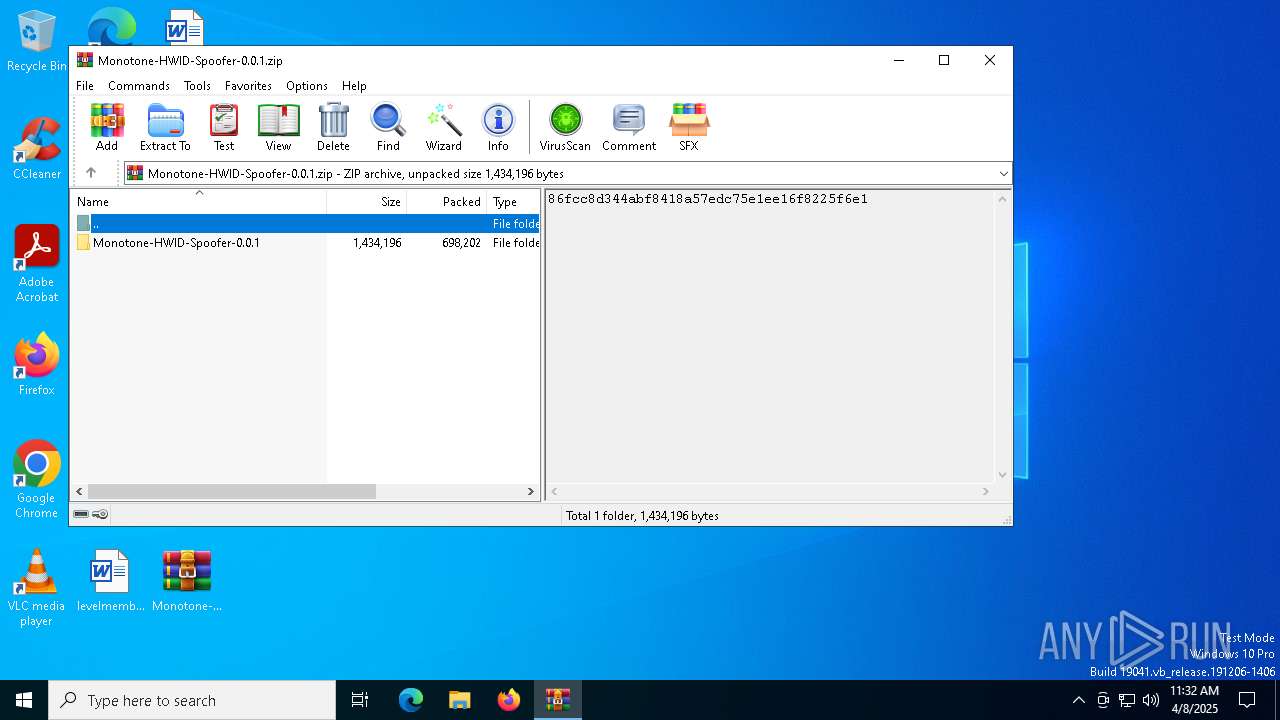
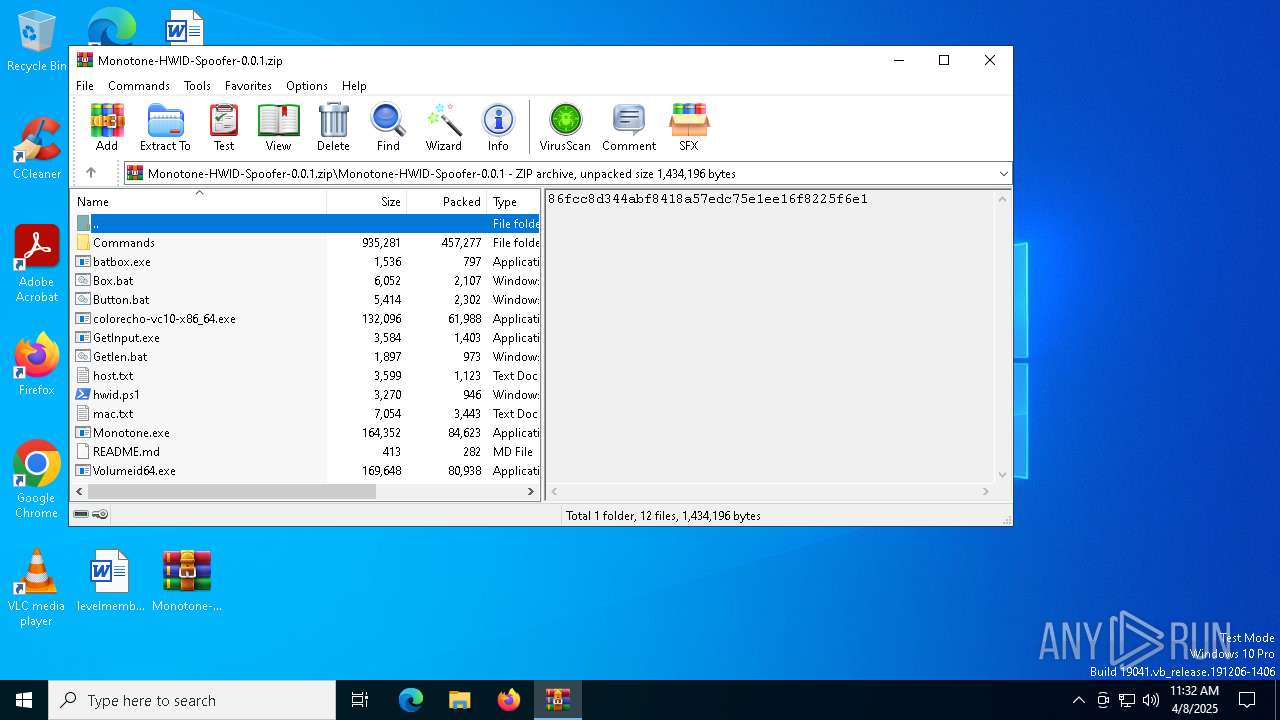
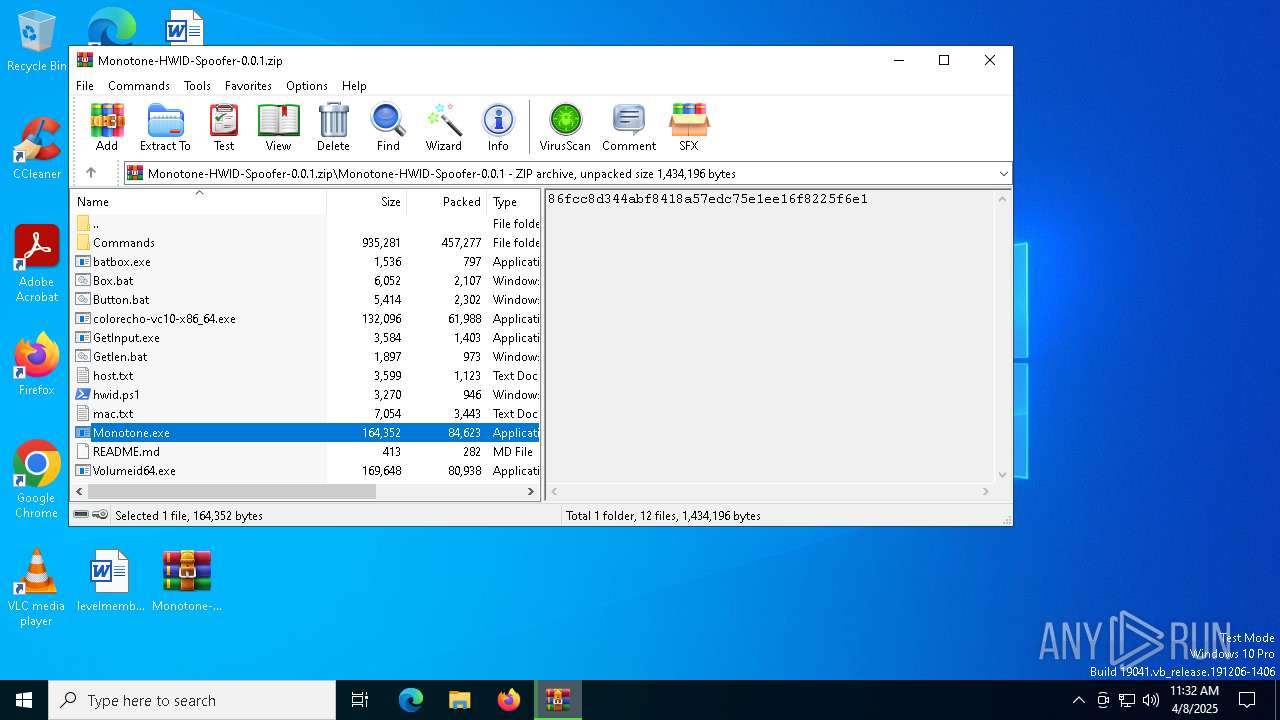
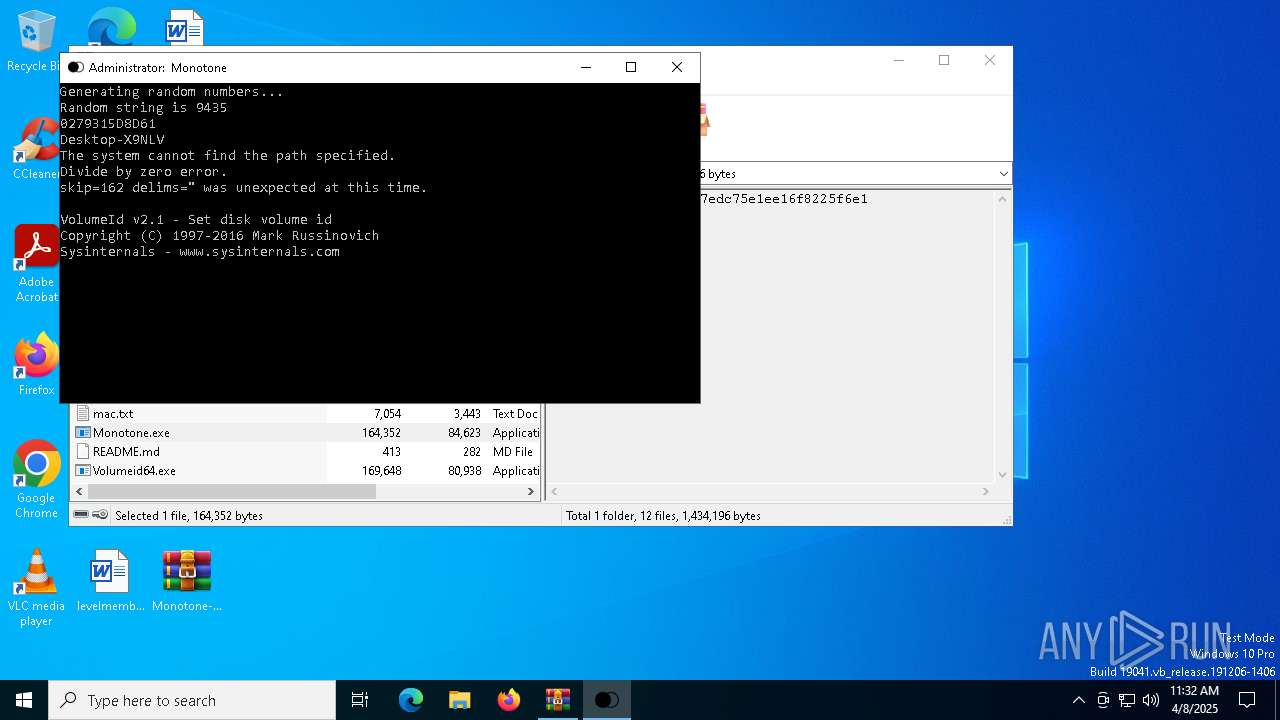
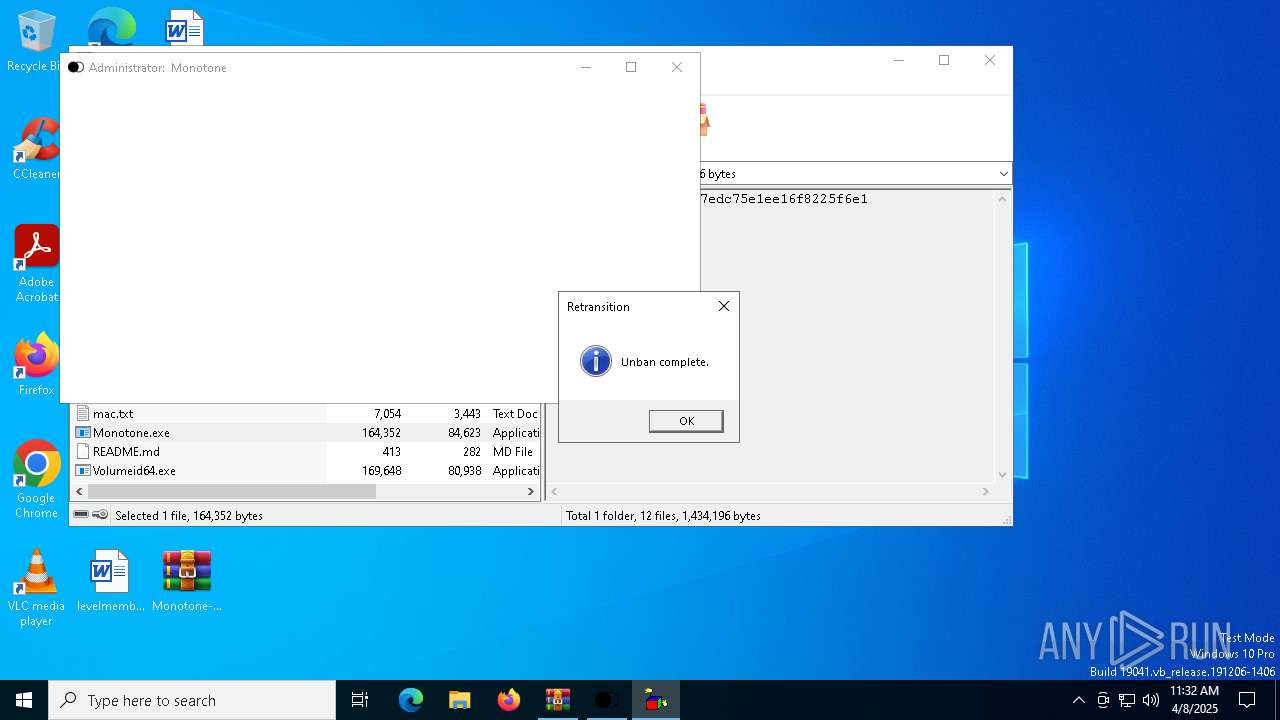
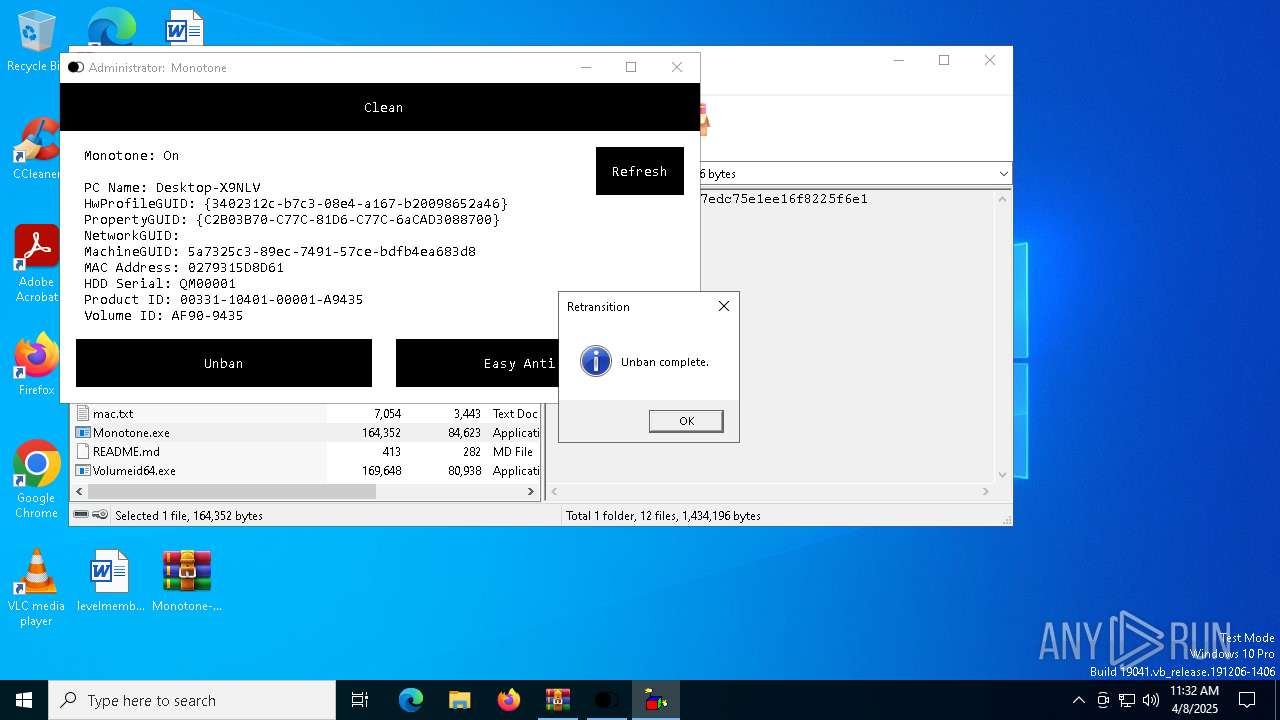
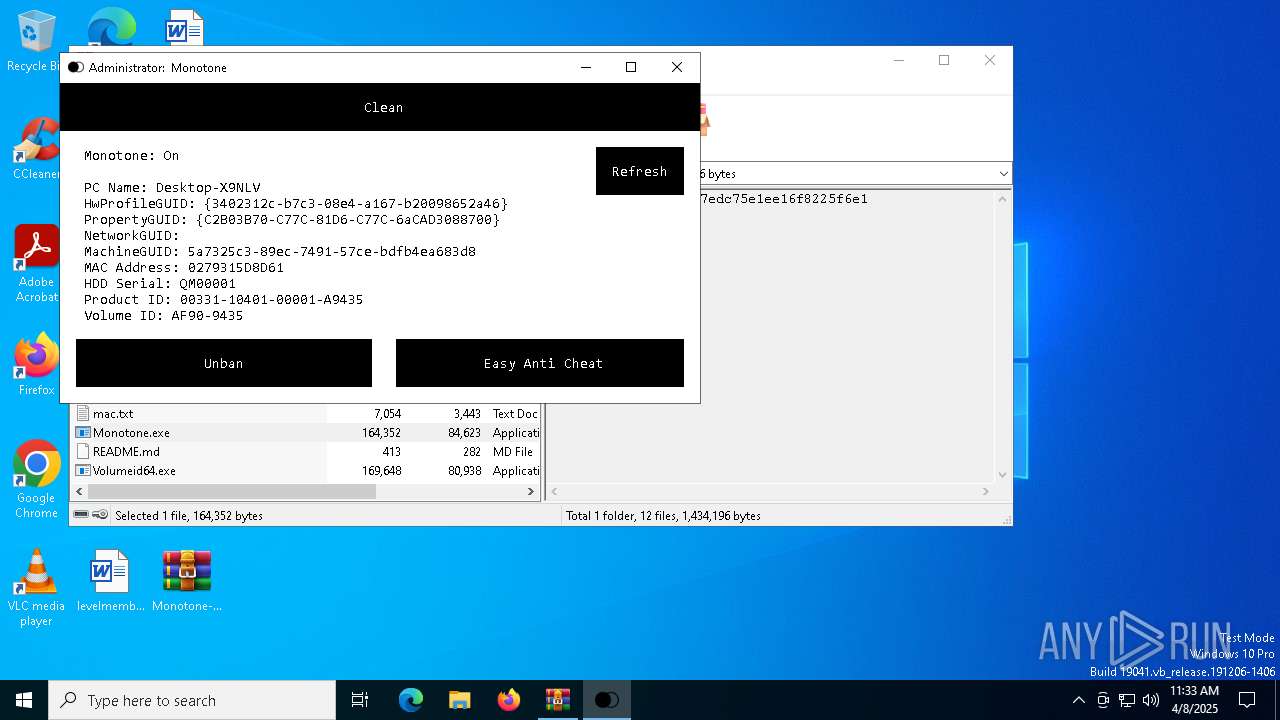
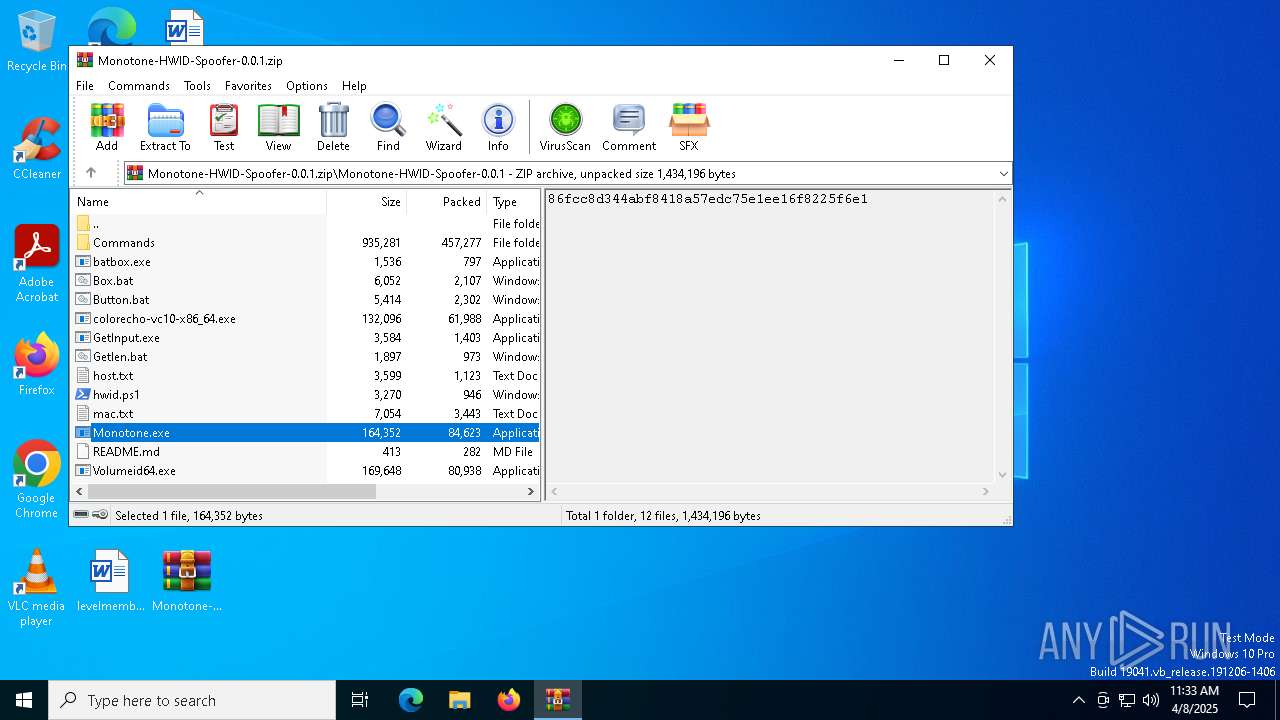
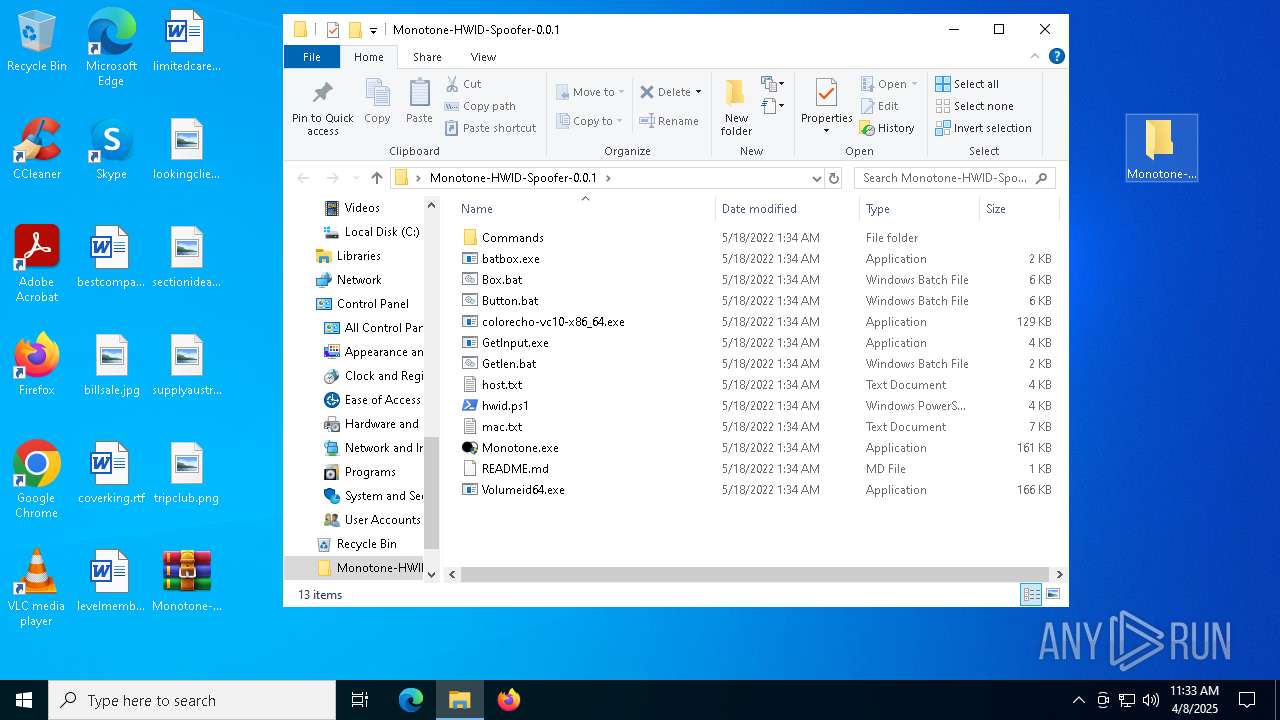
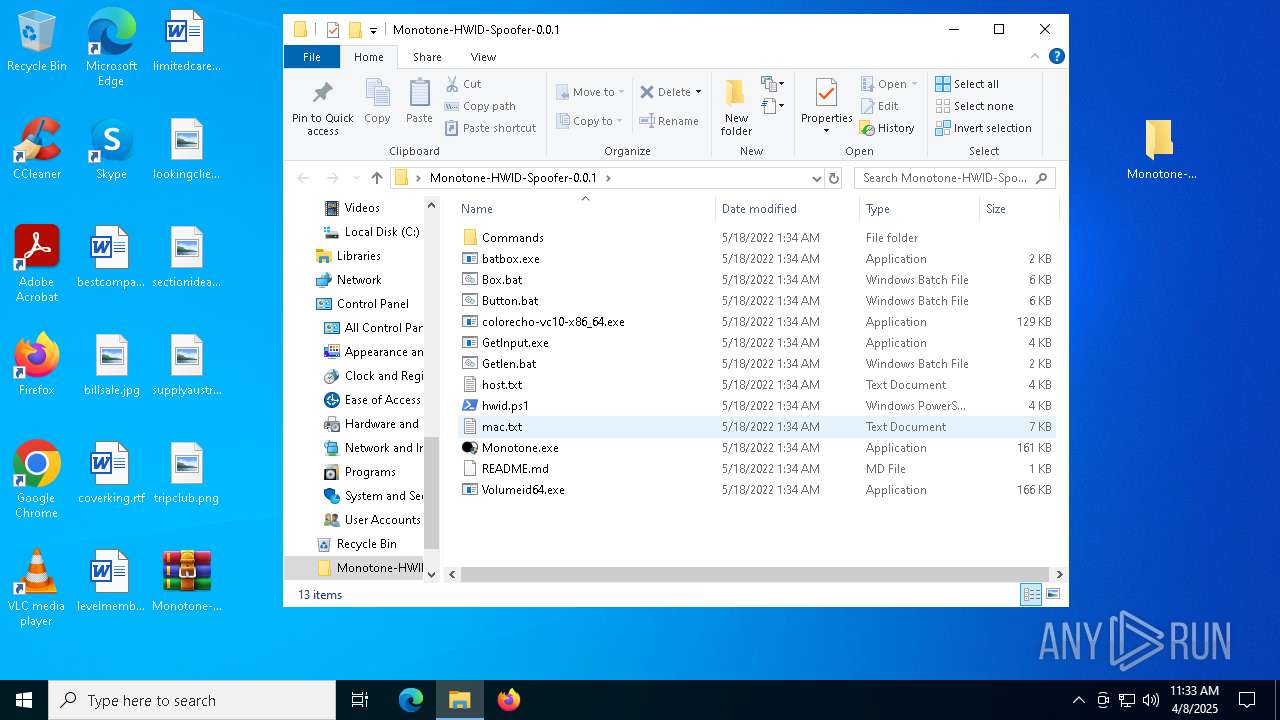
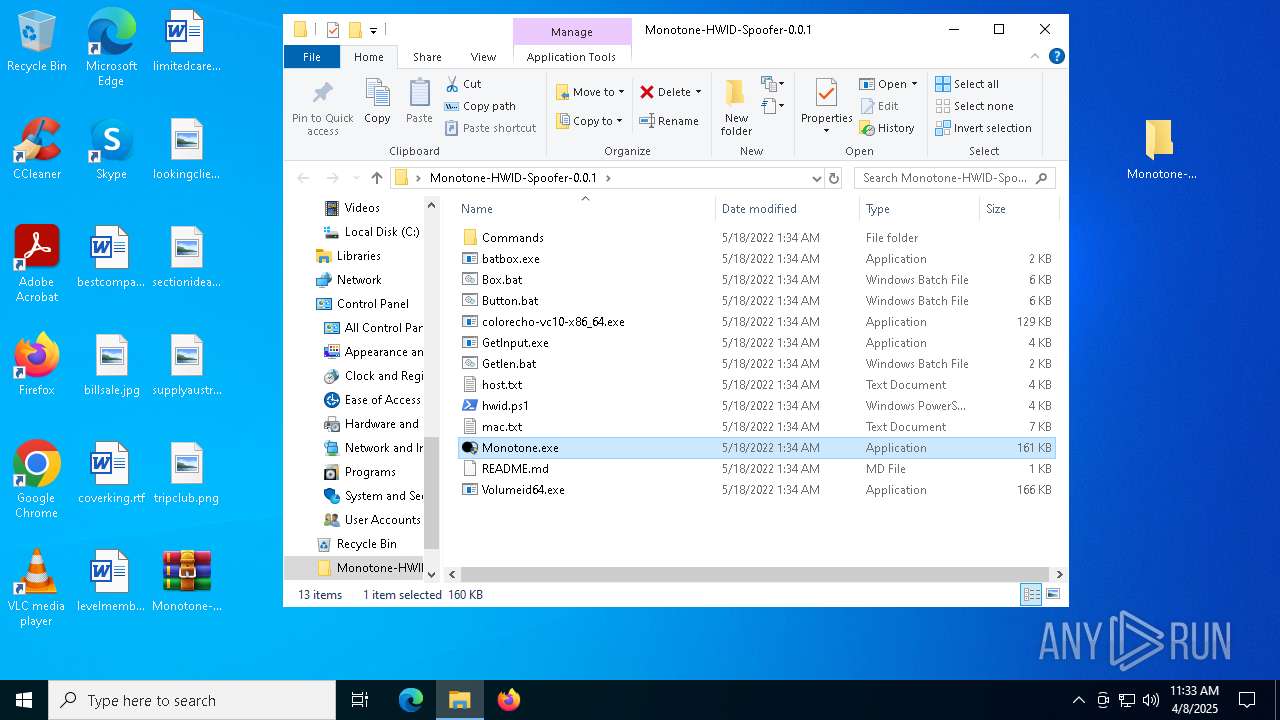
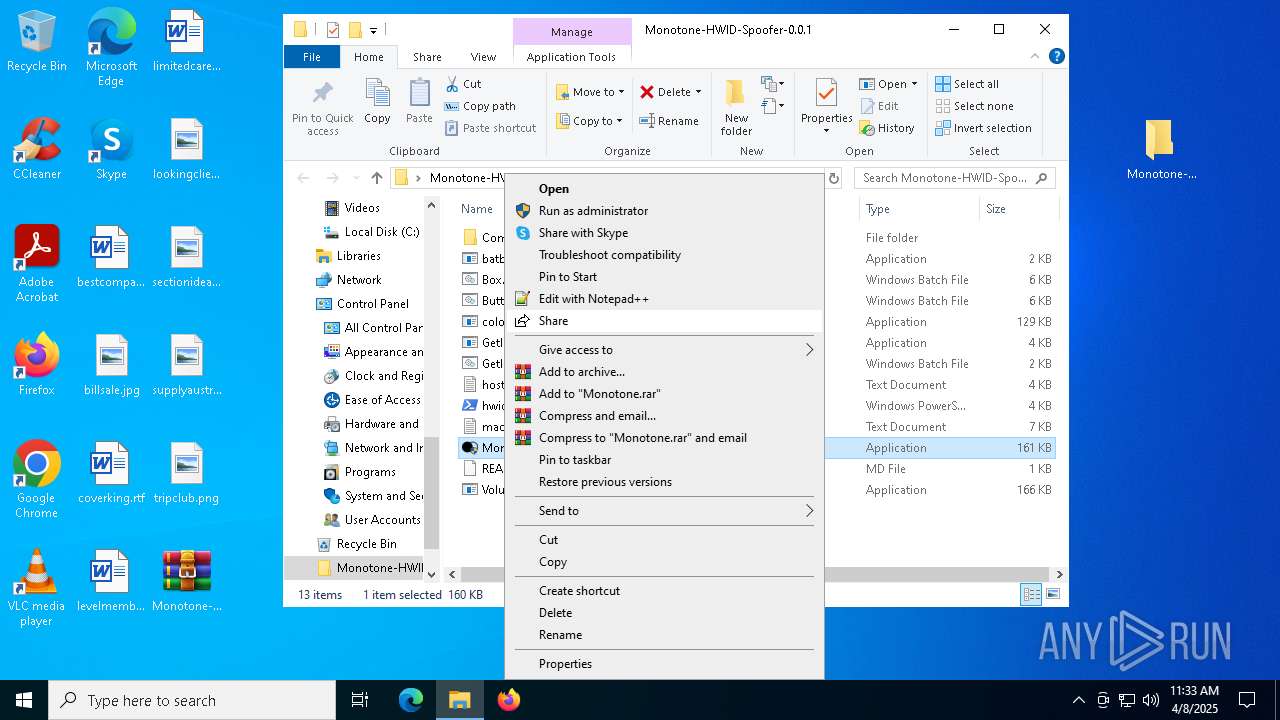
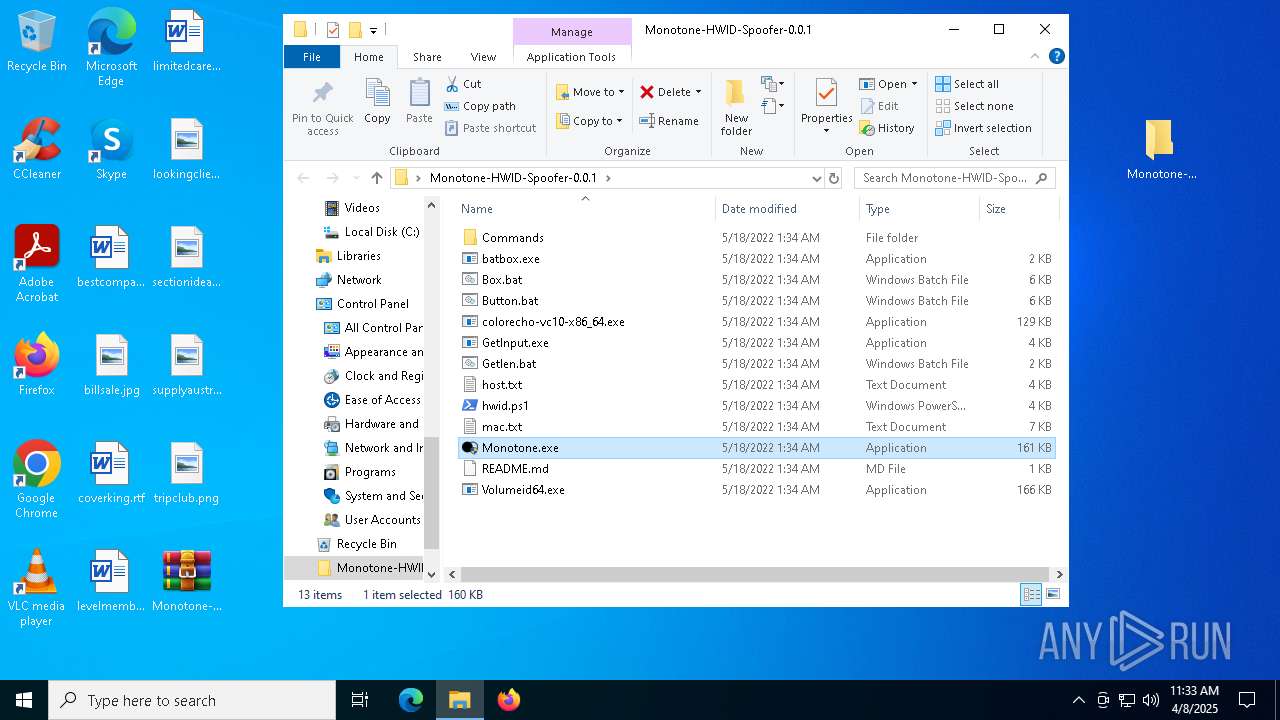
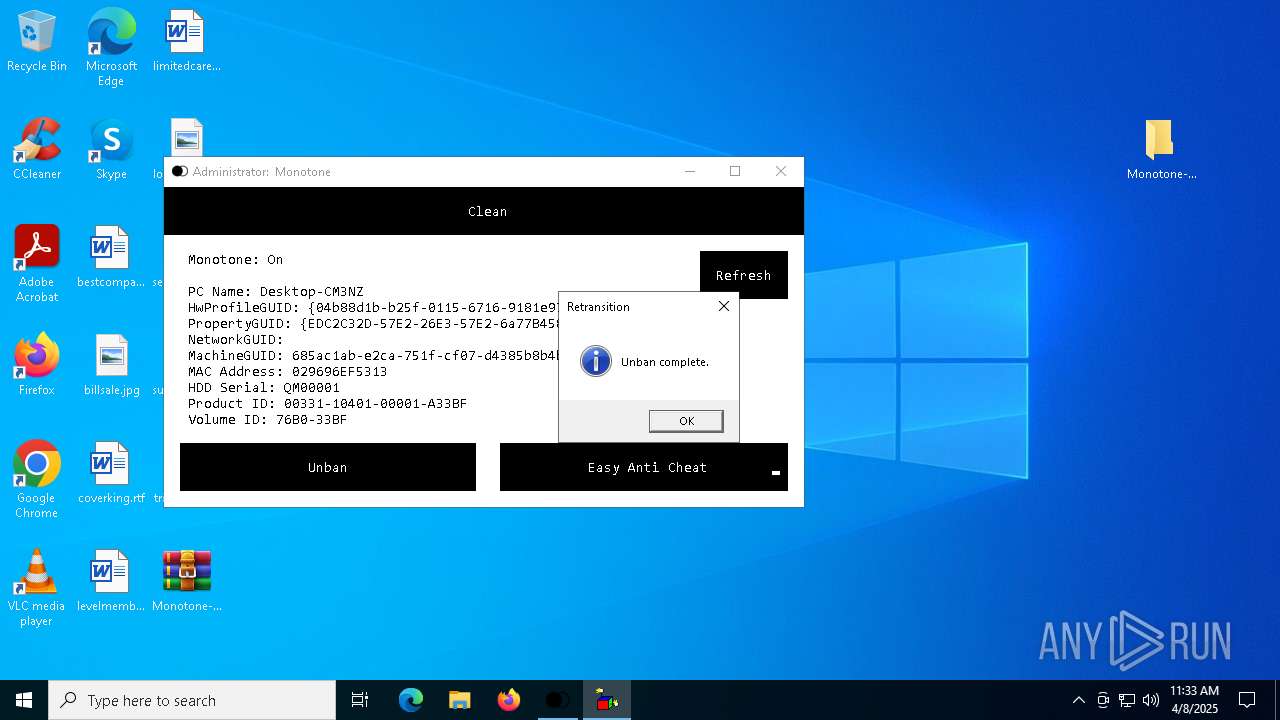
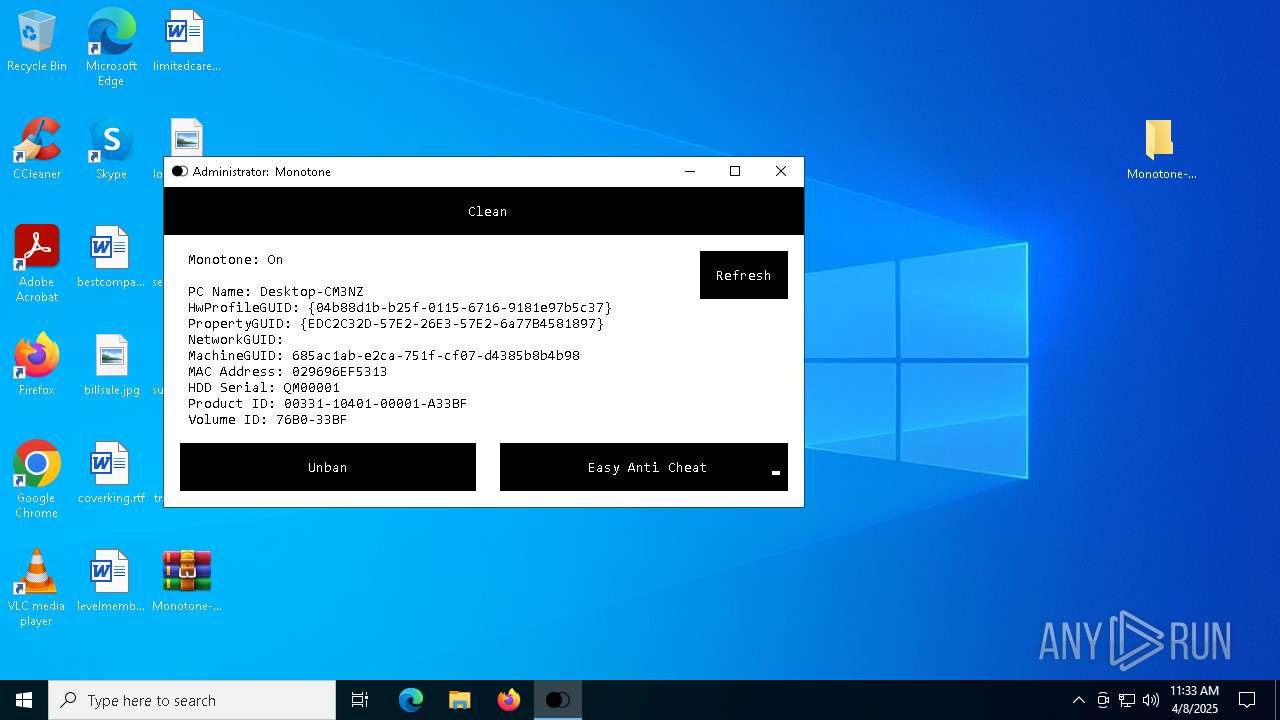
| File name: | Monotone-HWID-Spoofer-0.0.1.zip |
| Full analysis: | https://app.any.run/tasks/78270553-92e1-4a13-aeb6-aeda3b980cec |
| Verdict: | Malicious activity |
| Analysis date: | April 08, 2025, 11:32:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 806CFDD8AEDC01685605268BB1778679 |
| SHA1: | 7F7818B723FCF707D2B7BB478243E2DD10D5BE56 |
| SHA256: | DB4E12073C2200C86E5F1DDA3ADF7633357906E2BB97853DAC9876680CD44D6C |
| SSDEEP: | 12288:sKSmTFPvU4UE33IqxmRjJiulBy0WO/UP0asQJ5kJOt5iK+0ECJAdKLpB4JtY:sbmpXU4rHIqxSiuW4Uq8+0tgPBCJ4Y79 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7084)
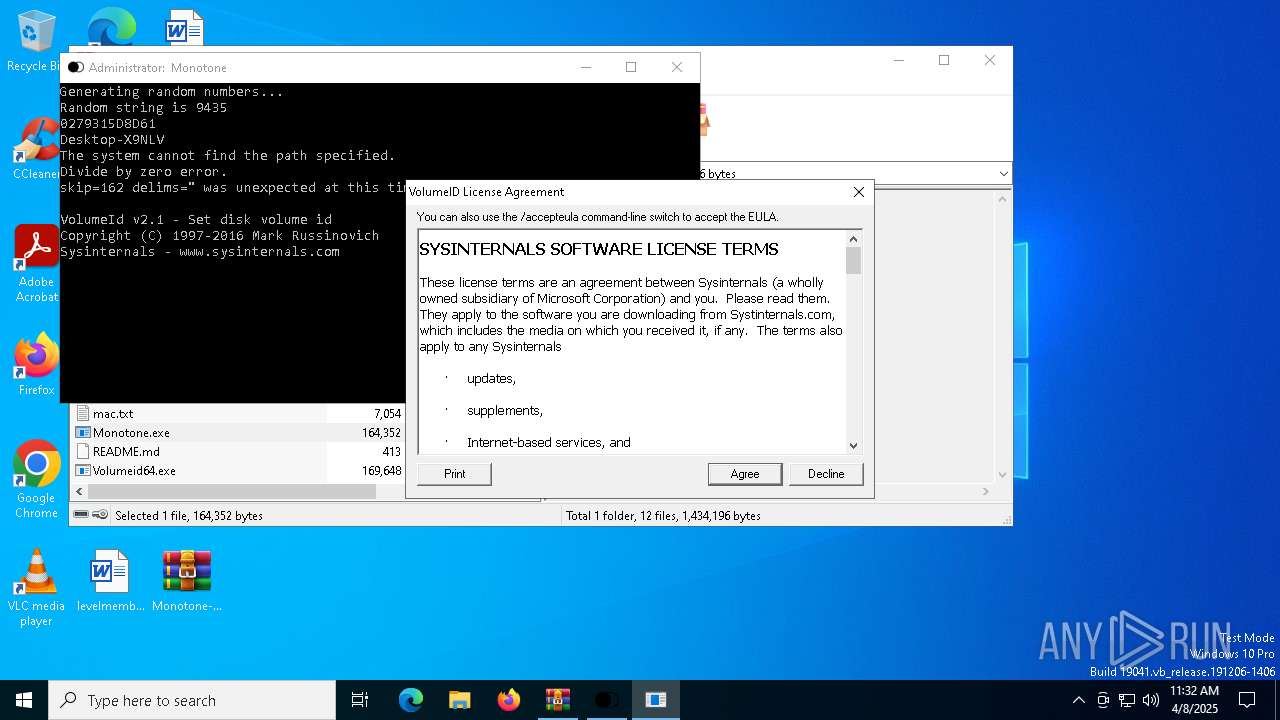
Executing a file with an untrusted certificate
- Volumeid64.exe (PID: 3008)
- Volumeid64.exe (PID: 1164)
Changes powershell execution policy (RemoteSigned)
- cmd.exe (PID: 5512)
- cmd.exe (PID: 5360)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7084)
- Block.exe (PID: 7036)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 7084)
Executing commands from a ".bat" file
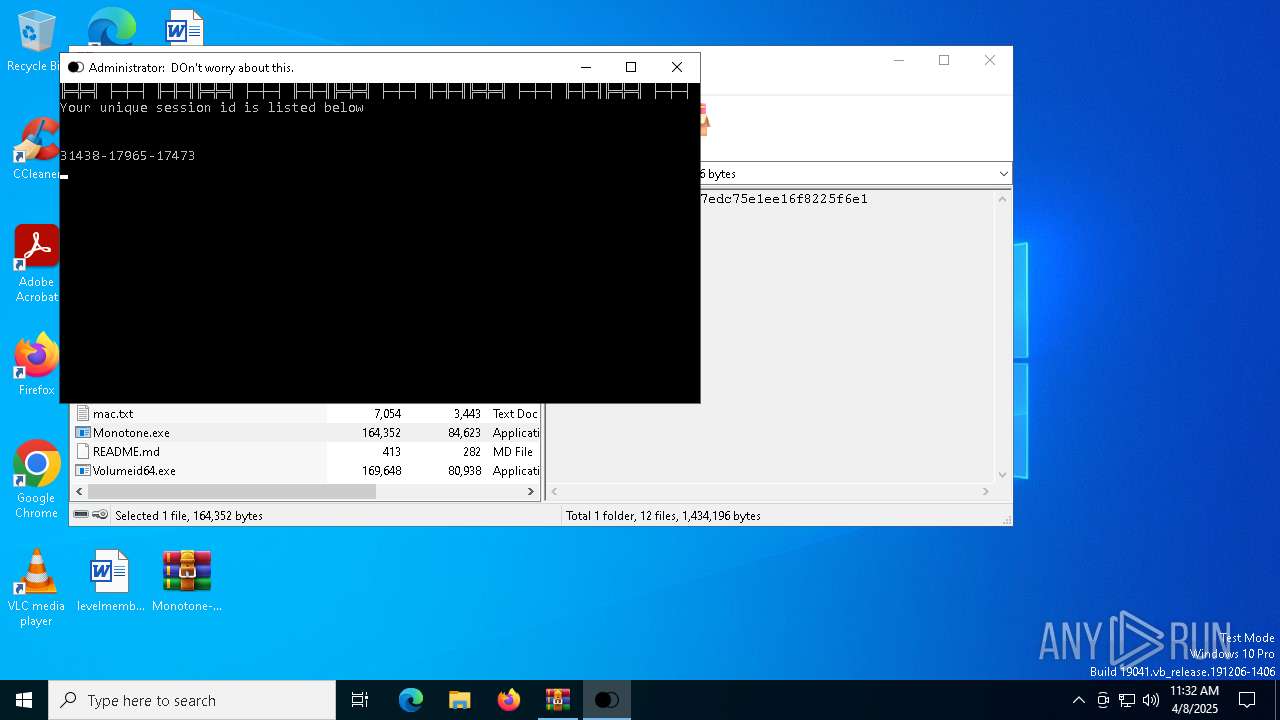
- Monotone.exe (PID: 1764)
- Block.exe (PID: 7036)
- Monotone.exe (PID: 4068)
- Block.exe (PID: 3156)
Starts CMD.EXE for commands execution
- Monotone.exe (PID: 1764)
- cmd.exe (PID: 5512)
- cmd.exe (PID: 5756)
- cmd.exe (PID: 4996)
- cmd.exe (PID: 7020)
- Block.exe (PID: 7036)
- Monotone.exe (PID: 4068)
- cmd.exe (PID: 5360)
- cmd.exe (PID: 6940)
- cmd.exe (PID: 2040)
- cmd.exe (PID: 1600)
- Block.exe (PID: 3156)
The executable file from the user directory is run by the CMD process
- colorecho-vc10-x86_64.exe (PID: 4452)
- batbox.exe (PID: 5800)
- GetInput.exe (PID: 1056)
- batbox.exe (PID: 812)
- batbox.exe (PID: 6108)
- batbox.exe (PID: 2656)
- batbox.exe (PID: 1020)
- batbox.exe (PID: 6540)
- batbox.exe (PID: 5008)
- Volumeid64.exe (PID: 3008)
- GetInput.exe (PID: 6372)
- Block.exe (PID: 7036)
- batbox.exe (PID: 5408)
- batbox.exe (PID: 3180)
- batbox.exe (PID: 3008)
- batbox.exe (PID: 4040)
- batbox.exe (PID: 6872)
- GetInput.exe (PID: 5800)
Get information on the list of running processes
- cmd.exe (PID: 5512)
- cmd.exe (PID: 6436)
- cmd.exe (PID: 5360)
- cmd.exe (PID: 684)
Uses WMIC.EXE to obtain physical disk drive information
- cmd.exe (PID: 4488)
- cmd.exe (PID: 6080)
- cmd.exe (PID: 5124)
- cmd.exe (PID: 6876)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5720)
- cmd.exe (PID: 5512)
- cmd.exe (PID: 2564)
- cmd.exe (PID: 2432)
- cmd.exe (PID: 5360)
- cmd.exe (PID: 2656)
Application launched itself
- cmd.exe (PID: 5512)
- cmd.exe (PID: 7020)
- cmd.exe (PID: 4996)
- cmd.exe (PID: 5756)
- cmd.exe (PID: 5360)
- cmd.exe (PID: 6940)
- cmd.exe (PID: 2040)
- cmd.exe (PID: 1600)
The process executes Powershell scripts
- cmd.exe (PID: 5512)
- cmd.exe (PID: 5360)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5512)
- cmd.exe (PID: 5360)
The process hides Powershell's copyright startup banner
- cmd.exe (PID: 5512)
- cmd.exe (PID: 5360)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 5512)
- cmd.exe (PID: 5360)
Reads the date of Windows installation
- Block.exe (PID: 7036)
- Block.exe (PID: 3156)
The process executes VB scripts
- cmd.exe (PID: 5512)
- cmd.exe (PID: 5360)
Converts a string into array of characters (POWERSHELL)
- powershell.exe (PID: 4244)
- powershell.exe (PID: 5008)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7084)
Checks supported languages
- Monotone.exe (PID: 1764)
- mode.com (PID: 4988)
- batbox.exe (PID: 5800)
- batbox.exe (PID: 812)
- colorecho-vc10-x86_64.exe (PID: 4452)
- mode.com (PID: 1348)
- batbox.exe (PID: 6540)
- batbox.exe (PID: 2656)
- batbox.exe (PID: 1020)
- batbox.exe (PID: 6108)
- batbox.exe (PID: 5008)
- Volumeid64.exe (PID: 3008)
- Block.exe (PID: 7036)
- mode.com (PID: 6512)
- batbox.exe (PID: 4040)
- batbox.exe (PID: 3180)
- batbox.exe (PID: 3008)
- batbox.exe (PID: 5408)
- batbox.exe (PID: 6872)
- Monotone.exe (PID: 4068)
- mode.com (PID: 6512)
- colorecho-vc10-x86_64.exe (PID: 6136)
- batbox.exe (PID: 6372)
- batbox.exe (PID: 6668)
- batbox.exe (PID: 2064)
- batbox.exe (PID: 208)
- batbox.exe (PID: 300)
- mode.com (PID: 5164)
- Volumeid64.exe (PID: 1164)
- batbox.exe (PID: 4996)
- batbox.exe (PID: 2152)
- Block.exe (PID: 3156)
- batbox.exe (PID: 4424)
- batbox.exe (PID: 6456)
- batbox.exe (PID: 5576)
- mode.com (PID: 5232)
- batbox.exe (PID: 4164)
The sample compiled with english language support
- WinRAR.exe (PID: 7084)
Create files in a temporary directory
- Monotone.exe (PID: 1764)
- Block.exe (PID: 7036)
- Monotone.exe (PID: 4068)
- Block.exe (PID: 3156)
Starts MODE.COM to configure console settings
- mode.com (PID: 4988)
- mode.com (PID: 1348)
- mode.com (PID: 6512)
- mode.com (PID: 6512)
- mode.com (PID: 5164)
- mode.com (PID: 5232)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 5332)
- WMIC.exe (PID: 5360)
- WMIC.exe (PID: 2984)
- WMIC.exe (PID: 5156)
Reads Windows Product ID
- reg.exe (PID: 2432)
- reg.exe (PID: 3888)
- reg.exe (PID: 5728)
- reg.exe (PID: 2772)
- reg.exe (PID: 1012)
- reg.exe (PID: 7000)
Gets data length (POWERSHELL)
- powershell.exe (PID: 4244)
- powershell.exe (PID: 5008)
Reads Environment values
- Volumeid64.exe (PID: 3008)
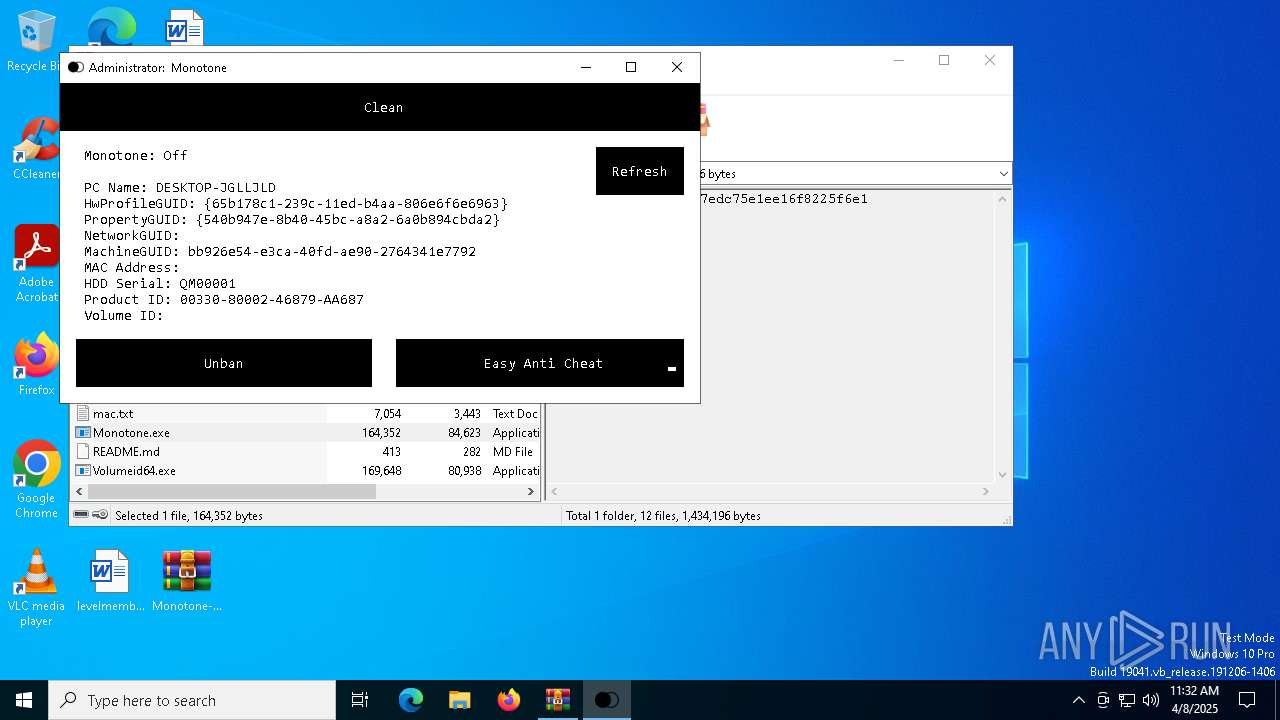
Reads the computer name
- Volumeid64.exe (PID: 3008)
- Block.exe (PID: 7036)
- Block.exe (PID: 3156)
Disables trace logs
- netsh.exe (PID: 2420)
- netsh.exe (PID: 5156)
- netsh.exe (PID: 2772)
Process checks computer location settings
- Block.exe (PID: 7036)
- Block.exe (PID: 3156)
Manual execution by a user
- Monotone.exe (PID: 4068)
Reads product name
- Volumeid64.exe (PID: 3008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2022:05:17 18:34:38 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Monotone-HWID-Spoofer-0.0.1/ |
Total processes
340
Monitored processes
212
Malicious processes
7
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | batbox /c 0x0f /g 2 18 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /g 2 17 /a 32 /d " " /a 32 /g 2 16 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /c 0x07 | C:\Users\admin\Desktop\Monotone-HWID-Spoofer-0.0.1\batbox.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 208 | REG ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion" /v DigitalProductId /t REG_BINARY /d A4000000000003030312D3836382D303030303030372D383535353700AA0000005831352D3333000000000000000C3AABF26E3BA18B8878E89D26E3000000000000396CC459BD030000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000057E26736 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | batbox /c 0x0f /g 0 2 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /g 0 1 /a 32 /d " " /a 32 /g 0 0 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /c 0x07 | C:\Users\admin\Desktop\Monotone-HWID-Spoofer-0.0.1\batbox.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 684 | C:\WINDOWS\system32\cmd.exe /S /D /c" type "mac.txt"" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | "C:\WINDOWS\system32\cmd.exe" /c "C:\Users\admin\AppData\Local\Temp\9140.tmp\9141.tmp\9142.bat C:\Users\admin\Desktop\Monotone-HWID-Spoofer-0.0.1\Commands\Hidden\Block.exe" | C:\Windows\System32\cmd.exe | — | Block.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | C:\WINDOWS\system32\cmd.exe /c reg.exe query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion" /v "ProductID" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | Batbox /g 23 16 /c 0xf0 /d " Enter " /c 0x07 | C:\Users\admin\AppData\Local\Temp\Rar$EXa7084.27065\Monotone-HWID-Spoofer-0.0.1\batbox.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 812 | reg.exe query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkCards\3" /v "ServiceName" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | tasklist /NH /FI "imagename eq Monotone.exe" | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
20 136
Read events
20 077
Write events
57
Delete events
2
Modification events
| (PID) Process: | (7084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Monotone-HWID-Spoofer-0.0.1.zip | |||
| (PID) Process: | (7084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
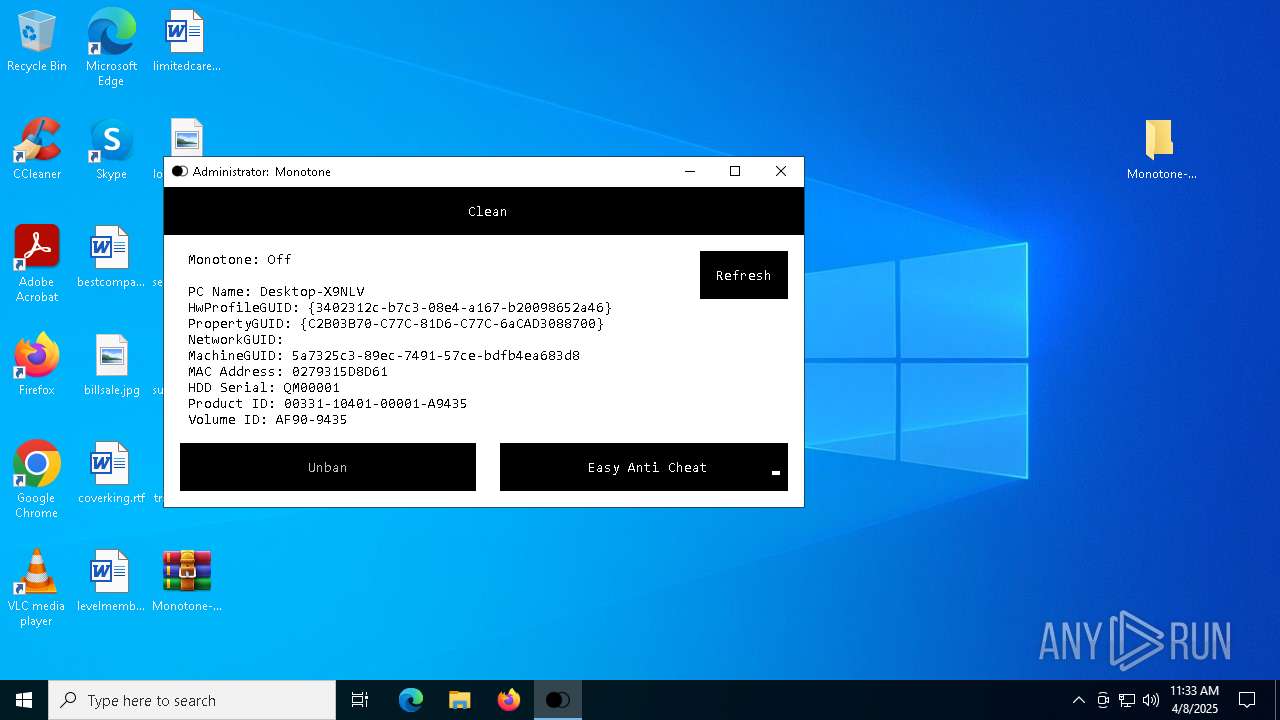
| (PID) Process: | (3008) Volumeid64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\VolumeID |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (4452) reg.exe | Key: | HKEY_CURRENT_USER\Monetone |
| Operation: | write | Name: | VolumeID |
Value: AF90-9435 | |||
Executable files
20
Suspicious files
1
Text files
28
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7084 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7084.27065\Monotone-HWID-Spoofer-0.0.1\Commands\Hidden\AlternateStreamView.cfg | text | |
MD5:D298348206017D0CB04217887A677334 | SHA256:2E44DAD813EFA86DDBD849A53962C5BDCACC9BCC2039DC09BCB2C25C770F3D8B | |||
| 7084 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7084.27065\Monotone-HWID-Spoofer-0.0.1\Getlen.bat | text | |
MD5:8C1812E76BA7BF09CB87384089A0AB7F | SHA256:83CE5342710A2F2E385A363402661E3426728DD6BCFE9D87E22F2FB858B07BDE | |||
| 3008 | Volumeid64.exe | \Device\HarddiskVolume2 | — | |
MD5:— | SHA256:— | |||
| 7084 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7084.27065\Monotone-HWID-Spoofer-0.0.1\Commands\Hidden\Adapters2.exe | executable | |
MD5:BB36D4578CE201DC932AB6BBC079875C | SHA256:4C831252AA6F193C4474BA74F352BEE7D00099DFAF5AC6E98AB1253E21999B4A | |||
| 7084 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7084.27065\Monotone-HWID-Spoofer-0.0.1\Box.bat | text | |
MD5:A95505942D3EBCF724F080B49D4E981F | SHA256:64556D24498BCD280CD7CC248A98ED22C4DB921495D825F141AF1547C8FDD275 | |||
| 7084 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7084.27065\Monotone-HWID-Spoofer-0.0.1\Commands\Hidden\Block.exe | executable | |
MD5:5782B8D469BBC9045EBD2316C2AEFBD5 | SHA256:DFD08E1D7A34BAE6836B3915B45B8637B85CDC998198C5BF148FBA5E96F15C21 | |||
| 7084 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7084.27065\Monotone-HWID-Spoofer-0.0.1\README.md | text | |
MD5:699D03E1E8ED798AEB721E8FD561682B | SHA256:4ABFD24B7422EE66D5849FDA386DFD1318DB4615F9126899A27FDB5A4FFA3D0D | |||
| 7084 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7084.27065\Monotone-HWID-Spoofer-0.0.1\Commands\Hidden\AlternateStreamView.exe | executable | |
MD5:CAEDE4F12AC17F3E0AD8E3C923FD510A | SHA256:669CE40107A2E05FC93DD37DF55C77EB155705B449B2E236423E8BB96B9985F0 | |||
| 7084 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7084.27065\Monotone-HWID-Spoofer-0.0.1\host.txt | text | |
MD5:CDDA0101630962EAEE1EF0305C2028C0 | SHA256:ECF34C7BC93D5B7F1EA5D8D17E488946EED415128658DA3BA2D02633C543234B | |||
| 7084 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7084.27065\Monotone-HWID-Spoofer-0.0.1\Commands\Hidden\process.bat | text | |
MD5:2D3F9B2D001ABD6E58AC6F0E7337C619 | SHA256:EF702CE2F8FB1BC71FB60E8B95CB83CEF4FA66AA96AFD7CA4FD67C96530B6E53 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
17
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5392 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5392 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.36:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5392 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5392 | SIHClient.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |