| File name: | BOT.exe |
| Full analysis: | https://app.any.run/tasks/4184b3ff-f76a-460e-83ac-97e89b5775fc |
| Verdict: | Malicious activity |
| Analysis date: | July 11, 2019, 16:24:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 9DF57545AF2241C1101624161B245AC5 |
| SHA1: | 50DABCDF509ED7130DA0C1D91082C41AF282EFDE |
| SHA256: | DAB5146F6C7EBE3D04C4D903922C7202CE1AF89F126386E317C7DE88C8532C92 |
| SSDEEP: | 196608:9zq+29L+NJ6ZQLJG4otpRDXAU9lKeHb3dlhr1ksBFyeSMeM/DckywX:NpToTtpRDQU/LHb33CjVMQpS |
MALICIOUS
Loads dropped or rewritten executable
- BOT.exe (PID: 2156)
SUSPICIOUS
Reads Internet Cache Settings
- BOT.exe (PID: 2156)
Executable content was dropped or overwritten
- BOT.exe (PID: 2156)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:07:10 11:34:43+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 1444352 |
| InitializedDataSize: | 1150976 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6792b9 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 10-Jul-2019 09:34:43 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000118 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 10-Jul-2019 09:34:43 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00426000 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.mapo | 0x00681000 | 0x00022000 | 0x000216D0 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 6.36525 |
.rsrc | 0x0067B000 | 0x00006000 | 0x00006000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.81575 |
.mapo2 | 0x006A3000 | 0x0064F000 | 0x0064ECEA | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.94412 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.07695 | 461 | UNKNOWN | UNKNOWN | RT_MANIFEST |
2 | 2.18858 | 296 | UNKNOWN | Chinese - PRC | RT_ICON |
3 | 4.46587 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 2.74274 | 180 | UNKNOWN | Chinese - PRC | RT_CURSOR |
127 | 1.4183 | 12 | UNKNOWN | Chinese - PRC | RT_MENU |
150 | 3.06278 | 152 | UNKNOWN | Chinese - PRC | RT_DIALOG |
286 | 3.5561 | 378 | UNKNOWN | Chinese - PRC | RT_DIALOG |
554 | 3.78697 | 250 | UNKNOWN | Chinese - PRC | RT_DIALOG |
1031 | 3.67246 | 584 | UNKNOWN | Chinese - PRC | RT_BITMAP |
1032 | 1.91924 | 20 | UNKNOWN | Chinese - PRC | RT_GROUP_CURSOR |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
IPHLPAPI.DLL |
OLEAUT32.dll |
RASAPI32.dll |
SHELL32.dll |
SHLWAPI.dll |
Secur32.dll |
USER32.dll |
Total processes
32
Monitored processes
1
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2156 | "C:\Users\admin\AppData\Local\Temp\BOT.exe" | C:\Users\admin\AppData\Local\Temp\BOT.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
42
Read events
16
Write events
26
Delete events
0
Modification events
| (PID) Process: | (2156) BOT.exe | Key: | HKEY_CURRENT_USER\Software\Maposafe\27884263 |
| Operation: | write | Name: | GongGao |
Value: 372D31322020C1E8B3BF31B5E3D7F3D3D2BDABCEACBBA4B7FECEF1C6F731B7D6D6D3C4DACDEAB1CF0ACEACBBA4B7FECEF1C6F7A3ACB3F6CFD6B9EDC1B3D6D8D0C2B5C7C2BDBECDBFC9D2D4C1CB0AB9B7CDF5C6C6BDE2424F54A3A8C7BFC1D2CDC6BCF6A3A90AC8ABB7FECEF1C6F7C3EBD7A2C8EB30B9EDC1B330B1C0C0A30AC8E7B9FBC4E3B3F6CFD6B9EDC1B3B1C0C0A3A3ACCBB5C3F7B7FECEF1C6F7B3F6CFD6CECACCE20AC7EBB2BBD2AAD7C5BCB10A35B7D6D6D3D6AEC4DAD0DEB8B4A3ACD6D8D0C2B5C7C2BCBECDBAC3C1CB0A000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2156) BOT.exe | Key: | HKEY_CURRENT_USER\Software\Maposafe\27884263 |
| Operation: | write | Name: | SoftName |
Value: 50A20B009A5BB2C65FEC3F3847C0EB94033CE790FF38E38CFB34DF88F730DB84F32CD780EF28D37CEB24CF78E720CB74E31CC770DF18C36CDB14BF68D710BB64 | |||
| (PID) Process: | (2156) BOT.exe | Key: | HKEY_CURRENT_USER\Software\Maposafe\27884263 |
| Operation: | write | Name: | PayMethod |
Value: 4 | |||
| (PID) Process: | (2156) BOT.exe | Key: | HKEY_CURRENT_USER\Software\Maposafe\27884263 |
| Operation: | write | Name: | CardLink |
Value: | |||
| (PID) Process: | (2156) BOT.exe | Key: | HKEY_CURRENT_USER\Software\Maposafe\27884263 |
| Operation: | write | Name: | user |
Value: 746B396873326D637162723237716E6F316B787563336D616E336D747271336B0000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2156) BOT.exe | Key: | HKEY_CURRENT_USER\Software\Maposafe\27884263 |
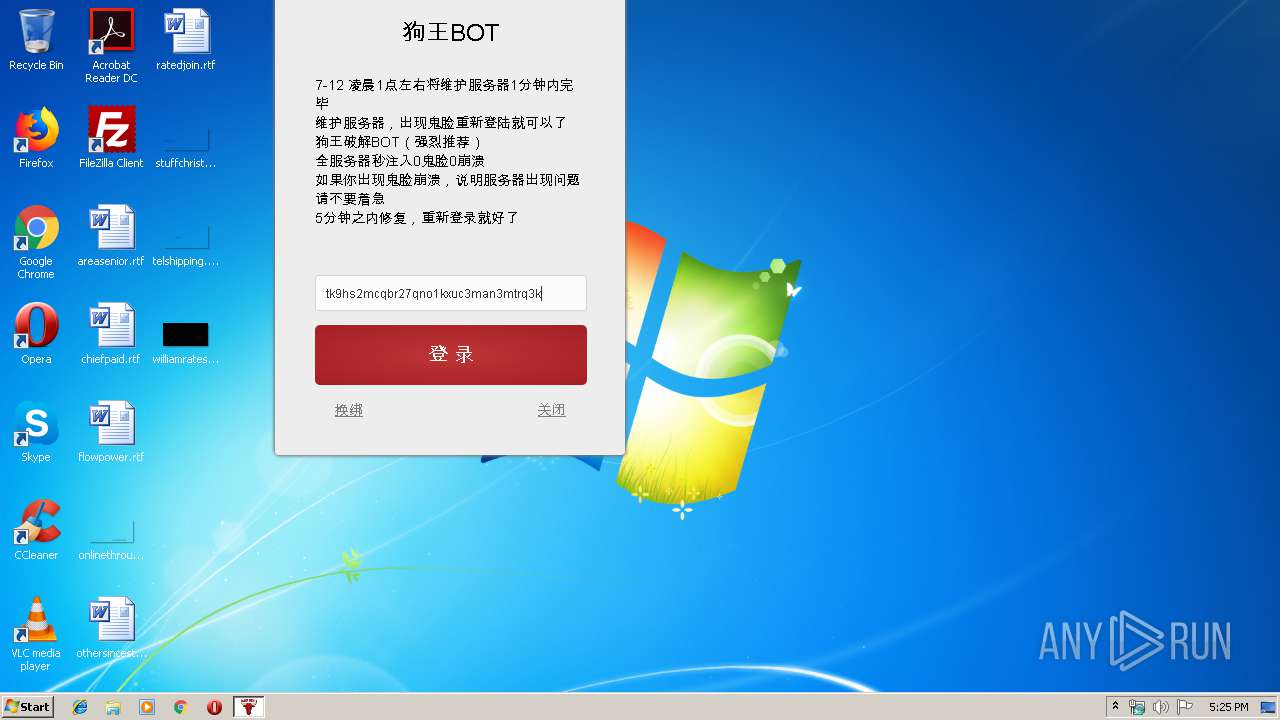
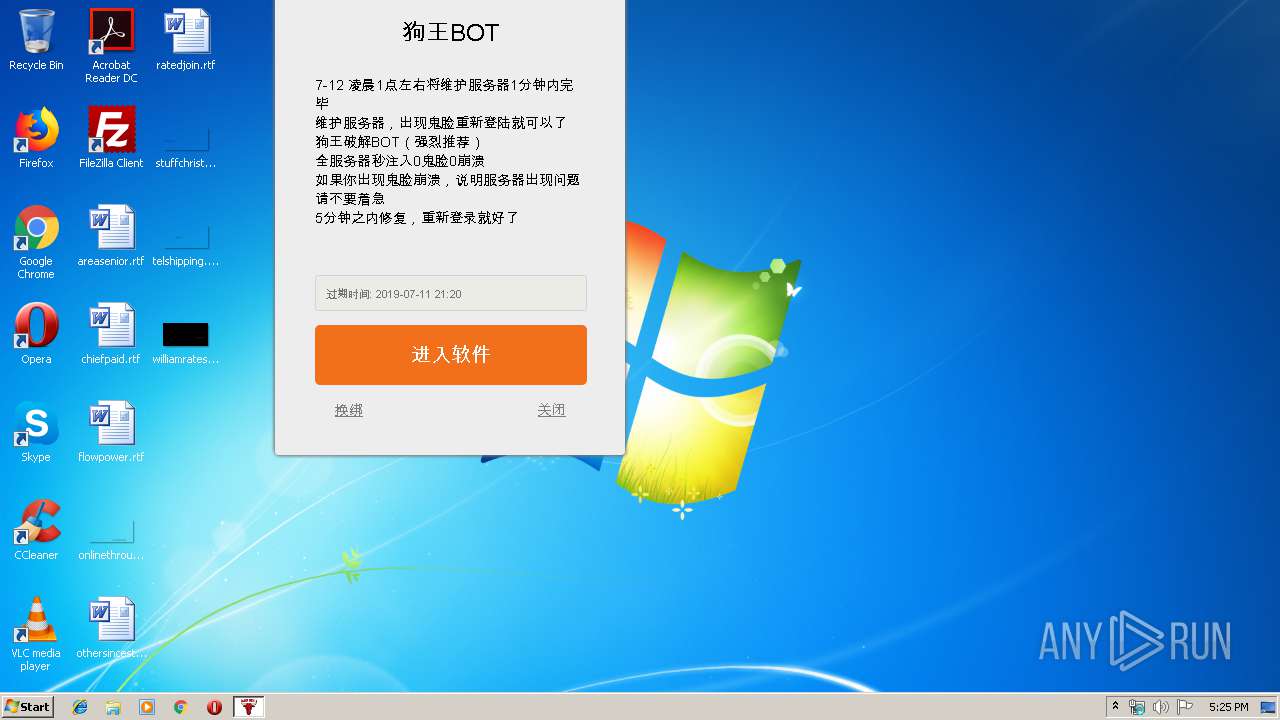
| Operation: | write | Name: | expire |
Value: 2019-07-11 21:20 | |||
| (PID) Process: | (2156) BOT.exe | Key: | HKEY_CURRENT_USER\Software\Maposafe\27884263 |
| Operation: | write | Name: | remember |
Value: 1 | |||
| (PID) Process: | (2156) BOT.exe | Key: | HKEY_CURRENT_USER\Software\Maposafe\27884263 |
| Operation: | write | Name: | password |
Value: 7ea4686365276e2ab944e2b8ded67e6c | |||
| (PID) Process: | (2156) BOT.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\BOT_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2156) BOT.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\BOT_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2156 | BOT.exe | C:\Users\admin\AppData\Local\Temp\16fc27.tmp | — | |
MD5:— | SHA256:— | |||
| 2156 | BOT.exe | C:\Users\admin\AppData\Local\Temp\16fc37.tmp | — | |
MD5:— | SHA256:— | |||
| 2156 | BOT.exe | C:\Users\admin\AppData\Local\Temp\1476593\12376.dll | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
8
DNS requests
7
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2156 | BOT.exe | GET | — | 218.93.206.121:888 | http://218.93.206.121:888/L(7~.dll | CN | — | — | malicious |
2156 | BOT.exe | POST | — | 120.41.41.9:80 | http://ieqgmccbgb66pn86.soft.maposafe.com/wx.php | CN | — | — | malicious |
2156 | BOT.exe | POST | — | 120.41.41.9:80 | http://ieqgmccbgb66pn86.soft.maposafe.com/wx.php | CN | — | — | malicious |
2156 | BOT.exe | POST | — | 111.231.222.16:80 | http://baklogin2.maposafe.mapoprotect.com/wx.php | CN | — | — | malicious |
2156 | BOT.exe | POST | — | 120.41.41.9:80 | http://ieqgmccbgb66pn86.soft.maposafe.com/wx.php | CN | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2156 | BOT.exe | 120.41.41.9:80 | ieqgmccbgb66pn86.soft.maposafe.com | Xiamen | CN | malicious |
2156 | BOT.exe | 123.129.217.246:80 | baklogin.maposafe.mapoprotect.com | CHINA UNICOM China169 Backbone | CN | malicious |
2156 | BOT.exe | 111.231.222.16:80 | baklogin2.maposafe.mapoprotect.com | Shenzhen Tencent Computer Systems Company Limited | CN | malicious |
2156 | BOT.exe | 218.93.206.121:3600 | — | No.31,Jin-rong Street | CN | malicious |
— | — | 218.93.206.121:888 | — | No.31,Jin-rong Street | CN | malicious |
— | — | 120.41.41.9:80 | ieqgmccbgb66pn86.soft.maposafe.com | Xiamen | CN | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ieqgmccbgb66pn86.soft.maposafe.com |
| unknown |
baklogin.maposafe.mapoprotect.com |
| malicious |
baklogin2.maposafe.mapoprotect.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2156 | BOT.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojWare.Win32.Agent.ISVQ server response (HackingTeam) |
2156 | BOT.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojWare.Win32.Agent.ISVQ server response (HackingTeam) |
2156 | BOT.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojWare.Win32.Agent.ISVQ server response (HackingTeam) |
2156 | BOT.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojWare.Win32.Agent.ISVQ server response (HackingTeam) |
2156 | BOT.exe | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Windows NT Version 5.0 |
Process | Message |
|---|---|
BOT.exe | scrt_initialize_thread_safe_statics
|
BOT.exe | WebPageImpl::init: 01EAB7C0
|
BOT.exe | GetFromBuf Error:file:///C:/Users/admin/AppData/Local/Temp/ui/custom.css |
BOT.exe | isLocalFileNotExist: C:\Users\admin\AppData\Local\Temp\ui\custom.css
|
BOT.exe | Console:[1],[Uncaught SyntaxError: Unexpected token ILLEGAL],[cwebview::runJS]
|
BOT.exe | WebPageImpl::~WebPageImpl: 01EAB7C0
|