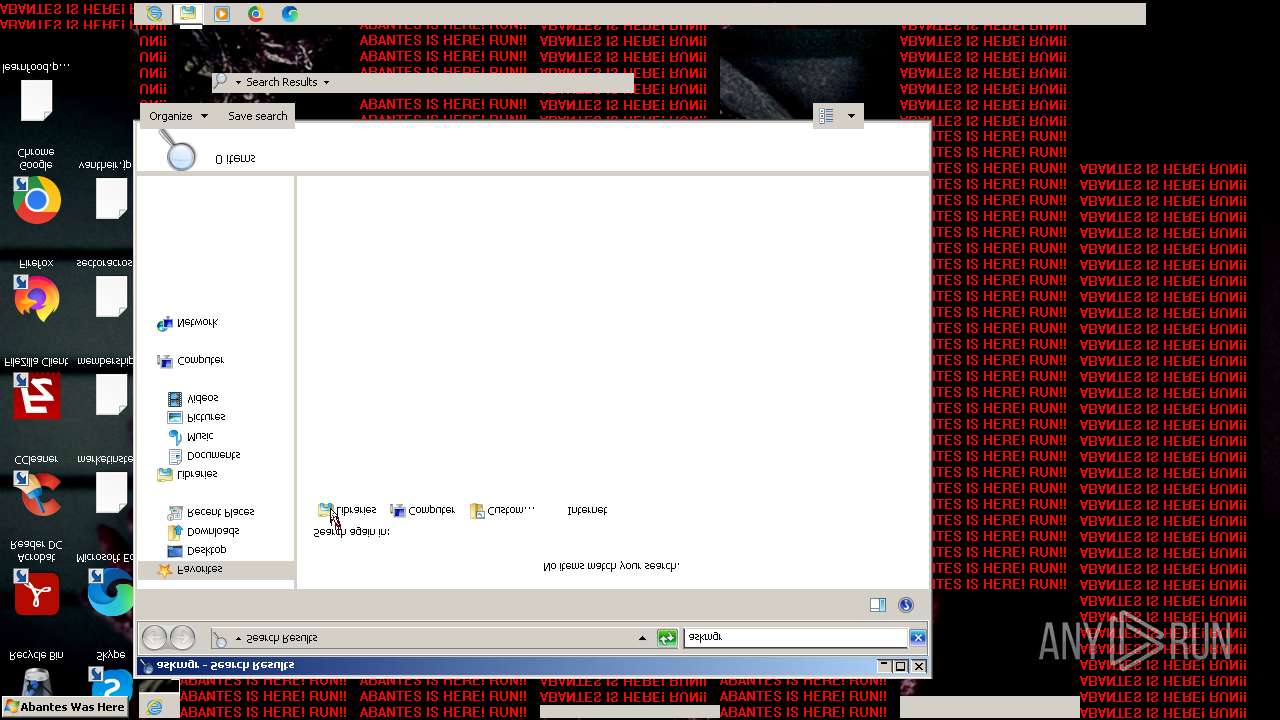
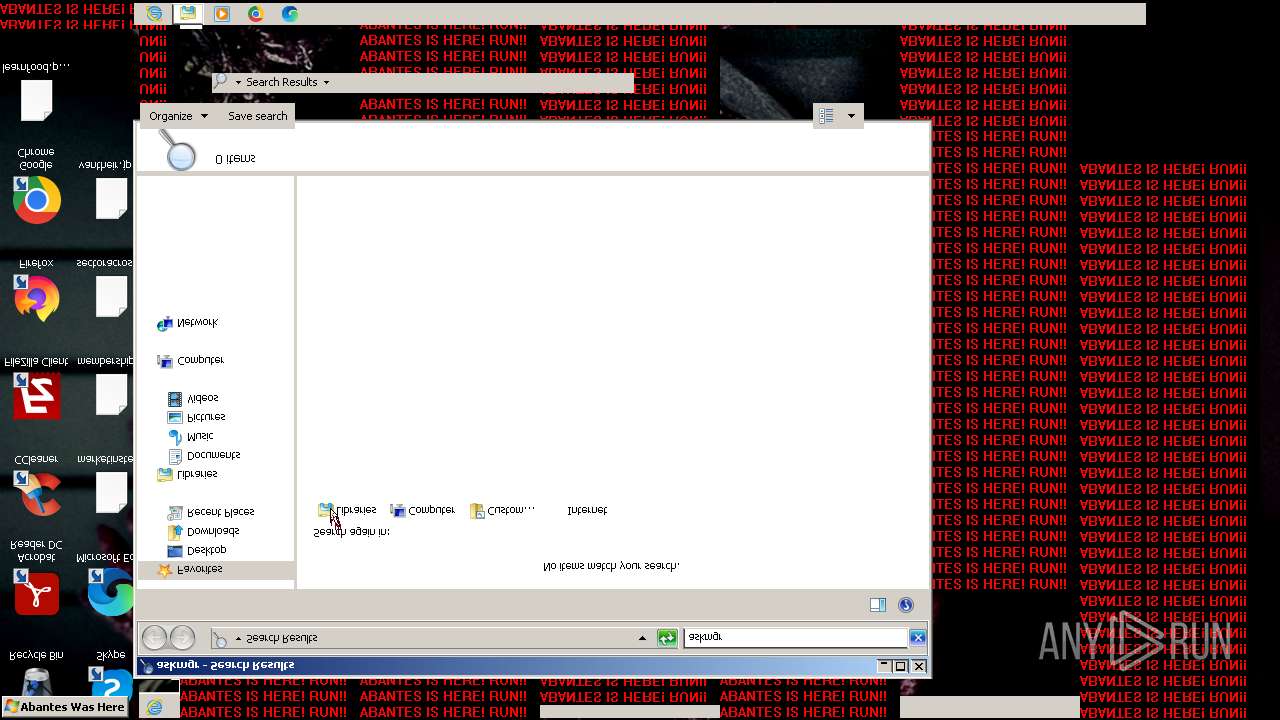
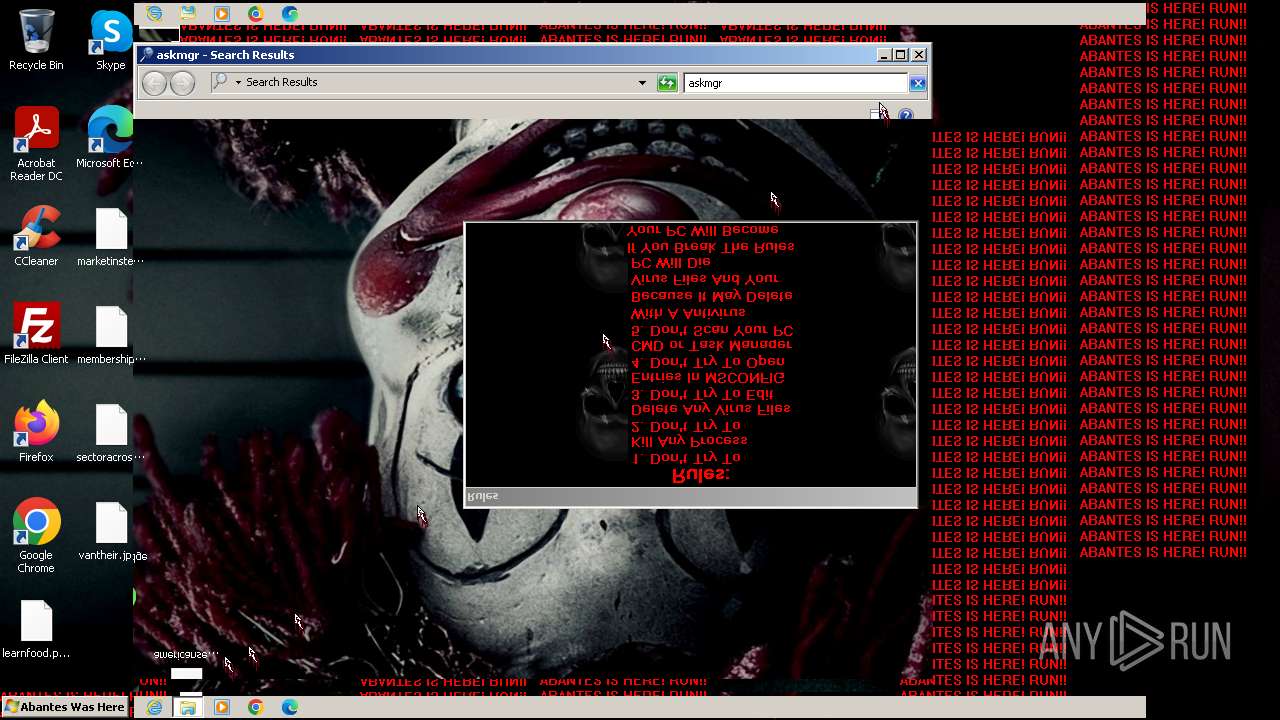
| File name: | Abantes.exe |
| Full analysis: | https://app.any.run/tasks/53c469c1-3b0f-4900-8bcb-a3f86e305fa6 |
| Verdict: | Malicious activity |
| Analysis date: | April 21, 2024, 16:00:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | CD2E58136D3049E9BE40AE29F9250C93 |
| SHA1: | E97BEB8B87D130E5C5745981E3614ED6AA3CAAE3 |
| SHA256: | DAC4B5511343CF863832E38886AF8A3E1D55529648314EB02CC21FA3979F6419 |
| SSDEEP: | 98304:sfVayUb+JmNyVQFWSEtVRMUx+JmNyVQFWSEtVRS+JmNyVQFWSEtVRvJ4tw4A7:xklk6k |
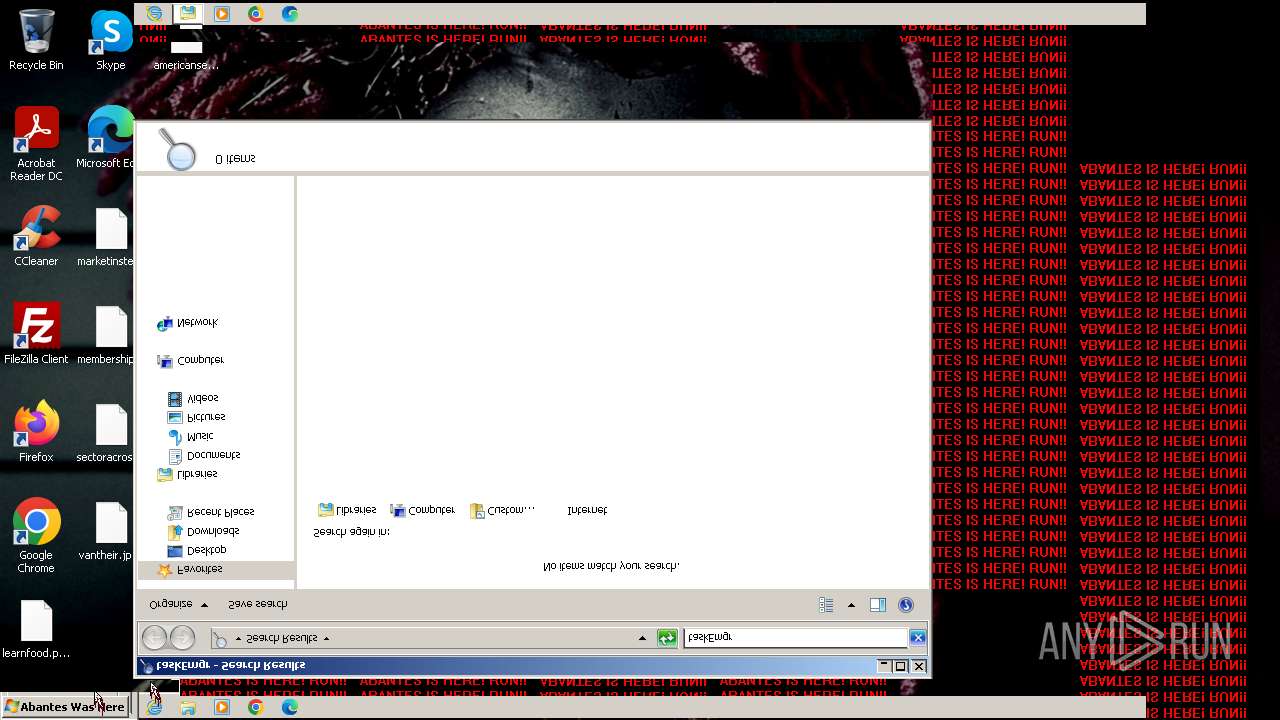
MALICIOUS
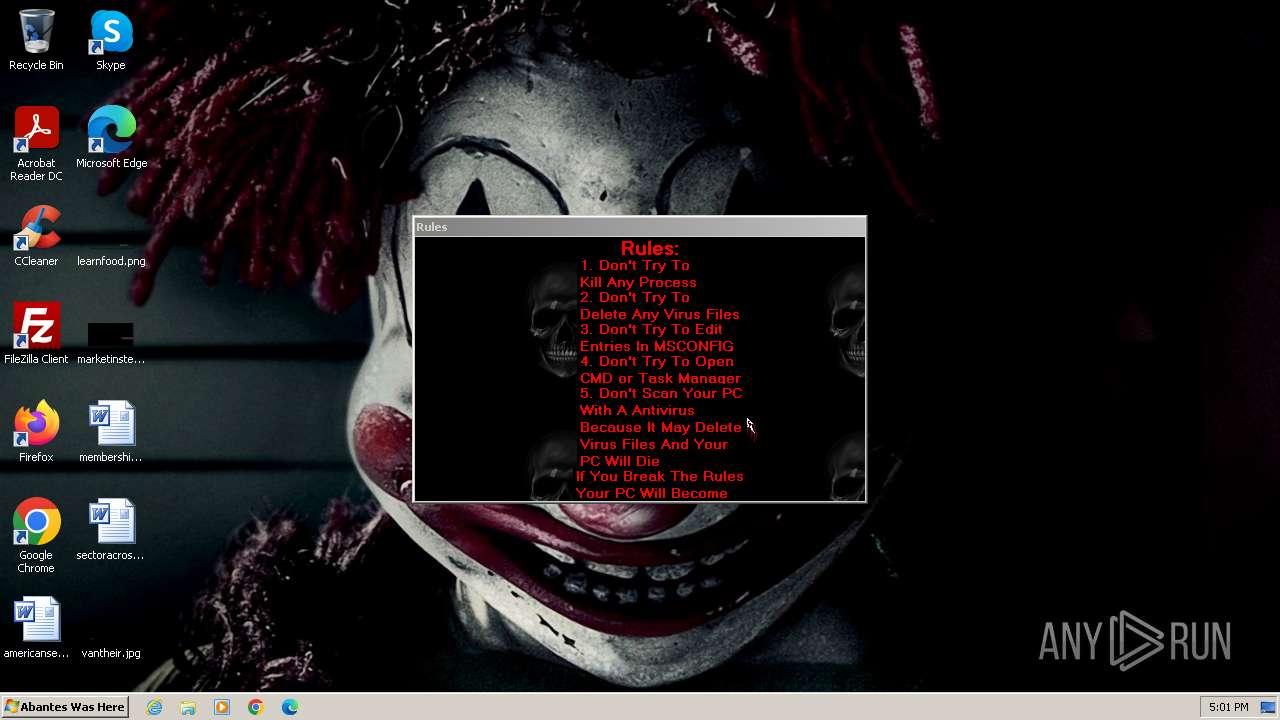
Drops the executable file immediately after the start
- Abantes.exe (PID: 548)
- cmd.exe (PID: 3808)
UAC/LUA settings modification
- Abantes.exe (PID: 548)
Changes image file execution options
- Abantes.exe (PID: 548)
Changes the login/logoff helper path in the registry
- Abantes.exe (PID: 548)
Deletes shadow copies
- cmd.exe (PID: 3808)
Steals credentials from Web Browsers
- taskhost.exe (PID: 3936)
SUSPICIOUS
Process drops legitimate windows executable
- Abantes.exe (PID: 548)
- cmd.exe (PID: 3808)
Executable content was dropped or overwritten
- Abantes.exe (PID: 548)
- cmd.exe (PID: 3808)
The process creates files with name similar to system file names
- Abantes.exe (PID: 548)
Starts CMD.EXE for commands execution
- Abantes.exe (PID: 548)
Executing commands from a ".bat" file
- Abantes.exe (PID: 548)
Found strings related to reading or modifying Windows Defender settings
- Abantes.exe (PID: 548)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 3808)
Reads the Internet Settings
- WMIC.exe (PID: 2576)
- Abantes.exe (PID: 548)
- taskhost.exe (PID: 3936)
- sipnotify.exe (PID: 3724)
- WMIC.exe (PID: 1408)
- Abantes.exe (PID: 4048)
Uses WMIC.EXE to obtain user accounts information
- cmd.exe (PID: 3808)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 3808)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 3808)
The system shut down or reboot
- Abantes.exe (PID: 548)
Reads security settings of Internet Explorer
- Abantes.exe (PID: 548)
- Abantes.exe (PID: 4048)
Executes as Windows Service
- VSSVC.exe (PID: 980)
- taskhost.exe (PID: 3936)
- EOSNotify.exe (PID: 1424)
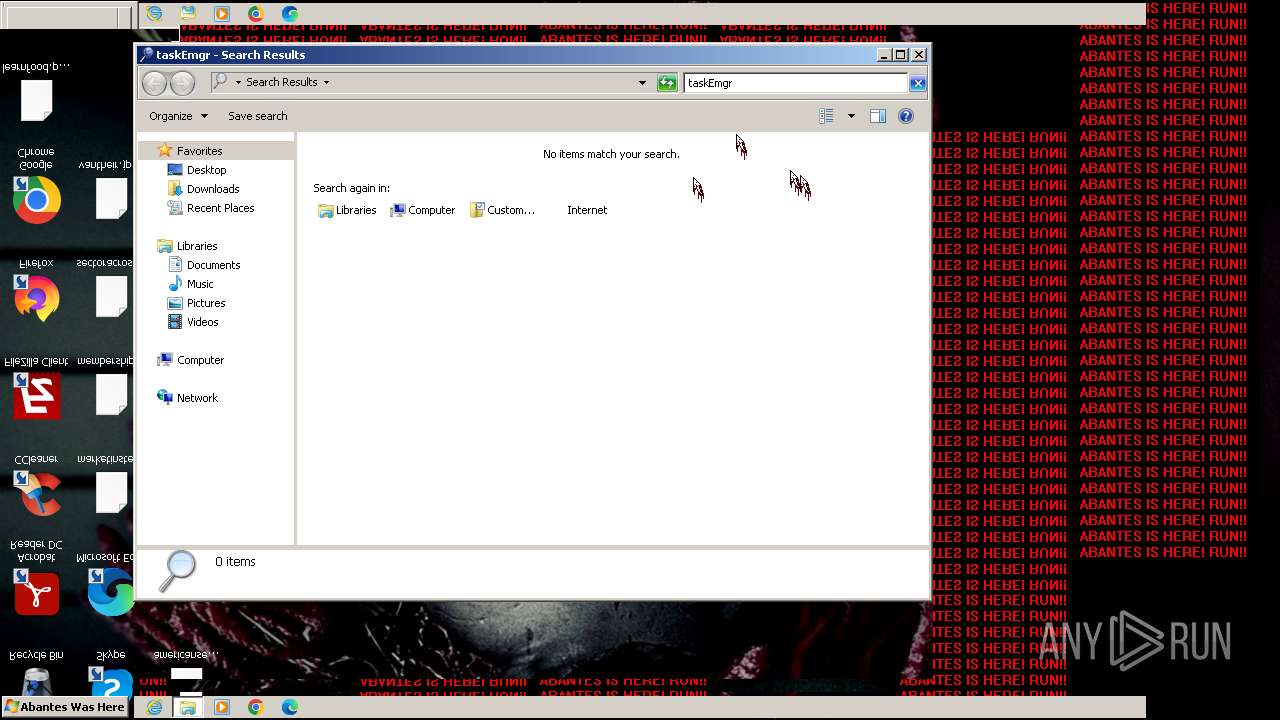
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3808)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 3808)
The process executes via Task Scheduler
- sipnotify.exe (PID: 3724)
- ctfmon.exe (PID: 2588)
- Abantes.exe (PID: 4048)
Reads settings of System Certificates
- sipnotify.exe (PID: 3724)
Reads Internet Explorer settings
- WinMail.exe (PID: 2892)
INFO
Checks supported languages
- Abantes.exe (PID: 548)
- Rules.exe (PID: 3252)
- Abantes.exe (PID: 4048)
- WinMail.exe (PID: 2892)
- IMEKLMG.EXE (PID: 3832)
- wmpnscfg.exe (PID: 2836)
- wmpnscfg.exe (PID: 3768)
- IFEO.exe (PID: 2488)
- IMEKLMG.EXE (PID: 3868)
Reads the computer name
- Abantes.exe (PID: 548)
- WinMail.exe (PID: 2892)
- Abantes.exe (PID: 4048)
- Rules.exe (PID: 3252)
- IMEKLMG.EXE (PID: 3832)
- IMEKLMG.EXE (PID: 3868)
- wmpnscfg.exe (PID: 3768)
- IFEO.exe (PID: 2488)
- wmpnscfg.exe (PID: 2836)
Reads the machine GUID from the registry
- Abantes.exe (PID: 548)
- WinMail.exe (PID: 2892)
- Abantes.exe (PID: 4048)
- Rules.exe (PID: 3252)
Create files in a temporary directory
- Abantes.exe (PID: 548)
Process checks whether UAC notifications are on
- Abantes.exe (PID: 548)
- IMEKLMG.EXE (PID: 3868)
- IMEKLMG.EXE (PID: 3832)
Reads mouse settings
- Abantes.exe (PID: 548)
Manual execution by a user
- WinMail.exe (PID: 2892)
- IMEKLMG.EXE (PID: 3868)
- IFEO.exe (PID: 2488)
- wmpnscfg.exe (PID: 2836)
- wmpnscfg.exe (PID: 3768)
- taskmgr.exe (PID: 3136)
- IMEKLMG.EXE (PID: 3832)
Reads the software policy settings
- sipnotify.exe (PID: 3724)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 3724)
Creates files or folders in the user directory
- WinMail.exe (PID: 2892)
- Abantes.exe (PID: 4048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:05:23 17:04:16+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 2820096 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2b274e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.163 |
| ProductVersionNumber: | 2.0.0.163 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Abantes Trojan |
| CompanyName: | - |
| FileDescription: | Abantes |
| FileVersion: | 2.0.0.163 |
| InternalName: | Abantes.exe |
| LegalCopyright: | Copyright 2018 |
| LegalTrademarks: | - |
| OriginalFileName: | Abantes.exe |
| ProductName: | Abantes |
| ProductVersion: | 2.0.0.163 |
| AssemblyVersion: | 2.0.0.163 |
Total processes
93
Monitored processes
41
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 548 | "C:\Users\admin\AppData\Local\Temp\Abantes.exe" | C:\Users\admin\AppData\Local\Temp\Abantes.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Abantes Exit code: 1073807364 Version: 2.0.0.163 Modules
| |||||||||||||||
| 572 | takeown /f "C:\Windows\en-US" /r /d y | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 668 | "C:\Users\admin\AppData\Local\Temp\Abantes.exe" | C:\Users\admin\AppData\Local\Temp\Abantes.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Abantes Exit code: 3221226540 Version: 2.0.0.163 Modules
| |||||||||||||||
| 896 | takeown /f HelpPane.exe | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 900 | "C:\Windows\System32\shutdown.exe" /l /f | C:\Windows\System32\shutdown.exe | — | Abantes.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Shutdown and Annotation Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 980 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1408 | wmic useraccount where name='admin' rename 'Abantes Was Here' | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1424 | C:\Windows\system32\EOSNotify.exe | C:\Windows\System32\EOSNotify.exe | — | services.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: EOS Notification Exit code: 0 Version: 6.1.7601.24544 (win7sp1_ldr_escrow.191230-1647) Modules
| |||||||||||||||
| 1556 | icacls HelpPane.exe /granted admin:F | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2072 | icacls "C:\Windows\en-US" /granted admin:F /T /C | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
8 811
Read events
8 637
Write events
161
Delete events
13
Modification events
| (PID) Process: | (548) Abantes.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | WallpaperStyle |
Value: 2 | |||
| (PID) Process: | (548) Abantes.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | TileWallpaper |
Value: 0 | |||
| (PID) Process: | (548) Abantes.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | legalnoticecaption |
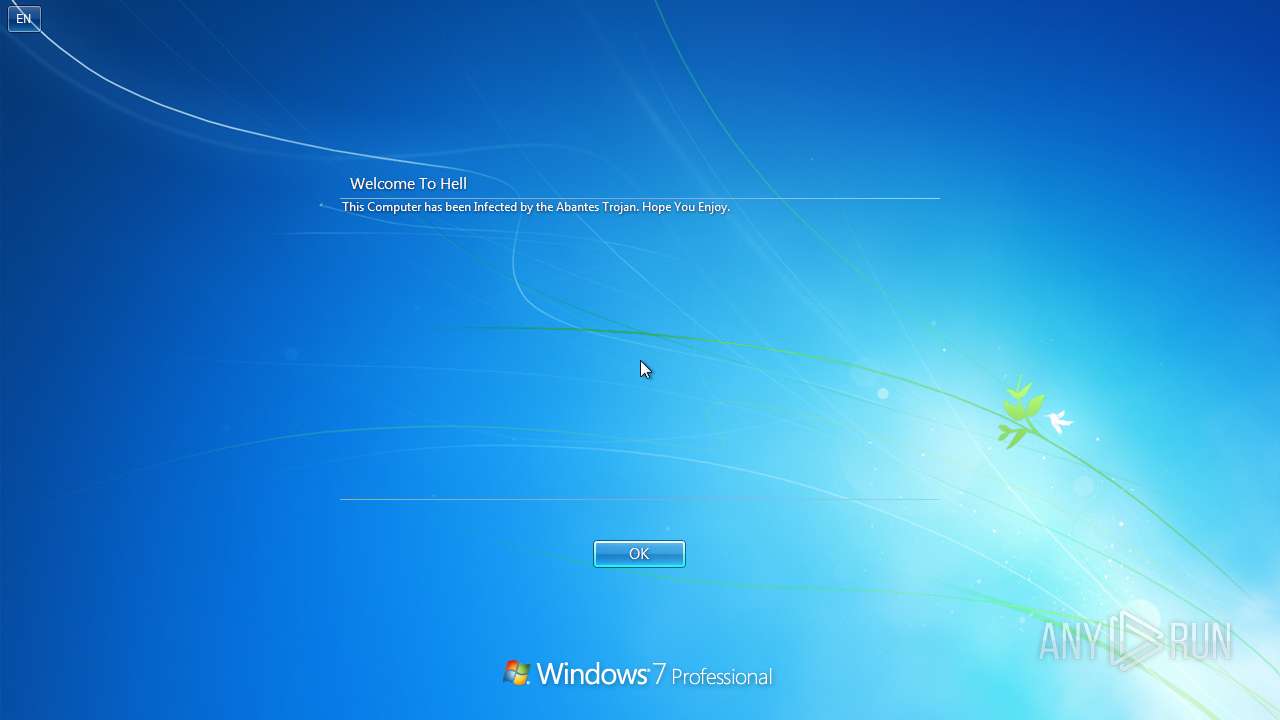
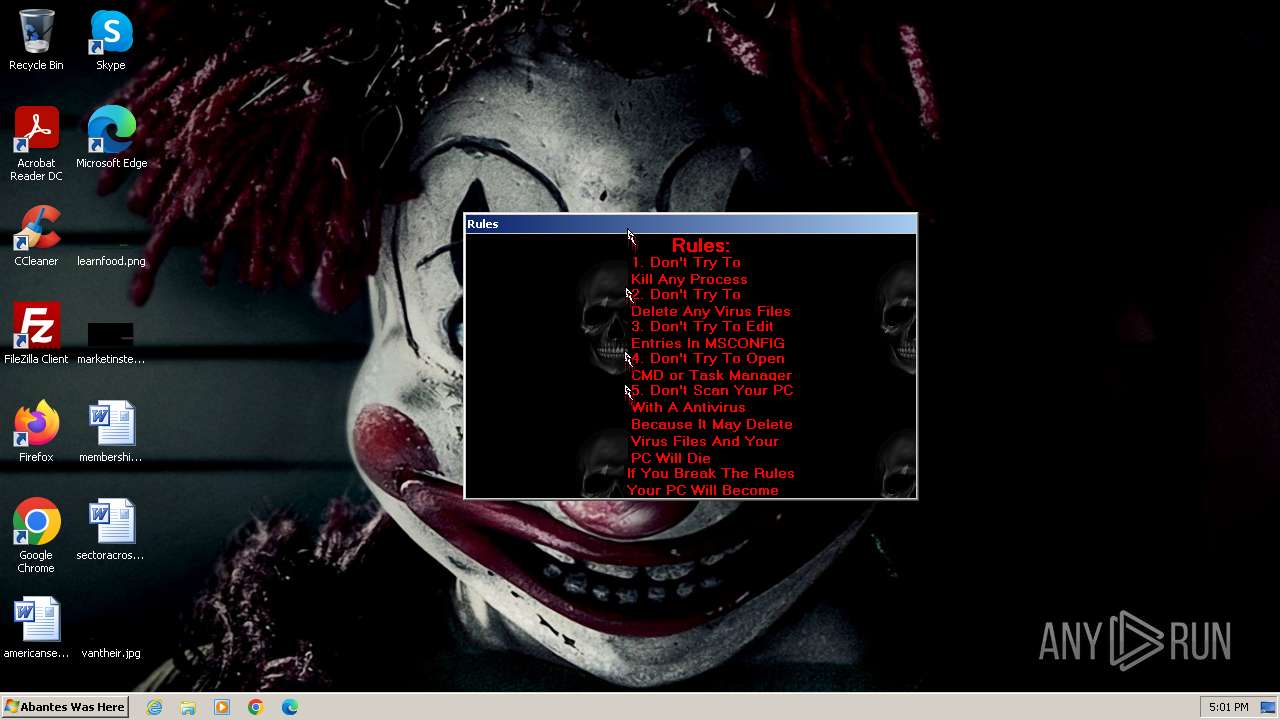
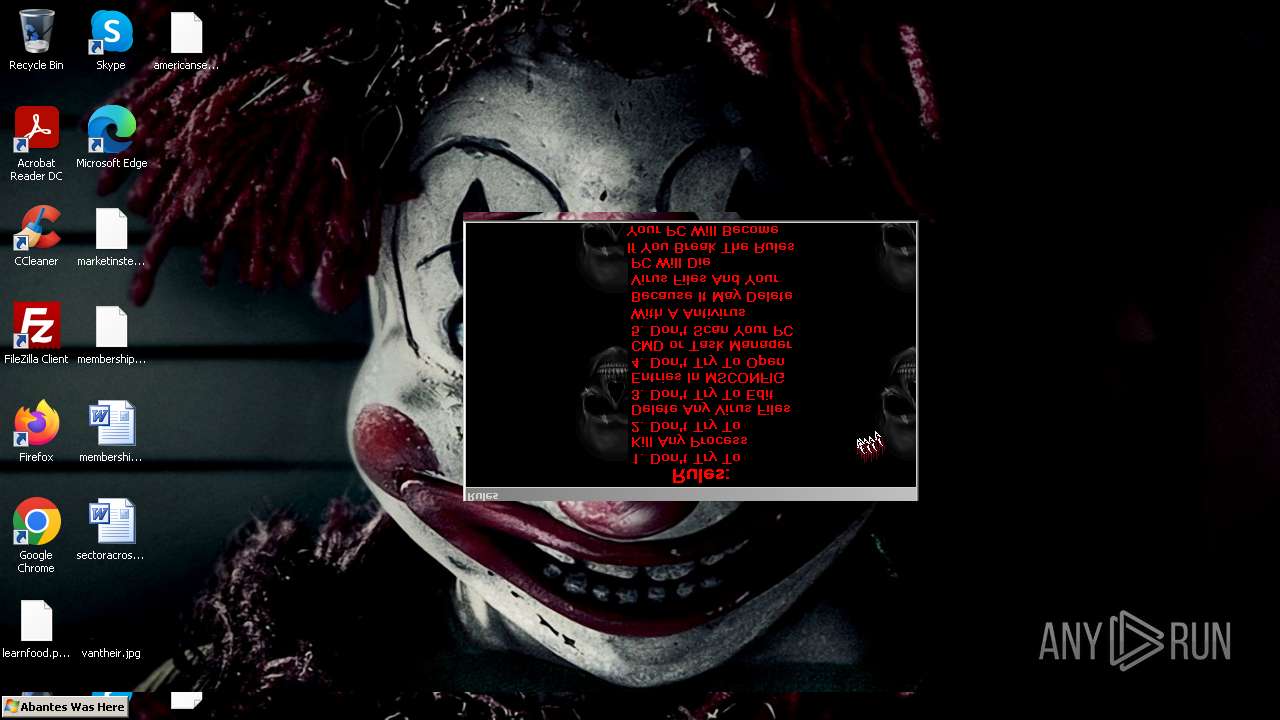
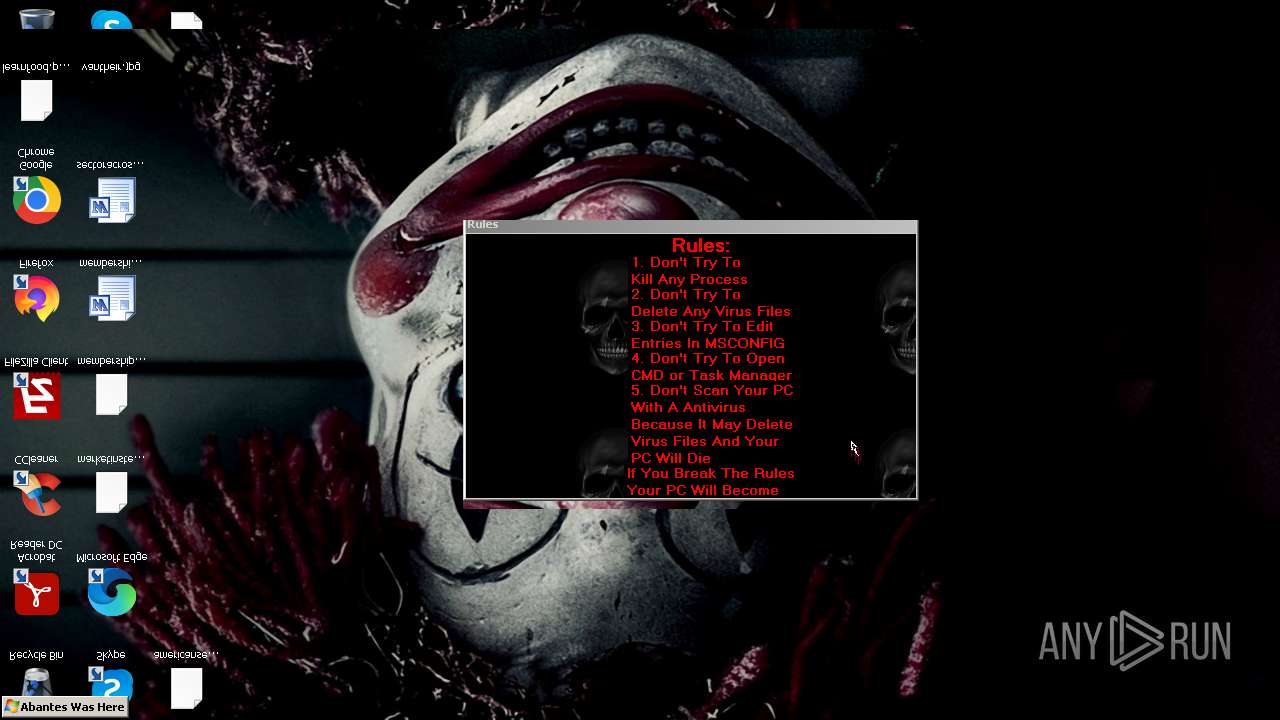
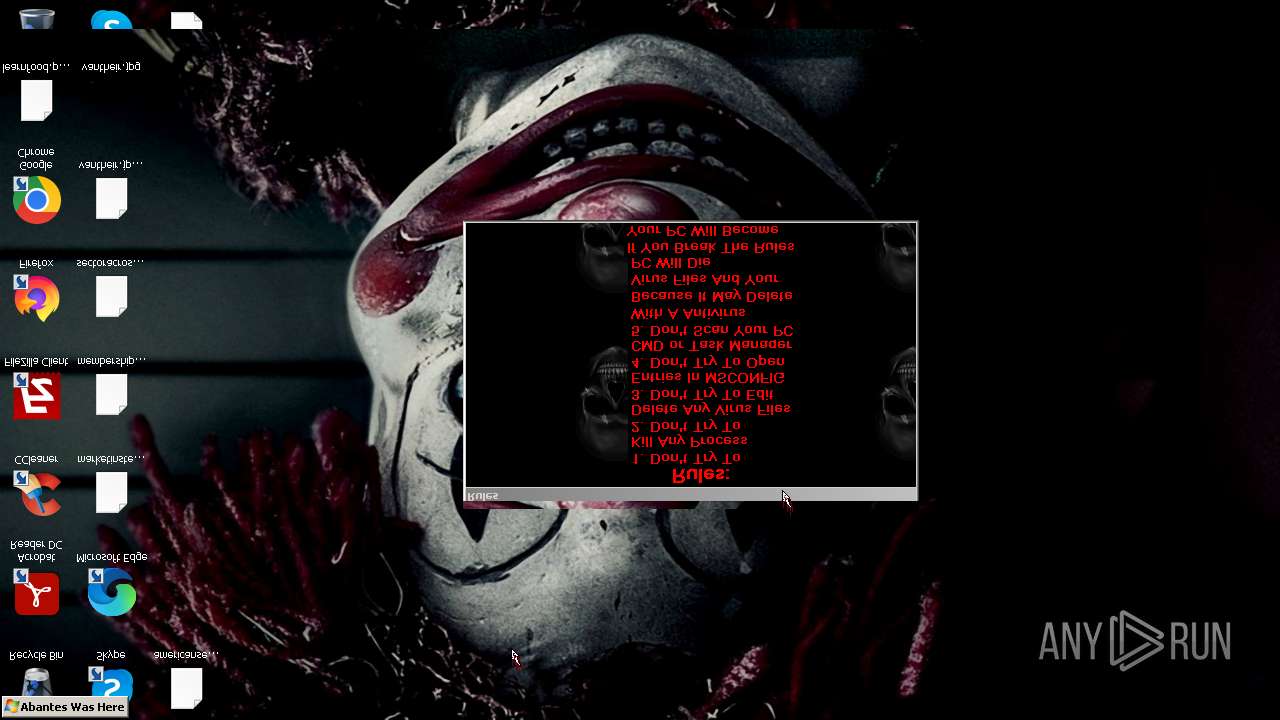
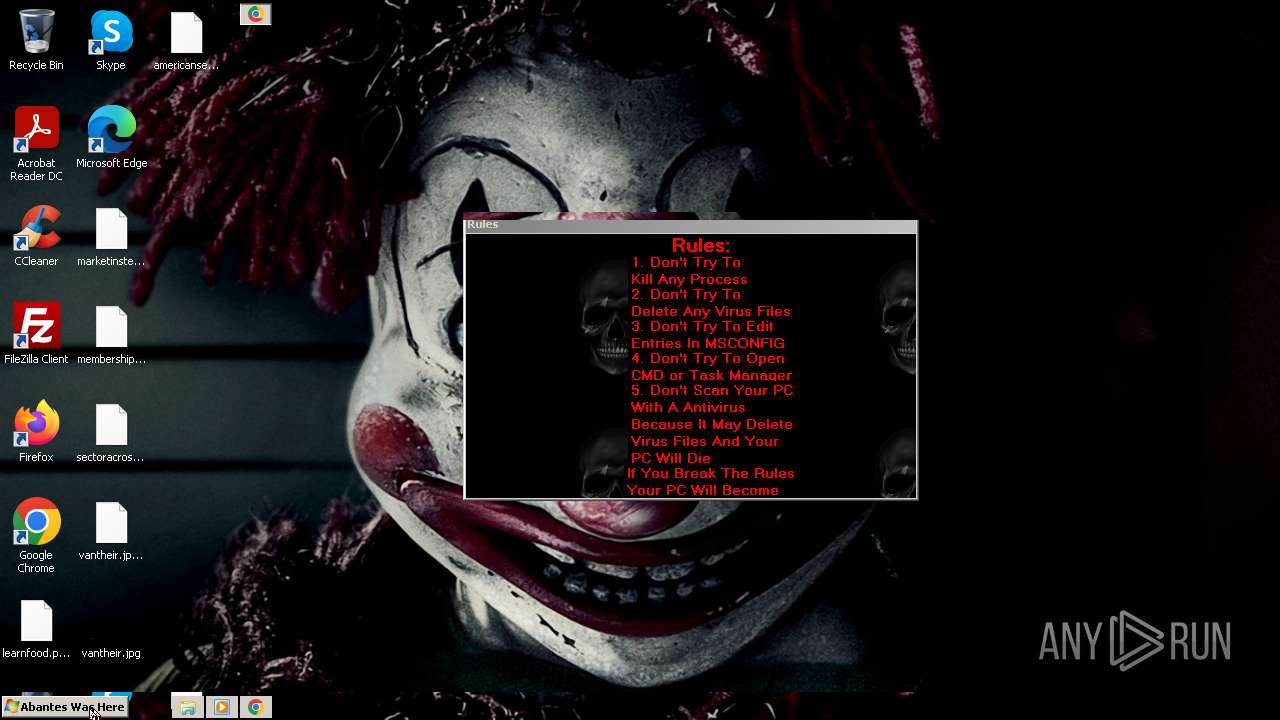
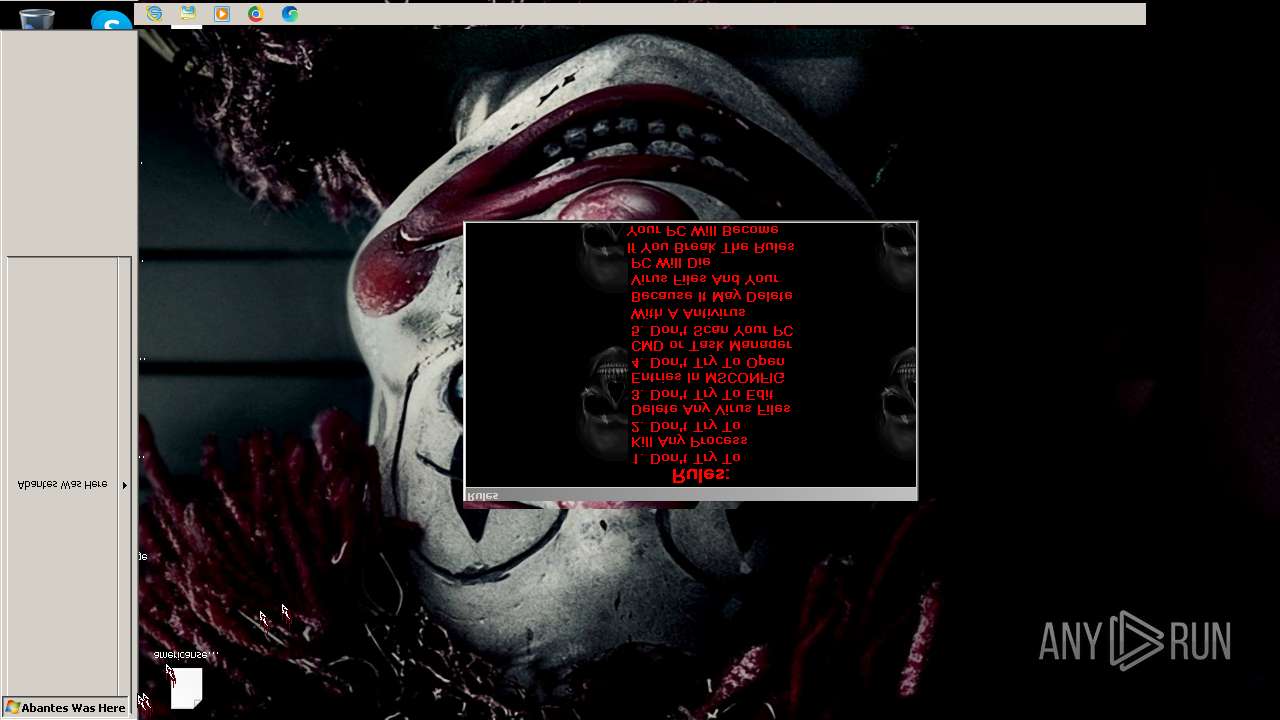
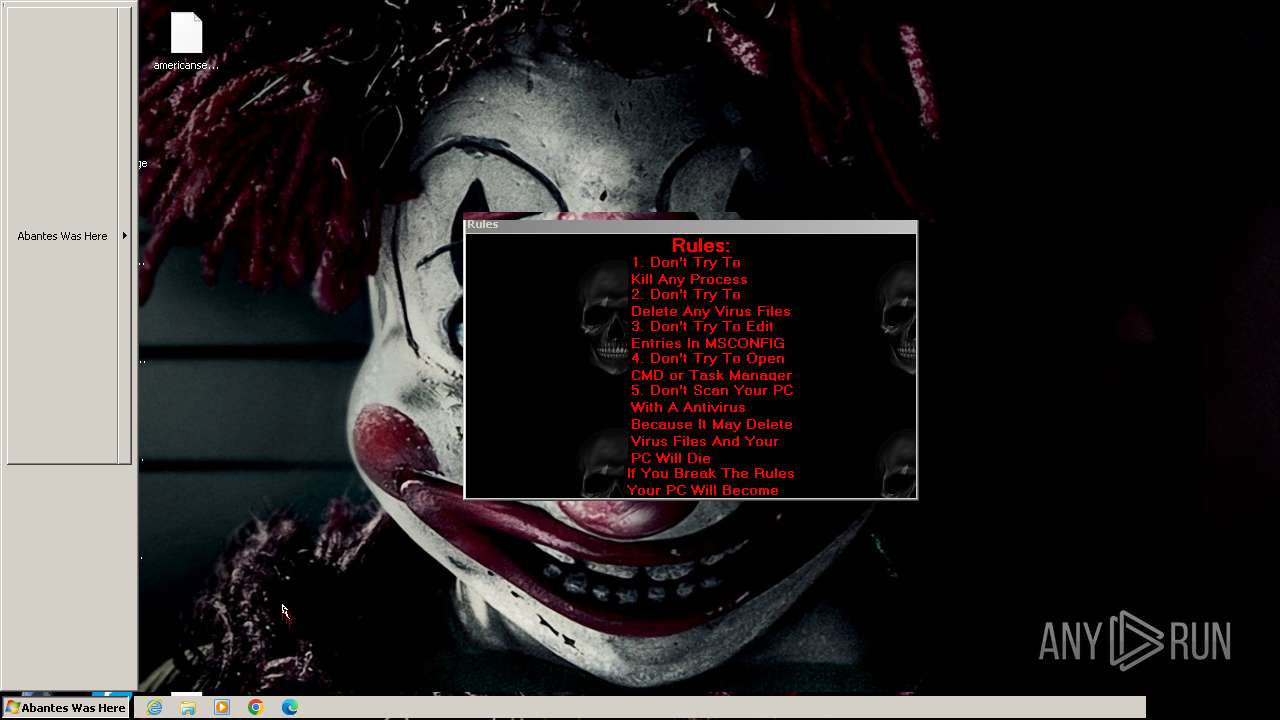
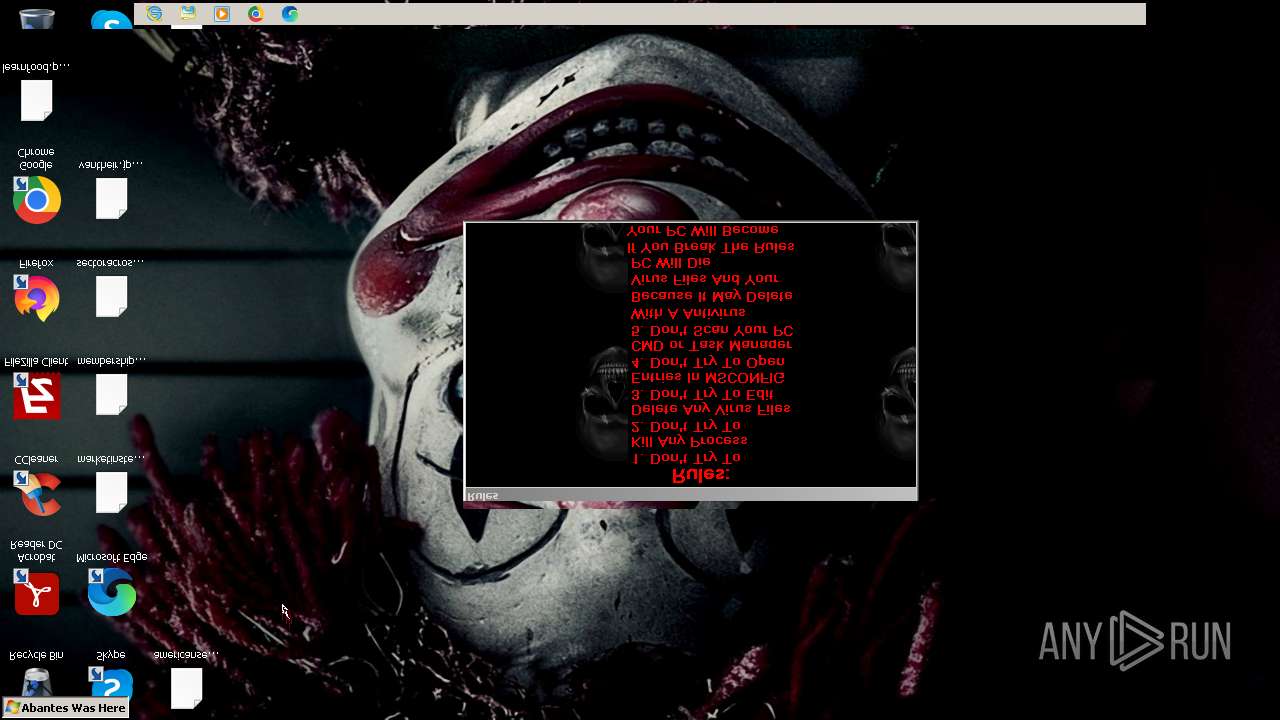
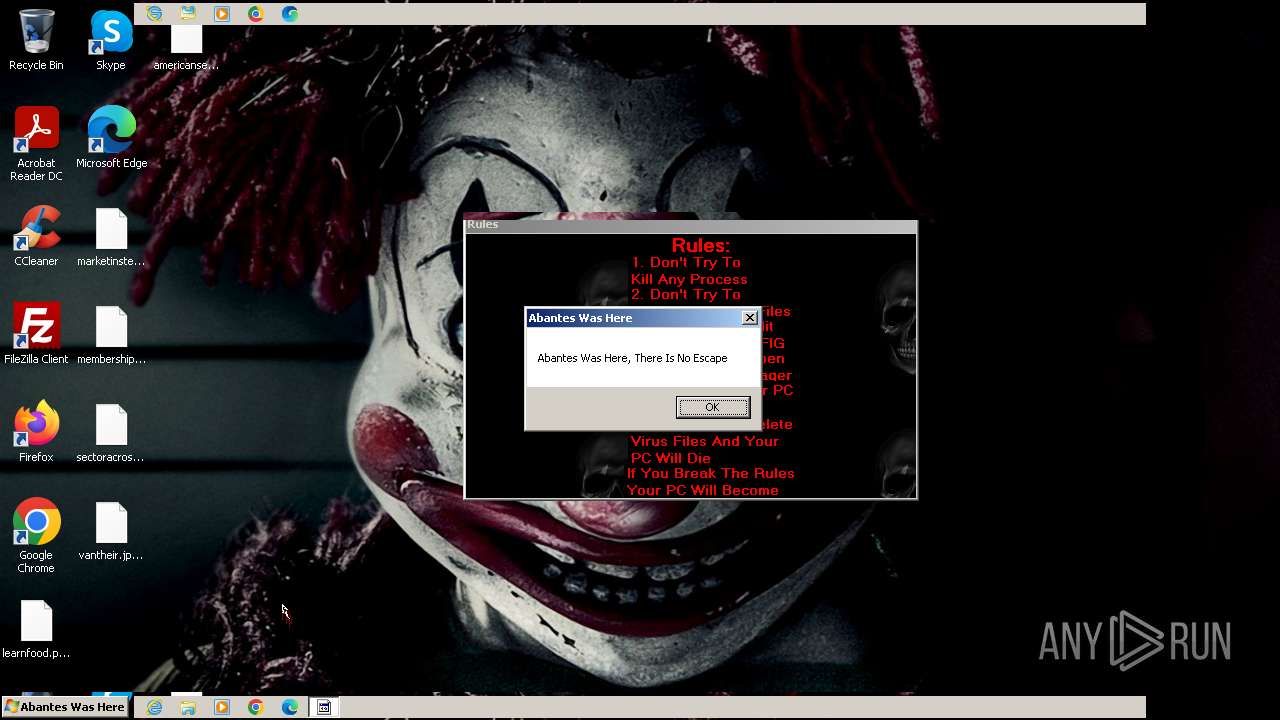
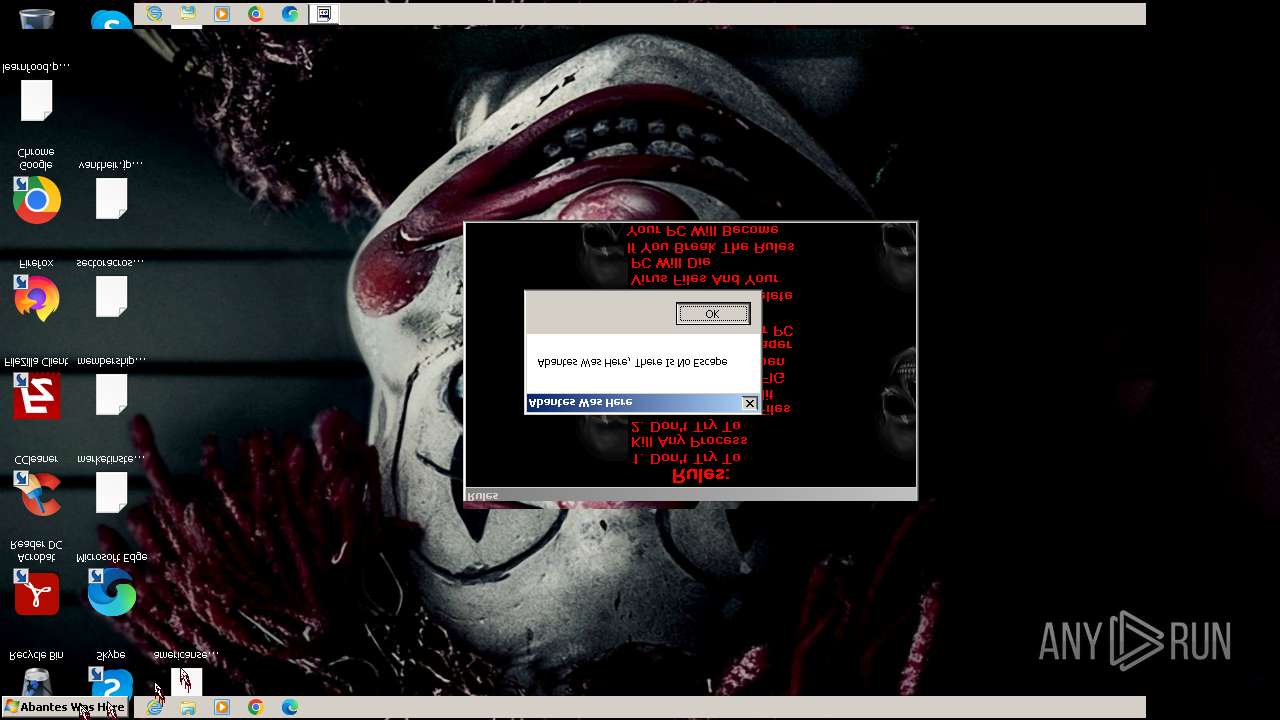
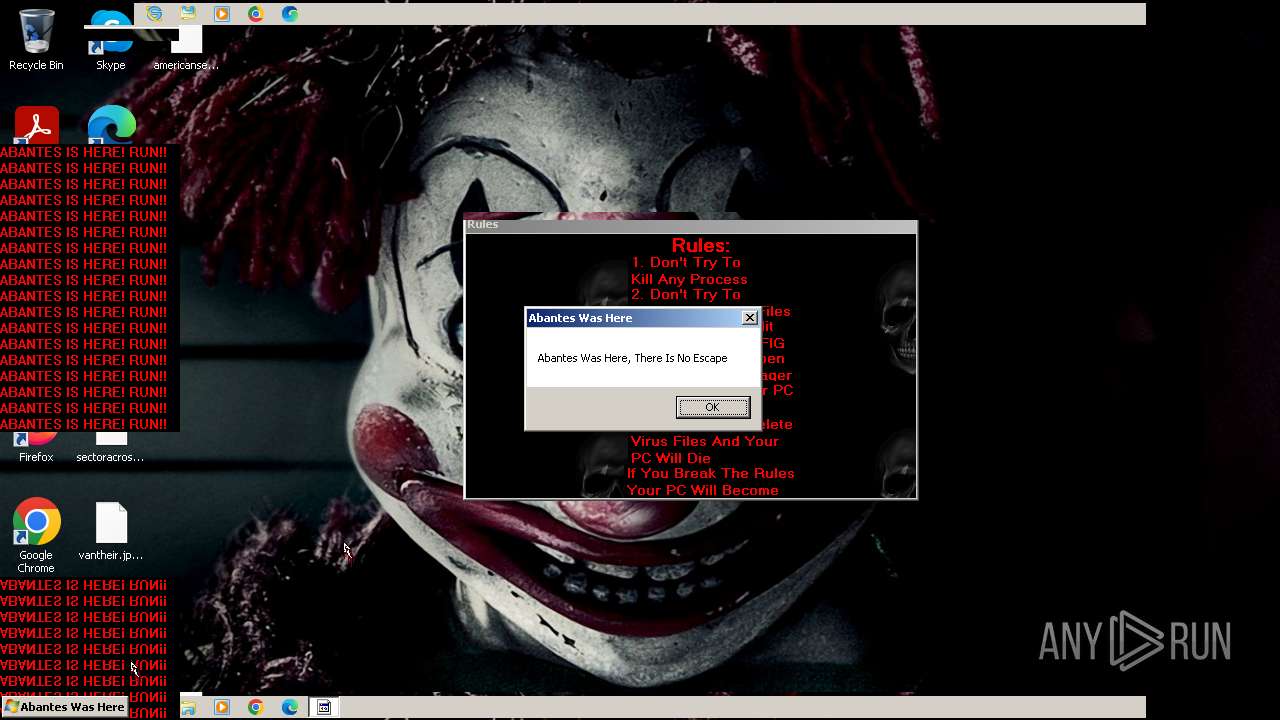
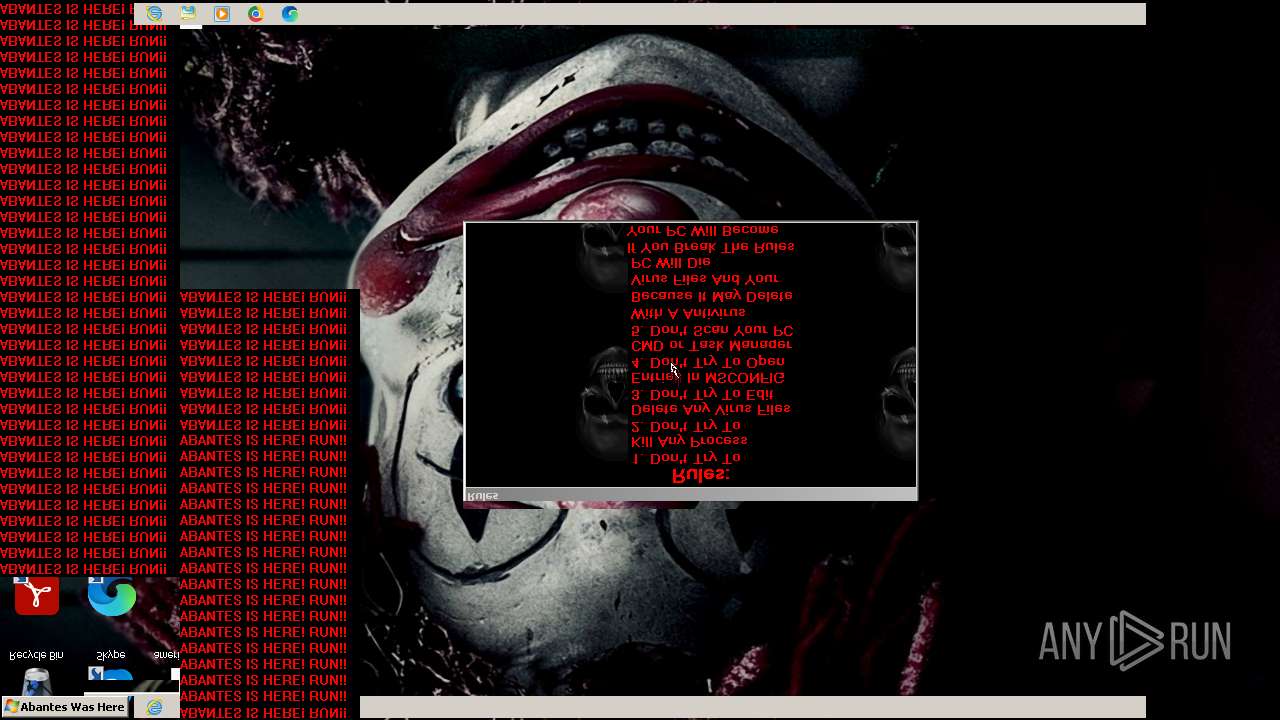
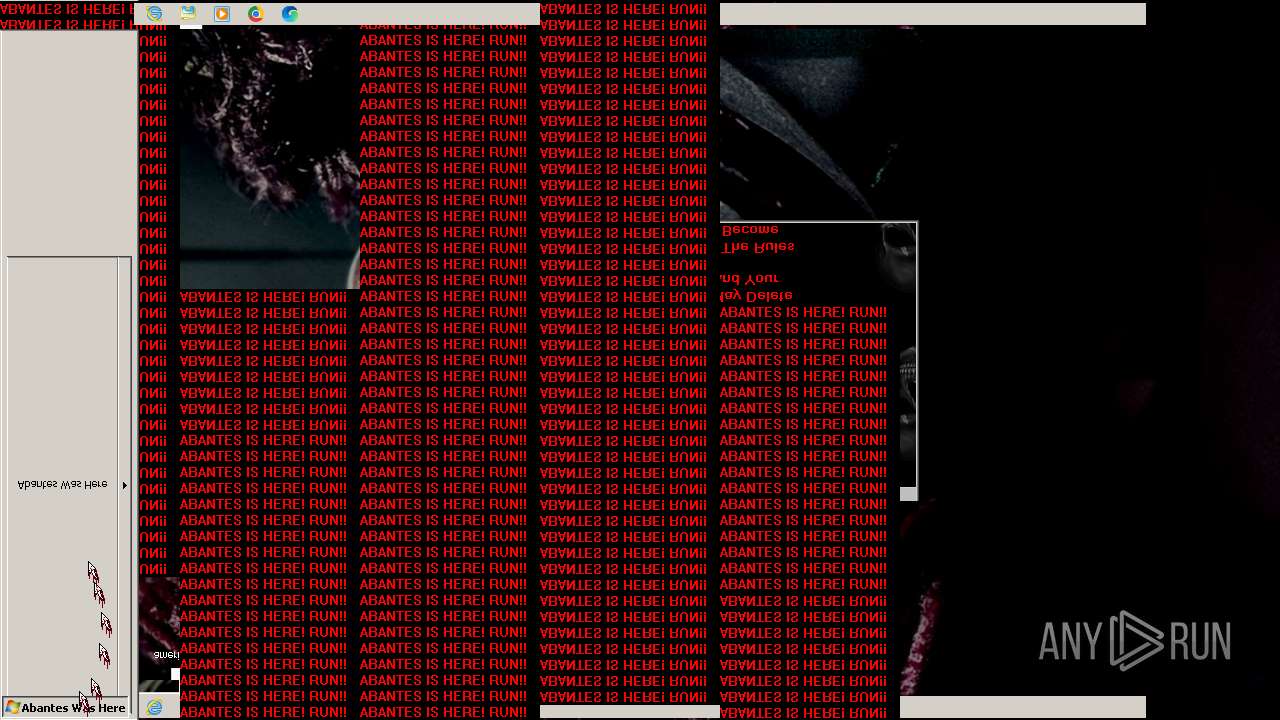
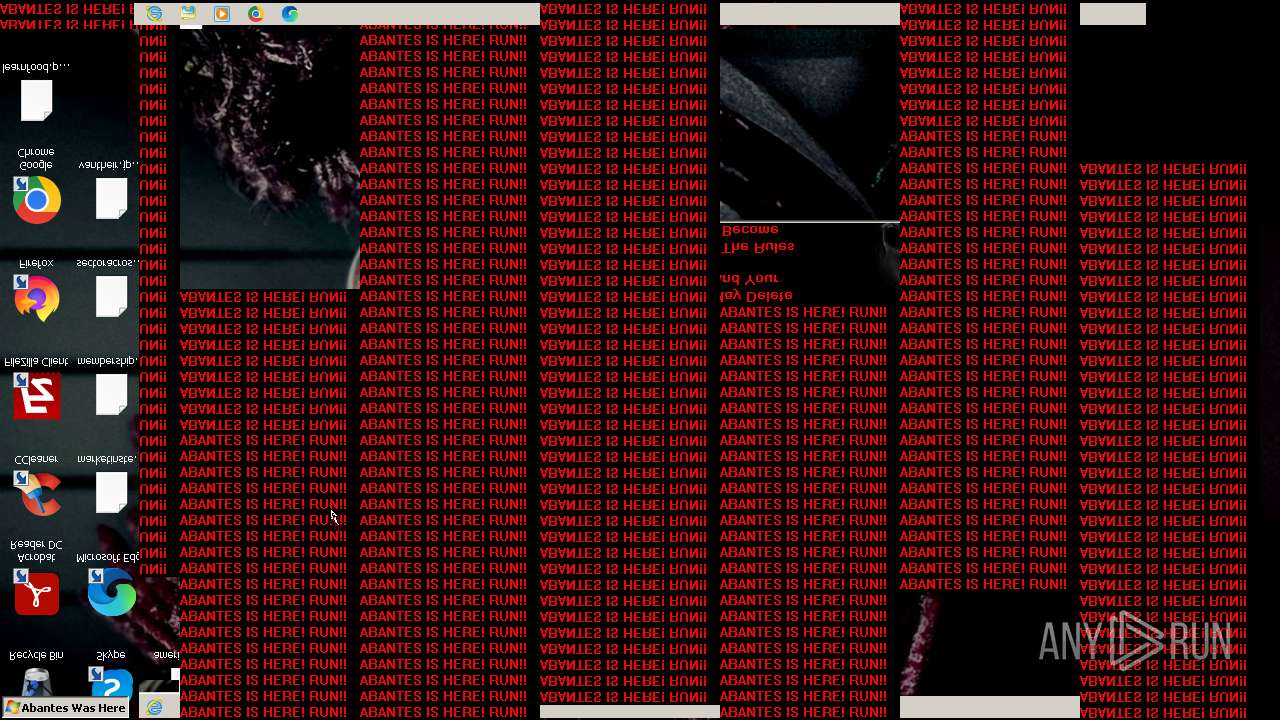
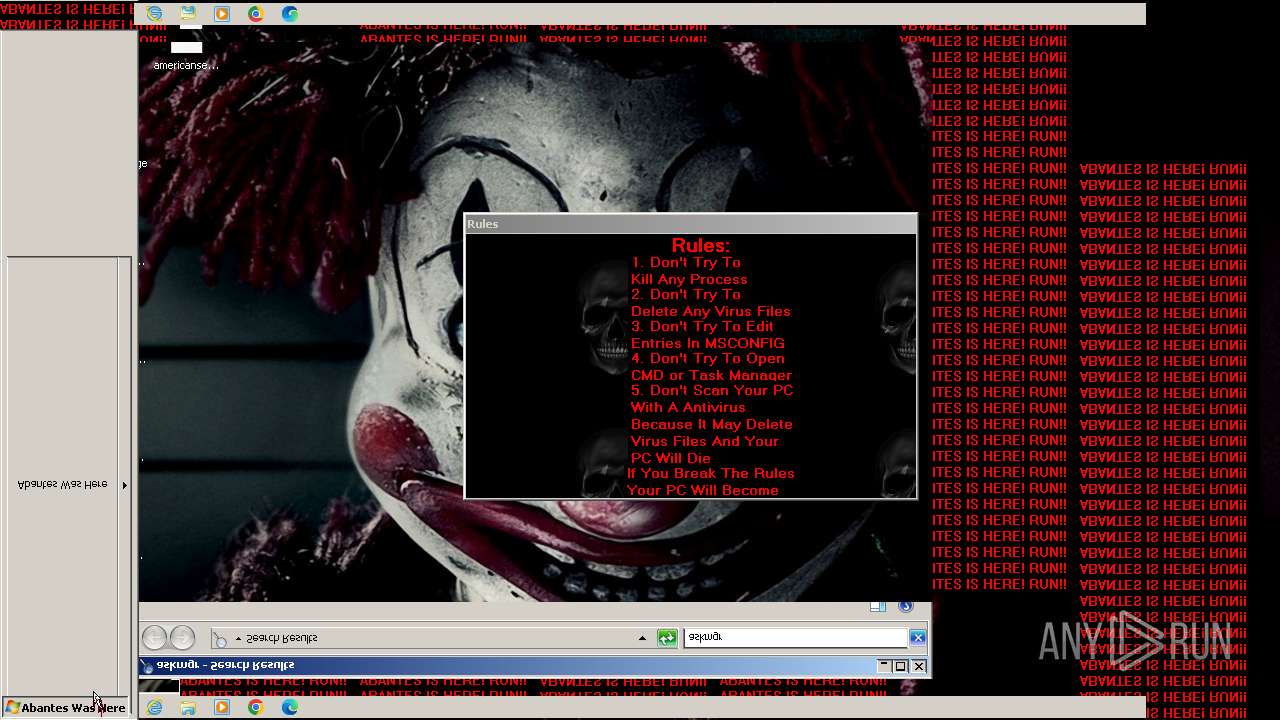
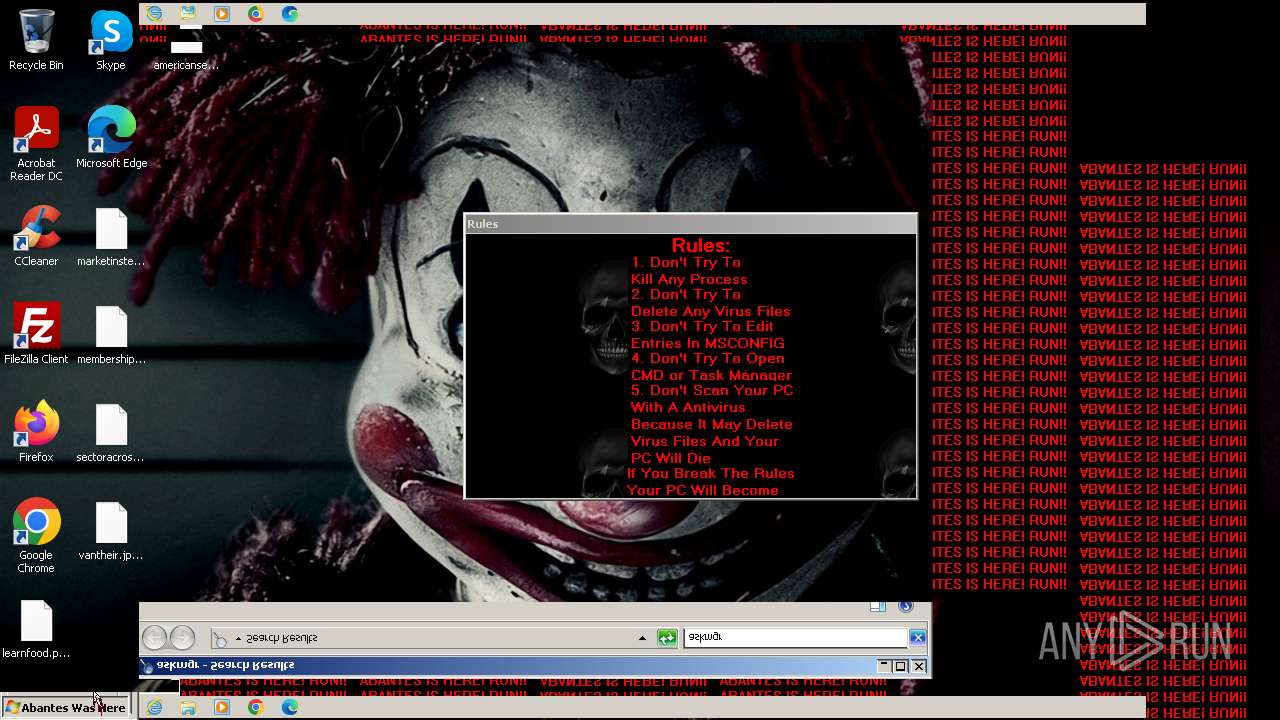
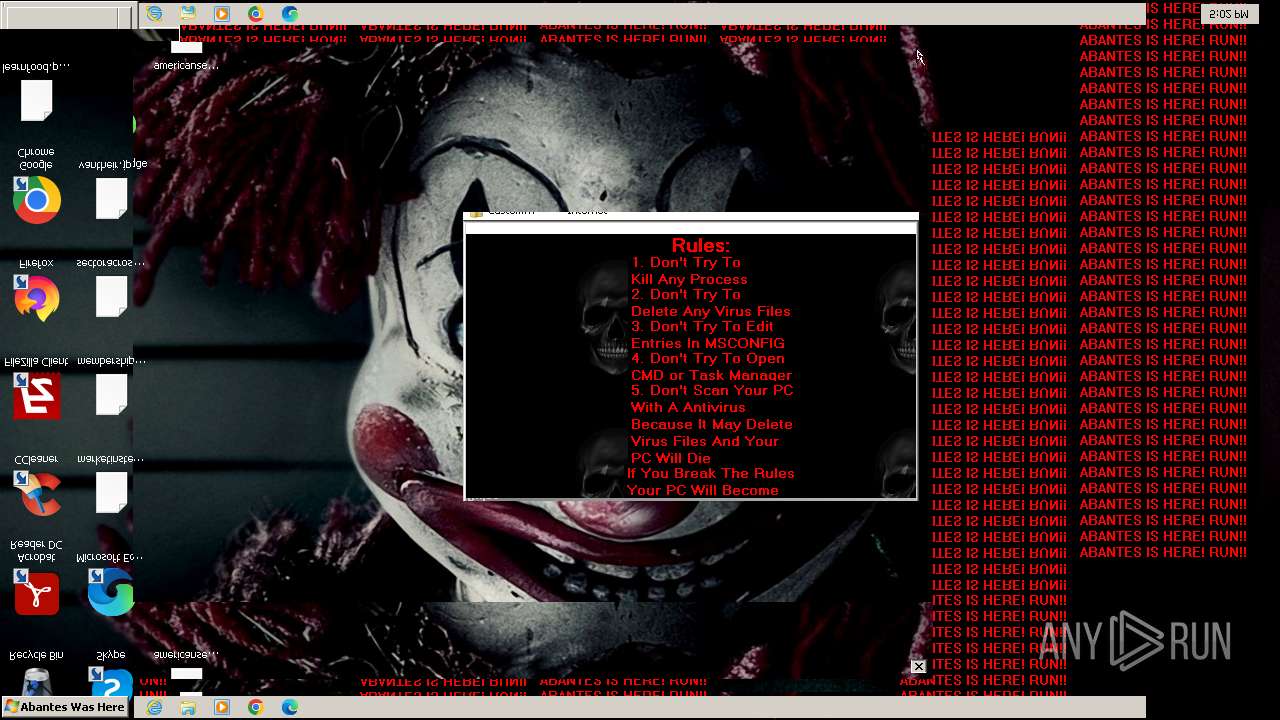
Value: Welcome To Hell | |||
| (PID) Process: | (548) Abantes.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | legalnoticetext |
Value: This Computer has been Infected by the Abantes Trojan. Hope You Enjoy. | |||
| (PID) Process: | (548) Abantes.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoControlPanel |
Value: 1 | |||
| (PID) Process: | (548) Abantes.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | AutoRestartShell |
Value: 0 | |||
| (PID) Process: | (548) Abantes.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | Userinit |
Value: C:\Windows\System32\userinit.exe, C:\Windows\Defender\Abantes.exe | |||
| (PID) Process: | (548) Abantes.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (548) Abantes.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System |
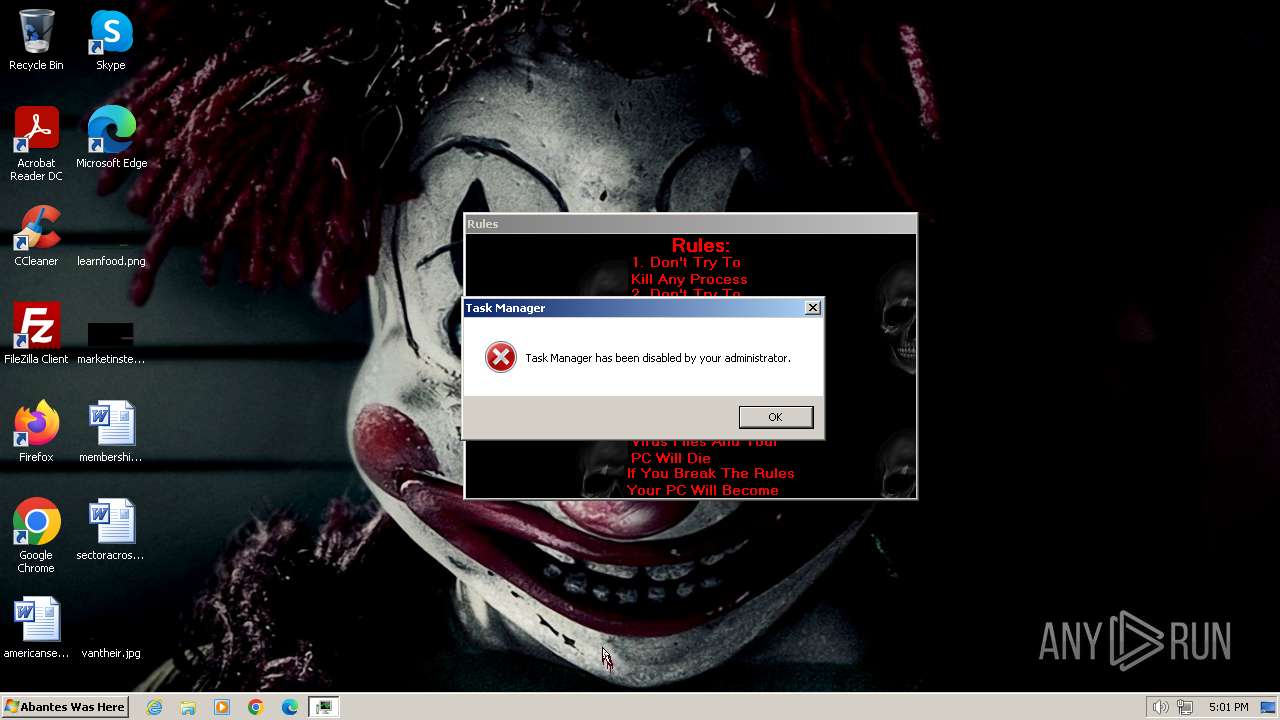
| Operation: | write | Name: | DisableTaskMgr |
Value: 1 | |||
| (PID) Process: | (548) Abantes.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\regedit.exe |
| Operation: | write | Name: | Debugger |
Value: C:\Windows\Defender\IFEO.exe | |||
Executable files
10
Suspicious files
33
Text files
9
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 548 | Abantes.exe | C:\Users\admin\AppData\Local\Temp\wallpaper.bmp | — | |
MD5:— | SHA256:— | |||
| 548 | Abantes.exe | C:\Windows\Defender\cursor.cur | binary | |
MD5:F45D84E471C87561676942F31167B952 | SHA256:B01930E8CFC1ECC9E2F3F7930D0999B32C928351BECB9ACEC227079730F466A6 | |||
| 548 | Abantes.exe | C:\Windows\Defender\LogonUIStart.exe | executable | |
MD5:B131EEC92EA7D74FBA7A5D5895045E5D | SHA256:6500506FC7441CBD1B944D62B7E4B4F8759D93BE3B97900420B0E57CCB14656B | |||
| 2892 | WinMail.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Mail\edb.log | binary | |
MD5:09F9EC30C43F61C1B4E3CF574CEF1740 | SHA256:3A2C8485989DE3437B107D5459308E6984CC2D0F029B25CA74DFA0BC4B754054 | |||
| 2892 | WinMail.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Mail\tmp.edb | gmc | |
MD5:290708775281BF2F313B4894208B72E5 | SHA256:C1E6C1DE033F540BDA5F1C8804B200E325E1B87FAB420EF5F20F2993007F432E | |||
| 548 | Abantes.exe | C:\Windows\Defender\Abantes.exe | executable | |
MD5:CD2E58136D3049E9BE40AE29F9250C93 | SHA256:DAC4B5511343CF863832E38886AF8A3E1D55529648314EB02CC21FA3979F6419 | |||
| 2892 | WinMail.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Mail\edb.chk | binary | |
MD5:FDA68760ED7547A701169AEEFAC62B34 | SHA256:75E90B677C16829EE1789C378AA6775FD201999ABB4DB9474046078F016A40E2 | |||
| 548 | Abantes.exe | C:\Windows\Defender\wallpaper.jpg | image | |
MD5:88994751A9562A808E8AE3A26D64A22B | SHA256:D26905C24CC4961B75827C23DC28871A087CF01F9824DA1D463BC2BFAB484A27 | |||
| 3808 | cmd.exe | C:\Windows\en-US\explorer.exe.mui | executable | |
MD5:39F1A6A8B713FCF30AFC03EA3C936F85 | SHA256:B69B61675531060D350A795A53568CCF19A146060CEBB659EBC658A0E8B27FC9 | |||
| 548 | Abantes.exe | C:\Windows\Defender\Payloads.dll | executable | |
MD5:1267609A5F26696613050A2DE89FE470 | SHA256:D6E77BC9B31AB9CEFE74C688349545908A633D0E09B80FAAECEF837565775B8E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3724 | sipnotify.exe | HEAD | 200 | 23.197.138.118:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133581924798320000 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3724 | sipnotify.exe | 23.197.138.118:80 | query.prod.cms.rt.microsoft.com | Akamai International B.V. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
query.prod.cms.rt.microsoft.com |
| whitelisted |