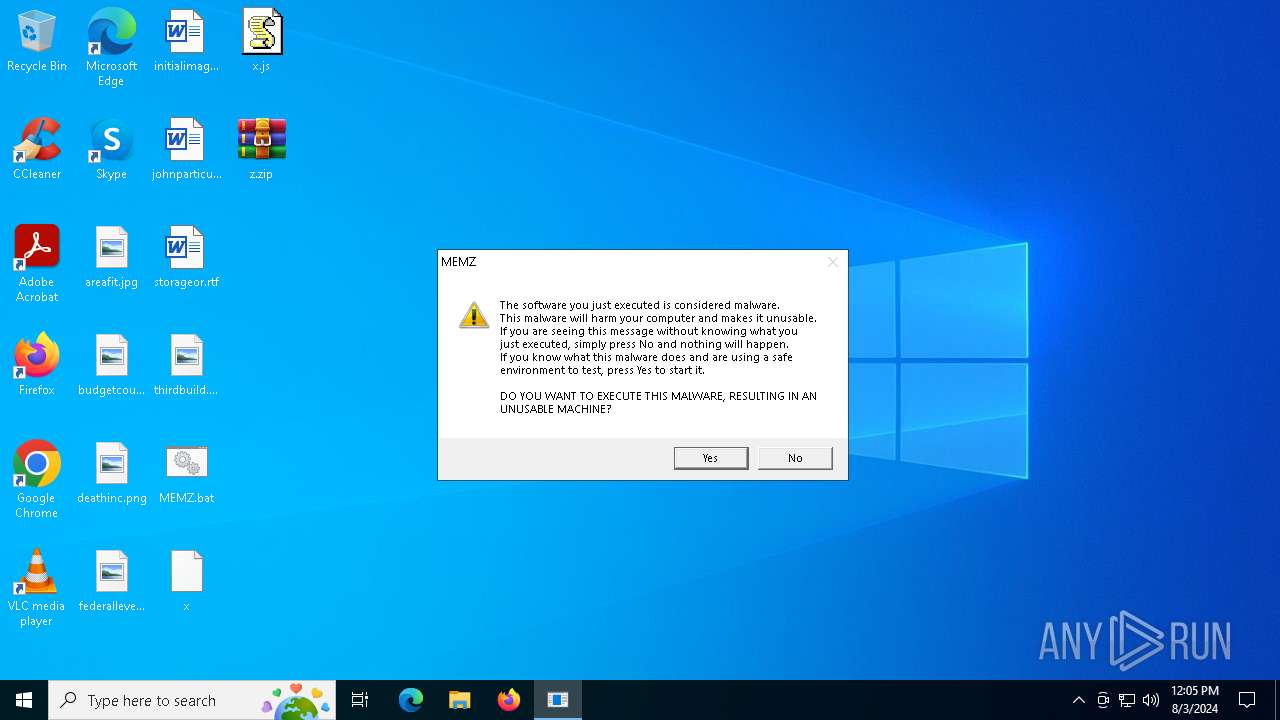
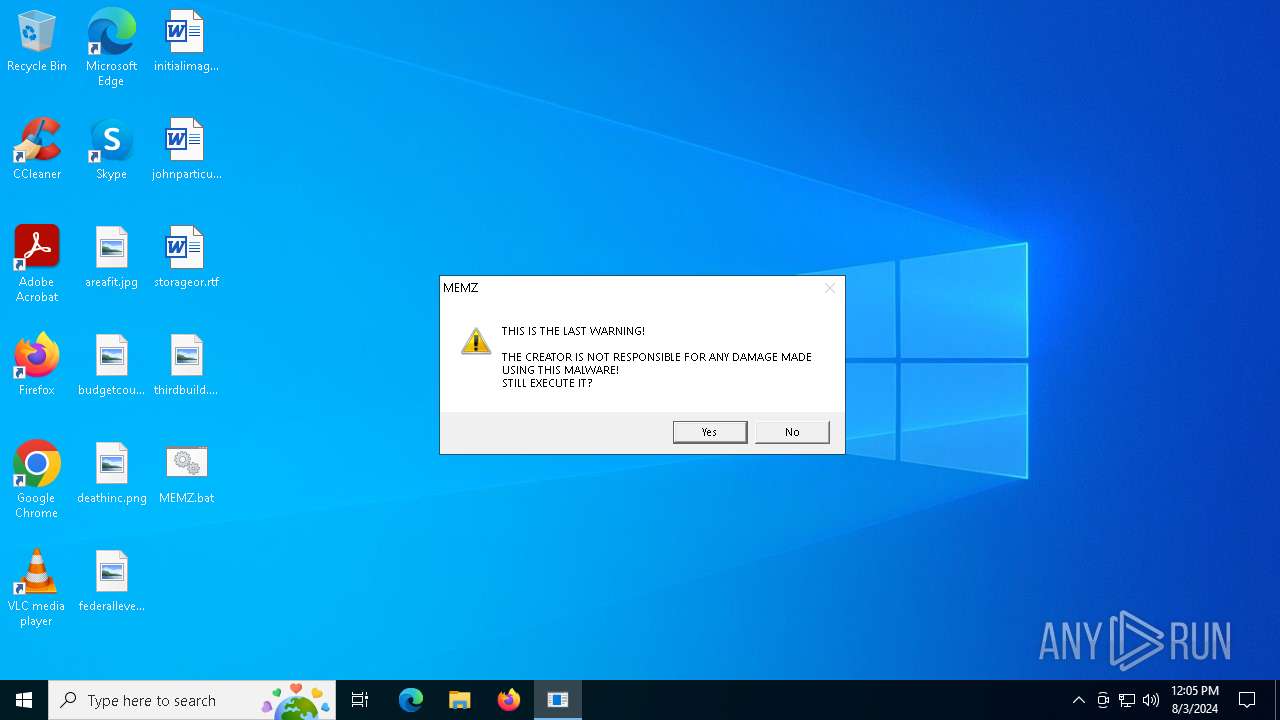
| File name: | MEMZ.bat |
| Full analysis: | https://app.any.run/tasks/3e05b204-ecd8-45ca-97bd-e2989e3c0bb7 |
| Verdict: | Malicious activity |
| Analysis date: | August 03, 2024, 12:05:46 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text |
| MD5: | 63C6EC6B042BCB00D2D832C0E4F25DCA |
| SHA1: | A904A7C3FC89FF497E91384A63DB3282E00D31CE |
| SHA256: | DAE968F47476EF79B122E771CCD0A2BACDE2AC3535F68047239682FEFA3DFE50 |
| SSDEEP: | 192:E7N3ODNPiwc205VjF+Ijytxd+7yxpVtLoTKihWn5hhHxGtHfzf+H/0Nz6hcbXR:E85qwc35O1+7y/LphxxGtHAhubXR |
MALICIOUS
Gets a file object corresponding to the file in a specified path (SCRIPT)
- cscript.exe (PID: 6380)
Uses base64 encoding (SCRIPT)
- cscript.exe (PID: 6380)
SUSPICIOUS
The process executes JS scripts
- cmd.exe (PID: 6320)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 6380)
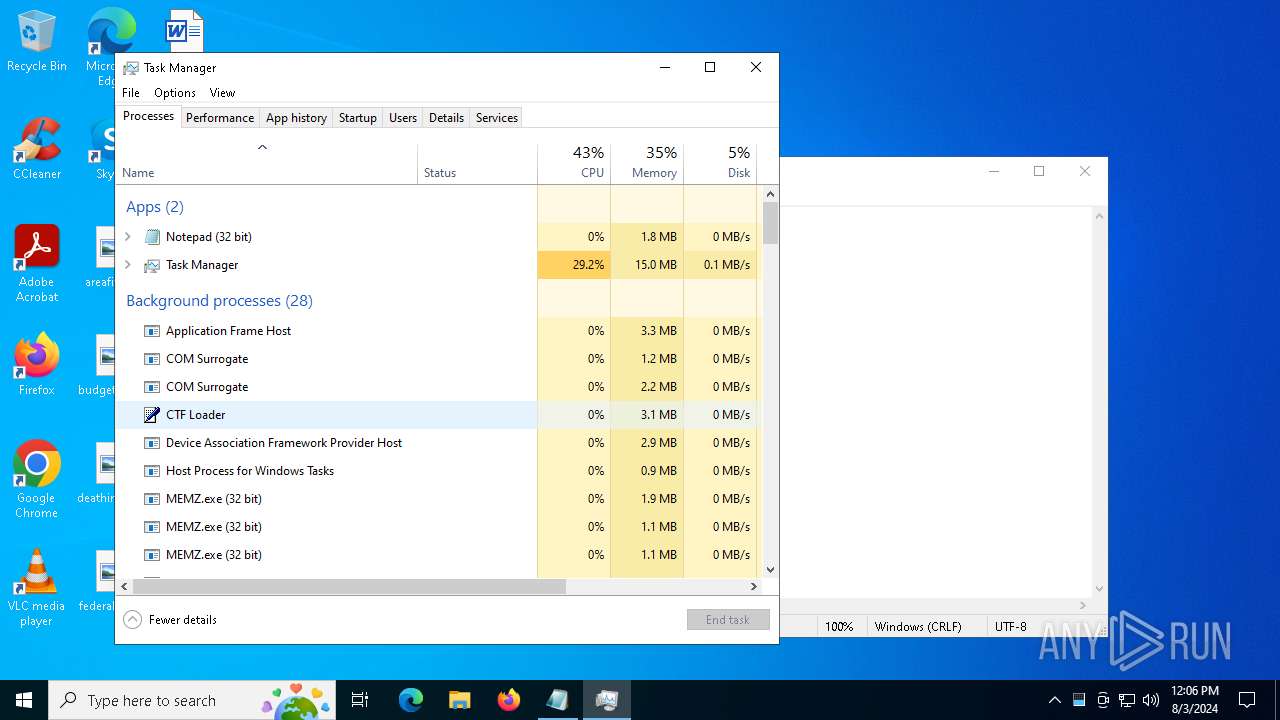
The executable file from the user directory is run by the CMD process
- MEMZ.exe (PID: 6456)
- MEMZ.exe (PID: 6488)
- MEMZ.exe (PID: 6536)
Creates a Folder object (SCRIPT)
- cscript.exe (PID: 6380)
Writes binary data to a Stream object (SCRIPT)
- cscript.exe (PID: 6380)
Saves data to a binary file (SCRIPT)
- cscript.exe (PID: 6380)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 6380)
Sets XML DOM element text (SCRIPT)
- cscript.exe (PID: 6380)
Script creates XML DOM node (SCRIPT)
- cscript.exe (PID: 6380)
Executable content was dropped or overwritten
- cscript.exe (PID: 6380)
Creates XML DOM element (SCRIPT)
- cscript.exe (PID: 6380)
Reads security settings of Internet Explorer
- MEMZ.exe (PID: 6536)
- MEMZ.exe (PID: 4772)
Reads the date of Windows installation
- MEMZ.exe (PID: 6536)
- MEMZ.exe (PID: 4772)
Application launched itself
- MEMZ.exe (PID: 6536)
Creates file in the systems drive root
- MEMZ.exe (PID: 4772)
- notepad.exe (PID: 3812)
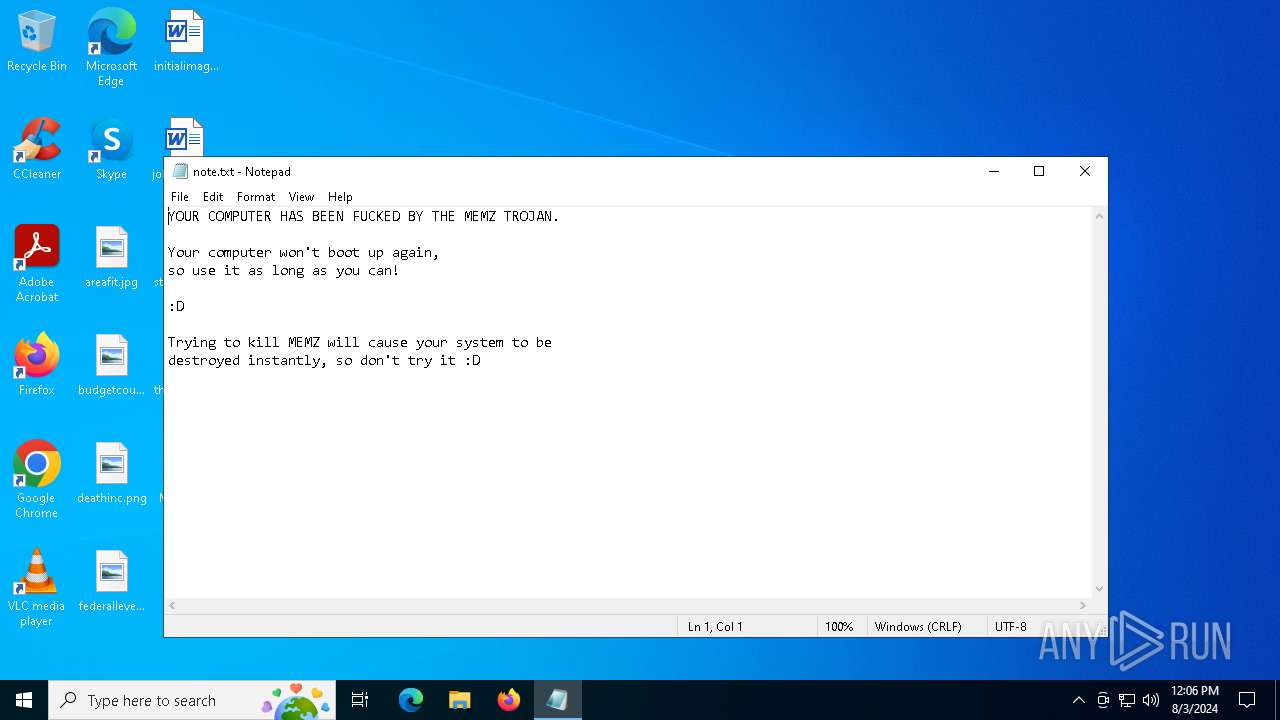
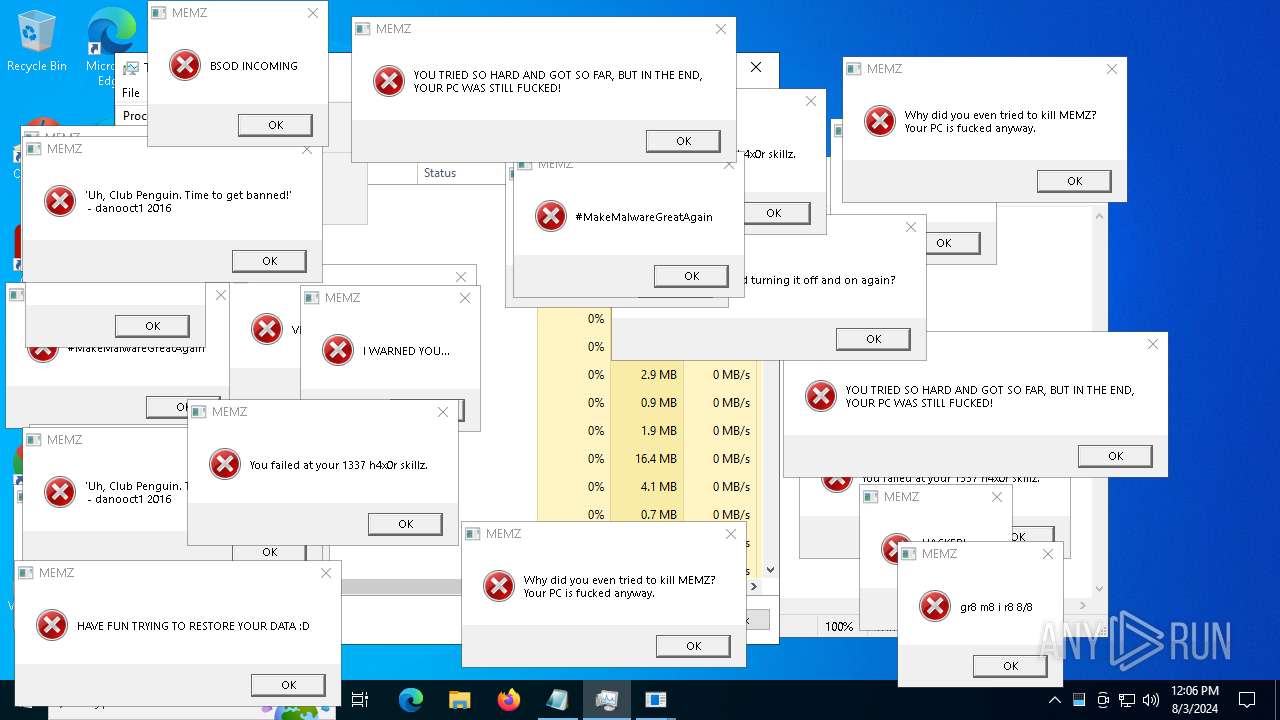
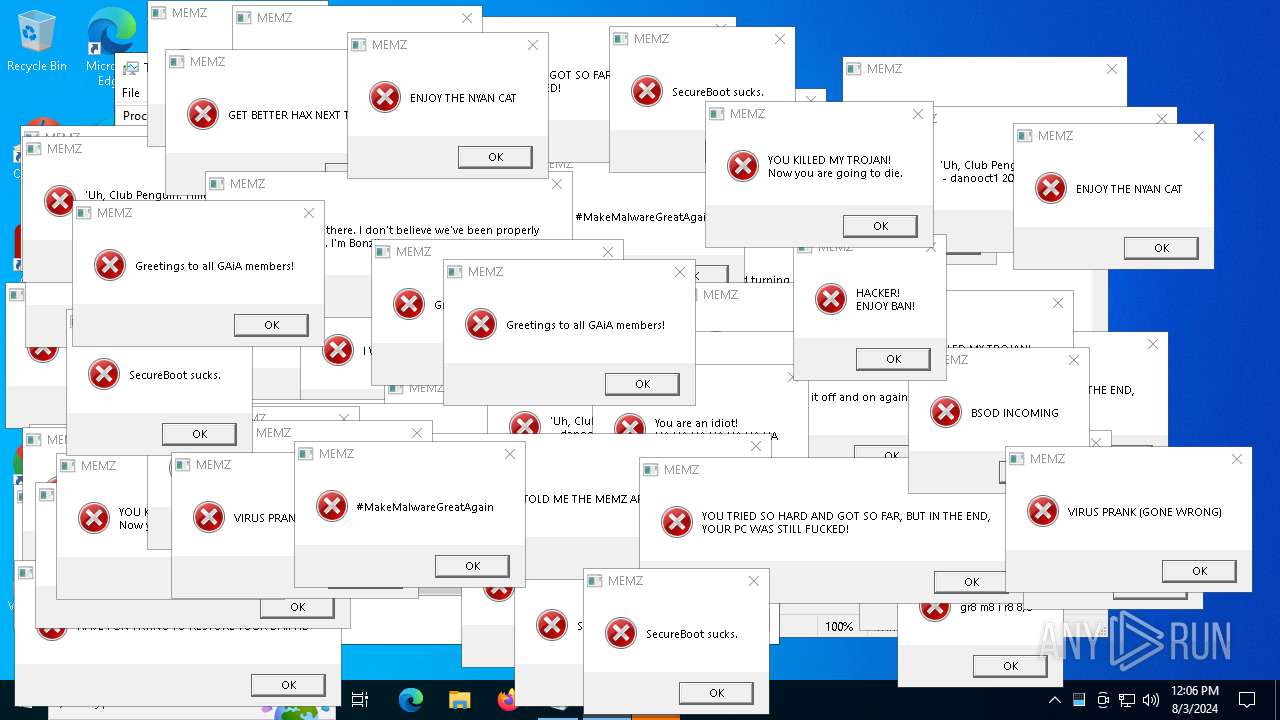
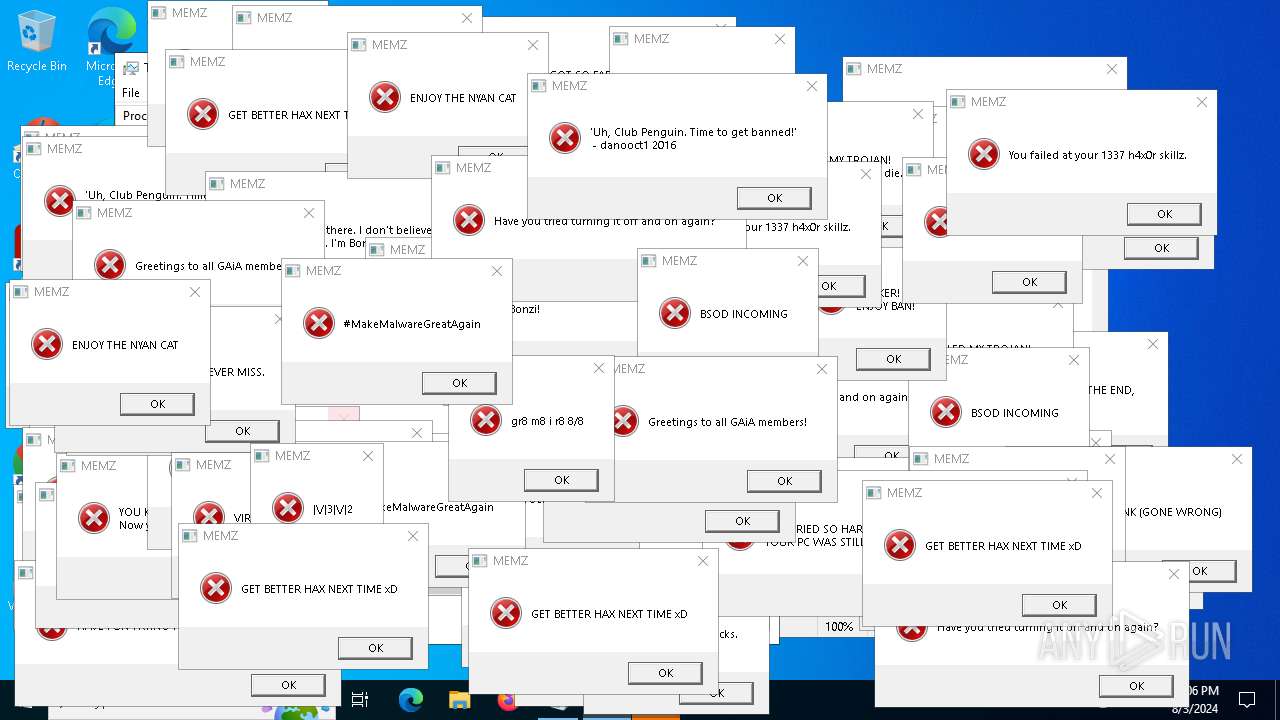
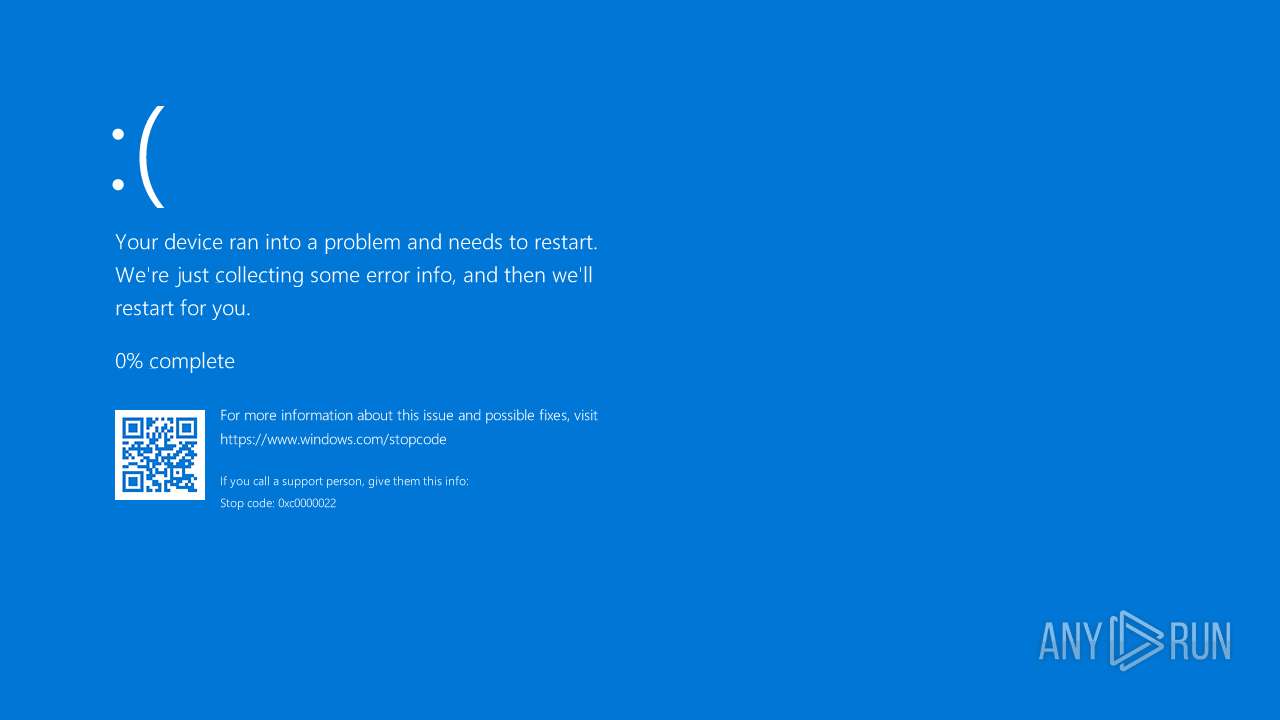
Start notepad (likely ransomware note)
- MEMZ.exe (PID: 4772)
INFO
Creates files or folders in the user directory
- cscript.exe (PID: 6380)
Reads security settings of Internet Explorer
- cscript.exe (PID: 6380)
- Taskmgr.exe (PID: 3136)
- notepad.exe (PID: 3812)
Drops the executable file immediately after the start
- cscript.exe (PID: 6380)
Reads the computer name
- MEMZ.exe (PID: 6536)
- MEMZ.exe (PID: 4772)
- MEMZ.exe (PID: 7148)
- MEMZ.exe (PID: 1140)
- MEMZ.exe (PID: 7128)
- MEMZ.exe (PID: 6204)
Checks supported languages
- MEMZ.exe (PID: 6536)
- MEMZ.exe (PID: 7128)
- MEMZ.exe (PID: 7148)
- MEMZ.exe (PID: 1140)
- MEMZ.exe (PID: 6208)
- MEMZ.exe (PID: 4772)
- MEMZ.exe (PID: 6204)
Process checks computer location settings
- MEMZ.exe (PID: 6536)
- MEMZ.exe (PID: 4772)
Reads the machine GUID from the registry
- MEMZ.exe (PID: 7128)
- MEMZ.exe (PID: 6204)
- MEMZ.exe (PID: 1140)
- MEMZ.exe (PID: 7148)
Manual execution by a user
- Taskmgr.exe (PID: 3068)
- Taskmgr.exe (PID: 3136)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
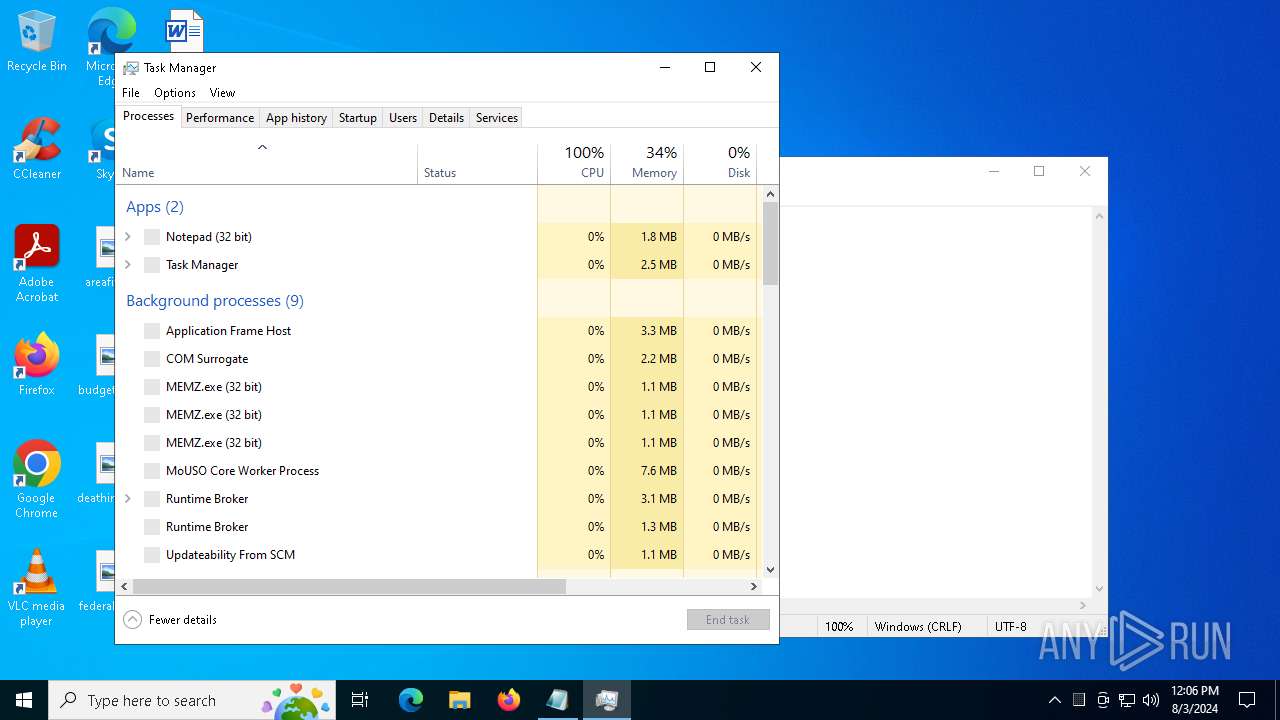
Total processes
134
Monitored processes
15
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1140 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 3068 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3136 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3812 | "C:\Windows\System32\notepad.exe" \note.txt | C:\Windows\SysWOW64\notepad.exe | — | MEMZ.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4772 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /main | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6204 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6208 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 6320 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\MEMZ.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6380 | cscript x.js | C:\Windows\System32\cscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
15 932
Read events
15 894
Write events
37
Delete events
1
Modification events
| (PID) Process: | (6380) cscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6380) cscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6380) cscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6380) cscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6380) cscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Discardable\PostSetup\Component Categories64\{56FFCC30-D398-11D0-B2AE-00A0C908FA49}\Enum |
| Operation: | write | Name: | Implementing |
Value: 1C00000001000000E8070800060003000C00050037001301010000001E768127E028094199FEB9D127C57AFE | |||
| (PID) Process: | (6380) cscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000C4A2517E9DE5DA01 | |||
| (PID) Process: | (6380) cscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Discardable\PostSetup\Component Categories64\{56FFCC30-D398-11D0-B2AE-00A0C908FA49}\Enum |
| Operation: | write | Name: | Implementing |
Value: 1C00000001000000E8070800060003000C00050037002301010000001E768127E028094199FEB9D127C57AFE | |||
| (PID) Process: | (6380) cscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\cscript.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: 7B600E0000000000 | |||
| (PID) Process: | (6320) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6320) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
1
Suspicious files
2
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4772 | MEMZ.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 6320 | cmd.exe | C:\Users\admin\Desktop\x.js | text | |
MD5:D94C93F882CF030ED9D66CC35796731D | SHA256:F7941E6BE49D757B46B9D6FB5ECB15392EC36A64E8906692D2EEB2BA9FC67CB6 | |||
| 6380 | cscript.exe | C:\Users\admin\AppData\Roaming\MEMZ.exe | executable | |
MD5:19DBEC50735B5F2A72D4199C4E184960 | SHA256:A3D5715A81F2FBEB5F76C88C9C21EEEE87142909716472F911FF6950C790C24D | |||
| 6320 | cmd.exe | C:\Users\admin\Desktop\x | text | |
MD5:CFC1E7E18B9F9B70310C88F922E59B29 | SHA256:3DCF309E134AE67CAED27FA52782267C90646B405C4A9594041B284733B8E346 | |||
| 6380 | cscript.exe | C:\Users\admin\Desktop\z.zip | compressed | |
MD5:63EE4412B95D7AD64C54B4BA673470A7 | SHA256:44C1857B1C4894B3DFBACCBE04905652E634283DCF6B06C25A74B17021E2A268 | |||
| 4772 | MEMZ.exe | C:\note.txt | binary | |
MD5:AFA6955439B8D516721231029FB9CA1B | SHA256:8E9F20F6864C66576536C0B866C6FFDCF11397DB67FE120E972E244C3C022270 | |||
| 3136 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
14
DNS requests
4
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3972 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5112 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4324 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |