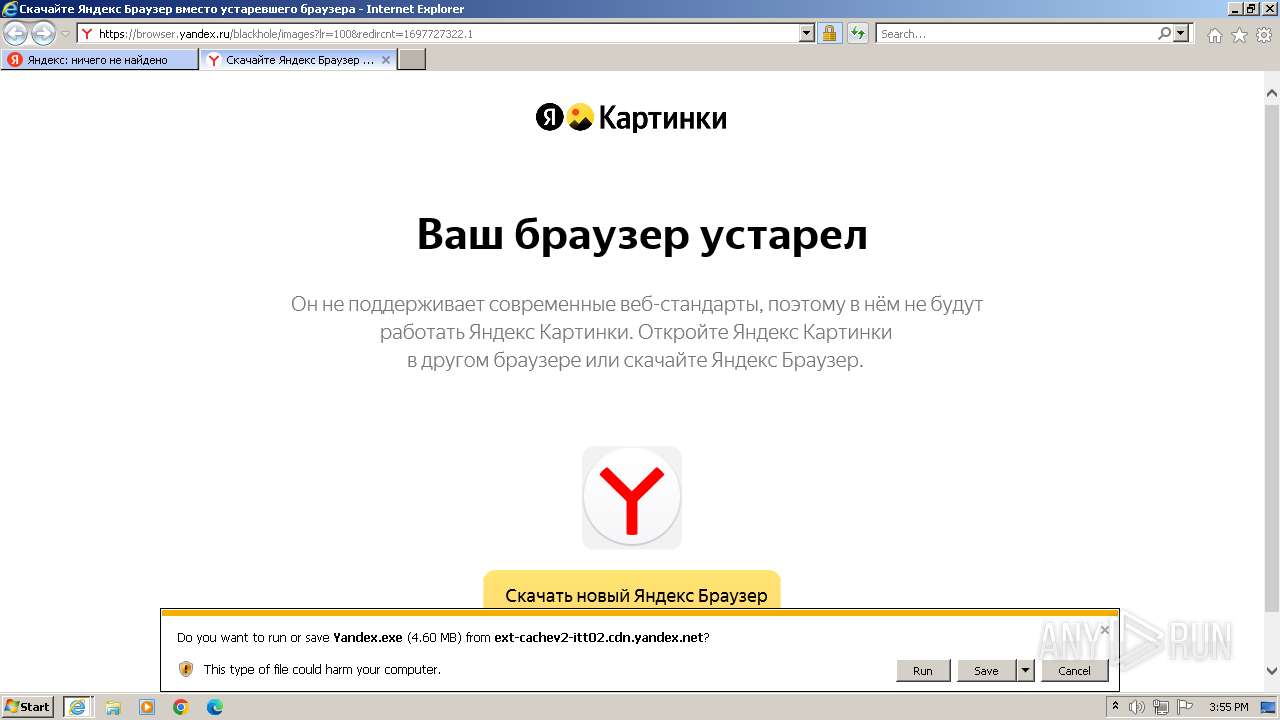
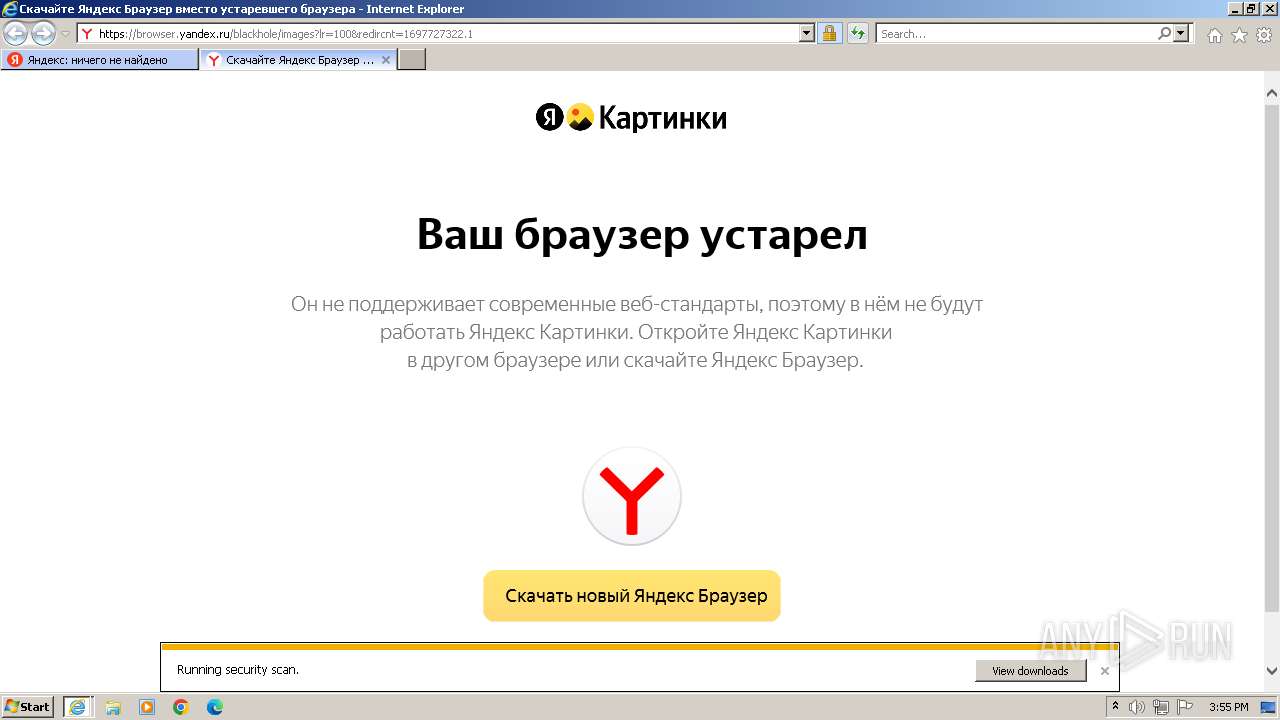
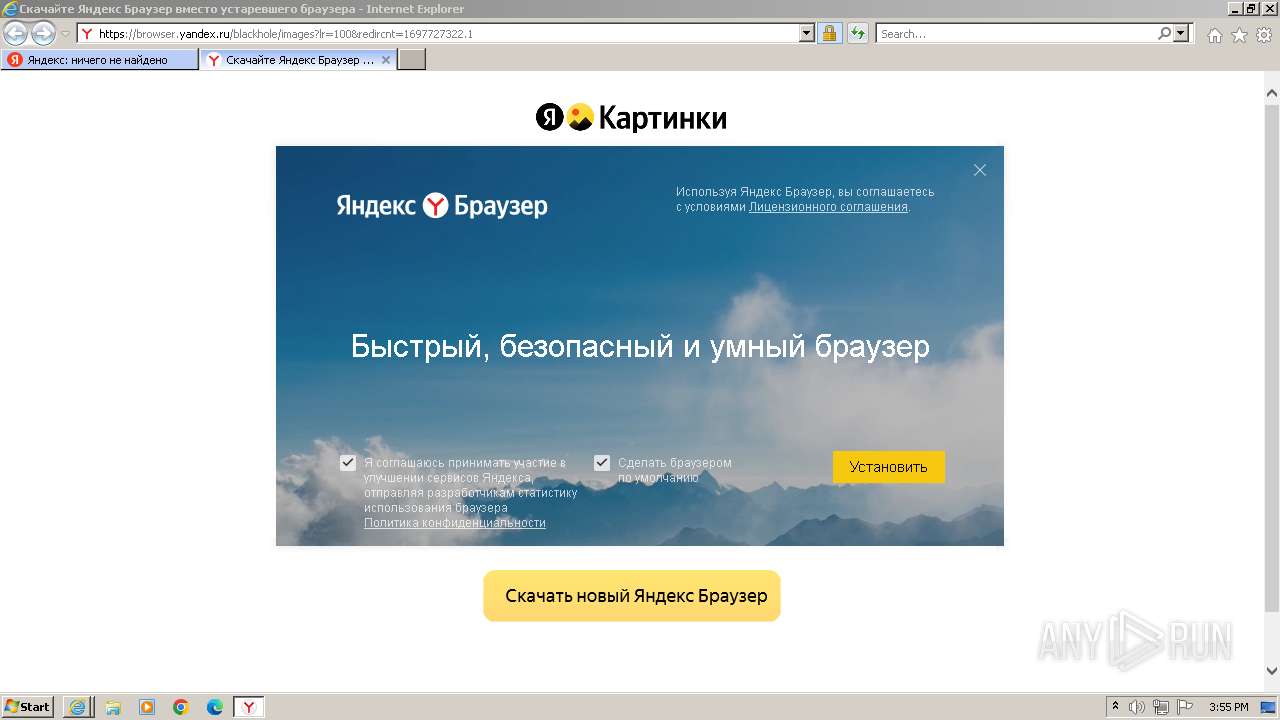
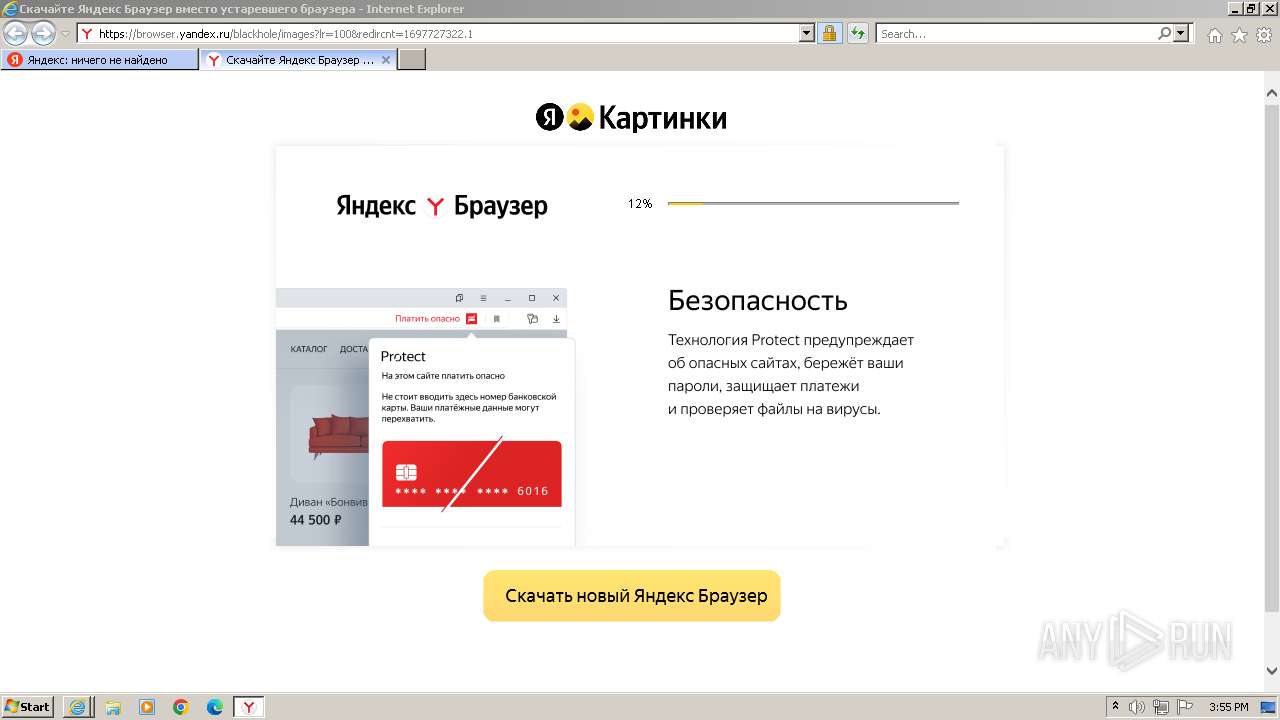
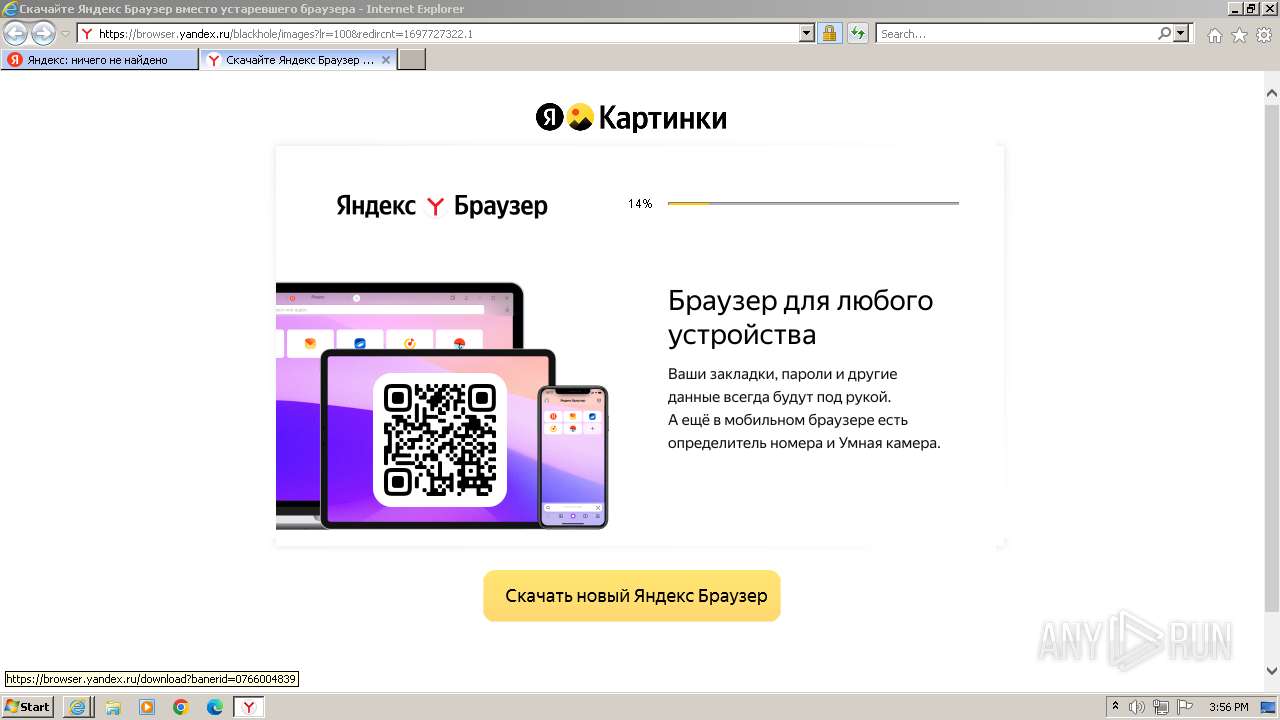
| URL: | https://bs.yandex.ru |
| Full analysis: | https://app.any.run/tasks/7c8511b8-483b-410a-b809-ec594c8819a1 |
| Verdict: | Malicious activity |
| Analysis date: | October 19, 2023, 14:53:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | D9B9A5E5CE4EF2614EFDEF5FE2A12702 |
| SHA1: | 522D0A2FE3F8FCD8A297CD3CD122B6D78A1769BB |
| SHA256: | DAC224B1E025C4239F92A3F9026973BF51A2E366E2149B83B28911FB85D4E176 |
| SSDEEP: | 3:N8LEn:2m |
MALICIOUS
Application was dropped or rewritten from another process
- Yandex.exe (PID: 1928)
- Yandex.exe (PID: 1432)
SUSPICIOUS
Application launched itself
- Yandex.exe (PID: 1432)
Reads the Internet Settings
- Yandex.exe (PID: 1432)
Reads settings of System Certificates
- Yandex.exe (PID: 1432)
Reads security settings of Internet Explorer
- Yandex.exe (PID: 1432)
Checks Windows Trust Settings
- Yandex.exe (PID: 1432)
INFO
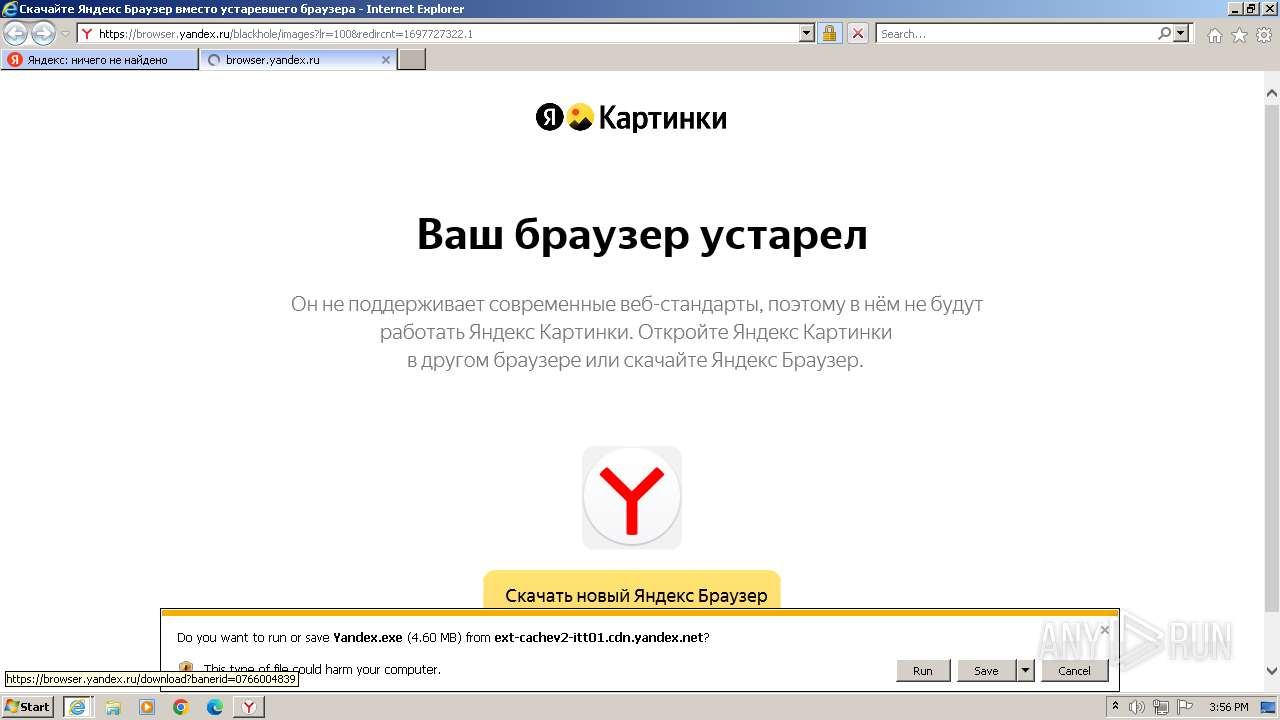
The process uses the downloaded file
- iexplore.exe (PID: 556)
- Yandex.exe (PID: 1432)
Application launched itself
- iexplore.exe (PID: 556)
Checks supported languages
- Yandex.exe (PID: 1928)
- Yandex.exe (PID: 1432)
Drops the executable file immediately after the start
- iexplore.exe (PID: 556)
- iexplore.exe (PID: 3716)
Reads the computer name
- Yandex.exe (PID: 1432)
Creates files or folders in the user directory
- Yandex.exe (PID: 1432)
Create files in a temporary directory
- Yandex.exe (PID: 1432)
Checks proxy server information
- Yandex.exe (PID: 1432)
Reads the machine GUID from the registry
- Yandex.exe (PID: 1432)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
46
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
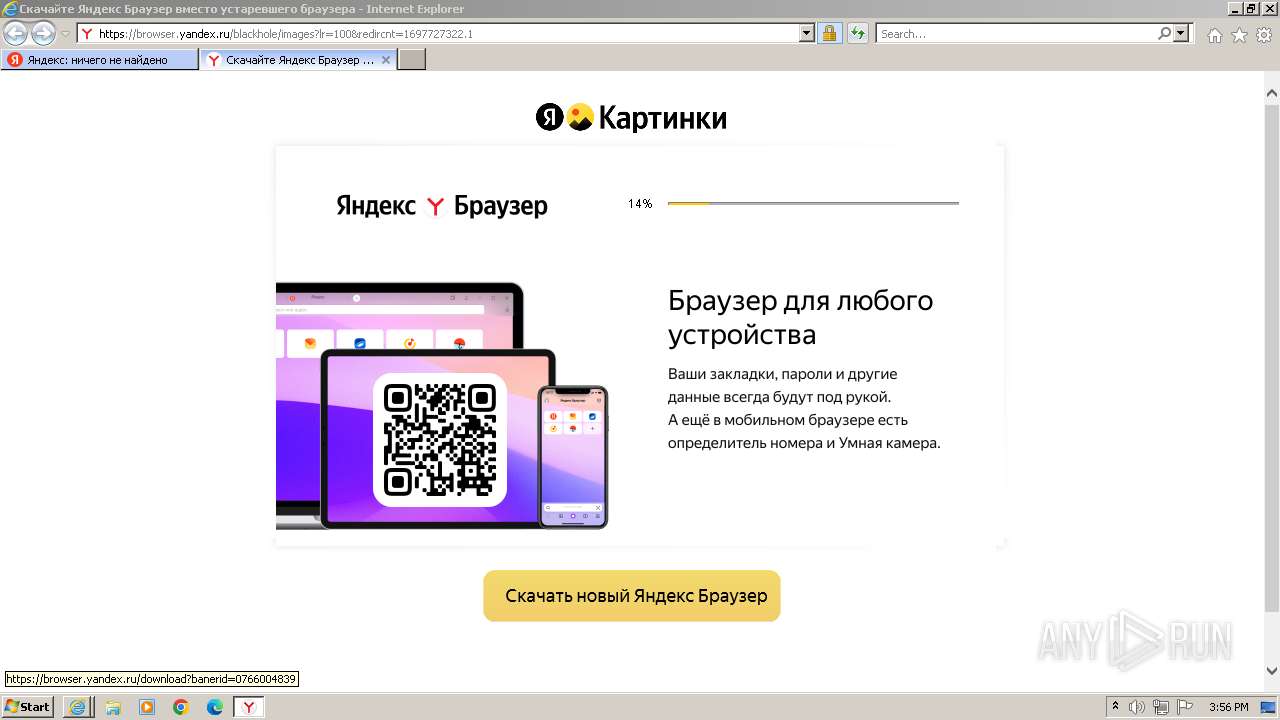
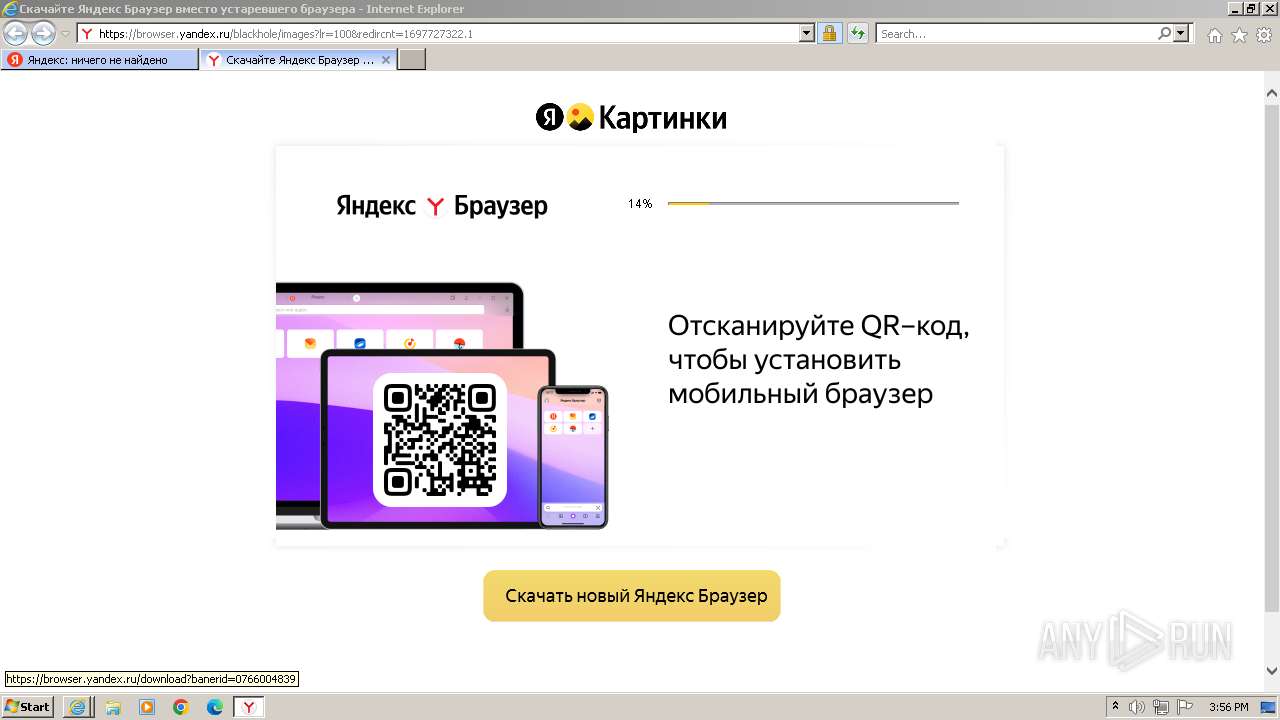
| 556 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://bs.yandex.ru" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
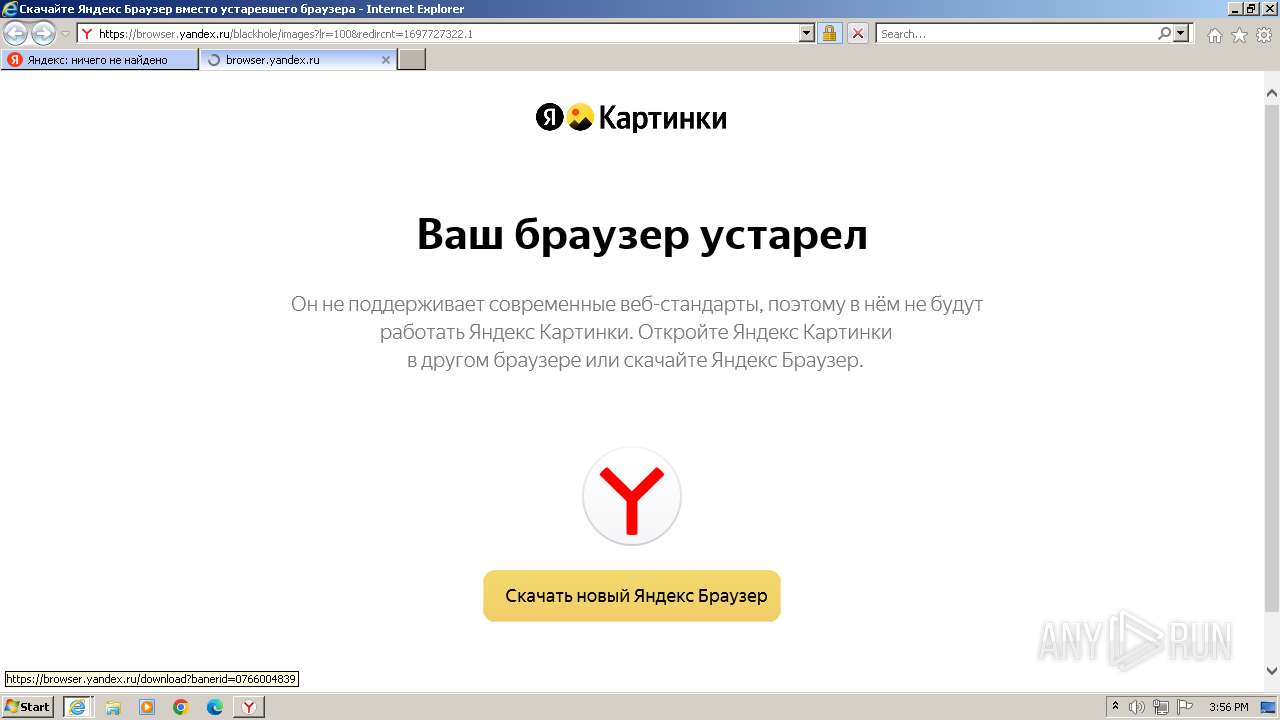
| 1432 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\Yandex.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\Yandex.exe | iexplore.exe | ||||||||||||
User: admin Company: YANDEX LLC Integrity Level: MEDIUM Description: Yandex Exit code: 0 Version: 23.9.3.936 Modules
| |||||||||||||||
| 1928 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\Yandex.exe" --parent-installer-process-id=1432 --run-as-admin --setup-cmd-line="fake_browser_arc --abt-config-resource-file=\"C:\Users\admin\AppData\Local\Temp\abt_config_resource\" --abt-update-path=\"C:\Users\admin\AppData\Local\Temp\cd350826-8e01-4018-8011-0238f00ddd3c.tmp\" --brand-name=yandex --distr-info-file=\"C:\Users\admin\AppData\Local\Temp\distrib_info\" --make-browser-default-after-import --ok-button-pressed-time=2134653320 --progress-window=131904 --send-statistics --variations-update-path=\"C:\Users\admin\AppData\Local\Temp\66f801de-f283-4117-a022-0e57a718daf4.tmp\" --verbose-logging" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\Yandex.exe | Yandex.exe | ||||||||||||
User: admin Company: YANDEX LLC Integrity Level: HIGH Description: Yandex Exit code: 0 Version: 23.9.3.936 Modules
| |||||||||||||||
| 3248 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:556 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3716 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:556 CREDAT:1054000 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
35 716
Read events
35 510
Write events
198
Delete events
8
Modification events
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000056010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (556) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
5
Suspicious files
72
Text files
132
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3248 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0DA515F703BB9B49479E8697ADB0B955_7DAD5545724AA2C98C55095F428499FB | binary | |
MD5:80D8EEC0B8258778CCD0F565E6948A7B | SHA256:70B520DC24795210B674A83F189FAB6D9CE90DAB558285019A72E687F14EC9E6 | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\66F835E41EC6A985EB9271E4A70169D7_CF44E3C99F7F4AC558EEB35244F7E046 | binary | |
MD5:5B895CD51E8130795FCBC628C84729C0 | SHA256:6F3F0B424C47AF87817A8728DB073BEF0B169304DDB80227670393E7567D2928 | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\66F835E41EC6A985EB9271E4A70169D7_CF44E3C99F7F4AC558EEB35244F7E046 | binary | |
MD5:E76FCCFF3DAB1B5FF83FA66F2FED70BF | SHA256:DAB47D6F709BD3FF31944BE45B3393DF1AFFCCCED868B008C4E1470688A8245A | |||
| 556 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[2].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\0DA515F703BB9B49479E8697ADB0B955_7DAD5545724AA2C98C55095F428499FB | binary | |
MD5:740C40D7F20842AA38E5BBD7124A3A94 | SHA256:B6CCC62E41C957438FB7590695761E9E20D63312A28528C10217081D34312F02 | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:4D1A8D93E4368E23742623105B4F2476 | SHA256:F99F9767FE1AAA9ABA2105C664EE3B0BB468120289B9CC3090F720C6434912AB | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\81B9B36F9ABC4DA631A4713EE66FAEC6_29FE8CD43EAA1639E5932AC185712964 | binary | |
MD5:59C06CB36E6D1F1E54BC2F4371692878 | SHA256:5A871D2F3F5675A32C35EB0658D8066B7EE89B32084FDDAC9033FDEFD52EC93A | |||
| 556 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 556 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
98
DNS requests
39
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3248 | iexplore.exe | GET | 200 | 72.21.81.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8f869686e34b7eef | unknown | compressed | 4.66 Kb | unknown |
3248 | iexplore.exe | GET | 200 | 146.75.122.133:80 | http://ocsp.globalsign.com/gseccovsslca2018/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBSTMjK03nNiYoQYvu4Izyfn9OJNdAQUWHuOdSr%2BYYCqkEABrtboB0ZuP0gCDENqNL2NzdqQCxTmkQ%3D%3D | unknown | binary | 938 b | unknown |
3248 | iexplore.exe | GET | 200 | 146.75.122.133:80 | http://ocsp2.globalsign.com/rootr3/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCDQHuXyId%2FGI71DM6hVc%3D | unknown | binary | 1.40 Kb | unknown |
3248 | iexplore.exe | GET | 200 | 72.21.81.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f8f3bf607e1d79ae | unknown | compressed | 4.66 Kb | unknown |
3248 | iexplore.exe | GET | 200 | 146.75.122.133:80 | http://ocsp.globalsign.com/rootr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDQHuXxad%2F5c1K2Rl1mo%3D | unknown | binary | 1.41 Kb | unknown |
3248 | iexplore.exe | GET | 200 | 146.75.122.133:80 | http://ocsp.globalsign.com/gsrsaovsslca2018/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBRrcGT%2BanRD3C1tW3nsrKeuXC7DPwQU%2BO9%2F8s14Z6jeb48kjYjxhwMCs%2BsCDGRXYw0qv%2BdJBvJ6dg%3D%3D | unknown | binary | 1.40 Kb | unknown |
3248 | iexplore.exe | GET | 200 | 146.75.122.133:80 | http://ocsp.globalsign.com/gsrsaovsslca2018/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBRrcGT%2BanRD3C1tW3nsrKeuXC7DPwQU%2BO9%2F8s14Z6jeb48kjYjxhwMCs%2BsCDGegxaUvIZsHU9x8DA%3D%3D | unknown | binary | 1.40 Kb | unknown |
556 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
3248 | iexplore.exe | GET | 200 | 146.75.122.133:80 | http://ocsp.globalsign.com/gseccovsslca2018/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBSTMjK03nNiYoQYvu4Izyfn9OJNdAQUWHuOdSr%2BYYCqkEABrtboB0ZuP0gCDEHsohnj8sQ7zjdN1w%3D%3D | unknown | binary | 939 b | unknown |
556 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3248 | iexplore.exe | 77.88.21.90:443 | — | YANDEX LLC | RU | whitelisted |
3248 | iexplore.exe | 72.21.81.240:80 | ctldl.windowsupdate.com | EDGECAST | US | whitelisted |
3248 | iexplore.exe | 146.75.122.133:80 | ocsp.globalsign.com | FASTLY | US | unknown |
556 | iexplore.exe | 23.53.43.176:443 | www.bing.com | Akamai International B.V. | DE | unknown |
556 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
556 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
3248 | iexplore.exe | 5.255.255.70:443 | yandex.ru | YANDEX LLC | RU | whitelisted |
3248 | iexplore.exe | 5.255.255.242:443 | ya.ru | YANDEX LLC | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
yandex.ru |
| whitelisted |
ya.ru |
| whitelisted |