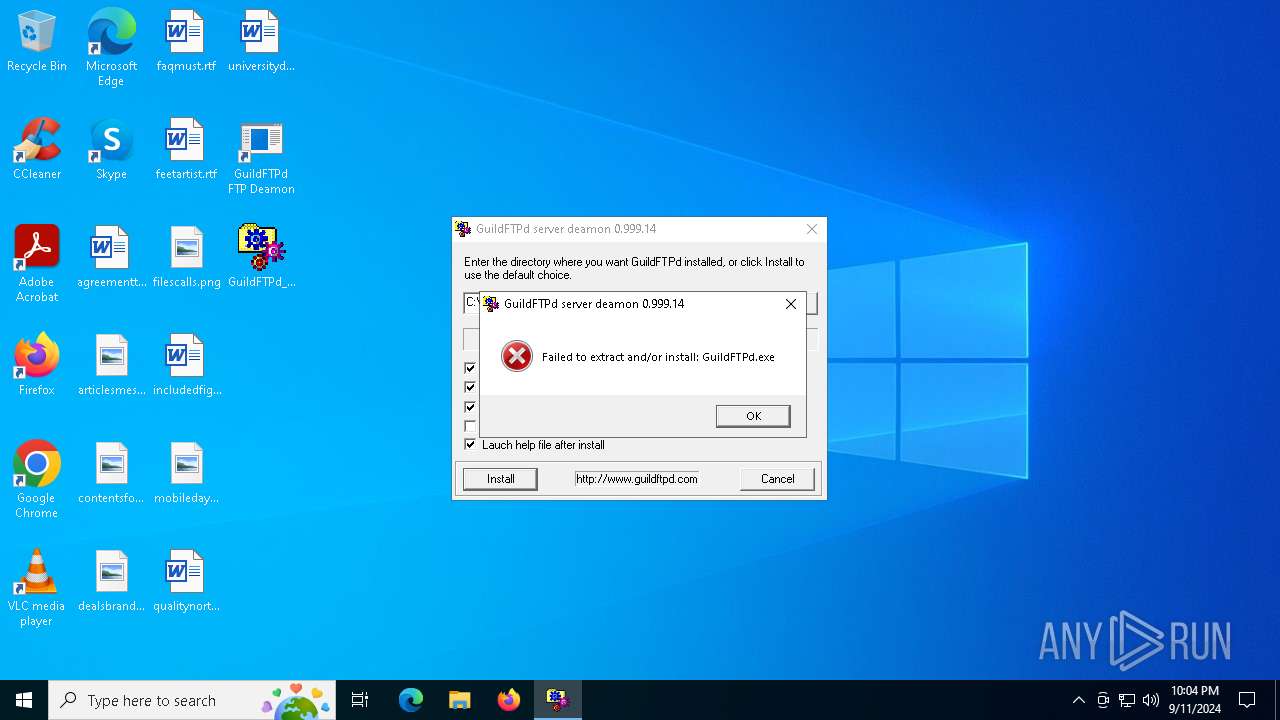
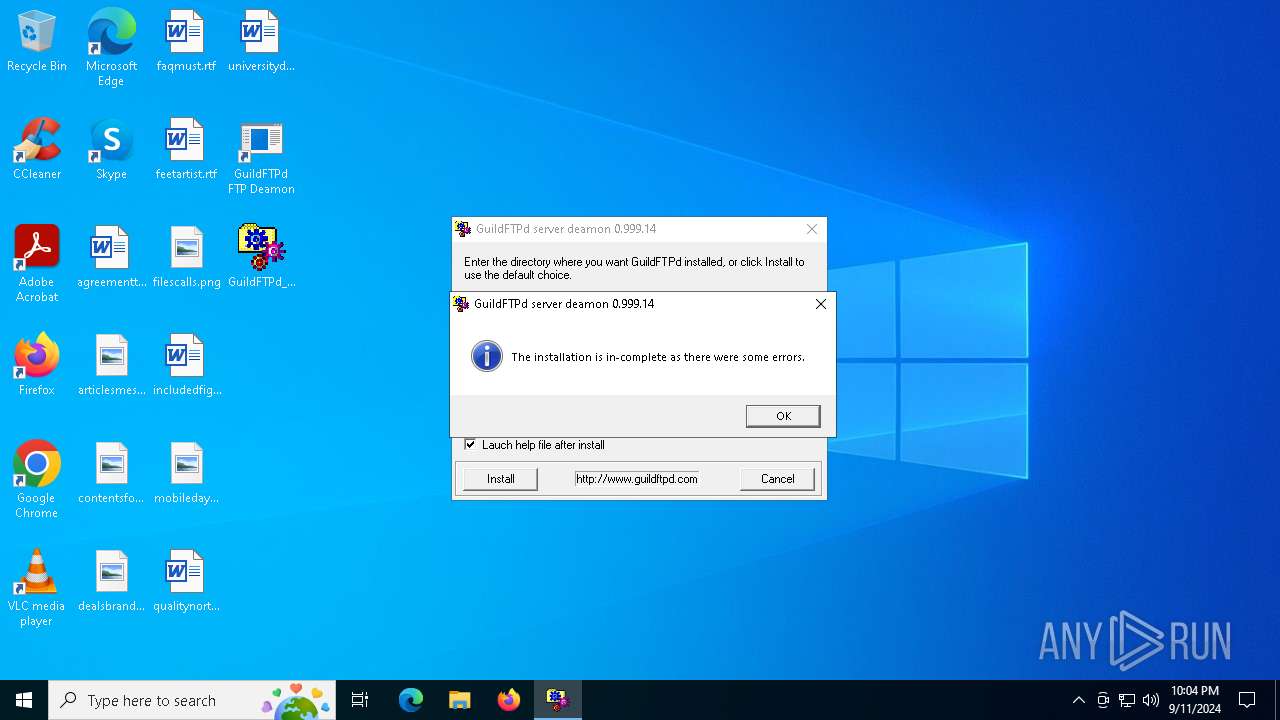
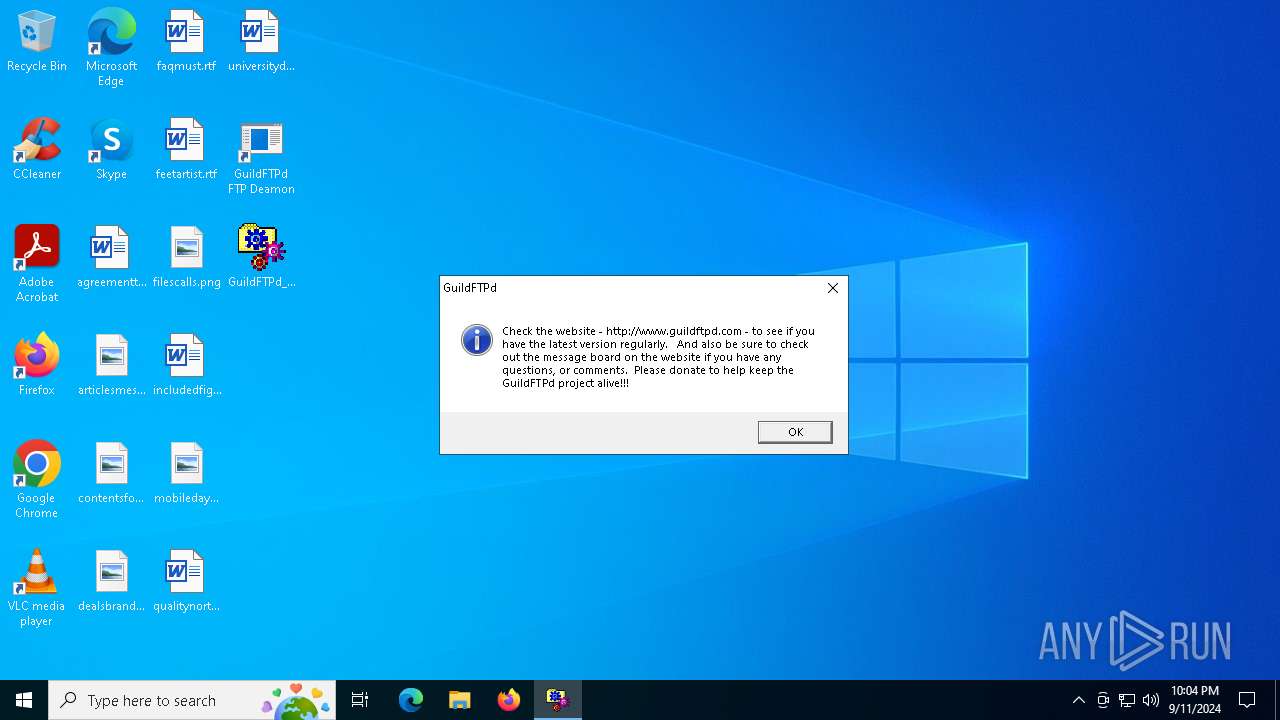
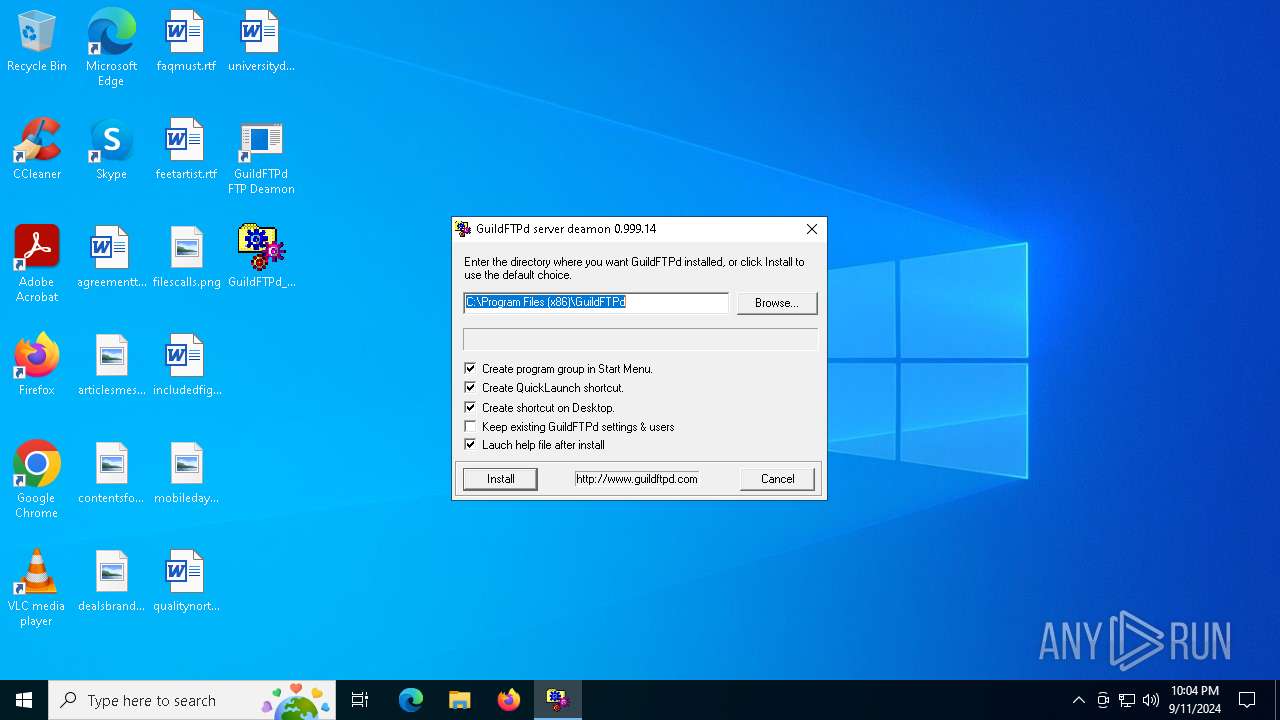
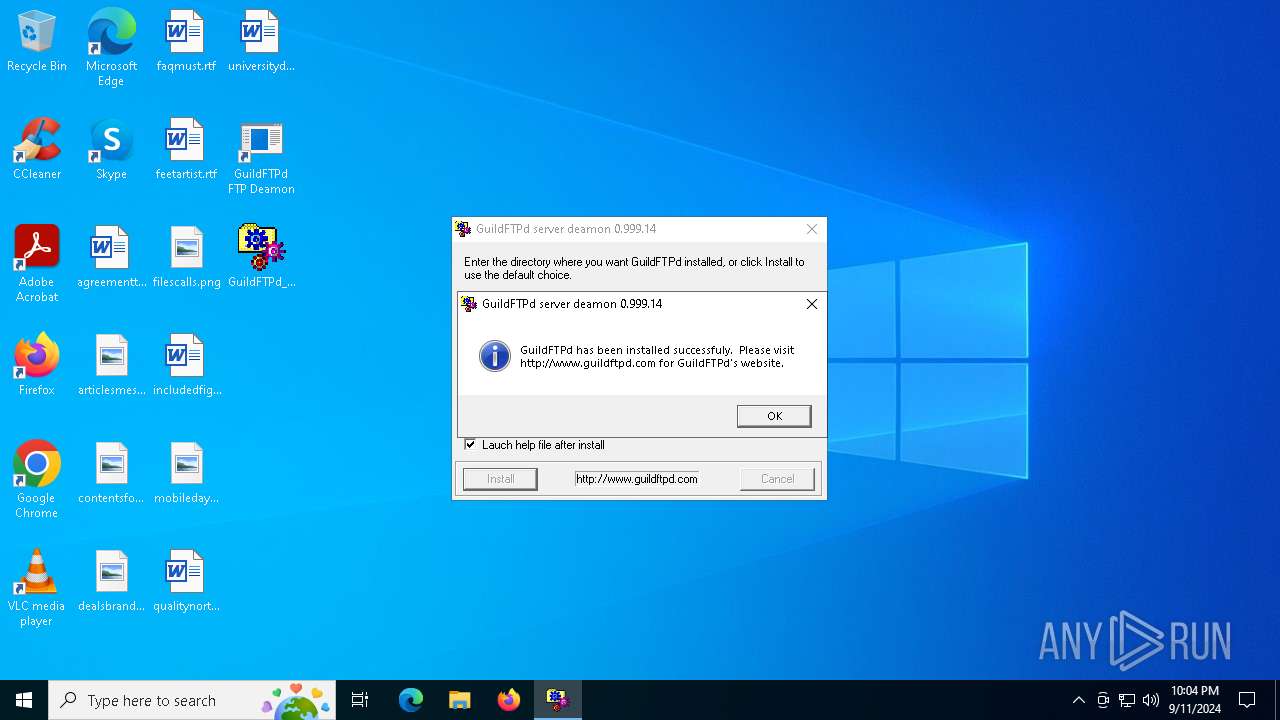
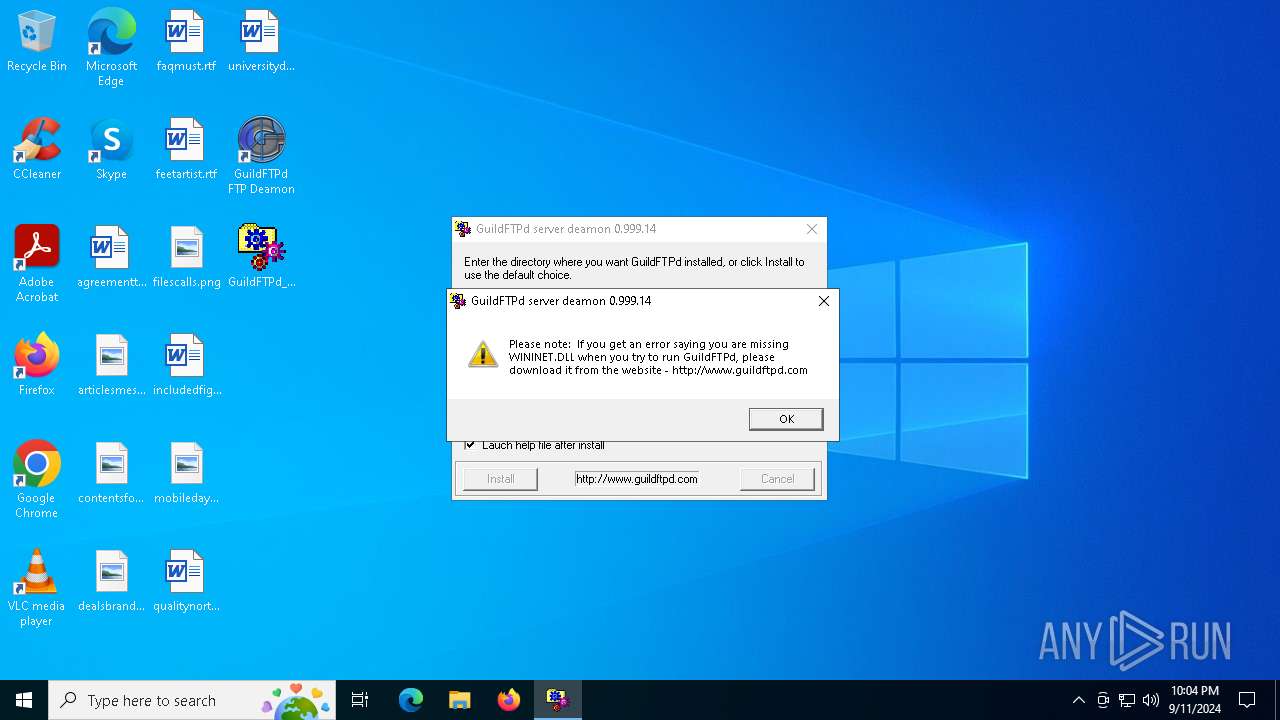
| File name: | GuildFTPd_0.999.14.exe |
| Full analysis: | https://app.any.run/tasks/2532b1f1-78b4-4664-a01a-a03df4019a91 |
| Verdict: | Malicious activity |
| Analysis date: | September 11, 2024, 22:03:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 9A15F9A3287C06D56DE9D23654FC61B6 |
| SHA1: | 1570A70CBBD5762A2E32144484914887BA0B4C21 |
| SHA256: | DAFE744AB172692A9F9F8B72D7D856CEA78B19340E8271EB37F775DC21FCC23A |
| SSDEEP: | 98304:LYmkmnReS03nk5nt2/Upnh8iB+Jiwtcv41TURydb2/tJJNnk6NZOo0qvDF+5Ow3+: |
MALICIOUS
No malicious indicators.SUSPICIOUS
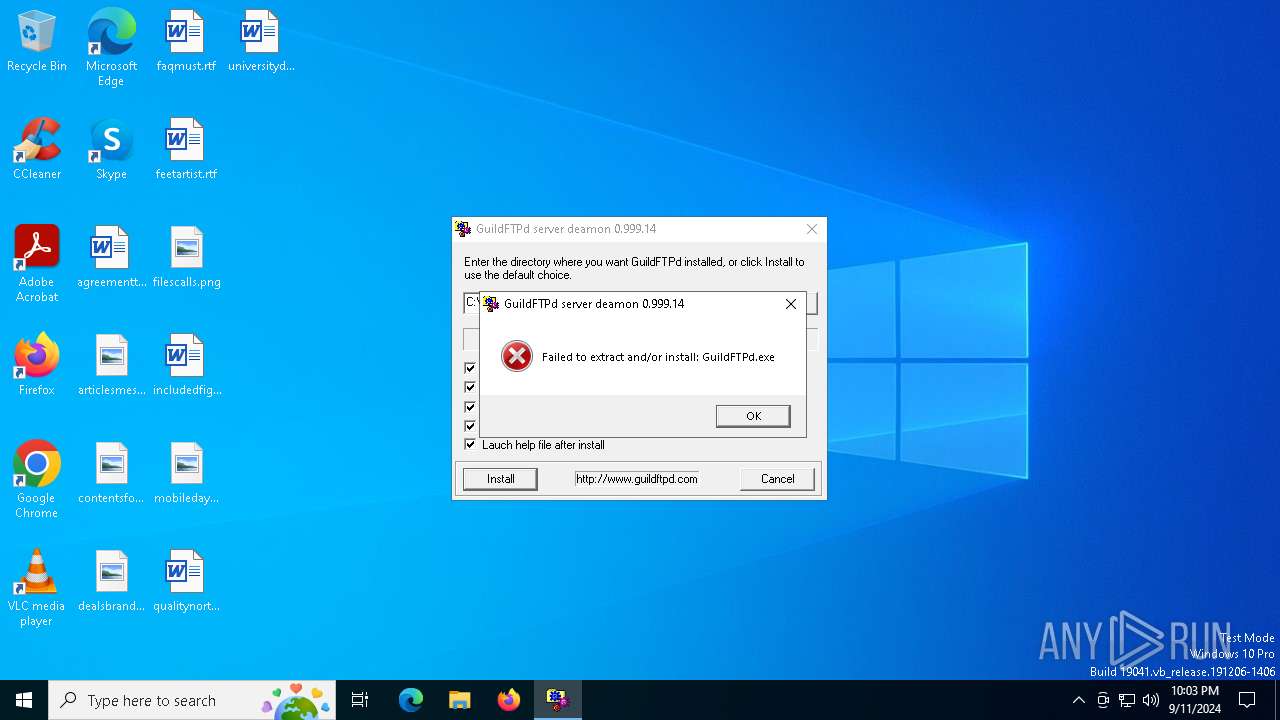
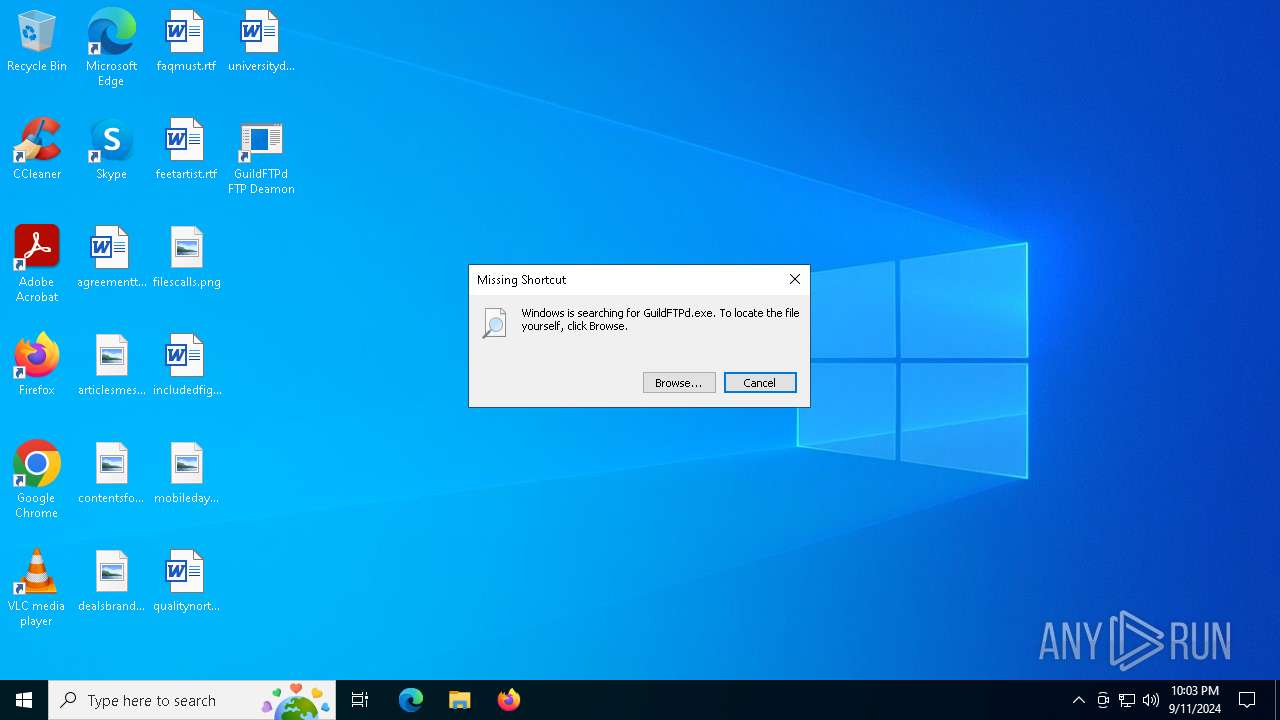
The process creates files with name similar to system file names
- GuildFTPd_0.999.14.exe (PID: 812)
- GuildFTPd_0.999.14.exe (PID: 1164)
Process drops legitimate windows executable
- GuildFTPd_0.999.14.exe (PID: 812)
- GuildFTPd_0.999.14.exe (PID: 1164)
- GuildFTPd_0.999.14.exe (PID: 5044)
Executable content was dropped or overwritten
- GuildFTPd_0.999.14.exe (PID: 812)
- GuildFTPd_0.999.14.exe (PID: 1164)
Reads security settings of Internet Explorer
- GuildFTPd_0.999.14.exe (PID: 812)
- GuildFTPd_0.999.14.exe (PID: 1164)
- GuildFTPd_0.999.14.exe (PID: 5044)
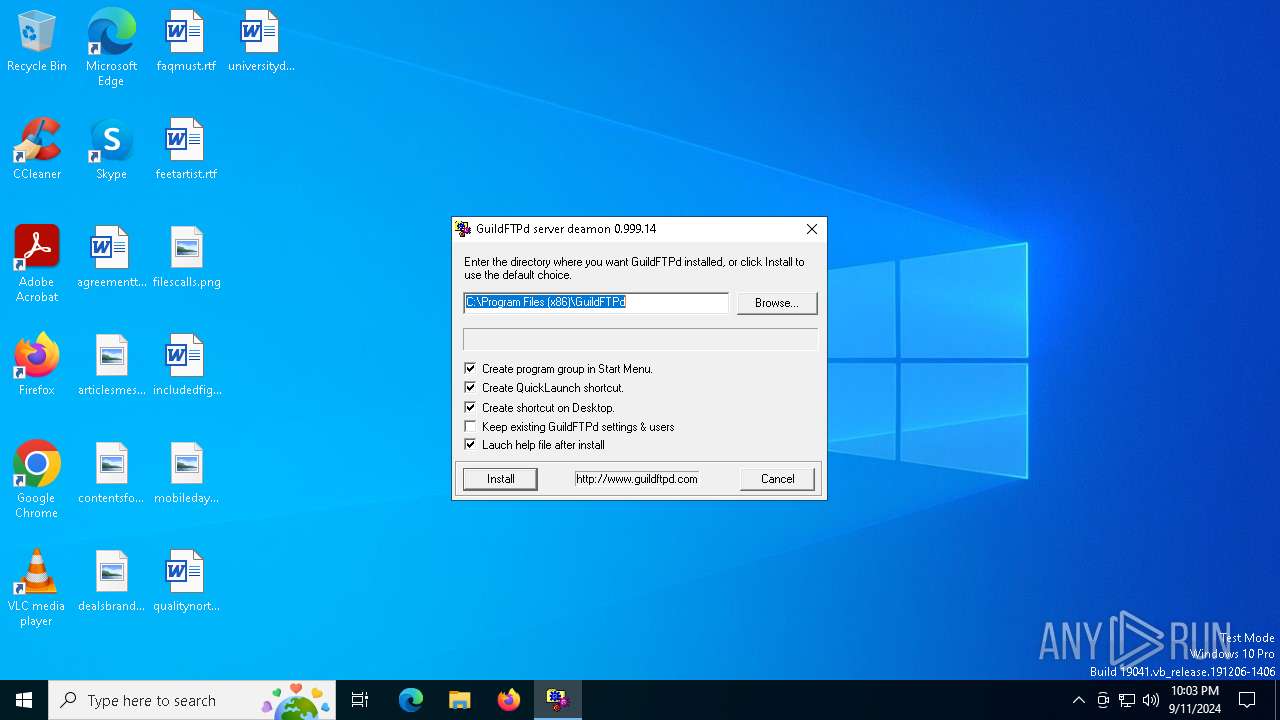
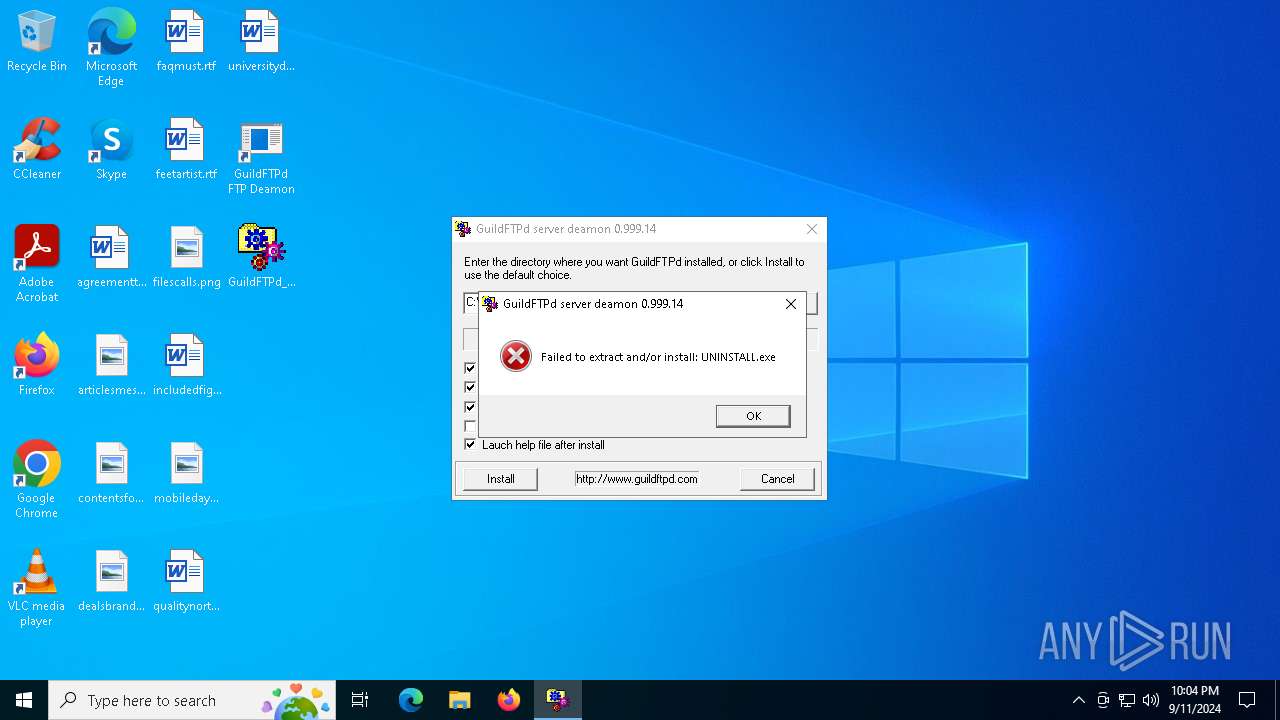
Creates a software uninstall entry
- GuildFTPd_0.999.14.exe (PID: 1164)
Reads Internet Explorer settings
- hh.exe (PID: 2572)
Reads Microsoft Outlook installation path
- hh.exe (PID: 2572)
INFO
Reads the computer name
- GuildFTPd_0.999.14.exe (PID: 812)
- GuildFTPd_0.999.14.exe (PID: 5044)
- GuildFTPd.exe (PID: 5516)
- GuildFTPd_0.999.14.exe (PID: 1164)
Create files in a temporary directory
- GuildFTPd_0.999.14.exe (PID: 812)
- GuildFTPd_0.999.14.exe (PID: 5044)
- hh.exe (PID: 2572)
- GuildFTPd_0.999.14.exe (PID: 1164)
Checks supported languages
- GuildFTPd_0.999.14.exe (PID: 812)
- GuildFTPd_0.999.14.exe (PID: 5044)
- GuildFTPd.exe (PID: 5516)
- GuildFTPd_0.999.14.exe (PID: 1164)
Creates files or folders in the user directory
- GuildFTPd_0.999.14.exe (PID: 812)
- GuildFTPd.exe (PID: 5516)
- hh.exe (PID: 2572)
- GuildFTPd_0.999.14.exe (PID: 5044)
Manual execution by a user
- GuildFTPd_0.999.14.exe (PID: 5044)
- GuildFTPd.exe (PID: 5516)
- GuildFTPd_0.999.14.exe (PID: 1164)
Creates files in the program directory
- GuildFTPd_0.999.14.exe (PID: 1164)
The process uses the downloaded file
- GuildFTPd_0.999.14.exe (PID: 1164)
- hh.exe (PID: 2572)
Checks proxy server information
- hh.exe (PID: 2572)
Reads security settings of Internet Explorer
- hh.exe (PID: 2572)
Process checks computer location settings
- GuildFTPd_0.999.14.exe (PID: 1164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2006:05:27 03:33:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 49152 |
| InitializedDataSize: | 1798144 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6c1f |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.1 |
| ProductVersionNumber: | 1.0.0.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
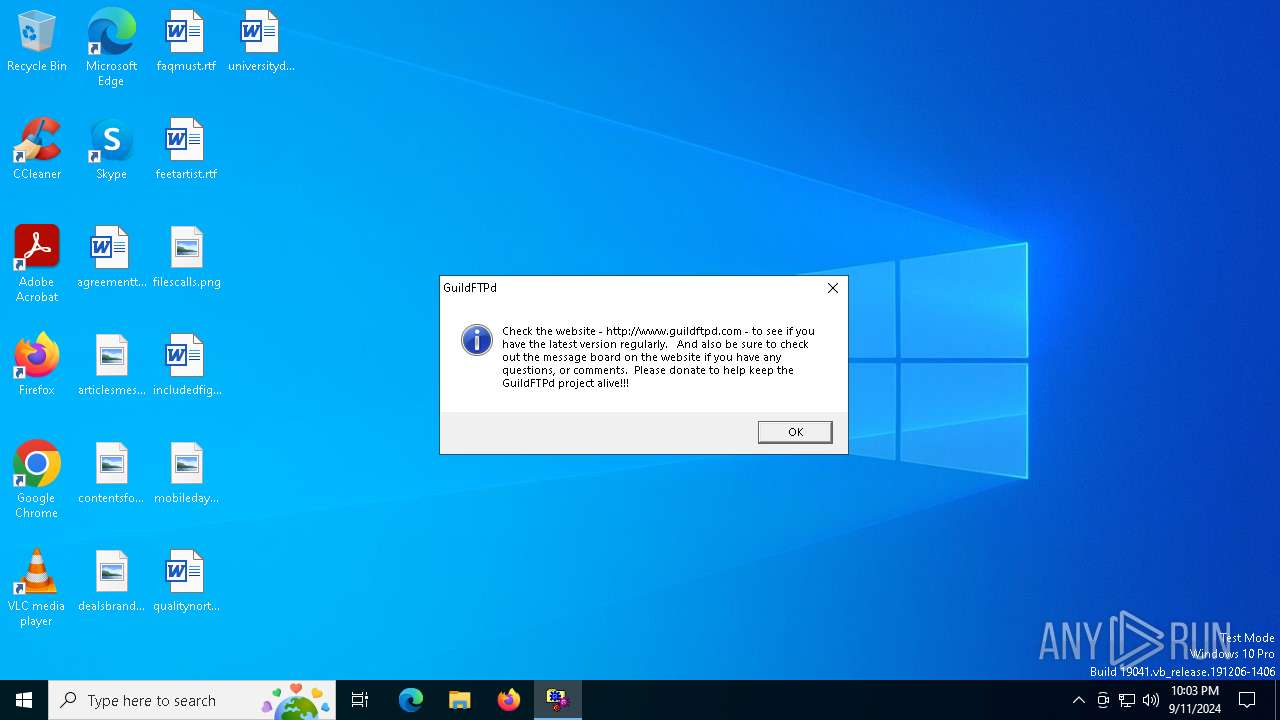
| Comments: | http://www.guildftpd.com |
| CompanyName: | Nitrolic, GuildFTPd |
| FileDescription: | GuildFTPd FTP server deamon |
| FileVersion: | 1.01 |
| LegalCopyright: | Copyright © Nitrolic 2001 |
| ProductName: | GuildFTPd |
| Undernet: | #GuildFTPd |
| Efnet: | #GuildFTPd |
| ProductVersion: | 1.01 |
Total processes
137
Monitored processes
5
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 812 | "C:\Users\admin\AppData\Local\Temp\GuildFTPd_0.999.14.exe" | C:\Users\admin\AppData\Local\Temp\GuildFTPd_0.999.14.exe | explorer.exe | ||||||||||||
User: admin Company: Nitrolic, GuildFTPd Integrity Level: MEDIUM Description: GuildFTPd FTP server deamon Exit code: 0 Version: 1.01 Modules
| |||||||||||||||
| 1164 | "C:\Users\admin\Desktop\GuildFTPd_0.999.14.exe" | C:\Users\admin\Desktop\GuildFTPd_0.999.14.exe | explorer.exe | ||||||||||||
User: admin Company: Nitrolic, GuildFTPd Integrity Level: HIGH Description: GuildFTPd FTP server deamon Exit code: 0 Version: 1.01 Modules
| |||||||||||||||
| 2572 | "C:\WINDOWS\hh.exe" C:\PROGRA~2\GUILDF~1\guildftpd.chm | C:\Windows\hh.exe | — | GuildFTPd_0.999.14.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® HTML Help Executable Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5044 | "C:\Users\admin\Desktop\GuildFTPd_0.999.14.exe" | C:\Users\admin\Desktop\GuildFTPd_0.999.14.exe | — | explorer.exe | |||||||||||
User: admin Company: Nitrolic, GuildFTPd Integrity Level: MEDIUM Description: GuildFTPd FTP server deamon Exit code: 0 Version: 1.01 Modules
| |||||||||||||||
| 5516 | "C:\Program Files (x86)\GuildFTPd\GuildFTPd.exe" | C:\Program Files (x86)\GuildFTPd\GuildFTPd.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: GuildFTPd FTP Server Deamon Version: 0.999.14 Modules
| |||||||||||||||
Total events
1 684
Read events
1 675
Write events
9
Delete events
0
Modification events
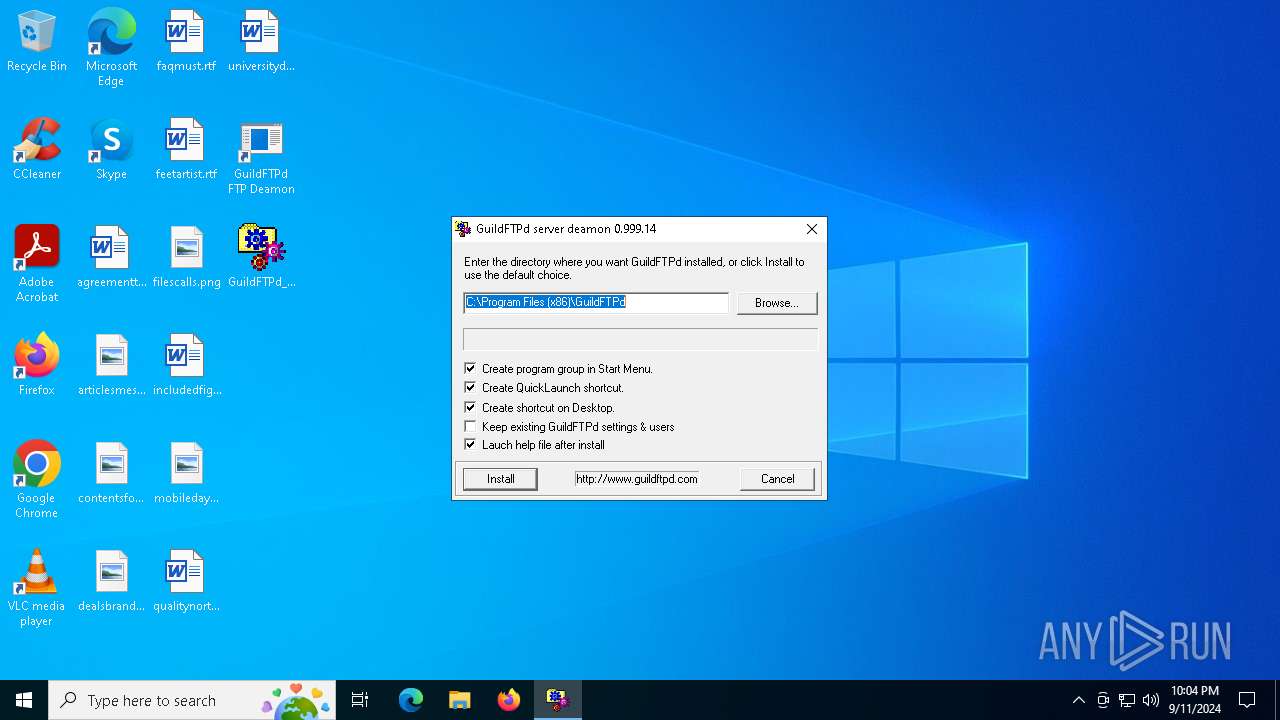
| (PID) Process: | (1164) GuildFTPd_0.999.14.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\GuildFTPd |
| Operation: | write | Name: | DisplayName |
Value: GuildFTPd FTP Deamon | |||
| (PID) Process: | (1164) GuildFTPd_0.999.14.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\GuildFTPd |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files (x86)\GuildFTPd\Uninstall.exe | |||
| (PID) Process: | (1164) GuildFTPd_0.999.14.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\GuildFTPd |
| Operation: | write | Name: | Installation directory |
Value: C:\Program Files (x86)\GuildFTPd | |||
| (PID) Process: | (1164) GuildFTPd_0.999.14.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\GuildFTPd |
| Operation: | write | Name: | InstallDir |
Value: C:\Program Files (x86)\GuildFTPd | |||
| (PID) Process: | (1164) GuildFTPd_0.999.14.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.chm\OpenWithProgids |
| Operation: | write | Name: | chm.file |
Value: | |||
| (PID) Process: | (2572) hh.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2572) hh.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2572) hh.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5516) GuildFTPd.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\GuildFTPd |
| Operation: | write | Name: | LogDir |
Value: C:\Program Files (x86)\GuildFTPd\syslog.txt | |||
Executable files
18
Suspicious files
16
Text files
24
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 812 | GuildFTPd_0.999.14.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files (x86)\GuildFTPd\site_commands.txt | text | |
MD5:237E5BE199B011A087D65332A9E5717A | SHA256:A4B9B606CA6FA55FA5EF26760EFC1190E9776238D9896FA874B0368A5989A08A | |||
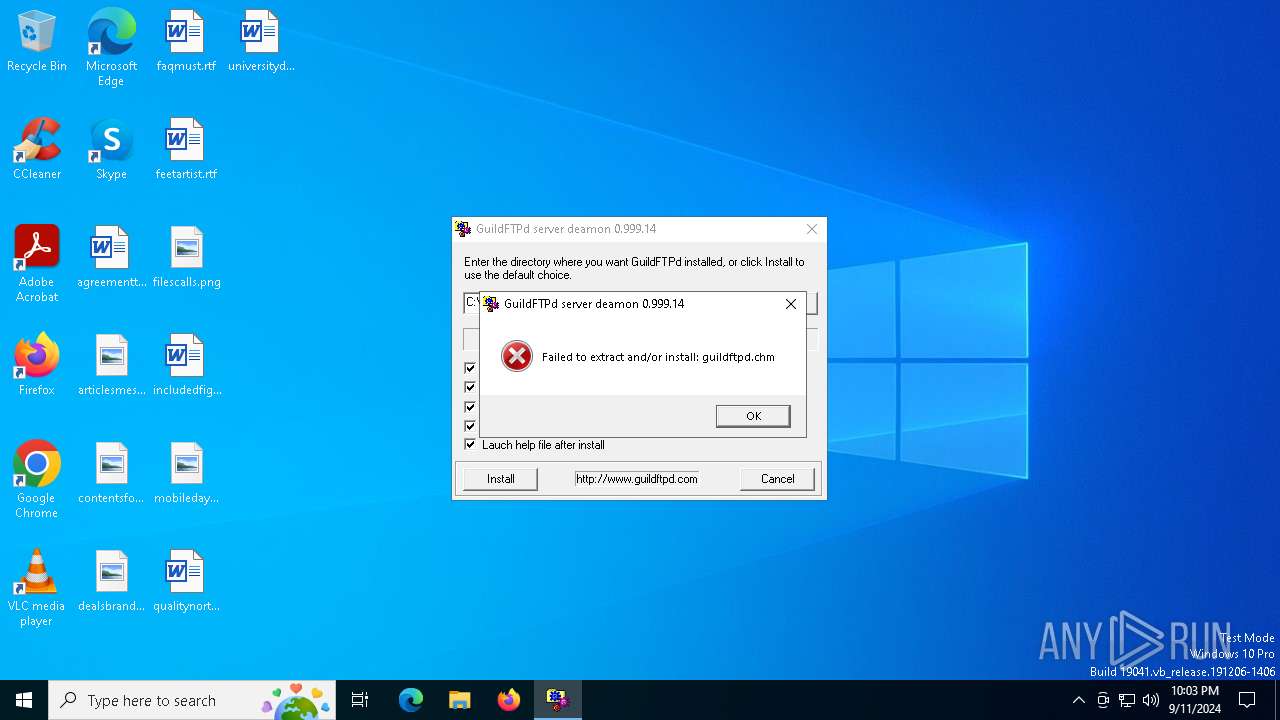
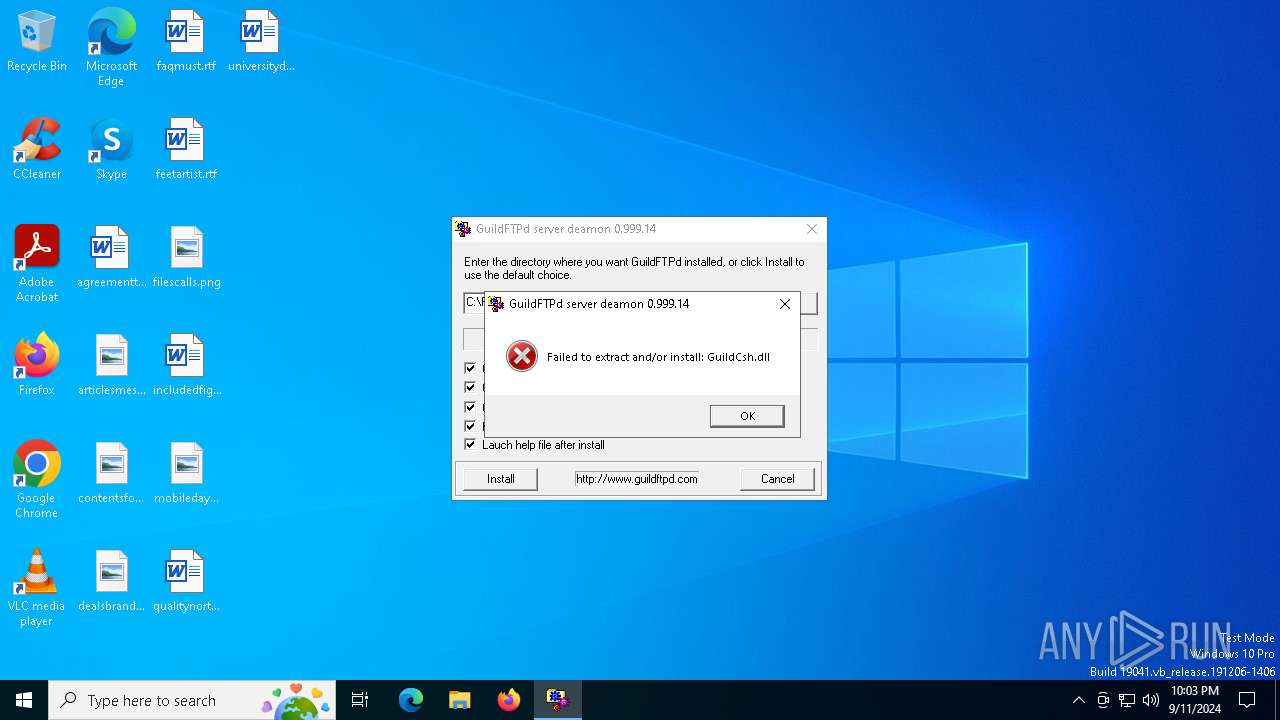
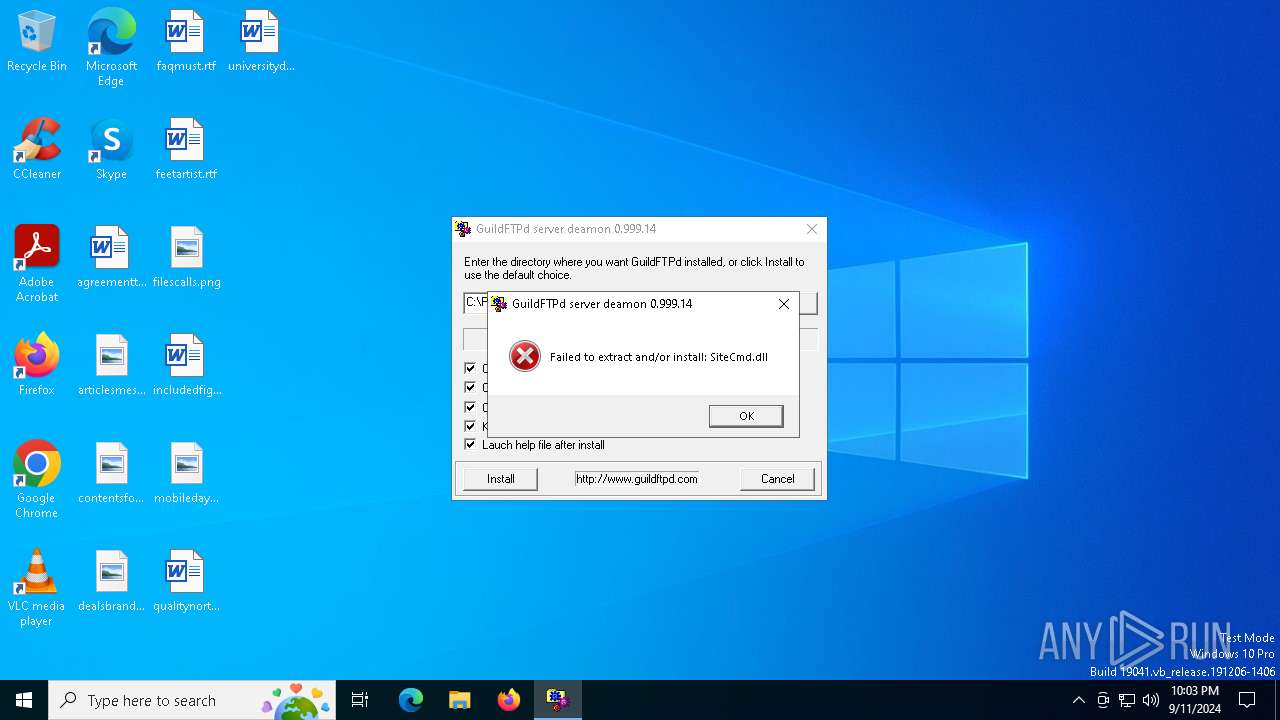
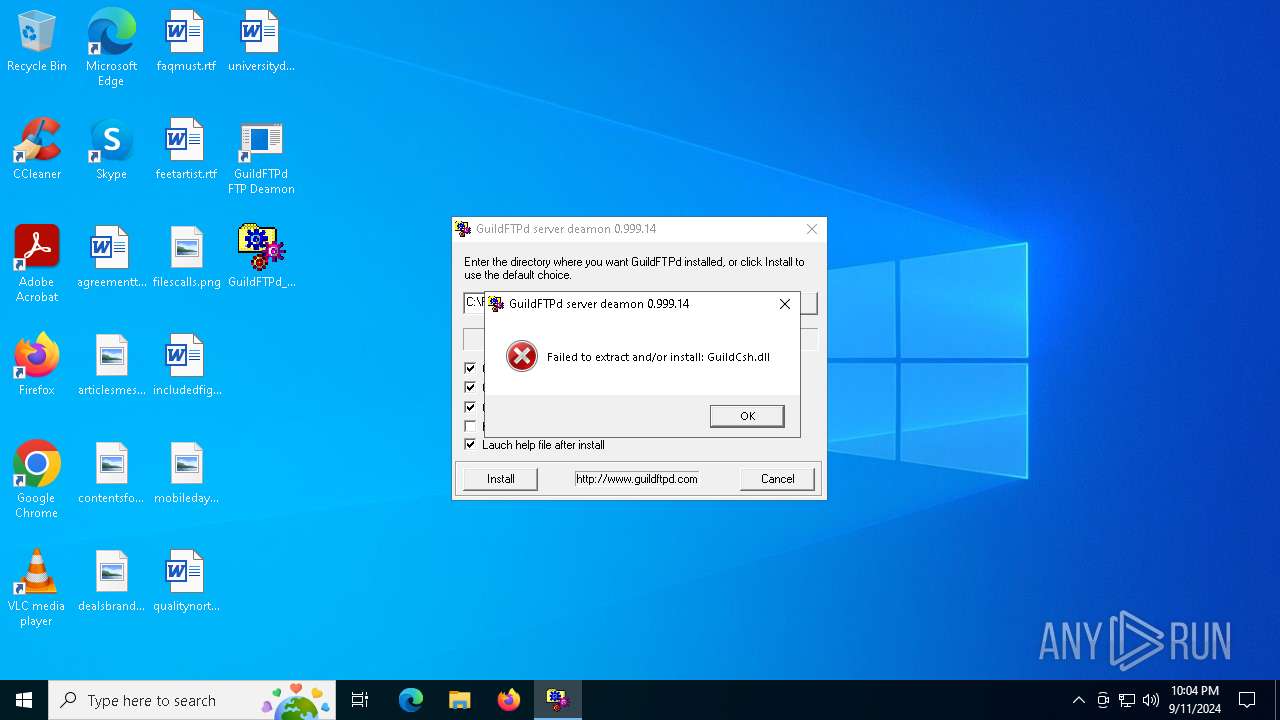
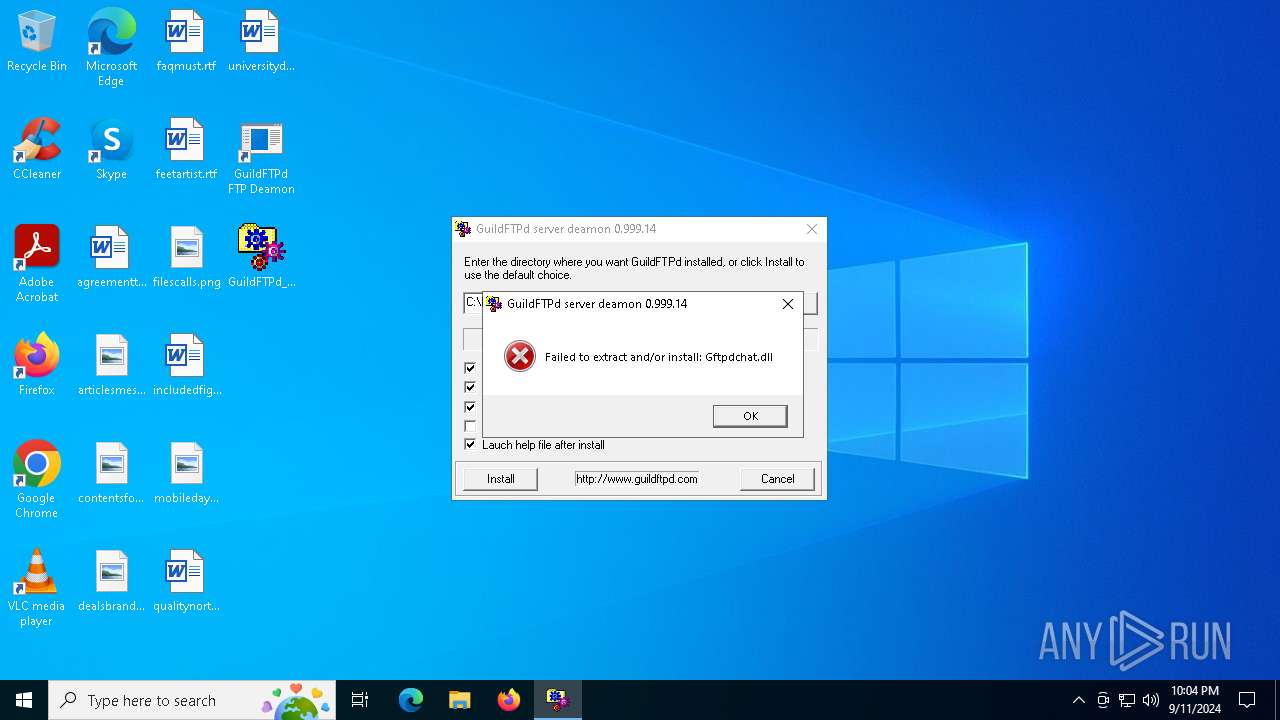
| 812 | GuildFTPd_0.999.14.exe | C:\Users\admin\AppData\Local\Temp\GuildCsh.dll | executable | |
MD5:F3DF70C4DAB6675C9FAA3FC568EB2C2E | SHA256:538E7624E5DA7011293C5C99068E84BB7EE55B673556456484D01D9275B85361 | |||
| 812 | GuildFTPd_0.999.14.exe | C:\Users\admin\AppData\Local\Temp\2 | compressed | |
MD5:1DEC59D2C985B5EEA0A0BD30A3166558 | SHA256:8F032EE8EA9D75E6911E8034C756480E4546A9477C59A036DCCFD8B3D8A4362A | |||
| 812 | GuildFTPd_0.999.14.exe | C:\Users\admin\Desktop\GuildFTPd FTP Deamon.lnk | lnk | |
MD5:CB40558CDB009B3701BF513664428655 | SHA256:E607979CBFC7EC8FF73E3D720053ABA38393A065B9B9A25562332477BB2BDC0D | |||
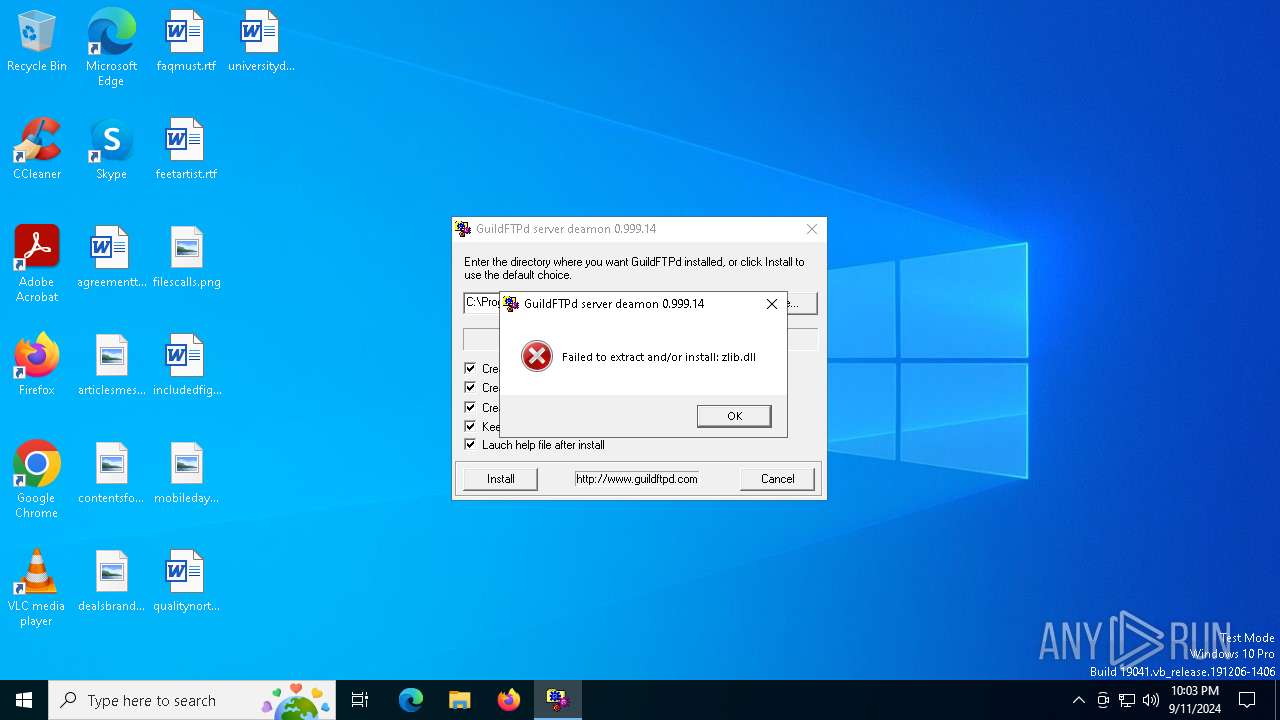
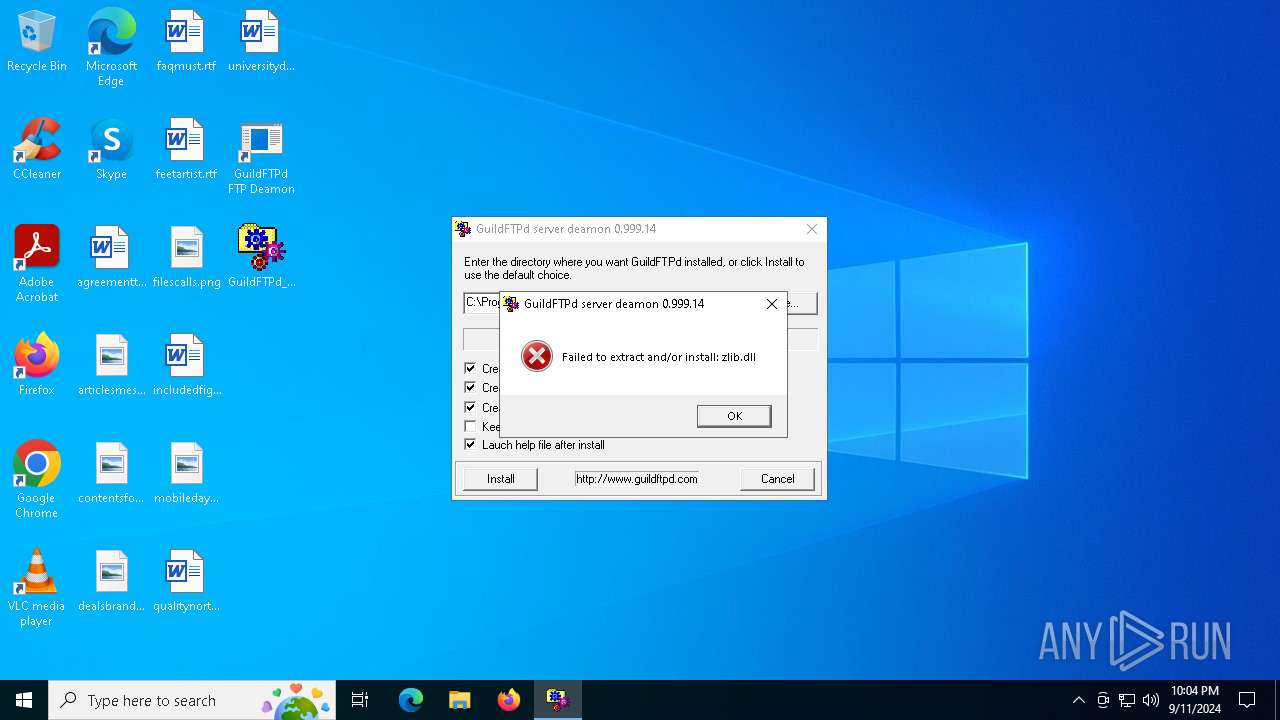
| 812 | GuildFTPd_0.999.14.exe | C:\Users\admin\AppData\Local\Temp\zlib.dll | executable | |
MD5:87EDDCEB9D22C129E386E652C5CDA521 | SHA256:792D768258EDDAEC86D9263E51FF64EE6F0BED2F28205F535EE150E94F8D6A2B | |||
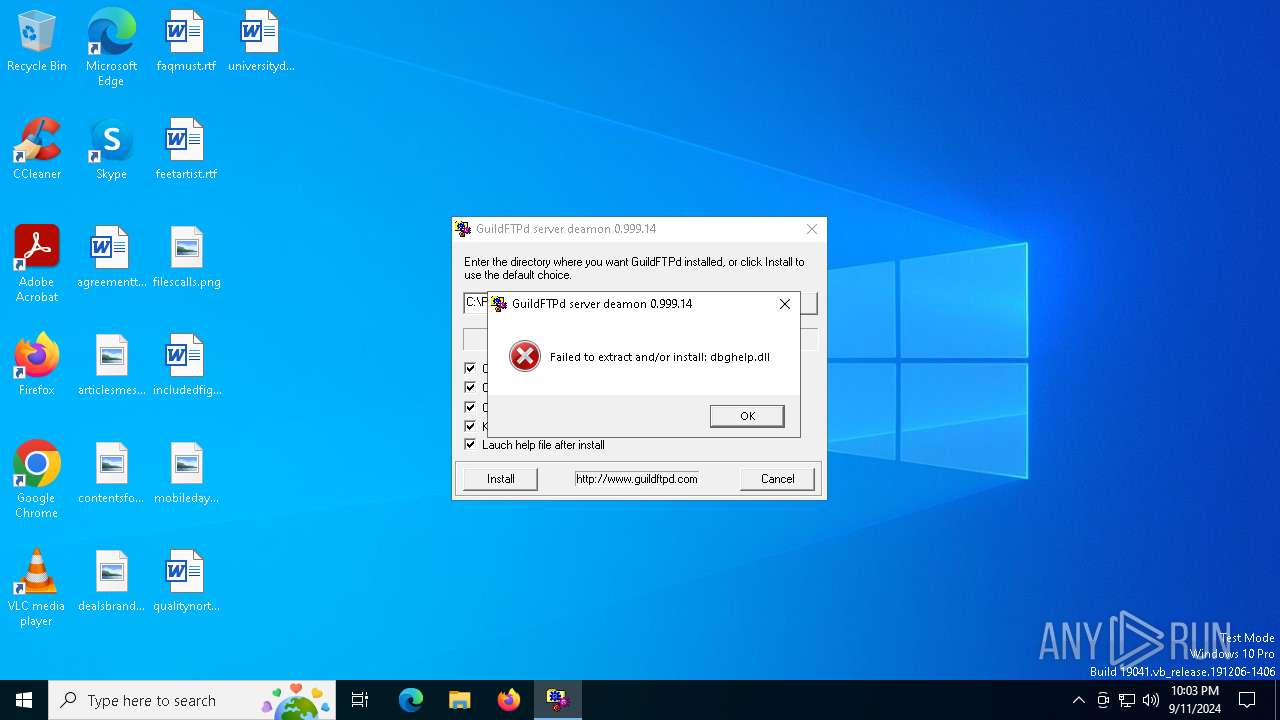
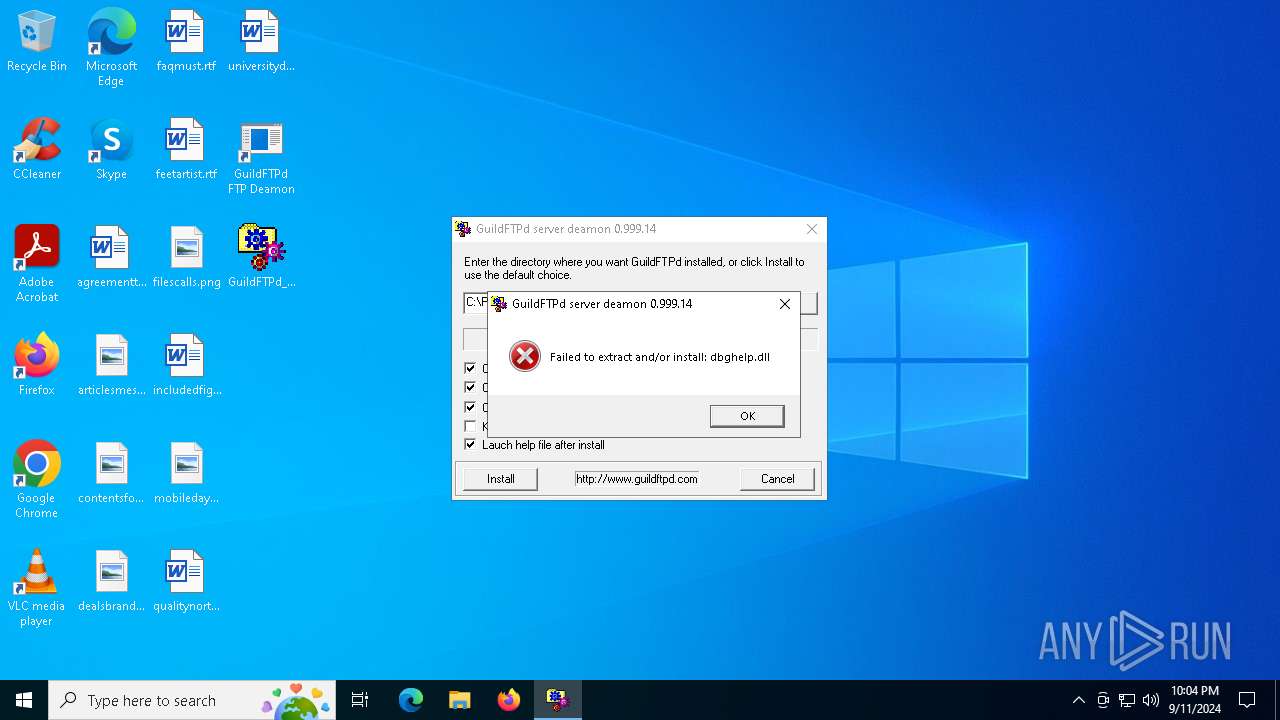
| 812 | GuildFTPd_0.999.14.exe | C:\Users\admin\AppData\Local\Temp\dbghelp.dll | executable | |
MD5:E458D88C71990F545EF941CD16080BAD | SHA256:5EC121730240548A85B7EF1F7E30D5FDBEE153BB20DD92C2D44BF37395294EC0 | |||
| 812 | GuildFTPd_0.999.14.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files (x86)\GuildFTPd\Tips.txt | text | |
MD5:B9B6D7D81409613D7A7B0F428ABD4AB7 | SHA256:06D6AAA8855F700EAB54F25F0F9850A6EC3BFD7168D14746F75219A028B20EAE | |||
| 812 | GuildFTPd_0.999.14.exe | C:\Users\admin\AppData\Local\Temp\Tips.txt | text | |
MD5:B9B6D7D81409613D7A7B0F428ABD4AB7 | SHA256:06D6AAA8855F700EAB54F25F0F9850A6EC3BFD7168D14746F75219A028B20EAE | |||
| 812 | GuildFTPd_0.999.14.exe | C:\Users\admin\AppData\Local\Temp\site_commands.txt | text | |
MD5:237E5BE199B011A087D65332A9E5717A | SHA256:A4B9B606CA6FA55FA5EF26760EFC1190E9776238D9896FA874B0368A5989A08A | |||
| 812 | GuildFTPd_0.999.14.exe | C:\Users\admin\AppData\Local\Temp\readme.txt | text | |
MD5:C932A2326FE8CD4399AF924D4B6F84F5 | SHA256:B0138D2BF57465BF2EA9762FDB081BBCB12A43C873653497B71B9700DC52E3B4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
32
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4132 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1780 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7156 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7156 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6260 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4132 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4132 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4132 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1780 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1780 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |