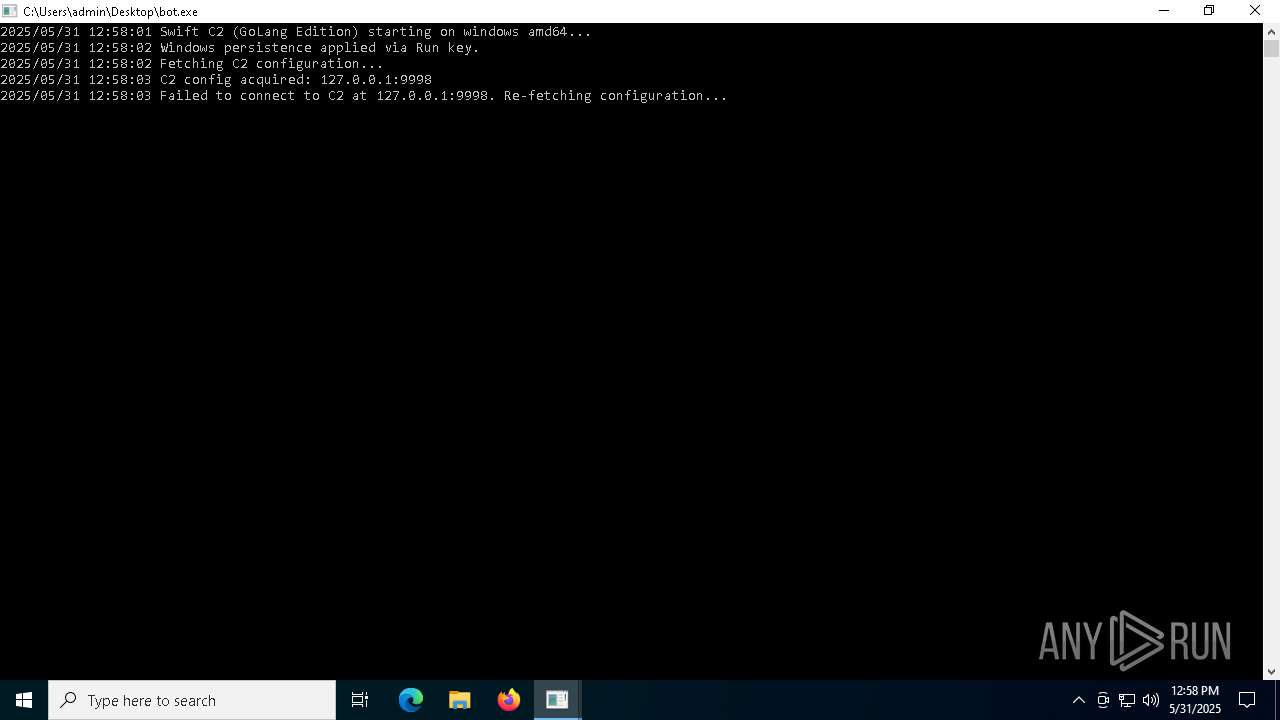
Changes the autorun value in the registry
- bot.exe (PID: 6988)
- bot.exe (PID: 7488)
SUSPICIOUS
The process checks if it is being run in the virtual environment
- conhost.exe (PID: 6248)
INFO
Checks supported languages
- bot.exe (PID: 6988)
- bot.exe (PID: 7488)
Reads the machine GUID from the registry
- bot.exe (PID: 6988)
- bot.exe (PID: 7488)
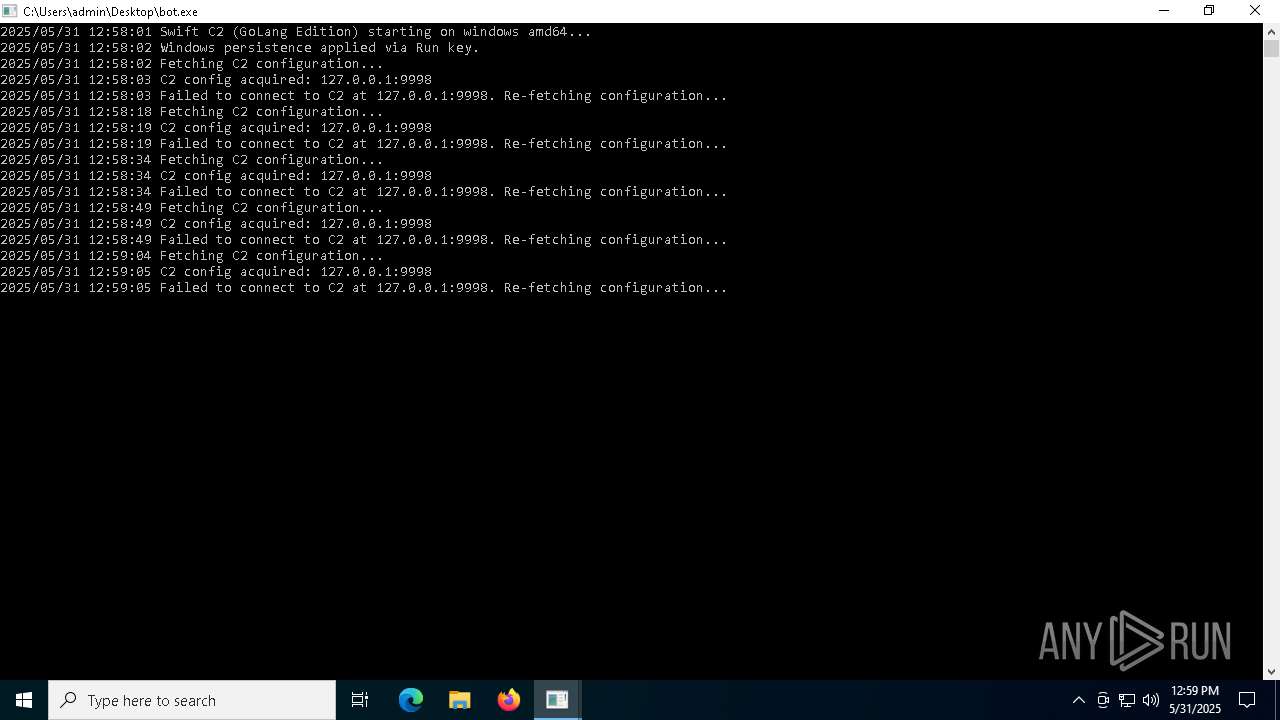
Launch of the file from Registry key
- bot.exe (PID: 6988)
- bot.exe (PID: 7488)
Reads the computer name
- bot.exe (PID: 6988)
- bot.exe (PID: 7488)
Detects GO elliptic curve encryption (YARA)
- bot.exe (PID: 6988)
- bot.exe (PID: 7488)
Application based on Golang
- bot.exe (PID: 6988)
- bot.exe (PID: 7488)
Reads the software policy settings
- bot.exe (PID: 6988)
- bot.exe (PID: 7488)
- slui.exe (PID: 6920)
Manual execution by a user
- bot.exe (PID: 7488)
Checks proxy server information
- slui.exe (PID: 6920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 3 |
| CodeSize: | 3071488 |
| InitializedDataSize: | 414720 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x77420 |
| OSVersion: | 6.1 |
| ImageVersion: | 1 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows command line |
Total processes
130
Monitored processes
5
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6248 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | bot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6920 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6988 | "C:\Users\admin\Desktop\bot.exe" | C:\Users\admin\Desktop\bot.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7488 | C:\Users\admin\Desktop\bot.exe | C:\Users\admin\Desktop\bot.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7988 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | bot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 361
Read events
11 359
Write events
2
Delete events
0
Modification events
| (PID) Process: | (6988) bot.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | SwiftC2Bot |
Value: C:\Users\admin\Desktop\bot.exe | |||
| (PID) Process: | (7488) bot.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | SwiftC2Bot |
Value: C:\Users\admin\Desktop\bot.exe | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
17
DNS requests
8
Threats
56
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 64.29.17.129:443 | https://ipvariant.vercel.app/ipl | unknown | text | 9 b | unknown |
— | — | GET | 200 | 64.29.17.129:443 | https://ipvariant.vercel.app/port | unknown | text | 4 b | unknown |
— | — | GET | 200 | 216.198.79.129:443 | https://ipvariant.vercel.app/ipl | unknown | text | 9 b | unknown |
— | — | GET | 200 | 64.29.17.129:443 | https://ipvariant.vercel.app/port | unknown | text | 4 b | unknown |
— | — | GET | 200 | 216.198.79.129:443 | https://ipvariant.vercel.app/ipl | unknown | text | 9 b | unknown |
— | — | GET | 200 | 64.29.17.129:443 | https://ipvariant.vercel.app/port | unknown | text | 4 b | unknown |
— | — | GET | 200 | 216.198.79.129:443 | https://ipvariant.vercel.app/ipl | unknown | text | 9 b | unknown |
— | — | GET | 200 | 64.29.17.129:443 | https://ipvariant.vercel.app/port | unknown | text | 4 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7964 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6988 | bot.exe | 216.198.79.1:443 | ipvariant.vercel.app | — | US | unknown |
7488 | bot.exe | 216.198.79.1:443 | ipvariant.vercel.app | — | US | unknown |
4244 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ipvariant.vercel.app |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloud infrastructure to build app (vercel .app) |
— | — | Misc activity | ET INFO Go-http-client User-Agent Observed Outbound |
— | — | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |
— | — | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |
— | — | Misc activity | ET INFO Go-http-client User-Agent Observed Outbound |
— | — | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |
— | — | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |
— | — | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |
— | — | Misc activity | ET INFO Go-http-client User-Agent Observed Outbound |
— | — | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |