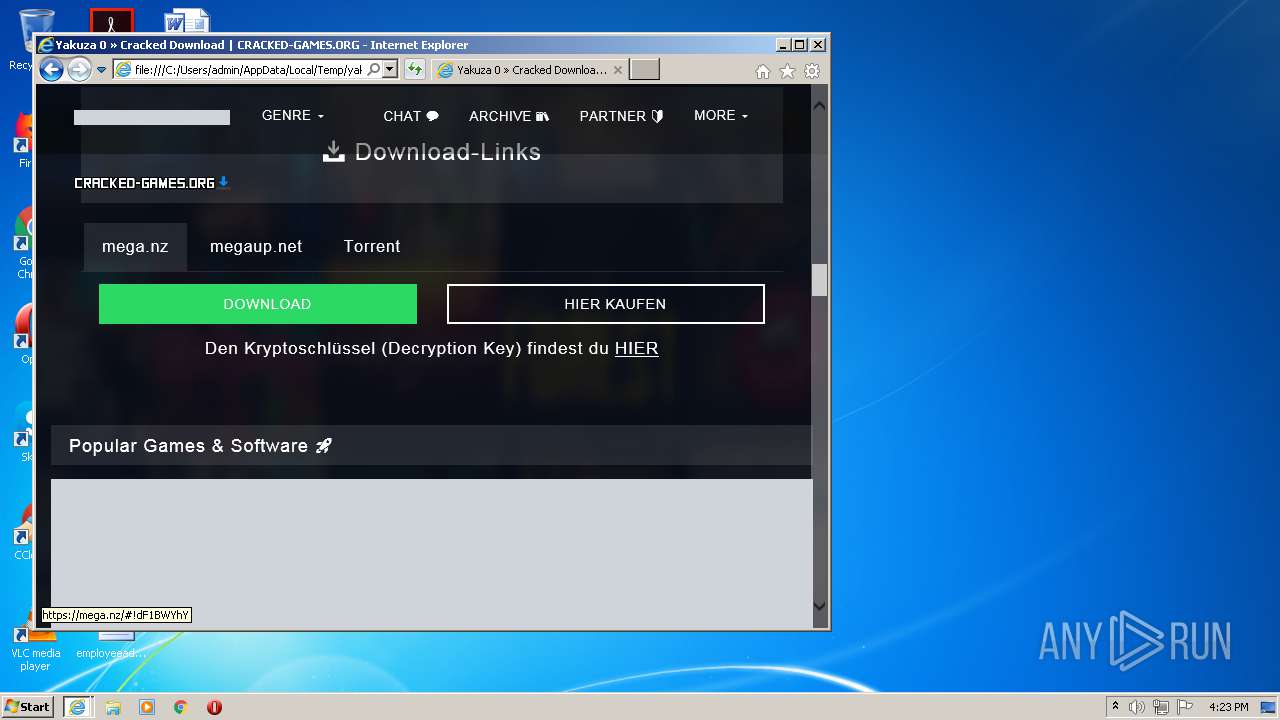
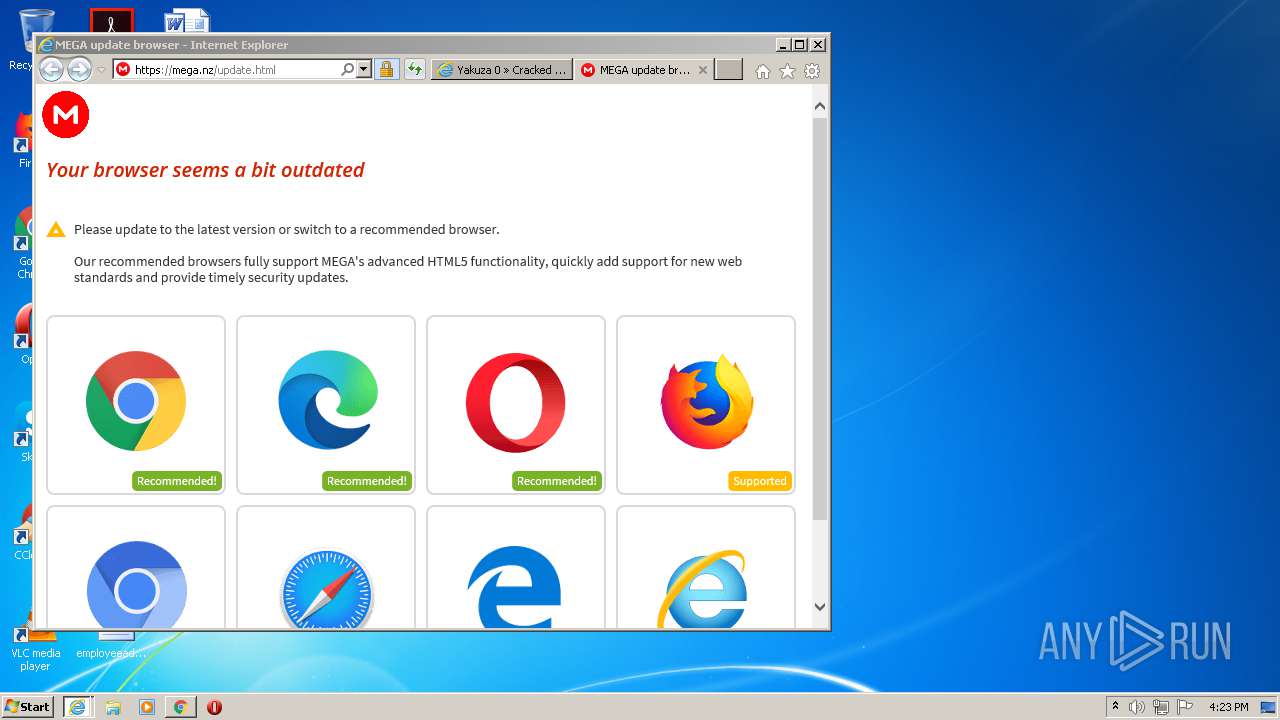
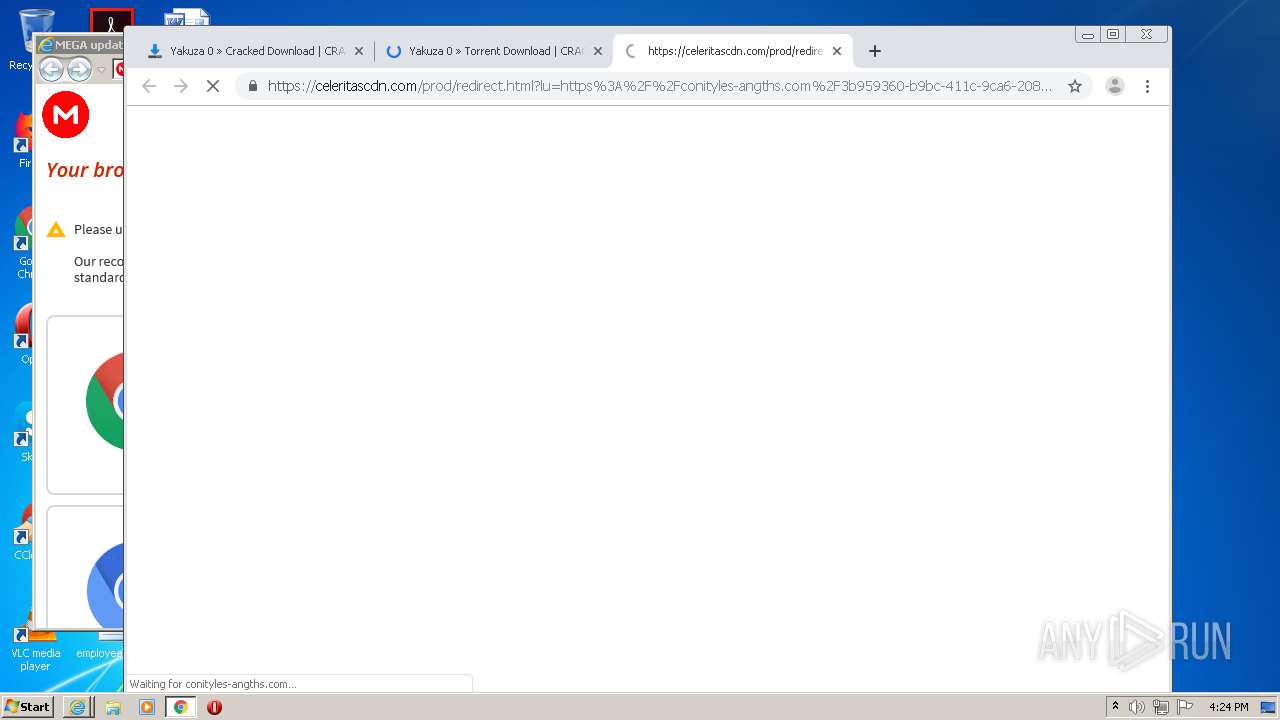
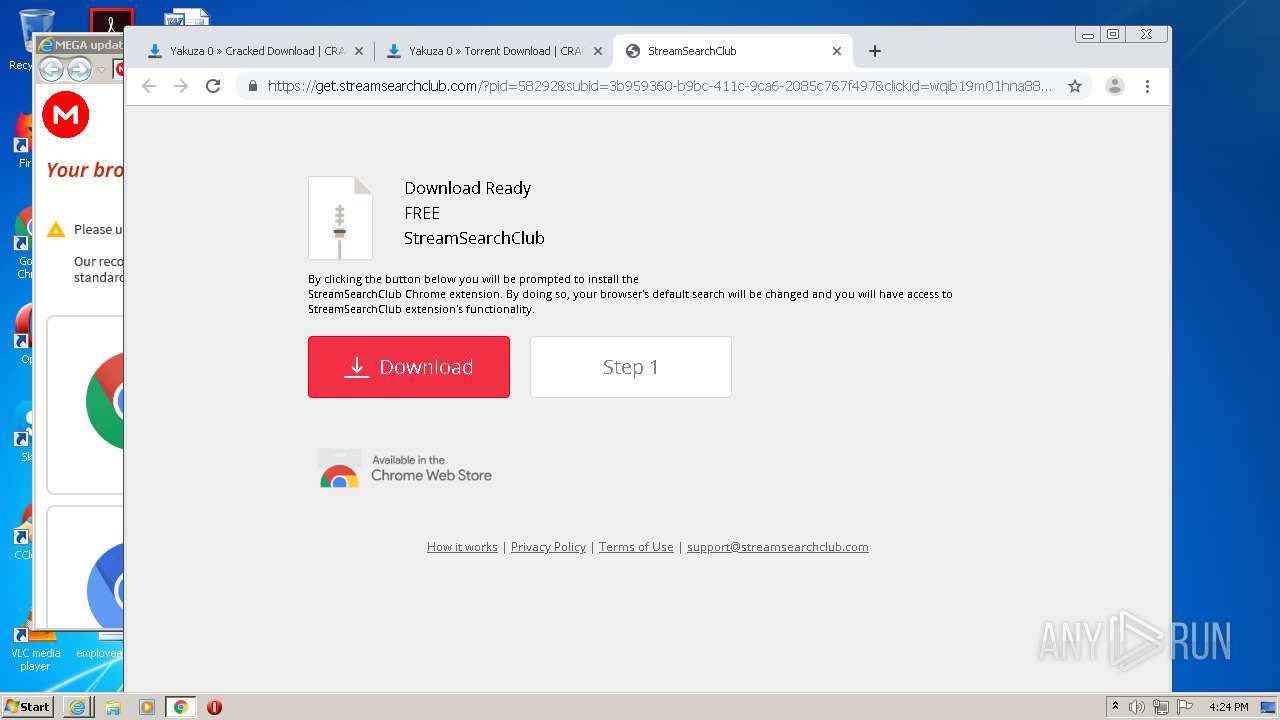
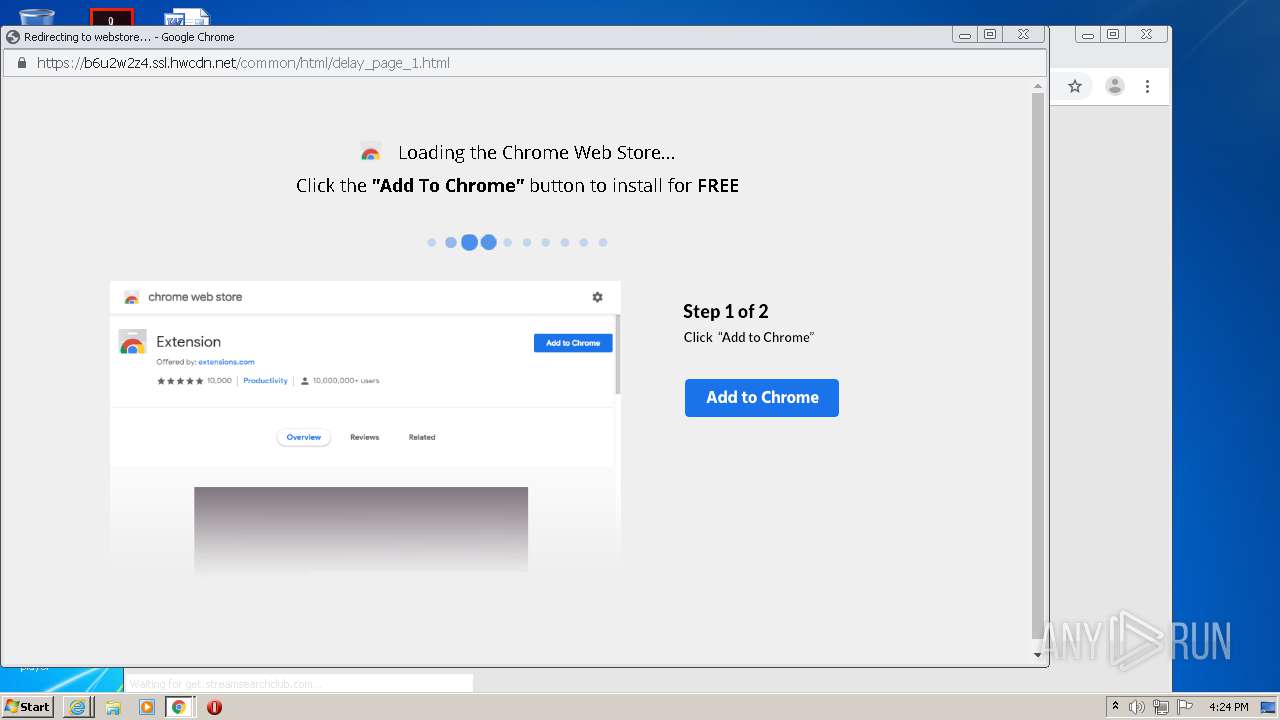
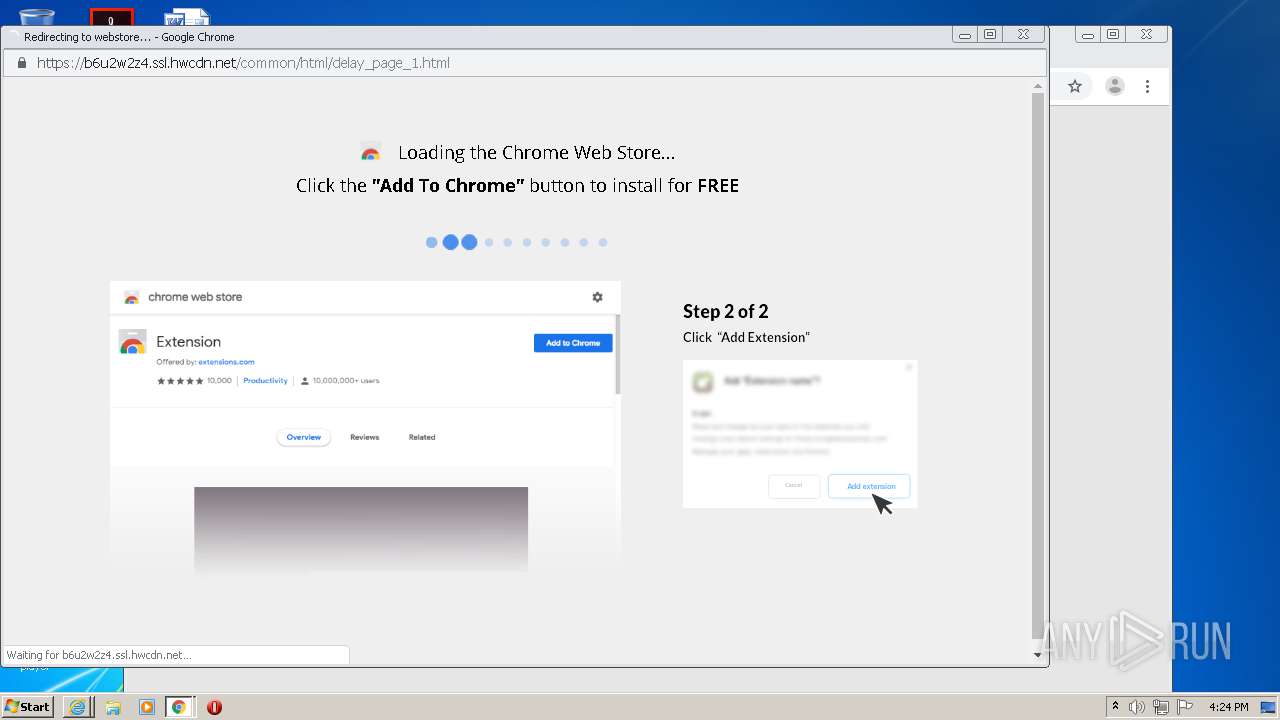
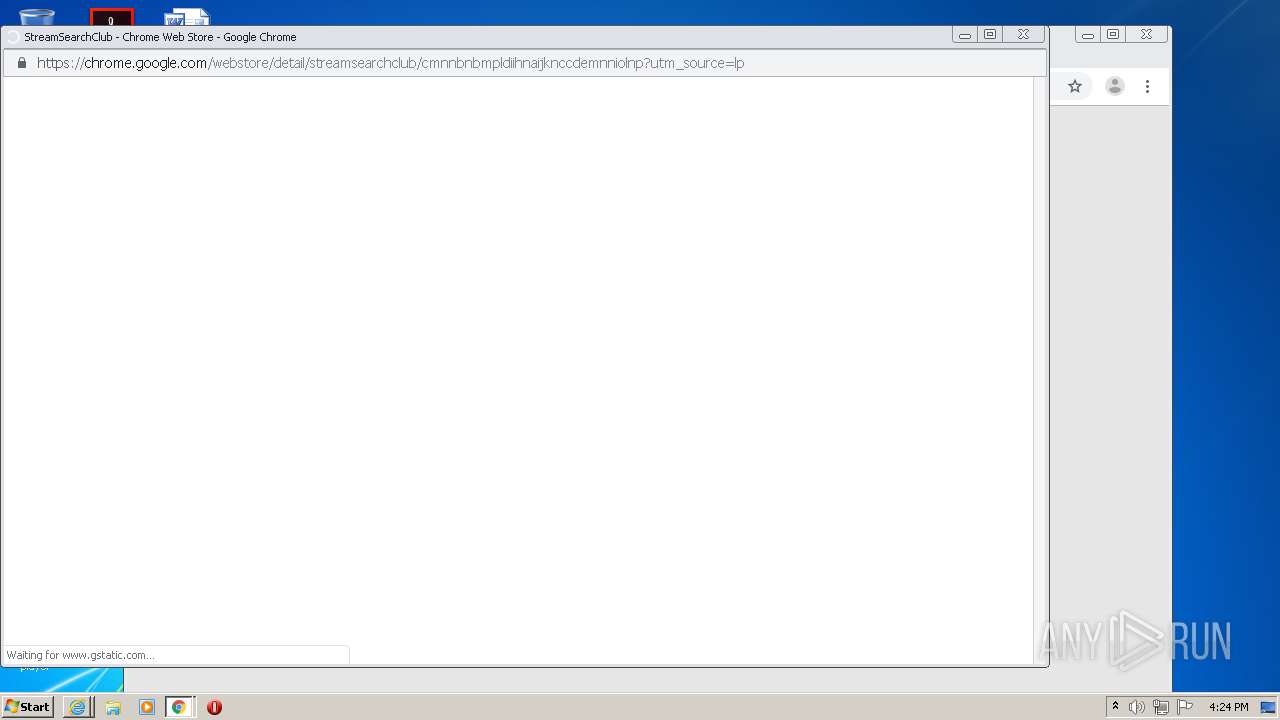
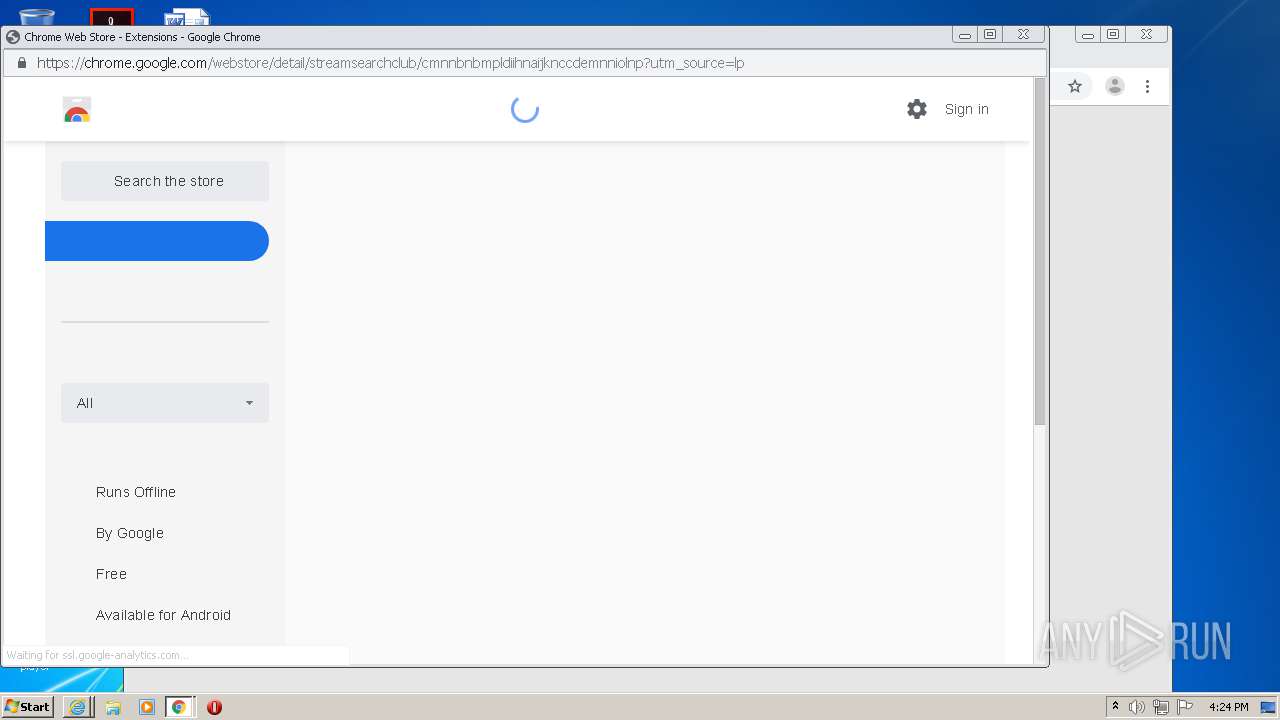
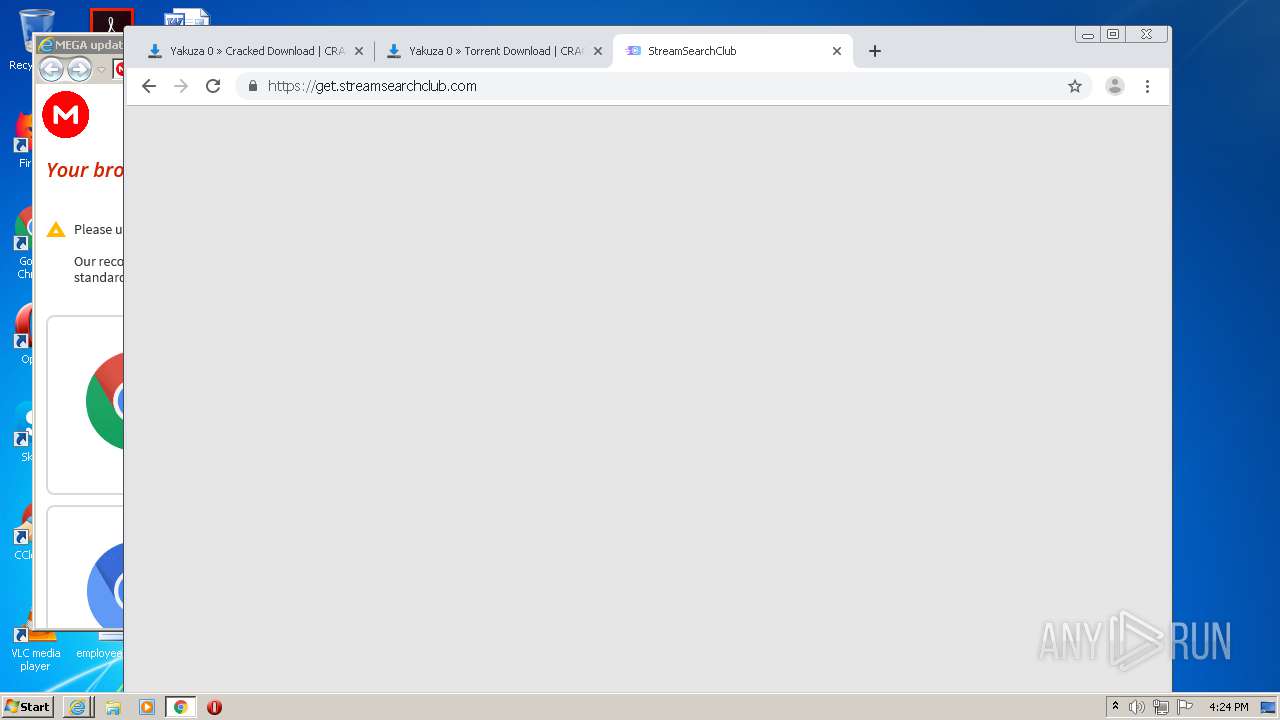
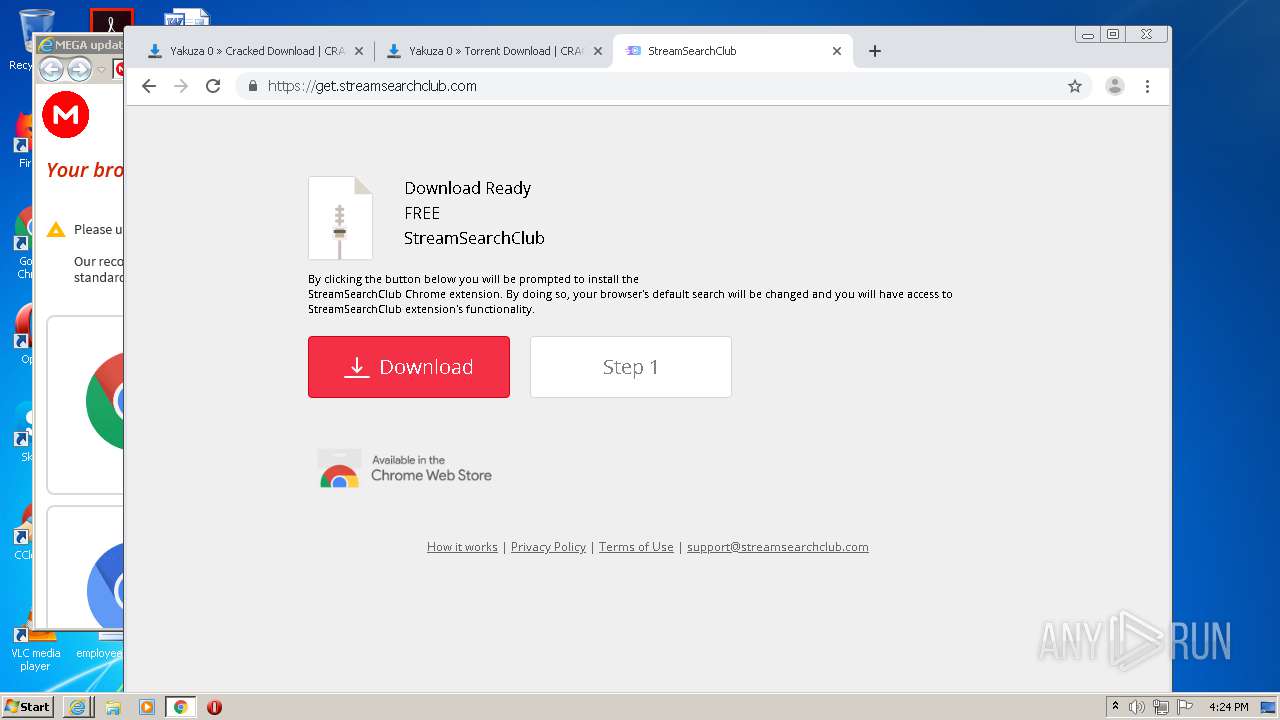
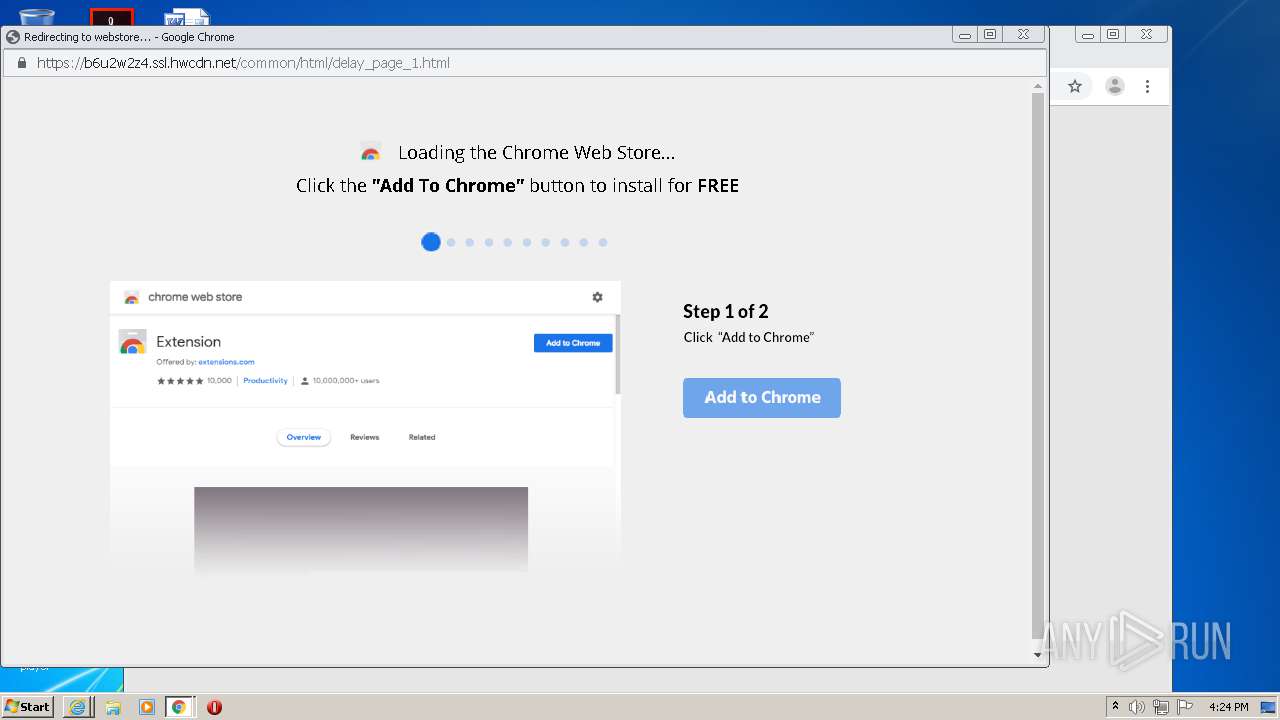
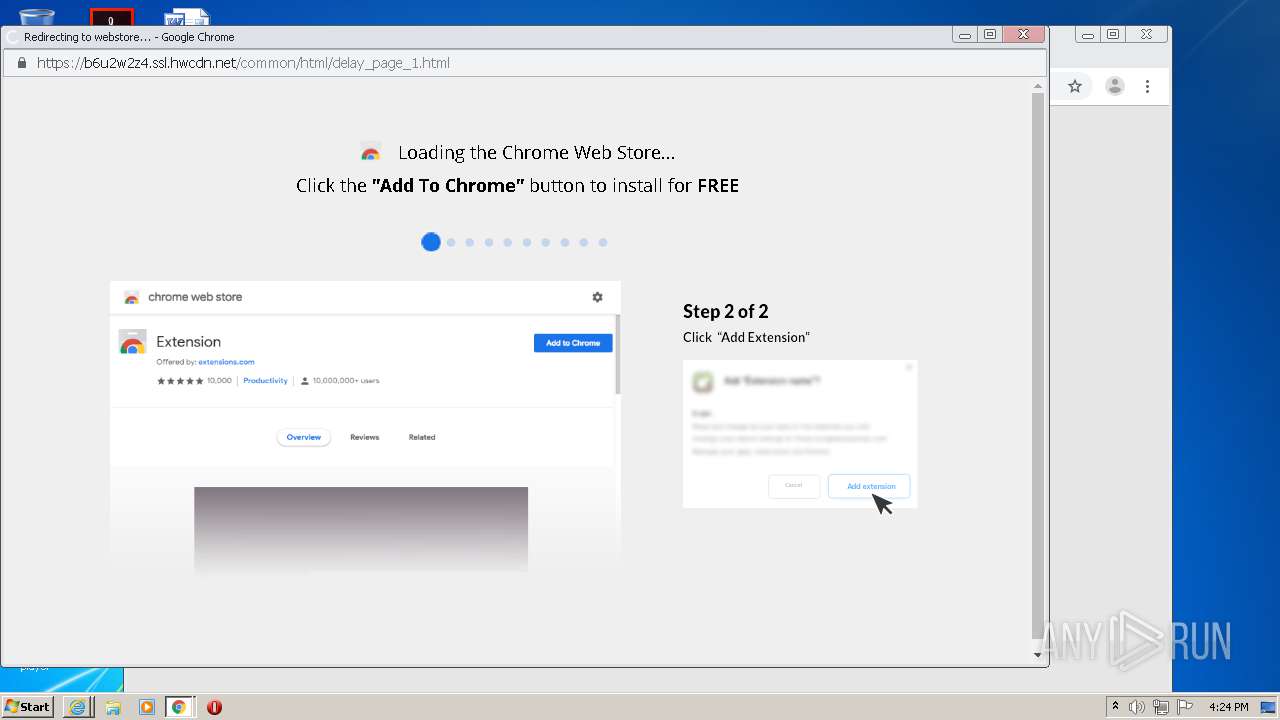
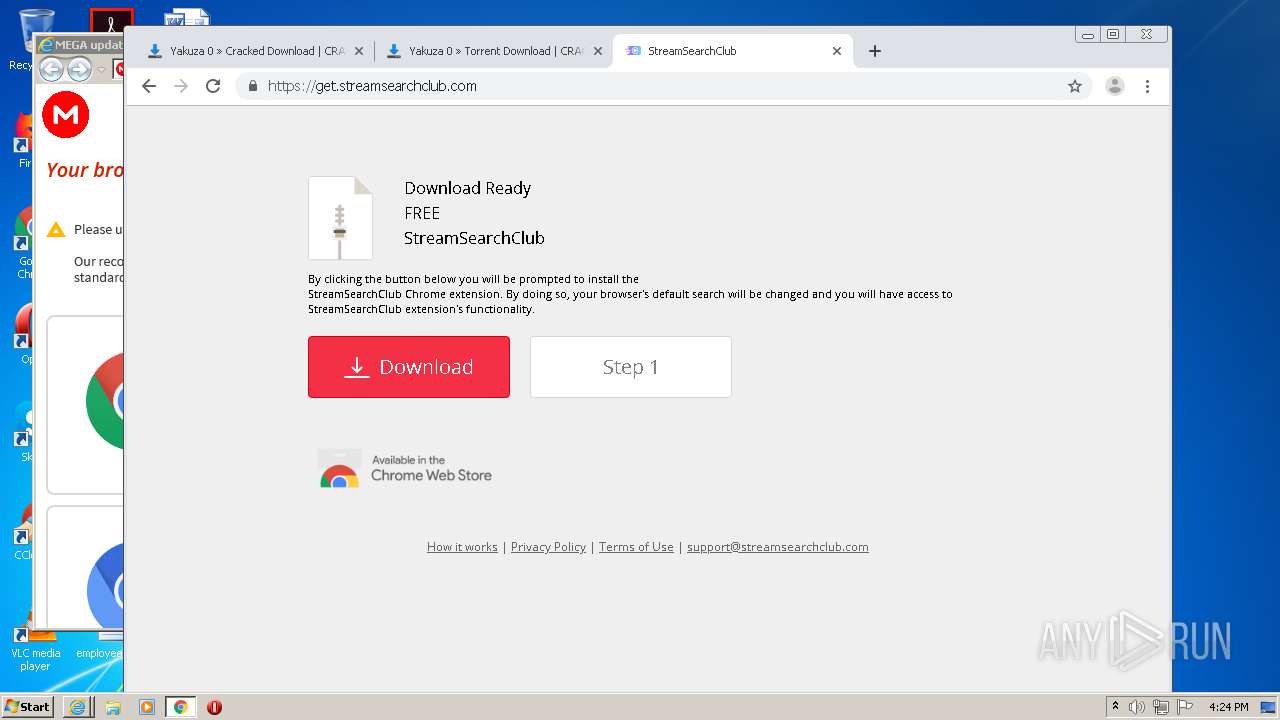
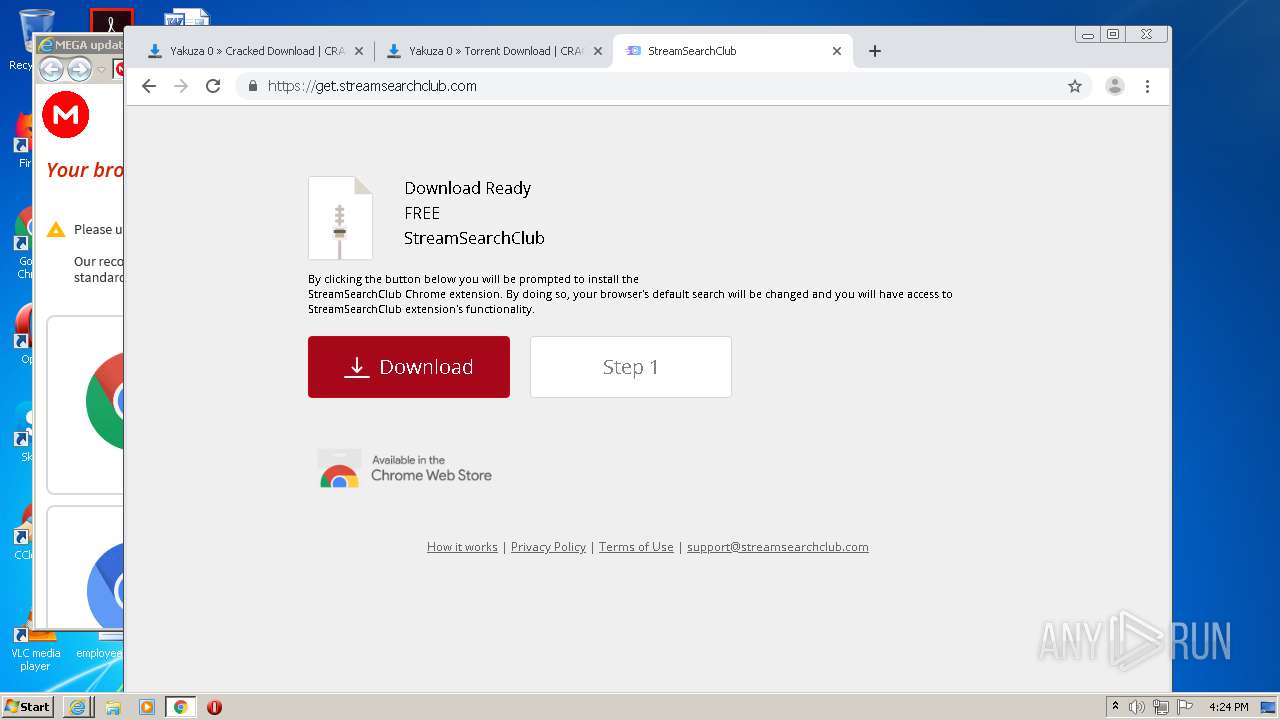
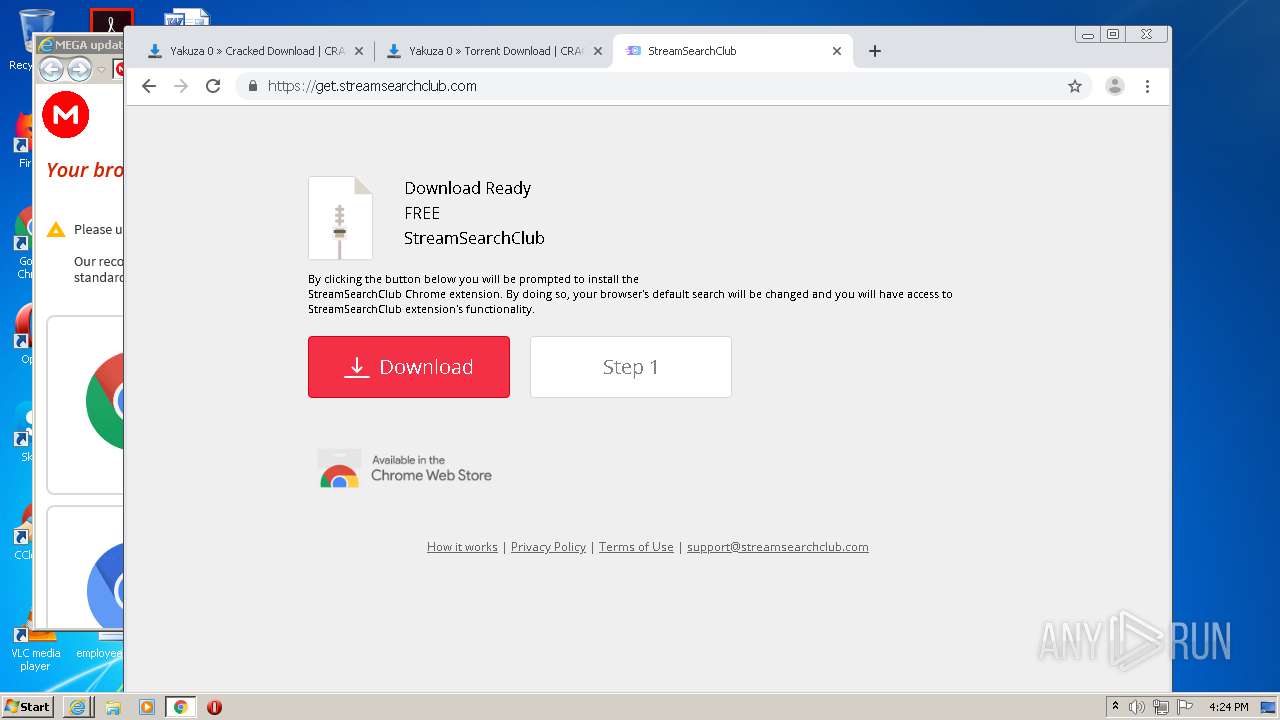
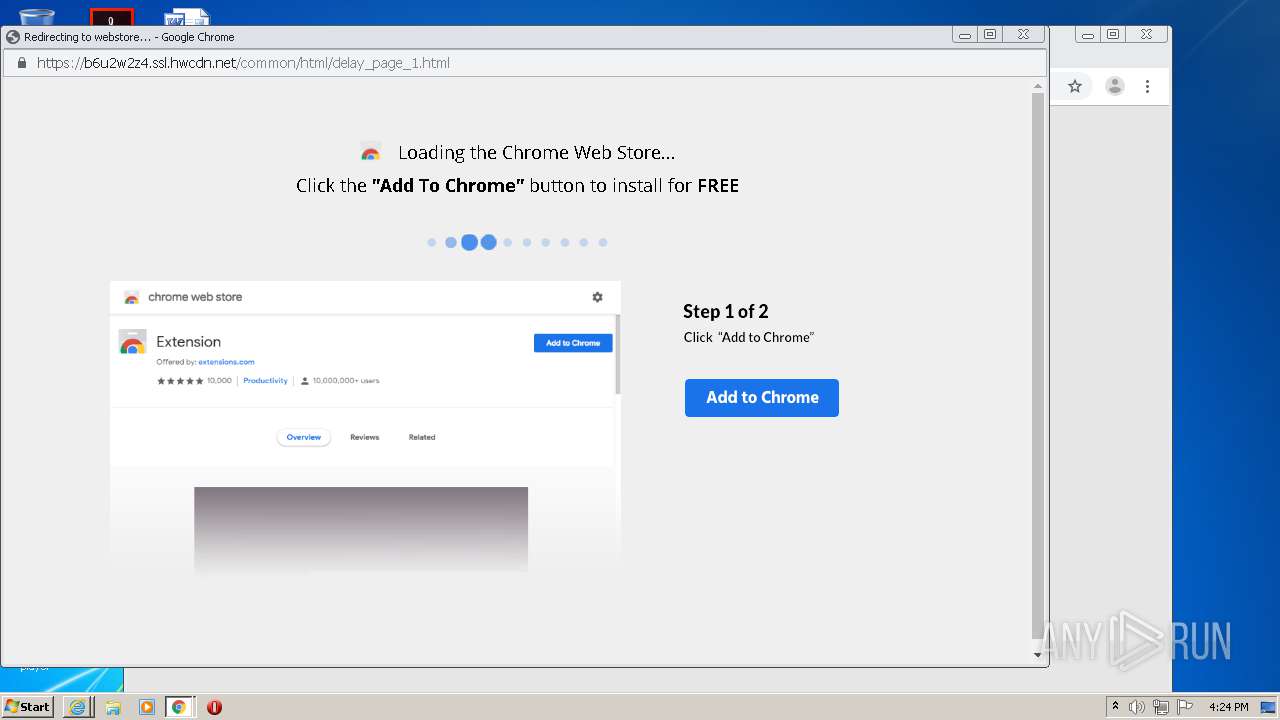
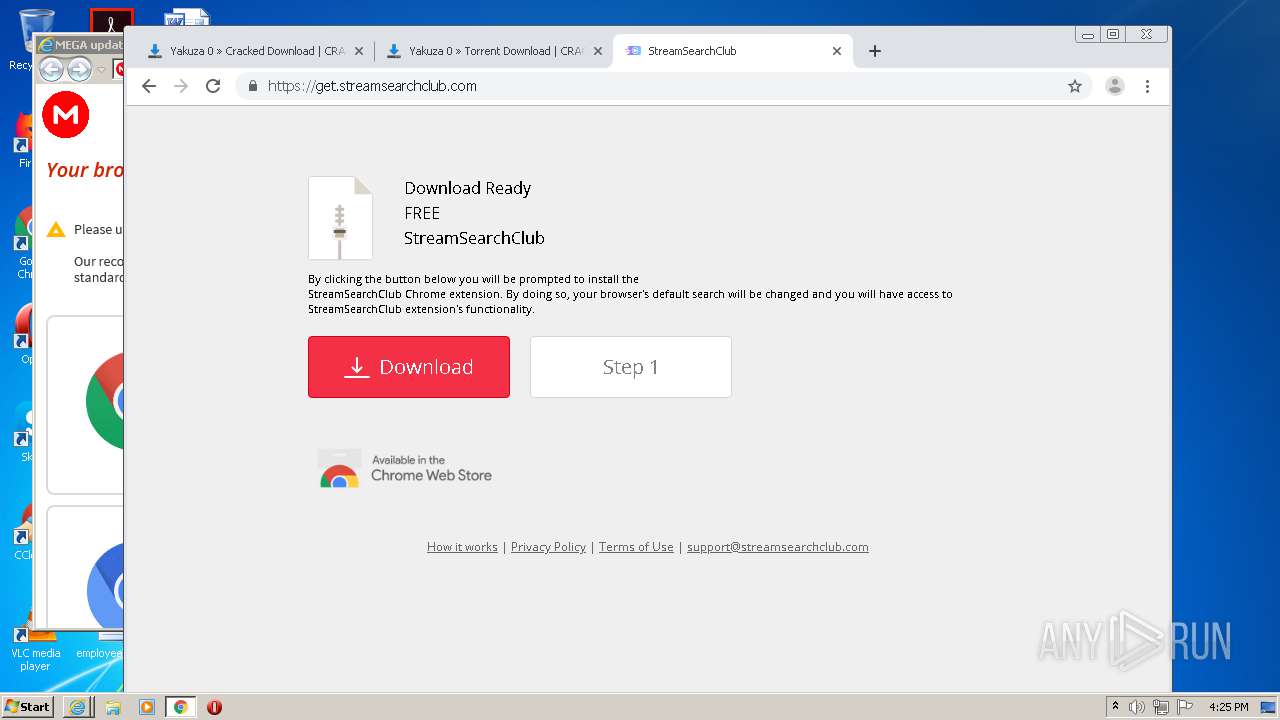
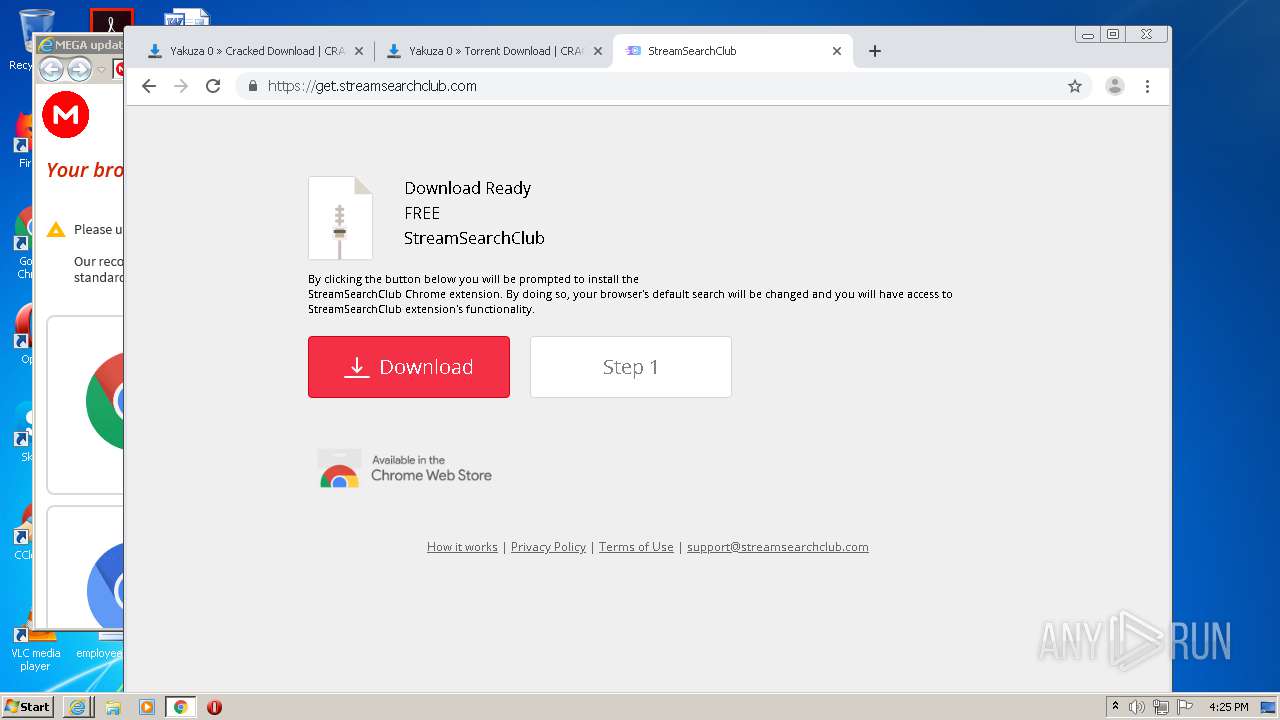
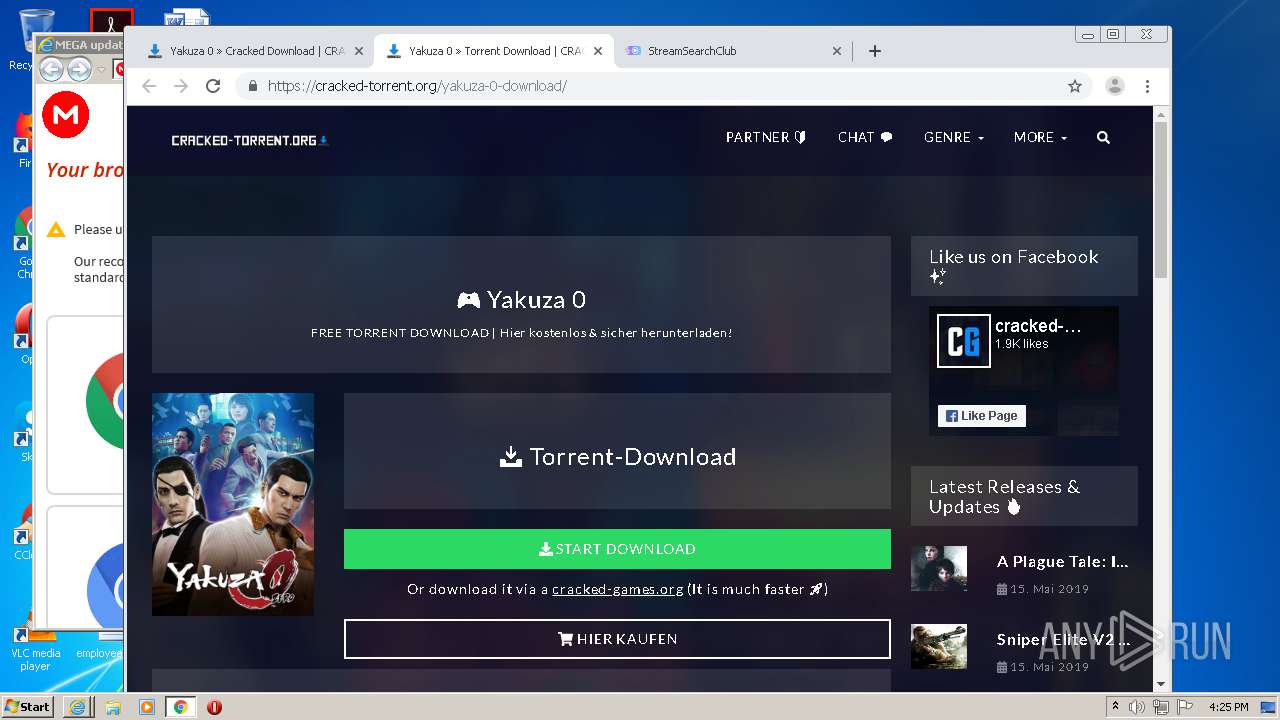
| download: | yakuza-0-free-download |
| Full analysis: | https://app.any.run/tasks/64bbc2b9-870d-433c-9f5e-5893e17d42d3 |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2020, 16:21:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines |
| MD5: | C14BBFAB12702D7FE18E0A866FB07072 |
| SHA1: | E25A9760CC9D870566036B0562AB01FEA9FAD6CF |
| SHA256: | DA8B3394A820544B0651D5D72BEDB3878D83DE95D181B17C860E881180ABCDCE |
| SSDEEP: | 1536:TrBmWQlFUTqb8yKEOh7+A6wSZgShEpgUgShEpglVAhDcb8m5j98rS63xUUhP1ZJc:/wuqslpbSZKbK8p8i98rS6hUUf/c |
MALICIOUS
No malicious indicators.SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 2784)
Uses RUNDLL32.EXE to load library
- chrome.exe (PID: 2784)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2220)
Reads settings of System Certificates
- iexplore.exe (PID: 1960)
- iexplore.exe (PID: 2220)
- iexplore.exe (PID: 3952)
- chrome.exe (PID: 3056)
Creates files in the user directory
- iexplore.exe (PID: 1960)
- iexplore.exe (PID: 2220)
- chrome.exe (PID: 2784)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2220)
- iexplore.exe (PID: 1960)
Reads internet explorer settings
- iexplore.exe (PID: 3952)
- iexplore.exe (PID: 1960)
Changes settings of System certificates
- iexplore.exe (PID: 1960)
- iexplore.exe (PID: 2220)
Application launched itself
- iexplore.exe (PID: 2220)
- iexplore.exe (PID: 1960)
- chrome.exe (PID: 2784)
Manual execution by user
- chrome.exe (PID: 2784)
Reads the hosts file
- chrome.exe (PID: 3056)
- chrome.exe (PID: 2784)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 2784)
- chrome.exe (PID: 3056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
Total processes
105
Monitored processes
67
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1076,16417030198778076574,17007801867837577787,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13243715052819276751 --renderer-client-id=58 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 256 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1076,16417030198778076574,17007801867837577787,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=5008991074963796114 --mojo-platform-channel-handle=3996 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 352 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1076,16417030198778076574,17007801867837577787,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12866305298949014936 --mojo-platform-channel-handle=4068 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 576 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1076,16417030198778076574,17007801867837577787,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8300219689253167340 --renderer-client-id=49 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2080 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 636 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1076,16417030198778076574,17007801867837577787,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=2918068492212696661 --mojo-platform-channel-handle=3688 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 836 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1076,16417030198778076574,17007801867837577787,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8411989947328172392 --renderer-client-id=23 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3892 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 912 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1076,16417030198778076574,17007801867837577787,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3977964646710984734 --renderer-client-id=39 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3976 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 932 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1076,16417030198778076574,17007801867837577787,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10811119616226628235 --renderer-client-id=50 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4736 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 976 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1076,16417030198778076574,17007801867837577787,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=15261138474665398973 --mojo-platform-channel-handle=3704 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 992 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1076,16417030198778076574,17007801867837577787,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15098671832779322268 --renderer-client-id=37 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4476 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
2 048
Read events
1 739
Write events
297
Delete events
12
Modification events
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 3560551360 | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30852715 | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
342
Text files
528
Unknown types
82
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2220 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 1960 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab8601.tmp | — | |
MD5:— | SHA256:— | |||
| 1960 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar8602.tmp | — | |
MD5:— | SHA256:— | |||
| 1960 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\b8642[1].js | — | |
MD5:— | SHA256:— | |||
| 1960 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 1960 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9FF67FB3141440EED32363089565AE60_444DE43FED932ACF85BE689919570420 | der | |
MD5:— | SHA256:— | |||
| 1960 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 1960 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\e82c7[1].css | text | |
MD5:— | SHA256:— | |||
| 1960 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\Yakuza-0-free-download[1].jpg | image | |
MD5:— | SHA256:— | |||
| 1960 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9FF67FB3141440EED32363089565AE60_444DE43FED932ACF85BE689919570420 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
39
TCP/UDP connections
214
DNS requests
127
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1960 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
1960 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEAQSqG2Vcy5VgVdz4Q5GOwg%3D | US | der | 279 b | whitelisted |
1960 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
1960 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEAQSqG2Vcy5VgVdz4Q5GOwg%3D | US | der | 279 b | whitelisted |
1960 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQC5No09bsBBmYIny%2BZ%2FEAg2 | US | der | 472 b | whitelisted |
1960 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
1960 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
1960 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEFcLuT0XSrlKAgAAAACAVZE%3D | US | der | 471 b | whitelisted |
1960 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
1960 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQD76E8xQFZstgIAAAAAgFWS | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1960 | iexplore.exe | 104.28.15.237:443 | cracked-games.org | Cloudflare Inc | US | unknown |
2220 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1960 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
4 | System | 172.217.10.234:139 | ajax.googleapis.com | Google Inc. | US | whitelisted |
4 | System | 172.217.10.234:445 | ajax.googleapis.com | Google Inc. | US | whitelisted |
1960 | iexplore.exe | 104.18.226.52:443 | cdn.onesignal.com | Cloudflare Inc | US | malicious |
1960 | iexplore.exe | 35.190.64.167:443 | www.onclickmega.com | Google Inc. | US | whitelisted |
1960 | iexplore.exe | 172.217.16.136:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
1960 | iexplore.exe | 216.58.206.14:443 | www.youtube.com | Google Inc. | US | whitelisted |
1960 | iexplore.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cracked-games.org |
| malicious |
ajax.googleapis.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
www.onclickmega.com |
| unknown |
cdn.onesignal.com |
| whitelisted |
www.youtube.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |