| File name: | OInstall.exe |
| Full analysis: | https://app.any.run/tasks/83cee305-0da0-45f8-8b49-f8b35606e9c6 |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2023, 08:19:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 7CB8C00408DA25A7A9774D48EE5848A2 |
| SHA1: | 49EE5BBAFEF9B20BBBF3B9CDED16D7AAA9C18052 |
| SHA256: | DAEB52896FED1ADC218E322A88285F9CBBA1891C81C517AD04AC059B292F85E2 |
| SSDEEP: | 98304:DNSIrYgH85aDZAYEOv9qrtRqIXHEaUlU1OMV7+IfvmaKDf1zBMcbXERZYlN7imhT:I4zQMNF7IhT4ekxp6W |
MALICIOUS
Drops the executable file immediately after the start
- files.dat (PID: 2792)
- OInstall.exe (PID: 3508)
Application was dropped or rewritten from another process
- files.dat (PID: 2792)
SUSPICIOUS
Process drops legitimate windows executable
- OInstall.exe (PID: 3508)
- files.dat (PID: 2792)
Starts application with an unusual extension
- cmd.exe (PID: 2036)
Starts CMD.EXE for commands execution
- OInstall.exe (PID: 3508)
Drops 7-zip archiver for unpacking
- OInstall.exe (PID: 3508)
The process drops C-runtime libraries
- files.dat (PID: 2792)
INFO
Reads the computer name
- OInstall.exe (PID: 3508)
Checks supported languages
- OInstall.exe (PID: 3508)
- files.dat (PID: 2792)
Reads Environment values
- OInstall.exe (PID: 3508)
The executable file from the user directory is run by the CMD process
- files.dat (PID: 2792)
Create files in a temporary directory
- files.dat (PID: 2792)
- OInstall.exe (PID: 3508)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (76) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.6) |
| .exe | | | Generic Win/DOS Executable (5.6) |
| .exe | | | DOS Executable Generic (5.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:01:07 04:22:16+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 9834496 |
| InitializedDataSize: | 90112 |
| UninitializedDataSize: | 9330688 |
| EntryPoint: | 0x1247530 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.5.3.0 |
| ProductVersionNumber: | 6.5.3.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
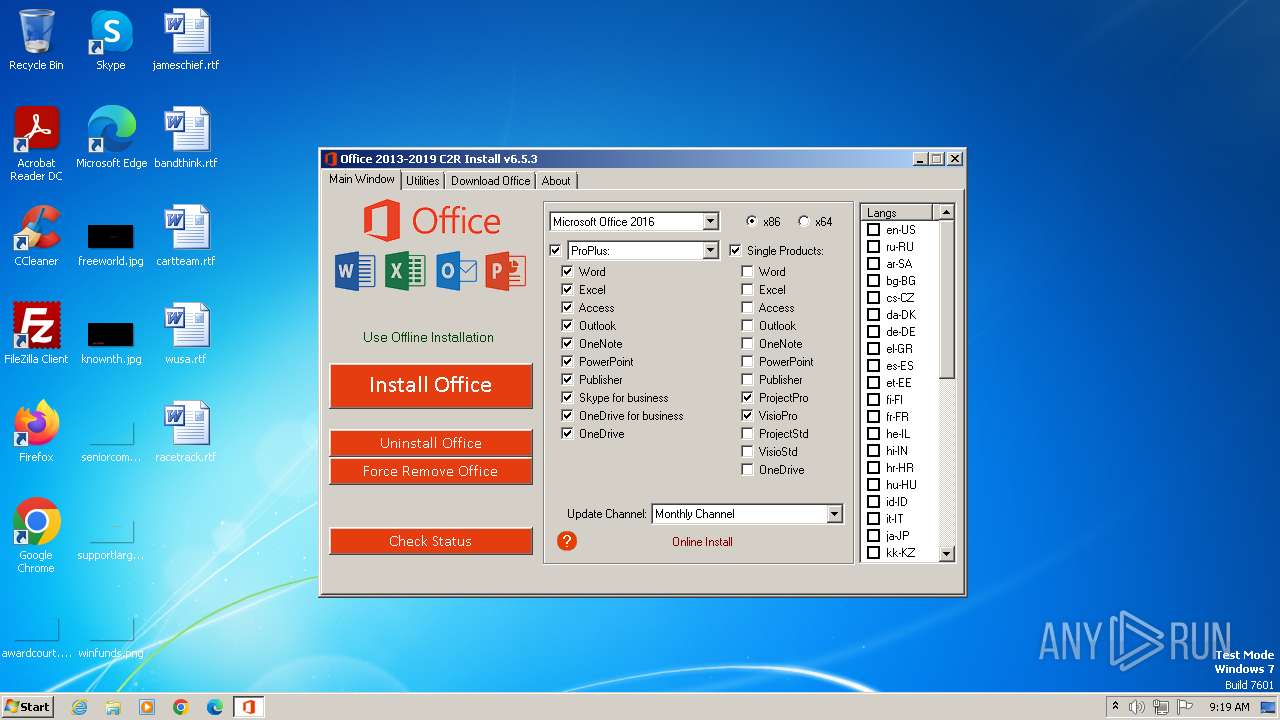
| ProductName: | Office 2013-2016 C2R Install |
| FileDescription: | Office 2013-2016 C2R Install |
Total processes
43
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2036 | "C:\Windows\System32\cmd.exe" /D /c files.dat -y -pkmsauto | C:\Windows\System32\cmd.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2404 | "C:\Windows\System32\cmd.exe" /D /c copy C:\Windows\system32\Tasks\OInstall "C:\Windows\Temp\OInstall.tmp" /Y | C:\Windows\System32\cmd.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2484 | "C:\Users\admin\AppData\Local\Temp\OInstall.exe" | C:\Users\admin\AppData\Local\Temp\OInstall.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Office 2013-2016 C2R Install Exit code: 3221226540 Modules
| |||||||||||||||
| 2792 | files.dat -y -pkmsauto | C:\Users\admin\AppData\Local\Temp\files\files.dat | — | cmd.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7z Console SFX Exit code: 0 Version: 9.20 Modules
| |||||||||||||||
| 3508 | "C:\Users\admin\AppData\Local\Temp\OInstall.exe" | C:\Users\admin\AppData\Local\Temp\OInstall.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Office 2013-2016 C2R Install Exit code: 0 Modules
| |||||||||||||||
Total events
104
Read events
104
Write events
0
Delete events
0
Modification events
Executable files
6
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2792 | files.dat | C:\Users\admin\AppData\Local\Temp\files\Uninstall.xml | text | |
MD5:364F86F97324EA82FE0D142CD01CF6DD | SHA256:09D5B42140BAB13165BA97FBD0E77792304C3C93555BE02C3DCE21A7A69C66DD | |||
| 3508 | OInstall.exe | C:\Users\admin\AppData\Local\Temp\files\files.dat | executable | |
MD5:55D21B2C272A5D6B9F54FA9ED82BF9EB | SHA256:7A1C82E264258470D14CA345EA1A9B6FC34FA19B393A92077A01BE5F1AD08F47 | |||
| 2792 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x64\cleanospp.exe | executable | |
MD5:162AB955CB2F002A73C1530AA796477F | SHA256:5CE462E5F34065FC878362BA58617FAB28C22D631B9D836DDDCF43FB1AD4DE6E | |||
| 3508 | OInstall.exe | C:\Users\admin\AppData\Local\Temp\files\setup.exe | executable | |
MD5:B374FA0E7E34B9CE9C142FE80E1EFADE | SHA256:A87105965530799BABBB71A1FD52DBD7CDDEE71C40E2C37576235D156FF02027 | |||
| 2792 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x86\cleanospp.exe | executable | |
MD5:5FD363D52D04AC200CD24F3BCC903200 | SHA256:3FDEFE2AD092A9A7FE0EDF0AC4DC2DE7E5B9CE6A0804F6511C06564194966CF9 | |||
| 2792 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x64\msvcr100.dll | executable | |
MD5:DF3CA8D16BDED6A54977B30E66864D33 | SHA256:1D1A1AE540BA132F998D60D3622F0297B6E86AE399332C3B47462D7C0F560A36 | |||
| 3508 | OInstall.exe | C:\Users\admin\AppData\Local\Temp\files\Configure.xml | text | |
MD5:AC6BE84084E31DBB0E08D188B6C86EC8 | SHA256:1879F7DE537C2AA70292C61EBEF9C6477D36E25B2E6A639E318B159E0A22B0FC | |||
| 2792 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x86\msvcr100.dll | executable | |
MD5:BF38660A9125935658CFA3E53FDC7D65 | SHA256:60C06E0FA4449314DA3A0A87C1A9D9577DF99226F943637E06F61188E5862EFA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |