| URL: | www.barthauer.de |
| Full analysis: | https://app.any.run/tasks/a52a2c43-1cda-4176-9ba8-8f63c6a15aa1 |
| Verdict: | Malicious activity |
| Analysis date: | December 10, 2025, 16:31:47 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C229E0101DC75B9AC68455F7B3FE5C8F |
| SHA1: | 908CE97BAA5764DDF98C8E8821A585A051CA9EEC |
| SHA256: | DAB009339949A8D6009D0ABCBAC904F4ADCA75A3DAF63FFF4B4A555B93BCFEC4 |
| SSDEEP: | 3:EKWQsAn:rWQh |
MALICIOUS
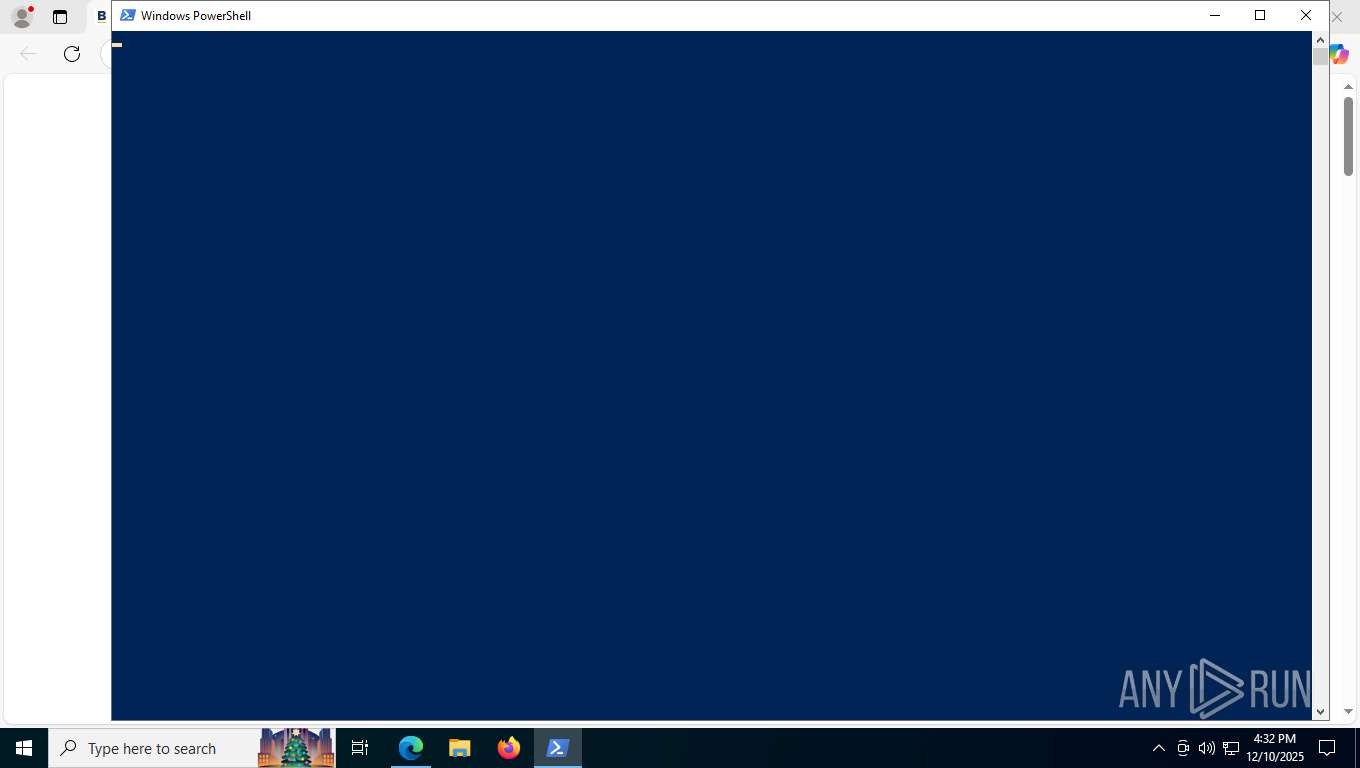
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 2488)
Reads a specific registry key of the VM
- powershell.exe (PID: 2488)
SUSPICIOUS
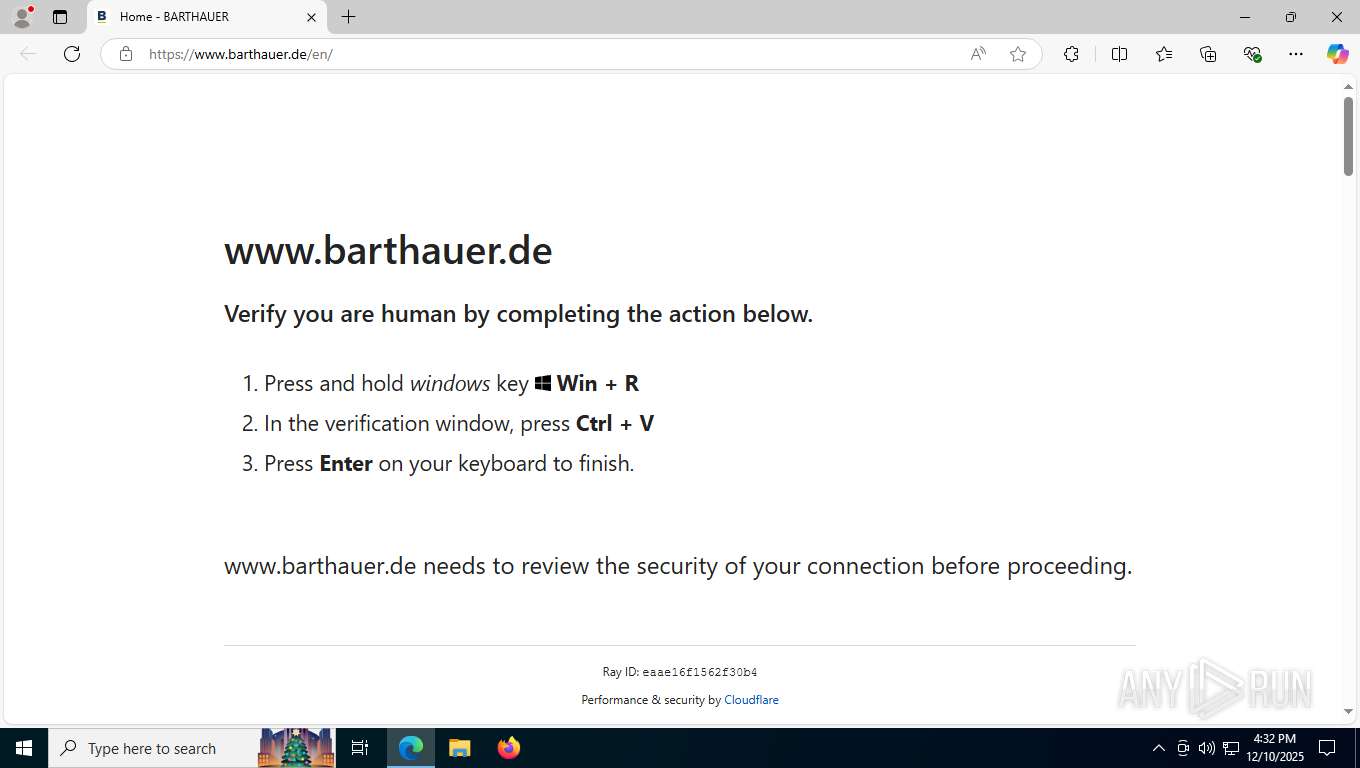
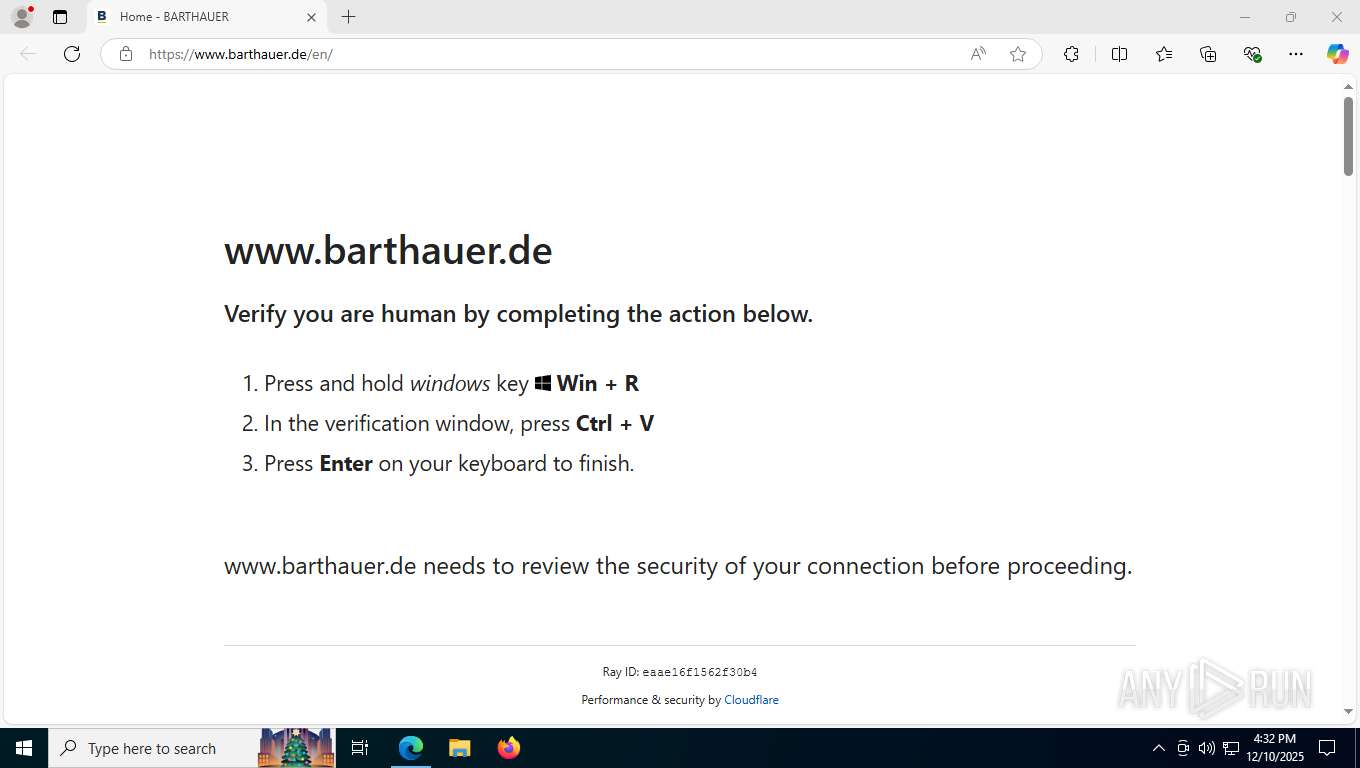
Suspicious clipboard command
- [System Process] (PID: 0)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 2488)
CSC.EXE is used to compile C# code
- csc.exe (PID: 7288)
- csc.exe (PID: 8520)
Executable content was dropped or overwritten
- csc.exe (PID: 8520)
- csc.exe (PID: 7288)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 2488)
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 2488)
Converts a string into array of characters (POWERSHELL)
- powershell.exe (PID: 2488)
Reads the BIOS version
- powershell.exe (PID: 2488)
Connects to unusual port
- powershell.exe (PID: 2488)
Possible stealing of FTP data
- powershell.exe (PID: 2488)
Reverses array data (POWERSHELL)
- powershell.exe (PID: 2488)
INFO
Application launched itself
- msedge.exe (PID: 7408)
Reads the computer name
- identity_helper.exe (PID: 7272)
- TextInputHost.exe (PID: 7244)
Checks supported languages
- identity_helper.exe (PID: 7272)
- TextInputHost.exe (PID: 7244)
- cvtres.exe (PID: 2680)
- csc.exe (PID: 8520)
- cvtres.exe (PID: 8540)
- csc.exe (PID: 7288)
Reads Environment values
- identity_helper.exe (PID: 7272)
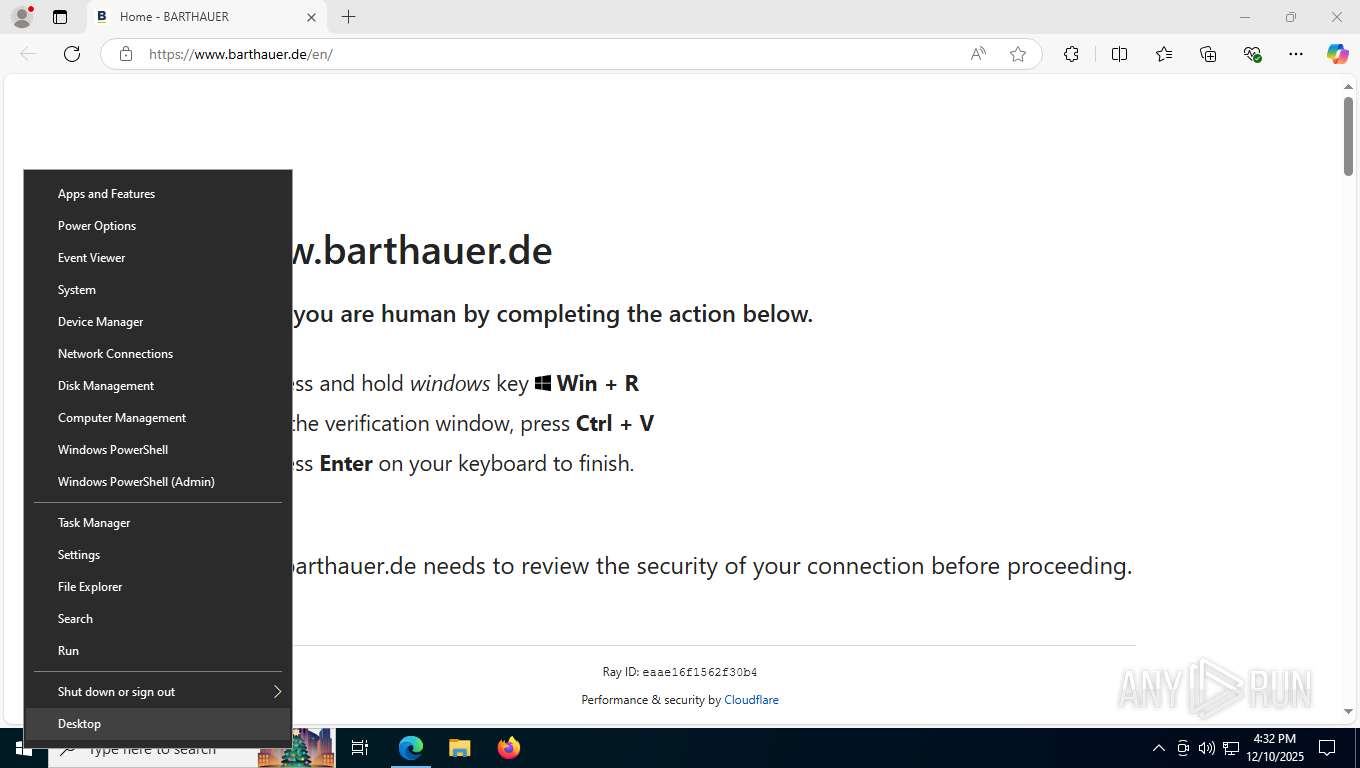
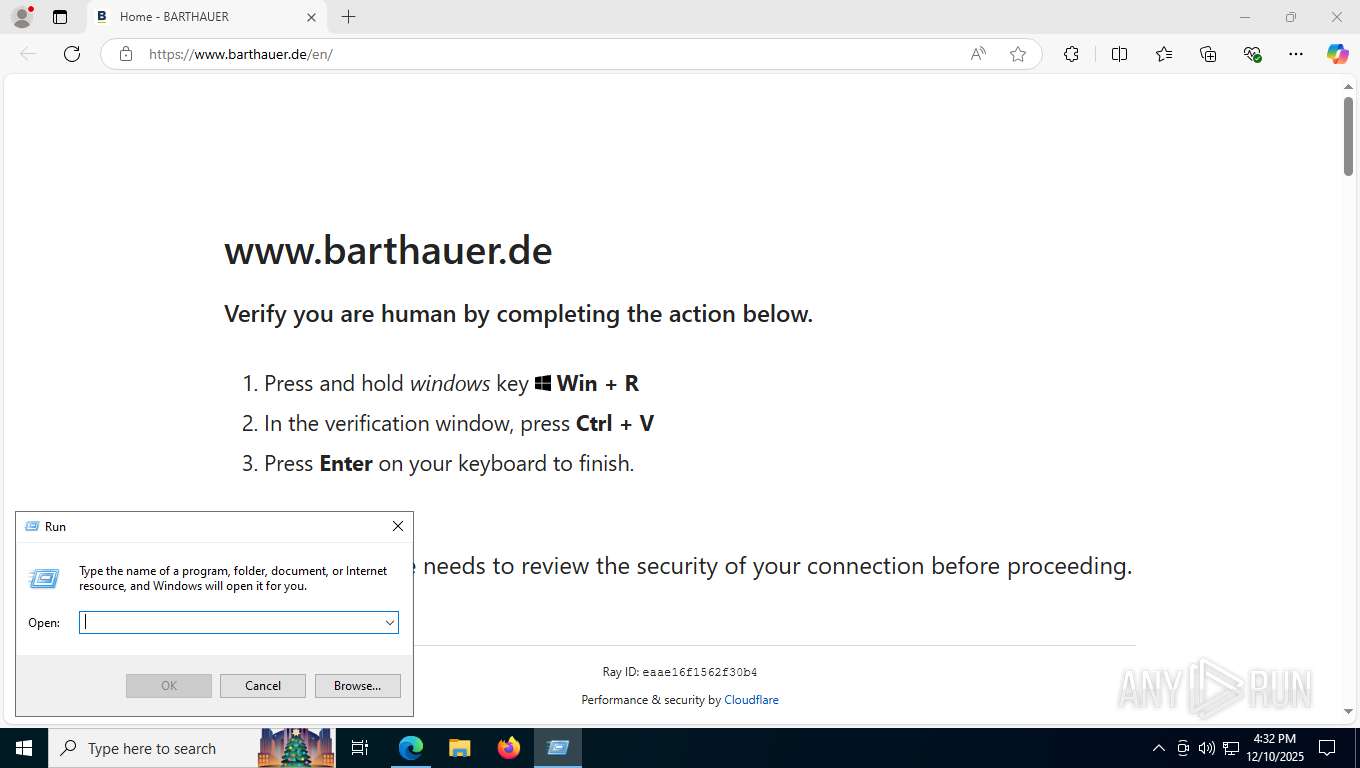
Manual execution by a user
- powershell.exe (PID: 2488)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 2488)
The Powershell gets current clipboard
- powershell.exe (PID: 2488)
Reads the machine GUID from the registry
- csc.exe (PID: 7288)
- csc.exe (PID: 8520)
Disables trace logs
- powershell.exe (PID: 2488)
Create files in a temporary directory
- cvtres.exe (PID: 2680)
- cvtres.exe (PID: 8540)
- csc.exe (PID: 7288)
- csc.exe (PID: 8520)
Checks proxy server information
- powershell.exe (PID: 2488)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 2488)
Gets data length (POWERSHELL)
- powershell.exe (PID: 2488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
174
Monitored processes
32
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0 | [System Process] | [System Process] | |||||||||||||
Integrity Level: UNKNOWN | |||||||||||||||
| 756 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1980 | "C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5784,i,14981721429595253578,2206545772855199849,262144 --variations-seed-version --mojo-platform-channel-handle=5692 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2016 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6060,i,14981721429595253578,2206545772855199849,262144 --variations-seed-version --mojo-platform-channel-handle=5876 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2416 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6792,i,14981721429595253578,2206545772855199849,262144 --variations-seed-version --mojo-platform-channel-handle=6576 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2488 | "C:\WINDOWS\system32\WindowsPowerShell\v1.0\PowerShell.exe" -c "Invoke-Expression(([System.Text.StringBuilder]::new((Get-Clipboard -Raw))).Remove(0, 256).ToString());" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2680 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESDB82.tmp" "c:\Users\admin\AppData\Local\Temp\CSCD73D6B9FC7564950896AB1D479956BE.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 5900 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5264,i,14981721429595253578,2206545772855199849,262144 --variations-seed-version --mojo-platform-channel-handle=5244 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 6408 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_xpay_wallet.mojom.EdgeXPayWalletService --lang=en-US --service-sandbox-type=utility --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=4480,i,14981721429595253578,2206545772855199849,262144 --variations-seed-version --mojo-platform-channel-handle=6728 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 6440 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=audio.mojom.AudioService --lang=en-US --service-sandbox-type=audio --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6740,i,14981721429595253578,2206545772855199849,262144 --variations-seed-version --mojo-platform-channel-handle=5816 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
10 841
Read events
10 841
Write events
0
Delete events
0
Modification events
Executable files
8
Suspicious files
326
Text files
82
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7408 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RFf67c9.TMP | — | |
MD5:— | SHA256:— | |||
| 7408 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7408 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RFf67e8.TMP | — | |
MD5:— | SHA256:— | |||
| 7408 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7408 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RFf67e8.TMP | — | |
MD5:— | SHA256:— | |||
| 7408 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7408 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RFf67f8.TMP | — | |
MD5:— | SHA256:— | |||
| 7408 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RFf67e8.TMP | — | |
MD5:— | SHA256:— | |||
| 7408 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7408 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
135
TCP/UDP connections
81
DNS requests
74
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7728 | msedge.exe | GET | 302 | 157.97.38.207:443 | https://www.barthauer.de/ | unknown | — | — | unknown |
7728 | msedge.exe | GET | — | 157.97.38.207:443 | https://www.barthauer.de/en/ | unknown | — | — | unknown |
7728 | msedge.exe | GET | 302 | 157.97.38.207:443 | https://www.barthauer.de/ | unknown | — | — | unknown |
7728 | msedge.exe | GET | 304 | 150.171.28.11:443 | https://edge.microsoft.com/abusiveadblocking/api/v1/blocklist | unknown | — | — | unknown |
7728 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:8MkBQ58GEMYUcXGBqjTYvZe9bTmLmrXaV_VkOMLibPA&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
7728 | msedge.exe | GET | 200 | 150.171.22.17:443 | https://config.edge.skype.com/config/v1/Edge/133.0.3065.92?clientId=4489578223053569932&agents=EdgeFirstRun%2CEdgeFirstRunConfig&osname=win&client=edge&channel=stable&scpfre=0&osarch=x86_64&osver=10.0.19045&wu=1&devicefamily=desktop&uma=0&sessionid=65&mngd=0&installdate=1661339457&edu=0&soobedate=1504771245&bphint=2&fg=1&lbfgdate=1741678270&lafgdate=0 | unknown | binary | 768 b | whitelisted |
7728 | msedge.exe | GET | 200 | 150.171.22.17:443 | https://config.edge.skype.com/config/v1/Edge/133.0.3065.92?clientId=4489578223053569932&agents=Edge%2CEdgeConfig%2CEdgeServices%2CEdgeFirstRun%2CEdgeFirstRunConfig&osname=win&client=edge&channel=stable&scpfre=0&osarch=x86_64&osver=10.0.19045&wu=1&devicefamily=desktop&uma=0&sessionid=65&mngd=0&installdate=1661339457&edu=0&soobedate=1504771245&bphint=2&fg=1&lbfgdate=1765384314&lafgdate=0 | unknown | binary | 4.65 Kb | whitelisted |
7728 | msedge.exe | GET | 200 | 150.171.22.17:443 | https://config.edge.skype.com/config/v1/Edge/133.0.3065.92?clientId=4489578223053569932&agents=EdgeRuntime%2CEdgeRuntimeConfig%2CEdgeDomainActions&osname=win&client=edge&channel=stable&scpfre=0&osarch=x86_64&osver=10.0.19045&wu=1&devicefamily=desktop&uma=0&sessionid=65&mngd=0&installdate=1661339457&edu=0&soobedate=1504771245&bphint=2&fg=1&lbfgdate=1765384314&lafgdate=0 | unknown | binary | 41.3 Kb | whitelisted |
7728 | msedge.exe | GET | 200 | 150.171.27.11:443 | https://edge.microsoft.com/entityextractiontemplates/api/v1/assets/find-assets?name=arbitration_priority_list&version=24.*.*&channel=stable&key=d414dd4f9db345fa8003e32adc81b362 | unknown | text | 271 b | whitelisted |
7728 | msedge.exe | GET | 200 | 104.18.22.222:443 | https://copilot.microsoft.com/c/api/user/eligibility | unknown | binary | 25 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | Not routed | — | whitelisted |
5984 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4992 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6768 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | Not routed | — | whitelisted |
7728 | msedge.exe | 150.171.22.17:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7728 | msedge.exe | 150.171.27.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7728 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7728 | msedge.exe | 157.97.38.207:80 | www.barthauer.de | MITTWALD-AS Mittwald CM Service GmbH und Co. KG | DE | unknown |
7728 | msedge.exe | 104.18.22.222:443 | copilot.microsoft.com | CLOUDFLARENET | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
www.barthauer.de |
| unknown |
copilot.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
clients2.googleusercontent.com |
| whitelisted |
edgeassetservice.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
7728 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Pages platform for frontend developers to collaborate and deploy websites (pages .dev) |
7728 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Pages platform for frontend developers to collaborate and deploy websites (pages .dev) |
7728 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7728 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7728 | msedge.exe | Misc activity | ET INFO Observed Cloudflare Page Developer Domain (pages .dev in TLS SNI) |
7728 | msedge.exe | Misc activity | ET INFO DNS Query to Cloudflare Page Developer Domain (pages .dev) |
7728 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7728 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7728 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Pages platform for frontend developers to collaborate and deploy websites (pages .dev) |