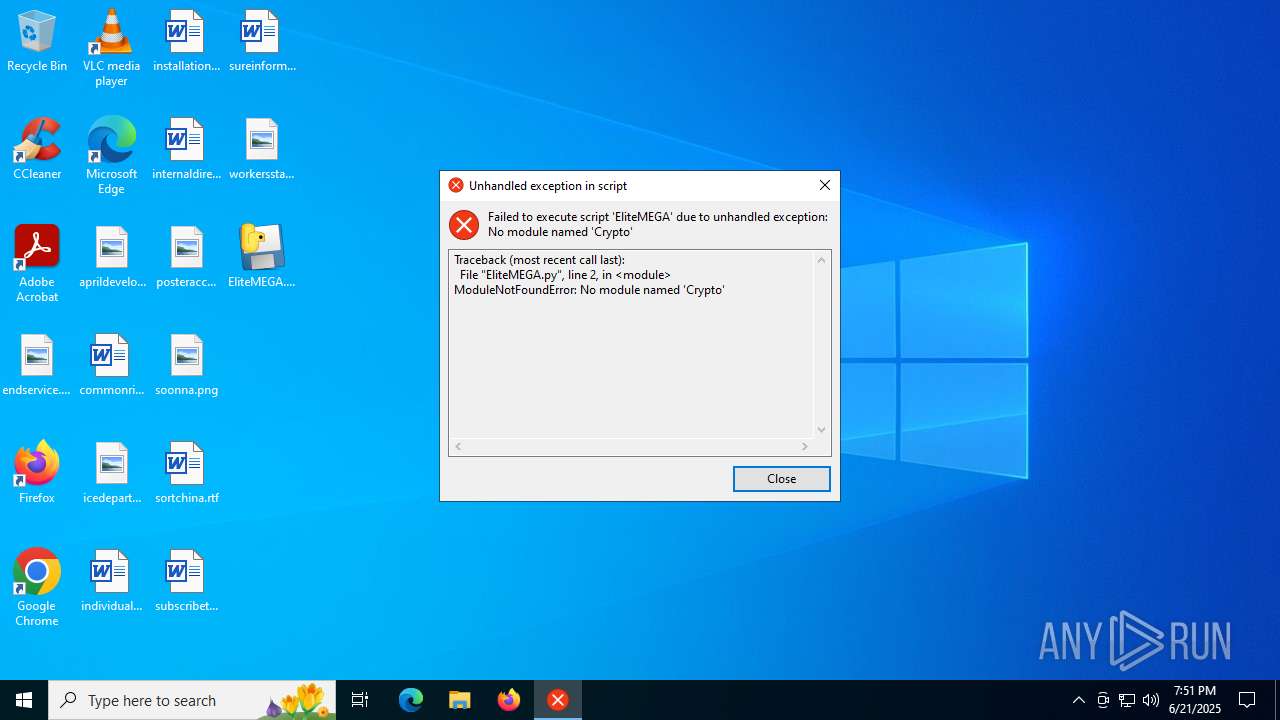
| File name: | EliteMEGA.exe |
| Full analysis: | https://app.any.run/tasks/5d0d20c5-0032-4a89-a4eb-209ceebdd6ae |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 19:51:40 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | B8955763C07B0A4D7FBC40C2F8651ECB |
| SHA1: | 6C4223F3A5CAC77FF19235BA769894B363B31113 |
| SHA256: | DB6DF8D9AE5E8E6DB0C33DD7A282FB2FC917829358F9E104EDB8ED715398383B |
| SSDEEP: | 98304:3C3CpAmOAMBtg3Rm1T8OFOMYFr3ZyUuYA3w31a+kzK/7ueSnKHdyIS0x8UBAoFq2:6xia2ztwkWR7fGDfarL |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- EliteMEGA.exe (PID: 3976)
The process drops C-runtime libraries
- EliteMEGA.exe (PID: 3976)
Application launched itself
- EliteMEGA.exe (PID: 3976)
Process drops python dynamic module
- EliteMEGA.exe (PID: 3976)
Executable content was dropped or overwritten
- EliteMEGA.exe (PID: 3976)
Loads Python modules
- EliteMEGA.exe (PID: 7048)
INFO
Checks supported languages
- EliteMEGA.exe (PID: 3976)
- EliteMEGA.exe (PID: 7048)
Create files in a temporary directory
- EliteMEGA.exe (PID: 3976)
Reads the computer name
- EliteMEGA.exe (PID: 3976)
- EliteMEGA.exe (PID: 7048)
The sample compiled with english language support
- EliteMEGA.exe (PID: 3976)
Reads the machine GUID from the registry
- EliteMEGA.exe (PID: 7048)
Reads the software policy settings
- slui.exe (PID: 6236)
Checks proxy server information
- slui.exe (PID: 6236)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:21 19:46:47+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 174592 |
| InitializedDataSize: | 157184 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xd0d0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
136
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3976 | "C:\Users\admin\Desktop\EliteMEGA.exe" | C:\Users\admin\Desktop\EliteMEGA.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 6236 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7048 | "C:\Users\admin\Desktop\EliteMEGA.exe" | C:\Users\admin\Desktop\EliteMEGA.exe | — | EliteMEGA.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
Total events
3 671
Read events
3 671
Write events
0
Delete events
0
Modification events
Executable files
64
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3976 | EliteMEGA.exe | C:\Users\admin\AppData\Local\Temp\_MEI39762\VCRUNTIME140_1.dll | executable | |
MD5:7667B0883DE4667EC87C3B75BED84D84 | SHA256:04E7CCBDCAD7CBAF0ED28692FB08EAB832C38AAD9071749037EE7A58F45E9D7D | |||
| 3976 | EliteMEGA.exe | C:\Users\admin\AppData\Local\Temp\_MEI39762\VCRUNTIME140.dll | executable | |
MD5:11D9AC94E8CB17BD23DEA89F8E757F18 | SHA256:E1D6F78A72836EA120BD27A33AE89CBDC3F3CA7D9D0231AAA3AAC91996D2FA4E | |||
| 3976 | EliteMEGA.exe | C:\Users\admin\AppData\Local\Temp\_MEI39762\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:7DC2026ABEDAA10841EAE4129EF1A9AE | SHA256:E83D5E5EB772070999F34A214EBFFCF0A6068EBC1C4B4F1991188448F323808D | |||
| 3976 | EliteMEGA.exe | C:\Users\admin\AppData\Local\Temp\_MEI39762\_decimal.pyd | executable | |
MD5:1CDD7239FC63B7C8A2E2BC0A08D9EA76 | SHA256:384993B2B8CFCBF155E63F0EE2383A9F9483DE92AB73736FF84590A0C4CA2690 | |||
| 3976 | EliteMEGA.exe | C:\Users\admin\AppData\Local\Temp\_MEI39762\_multiprocessing.pyd | executable | |
MD5:FCE357F864A558C03ED17755F87D0E30 | SHA256:000486AAAC9DD21E88B3DC65FD854DD83519B1FBCC224A70530BC3EC8CBD1A5D | |||
| 3976 | EliteMEGA.exe | C:\Users\admin\AppData\Local\Temp\_MEI39762\_queue.pyd | executable | |
MD5:C9EE37E9F3BFFD296ADE10A27C7E5B50 | SHA256:9ECEC72C5FE3C83C122043CAD8CEB80D239D99D03B8EA665490BBCED183CE42A | |||
| 3976 | EliteMEGA.exe | C:\Users\admin\AppData\Local\Temp\_MEI39762\_overlapped.pyd | executable | |
MD5:5BFE7D9E1877FDDE718BB84B67D8BE68 | SHA256:FE5666C1C8215CD2773744C815FB4A3B2F52F64CF0DDE25D458441DA22BF5568 | |||
| 3976 | EliteMEGA.exe | C:\Users\admin\AppData\Local\Temp\_MEI39762\_ssl.pyd | executable | |
MD5:11C5008E0BA2CAA8ADF7452F0AAAFD1E | SHA256:BF63F44951F14C9D0C890415D013276498D6D59E53811BBE2FA16825710BEA14 | |||
| 3976 | EliteMEGA.exe | C:\Users\admin\AppData\Local\Temp\_MEI39762\api-ms-win-core-errorhandling-l1-1-0.dll | executable | |
MD5:A538B281F8E84CECDAC507C73A43D744 | SHA256:45AFAF08D1CD7E43AC5DED47ED5FD708B86E835A9470C81E8130ED6955B84DB8 | |||
| 3976 | EliteMEGA.exe | C:\Users\admin\AppData\Local\Temp\_MEI39762\api-ms-win-core-console-l1-1-0.dll | executable | |
MD5:1BEBD9B65ED18B680F7E39BEF09FE6CE | SHA256:E756F6970905657CF73ECB3F57BAE55A67BE29AFA75AE4D16046B0F7229708EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
47
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1812 | RUXIMICS.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.160.66:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 200 | 20.190.160.4:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | POST | 200 | 20.190.160.67:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | POST | 200 | 20.190.160.128:443 | https://login.live.com/RST2.srf | unknown | xml | 11.0 Kb | whitelisted |
— | — | POST | 200 | 40.126.32.72:443 | https://login.live.com/RST2.srf | unknown | xml | 10.3 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1812 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1812 | RUXIMICS.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |