| File name: | 4bc701fc5e13c1287646e5d1f79760d4.exe |
| Full analysis: | https://app.any.run/tasks/835d38d2-44ca-43fd-a750-cceb5b05dde7 |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | March 25, 2025, 04:16:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 4 sections |
| MD5: | 4BC701FC5E13C1287646E5D1F79760D4 |
| SHA1: | 6BC6E4C44012084EC5AF5EBDFD09314E598464E1 |
| SHA256: | DA479AC3683EB1B6CC8CEE9967B33D7A299FB551B9A8A1DDD5182469DE37B2FB |
| SSDEEP: | 98304:1/7VgtQQZgeAP31fe4C6buIKcCXN7kbjsdV/lnVYNBq8Xg/x53ujxGcO4H45yRss:mk6 |
MALICIOUS
DCRAT mutex has been found
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7312)
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
- sihost.exe (PID: 8180)
UAC/LUA settings modification
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
- sihost.exe (PID: 8180)
Changes the login/logoff helper path in the registry
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
Changes the autorun value in the registry
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
Changes Windows Defender settings
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
Adds path to the Windows Defender exclusion list
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
DCRAT has been detected (YARA)
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 10652)
- wscript.exe (PID: 10600)
DARKCRYSTAL has been detected (SURICATA)
- sihost.exe (PID: 8180)
Actions looks like stealing of personal data
- sihost.exe (PID: 8180)
Steals credentials from Web Browsers
- sihost.exe (PID: 8180)
SUSPICIOUS
Reads security settings of Internet Explorer
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7312)
- ShellExperienceHost.exe (PID: 7776)
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
- sihost.exe (PID: 8180)
Reads the date of Windows installation
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7312)
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
- sihost.exe (PID: 8180)
The executable file from the user directory is run by the CMD process
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
Starts CMD.EXE for commands execution
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7312)
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
Executed via WMI
- schtasks.exe (PID: 7992)
- schtasks.exe (PID: 8016)
- schtasks.exe (PID: 7172)
- schtasks.exe (PID: 8116)
- schtasks.exe (PID: 8040)
- schtasks.exe (PID: 8072)
- schtasks.exe (PID: 8144)
- schtasks.exe (PID: 1852)
- schtasks.exe (PID: 4784)
- schtasks.exe (PID: 4776)
- schtasks.exe (PID: 7228)
- schtasks.exe (PID: 2136)
- schtasks.exe (PID: 5960)
- schtasks.exe (PID: 3884)
- schtasks.exe (PID: 7292)
- schtasks.exe (PID: 4300)
- schtasks.exe (PID: 3300)
- schtasks.exe (PID: 1660)
- schtasks.exe (PID: 6800)
- schtasks.exe (PID: 4244)
- schtasks.exe (PID: 1672)
- schtasks.exe (PID: 4608)
- schtasks.exe (PID: 1188)
- schtasks.exe (PID: 4988)
- schtasks.exe (PID: 1272)
- schtasks.exe (PID: 4408)
- schtasks.exe (PID: 5720)
- schtasks.exe (PID: 5892)
- schtasks.exe (PID: 5608)
- schtasks.exe (PID: 6744)
- schtasks.exe (PID: 5008)
- schtasks.exe (PID: 7328)
- schtasks.exe (PID: 7408)
- schtasks.exe (PID: 7440)
- schtasks.exe (PID: 7336)
- schtasks.exe (PID: 7388)
- schtasks.exe (PID: 8148)
- schtasks.exe (PID: 7552)
- schtasks.exe (PID: 7736)
- schtasks.exe (PID: 7892)
- schtasks.exe (PID: 8004)
- schtasks.exe (PID: 8048)
- schtasks.exe (PID: 8096)
- schtasks.exe (PID: 8168)
- schtasks.exe (PID: 6620)
- schtasks.exe (PID: 6480)
- schtasks.exe (PID: 6300)
- schtasks.exe (PID: 6036)
- schtasks.exe (PID: 7296)
- schtasks.exe (PID: 2384)
- schtasks.exe (PID: 7216)
- schtasks.exe (PID: 7228)
- schtasks.exe (PID: 7300)
- schtasks.exe (PID: 4980)
- schtasks.exe (PID: 5308)
- schtasks.exe (PID: 7676)
- schtasks.exe (PID: 3304)
The process creates files with name similar to system file names
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
Executable content was dropped or overwritten
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
- sihost.exe (PID: 8180)
Likely accesses (executes) a file from the Public directory
- schtasks.exe (PID: 7388)
- schtasks.exe (PID: 7408)
- schtasks.exe (PID: 7552)
- OpenWith.exe (PID: 4696)
- powershell.exe (PID: 7500)
Starts POWERSHELL.EXE for commands execution
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
Script adds exclusion path to Windows Defender
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
Found IP address in command line
- powershell.exe (PID: 4208)
Executing commands from a ".bat" file
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 9084)
There is functionality for taking screenshot (YARA)
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 10600)
- wscript.exe (PID: 10652)
The process executes VB scripts
- sihost.exe (PID: 8180)
Executes as Windows Service
- WmiApSrv.exe (PID: 9996)
- VSSVC.exe (PID: 11084)
The process checks if it is being run in the virtual environment
- sihost.exe (PID: 8180)
Searches for installed software
- sihost.exe (PID: 8180)
Loads DLL from Mozilla Firefox
- sihost.exe (PID: 8180)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- wscript.exe (PID: 10600)
INFO
Reads Environment values
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7312)
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
Reads the computer name
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7312)
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
- ShellExperienceHost.exe (PID: 7776)
- sihost.exe (PID: 8180)
The sample compiled with english language support
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7312)
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
- sihost.exe (PID: 8180)
Reads the machine GUID from the registry
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7312)
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
- sihost.exe (PID: 8180)
Process checks computer location settings
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7312)
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
- sihost.exe (PID: 8180)
Checks supported languages
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7312)
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
- ShellExperienceHost.exe (PID: 7776)
- sihost.exe (PID: 8180)
- identity_helper.exe (PID: 10500)
Process checks whether UAC notifications are on
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
- sihost.exe (PID: 8180)
Creates files in the program directory
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
Creates files or folders in the user directory
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
- BackgroundTransferHost.exe (PID: 7316)
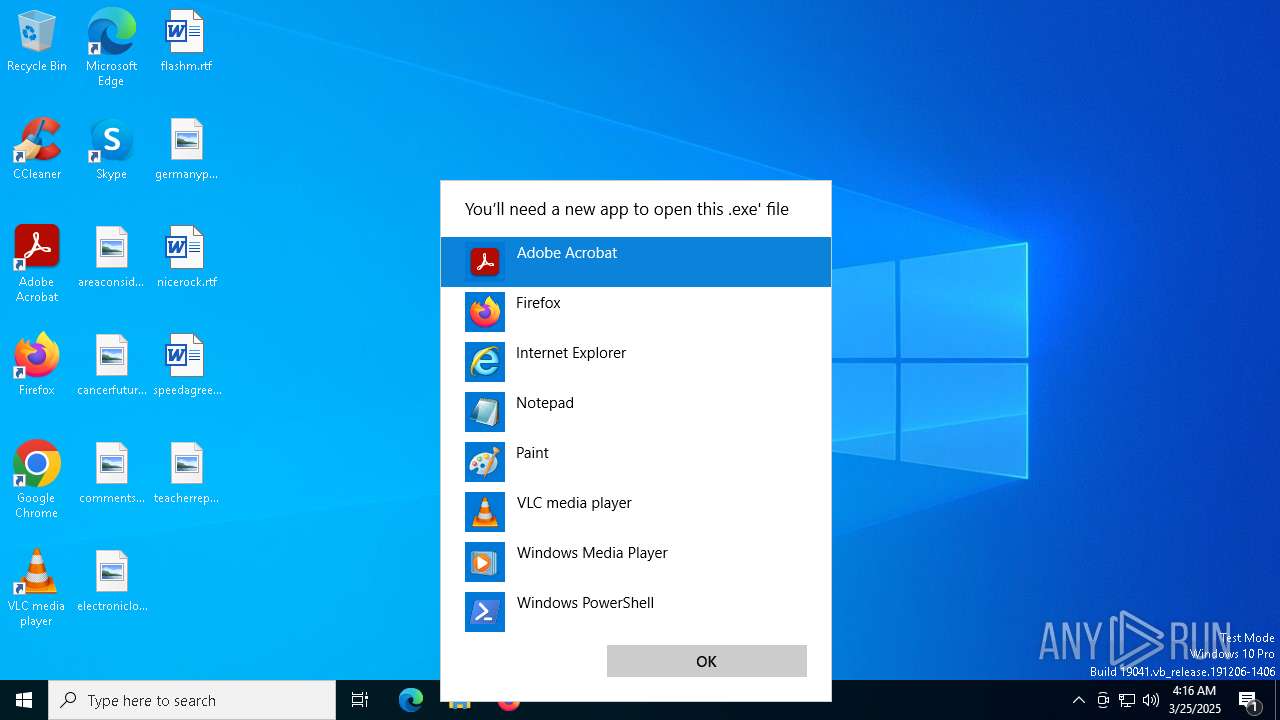
Manual execution by a user
- OpenWith.exe (PID: 1628)
- OpenWith.exe (PID: 5972)
- OpenWith.exe (PID: 5588)
- OpenWith.exe (PID: 2152)
- OpenWith.exe (PID: 1188)
- OpenWith.exe (PID: 7416)
- OpenWith.exe (PID: 1072)
- OpenWith.exe (PID: 6132)
- OpenWith.exe (PID: 8024)
- OpenWith.exe (PID: 8172)
- OpenWith.exe (PID: 5548)
- OpenWith.exe (PID: 8104)
- OpenWith.exe (PID: 7284)
- OpenWith.exe (PID: 4008)
- OpenWith.exe (PID: 4696)
- OpenWith.exe (PID: 7084)
- OpenWith.exe (PID: 6048)
- OpenWith.exe (PID: 2108)
- OpenWith.exe (PID: 4608)
- OpenWith.exe (PID: 4408)
- OpenWith.exe (PID: 7388)
- msedge.exe (PID: 8800)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 5972)
- OpenWith.exe (PID: 5588)
- OpenWith.exe (PID: 2152)
- OpenWith.exe (PID: 1188)
- OpenWith.exe (PID: 1628)
- OpenWith.exe (PID: 7416)
- OpenWith.exe (PID: 1072)
- OpenWith.exe (PID: 6132)
- OpenWith.exe (PID: 8172)
- OpenWith.exe (PID: 5548)
- OpenWith.exe (PID: 8104)
- OpenWith.exe (PID: 7284)
- OpenWith.exe (PID: 4008)
- OpenWith.exe (PID: 4696)
- OpenWith.exe (PID: 7084)
- OpenWith.exe (PID: 8024)
- OpenWith.exe (PID: 6048)
- OpenWith.exe (PID: 2108)
- OpenWith.exe (PID: 4408)
- OpenWith.exe (PID: 7388)
- OpenWith.exe (PID: 4608)
- sihost.exe (PID: 8180)
Create files in a temporary directory
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
- sihost.exe (PID: 8180)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 7316)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 7316)
- sihost.exe (PID: 8180)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 2088)
- BackgroundTransferHost.exe (PID: 7316)
- BackgroundTransferHost.exe (PID: 7376)
- OpenWith.exe (PID: 4608)
- BackgroundTransferHost.exe (PID: 5544)
- BackgroundTransferHost.exe (PID: 7000)
.NET Reactor protector has been detected
- 4bc701fc5e13c1287646e5d1f79760d4.exe (PID: 7584)
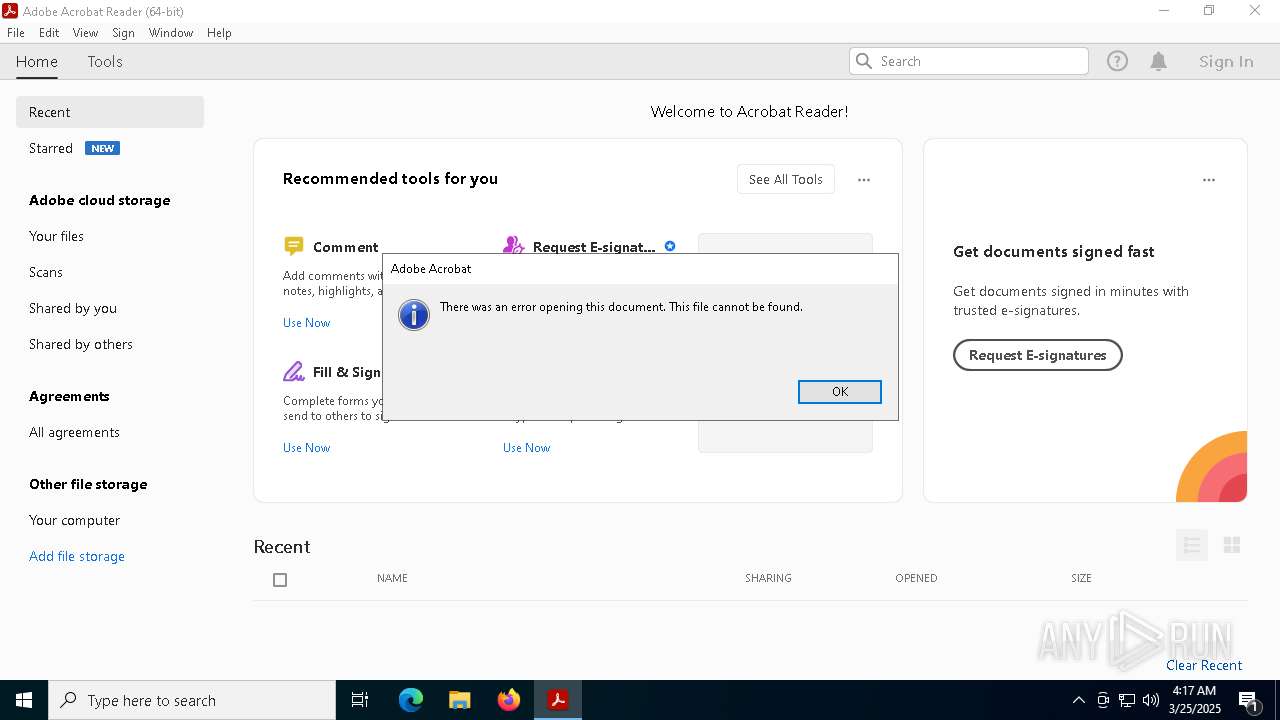
Application launched itself
- Acrobat.exe (PID: 6272)
- AcroCEF.exe (PID: 6988)
- msedge.exe (PID: 8464)
- msedge.exe (PID: 8800)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 2616)
- powershell.exe (PID: 644)
- powershell.exe (PID: 7500)
- powershell.exe (PID: 2980)
- powershell.exe (PID: 6300)
- powershell.exe (PID: 1132)
- powershell.exe (PID: 7404)
- powershell.exe (PID: 1324)
- powershell.exe (PID: 1164)
- powershell.exe (PID: 2908)
- powershell.exe (PID: 1300)
- powershell.exe (PID: 5064)
- powershell.exe (PID: 4208)
- powershell.exe (PID: 4448)
- powershell.exe (PID: 7148)
- powershell.exe (PID: 7676)
- powershell.exe (PID: 6268)
- powershell.exe (PID: 5988)
- powershell.exe (PID: 8056)
- powershell.exe (PID: 3240)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4208)
- powershell.exe (PID: 6268)
- powershell.exe (PID: 1164)
- powershell.exe (PID: 7676)
- powershell.exe (PID: 7148)
- powershell.exe (PID: 1324)
- powershell.exe (PID: 2980)
- powershell.exe (PID: 2908)
- powershell.exe (PID: 5064)
- powershell.exe (PID: 8056)
- powershell.exe (PID: 6300)
- powershell.exe (PID: 7404)
- powershell.exe (PID: 644)
- powershell.exe (PID: 3240)
- powershell.exe (PID: 7500)
- powershell.exe (PID: 2616)
- powershell.exe (PID: 4448)
- powershell.exe (PID: 5988)
- powershell.exe (PID: 1132)
- powershell.exe (PID: 1300)
Disables trace logs
- sihost.exe (PID: 8180)
Reads CPU info
- sihost.exe (PID: 8180)
Reads the time zone
- sihost.exe (PID: 8180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
DcRat
(PID) Process(7584) 4bc701fc5e13c1287646e5d1f79760d4.exe
C2 (1)http://a1101496.xsph.ru/9af4cbe8
Options
MutexDCR_MUTEX-ZcJ9oAfDXe1DHhgonmb4
savebrowsersdatatosinglefiletrue
ignorepartiallyemptydatatrue
cookiestrue
passwordstrue
formstrue
cctrue
historytrue
telegramtrue
steamtrue
discordtrue
filezillatrue
screenshottrue
clipboardtrue
sysinfotrue
searchpath{SYSTEMDRIVE}/Users/{USERNAME}/AppData/Local/;{SYSTEMDRIVE}/Users/{USERNAME}/AppData/Roaming/;D:/
Targetru
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (45.1) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (19.2) |
| .exe | | | Win64 Executable (generic) (17) |
| .scr | | | Windows screen saver (8) |
| .dll | | | Win32 Dynamic Link Library (generic) (4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:05:04 16:03:35+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 3162112 |
| InitializedDataSize: | 13824 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x305f9e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 387.148.792.396 |
| ProductVersionNumber: | 741.557.170.297 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| ProductName: | qwPYHgYUvqN8qn1ZEjrqUo1Y3Na60 |
| CompanyName: | WlGQ8T2ppSmM |
| InternalName: | Yx57U58h1k2h1p1t4D.exe |
| LegalCopyright: | tZDy2KmiitHKaH7 |
| Comments: | f7PPA1ltAOsGzAE |
| OriginalFileName: | OXkMUPDbyXwKxuRi4GNi.exe |
| ProductVersion: | 741.557.170.297 |
| FileVersion: | 387.148.792.396 |
Total processes
334
Monitored processes
191
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | "powershell" -Command Add-MpPreference -ExclusionPath 'C:\Recovery\Logs\dllhost.exe' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | 4bc701fc5e13c1287646e5d1f79760d4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | "C:\WINDOWS\System32\OpenWith.exe" "C:\Program Files (x86)\Windows Photo Viewer\en-US\backgroundTaskHost.exe'" | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | "powershell" -Command Add-MpPreference -ExclusionPath 'C:\Program Files (x86)\Common Files\Microsoft Shared\ink\HWRCustomization\MusNotificationUx.exe' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | 4bc701fc5e13c1287646e5d1f79760d4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | "powershell" -Command Add-MpPreference -ExclusionPath 'C:\Users\admin\Application Data\wininit.exe' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | 4bc701fc5e13c1287646e5d1f79760d4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1188 | schtasks.exe /create /tn "MusNotificationUxM" /sc MINUTE /mo 13 /tr "'C:\Program Files (x86)\Common Files\Microsoft Shared\ink\HWRCustomization\MusNotificationUx.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1188 | "C:\WINDOWS\System32\OpenWith.exe" "C:\Program Files (x86)\Windows Multimedia Platform\ctfmon.exe'" | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | schtasks.exe /create /tn "ctfmonc" /sc MINUTE /mo 5 /tr "'C:\Windows\ModemLogs\ctfmon.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
151 588
Read events
151 299
Write events
283
Delete events
6
Modification events
| (PID) Process: | (7584) 4bc701fc5e13c1287646e5d1f79760d4.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | wininit |
Value: "C:\Users\admin\Application Data\wininit.exe" | |||
| (PID) Process: | (7584) 4bc701fc5e13c1287646e5d1f79760d4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | wininit |
Value: "C:\Users\admin\Application Data\wininit.exe" | |||
| (PID) Process: | (7584) 4bc701fc5e13c1287646e5d1f79760d4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | Shell |
Value: explorer.exe, "C:\Windows\Installer\{420AE50D-8B07-4845-8592-3BECCD71DE80}\firefox.exe", "C:\Program Files\Google\Chrome\Application\122.0.6261.70\Installer\default-browser-agent.exe", "C:\Users\admin\Recent\ctfmon.exe", "C:\Program Files (x86)\Windows Multimedia Platform\ctfmon.exe", "C:\Users\admin\Application Data\wininit.exe" | |||
| (PID) Process: | (7584) 4bc701fc5e13c1287646e5d1f79760d4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (7584) 4bc701fc5e13c1287646e5d1f79760d4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | ConsentPromptBehaviorAdmin |
Value: 0 | |||
| (PID) Process: | (7584) 4bc701fc5e13c1287646e5d1f79760d4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | PromptOnSecureDesktop |
Value: 0 | |||
| (PID) Process: | (7584) 4bc701fc5e13c1287646e5d1f79760d4.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 23004100430042006C006F00620000000000000000000000010000000000000000000000 | |||
| (PID) Process: | (7584) 4bc701fc5e13c1287646e5d1f79760d4.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | firefox |
Value: "C:\Windows\Installer\{420AE50D-8B07-4845-8592-3BECCD71DE80}\firefox.exe" | |||
| (PID) Process: | (7584) 4bc701fc5e13c1287646e5d1f79760d4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | firefox |
Value: "C:\Windows\Installer\{420AE50D-8B07-4845-8592-3BECCD71DE80}\firefox.exe" | |||
| (PID) Process: | (7584) 4bc701fc5e13c1287646e5d1f79760d4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | Shell |
Value: explorer.exe, "C:\Windows\Installer\{420AE50D-8B07-4845-8592-3BECCD71DE80}\firefox.exe" | |||
Executable files
92
Suspicious files
250
Text files
104
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7584 | 4bc701fc5e13c1287646e5d1f79760d4.exe | C:\Windows\Installer\{420AE50D-8B07-4845-8592-3BECCD71DE80}\firefox.exe | executable | |
MD5:4BC701FC5E13C1287646E5D1F79760D4 | SHA256:DA479AC3683EB1B6CC8CEE9967B33D7A299FB551B9A8A1DDD5182469DE37B2FB | |||
| 7584 | 4bc701fc5e13c1287646e5d1f79760d4.exe | C:\Windows\Installer\{420AE50D-8B07-4845-8592-3BECCD71DE80}\0fc223bdacedc3 | text | |
MD5:8B4D3F4A162B8EBDFF0B918A816C4356 | SHA256:A9EBDCDB481E22412A70E47E9602EF5352CE89F46D7A9ADD3DED9499D041A81E | |||
| 7584 | 4bc701fc5e13c1287646e5d1f79760d4.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\26c12092da979c | text | |
MD5:7F529C666B66CB238F96AF8555B30921 | SHA256:0D1142B834134FFAFCB1CE4667CA758F774D4CD0083B59AAEC4DA0594A80D6AD | |||
| 7584 | 4bc701fc5e13c1287646e5d1f79760d4.exe | C:\Program Files\Google\Chrome\Application\122.0.6261.70\Installer\2170b3df528a5f | text | |
MD5:7DC6D603FBD5E562AB89CE94706519E8 | SHA256:72F7FB0379DA37020DDD72B98AEC7E7101E5662FFBCD3793518B0AFB57195208 | |||
| 7584 | 4bc701fc5e13c1287646e5d1f79760d4.exe | C:\Program Files (x86)\Windows Multimedia Platform\ctfmon.exe | executable | |
MD5:4BC701FC5E13C1287646E5D1F79760D4 | SHA256:DA479AC3683EB1B6CC8CEE9967B33D7A299FB551B9A8A1DDD5182469DE37B2FB | |||
| 7584 | 4bc701fc5e13c1287646e5d1f79760d4.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\ctfmon.exe | executable | |
MD5:4BC701FC5E13C1287646E5D1F79760D4 | SHA256:DA479AC3683EB1B6CC8CEE9967B33D7A299FB551B9A8A1DDD5182469DE37B2FB | |||
| 7584 | 4bc701fc5e13c1287646e5d1f79760d4.exe | C:\Program Files (x86)\Windows Photo Viewer\en-US\backgroundTaskHost.exe | executable | |
MD5:4BC701FC5E13C1287646E5D1F79760D4 | SHA256:DA479AC3683EB1B6CC8CEE9967B33D7A299FB551B9A8A1DDD5182469DE37B2FB | |||
| 7584 | 4bc701fc5e13c1287646e5d1f79760d4.exe | C:\Program Files (x86)\Windows Multimedia Platform\26c12092da979c | text | |
MD5:862BA363F890D526532F575ADE17B7E8 | SHA256:05CCF9059EA76311838EAF57C2E7FAB16FCCB70A4E62C081630D2223792C6A1B | |||
| 7584 | 4bc701fc5e13c1287646e5d1f79760d4.exe | C:\found.000\dir_00000002.chk\38384e6a620884 | text | |
MD5:DB94B733653667127823ED754B79AEA5 | SHA256:2824602E679211873CD8B771DAC082737B0E66A635E47AA625CDECB4D6732DA1 | |||
| 7584 | 4bc701fc5e13c1287646e5d1f79760d4.exe | C:\found.000\dir_00000002.chk\SearchApp.exe | executable | |
MD5:4BC701FC5E13C1287646E5D1F79760D4 | SHA256:DA479AC3683EB1B6CC8CEE9967B33D7A299FB551B9A8A1DDD5182469DE37B2FB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
68
TCP/UDP connections
78
DNS requests
62
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4560 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7316 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
8180 | sihost.exe | GET | — | 141.8.193.104:80 | http://a1101496.xsph.ru/9af4cbe8.php?MBpSMz75rpMCNVMFkzl6tetkL=8lxIbDGJqXc&a9bdf0e6df51b632aa7106fb07cb3a43=gZxMjYhFWYmZjNyIDNjBjZ4UzYwczN3cTMjdzMwkzNyMGOiVWN3ImZ5ITMzETOwUDOxITM2IzM&87a21e5fba9364f9111102fd18e0274e=QZ0kjMmdzNxQjM1EDOlRTO0YTNhZDNwcDZ4YTMyUGOzAjNyUTMkNWY&e6c6b1d168ea7693169938c167554ca8=d1nIlRDNzEWOllTMmFTNxEmYmhDO3AzY3EmMkVGO3IzM4I2MhNzMmNGM4IiOiUGNwQGZ3IGNidDM4EWMzQWYxYDMwkDMxYzY1EjZ3QmZiwiIjJWOjNTMilTNjNWN4MGMkJWZ2MzMhJWO1MTNlR2NkZmN2gTZzUjM4IiOiUzMwcjNkV2NzQWZlF2N0YDZiVWO5MWN1ITY4YGOhBzMis3W | unknown | — | — | whitelisted |
7156 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8180 | sihost.exe | GET | 200 | 141.8.193.104:80 | http://a1101496.xsph.ru/9af4cbe8.php?JV8=PLd80SeS&alDsREG30VIiOJ5=pym&wckvReZrUITSz9meF7GXlISA0oBC=4Ld1ap8BSaxpYjsBzs&eef1377fe73a82fe210b7201a6fdbfd9=1efd53a6698e8991347e14b4df4c2364&87a21e5fba9364f9111102fd18e0274e=gNiVDOyYGZmVGOiVzNzETNyUmN0IWZzgTNzMmZ3QzYjljNzgzMyUGN&JV8=PLd80SeS&alDsREG30VIiOJ5=pym&wckvReZrUITSz9meF7GXlISA0oBC=4Ld1ap8BSaxpYjsBzs | unknown | — | — | whitelisted |
7156 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8180 | sihost.exe | GET | 200 | 141.8.193.104:80 | http://a1101496.xsph.ru/9af4cbe8.php?MBpSMz75rpMCNVMFkzl6tetkL=8lxIbDGJqXc&a9bdf0e6df51b632aa7106fb07cb3a43=gZxMjYhFWYmZjNyIDNjBjZ4UzYwczN3cTMjdzMwkzNyMGOiVWN3ImZ5ITMzETOwUDOxITM2IzM&87a21e5fba9364f9111102fd18e0274e=QZ0kjMmdzNxQjM1EDOlRTO0YTNhZDNwcDZ4YTMyUGOzAjNyUTMkNWY&e6c6b1d168ea7693169938c167554ca8=d1nIlBDZlJmZkRWZyITM0MGNlJjZhV2YhRWYwITOmBjNjJDO2IGMzcTZ2IiOiUGNwQGZ3IGNidDM4EWMzQWYxYDMwkDMxYzY1EjZ3QmZiwiIjJWOjNTMilTNjNWN4MGMkJWZ2MzMhJWO1MTNlR2NkZmN2gTZzUjM4IiOiUzMwcjNkV2NzQWZlF2N0YDZiVWO5MWN1ITY4YGOhBzMis3W | unknown | — | — | whitelisted |
8180 | sihost.exe | GET | 200 | 141.8.193.104:80 | http://a1101496.xsph.ru/9af4cbe8.php?MBpSMz75rpMCNVMFkzl6tetkL=8lxIbDGJqXc&a9bdf0e6df51b632aa7106fb07cb3a43=gZxMjYhFWYmZjNyIDNjBjZ4UzYwczN3cTMjdzMwkzNyMGOiVWN3ImZ5ITMzETOwUDOxITM2IzM&87a21e5fba9364f9111102fd18e0274e=QZ0kjMmdzNxQjM1EDOlRTO0YTNhZDNwcDZ4YTMyUGOzAjNyUTMkNWY&eee85876775262fc5beaaf3e1f7e6160=0VfiIiOiUmYyMmN4ADNjFmNwUTO3IGO4IGMiZGMmhjZ4UzNmZTYiwiI4MDO1UzYhRWYjBDOkFTN1kzMmRmZxYDMxADOwYjNzUmYhhjY5kjMlJiOiUGNwQGZ3IGNidDM4EWMzQWYxYDMwkDMxYzY1EjZ3QmZiwiIjJWOjNTMilTNjNWN4MGMkJWZ2MzMhJWO1MTNlR2NkZmN2gTZzUjM4IiOiUzMwcjNkV2NzQWZlF2N0YDZiVWO5MWN1ITY4YGOhBzMis3W | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3216 | svchost.exe | 20.198.162.78:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
6544 | svchost.exe | 20.190.160.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
4560 | backgroundTaskHost.exe | 20.31.169.57:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4560 | backgroundTaskHost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
7316 | BackgroundTransferHost.exe | 92.123.104.34:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected domain Associated with Malware Distribution (xsph .ru) |
2196 | svchost.exe | Misc activity | ET INFO Observed DNS Query to xsph .ru Domain |
8180 | sihost.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |
8180 | sihost.exe | Potentially Bad Traffic | ET HUNTING Observed POST to xsph .ru Domain |
8180 | sihost.exe | A Network Trojan was detected | ET HUNTING Observed Malicious Filename in Outbound POST Request (Information.txt) |