| URL: | https://any.run/ |
| Full analysis: | https://app.any.run/tasks/a679d3da-e511-44d2-b679-e84351fa8fde |
| Verdict: | Malicious activity |
| Analysis date: | August 09, 2020, 02:04:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | ECCF006CD5014DAF32D8D75278D844DC |
| SHA1: | 813BB606577B4BD57FD32D26B78E91DBD7CF7BE9 |
| SHA256: | DABE4C5B2A89F3B94F3B526D71242FCABE9C37D229696FF294B058BA6B0C5E21 |
| SSDEEP: | 3:N8lF:2lF |
MALICIOUS
Application was dropped or rewritten from another process
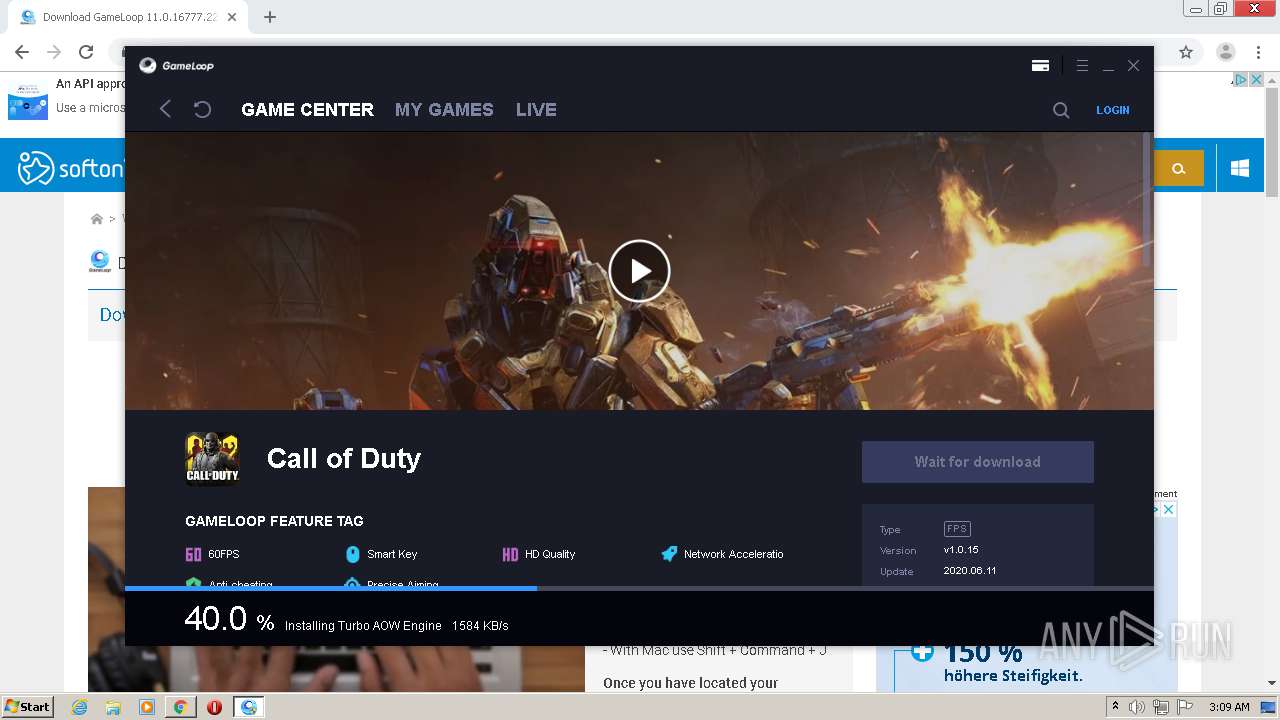
- Gameloop_Download_SpecialPackage.exe (PID: 2872)
- Gameloop_Download_SpecialPackage.exe (PID: 2904)
- TenioDL.exe (PID: 5000)
- QMEmulatorService.exe (PID: 4316)
- Tinst.exe (PID: 3940)
- TBSWebRenderer.exe (PID: 3500)
- AppMarket.exe (PID: 4896)
- GameDownload.exe (PID: 4968)
- TenioDL.exe (PID: 5216)
Loads dropped or rewritten executable
- Gameloop_Download_SpecialPackage.exe (PID: 2904)
- TenioDL.exe (PID: 5000)
- QMEmulatorService.exe (PID: 4316)
- AppMarket.exe (PID: 4896)
- TBSWebRenderer.exe (PID: 3500)
- GameDownload.exe (PID: 4968)
Changes settings of System certificates
- Gameloop_Download_SpecialPackage.exe (PID: 2904)
- AppMarket.exe (PID: 4896)
- GameDownload.exe (PID: 4968)
Adds new firewall rule via NETSH.EXE
- Tinst.exe (PID: 3940)
Actions looks like stealing of personal data
- AppMarket.exe (PID: 4896)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 2592)
- chrome.exe (PID: 2488)
- Gameloop_Download_SpecialPackage.exe (PID: 2904)
- Market.exe (PID: 4240)
- GameDownload.exe (PID: 4968)
- Tinst.exe (PID: 3940)
Creates files in the user directory
- TenioDL.exe (PID: 5000)
- Gameloop_Download_SpecialPackage.exe (PID: 2904)
- AppMarket.exe (PID: 4896)
Low-level read access rights to disk partition
- Gameloop_Download_SpecialPackage.exe (PID: 2904)
- QMEmulatorService.exe (PID: 4316)
- AppMarket.exe (PID: 4896)
- GameDownload.exe (PID: 4968)
Executed as Windows Service
- QMEmulatorService.exe (PID: 4316)
Creates files in the program directory
- QMEmulatorService.exe (PID: 4316)
- AppMarket.exe (PID: 4896)
- Gameloop_Download_SpecialPackage.exe (PID: 2904)
- Tinst.exe (PID: 3940)
Reads Internet Cache Settings
- Gameloop_Download_SpecialPackage.exe (PID: 2904)
- GameDownload.exe (PID: 4968)
Uses NETSH.EXE for network configuration
- Tinst.exe (PID: 3940)
- Gameloop_Download_SpecialPackage.exe (PID: 2904)
Creates files in the Windows directory
- QMEmulatorService.exe (PID: 4316)
Modifies the open verb of a shell class
- Tinst.exe (PID: 3940)
Creates a software uninstall entry
- Tinst.exe (PID: 3940)
Adds / modifies Windows certificates
- AppMarket.exe (PID: 4896)
- GameDownload.exe (PID: 4968)
Uses ICACLS.EXE to modify access control list
- TenioDL.exe (PID: 5000)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2812)
- iexplore.exe (PID: 892)
- chrome.exe (PID: 2592)
Application launched itself
- iexplore.exe (PID: 2812)
- chrome.exe (PID: 2592)
Changes internet zones settings
- iexplore.exe (PID: 2812)
Reads settings of System Certificates
- iexplore.exe (PID: 892)
- chrome.exe (PID: 2488)
- Gameloop_Download_SpecialPackage.exe (PID: 2904)
- TBSWebRenderer.exe (PID: 3500)
- GameDownload.exe (PID: 4968)
Reads internet explorer settings
- iexplore.exe (PID: 892)
Manual execution by user
- chrome.exe (PID: 2592)
Reads the hosts file
- chrome.exe (PID: 2592)
- chrome.exe (PID: 2488)
- Gameloop_Download_SpecialPackage.exe (PID: 2904)
- AppMarket.exe (PID: 4896)
- GameDownload.exe (PID: 4968)
Creates files in the user directory
- iexplore.exe (PID: 892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
142
Monitored processes
90
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,1137715023569309274,8201008339025730913,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7451000538127550204 --renderer-client-id=58 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5340 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 892 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2812 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 956 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,1137715023569309274,8201008339025730913,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17826709498996535634 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2252 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 976 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,1137715023569309274,8201008339025730913,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3221275583582408171 --renderer-client-id=19 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3628 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1120 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,1137715023569309274,8201008339025730913,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11193731095794466189 --renderer-client-id=37 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5056 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1256 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,1137715023569309274,8201008339025730913,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=14144793012888676523 --mojo-platform-channel-handle=3396 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1328 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,1137715023569309274,8201008339025730913,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=5561588957623279421 --mojo-platform-channel-handle=1220 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1352 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,1137715023569309274,8201008339025730913,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=14289966765169476484 --mojo-platform-channel-handle=6828 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1388 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,1137715023569309274,8201008339025730913,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9306700361113176536 --renderer-client-id=31 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2464 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1556 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,1137715023569309274,8201008339025730913,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=7663822998143574213 --mojo-platform-channel-handle=2568 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
2 776
Read events
2 013
Write events
752
Delete events
11
Modification events
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 2388794510 | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30830065 | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A3000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2812) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
240
Suspicious files
515
Text files
2 022
Unknown types
68
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 892 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab14A7.tmp | — | |
MD5:— | SHA256:— | |||
| 892 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar14A8.tmp | — | |
MD5:— | SHA256:— | |||
| 892 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 892 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\stylesheetMain.min[1].css | text | |
MD5:— | SHA256:— | |||
| 892 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\3083[1].js | text | |
MD5:— | SHA256:— | |||
| 892 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\SPWVH57H.htm | html | |
MD5:— | SHA256:— | |||
| 892 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EDC238BFF48A31D55A97E1E93892934B_C20E0DA2D0F89FE526E1490F4A2EE5AB | binary | |
MD5:— | SHA256:— | |||
| 892 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 892 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\targetLine[1].png | image | |
MD5:— | SHA256:— | |||
| 892 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\MSIMGSIZ.DAT | smt | |
MD5:0392ADA071EB68355BED625D8F9695F3 | SHA256:B1313DD95EAF63F33F86F72F09E2ECD700D11159A8693210C37470FCB84038F7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
48
TCP/UDP connections
493
DNS requests
298
Threats
45
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5000 | TenioDL.exe | GET | — | 2.16.186.40:80 | http://dldir1.qq.com/syzs/oversea_component/Market_3.11.377.100.dat | unknown | — | — | whitelisted |
892 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
892 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAHBrC%2BxeCnHJwc5Xn74zbM%3D | US | der | 471 b | whitelisted |
2488 | chrome.exe | GET | 304 | 2.16.186.56:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | compressed | 56.7 Kb | whitelisted |
892 | iexplore.exe | GET | 200 | 172.217.23.131:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDM9j8%2B94pW6ggAAAAATZ8E | US | der | 472 b | whitelisted |
892 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
2488 | chrome.exe | GET | 304 | 2.16.186.56:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | compressed | 56.7 Kb | whitelisted |
892 | iexplore.exe | GET | 200 | 172.217.23.131:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDM9j8%2B94pW6ggAAAAATZ8E | US | der | 472 b | whitelisted |
892 | iexplore.exe | GET | 200 | 172.217.23.131:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
892 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEAEfVE26mm00vhn9fSedUSo%3D | US | der | 279 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
892 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
892 | iexplore.exe | 104.22.49.74:443 | any.run | Cloudflare Inc | US | malicious |
892 | iexplore.exe | 104.19.148.8:443 | script.crazyegg.com | Cloudflare Inc | US | shared |
892 | iexplore.exe | 185.60.216.35:443 | www.facebook.com | Facebook, Inc. | IE | whitelisted |
892 | iexplore.exe | 185.60.216.19:443 | connect.facebook.net | Facebook, Inc. | IE | whitelisted |
2812 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2488 | chrome.exe | 216.58.207.77:443 | accounts.google.com | Google Inc. | US | whitelisted |
2488 | chrome.exe | 172.217.18.163:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
892 | iexplore.exe | 172.217.23.131:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2488 | chrome.exe | 172.217.18.4:443 | www.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
any.run |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
script.crazyegg.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
connect.facebook.net |
| whitelisted |
www.facebook.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2904 | Gameloop_Download_SpecialPackage.exe | Generic Protocol Command Decode | SURICATA TLS error message encountered |
2904 | Gameloop_Download_SpecialPackage.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
2904 | Gameloop_Download_SpecialPackage.exe | Generic Protocol Command Decode | SURICATA TLS error message encountered |
5000 | TenioDL.exe | Generic Protocol Command Decode | ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag false change port flag false) |
5000 | TenioDL.exe | Generic Protocol Command Decode | ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag true change port flag false) |
5000 | TenioDL.exe | Generic Protocol Command Decode | ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag false change port flag true) |
— | — | Generic Protocol Command Decode | ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag false change port flag false) |
— | — | Generic Protocol Command Decode | ET INFO Session Traversal Utilities for NAT (STUN Binding Request obsolete rfc 3489 CHANGE-REQUEST attribute change IP flag false change port flag false) |
5000 | TenioDL.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2904 | Gameloop_Download_SpecialPackage.exe | Generic Protocol Command Decode | SURICATA TLS error message encountered |
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
Gameloop_Download_SpecialPackage.exe | [Downloader] GetLogicalDrives 4
|
Gameloop_Download_SpecialPackage.exe | [Downloader] DriverType C: = 3
|
Gameloop_Download_SpecialPackage.exe | [Downloader] GetLogicalDrives 4
|
Gameloop_Download_SpecialPackage.exe | [Downloader] DriverType C: = 3
|
AppMarket.exe | [0809/030749:INFO:exception_record.cc(518)] [QB]Process ID: 4896 Type: 1
|
TBSWebRenderer.exe | [0809/030754:INFO:exception_record.cc(518)] [QB]Process ID: 3500 Type: 2
|
GameDownload.exe | [Downloader] DriverType C: = 3
|
GameDownload.exe | [Downloader] GetLogicalDrives 4
|
GameDownload.exe | [Downloader] DriverType C: = 3
|
GameDownload.exe | [Downloader] GetLogicalDrives 4
|