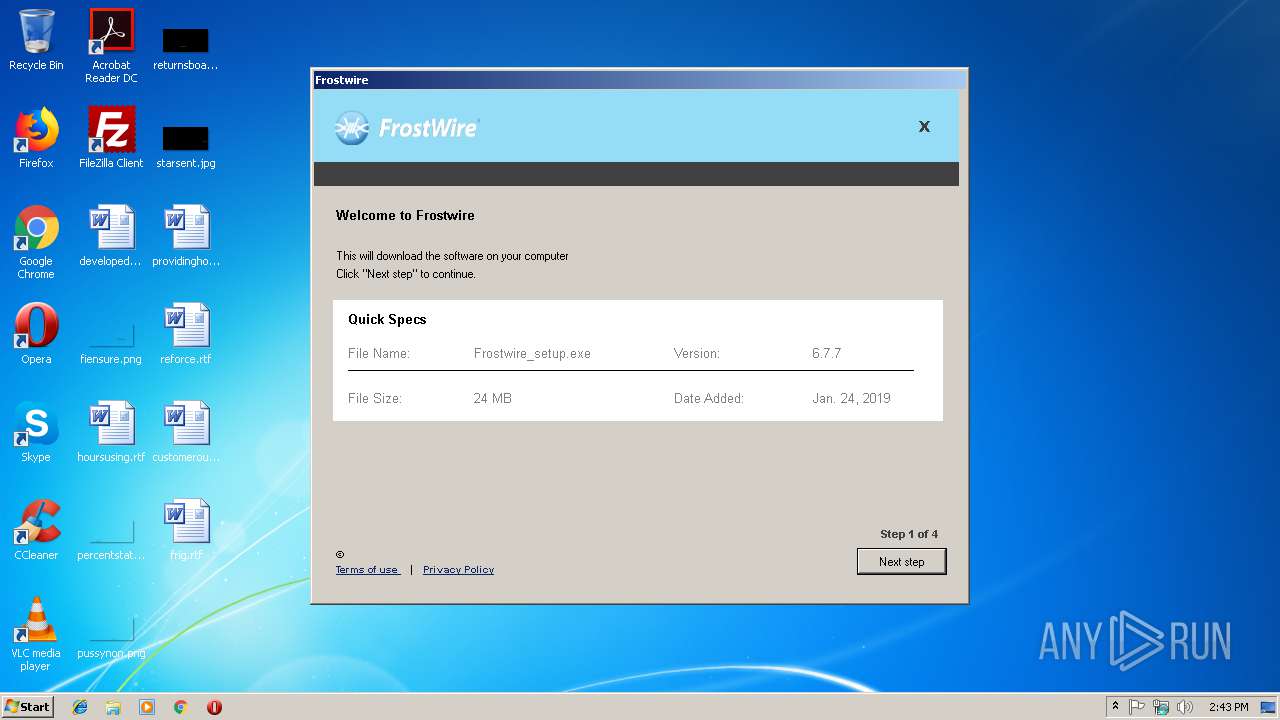
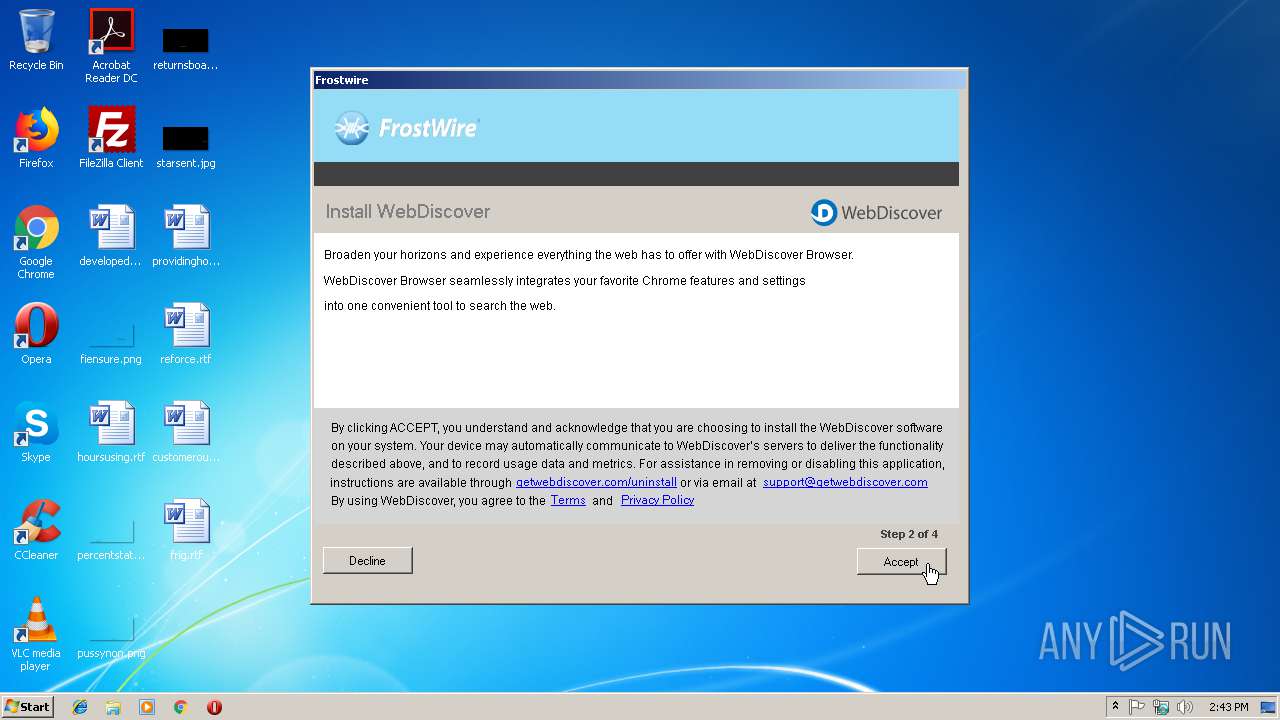
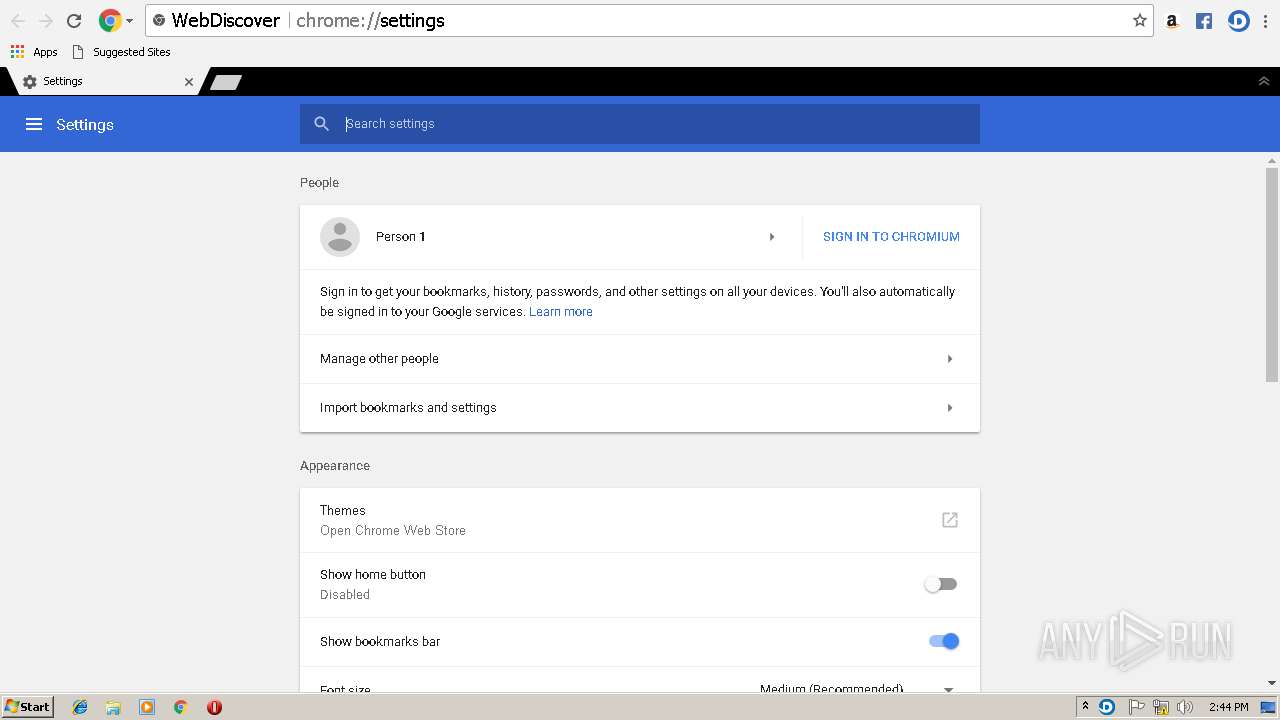
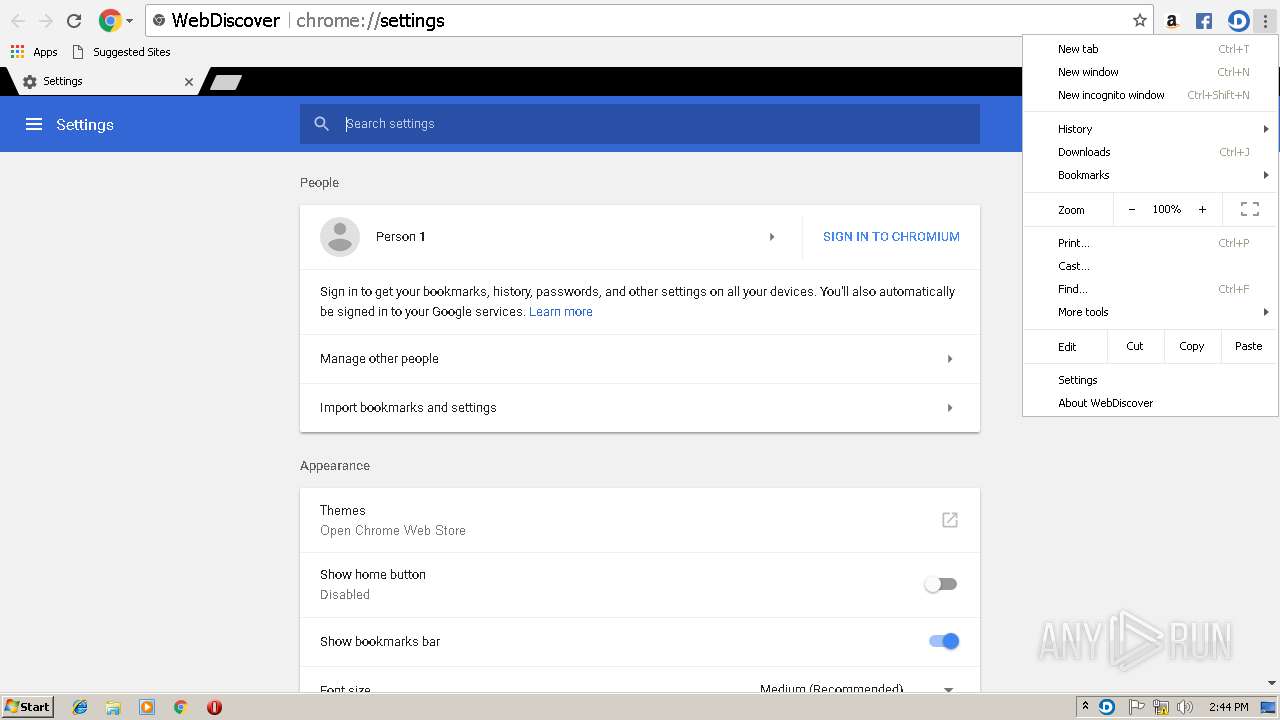
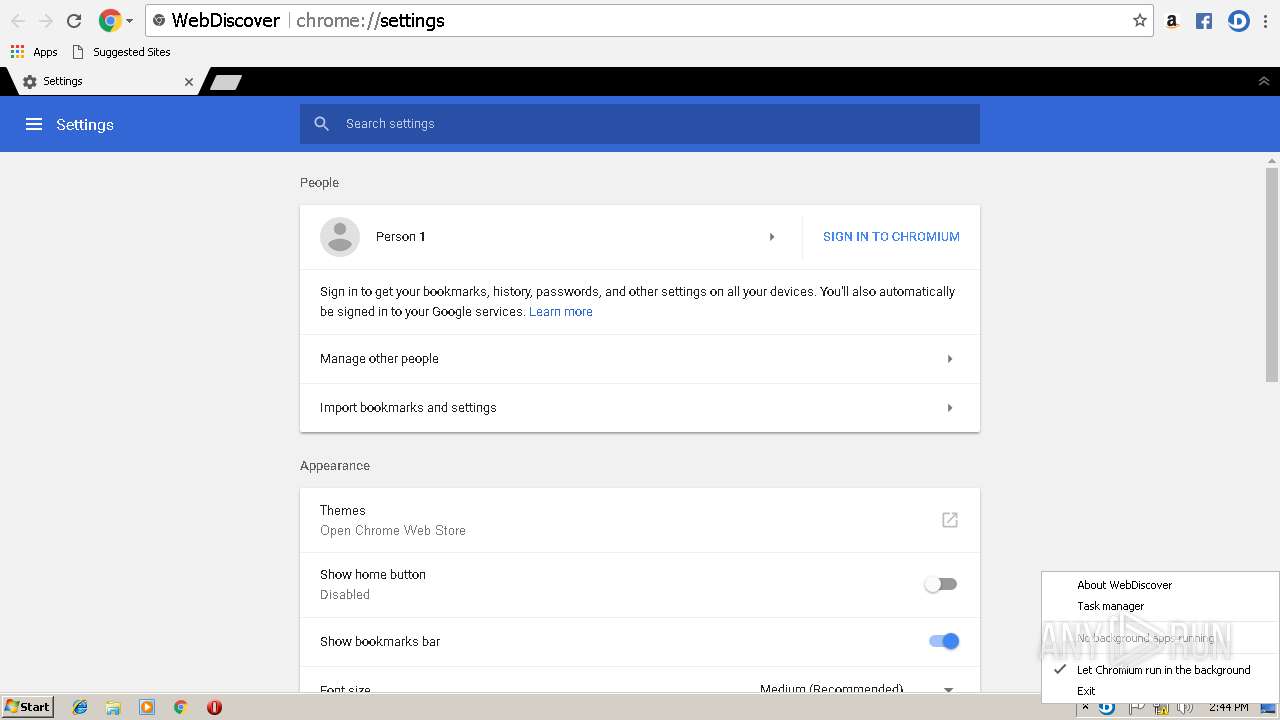
| File name: | Frostwire.exe |
| Full analysis: | https://app.any.run/tasks/1ab750c9-cc1b-4e89-9d21-a733ab165cc4 |
| Verdict: | Malicious activity |
| Analysis date: | January 26, 2019, 14:42:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | CC774E9FA0F6C59618B0A7BBD43B2E67 |
| SHA1: | 673F7653116E9A358BC67439EC7FB53A293982CB |
| SHA256: | DB6E9F121CF5CB31E6938074D0CBF4035AB7EE335393721A1FB88DFDA85183D1 |
| SSDEEP: | 6144:t9L2n0e/E4T9LPa5etgtxOAFygX3raiN8bkd9RP3EHl5E4pmNJ0z+jIayISl9N:qnL/IbgENX3rbCbSjvU/E4pEJdIuS7N |
MALICIOUS
Application was dropped or rewritten from another process
- Frostwire_setup.exe (PID: 3248)
- browser.exe (PID: 3008)
- browser.exe (PID: 3744)
- browser.exe (PID: 2120)
- browser.exe (PID: 2504)
- browser.exe (PID: 3572)
- browser.exe (PID: 3068)
- browser.exe (PID: 992)
- browser.exe (PID: 3360)
- browser.exe (PID: 2412)
- browser.exe (PID: 2228)
- browser.exe (PID: 3940)
- browser.exe (PID: 3820)
- browser.exe (PID: 3368)
- browser.exe (PID: 3240)
- unpack200.exe (PID: 3436)
- browser.exe (PID: 2848)
- unpack200.exe (PID: 2592)
- browser.exe (PID: 2964)
Uses Task Scheduler to run other applications
- WebDiscovery_setup.tmp (PID: 1048)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 3056)
- schtasks.exe (PID: 4020)
- schtasks.exe (PID: 2728)
- schtasks.exe (PID: 3716)
- schtasks.exe (PID: 316)
- schtasks.exe (PID: 2984)
Loads dropped or rewritten executable
- Frostwire_setup.exe (PID: 3248)
- browser.exe (PID: 2120)
- browser.exe (PID: 3744)
- browser.exe (PID: 3008)
- browser.exe (PID: 2504)
- browser.exe (PID: 3572)
- browser.exe (PID: 3068)
- browser.exe (PID: 3360)
- browser.exe (PID: 992)
- browser.exe (PID: 2228)
- browser.exe (PID: 3940)
- browser.exe (PID: 2412)
- browser.exe (PID: 3368)
- browser.exe (PID: 3820)
- browser.exe (PID: 3240)
- unpack200.exe (PID: 2592)
- browser.exe (PID: 2848)
- unpack200.exe (PID: 3436)
- browser.exe (PID: 2964)
Changes the autorun value in the registry
- WebDiscovery_setup.tmp (PID: 1048)
Changes settings of System certificates
- browser.exe (PID: 2504)
Downloads executable files from the Internet
- Frostwire.exe (PID: 3824)
SUSPICIOUS
Reads internet explorer settings
- Frostwire.exe (PID: 3824)
Reads Windows owner or organization settings
- WebDiscovery_setup.tmp (PID: 1048)
Creates files in the user directory
- Frostwire.exe (PID: 3824)
- Frostwire_setup.exe (PID: 3248)
Executable content was dropped or overwritten
- WebDiscovery_setup.exe (PID: 3792)
- WebDiscovery_setup.tmp (PID: 1048)
- Frostwire_setup.exe (PID: 3248)
- Frostwire.exe (PID: 3824)
Reads the Windows organization settings
- WebDiscovery_setup.tmp (PID: 1048)
Reads the machine GUID from the registry
- WebDiscovery_setup.tmp (PID: 1048)
Starts SC.EXE for service management
- WebDiscovery_setup.tmp (PID: 1048)
Application launched itself
- browser.exe (PID: 3008)
- browser.exe (PID: 2504)
Searches for installed software
- WebDiscovery_setup.tmp (PID: 1048)
Creates files in the program directory
- Frostwire_setup.exe (PID: 3248)
- unpack200.exe (PID: 2592)
- unpack200.exe (PID: 3436)
Modifies the open verb of a shell class
- Frostwire_setup.exe (PID: 3248)
Adds / modifies Windows certificates
- browser.exe (PID: 2504)
Creates a software uninstall entry
- Frostwire_setup.exe (PID: 3248)
Starts Internet Explorer
- Frostwire_setup.exe (PID: 3248)
INFO
Application was dropped or rewritten from another process
- WebDiscovery_setup.tmp (PID: 1048)
Dropped object may contain Bitcoin addresses
- WebDiscovery_setup.tmp (PID: 1048)
Creates a software uninstall entry
- WebDiscovery_setup.tmp (PID: 1048)
Creates files in the program directory
- WebDiscovery_setup.tmp (PID: 1048)
Changes internet zones settings
- iexplore.exe (PID: 2988)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3876)
Application launched itself
- iexplore.exe (PID: 2988)
Reads internet explorer settings
- iexplore.exe (PID: 3876)
Creates files in the user directory
- iexplore.exe (PID: 3876)
Reads Internet Cache Settings
- iexplore.exe (PID: 3876)
- iexplore.exe (PID: 2988)
Changes settings of System certificates
- iexplore.exe (PID: 3876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:01:24 15:34:54+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 378880 |
| InitializedDataSize: | 134144 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5e642 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Frostwire |
| FileVersion: | 1.0.0.0 |
| InternalName: | Frostwire.exe |
| LegalCopyright: | Copyright © 2018 |
| LegalTrademarks: | - |
| OriginalFileName: | Frostwire.exe |
| ProductName: | Frostwire |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 24-Jan-2019 14:34:54 |
| Debug artifacts: |
|
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Frostwire |
| FileVersion: | 1.0.0.0 |
| InternalName: | Frostwire.exe |
| LegalCopyright: | Copyright © 2018 |
| LegalTrademarks: | - |
| OriginalFilename: | Frostwire.exe |
| ProductName: | Frostwire |
| ProductVersion: | 1.0.0.0 |
| Assembly Version: | 1.0.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 24-Jan-2019 14:34:54 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x0005C648 | 0x0005C800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.57351 |
.rsrc | 0x00060000 | 0x00020984 | 0x00020A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.14593 |
.reloc | 0x00082000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.0055 | 3174 | UNKNOWN | UNKNOWN | RT_MANIFEST |
2 | 6.05 | 2216 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 6.02158 | 1736 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 6.11117 | 1384 | UNKNOWN | UNKNOWN | RT_ICON |
5 | 7.96208 | 34461 | UNKNOWN | UNKNOWN | RT_ICON |
6 | 4.82148 | 67624 | UNKNOWN | UNKNOWN | RT_ICON |
7 | 5.0654 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
8 | 5.21567 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
9 | 5.05767 | 2440 | UNKNOWN | UNKNOWN | RT_ICON |
10 | 5.22344 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
Imports
mscoree.dll |
Total processes
75
Monitored processes
32
Malicious processes
5
Suspicious processes
12
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "schtasks" /create /ru SYSTEM /tn "WebDiscover Browser Update Task" /tr "\"C:\Program Files\WebDiscoverBrowser\4.28.2\browser.exe\" --update" /sc daily /ri 120 /du 24:00 /f | C:\Windows\system32\schtasks.exe | — | WebDiscovery_setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 992 | "C:\Program Files\WebDiscoverBrowser\4.28.2\browser.exe" --type=renderer --field-trial-handle=2028,7112174566135418253,16534492324882701172,131072 --service-pipe-token=FFFF4B839B834F18BEF2901236E5FD87 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --enable-gpu-async-worker-context --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553;5,0,3553;5,1,3553;5,2,3553;5,3,3553;5,4,3553;5,5,3553;5,6,3553;5,7,3553;5,8,3553;5,9,3553;5,10,3553;5,11,3553;5,12,3553;5,13,3553;5,14,3553;5,15,3553;5,16,3553;5,17,3553;6,0,3553;6,1,3553;6,2,3553;6,3,3553;6,4,3553;6,5,3553;6,6,3553;6,7,3553;6,8,3553;6,9,3553;6,10,3553;6,11,3553;6,12,3553;6,13,3553;6,14,3553;6,15,3553;6,16,3553;6,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --service-request-channel-token=FFFF4B839B834F18BEF2901236E5FD87 --renderer-client-id=2 --mojo-platform-channel-handle=2016 /prefetch:1 | C:\Program Files\WebDiscoverBrowser\4.28.2\browser.exe | — | browser.exe | |||||||||||
User: admin Company: WebDiscover Media Integrity Level: LOW Description: WebDiscover Browser Exit code: 0 Version: 63.0.3239.132 Modules
| |||||||||||||||
| 1048 | "C:\Users\admin\AppData\Local\Temp\is-UFLDQ.tmp\WebDiscovery_setup.tmp" /SL5="$101A6,48494708,225280,C:\Users\admin\AppData\Roaming\WebDiscovery_setup.exe" /VERYSILENT /SUPPRESSMSGBOXES /NORESTART /NOCLOSEAPPLICATIONS /TID=kodio /PROFILE=kodio /CHANNEL=kodio /SID=814 | C:\Users\admin\AppData\Local\Temp\is-UFLDQ.tmp\WebDiscovery_setup.tmp | WebDiscovery_setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2120 | "C:\Program Files\WebDiscoverBrowser\4.28.2\browser.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\WebDiscoverBrowser\User Data" /prefetch:7 --no-periodic-tasks --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\WebDiscoverBrowser\User Data\Crashpad" --annotation=plat=Win32 --annotation=prod=WebDiscover --annotation=ver=63.0.3239.132-devel --initial-client-data=0x90,0x94,0x98,0x88,0x9c,0xd70cd0,0xd70ca8,0xd70cb8 | C:\Program Files\WebDiscoverBrowser\4.28.2\browser.exe | — | browser.exe | |||||||||||
User: admin Company: WebDiscover Media Integrity Level: HIGH Description: WebDiscover Browser Exit code: 0 Version: 63.0.3239.132 Modules
| |||||||||||||||
| 2228 | "C:\Program Files\WebDiscoverBrowser\4.28.2\browser.exe" --type=utility --field-trial-handle=2028,7112174566135418253,16534492324882701172,131072 --lang=en-US --service-sandbox-type=utility --service-request-channel-token=860C467B1DB15F184A8A6E0E6764A56C --mojo-platform-channel-handle=2640 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\WebDiscoverBrowser\4.28.2\browser.exe | — | browser.exe | |||||||||||
User: admin Company: WebDiscover Media Integrity Level: LOW Description: WebDiscover Browser Exit code: 0 Version: 63.0.3239.132 Modules
| |||||||||||||||
| 2412 | "C:\Program Files\WebDiscoverBrowser\4.28.2\browser.exe" --type=utility --field-trial-handle=2028,7112174566135418253,16534492324882701172,131072 --lang=en-US --service-sandbox-type=utility --service-request-channel-token=95BC19767F437D0DE0CAF408B39C2C0E --mojo-platform-channel-handle=2980 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\WebDiscoverBrowser\4.28.2\browser.exe | — | browser.exe | |||||||||||
User: admin Company: WebDiscover Media Integrity Level: LOW Description: WebDiscover Browser Exit code: 0 Version: 63.0.3239.132 Modules
| |||||||||||||||
| 2504 | "C:\Program Files\WebDiscoverBrowser\4.28.2\browser.exe" --docked | C:\Program Files\WebDiscoverBrowser\4.28.2\browser.exe | WebDiscovery_setup.tmp | ||||||||||||
User: admin Company: WebDiscover Media Integrity Level: HIGH Description: WebDiscover Browser Exit code: 0 Version: 63.0.3239.132 Modules
| |||||||||||||||
| 2592 | "C:\Program Files\FrostWire 6\jre\bin\unpack200.exe" "C:\Program Files\FrostWire 6\frostwire.jar.pack" "C:\Program Files\FrostWire 6\frostwire.jar" | C:\Program Files\FrostWire 6\jre\bin\unpack200.exe | — | Frostwire_setup.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.1620.12 Modules
| |||||||||||||||
| 2728 | "schtasks" /delete /tn "WebDiscover Launch Task" /f | C:\Windows\system32\schtasks.exe | — | WebDiscovery_setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2848 | "C:\Program Files\WebDiscoverBrowser\4.28.2\browser.exe" --type=renderer --field-trial-handle=2028,7112174566135418253,16534492324882701172,131072 --service-pipe-token=65399BA1F05861DE1D02A859B27DE8E2 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --enable-gpu-async-worker-context --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553;5,0,3553;5,1,3553;5,2,3553;5,3,3553;5,4,3553;5,5,3553;5,6,3553;5,7,3553;5,8,3553;5,9,3553;5,10,3553;5,11,3553;5,12,3553;5,13,3553;5,14,3553;5,15,3553;5,16,3553;5,17,3553;6,0,3553;6,1,3553;6,2,3553;6,3,3553;6,4,3553;6,5,3553;6,6,3553;6,7,3553;6,8,3553;6,9,3553;6,10,3553;6,11,3553;6,12,3553;6,13,3553;6,14,3553;6,15,3553;6,16,3553;6,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --service-request-channel-token=65399BA1F05861DE1D02A859B27DE8E2 --renderer-client-id=10 --mojo-platform-channel-handle=3196 /prefetch:1 | C:\Program Files\WebDiscoverBrowser\4.28.2\browser.exe | — | browser.exe | |||||||||||
User: admin Company: WebDiscover Media Integrity Level: LOW Description: WebDiscover Browser Exit code: 0 Version: 63.0.3239.132 Modules
| |||||||||||||||
Total events
1 570
Read events
1 289
Write events
275
Delete events
6
Modification events
| (PID) Process: | (3824) Frostwire.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Frostwire_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3824) Frostwire.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Frostwire_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3824) Frostwire.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Frostwire_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3824) Frostwire.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Frostwire_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3824) Frostwire.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Frostwire_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3824) Frostwire.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Frostwire_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3824) Frostwire.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Frostwire_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3824) Frostwire.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Frostwire_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3824) Frostwire.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Frostwire_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3824) Frostwire.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Frostwire_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
Executable files
106
Suspicious files
41
Text files
121
Unknown types
104
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3824 | Frostwire.exe | C:\Users\admin\AppData\Roaming\WebDiscovery_setup.exe | — | |
MD5:— | SHA256:— | |||
| 1048 | WebDiscovery_setup.tmp | C:\Program Files\WebDiscoverBrowser\is-LLAUS.tmp | — | |
MD5:— | SHA256:— | |||
| 1048 | WebDiscovery_setup.tmp | C:\Program Files\WebDiscoverBrowser\4.28.2\is-MRAV2.tmp | — | |
MD5:— | SHA256:— | |||
| 1048 | WebDiscovery_setup.tmp | C:\Program Files\WebDiscoverBrowser\4.28.2\is-CONR6.tmp | — | |
MD5:— | SHA256:— | |||
| 1048 | WebDiscovery_setup.tmp | C:\Program Files\WebDiscoverBrowser\4.28.2\is-6C0G2.tmp | — | |
MD5:— | SHA256:— | |||
| 1048 | WebDiscovery_setup.tmp | C:\Program Files\WebDiscoverBrowser\4.28.2\chrome.dll | — | |
MD5:— | SHA256:— | |||
| 1048 | WebDiscovery_setup.tmp | C:\Program Files\WebDiscoverBrowser\4.28.2\is-MTT1M.tmp | — | |
MD5:— | SHA256:— | |||
| 1048 | WebDiscovery_setup.tmp | C:\Program Files\WebDiscoverBrowser\4.28.2\is-B0A83.tmp | — | |
MD5:— | SHA256:— | |||
| 1048 | WebDiscovery_setup.tmp | C:\Program Files\WebDiscoverBrowser\4.28.2\is-6FCFC.tmp | — | |
MD5:— | SHA256:— | |||
| 1048 | WebDiscovery_setup.tmp | C:\Program Files\WebDiscoverBrowser\4.28.2\chrome_child.dll | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
56
TCP/UDP connections
47
DNS requests
40
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3824 | Frostwire.exe | GET | — | 151.139.240.12:80 | http://source.cdnquest.com/1b1d4cde/setupdsc.exe | US | — | — | malicious |
— | — | HEAD | 302 | 216.58.207.78:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/cfplL4AmE8U_32.0.0.114/32.0.0.114_win_PepperFlashPlayer.crx3 | US | — | — | whitelisted |
3824 | Frostwire.exe | GET | 200 | 195.154.62.36:80 | http://cache-01.net/readautoip.php?prefix=wink | FR | text | 432 b | malicious |
3824 | Frostwire.exe | GET | 200 | 143.204.101.33:80 | http://dl7.frostwire.com/frostwire/6.7.7/frostwire-6.7.7.windows.kodio.exe | US | executable | 23.4 Mb | whitelisted |
— | — | HEAD | 200 | 173.194.182.234:80 | http://r5---sn-4g5e6nsz.gvt1.com/edgedl/release2/chrome_component/cfplL4AmE8U_32.0.0.114/32.0.0.114_win_PepperFlashPlayer.crx3?cms_redirect=yes&mip=185.183.107.227&mm=28&mn=sn-4g5e6nsz&ms=nvh&mt=1548513740&mv=m&pl=24&shardbypass=yes | US | — | — | whitelisted |
— | — | GET | 206 | 173.194.182.234:80 | http://r5---sn-4g5e6nsz.gvt1.com/edgedl/release2/chrome_component/cfplL4AmE8U_32.0.0.114/32.0.0.114_win_PepperFlashPlayer.crx3?cms_redirect=yes&mip=185.183.107.227&mm=28&mn=sn-4g5e6nsz&ms=nvh&mt=1548513815&mv=m&pl=24&shardbypass=yes | US | binary | 10.6 Kb | whitelisted |
1048 | WebDiscovery_setup.tmp | GET | 200 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 55.2 Kb | whitelisted |
2504 | browser.exe | GET | 302 | 216.58.207.78:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/AI-EZDZO96NE_4936/4936_all_crl-set-7431647380890755595.data.crx3 | US | html | 465 b | whitelisted |
— | — | GET | 302 | 216.58.207.78:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/cfplL4AmE8U_32.0.0.114/32.0.0.114_win_PepperFlashPlayer.crx3 | US | html | 461 b | whitelisted |
2504 | browser.exe | GET | 200 | 74.125.13.231:80 | http://r2---sn-4g5e6nzs.gvt1.com/edgedl/release2/chrome_component/AI-EZDZO96NE_4936/4936_all_crl-set-7431647380890755595.data.crx3?cms_redirect=yes&mip=185.183.107.227&mm=28&mn=sn-4g5e6nzs&ms=nvh&mt=1548513740&mv=m&pl=24&shardbypass=yes | US | crx | 16.3 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3824 | Frostwire.exe | 195.154.62.36:80 | cache-01.net | Online S.a.s. | FR | malicious |
3824 | Frostwire.exe | 151.139.240.12:80 | source.cdnquest.com | netDNA | US | suspicious |
3824 | Frostwire.exe | 143.204.101.33:80 | dl7.frostwire.com | — | US | malicious |
3824 | Frostwire.exe | 62.210.6.175:80 | pix-fix.net | Online S.a.s. | FR | suspicious |
1048 | WebDiscovery_setup.tmp | 104.18.61.205:443 | update.getdiscoverbrowser.com | Cloudflare Inc | US | shared |
3248 | Frostwire_setup.exe | 50.16.13.109:80 | logs.frostwire.com | Amazon.com, Inc. | US | suspicious |
3008 | browser.exe | 104.18.61.205:443 | update.getdiscoverbrowser.com | Cloudflare Inc | US | shared |
1048 | WebDiscovery_setup.tmp | 52.89.177.131:443 | api.keen.io | Amazon.com, Inc. | US | unknown |
2504 | browser.exe | 104.18.61.205:443 | update.getdiscoverbrowser.com | Cloudflare Inc | US | shared |
2504 | browser.exe | 104.24.123.44:443 | getwebdiscover.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cache-01.net |
| malicious |
source.cdnquest.com |
| malicious |
dl7.frostwire.com |
| whitelisted |
update.getdiscoverbrowser.com |
| whitelisted |
pix-fix.net |
| suspicious |
logs.frostwire.com |
| suspicious |
api.keen.io |
| whitelisted |
x.ss2.us |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3824 | Frostwire.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3824 | Frostwire.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3824 | Frostwire.exe | Potentially Bad Traffic | ET POLICY Executable served from Amazon S3 |
3824 | Frostwire.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3824 | Frostwire.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3248 | Frostwire_setup.exe | A Network Trojan was detected | ET POLICY User-Agent (NSIS_Inetc (Mozilla)) - Sometimes used by hostile installers |
3248 | Frostwire_setup.exe | Misc activity | SUSPICIOUS [PTsecurity] Suspicious HTTP header - Sometimes used by hostile installer |
3248 | Frostwire_setup.exe | A Network Trojan was detected | ET POLICY User-Agent (NSIS_Inetc (Mozilla)) - Sometimes used by hostile installers |
3248 | Frostwire_setup.exe | Misc activity | SUSPICIOUS [PTsecurity] Suspicious HTTP header - Sometimes used by hostile installer |
3248 | Frostwire_setup.exe | A Network Trojan was detected | ET POLICY User-Agent (NSIS_Inetc (Mozilla)) - Sometimes used by hostile installers |