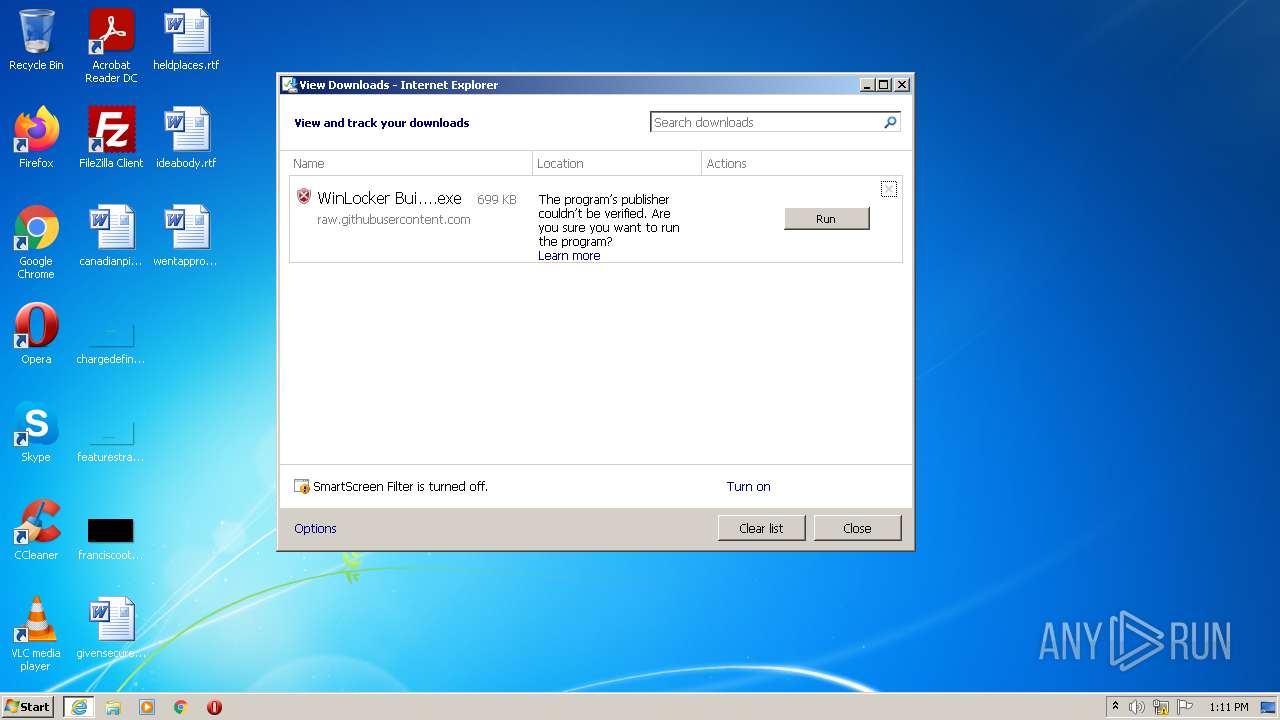
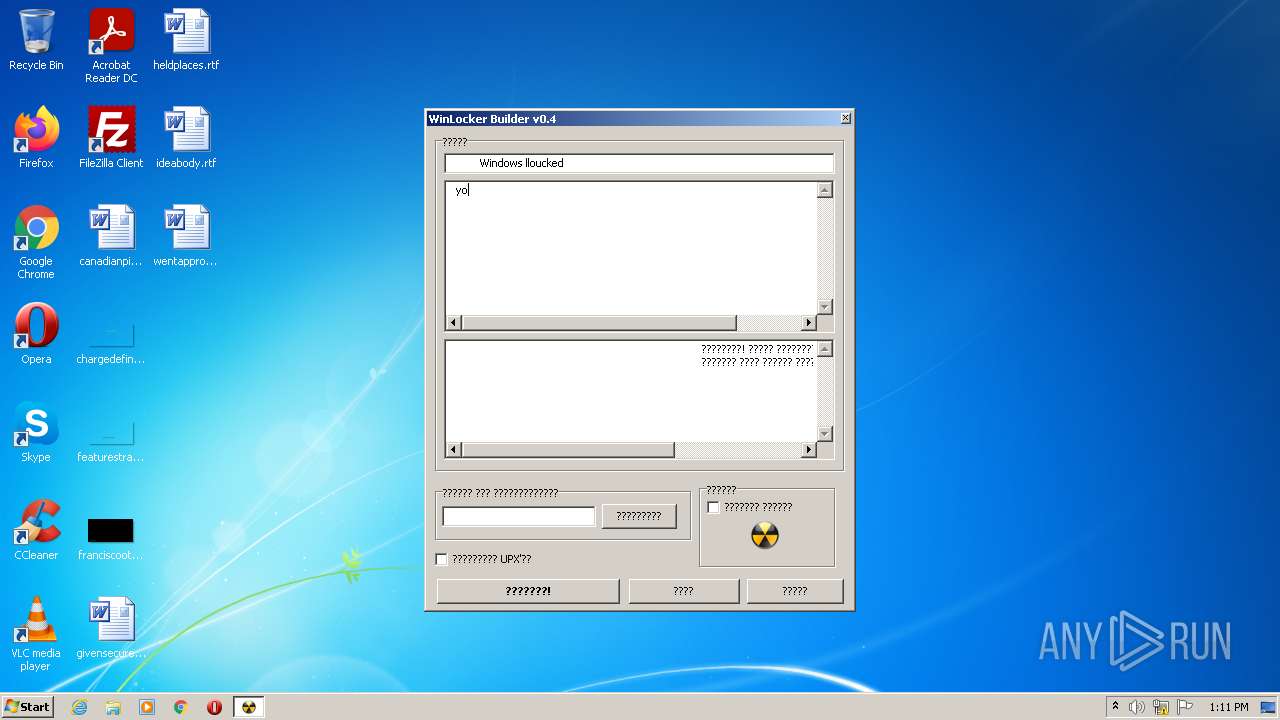
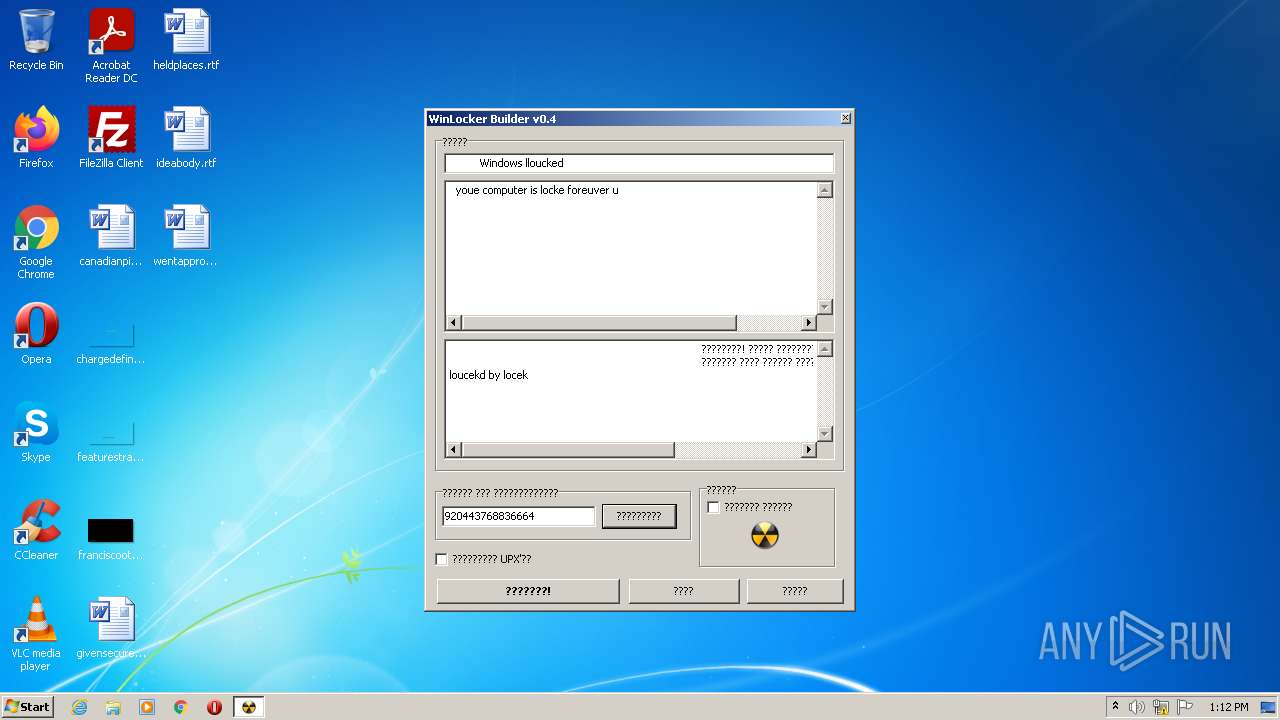
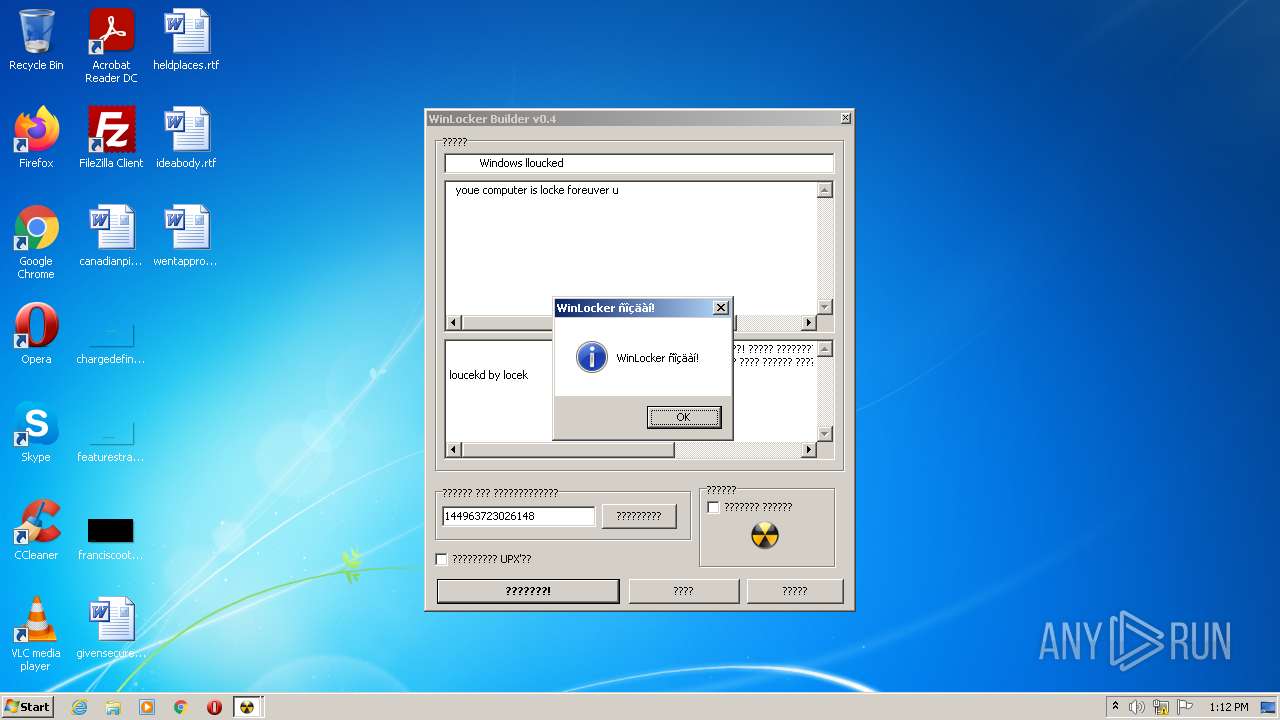
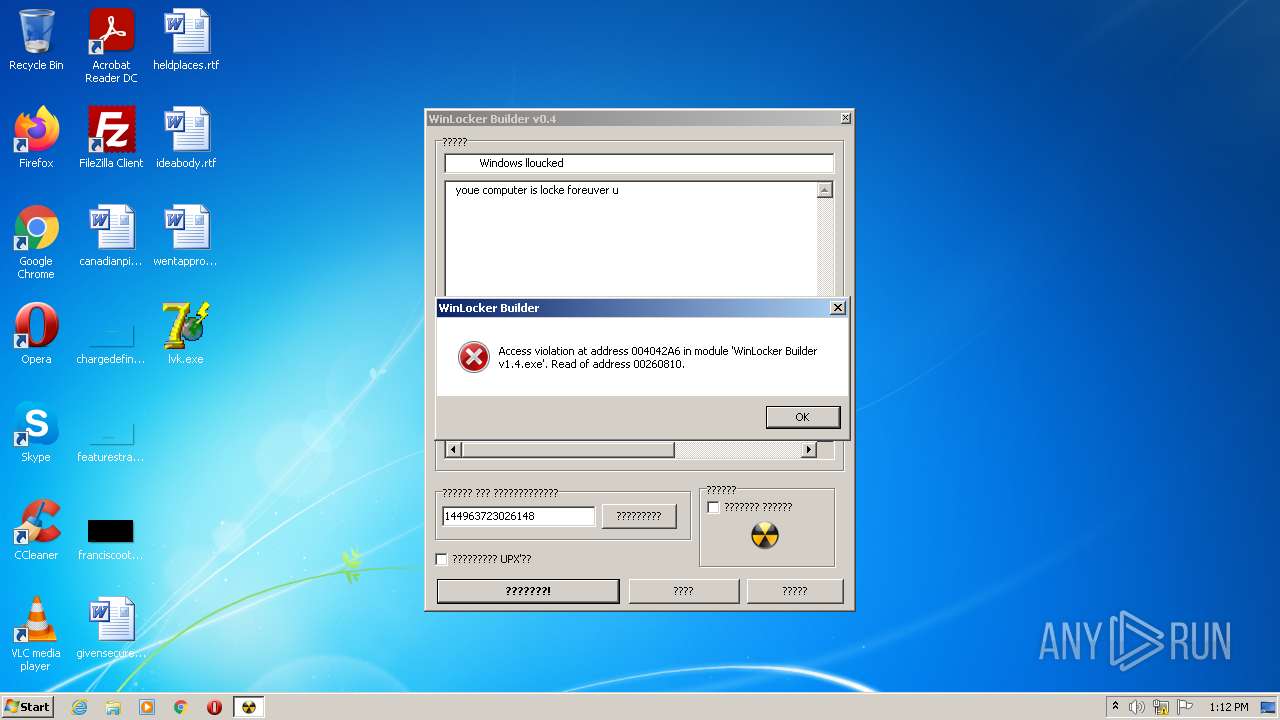
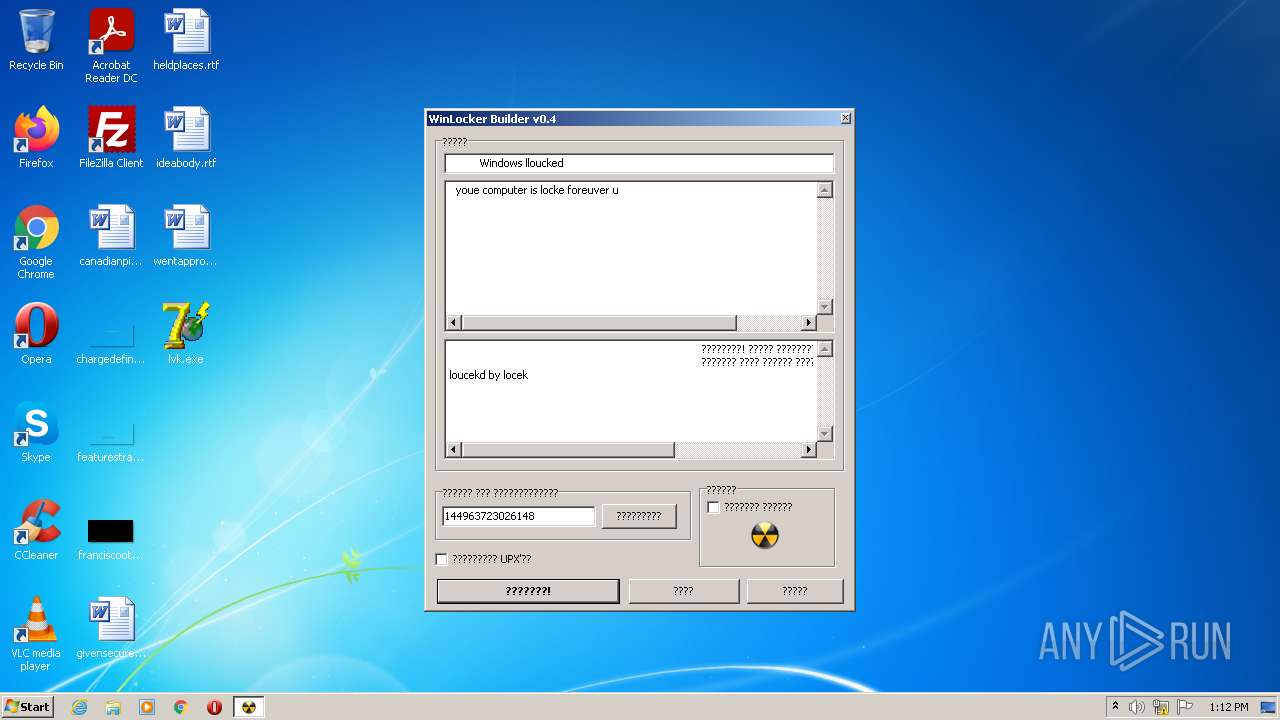
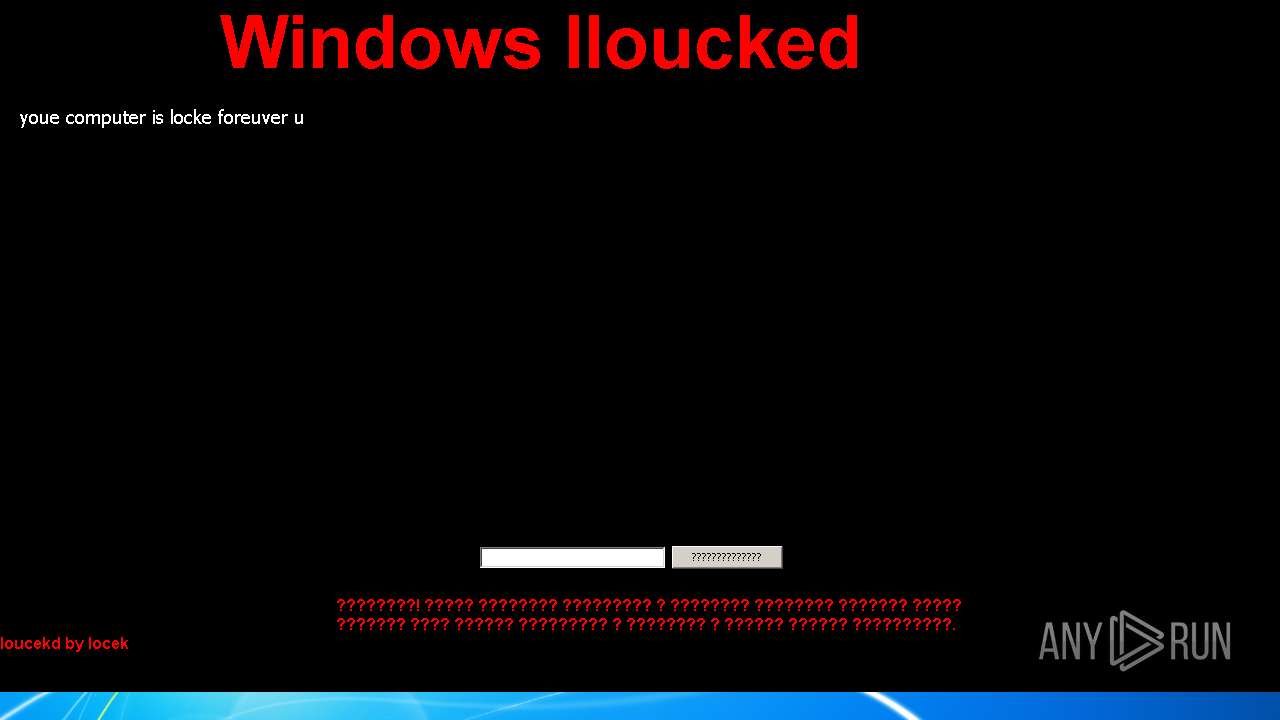
| URL: | https://github.com/dimavoronkov2/WinLocker-Builder-/raw/master/WinLocker%20Builder%20v1.4.exe |
| Full analysis: | https://app.any.run/tasks/8b234ada-8645-4372-b75d-44823fbe1534 |
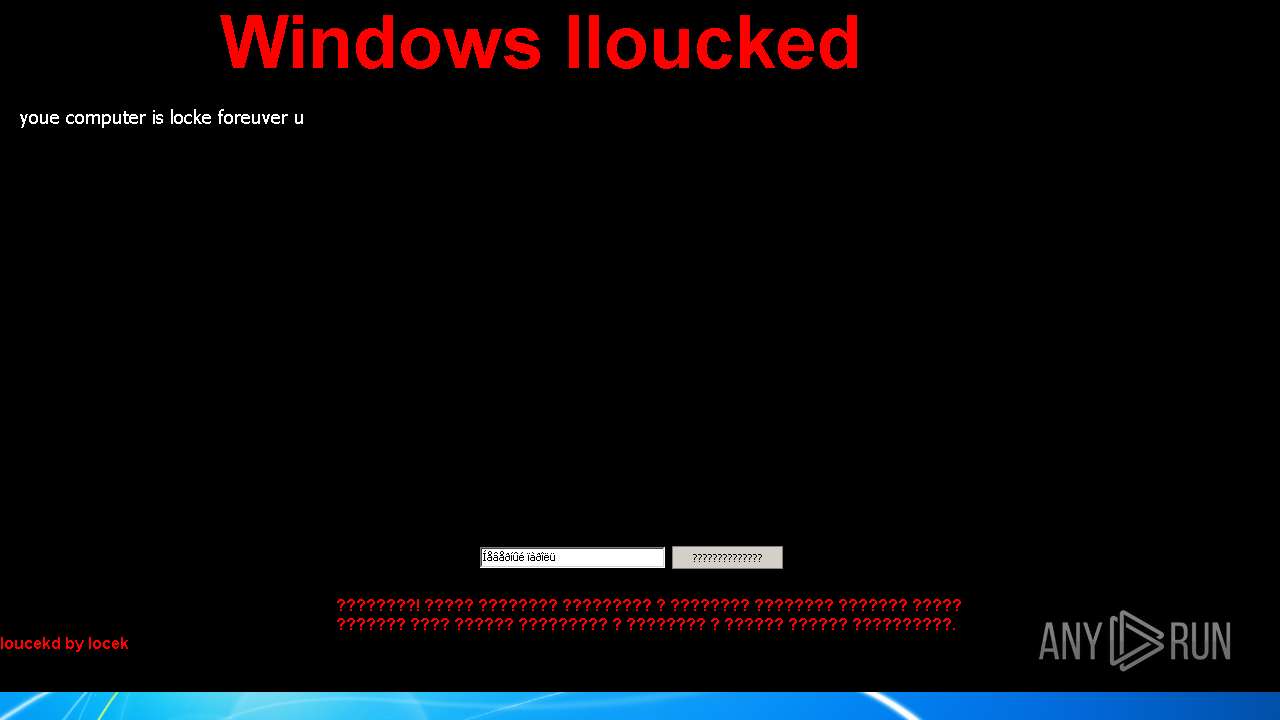
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2022, 12:11:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 5C9693C21C9769CAA71BC0BD2F975570 |
| SHA1: | 0D7928A06FBF9EC55778981A160E595FE7FBD5C8 |
| SHA256: | DADE5877FAF1318A92DECC4C761E15BD328D5D5CEDB7B03C374D45B72930899F |
| SSDEEP: | 3:N8tEdxMIaGkGPaZ4YMnldPGZPT6l0C:2uMd1GSaldeZP+mC |
MALICIOUS
Drops executable file immediately after starts
- iexplore.exe (PID: 1124)
- iexplore.exe (PID: 2684)
- WinLocker Builder v1.4.exe (PID: 3868)
Application was dropped or rewritten from another process
- WinLocker Builder v1.4.exe (PID: 3868)
- lvk.exe (PID: 2440)
Changes the autorun value in the registry
- lvk.exe (PID: 2440)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1124)
Executable content was dropped or overwritten
- iexplore.exe (PID: 1124)
- WinLocker Builder v1.4.exe (PID: 3868)
- iexplore.exe (PID: 2684)
Drops a file with a compile date too recent
- iexplore.exe (PID: 1124)
- iexplore.exe (PID: 2684)
- WinLocker Builder v1.4.exe (PID: 3868)
Checks supported languages
- WinLocker Builder v1.4.exe (PID: 3868)
- lvk.exe (PID: 2440)
Reads the computer name
- WinLocker Builder v1.4.exe (PID: 3868)
INFO
Checks supported languages
- iexplore.exe (PID: 2684)
- iexplore.exe (PID: 1124)
Reads the computer name
- iexplore.exe (PID: 2684)
- iexplore.exe (PID: 1124)
Application launched itself
- iexplore.exe (PID: 2684)
Checks Windows Trust Settings
- iexplore.exe (PID: 1124)
- iexplore.exe (PID: 2684)
Changes internet zones settings
- iexplore.exe (PID: 2684)
Reads the date of Windows installation
- iexplore.exe (PID: 2684)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2684)
Manual execution by user
- lvk.exe (PID: 2440)
Reads settings of System Certificates
- iexplore.exe (PID: 1124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
4
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1124 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2684 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2440 | "C:\Users\admin\Desktop\lvk.exe" | C:\Users\admin\Desktop\lvk.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2684 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://github.com/dimavoronkov2/WinLocker-Builder-/raw/master/WinLocker%20Builder%20v1.4.exe" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3868 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\WinLocker Builder v1.4.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\WinLocker Builder v1.4.exe | iexplore.exe | ||||||||||||
User: admin Company: VAN32 Integrity Level: MEDIUM Description: WinLocker Builder Exit code: 0 Version: 0.4.0.0 Modules
| |||||||||||||||
Total events
7 855
Read events
7 731
Write events
122
Delete events
2
Modification events
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30955677 | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30955677 | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
12
Suspicious files
7
Text files
1
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | binary | |
MD5:— | SHA256:— | |||
| 1124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\50CD3D75D026C82E2E718570BD6F44D0_60E83F2095C16CA099C94596E7B8AA5D | der | |
MD5:— | SHA256:— | |||
| 1124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\50CD3D75D026C82E2E718570BD6F44D0_60E83F2095C16CA099C94596E7B8AA5D | binary | |
MD5:— | SHA256:— | |||
| 1124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:— | SHA256:— | |||
| 1124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | der | |
MD5:— | SHA256:— | |||
| 3868 | WinLocker Builder v1.4.exe | C:\Users\admin\Desktop\RCX52C0.tmp | executable | |
MD5:— | SHA256:— | |||
| 3868 | WinLocker Builder v1.4.exe | C:\Users\admin\Desktop\RCX52E2.tmp | executable | |
MD5:— | SHA256:— | |||
| 3868 | WinLocker Builder v1.4.exe | C:\Users\admin\Desktop\RCX52D1.tmp | executable | |
MD5:— | SHA256:— | |||
| 1124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
7
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1124 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | US | der | 471 b | whitelisted |
1124 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | US | der | 471 b | whitelisted |
1124 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrHR6YzPN2BNbByL0VoiTIBBMAOAQUCrwIKReMpTlteg7OM8cus%2B37w3oCEAUYmlTr6MfpA%2BCrDZJVRd4%3D | US | der | 314 b | whitelisted |
1124 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e21d93dc37a0b040 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1124 | iexplore.exe | 185.199.111.133:443 | raw.githubusercontent.com | GitHub, Inc. | NL | suspicious |
1124 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1124 | iexplore.exe | 140.82.121.3:443 | github.com | — | US | suspicious |
1124 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
raw.githubusercontent.com |
| shared |