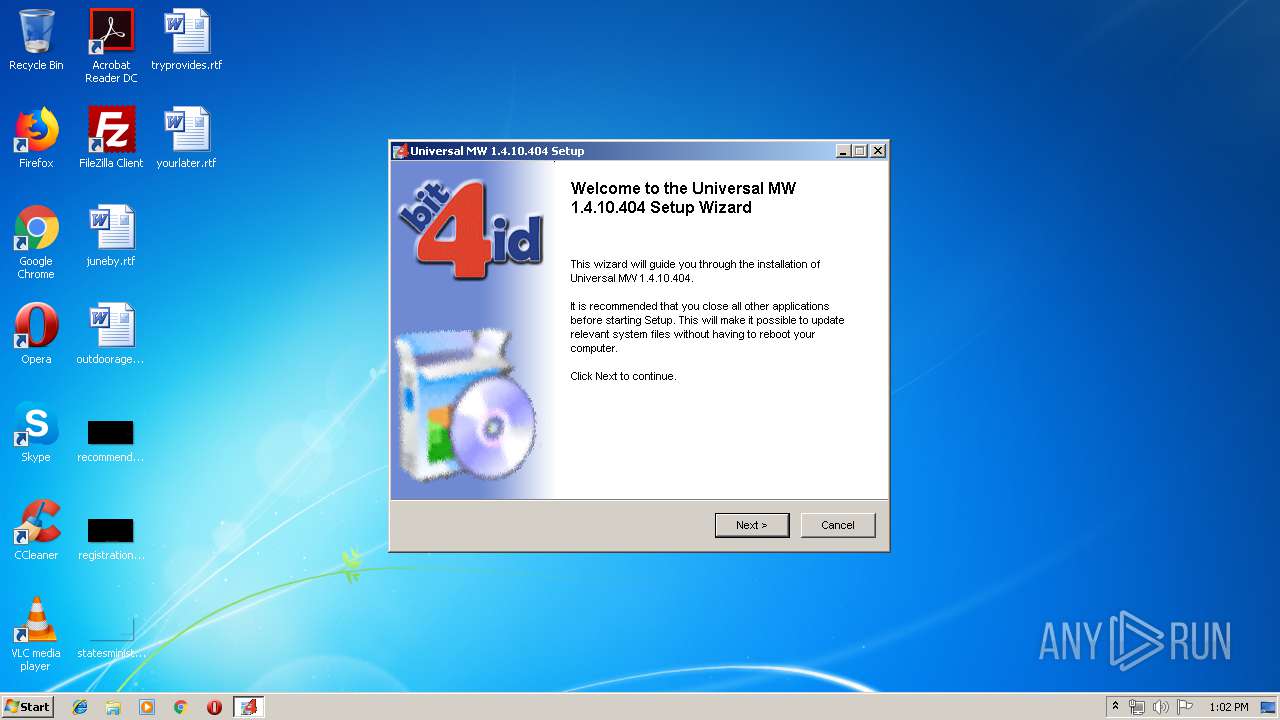
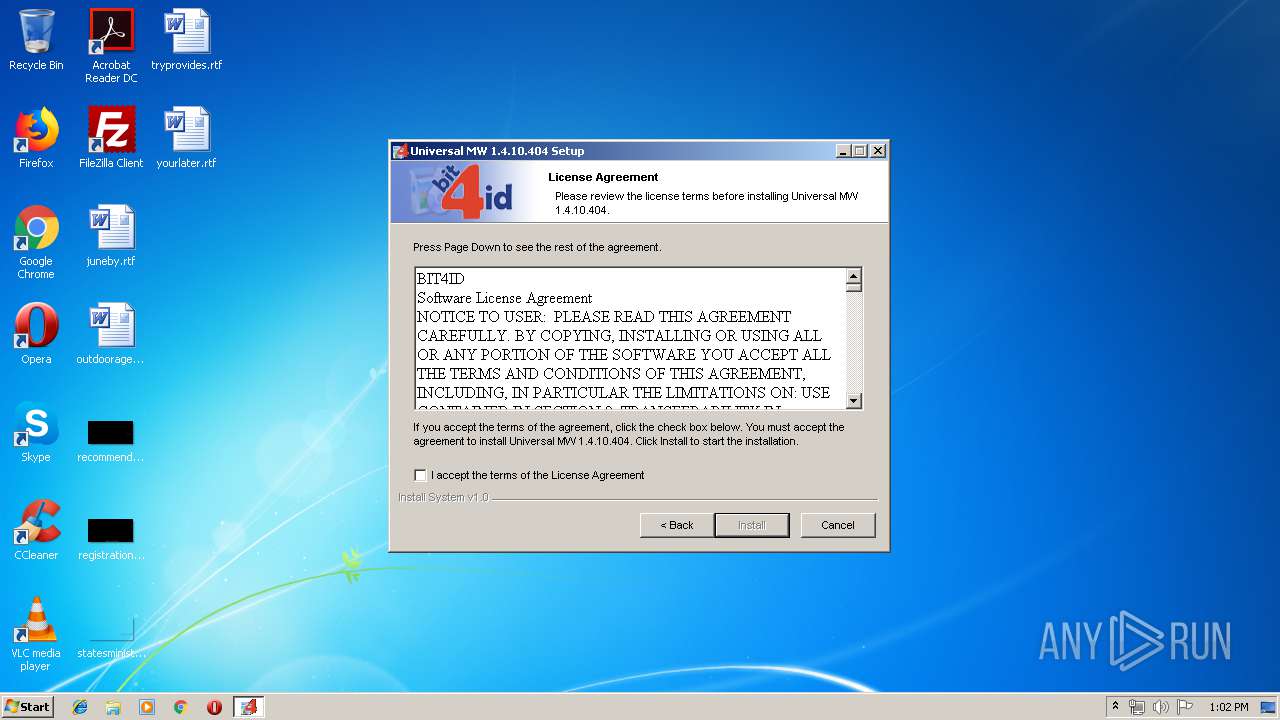
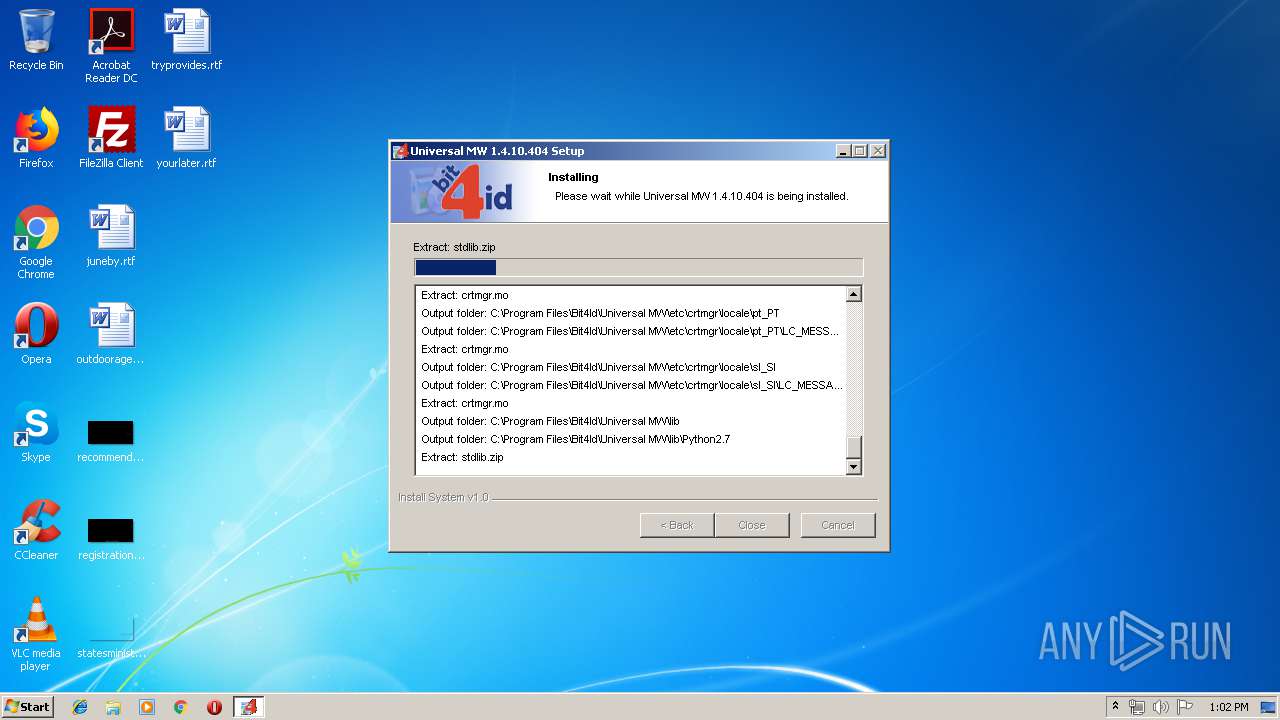
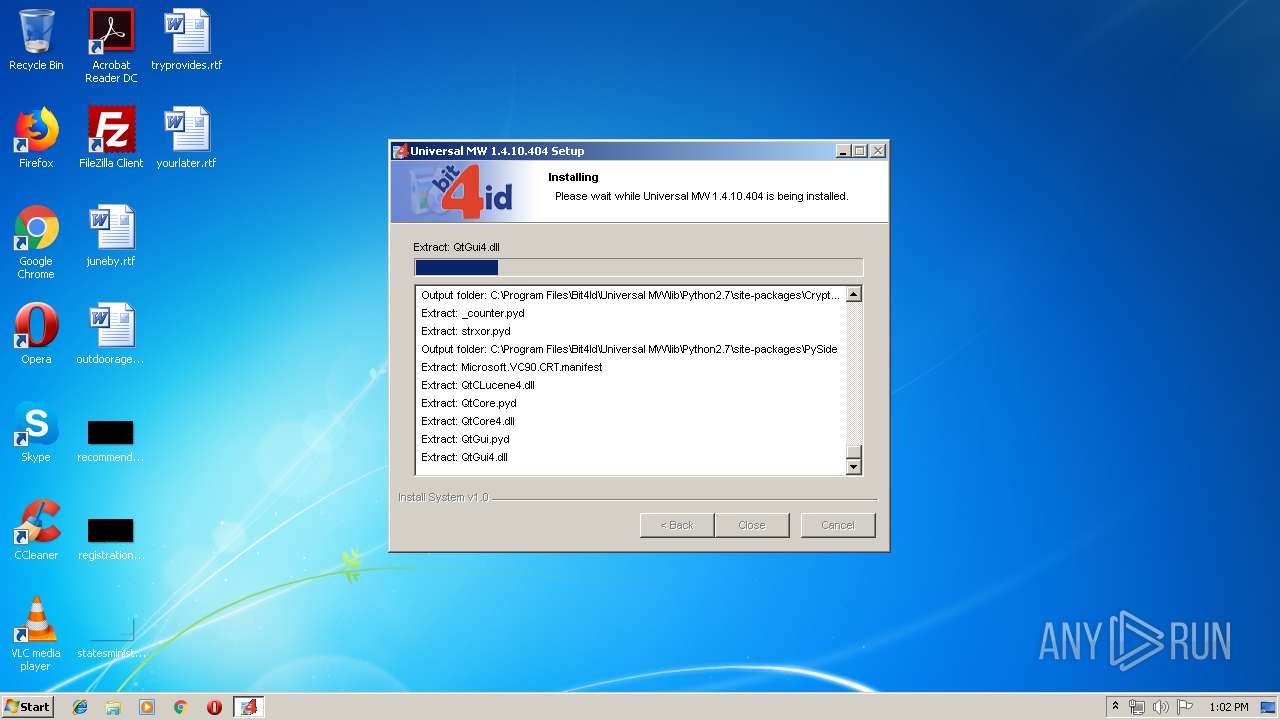
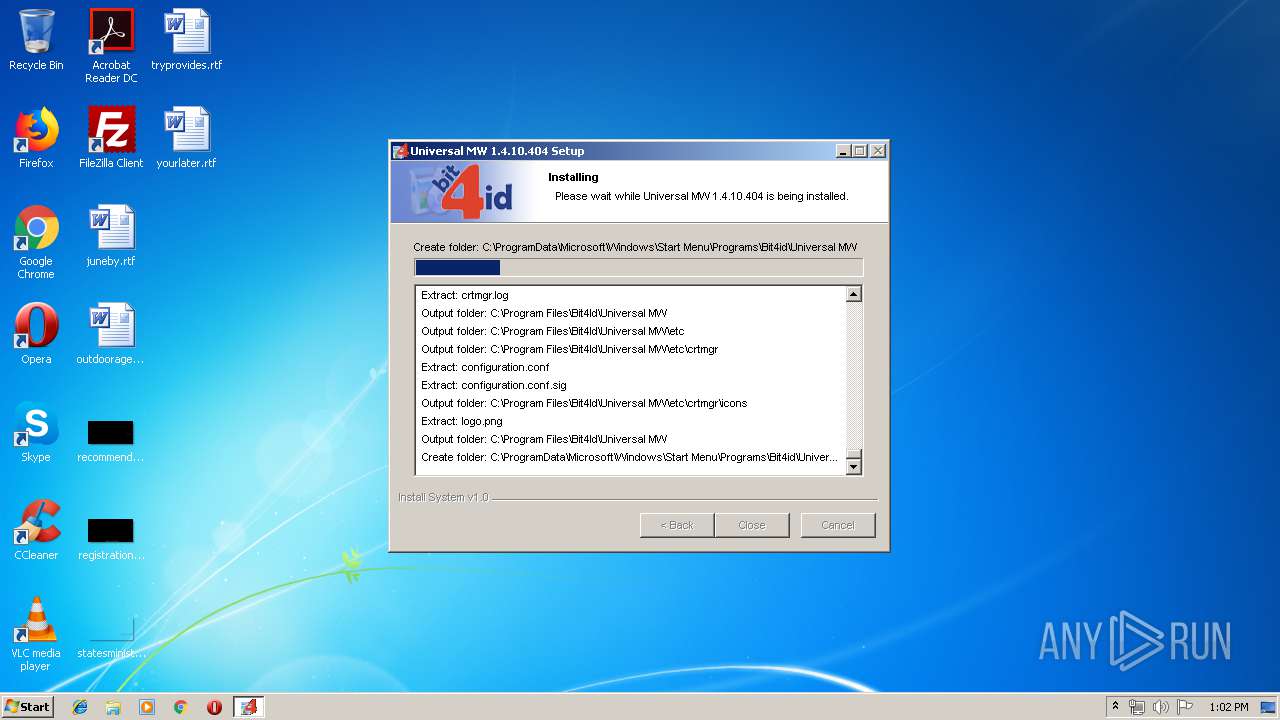
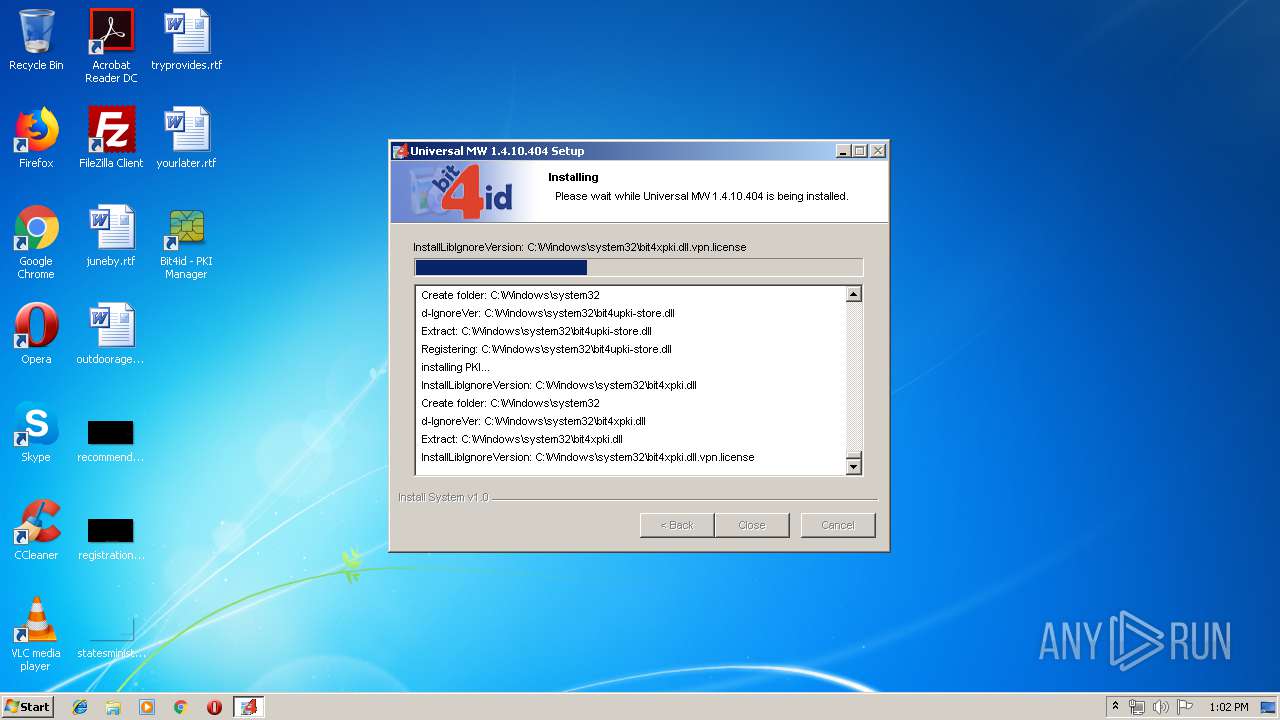
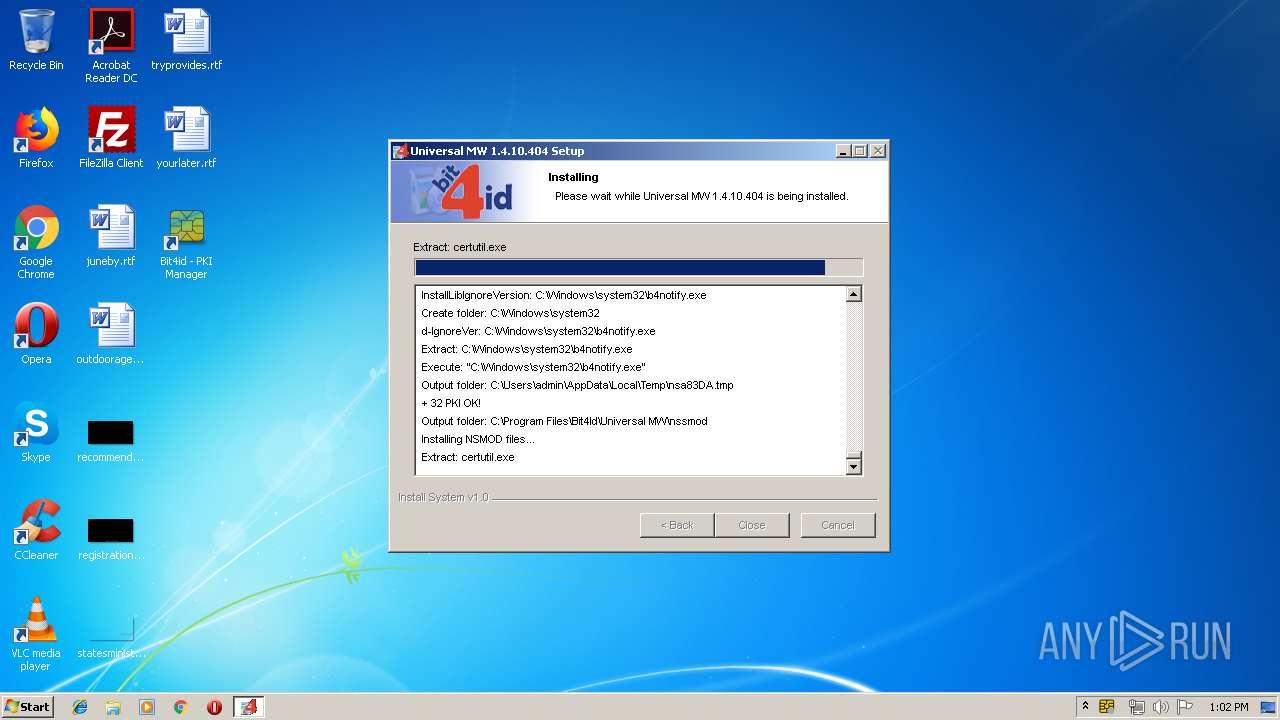
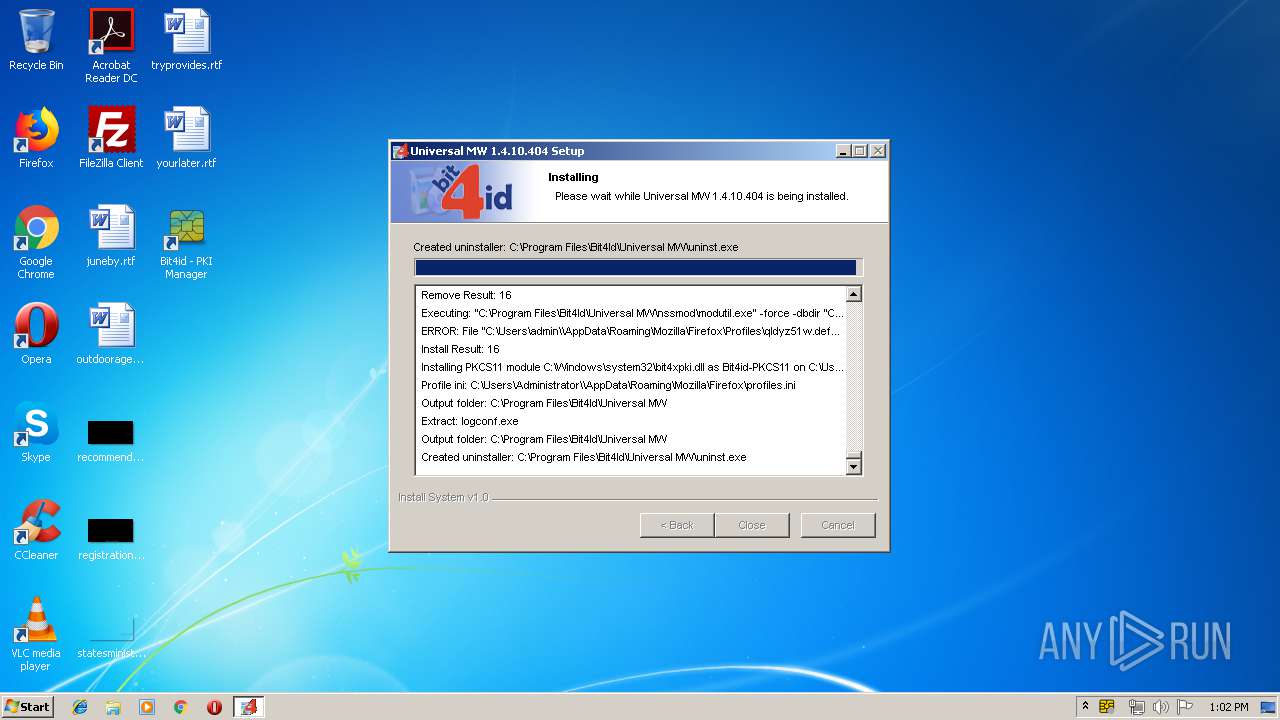
| download: | Bit4id_Middleware.exe |
| Full analysis: | https://app.any.run/tasks/19ee428e-4d40-46ce-bc25-3bc48dd5dc9b |
| Verdict: | Malicious activity |
| Analysis date: | April 07, 2019, 12:00:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 0E774956505B25B4F9F6CCAF05D698F8 |
| SHA1: | 3D258886E45E9ECF0A320276B111B8A983813774 |
| SHA256: | DB836691890A9A46B70B1832F6669376E4C911D3F3669850628708DE57EA13FF |
| SSDEEP: | 393216:QohAZXA6xGmM3ztV3NLk8j1oMllVq8P6qQNa5jUK6DK5XCV:QoATMjtXLkZhH1adx6DK5m |
MALICIOUS
Loads dropped or rewritten executable
- rundll32.exe (PID: 2560)
- RUNDLL32.EXE (PID: 2356)
- modutil.exe (PID: 3504)
- RUNDLL32.EXE (PID: 2140)
- Bit4id_Middleware.exe (PID: 2332)
- modutil.exe (PID: 672)
- crtmgr.exe (PID: 3256)
Application was dropped or rewritten from another process
- modutil.exe (PID: 672)
- b4notify.exe (PID: 1360)
- modutil.exe (PID: 3504)
- crtmgr.exe (PID: 3256)
Changes settings of System certificates
- Bit4id_Middleware.exe (PID: 2332)
Changes the autorun value in the registry
- Bit4id_Middleware.exe (PID: 2332)
SUSPICIOUS
Creates files in the Windows directory
- Bit4id_Middleware.exe (PID: 2332)
Application launched itself
- RUNDLL32.EXE (PID: 2356)
Uses RUNDLL32.EXE to load library
- Bit4id_Middleware.exe (PID: 2332)
- RUNDLL32.EXE (PID: 2356)
Creates a software uninstall entry
- Bit4id_Middleware.exe (PID: 2332)
Executable content was dropped or overwritten
- Bit4id_Middleware.exe (PID: 2332)
Loads Python modules
- crtmgr.exe (PID: 3256)
Creates files in the program directory
- Bit4id_Middleware.exe (PID: 2332)
INFO
Reads settings of System Certificates
- RUNDLL32.EXE (PID: 2140)
- RUNDLL32.EXE (PID: 2356)
Dropped object may contain Bitcoin addresses
- Bit4id_Middleware.exe (PID: 2332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:04:02 05:20:09+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24064 |
| InitializedDataSize: | 120320 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x326c |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.4.10.404 |
| ProductVersionNumber: | 1.4.10.404 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Windows, Latin1 |
| Comments: | Bit4id - Universal MW |
| CompanyName: | - |
| FileDescription: | Bit4id - Universal MW |
| FileVersion: | 1.4.10.404 |
| LegalCopyright: | (C) 2005-2016 |
| LegalTrademarks: | - |
| OriginalFileName: | bit4id_xpki_1.4.10.404-ng-crtmgr.exe |
| ProductName: | Bit4id - Universal MW |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 02-Apr-2016 03:20:09 |
| Detected languages: |
|
| Comments: | Bit4id - Universal MW |
| CompanyName: | - |
| FileDescription: | Bit4id - Universal MW |
| FileVersion: | 1.4.10.404 |
| LegalCopyright: | (C) 2005-2016 |
| LegalTrademarks: | - |
| OriginalFilename: | bit4id_xpki_1.4.10.404-ng-crtmgr.exe |
| ProductName: | Bit4id - Universal MW |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000C8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 02-Apr-2016 03:20:09 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00005C74 | 0x00005E00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.41039 |
.rdata | 0x00007000 | 0x00001196 | 0x00001200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.20374 |
.data | 0x00009000 | 0x0001B058 | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.13053 |
.ndata | 0x00025000 | 0x0000C000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x00031000 | 0x000016E8 | 0x00001800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.45585 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.21417 | 958 | UNKNOWN | English - United States | RT_MANIFEST |
103 | 1.5789 | 20 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.58881 | 500 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.80484 | 236 | UNKNOWN | English - United States | RT_DIALOG |
107 | 2.32668 | 148 | UNKNOWN | English - United States | RT_DIALOG |
109 | 2.5719 | 200 | UNKNOWN | English - United States | RT_DIALOG |
111 | 2.84525 | 226 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
45
Monitored processes
9
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 572 | "C:\Users\admin\AppData\Local\Temp\Bit4id_Middleware.exe" | C:\Users\admin\AppData\Local\Temp\Bit4id_Middleware.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Bit4id - Universal MW Exit code: 3221226540 Version: 1.4.10.404 Modules
| |||||||||||||||
| 672 | "C:\Program Files\Bit4Id\Universal MW\nssmod\modutil.exe" -force -dbdir "C:\Users\admin\\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default" -delete "Bit4id-PKCS11" | C:\Program Files\Bit4Id\Universal MW\nssmod\modutil.exe | — | Bit4id_Middleware.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 16 Modules
| |||||||||||||||
| 1360 | "C:\Windows\system32\b4notify.exe" | C:\Windows\system32\b4notify.exe | — | Bit4id_Middleware.exe | |||||||||||
User: admin Integrity Level: HIGH Description: b4notify Application Exit code: 0 Version: 1, 0, 3, 0 Modules
| |||||||||||||||
| 2140 | "C:\Windows\system32\RUNDLL32.EXE" "C:\Windows\system32\bit4upki-store.dll",RunImportSequence | C:\Windows\system32\RUNDLL32.EXE | — | RUNDLL32.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2332 | "C:\Users\admin\AppData\Local\Temp\Bit4id_Middleware.exe" | C:\Users\admin\AppData\Local\Temp\Bit4id_Middleware.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Bit4id - Universal MW Exit code: 0 Version: 1.4.10.404 Modules
| |||||||||||||||
| 2356 | "RUNDLL32.EXE" "C:\Windows\system32\bit4upki-store.dll",RunImportServer | C:\Windows\system32\RUNDLL32.EXE | — | Bit4id_Middleware.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2560 | "C:\Windows\system32\rundll32.exe " "C:\Windows\system32\bit4upki-store.dll",RunImportServer | C:\Windows\system32\rundll32.exe | — | Bit4id_Middleware.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3256 | "C:\Program Files\Bit4Id\Universal MW\bin\crtmgr.exe" | C:\Program Files\Bit4Id\Universal MW\bin\crtmgr.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3504 | "C:\Program Files\Bit4Id\Universal MW\nssmod\modutil.exe" -force -dbdir "C:\Users\admin\\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default" -add "Bit4id-PKCS11" -libfile "C:\Windows\system32\bit4xpki.dll" | C:\Program Files\Bit4Id\Universal MW\nssmod\modutil.exe | — | Bit4id_Middleware.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 16 Modules
| |||||||||||||||
Total events
749
Read events
394
Write events
355
Delete events
0
Modification events
| (PID) Process: | (2332) Bit4id_Middleware.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\bit4id\pkimanager |
| Operation: | write | Name: | path |
Value: C:\Program Files\Bit4Id\Universal MW\bin\crtmgr.exe | |||
| (PID) Process: | (2332) Bit4id_Middleware.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\bit4id\pkimanager |
| Operation: | write | Name: | name |
Value: Bit4id - PKI Manager | |||
| (PID) Process: | (2332) Bit4id_Middleware.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\Defaults\Provider\Bit4id Universal Middleware Provider |
| Operation: | write | Name: | |
Value: | |||
| (PID) Process: | (2332) Bit4id_Middleware.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\Defaults\Provider\Bit4id Universal Middleware Provider |
| Operation: | write | Name: | Image Path |
Value: bit4ucsp1.dll | |||
| (PID) Process: | (2332) Bit4id_Middleware.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\Defaults\Provider\Bit4id Universal Middleware Provider |
| Operation: | write | Name: | Type |
Value: 1 | |||
| (PID) Process: | (2332) Bit4id_Middleware.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\Defaults\Provider\Bit4id Universal Middleware Provider |
| Operation: | write | Name: | SigInFile |
Value: 0 | |||
| (PID) Process: | (2332) Bit4id_Middleware.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\Defaults\Provider\Bit4id Universal Middleware Provider |
| Operation: | write | Name: | Signature |
Value: E4B581DE9789FB55A13EE0729F15BE9B4D62E3FCB9CCA518822A8FB08B4D8676CAA48E63B64B968E6AFF0985C61708D2A293A8C66D70BDF4F1E4B9BF9DA885B7003E04E558BF9EE01DDBB351AA3E1CD0DB0D517E62873FAE2EE325188FDF0DAAA55E7F1B22F8BDD14567A0B099EA3D8D1A3DC6ABEC451671F313A9A289E711910000000000000000 | |||
| (PID) Process: | (2332) Bit4id_Middleware.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\bit4id\stub |
| Operation: | write | Name: | bit4ucsp2.dll |
Value: C:\Windows\system32\basecsp.dll | |||
| (PID) Process: | (2332) Bit4id_Middleware.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\bit4id\log |
| Operation: | write | Name: | bit4ucsp2.dll |
Value: 0 | |||
| (PID) Process: | (2332) Bit4id_Middleware.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\bit4id\log |
| Operation: | write | Name: | csp12.dll |
Value: 0 | |||
Executable files
90
Suspicious files
12
Text files
56
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2332 | Bit4id_Middleware.exe | C:\Users\admin\AppData\Local\Temp\nsa83DA.tmp\ioSpecial.ini | text | |
MD5:— | SHA256:— | |||
| 2332 | Bit4id_Middleware.exe | C:\Program Files\Bit4Id\Universal MW\icon.ico | image | |
MD5:0B24CB6BE9CF9C217EC21156B9CBBB10 | SHA256:586ACCAD16A20DF8A55F5D86C7637C6A5907444AAAFCF4C9844C294FC5B44311 | |||
| 2332 | Bit4id_Middleware.exe | C:\Program Files\Bit4Id\Universal MW\bin\Microsoft.VC90.CRT.manifest | xml | |
MD5:8AD846D90D4BCBCAF1A54CB2775F02E5 | SHA256:DDC41D9A17E607F33E5E1C23EA43CF691F761A3C7595225601DFB80615ABE620 | |||
| 2332 | Bit4id_Middleware.exe | C:\Users\admin\AppData\Local\Temp\nsa83DA.tmp\modern-wizard.bmp | image | |
MD5:2DDDAFD7D1C70ECE7D062EA77DEF5CC8 | SHA256:D092789EC8AEBD227408D874E7F7FF9A7937A1BCB6F3E78EDB1AAB4ECC490465 | |||
| 2332 | Bit4id_Middleware.exe | C:\Users\admin\AppData\Local\Temp\nsa83DA.tmp\System.dll | executable | |
MD5:56A321BD011112EC5D8A32B2F6FD3231 | SHA256:BB6DF93369B498EAA638B0BCDC4BB89F45E9B02CA12D28BCEDF4629EA7F5E0F1 | |||
| 2332 | Bit4id_Middleware.exe | C:\Users\admin\AppData\Local\Temp\nsa83DA.tmp\InstallOptions.dll | executable | |
MD5:D753362649AECD60FF434ADF171A4E7F | SHA256:8F24C6CF0B06D18F3C07E7BFCA4E92AFCE71834663746CFAA9DDF52A25D5C586 | |||
| 2332 | Bit4id_Middleware.exe | C:\Users\admin\AppData\Local\Temp\nsa83DA.tmp\LangDLL.dll | executable | |
MD5:E447E49175C0DB1F27888AEDE301084F | SHA256:FD26EF21D72797FEDECD3D15F2001CEA793383ACEB3CEE19A5AE2A3D30E197B6 | |||
| 2332 | Bit4id_Middleware.exe | C:\Users\admin\AppData\Local\Temp\nsa83DA.tmp\modern-header.bmp | image | |
MD5:CE7E83FD1FC35FCEAF5DE4224C77F08D | SHA256:294F6F6AB7EEF4B5A66BE185EB9E3AB4F85A74A73886441039AA2D3A45287260 | |||
| 2332 | Bit4id_Middleware.exe | C:\Program Files\Bit4Id\Universal MW\bin\qt_pt.qm | qm | |
MD5:51C3797845D9CED4C19EF6E3BA4E7CF6 | SHA256:452B07E281B1F80E8D9D09A63C50A246EBDC555F8959B5F4A537247FCEA1CFBF | |||
| 2332 | Bit4id_Middleware.exe | C:\Program Files\Bit4Id\Universal MW\bin\qt.conf | text | |
MD5:D0C3389EB6E14F0639E4F239A178E4E2 | SHA256:FA40BAFE3FF14BE61C2AA9FC205B34D3C07FDEEC3DB0125E563D57CC95BF95D8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report