| File name: | main.exe |
| Full analysis: | https://app.any.run/tasks/1253ee1c-1f98-4b43-b68a-e6b40329c2f2 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2020, 01:38:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 7C5055B0981FA1131A3D46DE51ED9389 |
| SHA1: | F1DD7429296F3B130CAE8D725CB062BF138FE502 |
| SHA256: | DA8E700DAF4CE36852A8F8B2D7C39712ADA90E99DF41E037B1C6CB15C96CEF6A |
| SSDEEP: | 196608:Zlmce67oP1HAwG93wXlttbYPvbJQlHIo1Az2Y58CjHKefsgYmufv83KV2:HmAsP1gwrX3kJQl8z2YsEPK |
MALICIOUS
Loads dropped or rewritten executable
- main.exe (PID: 2428)
SUSPICIOUS
Uses WMIC.EXE to obtain a system information
- main.exe (PID: 2428)
Application launched itself
- main.exe (PID: 2432)
Executed via COM
- DllHost.exe (PID: 2616)
Loads Python modules
- main.exe (PID: 2428)
Executable content was dropped or overwritten
- main.exe (PID: 2432)
INFO
Dropped object may contain Bitcoin addresses
- main.exe (PID: 2432)
Manual execution by user
- explorer.exe (PID: 924)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:08:08 14:29:54+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 128000 |
| InitializedDataSize: | 116736 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x781a |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows command line |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_CUI |
| Compilation Date: | 08-Aug-2020 12:29:54 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 08-Aug-2020 12:29:54 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0001F274 | 0x0001F400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.65656 |
.rdata | 0x00021000 | 0x0000B386 | 0x0000B400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.1121 |
.data | 0x0002D000 | 0x0000A668 | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.93189 |
.gfids | 0x00038000 | 0x000000B8 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.82045 |
.rsrc | 0x00039000 | 0x0000EF6C | 0x0000F000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.35031 |
.reloc | 0x00048000 | 0x000017FC | 0x00001800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.6693 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.27101 | 1262 | Latin 1 / Western European | UNKNOWN | RT_MANIFEST |
2 | 6.05629 | 2216 | Latin 1 / Western European | UNKNOWN | RT_ICON |
3 | 5.5741 | 1384 | Latin 1 / Western European | UNKNOWN | RT_ICON |
4 | 7.95079 | 37019 | Latin 1 / Western European | UNKNOWN | RT_ICON |
5 | 5.29119 | 9640 | Latin 1 / Western European | UNKNOWN | RT_ICON |
6 | 5.43869 | 4264 | Latin 1 / Western European | UNKNOWN | RT_ICON |
7 | 5.89356 | 1128 | Latin 1 / Western European | UNKNOWN | RT_ICON |
101 | 2.71858 | 104 | Latin 1 / Western European | UNKNOWN | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
KERNEL32.dll |
WS2_32.dll |
Total processes
50
Monitored processes
5
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 924 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
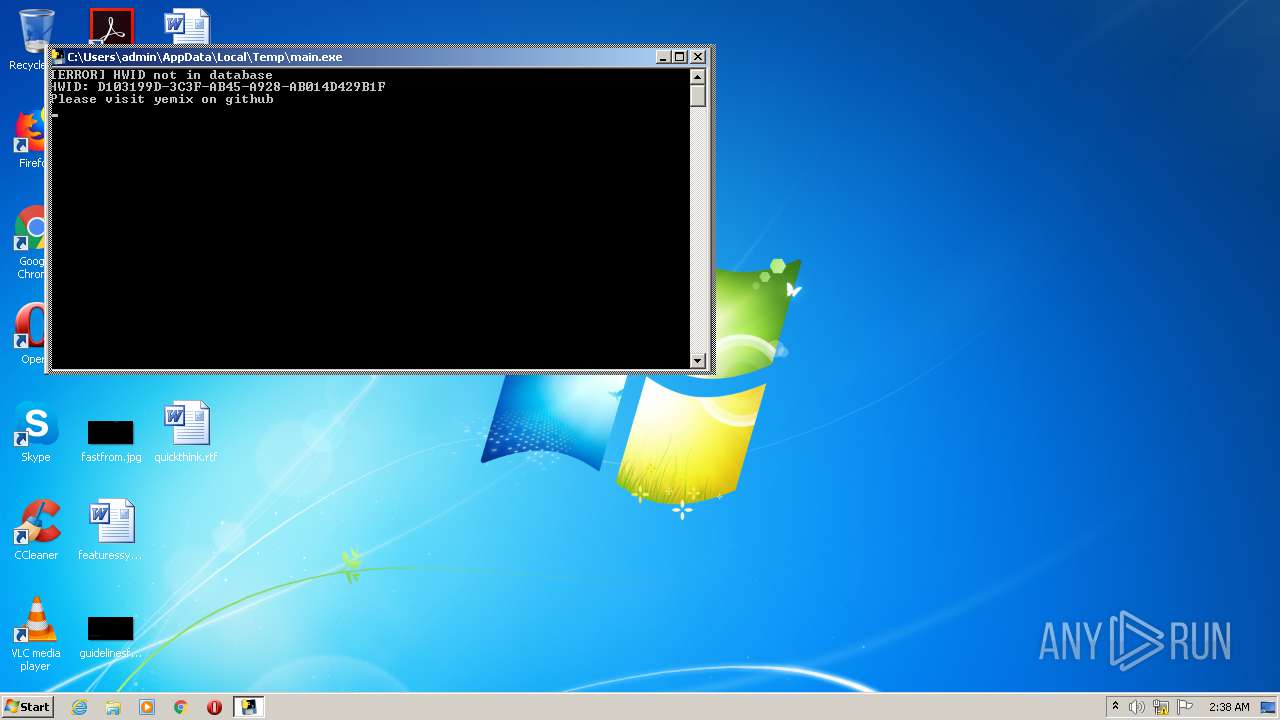
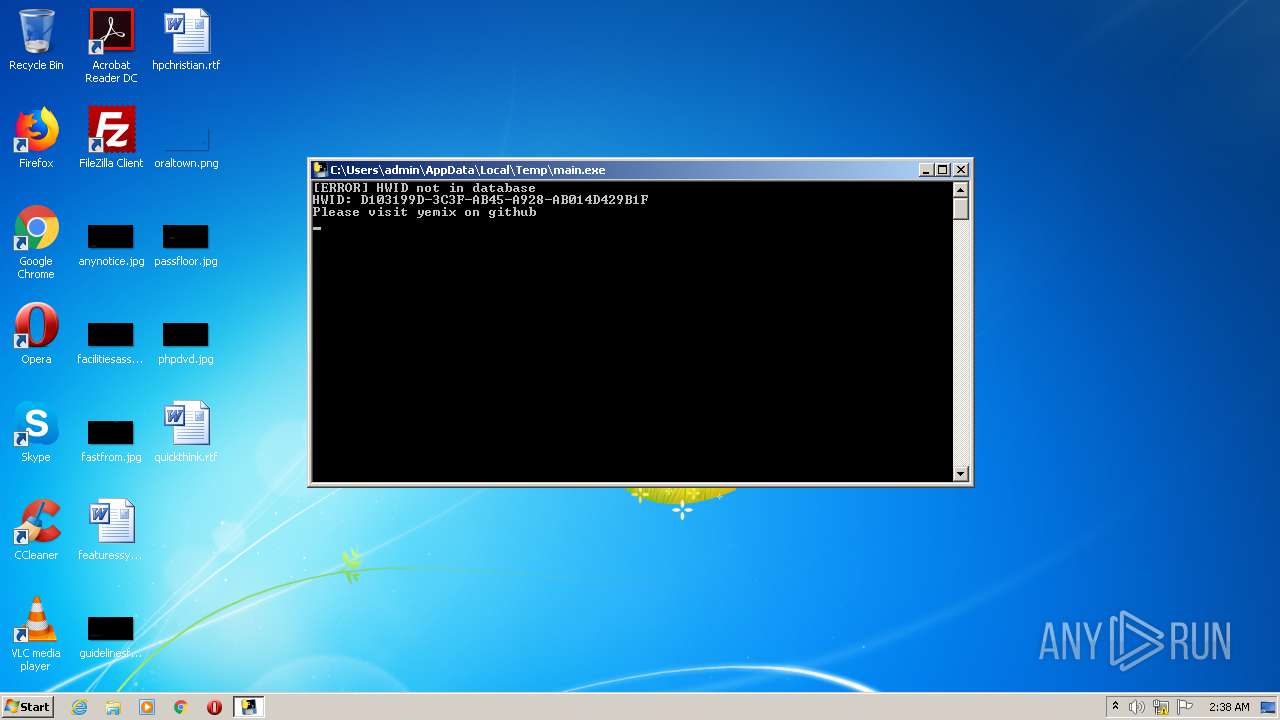
| 2428 | "C:\Users\admin\AppData\Local\Temp\main.exe" | C:\Users\admin\AppData\Local\Temp\main.exe | main.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2432 | "C:\Users\admin\AppData\Local\Temp\main.exe" | C:\Users\admin\AppData\Local\Temp\main.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2596 | wmic csproduct get uuid | C:\Windows\System32\Wbem\wmic.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2616 | C:\Windows\system32\DllHost.exe /Processid:{4D111E08-CBF7-4F12-A926-2C7920AF52FC} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
278
Read events
278
Write events
0
Delete events
0
Modification events
Executable files
26
Suspicious files
3
Text files
916
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2432 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI24322\_queue.pyd | executable | |
MD5:7D1F8B6DB5C99F4B86135EB7B125F029 | SHA256:7B5E1F2E2D82878064CF86A3425653759D116C154EFE18043D1BFA85BAD60D6C | |||
| 2432 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI24322\_socket.pyd | executable | |
MD5:8CBC7BD28CBDA6291AA3D8CEE8033F7F | SHA256:F0E11401B417AA7402E93A1EB4B9C594F5BB4522C31F345C28D62752DA09B232 | |||
| 2432 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI24322\VCRUNTIME140.dll | executable | |
MD5:55C8E69DAB59E56951D31350D7A94011 | SHA256:9D8D21022FF9D3F6B81A45209662A4F3481EDC2BEFAE0C73B83CF942EAB8BE25 | |||
| 2432 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI24322\_bz2.pyd | executable | |
MD5:AB43CE9D54C10EAA959DBA7DFE4E43D3 | SHA256:A6AF2196C3E73AED881BF5B4ACB79009C42CEC43AC022716AE760827263F31A0 | |||
| 2432 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI24322\libffi-7.dll | executable | |
MD5:BC20614744EBF4C2B8ACD28D1FE54174 | SHA256:0C7EC6DE19C246A23756B8550E6178AC2394B1093E96D0F43789124149486F57 | |||
| 2432 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI24322\_decimal.pyd | executable | |
MD5:47BF3A0FB39D865A771CA6CEB7139327 | SHA256:BA9CF83A6A0889A796EBD67BE478C43F184AA76E5E47CAAEFA7449CC491861A4 | |||
| 2432 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI24322\_asyncio.pyd | executable | |
MD5:57539BA21412485160500CB057AE797F | SHA256:4893C444389A7E92FCADF3C34D36B591EAF19C5ABFD33495516FCFBA32BD07E8 | |||
| 2432 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI24322\_testcapi.pyd | executable | |
MD5:32F84F84F2597D665DF666C659295BA1 | SHA256:6BB7049A27360276E690160A4375B06507694E25C9605841D666A9E8666E18DF | |||
| 2432 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI24322\main.exe.manifest | xml | |
MD5:AB714A291FDE70F49E9E94F3405FBAEB | SHA256:7EDC3B803390B3A1E1AA62435393A91C8EC27518D5BCA88A2F07E1BBB4E3458B | |||
| 2432 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI24322\multidict\_multidict.cp38-win32.pyd | executable | |
MD5:CED7F69AF68BD4A7A33FCE0A2678F896 | SHA256:D70D297510E753A76219DA700394DB288A3769E1DFD452797E39F1AD60732FB9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2428 | main.exe | 104.23.98.190:443 | pastebin.com | Cloudflare Inc | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |