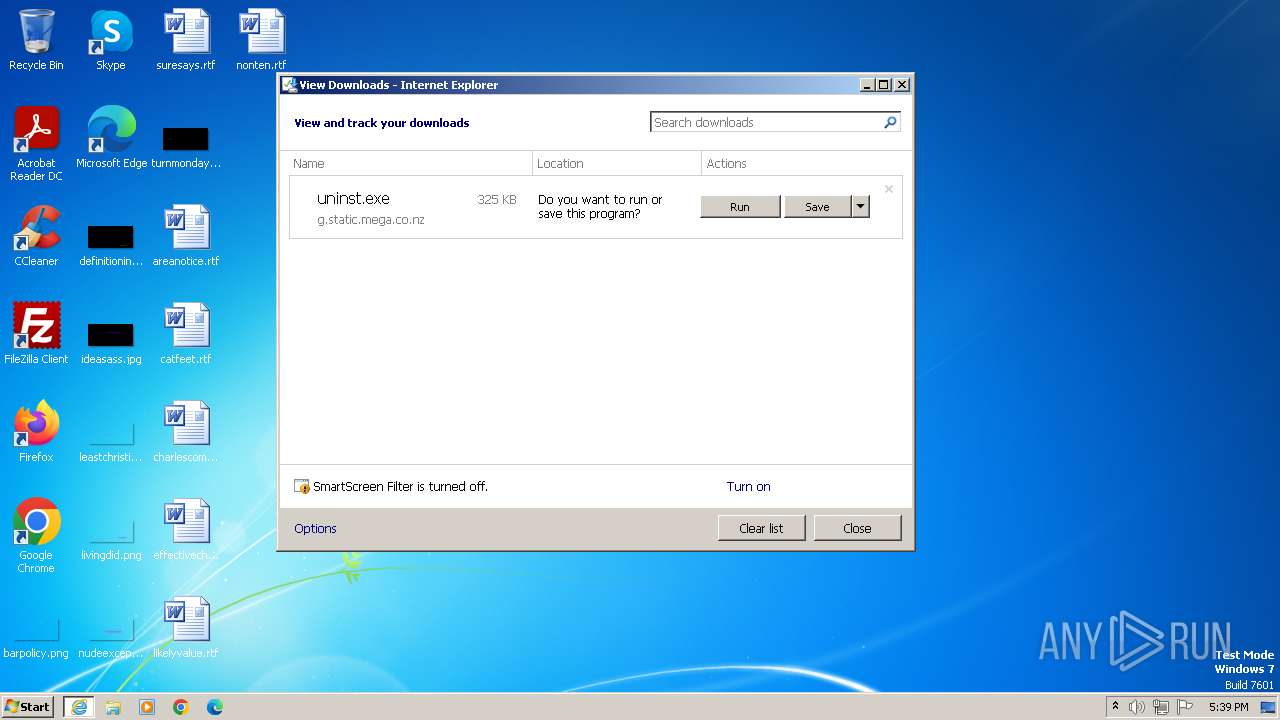
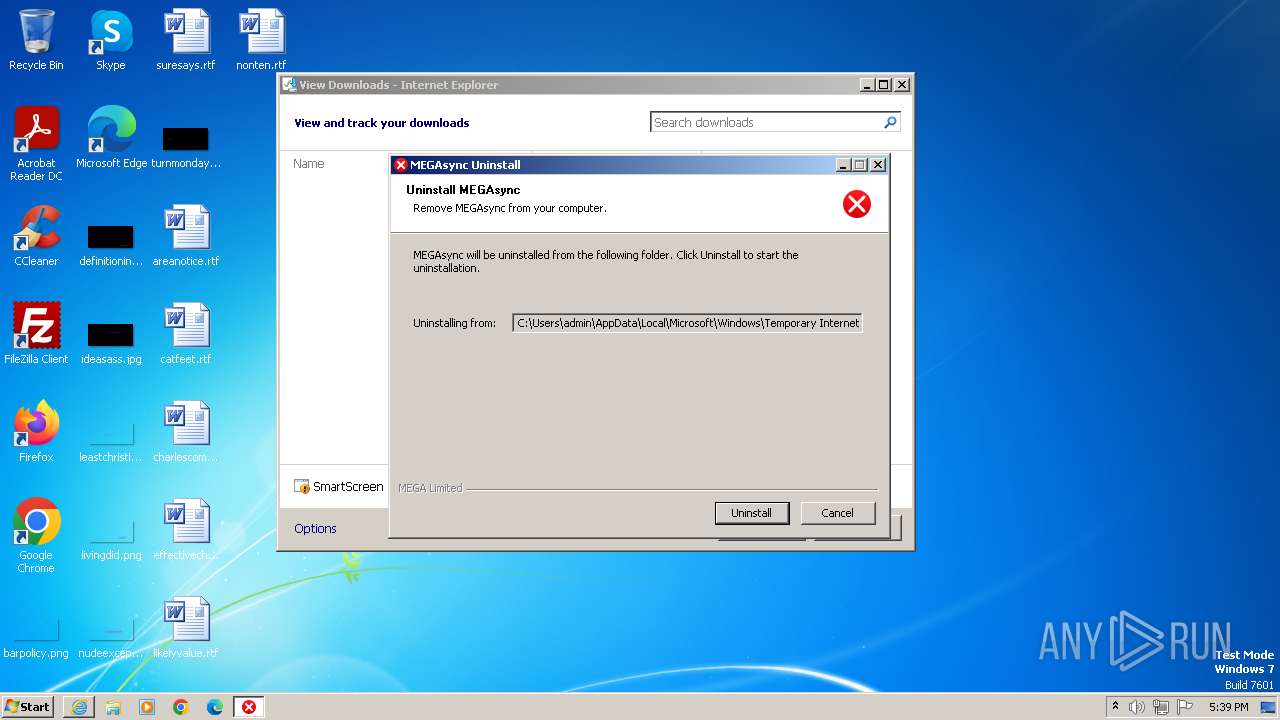
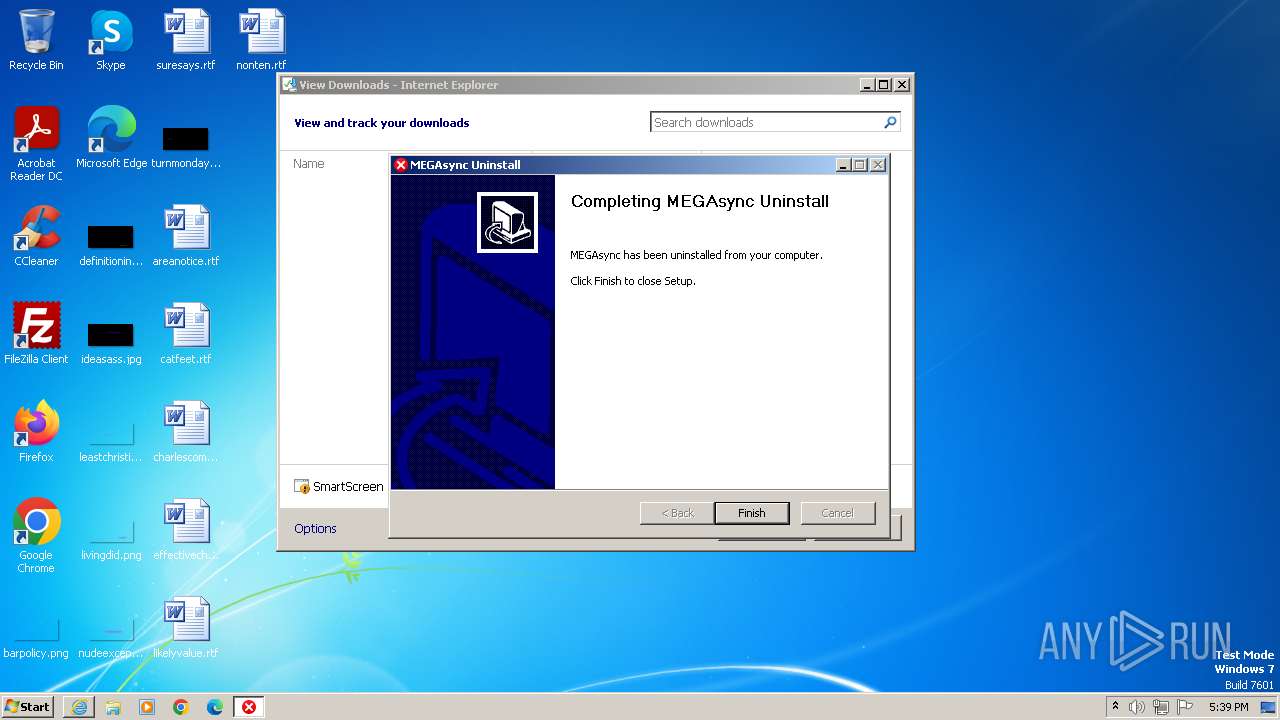
| URL: | http://g.static.mega.co.nz/upd/wsync64/uninst.exe |
| Full analysis: | https://app.any.run/tasks/c3b11c01-2862-4adc-9c3d-0be4e1a2e15b |
| Verdict: | Malicious activity |
| Analysis date: | October 30, 2023, 17:39:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | EC0AAC75B0CC7D9856043F293D7F7F2ABBD9F151 |
| SHA256: | DA9E4F60B1C4C455793AD5D8C9FE96B032E17215F2F812D88B5A01EDFA0B2726 |
| SSDEEP: | 3:N1KZiR4rBLFEtIQ0C:Cg4r/EtIhC |
MALICIOUS
Application was dropped or rewritten from another process
- uninst.exe (PID: 1304)
- Un_A.exe (PID: 1824)
- uninst.exe (PID: 1556)
- uninst.exe (PID: 2064)
Drops the executable file immediately after the start
- uninst.exe (PID: 1304)
- Un_A.exe (PID: 1824)
- uninst.exe (PID: 1556)
- uninst.exe (PID: 2064)
Loads dropped or rewritten executable
- uninst.exe (PID: 2064)
- uninst.exe (PID: 1556)
- Un_A.exe (PID: 1824)
SUSPICIOUS
Starts itself from another location
- uninst.exe (PID: 1304)
- Un_A.exe (PID: 1824)
Malware-specific behavior (creating "System.dll" in Temp)
- Un_A.exe (PID: 1824)
- uninst.exe (PID: 1556)
- uninst.exe (PID: 2064)
The process creates files with name similar to system file names
- Un_A.exe (PID: 1824)
- uninst.exe (PID: 1556)
- uninst.exe (PID: 2064)
Application launched itself
- uninst.exe (PID: 1556)
Uses TASKKILL.EXE to kill process
- uninst.exe (PID: 2064)
INFO
Drops the executable file immediately after the start
- iexplore.exe (PID: 2512)
- iexplore.exe (PID: 3852)
Application launched itself
- iexplore.exe (PID: 3852)
Checks supported languages
- uninst.exe (PID: 1304)
- Un_A.exe (PID: 1824)
- uninst.exe (PID: 1556)
- uninst.exe (PID: 2064)
The process uses the downloaded file
- iexplore.exe (PID: 3852)
- uninst.exe (PID: 1304)
Create files in a temporary directory
- uninst.exe (PID: 1304)
- Un_A.exe (PID: 1824)
- uninst.exe (PID: 1556)
- uninst.exe (PID: 2064)
Reads the computer name
- uninst.exe (PID: 1304)
- Un_A.exe (PID: 1824)
- uninst.exe (PID: 1556)
- uninst.exe (PID: 2064)
Reads the machine GUID from the registry
- Un_A.exe (PID: 1824)
Process checks are UAC notifies on
- uninst.exe (PID: 1556)
Manual execution by a user
- WINWORD.EXE (PID: 3716)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
51
Monitored processes
8
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1304 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\uninst.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\uninst.exe | — | iexplore.exe | |||||||||||
User: admin Company: MEGA Limited Integrity Level: MEDIUM Description: MEGAsync Exit code: 0 Version: 4.10.0.0 Modules
| |||||||||||||||
| 1556 | "C:\Users\admin\AppData\Local\Temp\nscC581.tmp\uninst.exe" _?=C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP | C:\Users\admin\AppData\Local\Temp\nscC581.tmp\uninst.exe | — | Un_A.exe | |||||||||||
User: admin Company: MEGA Limited Integrity Level: MEDIUM Description: MEGAsync Exit code: 0 Version: 4.10.0.0 Modules
| |||||||||||||||
| 1824 | "C:\Users\admin\AppData\Local\Temp\~nsu.tmp\Un_A.exe" _?=C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\ | C:\Users\admin\AppData\Local\Temp\~nsu.tmp\Un_A.exe | — | uninst.exe | |||||||||||
User: admin Company: MEGA Limited Integrity Level: MEDIUM Description: MEGAsync Exit code: 0 Version: 4.10.0.0 Modules
| |||||||||||||||
| 2064 | "C:\Users\admin\AppData\Local\Temp\nscC581.tmp\uninst.exe" /UAC:1201F6 /NCRC _?=C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP | C:\Users\admin\AppData\Local\Temp\nscC581.tmp\uninst.exe | uninst.exe | ||||||||||||
User: admin Company: MEGA Limited Integrity Level: HIGH Description: MEGAsync Exit code: 0 Version: 4.10.0.0 Modules
| |||||||||||||||
| 2512 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3852 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2820 | taskkill /f /IM MEGASync.exe | C:\Windows\System32\taskkill.exe | — | uninst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3716 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\charlescommon.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3852 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://g.static.mega.co.nz/upd/wsync64/uninst.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
14 133
Read events
13 887
Write events
98
Delete events
148
Modification events
| (PID) Process: | (3852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000056010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
18
Suspicious files
21
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2512 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:8E4FB46455AFC5EE7C811947432EEC11 | SHA256:E4196FAA8DA09147BD0691FB5F65121493101747D8E309B68D76EB831FD49EAA | |||
| 2512 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EEBED2DEC5DA9EF6B00DC06C9A3BA534 | binary | |
MD5:FCFFE1C19A5D9B79DB6408F546F240ED | SHA256:093DB18411355C5312B3FB7124C55CCAD4D936AB7380D45583F39AA23BE322C1 | |||
| 2512 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:AE96262DD8253F4080C9B2E213C0758C | SHA256:E2FB4CF6DDDD012B4903256A6165A71803AB02192A61C28518E3007457B295FB | |||
| 2512 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:87967EB753690D01175F2F1B2BC8EAA5 | SHA256:58D68D359E33051A9AB38C719AAD772B93C76D0391ED8D0BBC8C685FC52C1434 | |||
| 2512 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 2512 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:087D34750689883DD196CA3B072CB4A0 | SHA256:0198347B9AADFC25E93CE52DEB04DF99E9D95A2BD4C66C80CE6B09C99888D3FB | |||
| 2512 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\uninst[1].exe | executable | |
MD5:385C1FF20B6F77424FBF083ED9B95F2F | SHA256:720CC9171CEF74E9A39DE076341BE6B5C11FADAA0B7C55E570836217329A37EF | |||
| 2512 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EEBED2DEC5DA9EF6B00DC06C9A3BA534 | binary | |
MD5:BD33EA5633A70B22A8DBEBF2B1D95A9C | SHA256:5325DCE0658087D2AE184BA676AE72F29C1FE1BBCEC05E4A546494F76243C985 | |||
| 2512 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:4CF1DA8D132D43AB05E3D69F591BF0EC | SHA256:2CDE1331FA0E4D795282D6142B6A24C33FB075CD8EC210F27A6CCA8A5C9ADBE7 | |||
| 1824 | Un_A.exe | C:\Users\admin\AppData\Local\Temp\nscC581.tmp\UserInfo.dll | executable | |
MD5:9EB662F3B5FBDA28BFFE020E0AB40519 | SHA256:9AA388C7DE8E96885ADCB4325AF871B470AC50EDB60D4B0D876AD43F5332FFD1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
13
DNS requests
7
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2512 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | binary | 1.42 Kb | unknown |
2512 | iexplore.exe | GET | 200 | 184.24.77.202:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?060020e49c501eb3 | unknown | compressed | 4.66 Kb | unknown |
2512 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | binary | 2.18 Kb | unknown |
3852 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
2512 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEDU3H7cy26ELdLghTExcxKg%3D | unknown | binary | 471 b | unknown |
2512 | iexplore.exe | GET | 200 | 184.24.77.202:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?cea11e295b0381a5 | unknown | compressed | 4.66 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2512 | iexplore.exe | 184.24.77.202:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2512 | iexplore.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
2512 | iexplore.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | shared |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3852 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
3852 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |