| File name: | 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe |
| Full analysis: | https://app.any.run/tasks/0553feab-988b-4974-ac53-1b3f8e6be418 |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | July 09, 2025, 21:39:44 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 7 sections |
| MD5: | 79CF045349A688D3F29F85213B2B58E6 |
| SHA1: | 9C9E04E3CCAECF8F8B39061E05D4054BEC92E19D |
| SHA256: | DACED881BD18F3266A66044EE7B3737127A188C7DCAB9FC9F12561699360A4A1 |
| SSDEEP: | 98304:rSQe+3v3odTWAUMcYtyLI+kBxK/WyZE7eqcVqJjZs4COzpL2T6Ob4+fX1NTQYBU8:a15Djp7J7Uqdd6F |
MALICIOUS
Changes powershell execution policy (Bypass)
- msiexec.exe (PID: 5920)
Bypass execution policy to execute commands
- powershell.exe (PID: 1976)
Downloads files via BITSADMIN.EXE
- powershell.exe (PID: 1976)
Executing a file with an untrusted certificate
- smss.exe (PID: 5008)
- smss.exe (PID: 6016)
AUROTUN mutex has been found
- smss.exe (PID: 6016)
SUSPICIOUS
ADVANCEDINSTALLER mutex has been found
- 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe (PID: 4760)
Reads the Windows owner or organization settings
- 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe (PID: 4760)
- ssdfreshsetup.tmp (PID: 2692)
- msiexec.exe (PID: 6412)
Reads security settings of Internet Explorer
- 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe (PID: 4760)
- SSDFresh.exe (PID: 6124)
Process drops legitimate windows executable
- 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe (PID: 4760)
- ssdfreshsetup.tmp (PID: 2692)
Executable content was dropped or overwritten
- ssdfreshsetup.exe (PID: 640)
- 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe (PID: 4760)
- ssdfreshsetup.tmp (PID: 2692)
- powershell.exe (PID: 1976)
Detects AdvancedInstaller (YARA)
- 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe (PID: 4760)
- msiexec.exe (PID: 5920)
There is functionality for taking screenshot (YARA)
- 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe (PID: 4760)
Adds/modifies Windows certificates
- SSDFresh.exe (PID: 6124)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 5920)
The process executes Powershell scripts
- msiexec.exe (PID: 5920)
The process hide an interactive prompt from the user
- msiexec.exe (PID: 5920)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 5920)
The process executes via Task Scheduler
- explorer.exe (PID: 4888)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 1976)
Application launched itself
- smss.exe (PID: 5008)
Connects to unusual port
- smss.exe (PID: 6016)
INFO
Checks supported languages
- 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe (PID: 4760)
- msiexec.exe (PID: 6412)
- msiexec.exe (PID: 6700)
- ssdfreshsetup.exe (PID: 640)
- ssdfreshsetup.tmp (PID: 2692)
- closeapp.exe (PID: 2804)
- _setup64.tmp (PID: 5352)
- SSDFresh.exe (PID: 6124)
- msiexec.exe (PID: 6812)
- msiexec.exe (PID: 856)
- msiexec.exe (PID: 5920)
- smss.exe (PID: 5008)
- smss.exe (PID: 6016)
The sample compiled with english language support
- 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe (PID: 4760)
- msiexec.exe (PID: 6412)
- powershell.exe (PID: 1976)
Reads the computer name
- 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe (PID: 4760)
- msiexec.exe (PID: 6412)
- msiexec.exe (PID: 6700)
- SSDFresh.exe (PID: 6124)
- ssdfreshsetup.tmp (PID: 2692)
- msiexec.exe (PID: 6812)
- msiexec.exe (PID: 856)
- msiexec.exe (PID: 5920)
- smss.exe (PID: 6016)
Create files in a temporary directory
- 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe (PID: 4760)
- ssdfreshsetup.exe (PID: 640)
- ssdfreshsetup.tmp (PID: 2692)
- SSDFresh.exe (PID: 6124)
- powershell.exe (PID: 1976)
Reads Environment values
- 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe (PID: 4760)
- msiexec.exe (PID: 6700)
- SSDFresh.exe (PID: 6124)
- msiexec.exe (PID: 5920)
- msiexec.exe (PID: 6812)
Process checks computer location settings
- 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe (PID: 4760)
- smss.exe (PID: 6016)
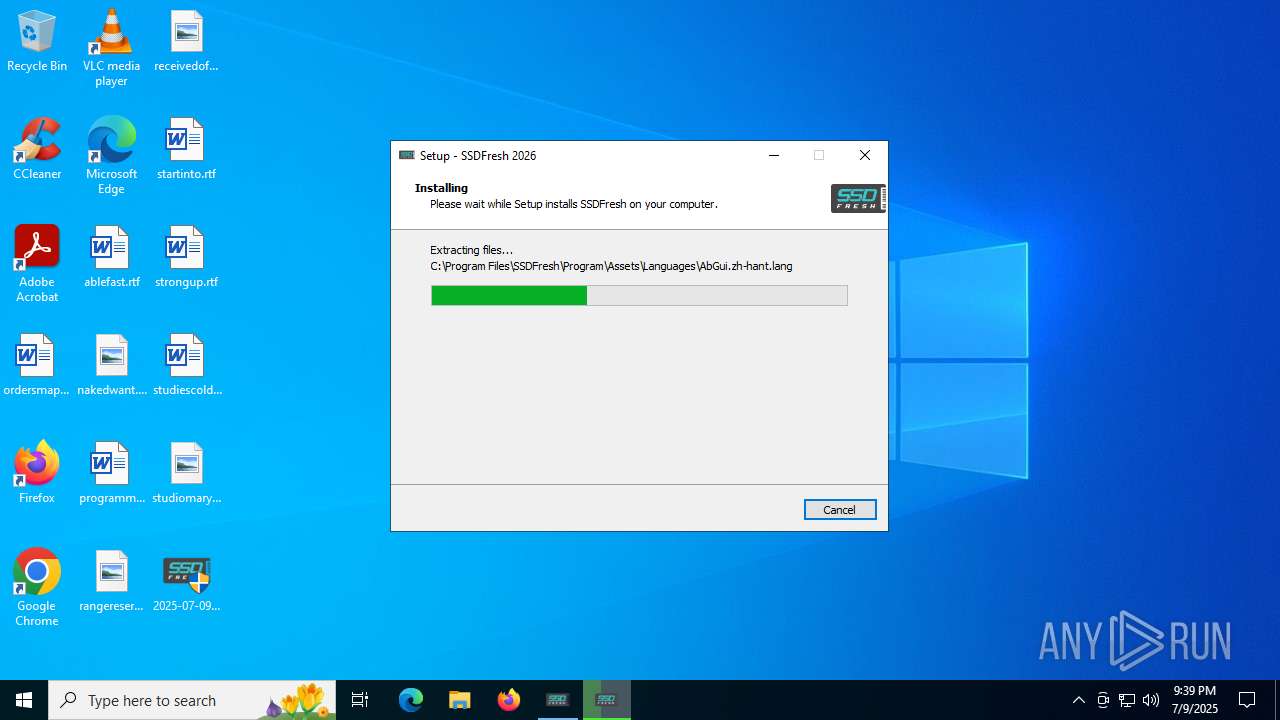
Creates files in the program directory
- ssdfreshsetup.tmp (PID: 2692)
- SSDFresh.exe (PID: 6124)
Creates a software uninstall entry
- ssdfreshsetup.tmp (PID: 2692)
Reads the machine GUID from the registry
- SSDFresh.exe (PID: 6124)
- smss.exe (PID: 6016)
Reads the software policy settings
- SSDFresh.exe (PID: 6124)
- powershell.exe (PID: 1976)
- slui.exe (PID: 6940)
Compiled with Borland Delphi (YARA)
- ssdfreshsetup.exe (PID: 640)
- ssdfreshsetup.tmp (PID: 2692)
Detects InnoSetup installer (YARA)
- ssdfreshsetup.tmp (PID: 2692)
- ssdfreshsetup.exe (PID: 640)
Disables trace logs
- SSDFresh.exe (PID: 6124)
- powershell.exe (PID: 1976)
Checks if a key exists in the options dictionary (POWERSHELL)
- SSDFresh.exe (PID: 6124)
- powershell.exe (PID: 1976)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6412)
Creates files or folders in the user directory
- SSDFresh.exe (PID: 6124)
Checks proxy server information
- SSDFresh.exe (PID: 6124)
- slui.exe (PID: 6940)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 1976)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 1976)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5712)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 1976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:03:03 13:51:40+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.43 |
| CodeSize: | 2920960 |
| InitializedDataSize: | 1262080 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2351b0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | GetintoWAY |
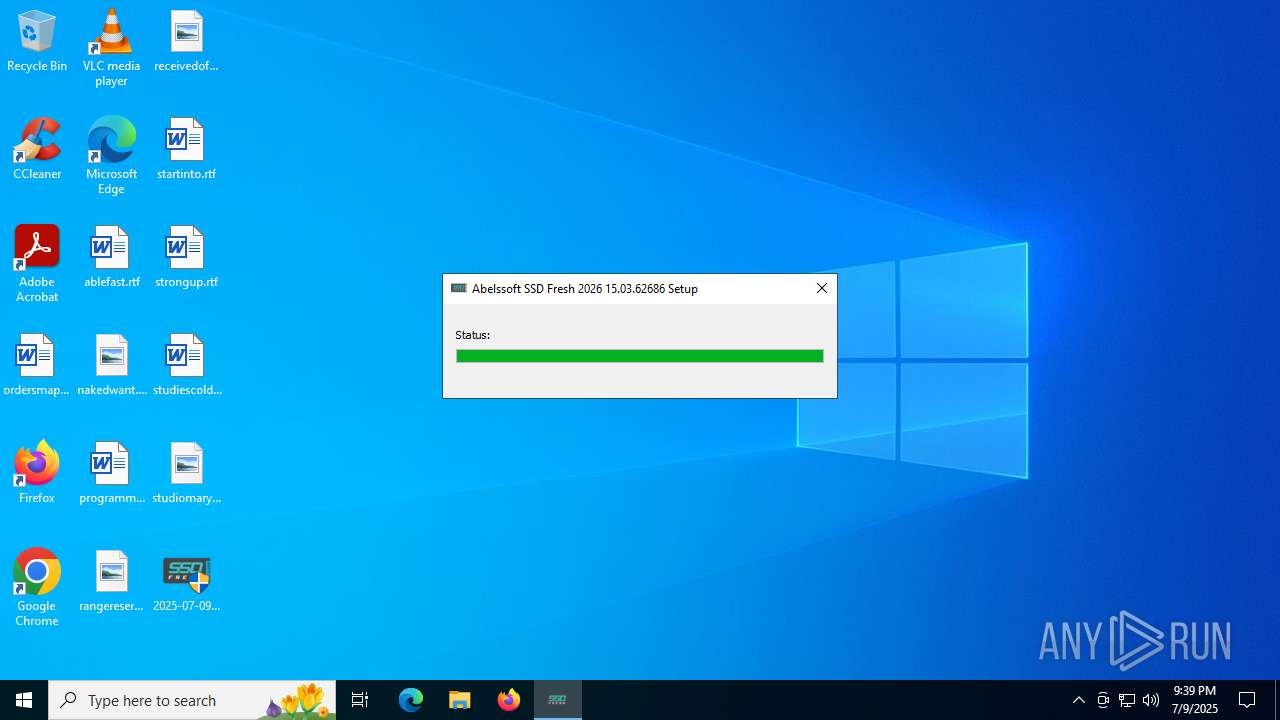
| FileDescription: | Abelssoft SSD Fresh 2026 15.03.62686 Installer |
| FileVersion: | 0.0.0.0 |
| InternalName: | Abelssoft SSD Fresh 2026 15.03.62686 |
| LegalCopyright: | Copyright (C) 2025 GetintoWAY |
| OriginalFileName: | Abelssoft SSD Fresh 2026 15.03.62686.exe |
| ProductName: | Abelssoft SSD Fresh 2026 15.03.62686 |
| ProductVersion: | 0.0.0.0 |
Total processes
161
Monitored processes
23
Malicious processes
6
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 640 | "C:\Users\admin\AppData\Local\Temp\SSDFresh\ssdfreshsetup.exe" /silent | C:\Users\admin\AppData\Local\Temp\SSDFresh\ssdfreshsetup.exe | — | 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe | |||||||||||
User: admin Company: Abelssoft Integrity Level: HIGH Description: SSDFresh 2026 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 856 | C:\Windows\syswow64\MsiExec.exe -Embedding 9D9F50D192E8A22053B42FACB7A80AC6 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1036 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | _setup64.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1632 | "C:\WINDOWS\system32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\38A78BD\Abelssoft SSD Fresh.msi" /qn AI_SETUPEXEPATH=C:\Users\admin\Desktop\2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe SETUPEXEDIR=C:\Users\admin\Desktop\ EXE_CMD_LINE="/exenoupdates /forcecleanup /wintime 1752095663 " ALLUSERS="1" AI_EUIMSI="" AI_MISSING_PREREQS="SSDFresh" | C:\Windows\SysWOW64\msiexec.exe | — | 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1976 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\WINDOWS\SystemTemp\pssCE20.ps1" -propFile "C:\WINDOWS\SystemTemp\msiCE1D.txt" -scriptFile "C:\WINDOWS\SystemTemp\scrCE1E.ps1" -scriptArgsFile "C:\WINDOWS\SystemTemp\scrCE1F.txt" -propSep " :<->: " -lineSep " <<:>> " -testPrefix "_testValue." | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2692 | "C:\Users\admin\AppData\Local\Temp\is-DGE0A.tmp\ssdfreshsetup.tmp" /SL5="$B02E4,5710843,886784,C:\Users\admin\AppData\Local\Temp\SSDFresh\ssdfreshsetup.exe" /silent | C:\Users\admin\AppData\Local\Temp\is-DGE0A.tmp\ssdfreshsetup.tmp | — | ssdfreshsetup.exe | |||||||||||
User: admin Company: Abelssoft Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2804 | "C:\Users\admin\AppData\Local\Temp\is-OOP89.tmp\closeapp.exe" SSDFresh | C:\Users\admin\AppData\Local\Temp\is-OOP89.tmp\closeapp.exe | — | ssdfreshsetup.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2808 | "C:\Users\admin\Desktop\2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe" | C:\Users\admin\Desktop\2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe | — | explorer.exe | |||||||||||
User: admin Company: GetintoWAY Integrity Level: MEDIUM Description: Abelssoft SSD Fresh 2026 15.03.62686 Installer Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
21 882
Read events
21 755
Write events
106
Delete events
21
Modification events
| (PID) Process: | (2692) ssdfreshsetup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Fonts |
| Operation: | write | Name: | Segoe WP Light (TrueType) |
Value: SegoeWP-Light_0.ttf | |||
| (PID) Process: | (2692) ssdfreshsetup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Fonts |
| Operation: | write | Name: | Segoe WP (TrueType) |
Value: SegoeWP_0.ttf | |||
| (PID) Process: | (2692) ssdfreshsetup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Fonts |
| Operation: | write | Name: | Segoe WP Black (TrueType) |
Value: SegoeWP-Black_0.ttf | |||
| (PID) Process: | (2692) ssdfreshsetup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Fonts |
| Operation: | write | Name: | Segoe WP (TrueType) |
Value: SegoeWP-Bold_0.ttf | |||
| (PID) Process: | (2692) ssdfreshsetup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Fonts |
| Operation: | write | Name: | Segoe WP SemiLight (TrueType) |
Value: SegoeWP-Semilight_0.ttf | |||
| (PID) Process: | (2692) ssdfreshsetup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Fonts |
| Operation: | write | Name: | Poppins Bold (TrueType) |
Value: Poppins-Bold.ttf | |||
| (PID) Process: | (2692) ssdfreshsetup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Fonts |
| Operation: | write | Name: | Poppins Medium (TrueType) |
Value: Poppins-Medium.ttf | |||
| (PID) Process: | (2692) ssdfreshsetup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Fonts |
| Operation: | write | Name: | Segoe WP Semibold (TrueType) |
Value: SegoeWP-Semibold_0.ttf | |||
| (PID) Process: | (2692) ssdfreshsetup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Fonts |
| Operation: | write | Name: | Poppins (TrueType) |
Value: Poppins-Regular.ttf | |||
| (PID) Process: | (2692) ssdfreshsetup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Fonts |
| Operation: | write | Name: | Poppins Light (TrueType) |
Value: Poppins-Light.ttf | |||
Executable files
143
Suspicious files
16
Text files
600
Unknown types
35
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4760 | 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe | C:\Users\admin\AppData\Local\Temp\38A78BD\Abelssoft SSD Fresh.msi | — | |
MD5:— | SHA256:— | |||
| 4760 | 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_4760\repairic | image | |
MD5:915E40A576FA41DC5F8486103341673E | SHA256:BF21B2BC3E7253968405F3D244CDB1C136672A5BDB088B524A333264898A2D11 | |||
| 4760 | 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe | C:\Users\admin\AppData\Local\Temp\shi61A8.tmp | executable | |
MD5:84A34BF3486F7B9B7035DB78D78BDD1E | SHA256:F85911C910B660E528D2CF291BAA40A92D09961996D6D84E7A53A7095C7CD96E | |||
| 4760 | 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_4760\custicon | image | |
MD5:BE6D2F48AA6634FB2101C273C798D4D9 | SHA256:0E22BC2BF7184DFDB55223A11439304A453FB3574E3C9034A6497AF405C628EF | |||
| 4760 | 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_4760\tabback | image | |
MD5:4C3DDA35E23D44E273D82F7F4C38470A | SHA256:E728F79439E07DF1AFBCF03E8788FA0B8B08CF459DB31FC8568BC511BF799537 | |||
| 4760 | 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe | C:\Users\admin\AppData\Local\Temp\MSI62D3.tmp | executable | |
MD5:2330EBBE491C6026AF5E8853F3692798 | SHA256:3ADA2257732FAE73114BB6A5E082CEF4BD72C3D6842924BE6F22728C7D7CACC4 | |||
| 4760 | 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe | C:\Users\admin\AppData\Local\Temp\MSI6342.tmp | executable | |
MD5:C9EF0378879C57A38C075BB28B88FCAB | SHA256:6E7CDAB18E1F705C0EA56A565577DB0389ECE2B5A4E0F31D3063E9103F59FBEE | |||
| 4760 | 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe | C:\Users\admin\AppData\Local\Temp\MSI6322.tmp | executable | |
MD5:2330EBBE491C6026AF5E8853F3692798 | SHA256:3ADA2257732FAE73114BB6A5E082CEF4BD72C3D6842924BE6F22728C7D7CACC4 | |||
| 4760 | 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_4760\completi | image | |
MD5:C23AF89757665BC0386FD798A61B2112 | SHA256:031ED0378F819926D7B5B2C6C9367A0FB1CBAE40E1A3959E2652FE30A47D52F2 | |||
| 4760 | 2025-07-09_79cf045349a688d3f29f85213b2b58e6_amadey_black-basta_darkgate_elex_luca-stealer.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_4760\dialog.jpg | image | |
MD5:5F6253CFF5A8B031BFB3B161079D0D86 | SHA256:36D9BAB35D1E4B50045BF902F5D42B6F865488C75F6E60FC00A6CD6F69034AB0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
49
TCP/UDP connections
31
DNS requests
14
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7004 | RUXIMICS.exe | GET | 200 | 23.48.23.148:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.148:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.148:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7004 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6124 | SSDFresh.exe | GET | 200 | 151.101.130.133:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDBRxX685PnItGaRPmg%3D%3D | unknown | — | — | whitelisted |
6124 | SSDFresh.exe | GET | 200 | 151.101.130.133:80 | http://ocsp.globalsign.com/rootr3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEHgDGEJFcIpBz28BuO60qVQ%3D | unknown | — | — | whitelisted |
6124 | SSDFresh.exe | GET | 200 | 151.101.130.133:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgW3WQu2HUdhUx4%2Fde0%3D | unknown | — | — | whitelisted |
— | — | HEAD | 301 | 185.208.156.66:443 | https://lofhr.com/windows11.25-kb4090007-x64_7063a0b6a38e2a648aa1d77570503f7062360c9d.zip | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7004 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.48.23.148:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.48.23.148:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
7004 | RUXIMICS.exe | 23.48.23.148:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
datahub.ascora.de |
| unknown |
lofhr.com |
| unknown |
loadingfreelofhr.net |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1976 | powershell.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 36 |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
2200 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected Domain Associated with Malware Distribution (loadingfreelofhr .net) |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
Process | Message |
|---|---|
SSDFresh.exe | Log4Net: 2025-07-09 21:40:16,636 [INFO ] [Thread: 1] (AbDefault.AbstractApplication.InitializeLogger) - Logged-In User: DESKTOP-JGLLJLD\admin
|
SSDFresh.exe | Log4Net: 2025-07-09 21:40:16,699 [INFO ] [Thread: 1] (AbDefault.AbstractApplication.InitializeLogger) - Context-User: DESKTOP-JGLLJLD\admin
|
SSDFresh.exe | Log4Net: 2025-07-09 21:40:16,699 [INFO ] [Thread: 1] (AbDefault.AbstractApplication.InitializeLogger) - Environment.Is64BitOperatingSystem: True
|
SSDFresh.exe | Log4Net: 2025-07-09 21:40:16,699 [INFO ] [Thread: 1] (AbDefault.AbstractApplication.InitializeLogger) - Environment.Is64BitProcess: True
|
SSDFresh.exe | Log4Net: 2025-07-09 21:40:16,699 [INFO ] [Thread: 1] (AbDefault.AbstractApplication.InitializeLogger) - .NET Runtime: 4.0.30319.42000
|
SSDFresh.exe | Log4Net: 2025-07-09 21:40:16,730 [INFO ] [Thread: 1] (AbDefault.AbstractApplication.InitializeLogger) - OS: Microsoft Windows 10 Pro, 64-bit, Version 10.0.19045, Build 19045
|
SSDFresh.exe | Log4Net: 2025-07-09 21:40:16,730 [INFO ] [Thread: 1] (AbDefault.AbstractApplication.InitializeLogger) - AbCore-Version: 12.10
|
SSDFresh.exe | Log4Net: 2025-07-09 21:40:16,730 [INFO ] [Thread: 1] (AbDefault.AbstractApplication.InitializeLogger) - AppInformation.Features.LiteRegistration: True
|
SSDFresh.exe | Log4Net: 2025-07-09 21:40:16,730 [INFO ] [Thread: 1] (AbDefault.AbstractApplication.InitializeLogger) - AppInformation.Features.TipScreen: True
|
SSDFresh.exe | Log4Net: 2025-07-09 21:40:16,730 [INFO ] [Thread: 1] (AbDefault.AbstractApplication.InitializeLogger) - AppInformation.Features.Advertisements: True
|