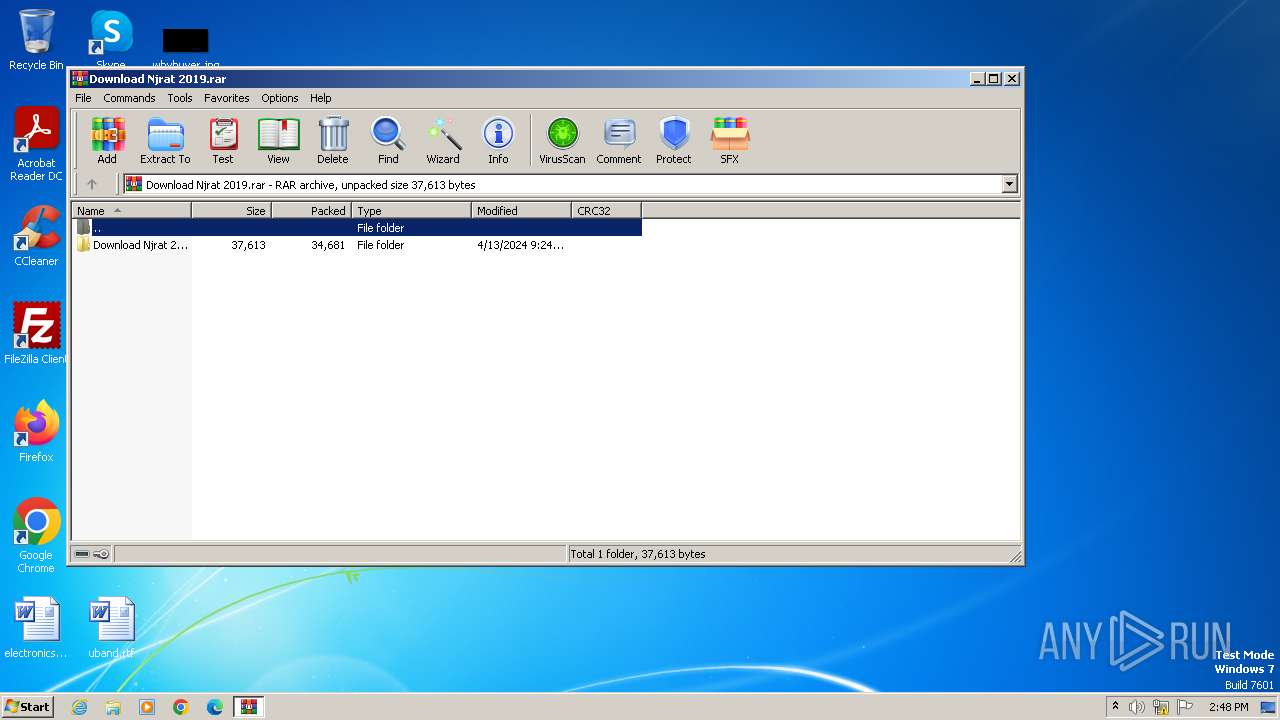
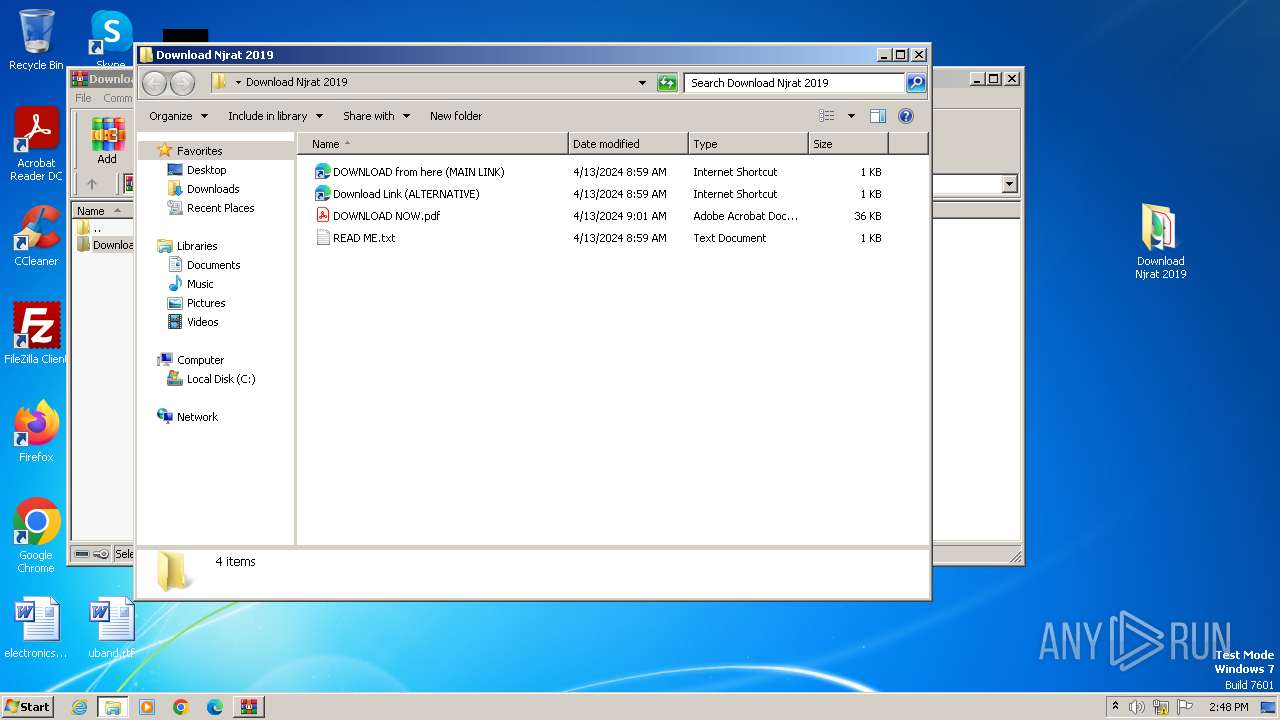
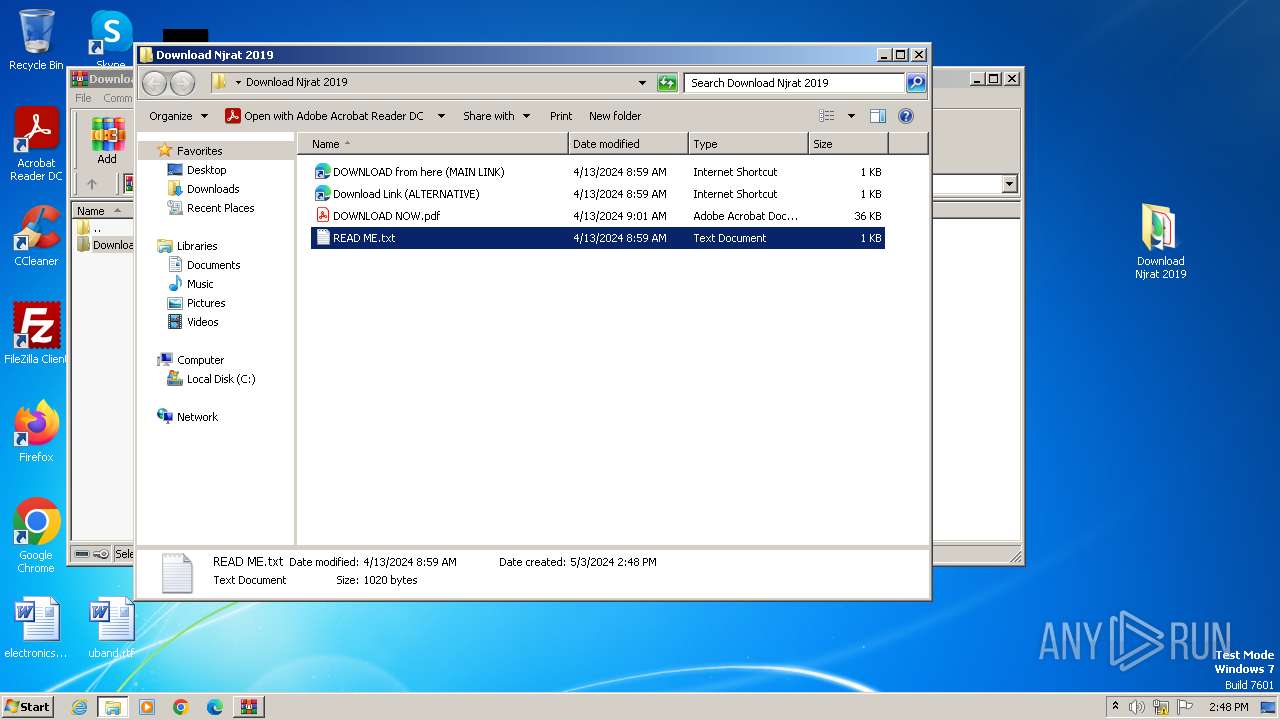
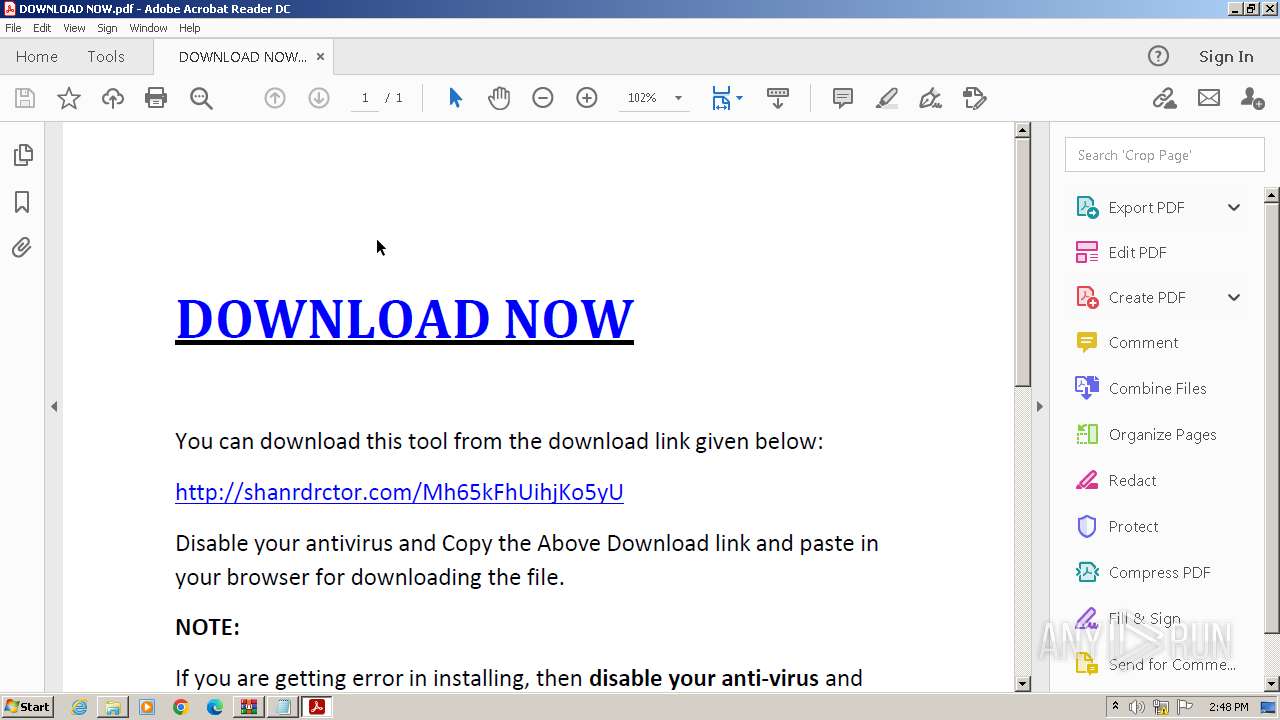
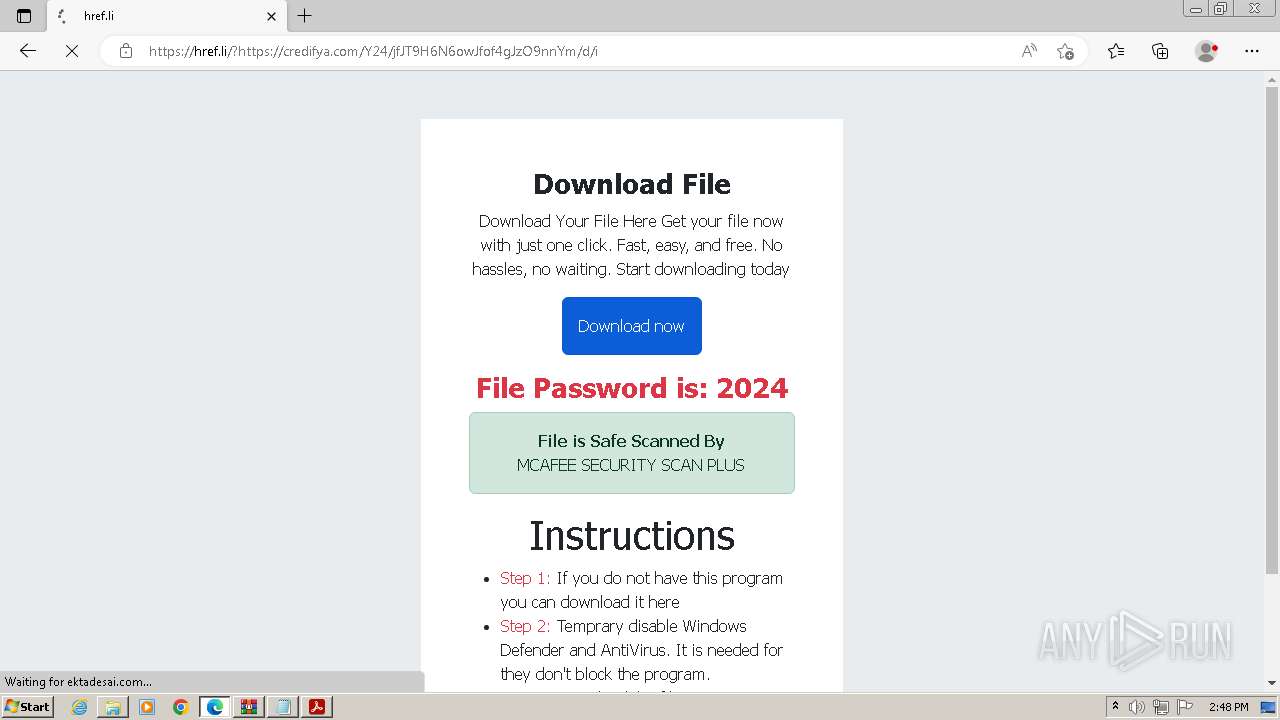
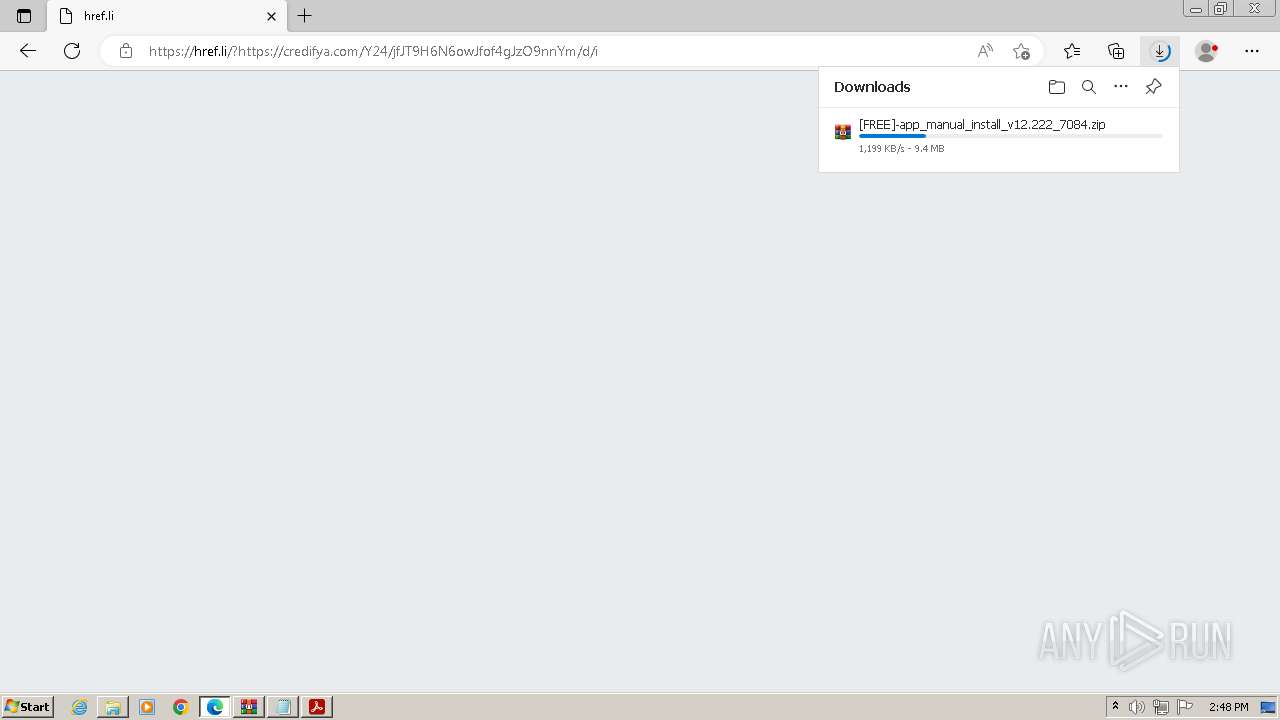
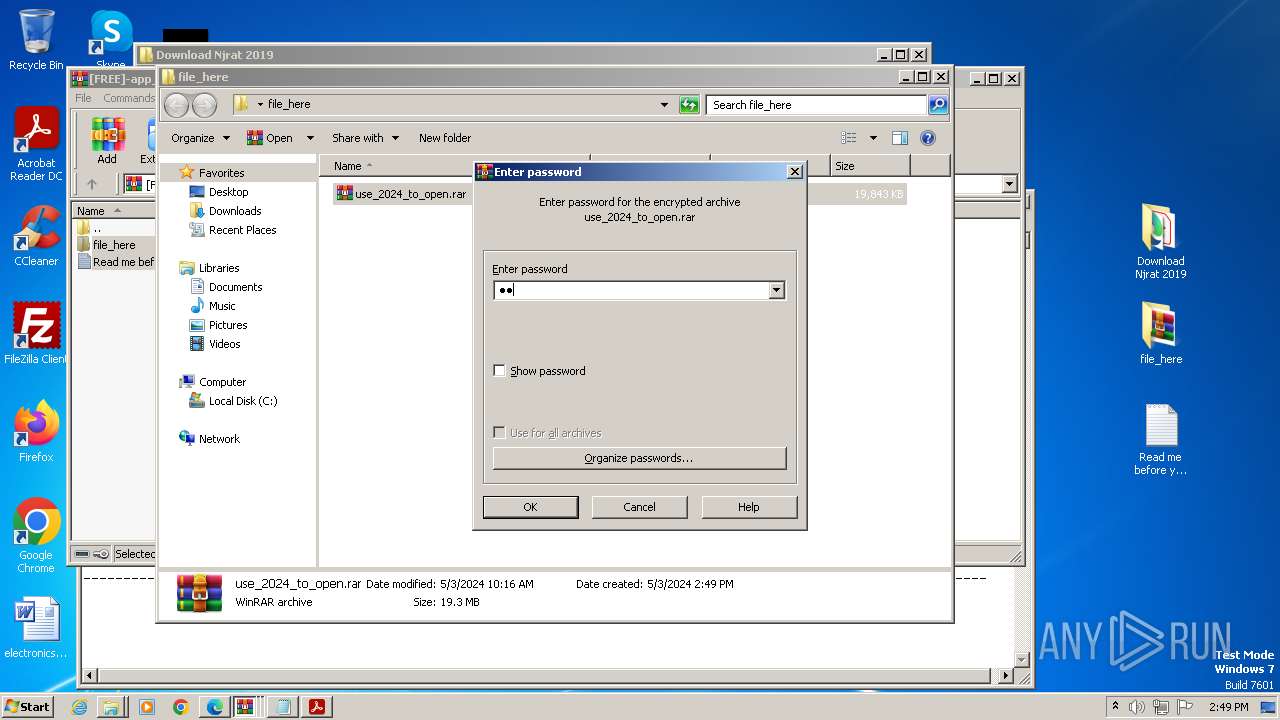
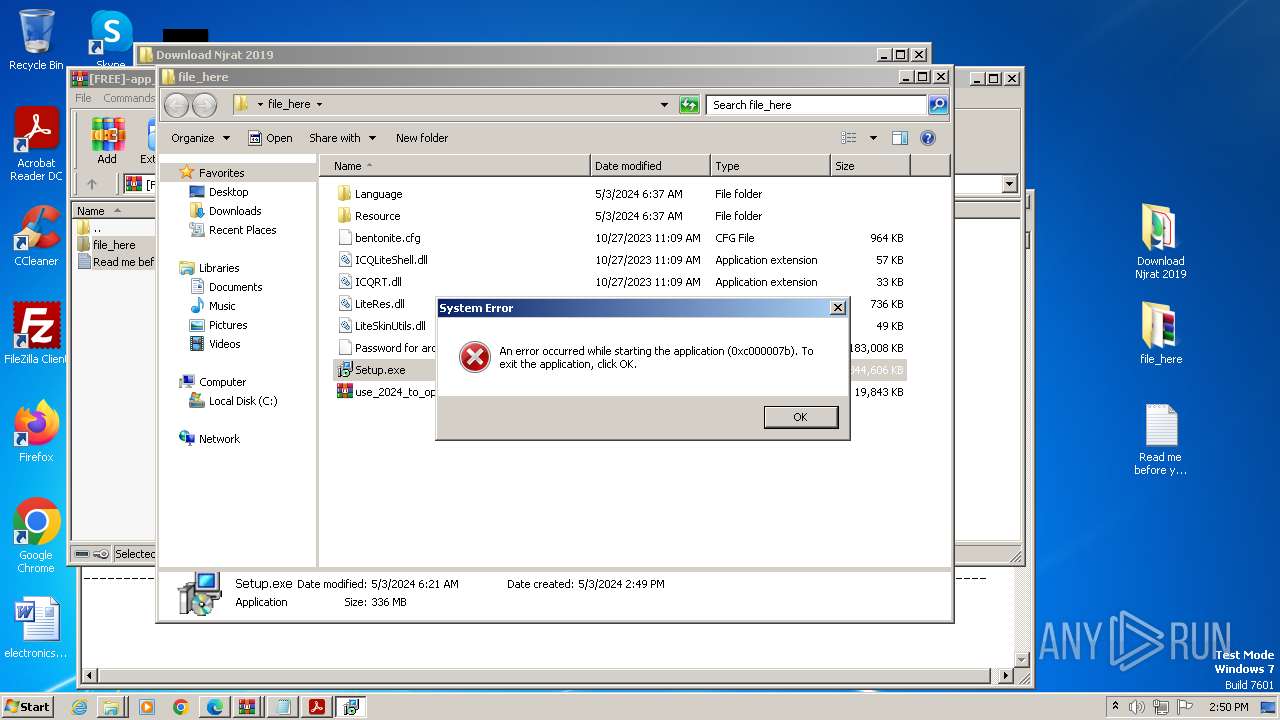
| File name: | Download Njrat 2019.rar |
| Full analysis: | https://app.any.run/tasks/b1a93b14-f43f-424c-80c9-50893b727e7a |
| Verdict: | Malicious activity |
| Analysis date: | May 03, 2024, 13:48:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 27E6E7A0B78A51BD01B874721FEBB4DF |
| SHA1: | 612821245420424E3DE9DE77547CE8FC792129EC |
| SHA256: | DB5A24F9ECD4E4413BFD3E48A1B519A49398D962E25535826779E2B067C455CB |
| SSDEEP: | 768:esaFZH0EuneO92dVKuyqZ7RP91R6ltzRmzNFsPZE3qwj:esajH/uljsrFyHzwz7sxs |
MALICIOUS
Actions looks like stealing of personal data
- Sеtup.exe (PID: 600)
SUSPICIOUS
Creates file in the systems drive root
- AcroRd32.exe (PID: 1184)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 3820)
Reads security settings of Internet Explorer
- Sеtup.exe (PID: 600)
Reads browser cookies
- Sеtup.exe (PID: 600)
Starts CMD.EXE for commands execution
- Sеtup.exe (PID: 600)
Reads the Internet Settings
- Sеtup.exe (PID: 600)
Executable content was dropped or overwritten
- expand.exe (PID: 1980)
The process executes via Task Scheduler
- Davonevur.exe (PID: 1468)
Searches for installed software
- Sеtup.exe (PID: 600)
INFO
Manual execution by a user
- AcroRd32.exe (PID: 2044)
- notepad.exe (PID: 1580)
- wmpnscfg.exe (PID: 2908)
- WinRAR.exe (PID: 3820)
- Sеtup.exe (PID: 600)
Application launched itself
- AcroRd32.exe (PID: 2044)
- msedge.exe (PID: 1652)
- RdrCEF.exe (PID: 1928)
Reads Microsoft Office registry keys
- AcroRd32.exe (PID: 1184)
Reads the computer name
- wmpnscfg.exe (PID: 2908)
- Sеtup.exe (PID: 600)
Checks supported languages
- wmpnscfg.exe (PID: 2908)
- Sеtup.exe (PID: 600)
- Davonevur.exe (PID: 1468)
Drops the executable file immediately after the start
- RdrCEF.exe (PID: 1928)
- WinRAR.exe (PID: 3820)
- expand.exe (PID: 1980)
The process uses the downloaded file
- msedge.exe (PID: 1044)
- WinRAR.exe (PID: 2484)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3820)
Reads CPU info
- Sеtup.exe (PID: 600)
Creates files or folders in the user directory
- Sеtup.exe (PID: 600)
- expand.exe (PID: 1980)
Reads mouse settings
- Davonevur.exe (PID: 1468)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
85
Monitored processes
44
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 580 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1240 --field-trial-handle=1204,i,1679408398775699420,11446288113067820106,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 600 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1172,3872827672467000618,11801581776725503836,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=15721198280771001302 --mojo-platform-channel-handle=1252 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 600 | "C:\Users\admin\Desktop\filе_hеrе\Sеtup.exe" | C:\Users\admin\Desktop\filе_hеrе\Sеtup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 664 | "C:\Windows\system32\cmd.exe" /c expand.exe "C:\Users\admin\AppData\Roaming\ServiceData\c2Gt4H.tmp" -F:* "C:\Users\admin\AppData\Roaming\ServiceData" | C:\Windows\System32\cmd.exe | — | Sеtup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1044 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1192 --field-trial-handle=1204,i,1679408398775699420,11446288113067820106,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1184 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\Desktop\Download Njrat 2019\DOWNLOAD NOW.pdf" | C:\program files\Adobe\acrobat reader dc\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x6a09f598,0x6a09f5a8,0x6a09f5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1468 | C:\Users\admin\AppData\Roaming\ServiceData\Davonevur.exe "C:\Users\admin\AppData\Roaming\ServiceData\Davonevur.jpg" | C:\Users\admin\AppData\Roaming\ServiceData\Davonevur.exe | — | taskeng.exe | |||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Version: 3, 3, 16, 1 Modules
| |||||||||||||||
| 1580 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Download Njrat 2019\READ ME.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1640 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1412 --field-trial-handle=1204,i,1679408398775699420,11446288113067820106,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
36 347
Read events
36 148
Write events
175
Delete events
24
Modification events
| (PID) Process: | (4012) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4012) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4012) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4012) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (4012) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (4012) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (4012) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Download Njrat 2019.rar | |||
| (PID) Process: | (4012) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4012) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4012) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
12
Suspicious files
139
Text files
145
Unknown types
109
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1652 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1065a1.TMP | — | |
MD5:— | SHA256:— | |||
| 1652 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1652 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:A6EBC0D32A7B9304824D19DB63B4E37A | SHA256:E991057C2B1718A151C5FD06E1C153F57130D195454A1F94C8C4C20971697093 | |||
| 4012 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4012.41511\Download Njrat 2019\DOWNLOAD from here (MAIN LINK).url | binary | |
MD5:486C68CD706226B11186D5DB1E706B74 | SHA256:D441CC8A56AC3A1A9EAA96DBEF1CD87E886AA29C1E1C4BC925D81DFD0C2EB0C6 | |||
| 4012 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4012.41511\Download Njrat 2019\Download Link (ALTERNATIVE).url | binary | |
MD5:2EC0232ABB29E702844DBB4FA053DE0F | SHA256:D0AAE45E343EFAA35FBD083D91170BF90113F235A60B8A0FC8C85927254A80F5 | |||
| 1652 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10660f.TMP | — | |
MD5:— | SHA256:— | |||
| 1652 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgeCoupons\coupons_data.db\LOG.old | text | |
MD5:2B5B565981E1565368EC9935843BD794 | SHA256:E98D615C43993262B2C3058F9E445BA09A496ED4CEE663371CABD0600CBBF122 | |||
| 1652 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1652 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF106709.TMP | — | |
MD5:— | SHA256:— | |||
| 1652 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
44
DNS requests
41
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2044 | AcroRd32.exe | GET | 304 | 2.16.100.168:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a345dff9a92f9db9 | unknown | — | — | unknown |
2044 | AcroRd32.exe | GET | 304 | 2.16.100.168:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?566ae8b88370a43c | unknown | — | — | unknown |
2044 | AcroRd32.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | unknown |
1088 | svchost.exe | GET | 304 | 173.222.108.147:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d05c9e21a8d1536d | unknown | — | — | unknown |
600 | Sеtup.exe | POST | 200 | 193.222.62.75:80 | http://gvtwelve12pt.top/upload.php | unknown | — | — | unknown |
600 | Sеtup.exe | POST | 200 | 193.222.62.75:80 | http://gvtwelve12pt.top/upload.php | unknown | — | — | unknown |
600 | Sеtup.exe | POST | 200 | 193.222.62.75:80 | http://gvtwelve12pt.top/upload.php | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1640 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1640 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1652 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
1640 | msedge.exe | 172.67.152.47:443 | shanrdrctor.com | CLOUDFLARENET | US | unknown |
1640 | msedge.exe | 188.114.97.3:443 | link.reditraff.online | CLOUDFLARENET | NL | unknown |
1640 | msedge.exe | 185.149.120.173:443 | ektadesai.com | Ddos-guard Ltd | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
shanrdrctor.com |
| unknown |
edge.microsoft.com |
| whitelisted |
link.reditraff.online |
| unknown |
ektadesai.com |
| unknown |
www.bing.com |
| whitelisted |
msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
cdn.jsdelivr.net |
| whitelisted |
code.jquery.com |
| whitelisted |
mtmoweb.website |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1640 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
1640 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
1640 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
1088 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
600 | Sеtup.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
7 ETPRO signatures available at the full report