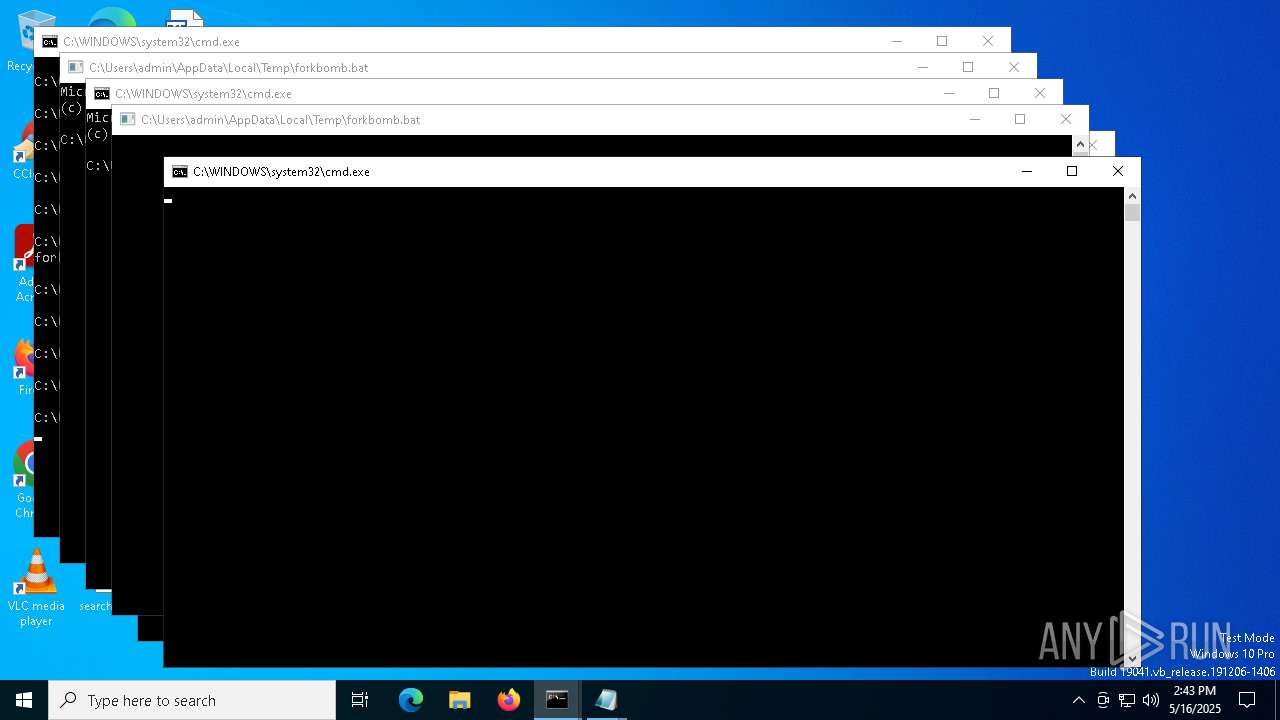
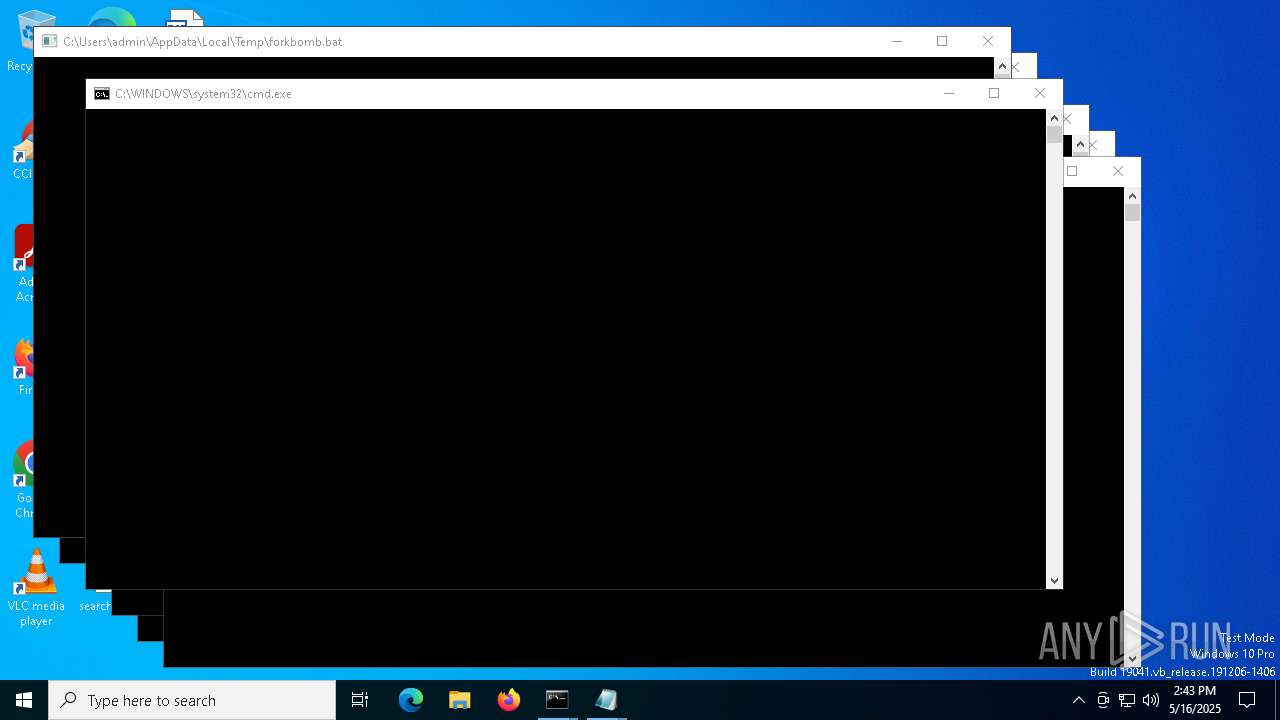
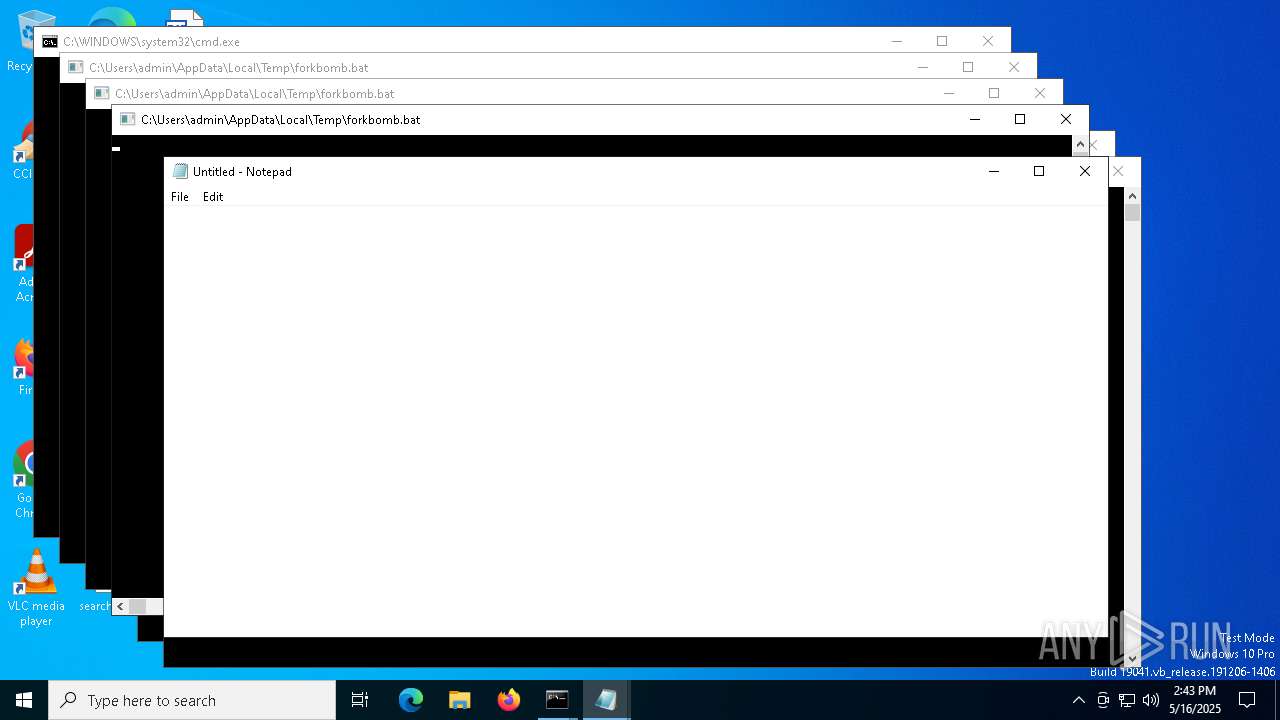
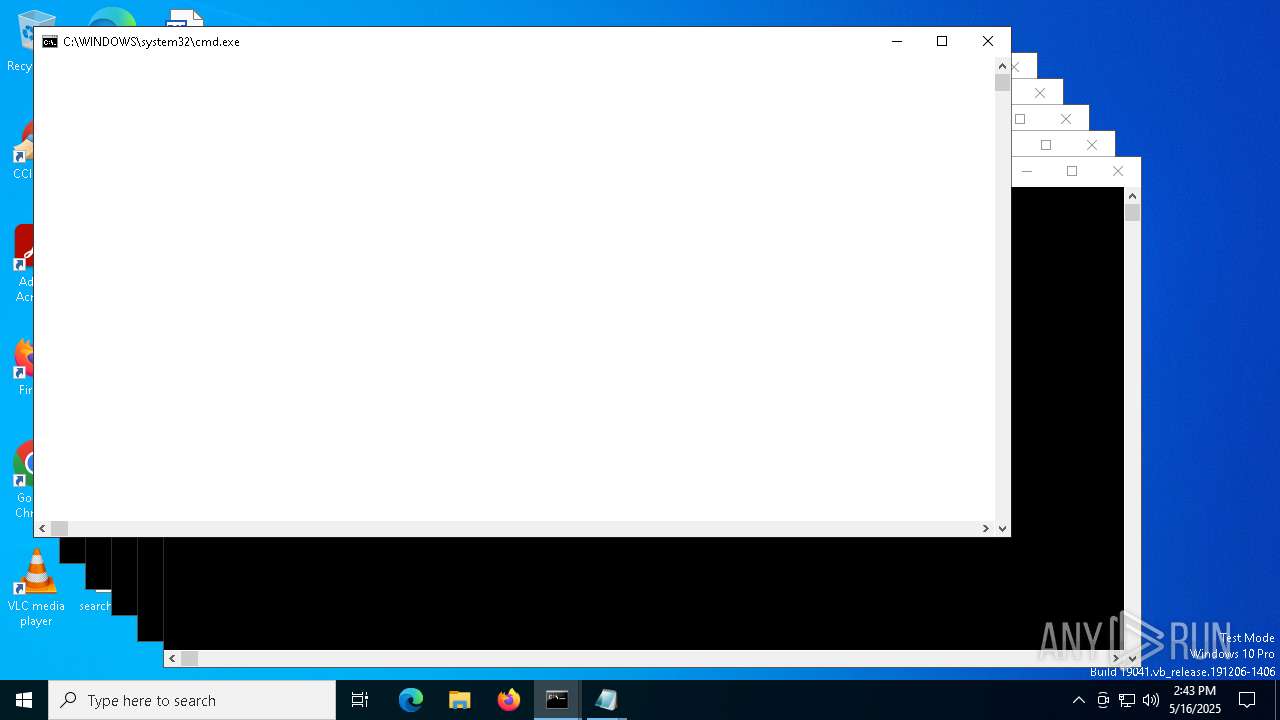
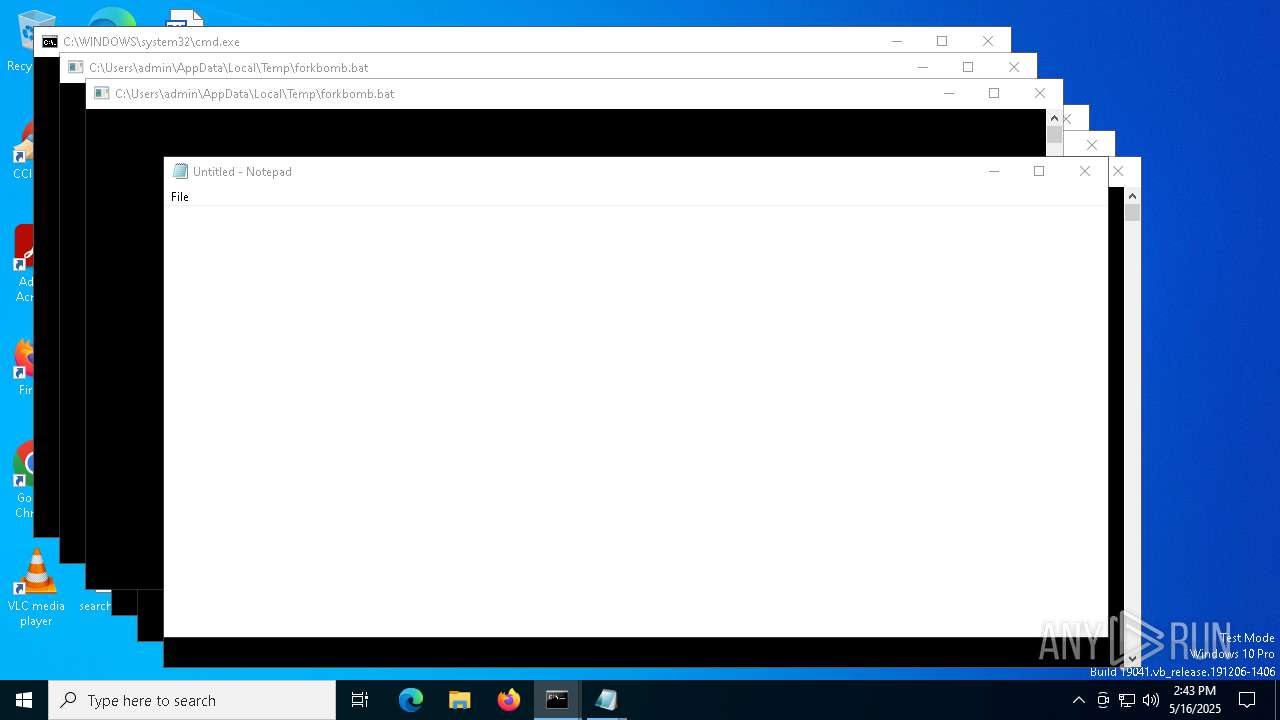
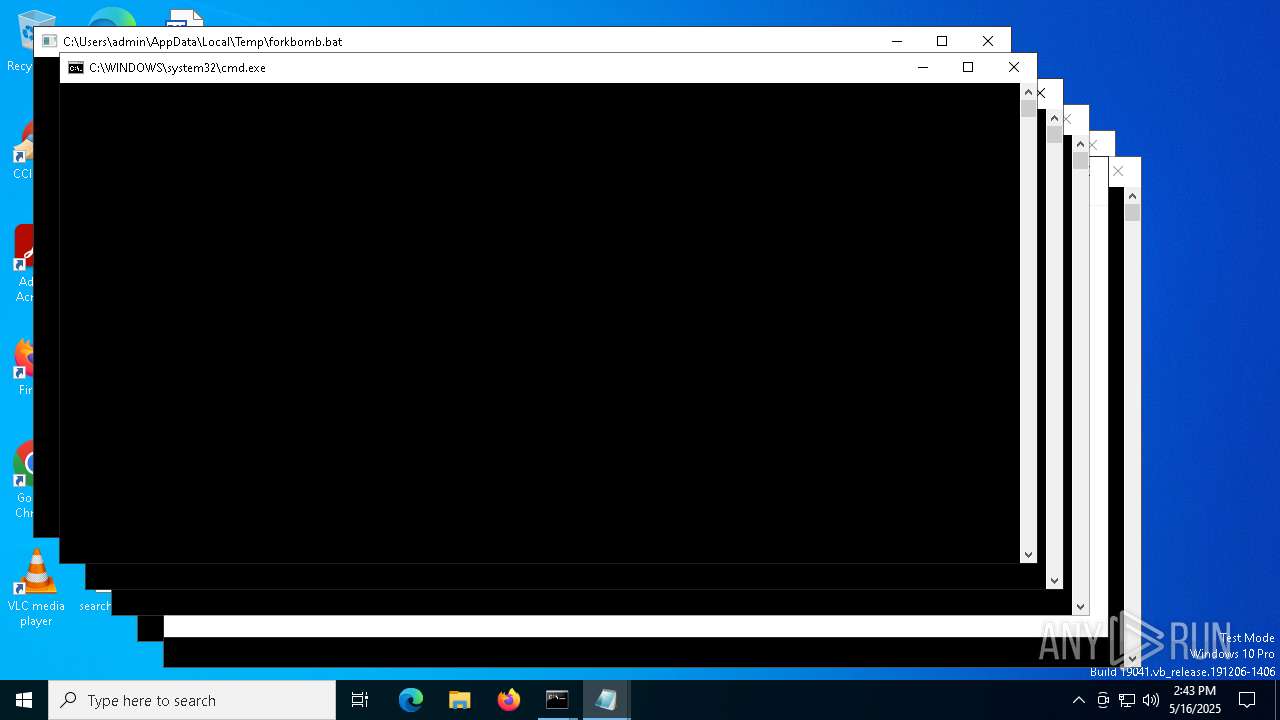
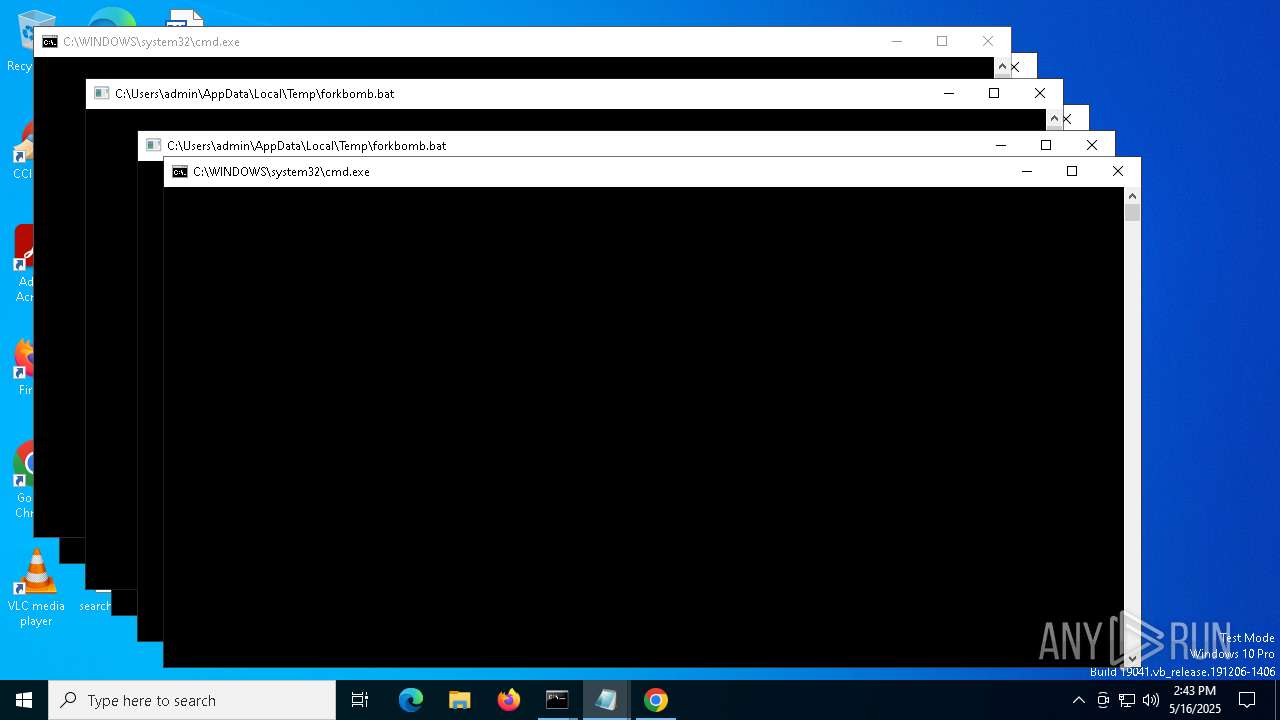
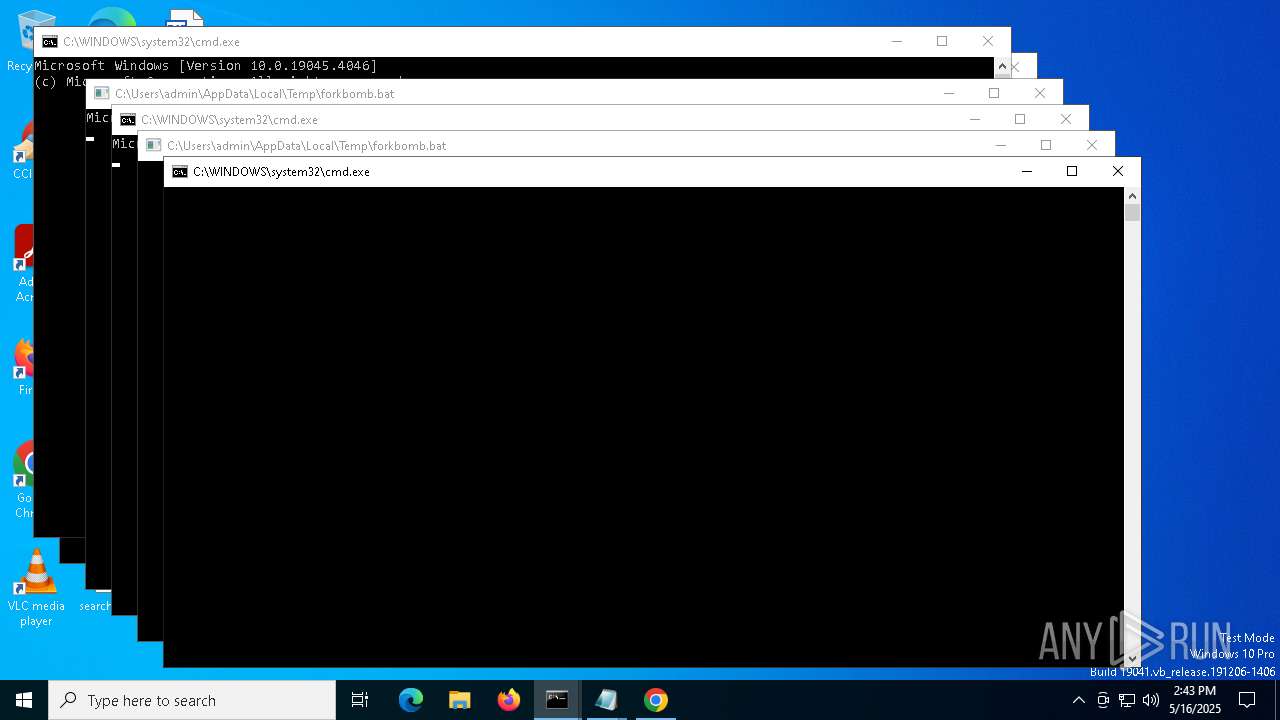
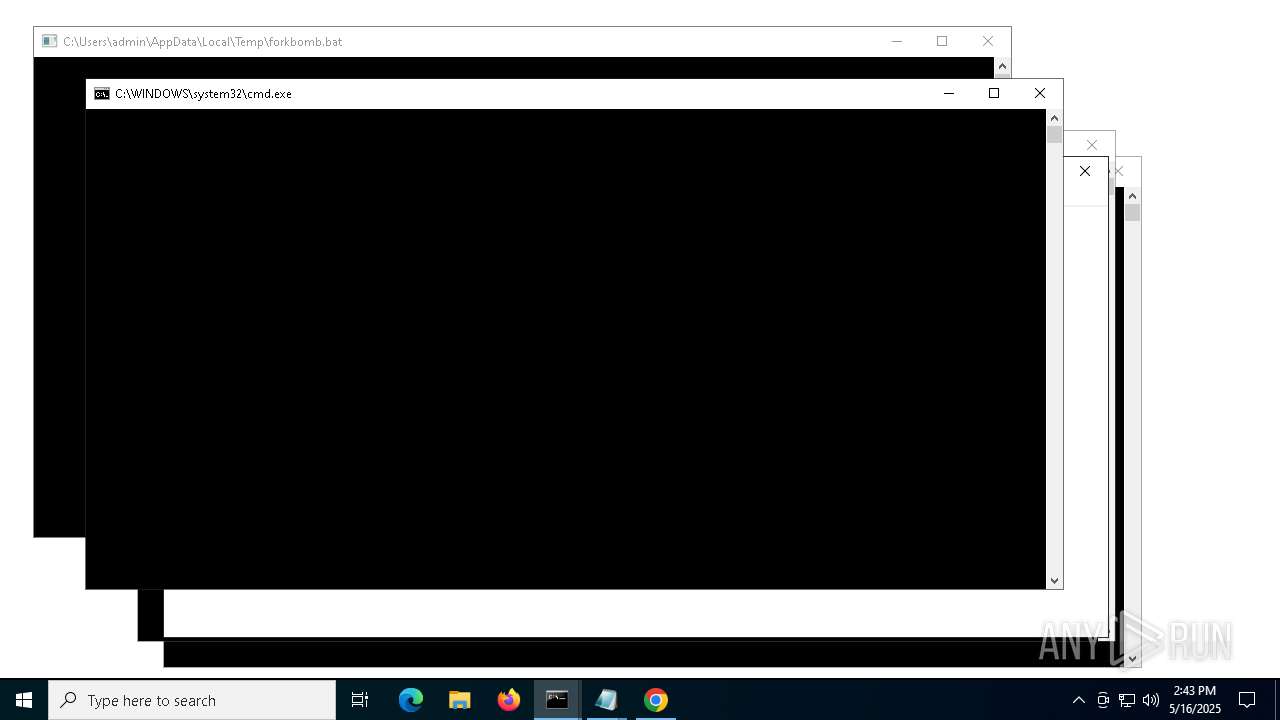
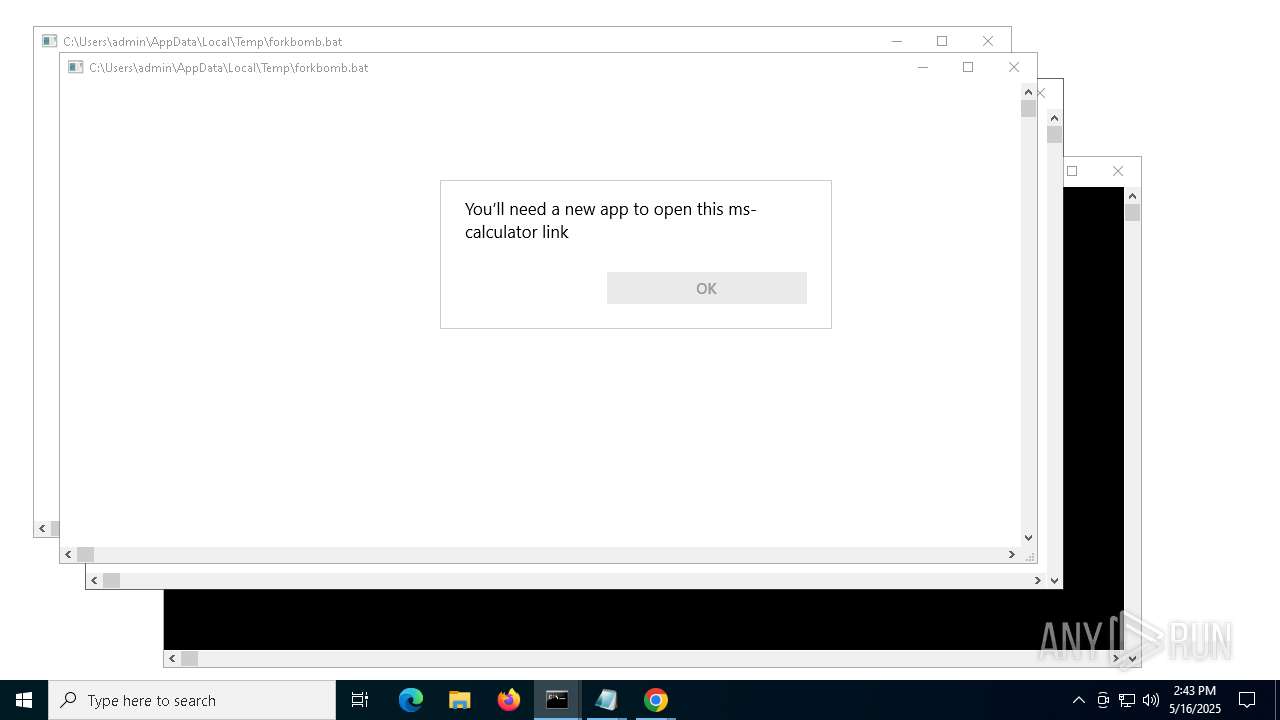
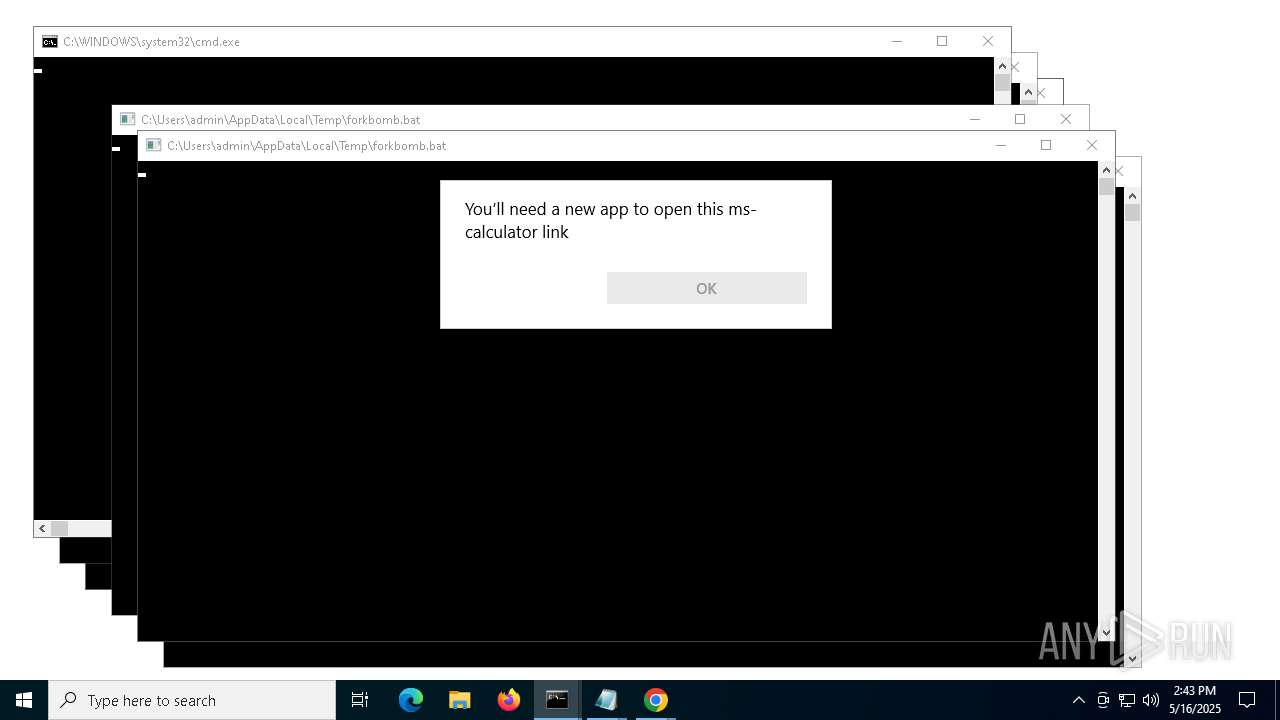
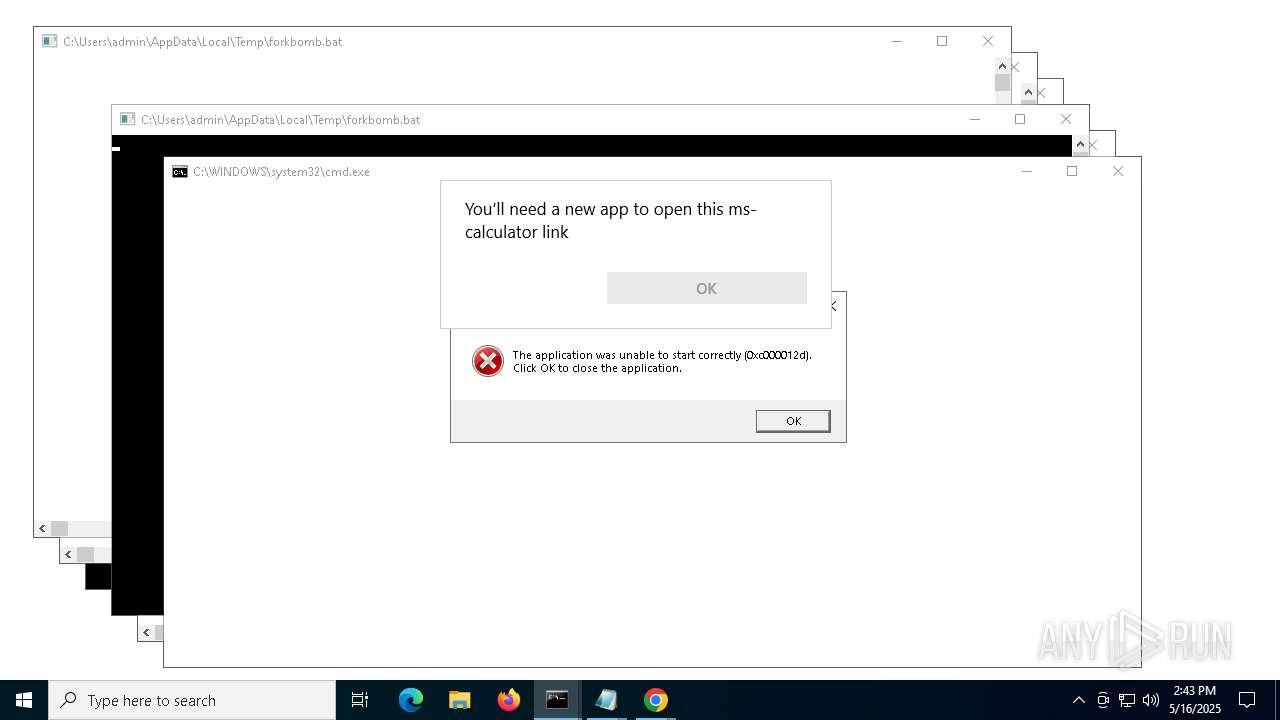
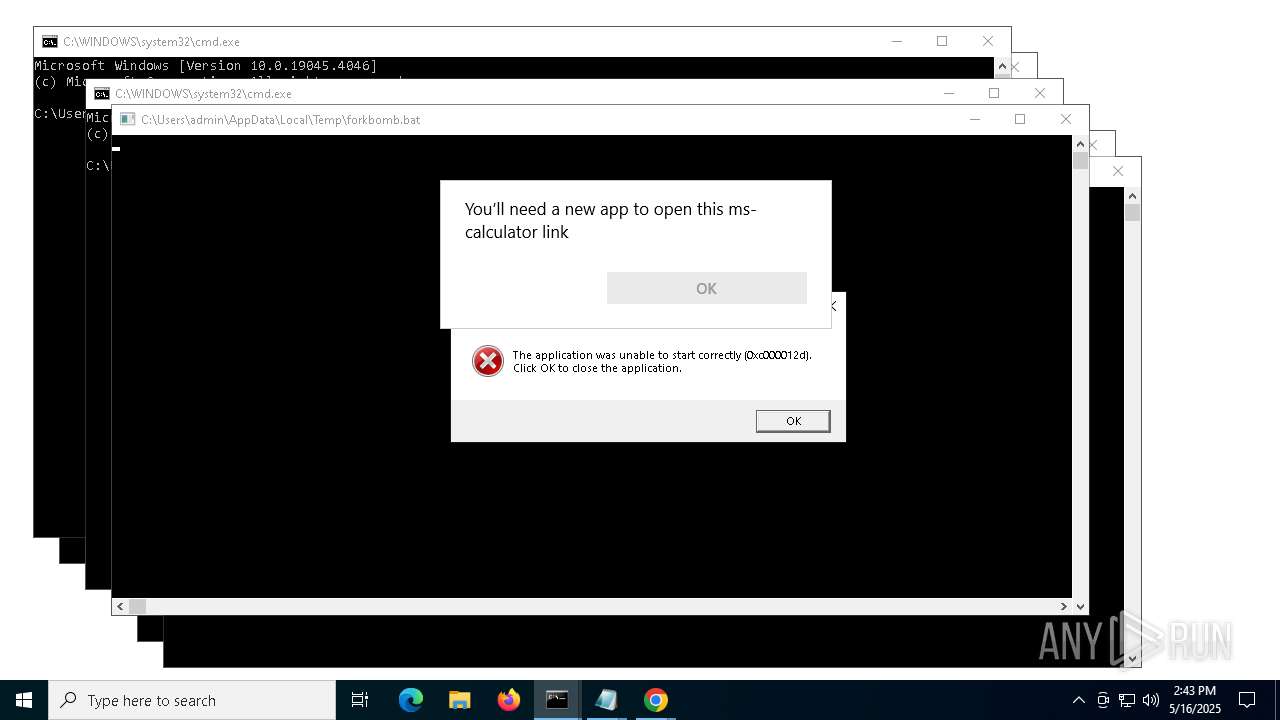
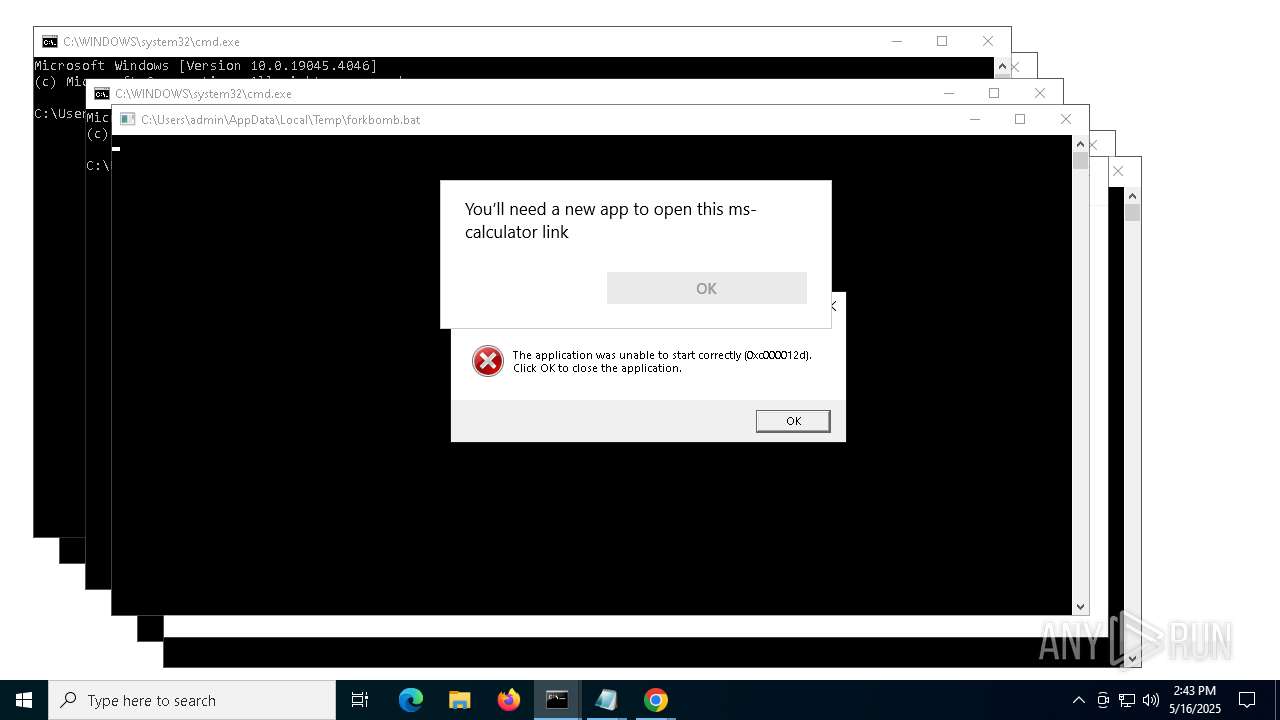
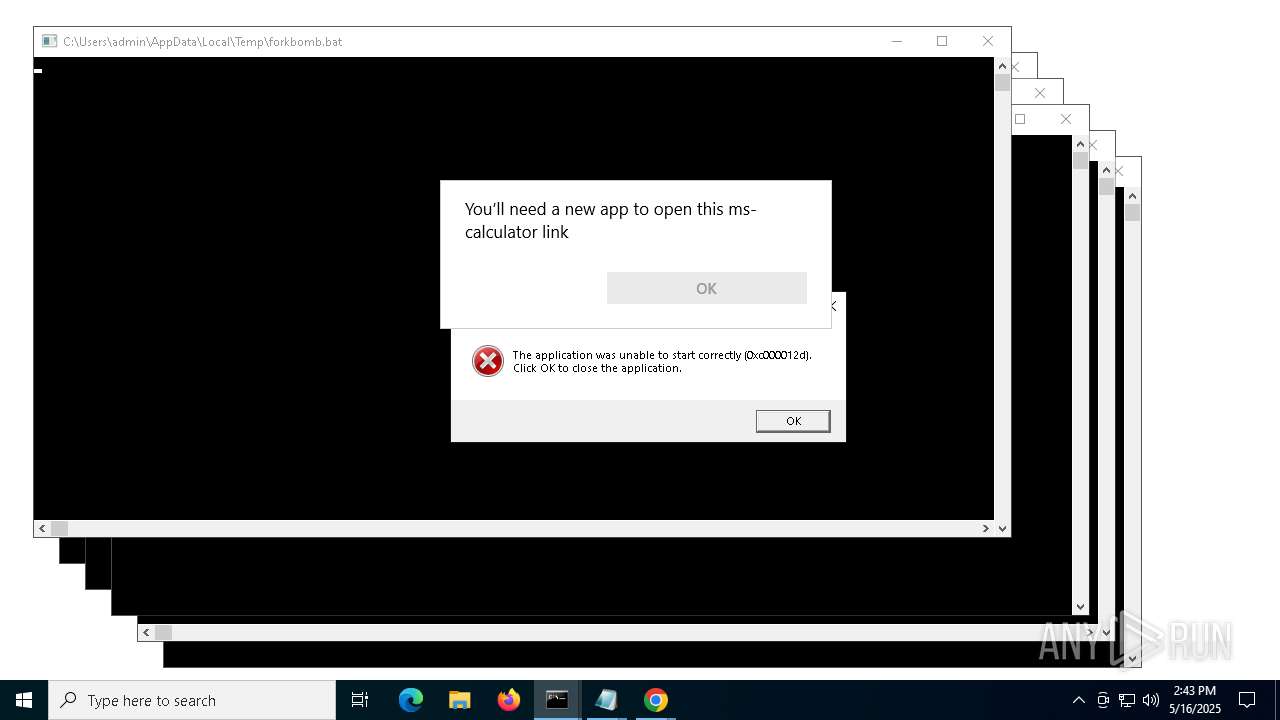
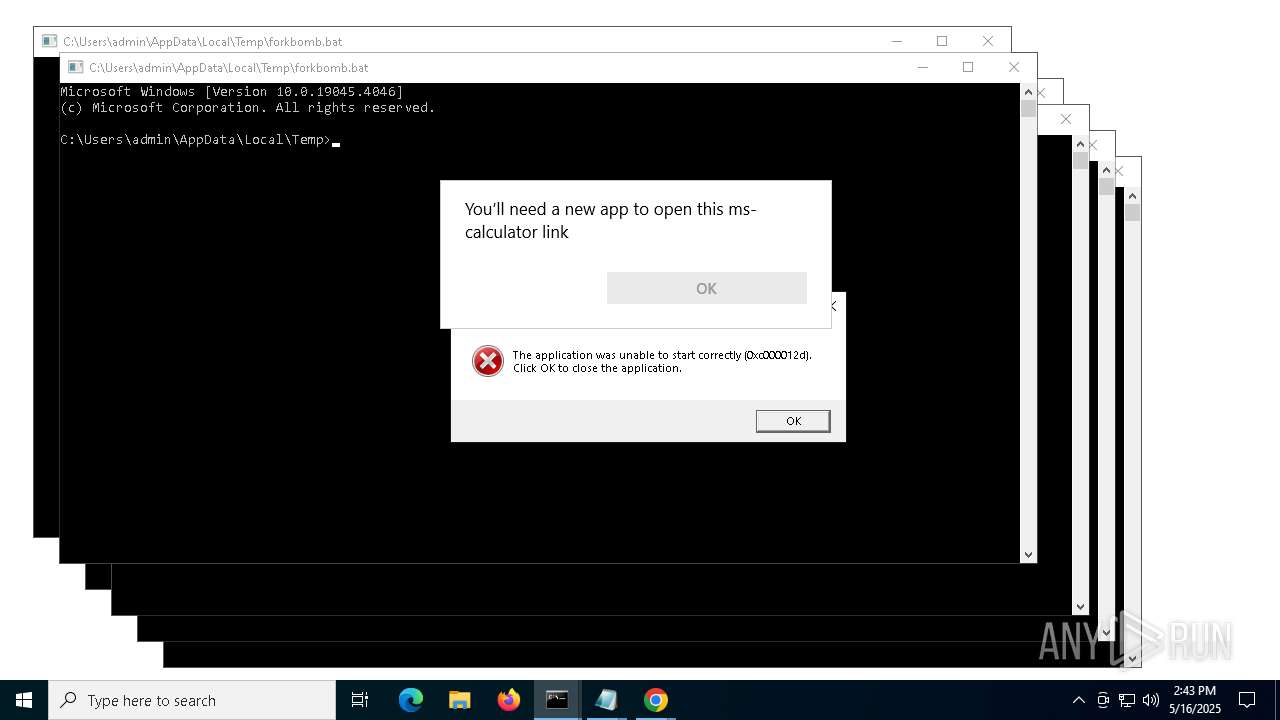
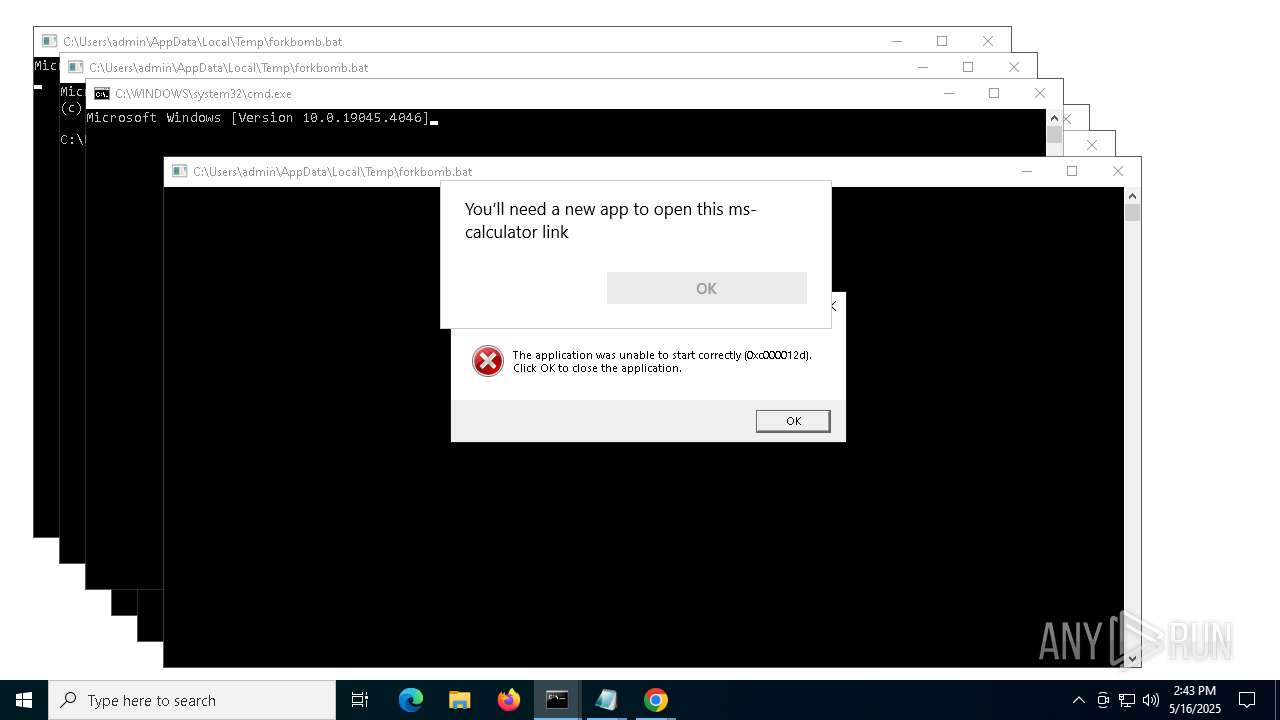
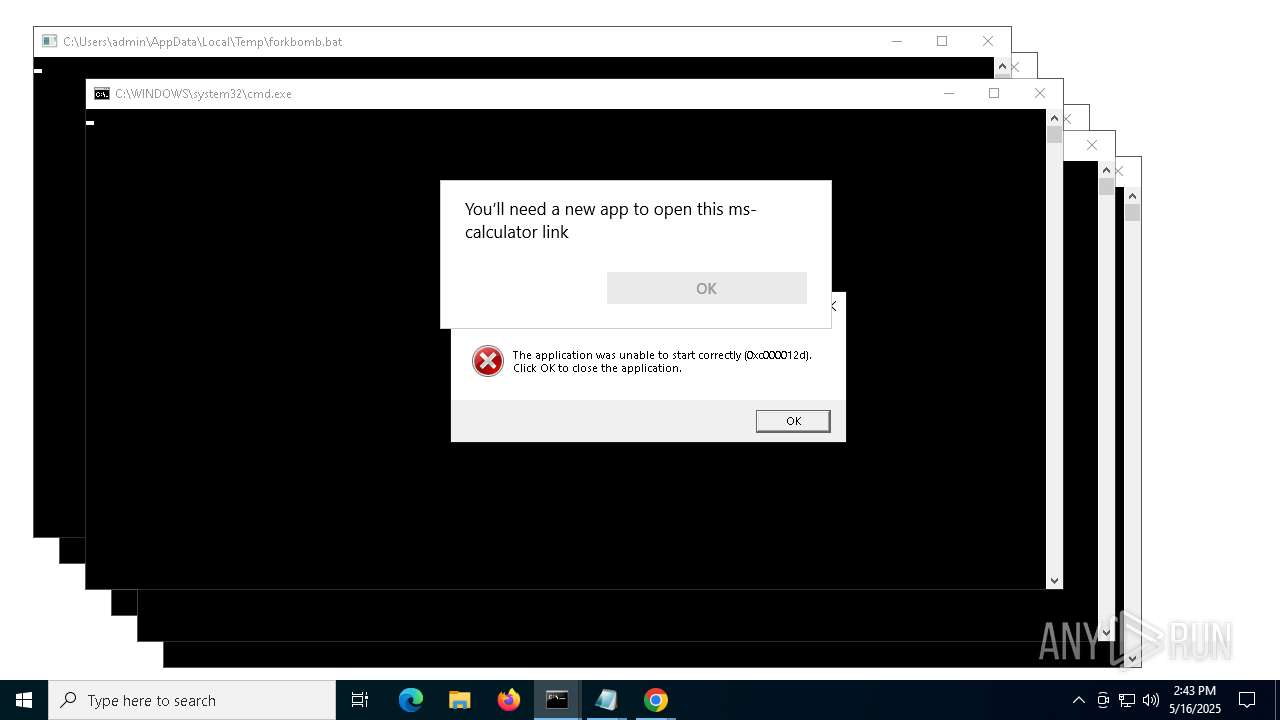
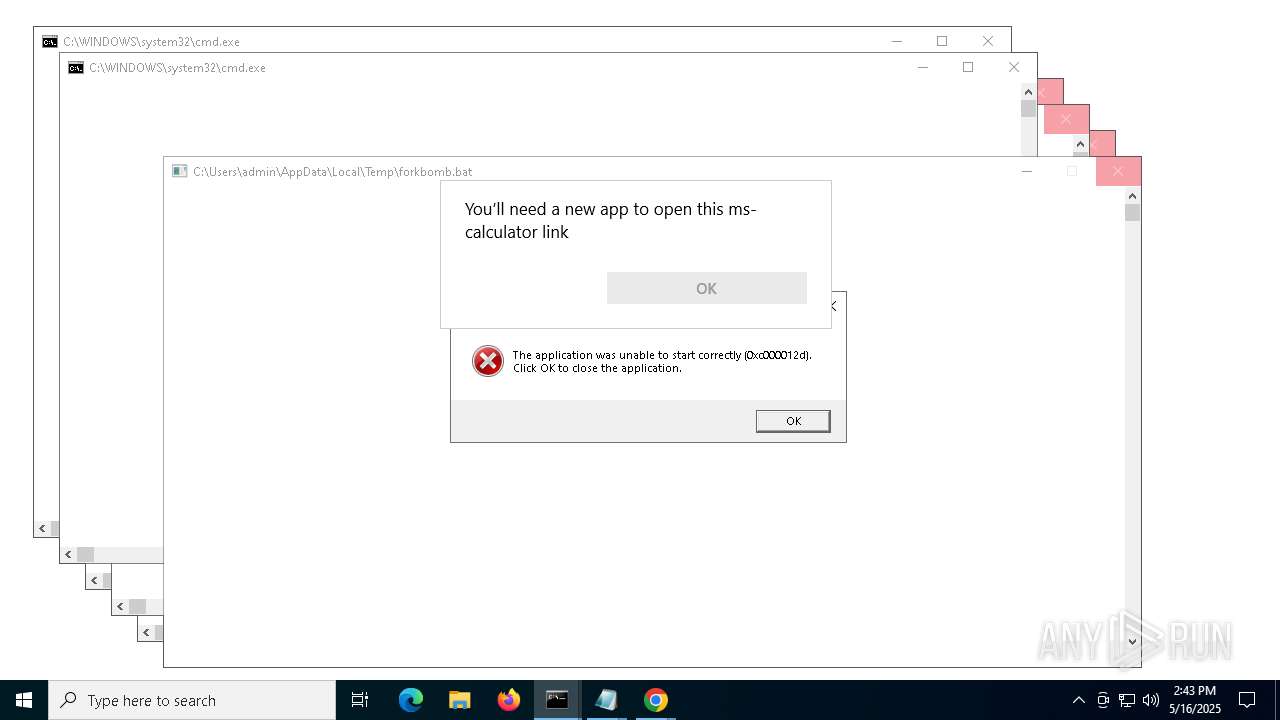
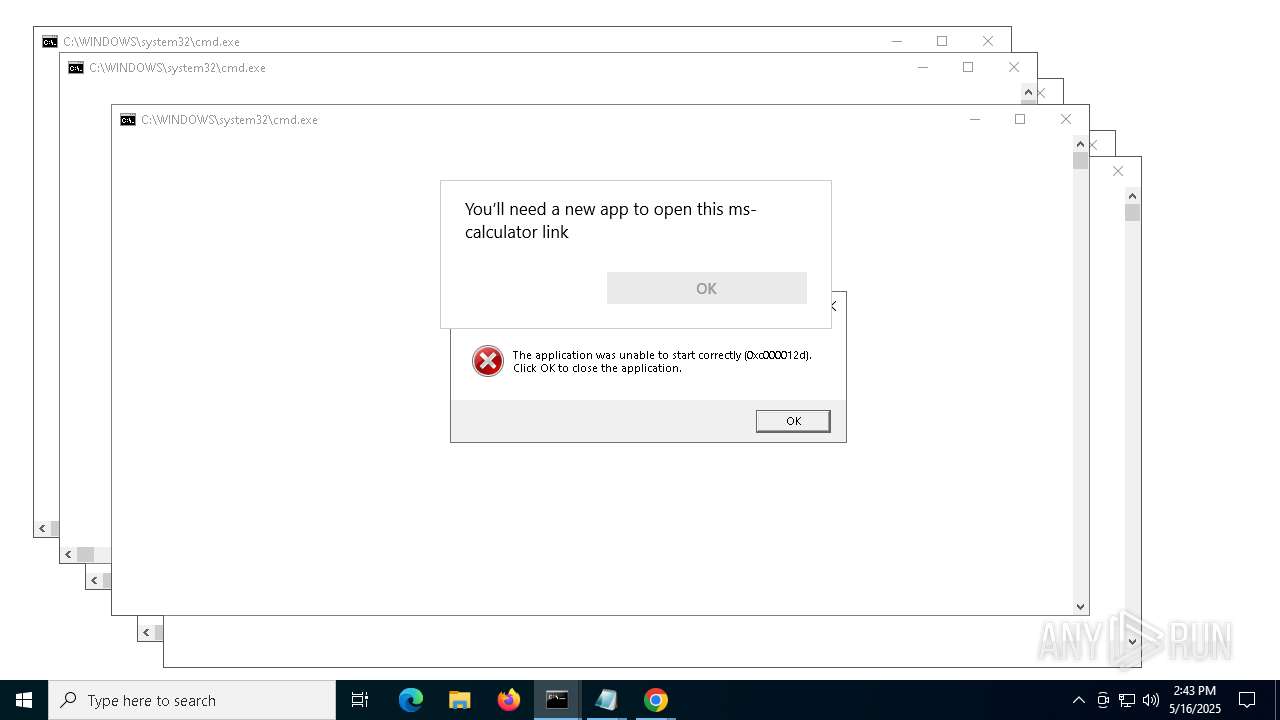
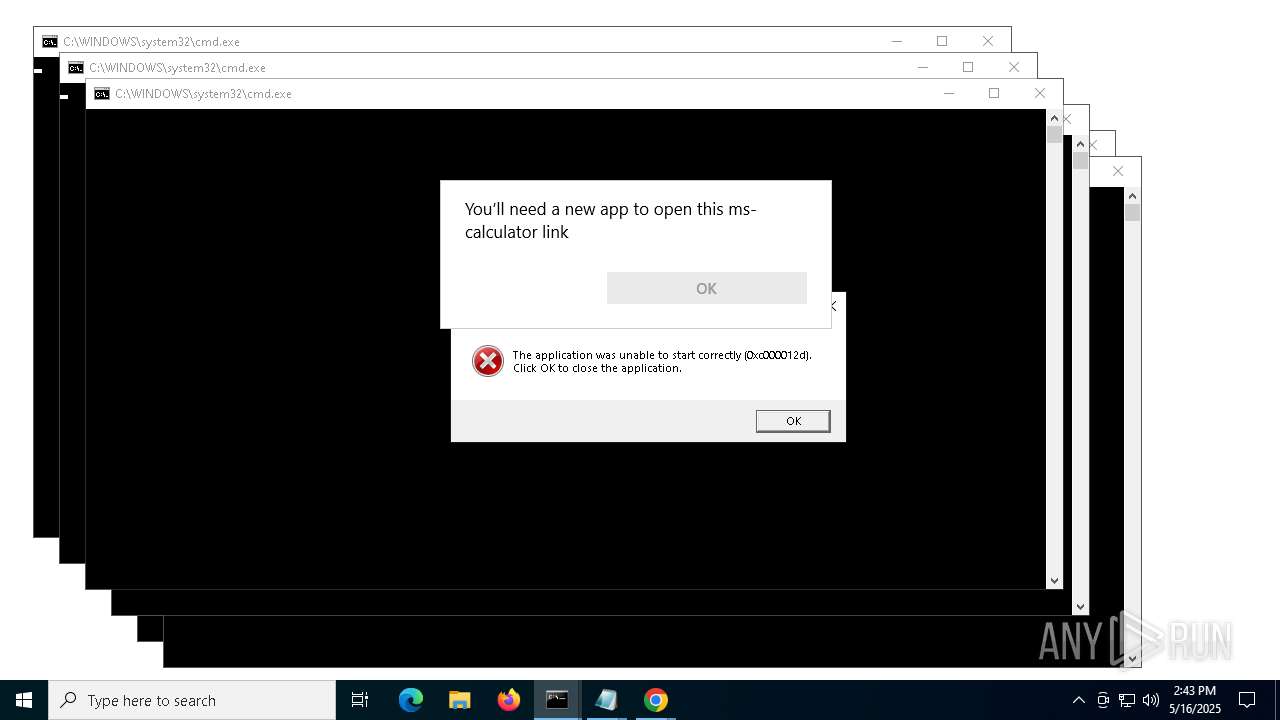
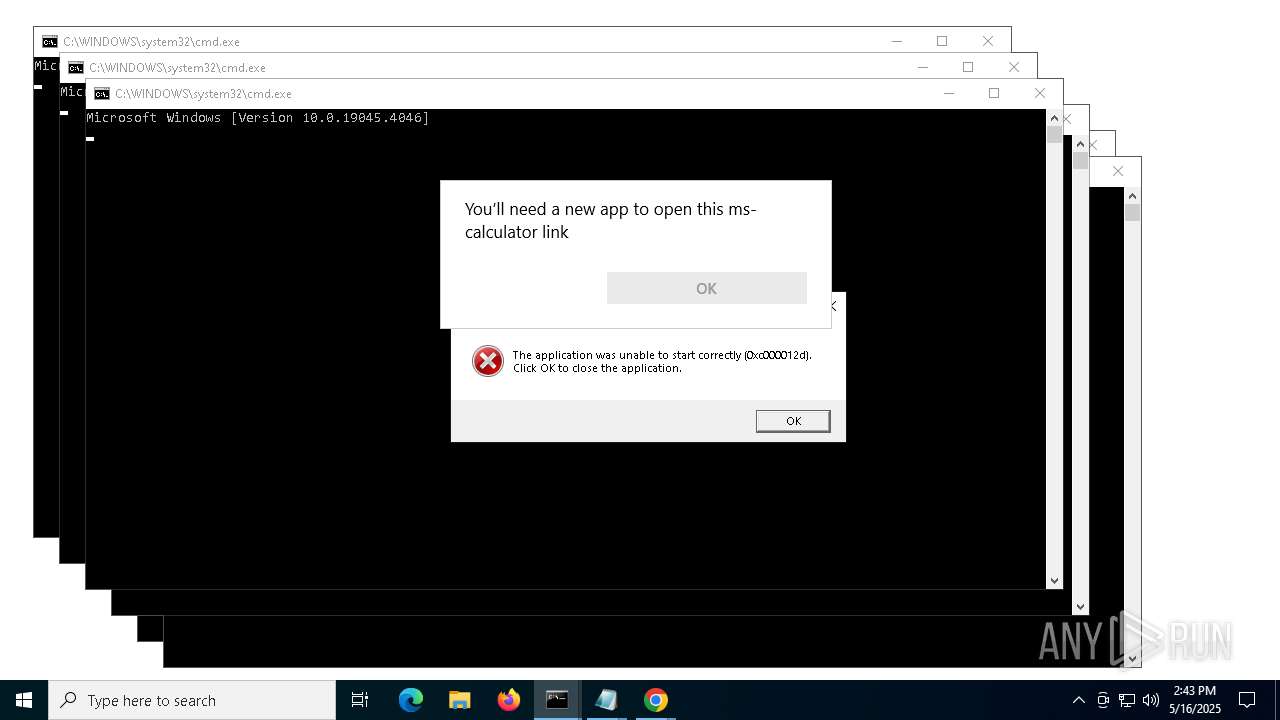
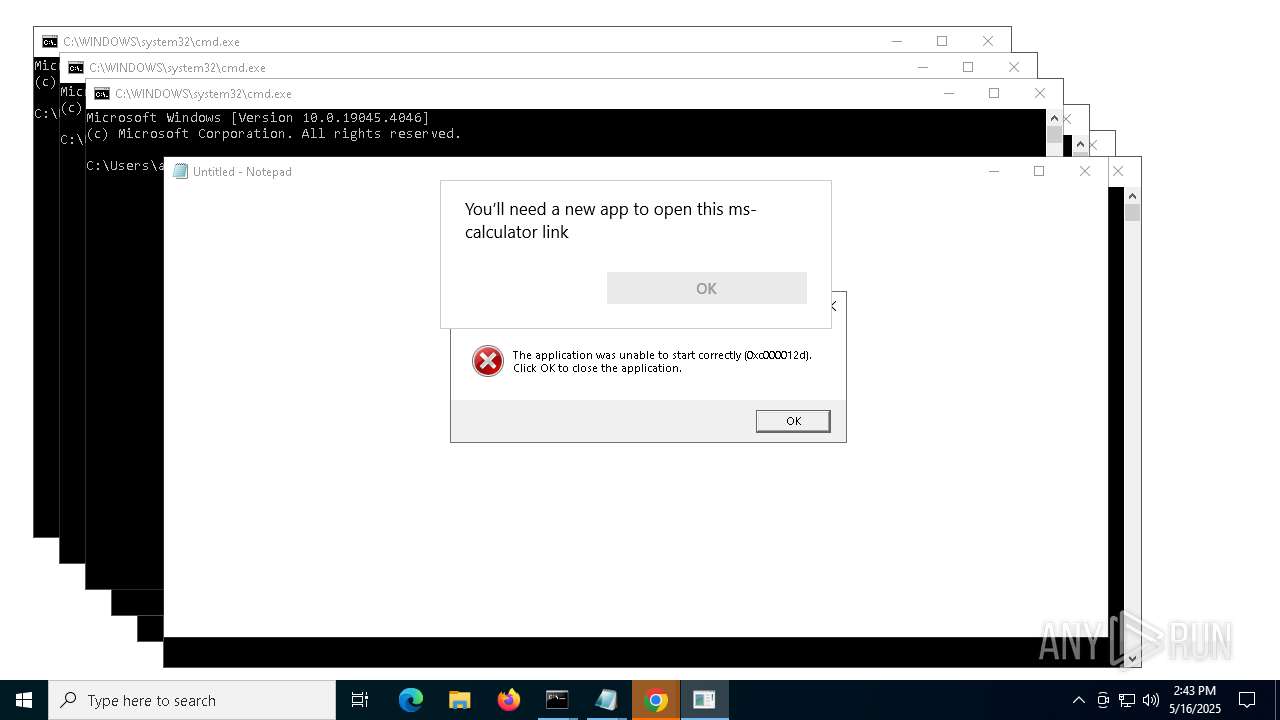
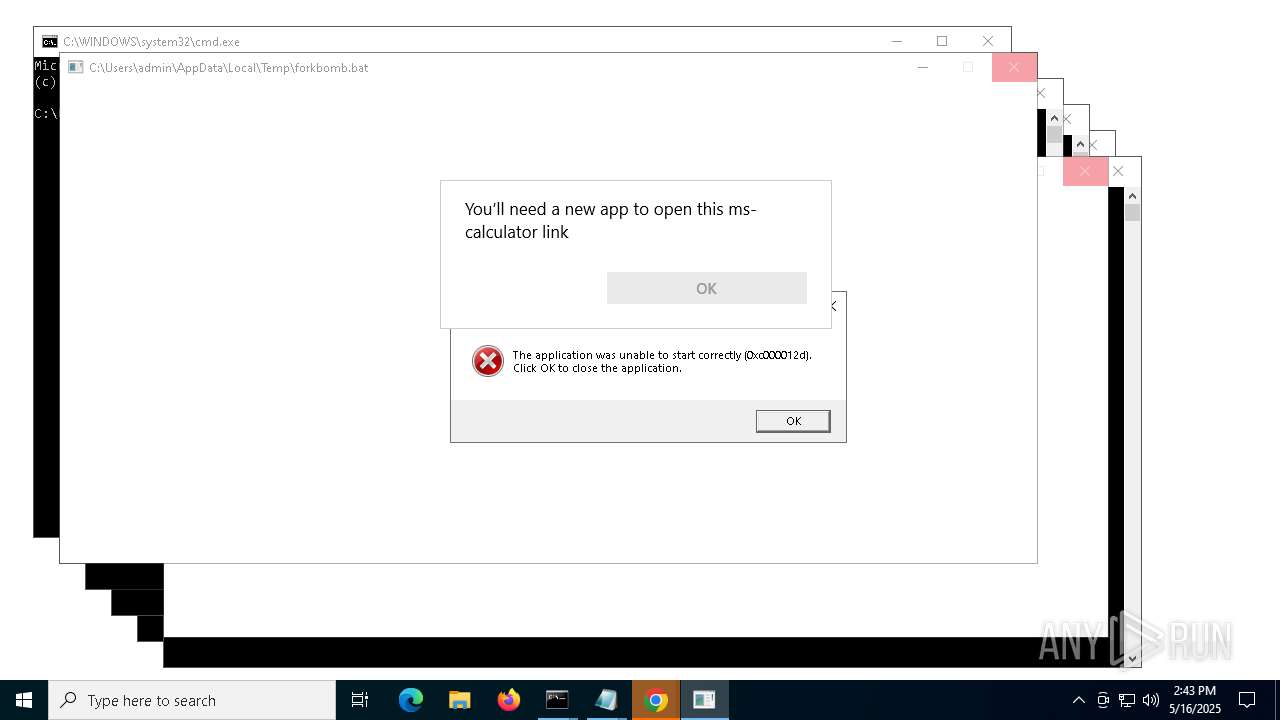
| File name: | forkbomb.bat |
| Full analysis: | https://app.any.run/tasks/e3b3b81b-6cb5-4caa-9a91-3a3b1c286e9a |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 14:42:59 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | E7D8857DF6B11DF65BDBE873970D9CA7 |
| SHA1: | F717B699A2A7768E6AB66BA66FCB2182084545F4 |
| SHA256: | DA3ED97290909567203DCDDF81E2825C37BD10C100FA7F10D0355C54A7369608 |
| SSDEEP: | 3:MRK5j2idN+KTIk9WKf9No+KaXMJZqoAAn:TyidNzd9H96hqNAn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6516)
- cmd.exe (PID: 7324)
- cmd.exe (PID: 7332)
- cmd.exe (PID: 7768)
- cmd.exe (PID: 7788)
- cmd.exe (PID: 7760)
- cmd.exe (PID: 7780)
- cmd.exe (PID: 8724)
- cmd.exe (PID: 8716)
- cmd.exe (PID: 8788)
- cmd.exe (PID: 9072)
- cmd.exe (PID: 8768)
- cmd.exe (PID: 9788)
- cmd.exe (PID: 9084)
- cmd.exe (PID: 9780)
- cmd.exe (PID: 10324)
- cmd.exe (PID: 10332)
- cmd.exe (PID: 10976)
- cmd.exe (PID: 10960)
- cmd.exe (PID: 10992)
- cmd.exe (PID: 10908)
- cmd.exe (PID: 11004)
- cmd.exe (PID: 11484)
- cmd.exe (PID: 11316)
- cmd.exe (PID: 12320)
- cmd.exe (PID: 11204)
- cmd.exe (PID: 11220)
- cmd.exe (PID: 10864)
- cmd.exe (PID: 12304)
- cmd.exe (PID: 11300)
- cmd.exe (PID: 13088)
- cmd.exe (PID: 11324)
- cmd.exe (PID: 13892)
- cmd.exe (PID: 13264)
- cmd.exe (PID: 14584)
- cmd.exe (PID: 15136)
- cmd.exe (PID: 14332)
- cmd.exe (PID: 14472)
- cmd.exe (PID: 14488)
- cmd.exe (PID: 14504)
- cmd.exe (PID: 15008)
- cmd.exe (PID: 15308)
- cmd.exe (PID: 14780)
- cmd.exe (PID: 14292)
- cmd.exe (PID: 14496)
- cmd.exe (PID: 8292)
- cmd.exe (PID: 11816)
- cmd.exe (PID: 8988)
- cmd.exe (PID: 10928)
- cmd.exe (PID: 8288)
- cmd.exe (PID: 16948)
Application launched itself
- cmd.exe (PID: 6516)
- cmd.exe (PID: 7324)
- cmd.exe (PID: 7332)
- cmd.exe (PID: 7768)
- cmd.exe (PID: 7780)
- cmd.exe (PID: 7760)
- cmd.exe (PID: 7788)
- cmd.exe (PID: 8724)
- cmd.exe (PID: 8788)
- cmd.exe (PID: 8716)
- cmd.exe (PID: 9072)
- cmd.exe (PID: 8768)
- cmd.exe (PID: 9788)
- cmd.exe (PID: 9084)
- cmd.exe (PID: 9780)
- cmd.exe (PID: 10332)
- cmd.exe (PID: 10324)
- cmd.exe (PID: 10908)
- cmd.exe (PID: 10960)
- cmd.exe (PID: 11220)
- cmd.exe (PID: 10992)
- cmd.exe (PID: 11204)
- cmd.exe (PID: 11004)
- cmd.exe (PID: 10976)
- cmd.exe (PID: 12304)
- cmd.exe (PID: 10864)
- cmd.exe (PID: 11316)
- cmd.exe (PID: 11300)
- cmd.exe (PID: 12320)
- cmd.exe (PID: 11484)
- cmd.exe (PID: 13088)
- cmd.exe (PID: 11324)
- cmd.exe (PID: 13264)
- cmd.exe (PID: 15136)
- cmd.exe (PID: 14584)
- cmd.exe (PID: 14780)
- cmd.exe (PID: 13892)
- cmd.exe (PID: 14292)
- cmd.exe (PID: 14472)
- cmd.exe (PID: 14504)
- cmd.exe (PID: 14488)
- cmd.exe (PID: 15008)
- cmd.exe (PID: 15308)
- cmd.exe (PID: 14496)
- cmd.exe (PID: 14332)
- cmd.exe (PID: 8292)
- cmd.exe (PID: 8988)
- cmd.exe (PID: 8288)
- cmd.exe (PID: 11816)
- cmd.exe (PID: 10928)
- cmd.exe (PID: 16948)
Executing commands from a ".bat" file
- cmd.exe (PID: 6516)
- cmd.exe (PID: 7332)
- cmd.exe (PID: 7324)
- cmd.exe (PID: 7780)
- cmd.exe (PID: 7760)
- cmd.exe (PID: 7788)
- cmd.exe (PID: 8724)
- cmd.exe (PID: 8716)
- cmd.exe (PID: 8768)
- cmd.exe (PID: 8788)
- cmd.exe (PID: 9780)
- cmd.exe (PID: 9084)
- cmd.exe (PID: 9072)
- cmd.exe (PID: 10324)
- cmd.exe (PID: 10332)
- cmd.exe (PID: 7768)
- cmd.exe (PID: 10976)
- cmd.exe (PID: 10992)
- cmd.exe (PID: 11220)
- cmd.exe (PID: 10908)
- cmd.exe (PID: 11004)
- cmd.exe (PID: 10960)
- cmd.exe (PID: 11204)
- cmd.exe (PID: 12320)
- cmd.exe (PID: 13088)
- cmd.exe (PID: 11316)
- cmd.exe (PID: 12304)
- cmd.exe (PID: 13264)
- cmd.exe (PID: 13892)
- cmd.exe (PID: 10864)
- cmd.exe (PID: 14292)
- cmd.exe (PID: 11300)
- cmd.exe (PID: 14584)
- cmd.exe (PID: 11484)
- cmd.exe (PID: 11324)
INFO
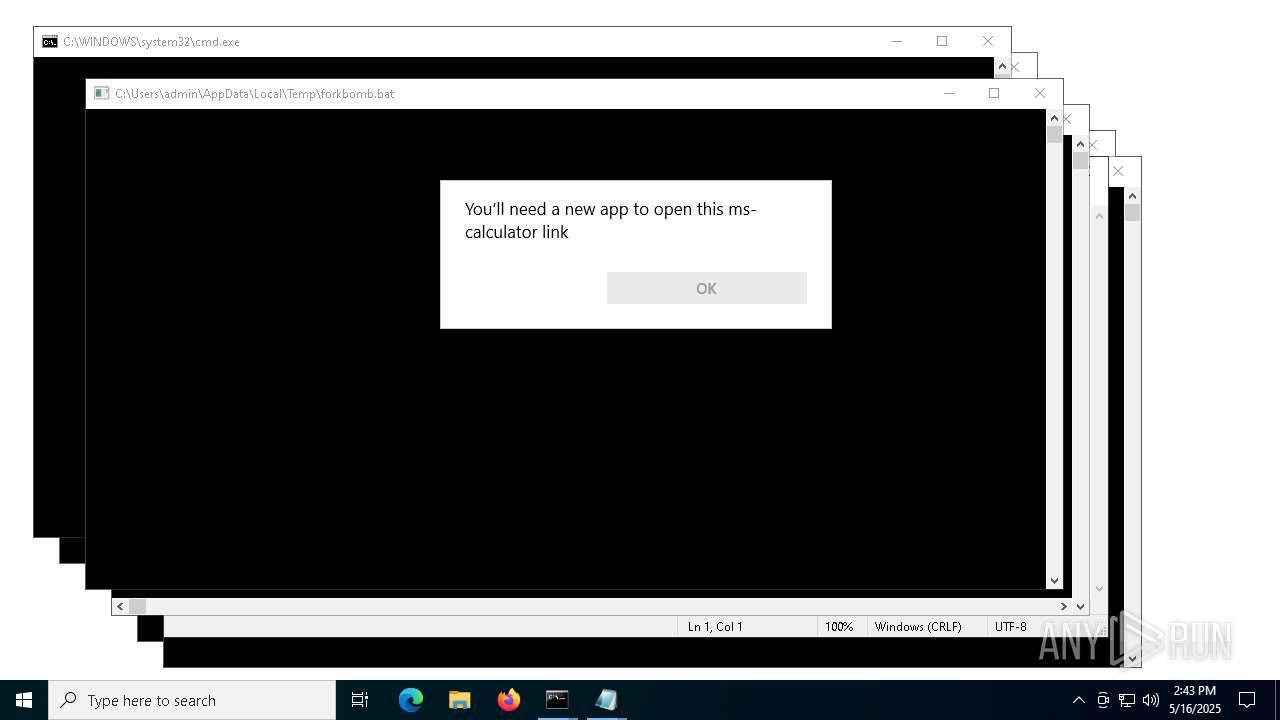
Reads security settings of Internet Explorer
- calc.exe (PID: 7184)
- calc.exe (PID: 7404)
- calc.exe (PID: 7380)
- calc.exe (PID: 7964)
- calc.exe (PID: 7924)
- calc.exe (PID: 7892)
- calc.exe (PID: 9424)
- calc.exe (PID: 8812)
- calc.exe (PID: 9136)
- calc.exe (PID: 9344)
- calc.exe (PID: 9236)
- calc.exe (PID: 9940)
- calc.exe (PID: 10560)
- calc.exe (PID: 10568)
- calc.exe (PID: 10804)
- calc.exe (PID: 11448)
- calc.exe (PID: 11356)
- calc.exe (PID: 10636)
- calc.exe (PID: 11124)
- calc.exe (PID: 11240)
- calc.exe (PID: 9176)
- calc.exe (PID: 7848)
- calc.exe (PID: 12952)
- calc.exe (PID: 13656)
- calc.exe (PID: 13688)
- OpenWith.exe (PID: 9688)
- calc.exe (PID: 13648)
- OpenWith.exe (PID: 9896)
- OpenWith.exe (PID: 7996)
- OpenWith.exe (PID: 8532)
- calc.exe (PID: 11092)
- calc.exe (PID: 13028)
- OpenWith.exe (PID: 9808)
Application launched itself
- chrome.exe (PID: 7316)
- chrome.exe (PID: 7736)
- chrome.exe (PID: 8636)
- chrome.exe (PID: 8616)
- chrome.exe (PID: 7724)
- chrome.exe (PID: 8700)
- chrome.exe (PID: 8736)
- chrome.exe (PID: 10276)
- chrome.exe (PID: 10772)
- chrome.exe (PID: 10780)
- chrome.exe (PID: 10824)
- chrome.exe (PID: 11032)
- chrome.exe (PID: 11024)
- chrome.exe (PID: 10876)
- chrome.exe (PID: 11864)
- chrome.exe (PID: 12376)
- chrome.exe (PID: 13520)
- chrome.exe (PID: 14196)
- chrome.exe (PID: 14204)
- chrome.exe (PID: 14260)
- chrome.exe (PID: 14564)
- chrome.exe (PID: 14020)
- chrome.exe (PID: 15648)
- chrome.exe (PID: 14572)
- chrome.exe (PID: 2148)
- chrome.exe (PID: 2236)
- chrome.exe (PID: 16348)
- chrome.exe (PID: 4892)
- chrome.exe (PID: 16660)
- chrome.exe (PID: 16408)
- chrome.exe (PID: 16520)
- chrome.exe (PID: 16464)
- chrome.exe (PID: 6192)
- chrome.exe (PID: 16584)
- chrome.exe (PID: 13912)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
581
Monitored processes
449
Malicious processes
23
Suspicious processes
12
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 456 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x218,0x21c,0x220,0x1f4,0x224,0x7ffc8829dc40,0x7ffc8829dc4c,0x7ffc8829dc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 672 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | — | cmd.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2148 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | — | cmd.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | — | cmd.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2320 | cmd.exe | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2596 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x220,0x224,0x228,0x1f8,0x22c,0x7ffc8829dc40,0x7ffc8829dc4c,0x7ffc8829dc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3020 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4000 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4120 | notepad.exe | C:\Windows\System32\notepad.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4776 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
39 948
Read events
39 691
Write events
257
Delete events
0
Modification events
| (PID) Process: | (7184) calc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (7184) calc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7184) calc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7184) calc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7380) calc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (7924) calc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (7404) calc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (7848) calc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (7892) calc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (7736) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 2 | |||
Executable files
0
Suspicious files
3
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 11024 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF10c9e9.TMP | — | |
MD5:— | SHA256:— | |||
| 11024 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF10c9f9.TMP | — | |
MD5:— | SHA256:— | |||
| 11024 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 11024 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 11024 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF10c9f9.TMP | — | |
MD5:— | SHA256:— | |||
| 11024 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 11024 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF10ca08.TMP | — | |
MD5:— | SHA256:— | |||
| 11024 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 11024 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF10ca08.TMP | — | |
MD5:— | SHA256:— | |||
| 11024 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF10ca08.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
18
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.34:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
13376 | chrome.exe | 172.217.18.3:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
— | — | 64.233.184.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| whitelisted |
www.google.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
optimizationguide-pa.googleapis.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |