| URL: | https://jsjcorporation-my.sharepoint.com/:o:/g/personal/gillesm_jsjcorp_com/El3LMnws4WZAn7a-DWcgo-oBQOivV1QSdopp5DSJ_EMPKQ?e=13FjPv |
| Full analysis: | https://app.any.run/tasks/45bc144a-7b47-4a53-a153-d8f36129bd40 |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 06:15:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 22A7F6B7F82DB4C6FBA91C37D639CC2D |
| SHA1: | C52A805E195DD2B766F9F0A625FE6B9F53D3E747 |
| SHA256: | DAC827E4401DAEB8865F53BF41C2B12F50EFC654BF22B506E012D3E6D3DD7EDE |
| SSDEEP: | 3:N8oXS88hiN+ArL5+KVFSCIOtTKI3mREcoKIK0qS4028VVQhf5w:2Kqhu+AfNQOtTKIC3oTlj402EVQh+ |
MALICIOUS
No malicious indicators.SUSPICIOUS
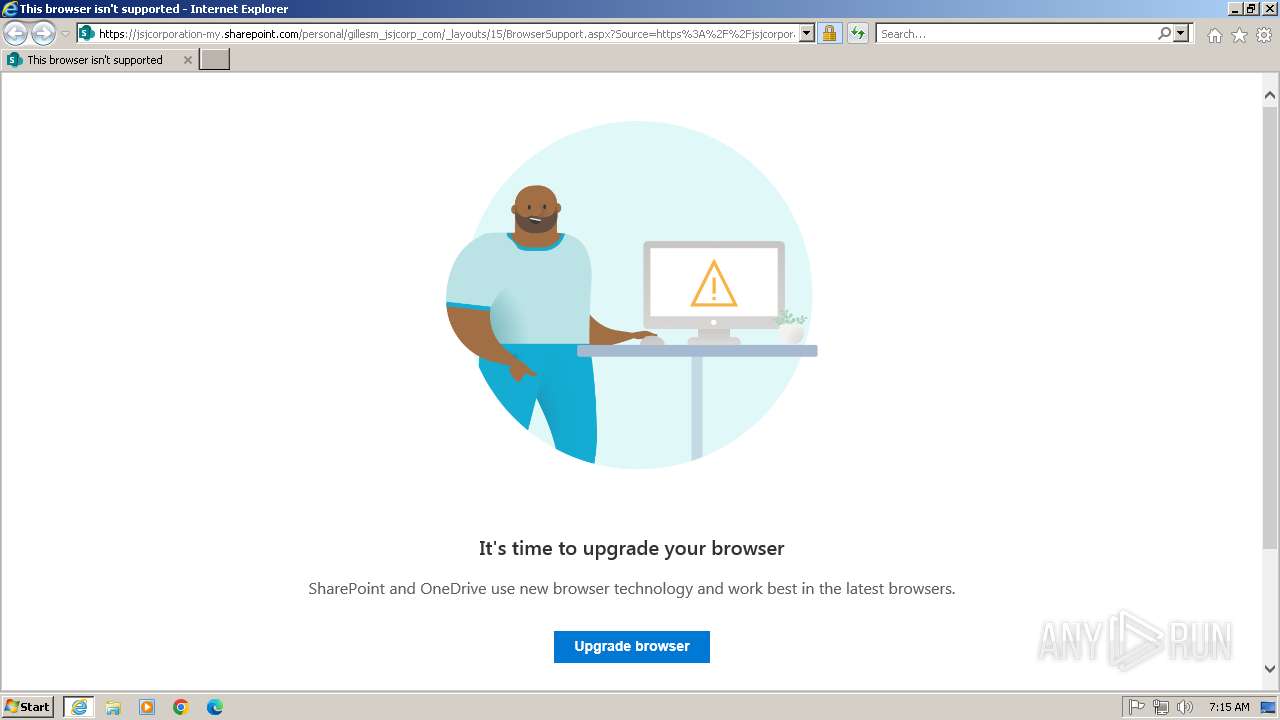
Access to SharePoint Content
- iexplore.exe (PID: 2812)
INFO
Application launched itself
- iexplore.exe (PID: 2812)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
35
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2236 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2812 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2812 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://jsjcorporation-my.sharepoint.com/:o:/g/personal/gillesm_jsjcorp_com/El3LMnws4WZAn7a-DWcgo-oBQOivV1QSdopp5DSJ_EMPKQ?e=13FjPv" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
16 079
Read events
15 990
Write events
71
Delete events
18
Modification events
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 553175824 | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31180531 | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 853495824 | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31180531 | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
7
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2236 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:AC56D37C7440D6E737A5F027B62099BE | SHA256:1602143F70673B2FB6E462D0163BA0D229103BB83C14C0EF44039FC1D57A7B24 | |||
| 2236 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:14FE013C670414DA5199B6DEADD8EE32 | SHA256:2D44053D2FBC058A80311CBF5AA368751F2D181EFF3EF22579B17BC5E2288388 | |||
| 2812 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 2812 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[2].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 2236 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:C60A64AC7776C5920251EA07CA98BA79 | SHA256:47272D84FDC453ECBB24C4D3988576AEC2BDA07E5DA7EA06DABF1386D110566F | |||
| 2236 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:77B20B5CD41BC6BB475CCA3F91AE6E3C | SHA256:5511A9B9F9144ED7BDE4CCB074733B7C564D918D2A8B10D391AFC6BE5B3B1509 | |||
| 2812 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 2812 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:18DB09149D7D016F3F631EAC9E6BF96A | SHA256:6B4E4390B8C9F324BAFB8834DC66E65496857A96D6EBBDF001D010080F96A52A | |||
| 2236 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\browserSupport[1].png | image | |
MD5:570379A3467DCE7026C15EB5B31549CF | SHA256:4B23ACF59874511EC32212CFC2CC59FF7216DDCA8B5FFC111E8DABB927D82214 | |||
| 2812 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\imagestore\f7ruq93\imagestore.dat | binary | |
MD5:9B87004A4107BFC615E2A6F05C0B9255 | SHA256:ED17BF17690490E8E9E5764982F064822204DD568DC2561685F4D0C4D09A4C71 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
16
DNS requests
10
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2236 | iexplore.exe | GET | 200 | 88.221.110.91:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?2c1c1224967e261d | unknown | — | — | whitelisted |
2236 | iexplore.exe | GET | 200 | 88.221.110.91:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7c6ee2c51c37faea | unknown | — | — | whitelisted |
2236 | iexplore.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
2812 | iexplore.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2236 | iexplore.exe | 13.107.136.10:443 | jsjcorporation-my.sharepoint.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2236 | iexplore.exe | 88.221.110.91:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2236 | iexplore.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2812 | iexplore.exe | 104.126.37.163:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
2812 | iexplore.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2812 | iexplore.exe | 13.107.136.10:443 | jsjcorporation-my.sharepoint.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
jsjcorporation-my.sharepoint.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to SharePoint public/private file sharing DNS (.sharepoint .com) |
2236 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to SharePoint public/private file sharing TLS SNI (.sharepoint .com) |
2236 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to SharePoint public/private file sharing TLS SNI (.sharepoint .com) |
2812 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to SharePoint public/private file sharing TLS SNI (.sharepoint .com) |
2812 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to SharePoint public/private file sharing TLS SNI (.sharepoint .com) |
2812 | iexplore.exe | Possible Social Engineering Attempted | SUSPICIOUS [ANY.RUN] Accessing SharePoint content without a legitimate Microsoft Sign-In |