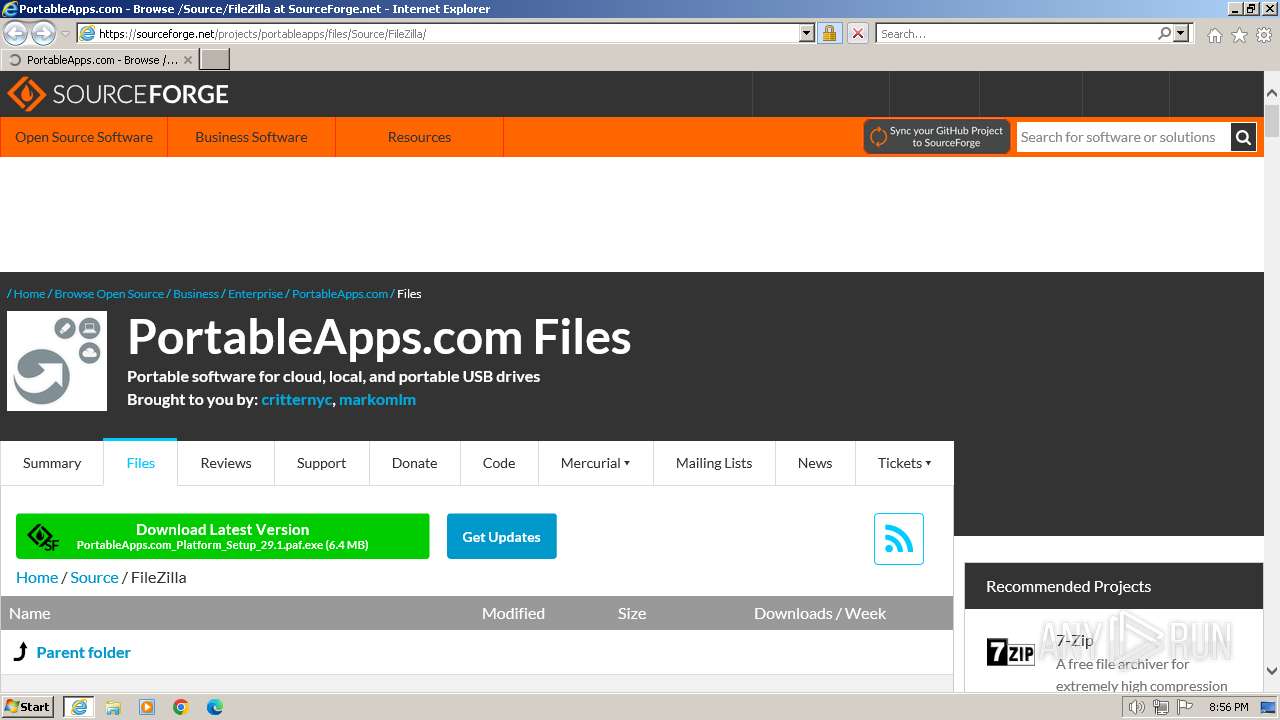
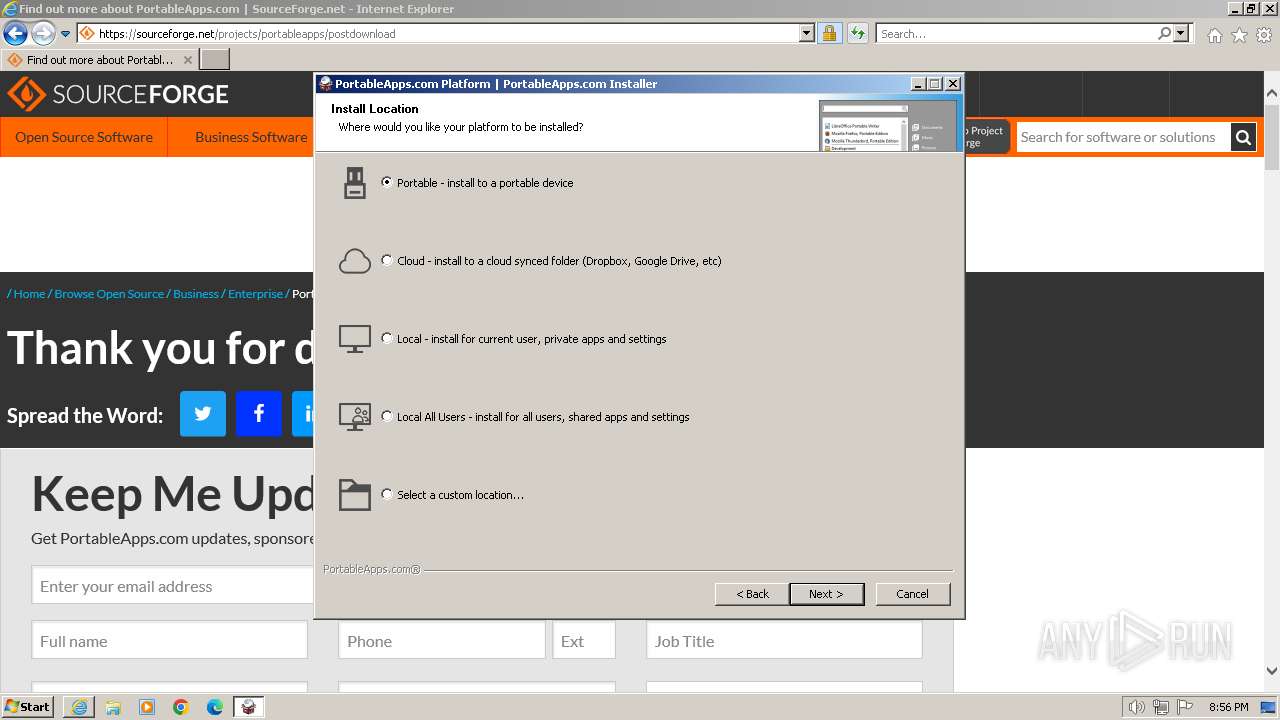
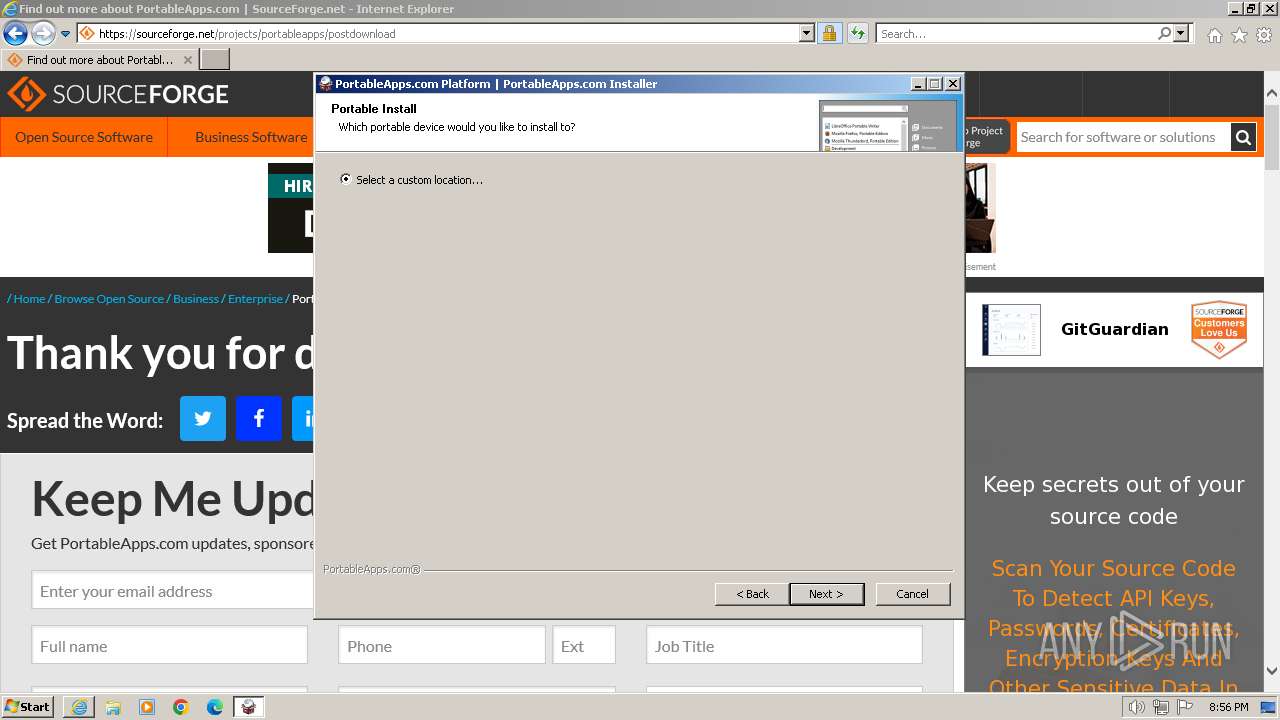
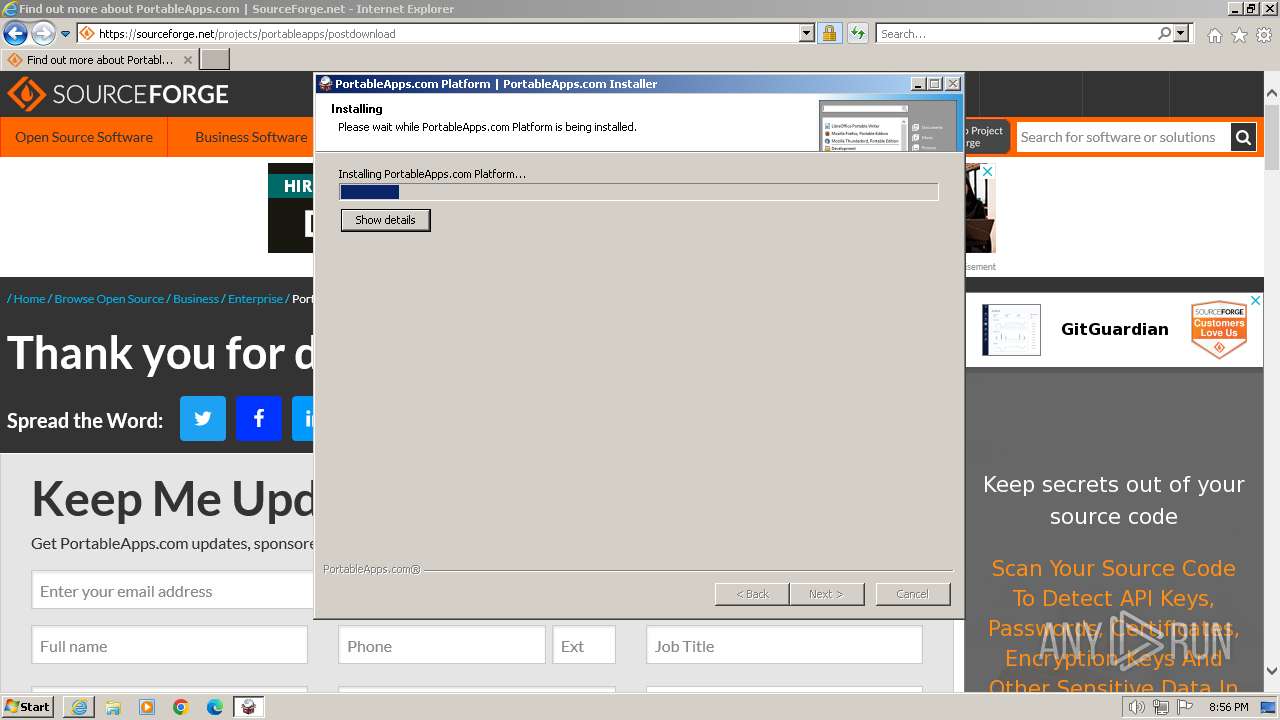
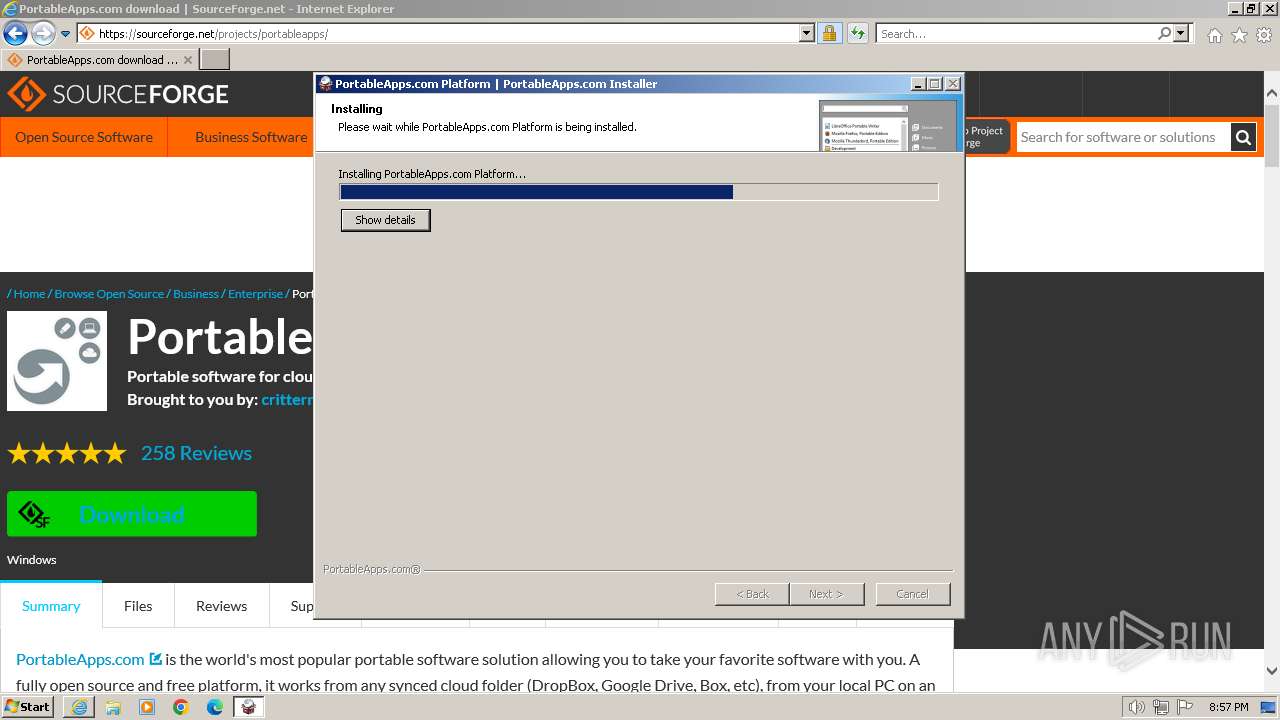
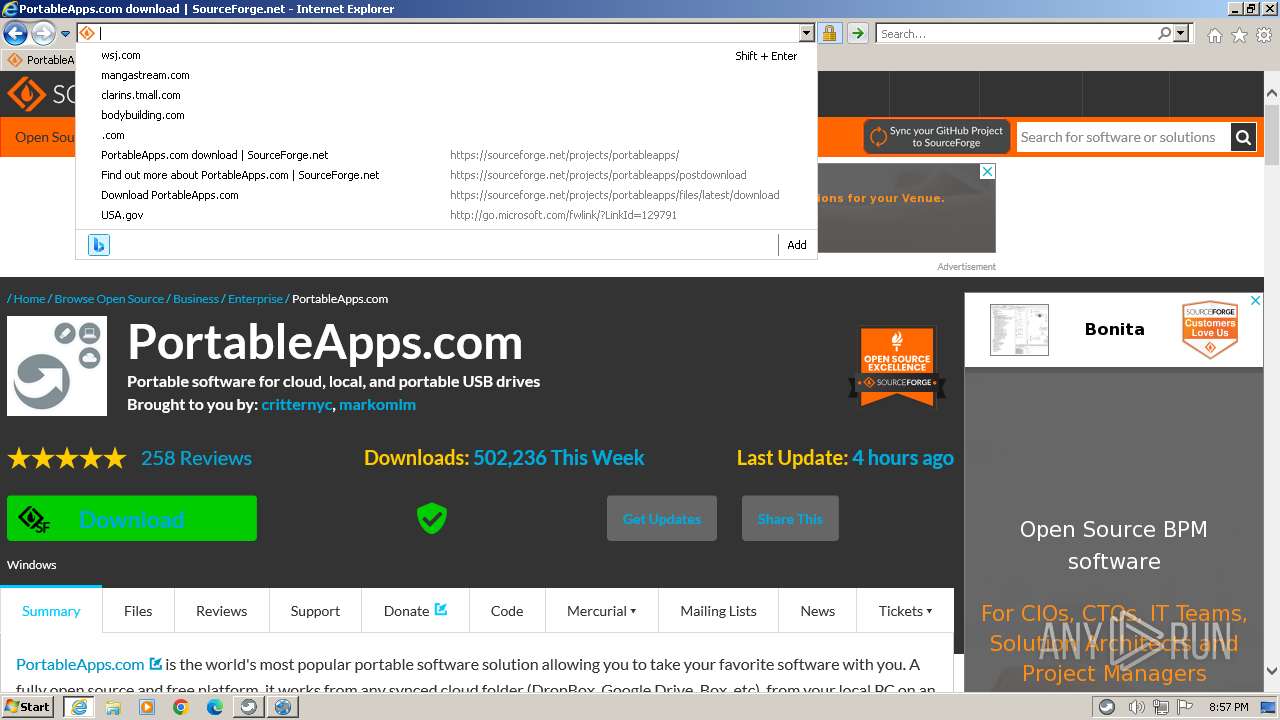
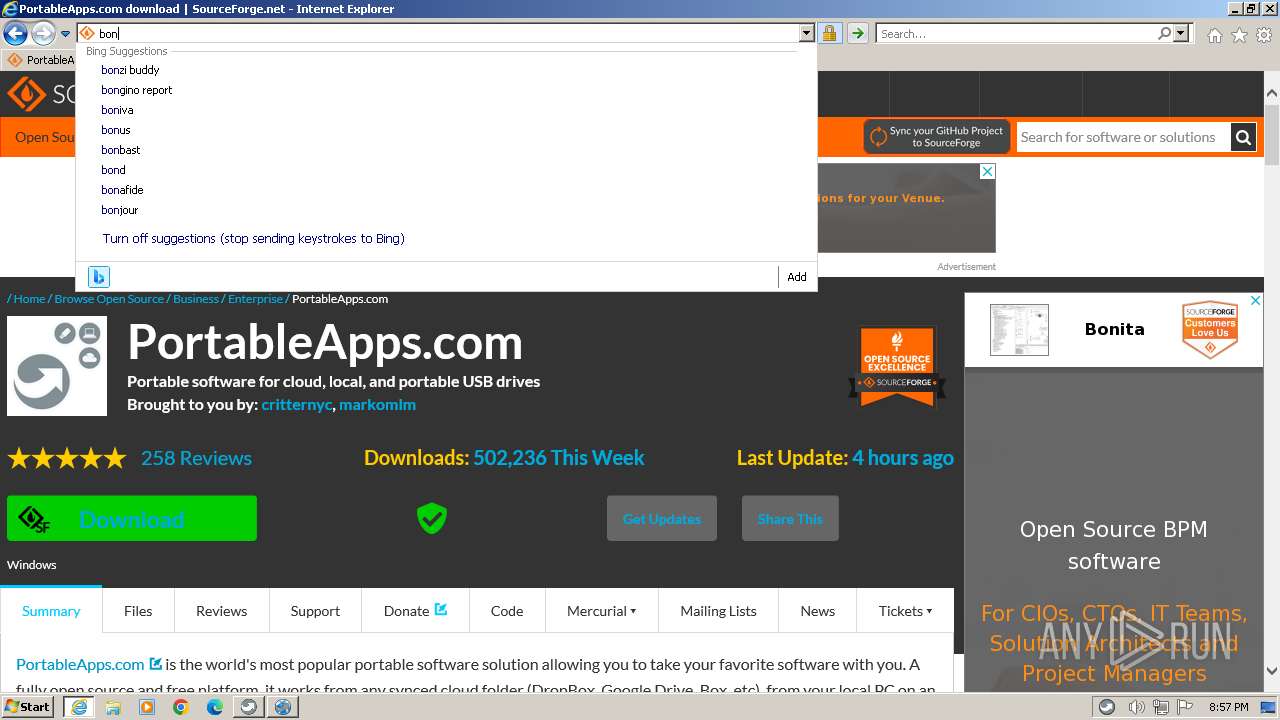
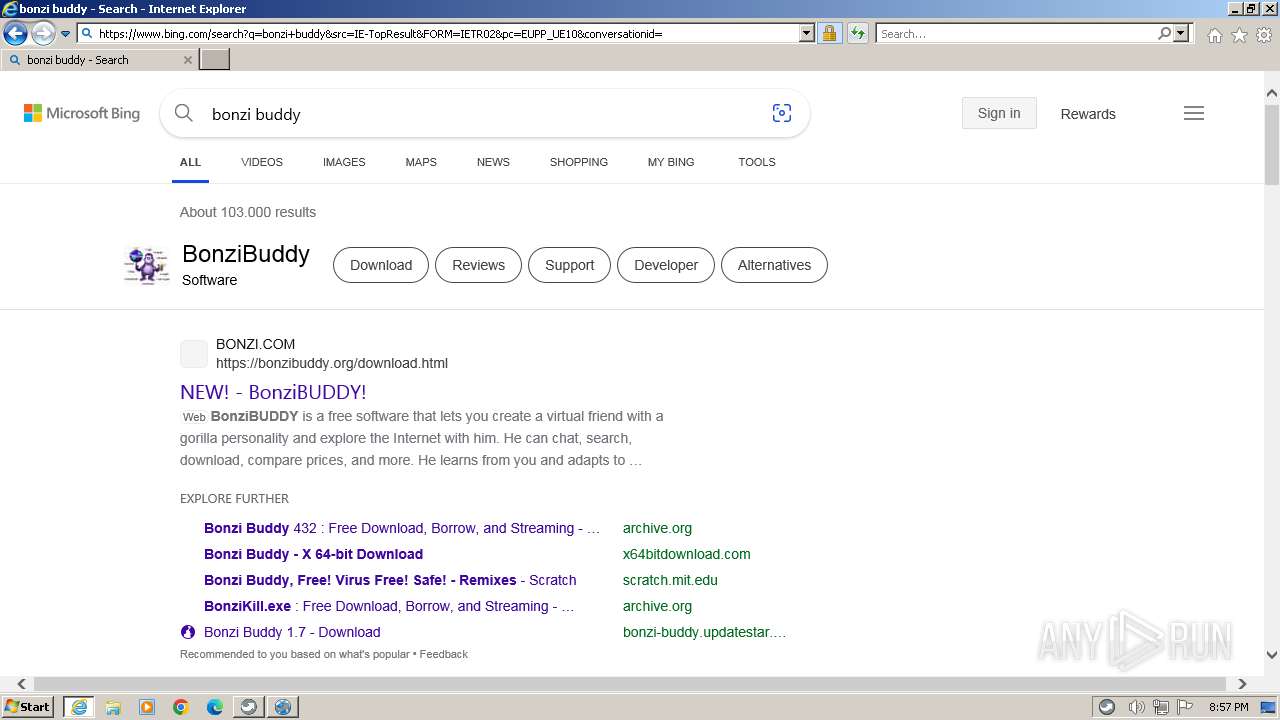
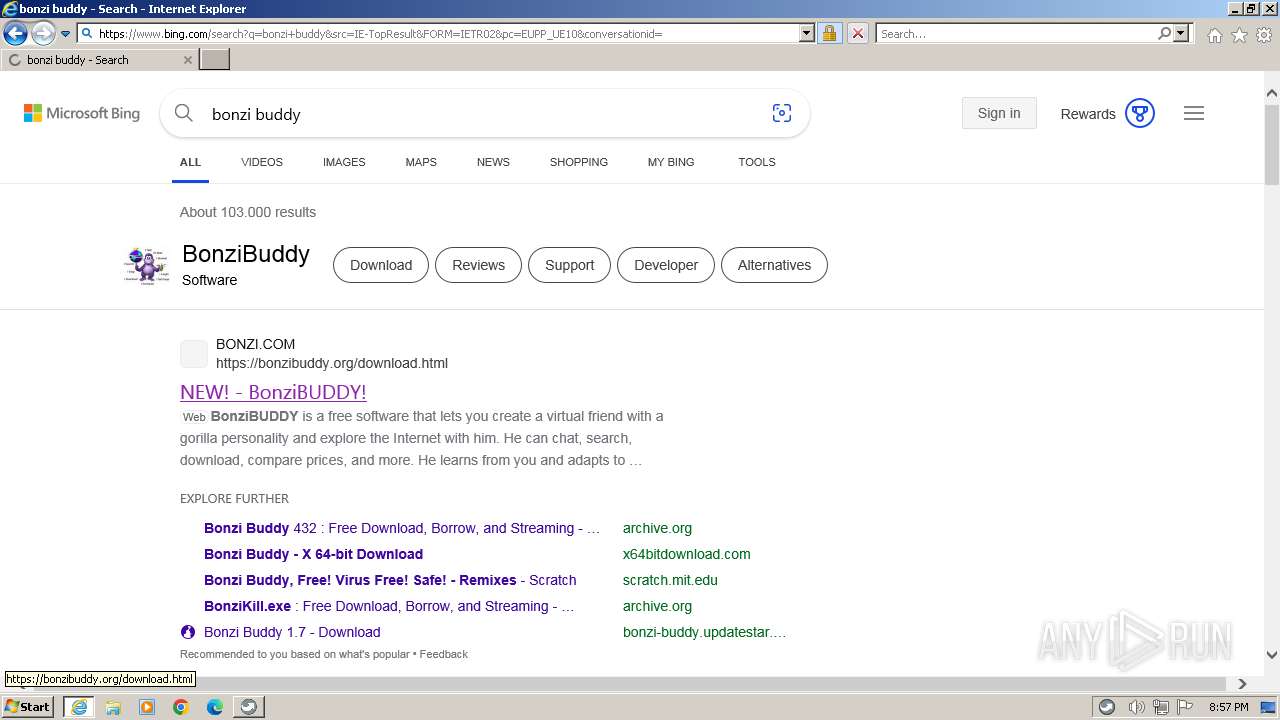
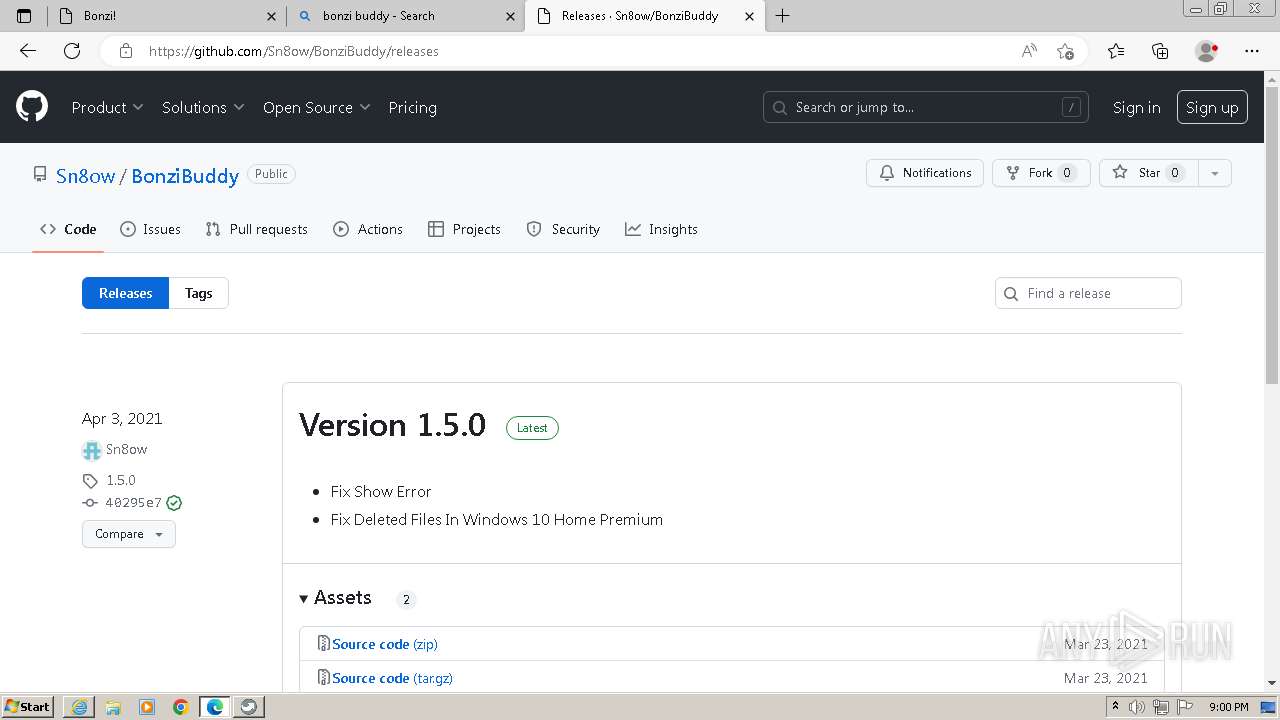
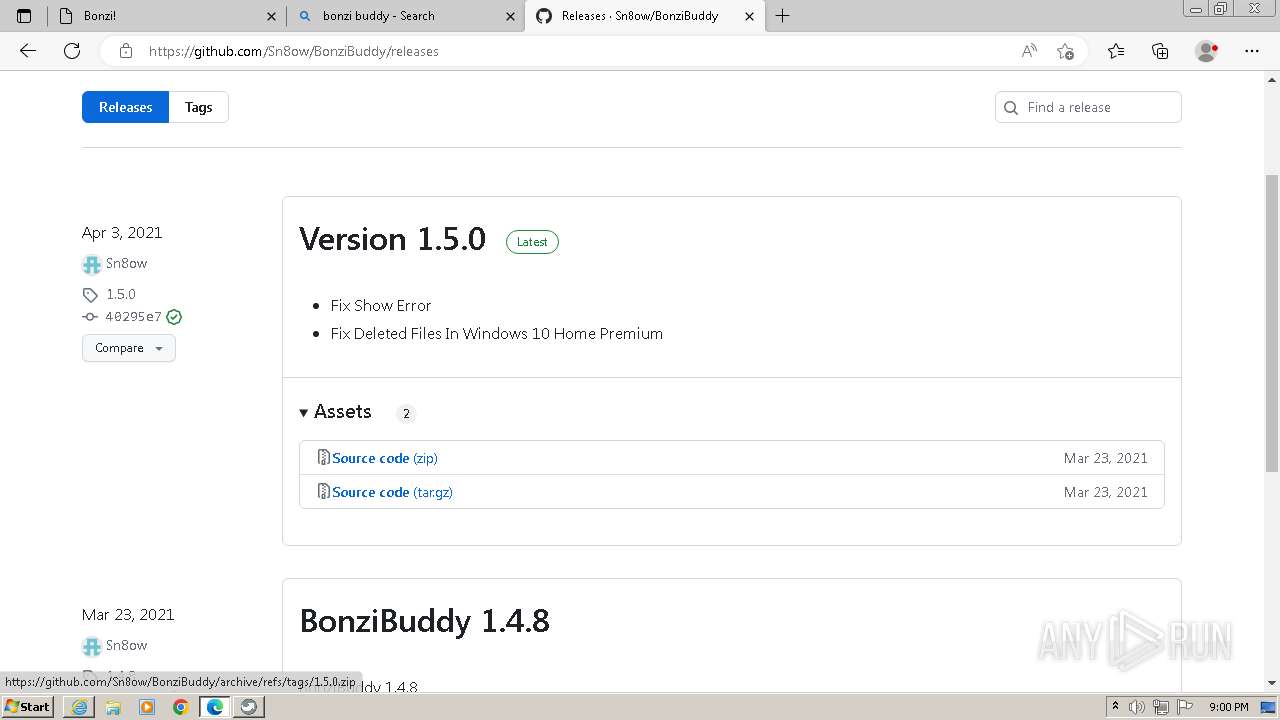
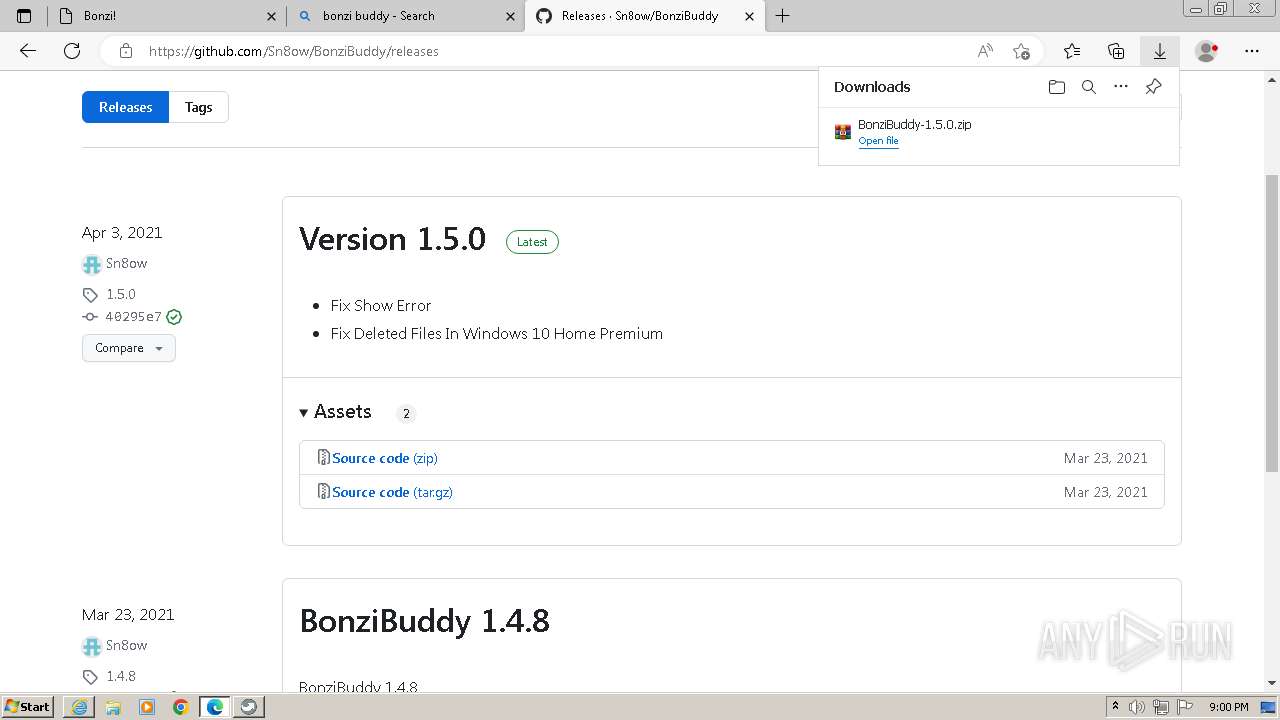
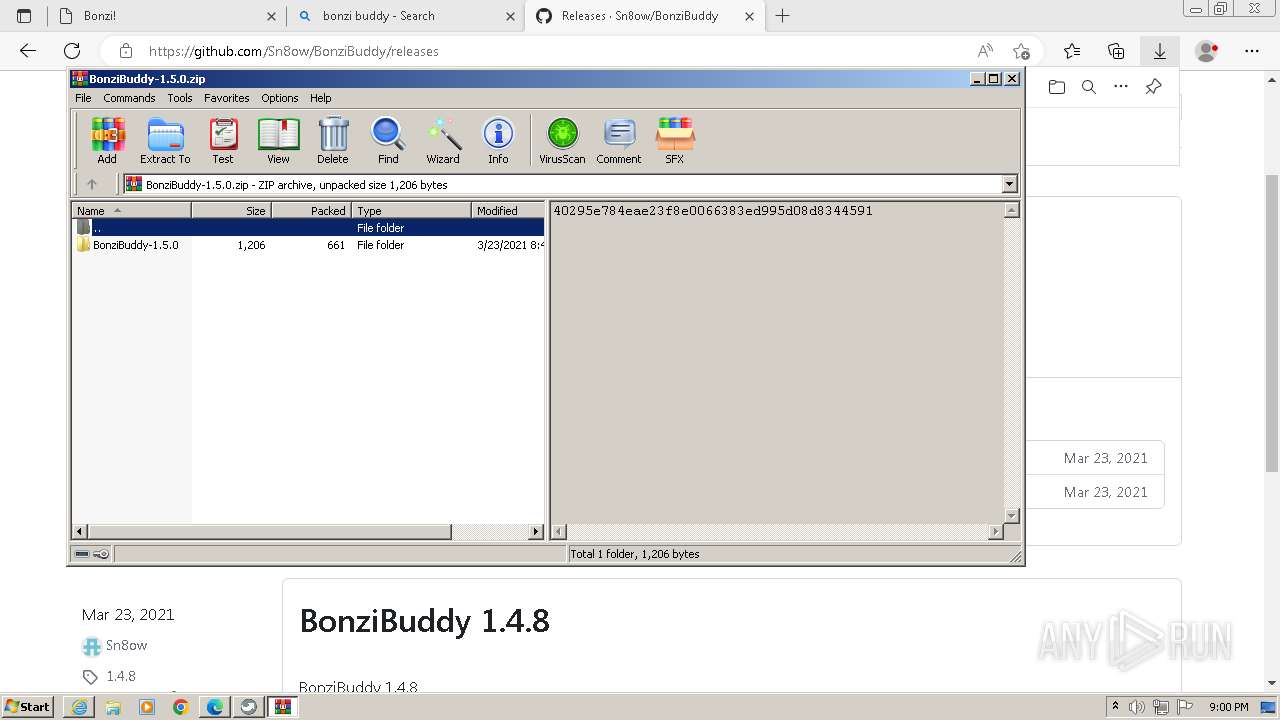
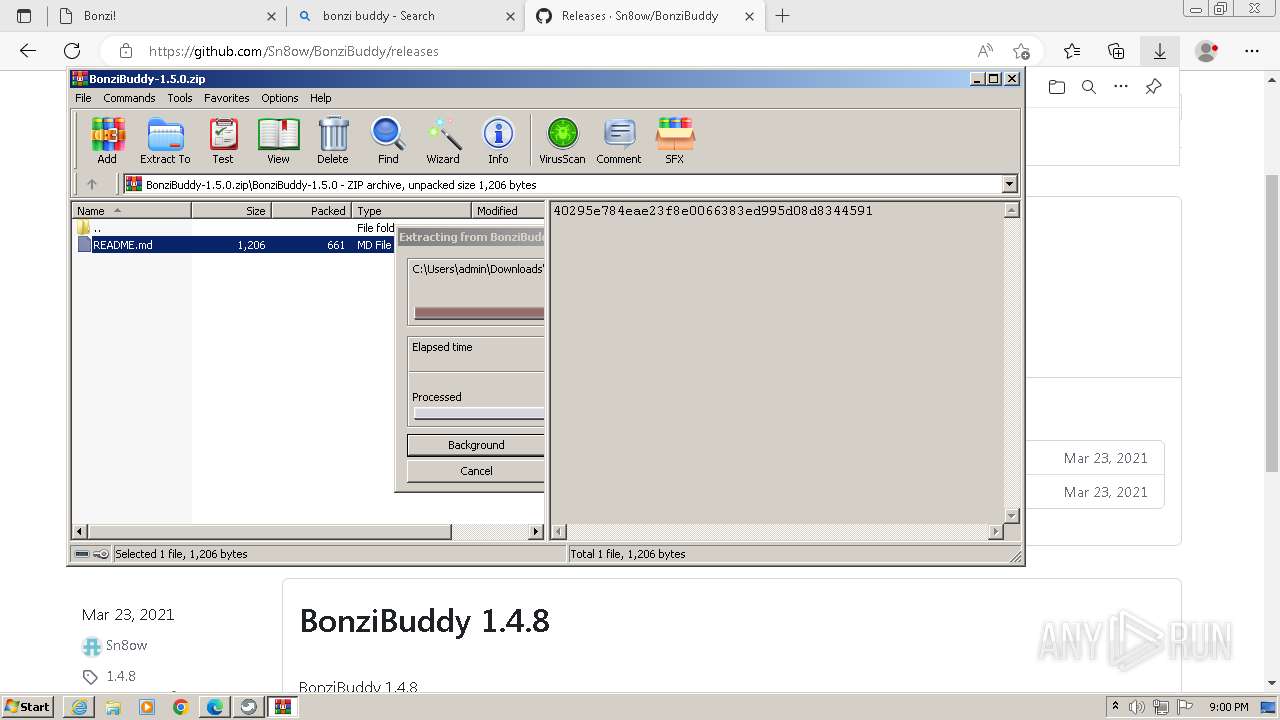
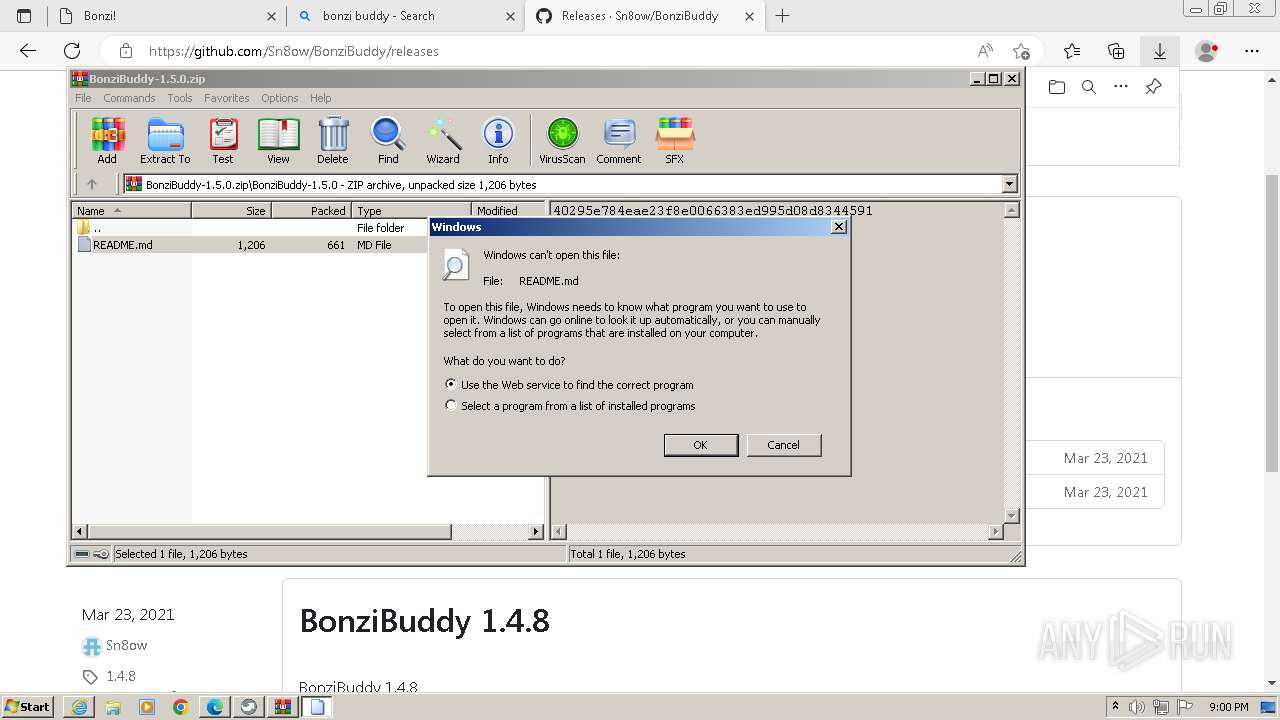
| URL: | https://sourceforge.net/projects/portableapps/files/Source/FileZilla/ |
| Full analysis: | https://app.any.run/tasks/b7133844-446f-4659-9256-6d1c47387e6d |
| Verdict: | Malicious activity |
| Analysis date: | February 05, 2024, 20:56:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | E04961A4B493419C10DEAE6B5F0E8C42 |
| SHA1: | 72755F70DC30427A19565FE3F264DC4212D09DB6 |
| SHA256: | DA218B73034AD73C3847ED033CA90AFCEB478DA7016E0D26B0D9533C184F8136 |
| SSDEEP: | 3:N8HCGSuLAuUtwEHqhUtQXGAKjIaIJEK:2iGnCtwEHLCGvjIaIKK |
MALICIOUS
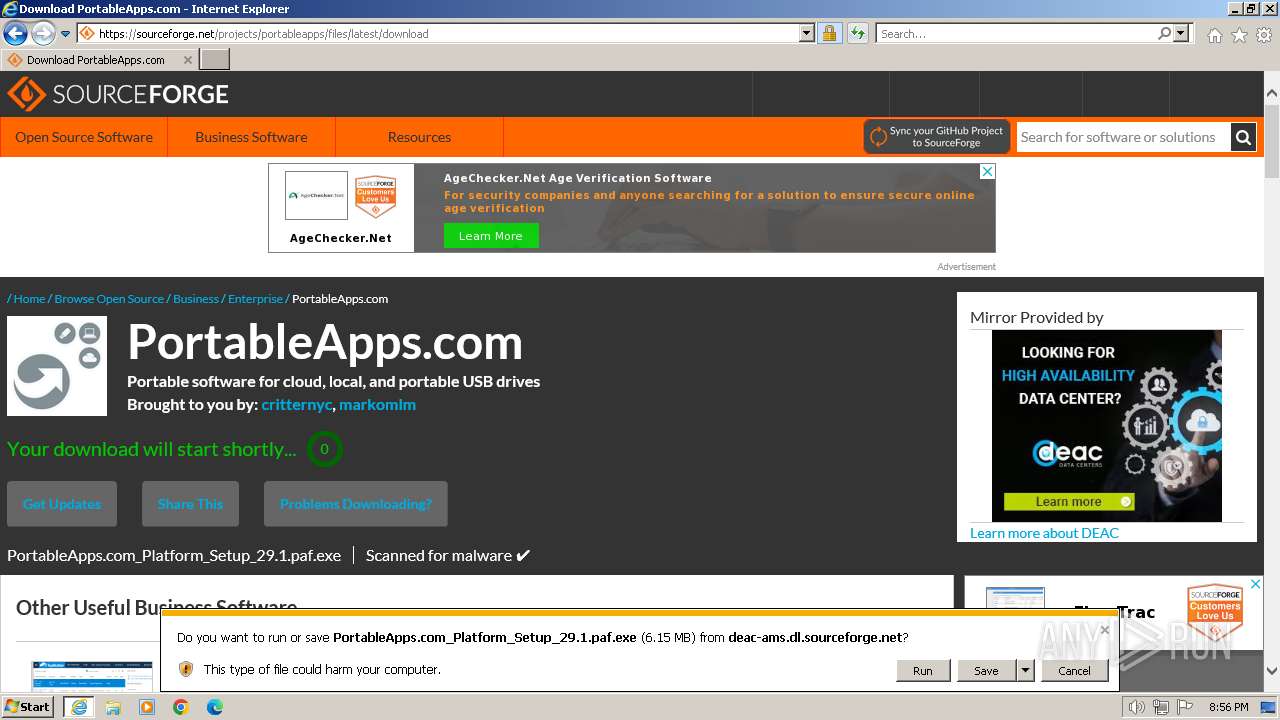
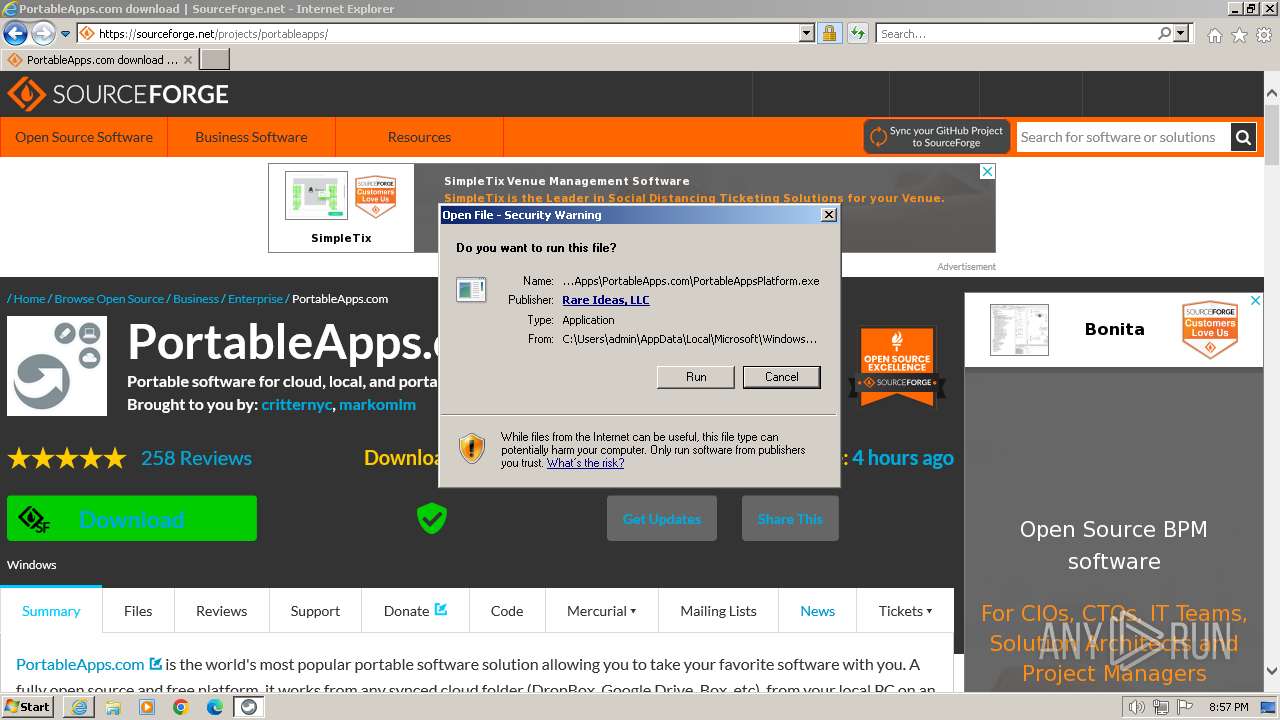
Drops the executable file immediately after the start
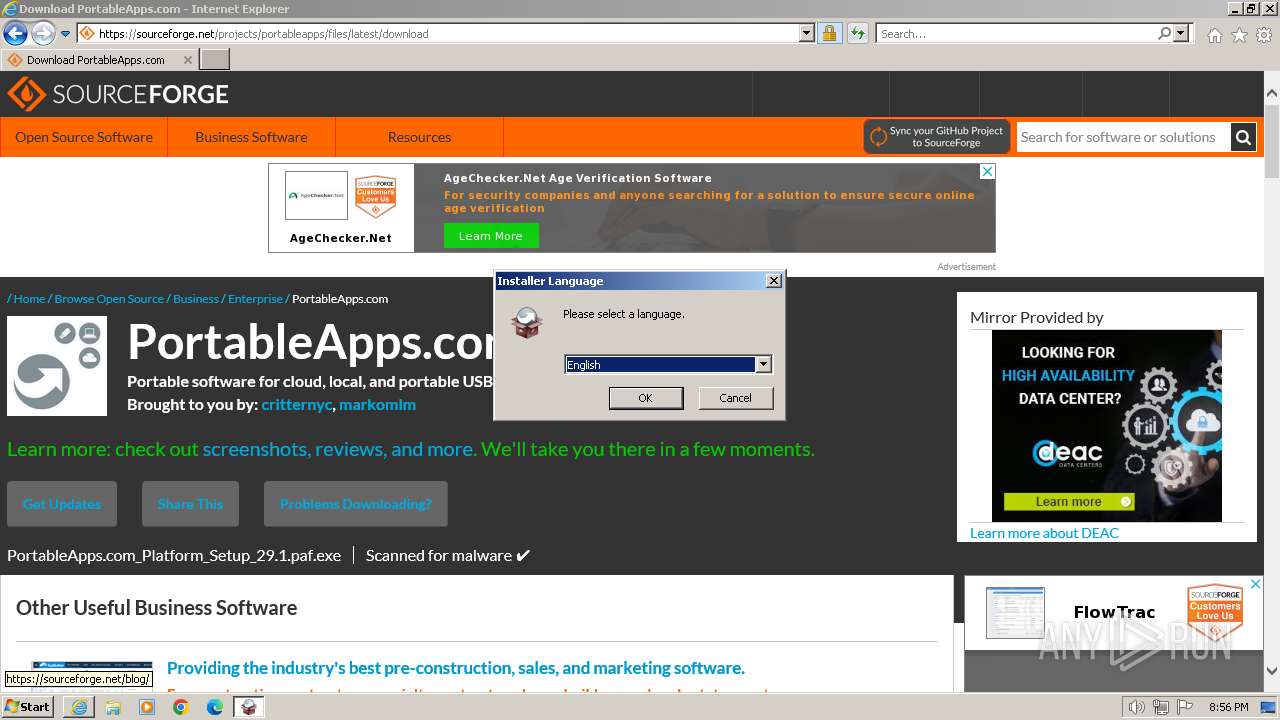
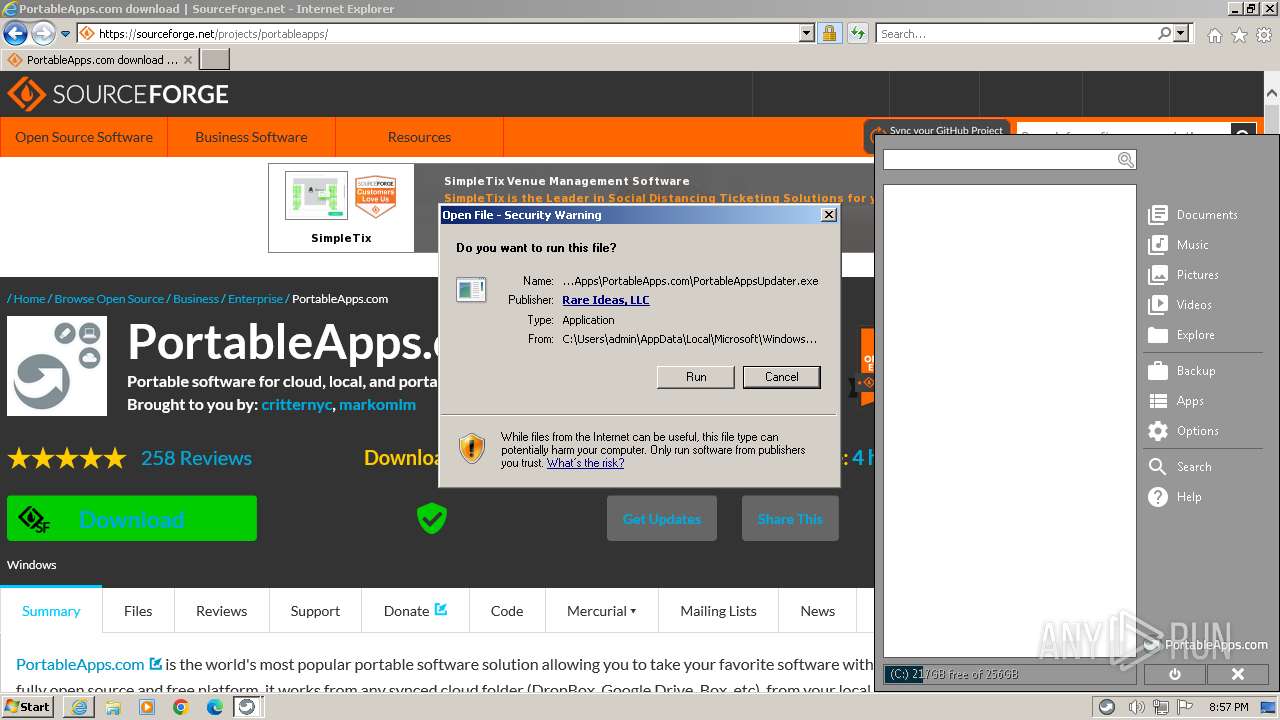
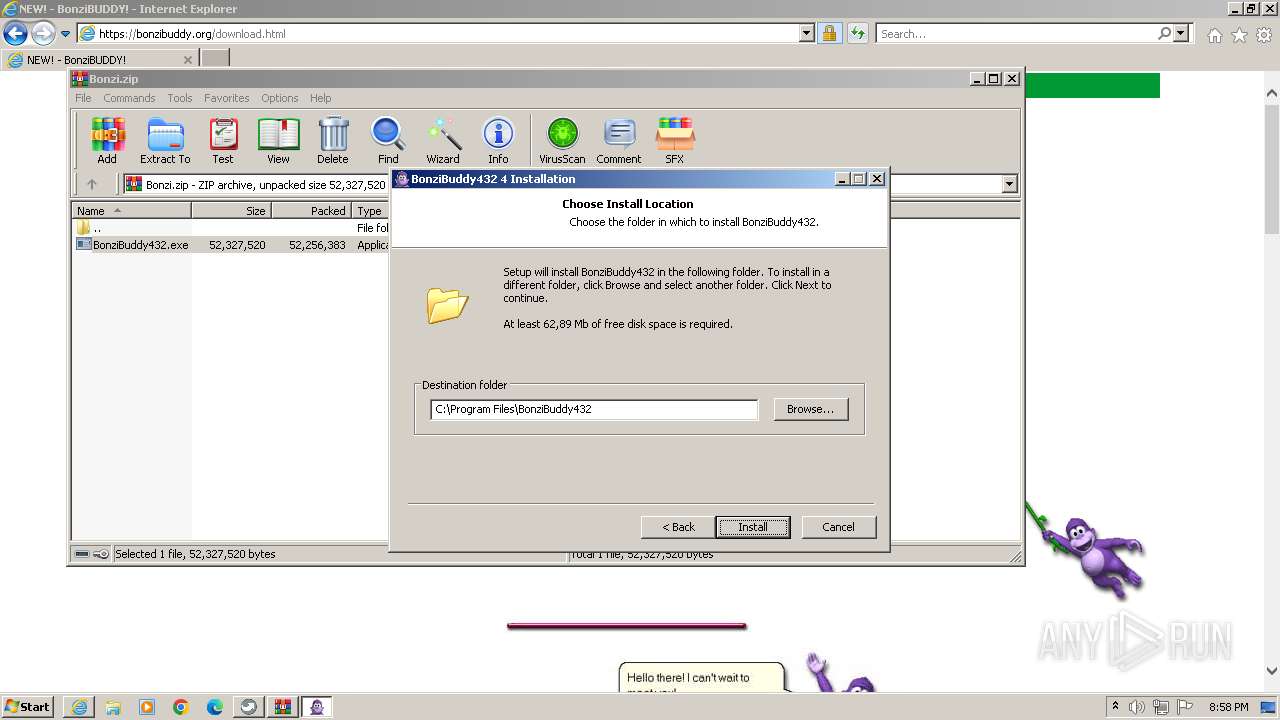
- PortableApps.com_Platform_Setup_29.1.paf.exe (PID: 3824)
- PortableAppsUpdater.exe (PID: 2932)
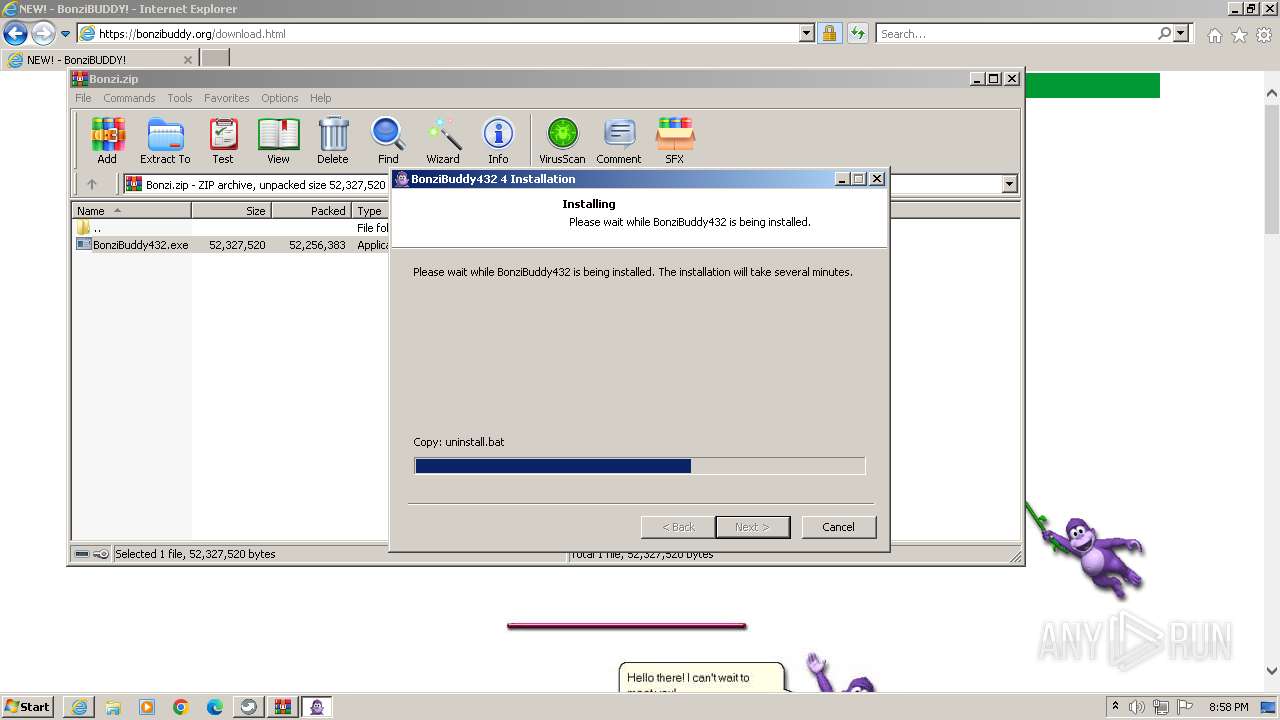
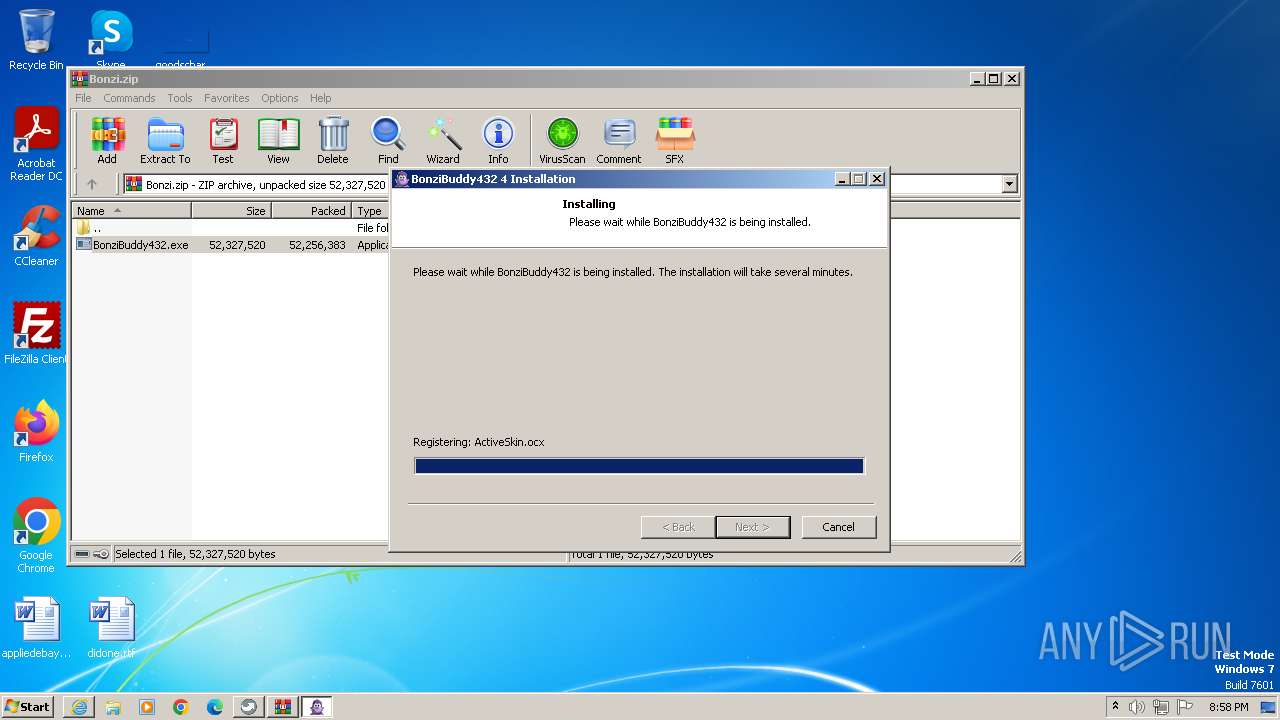
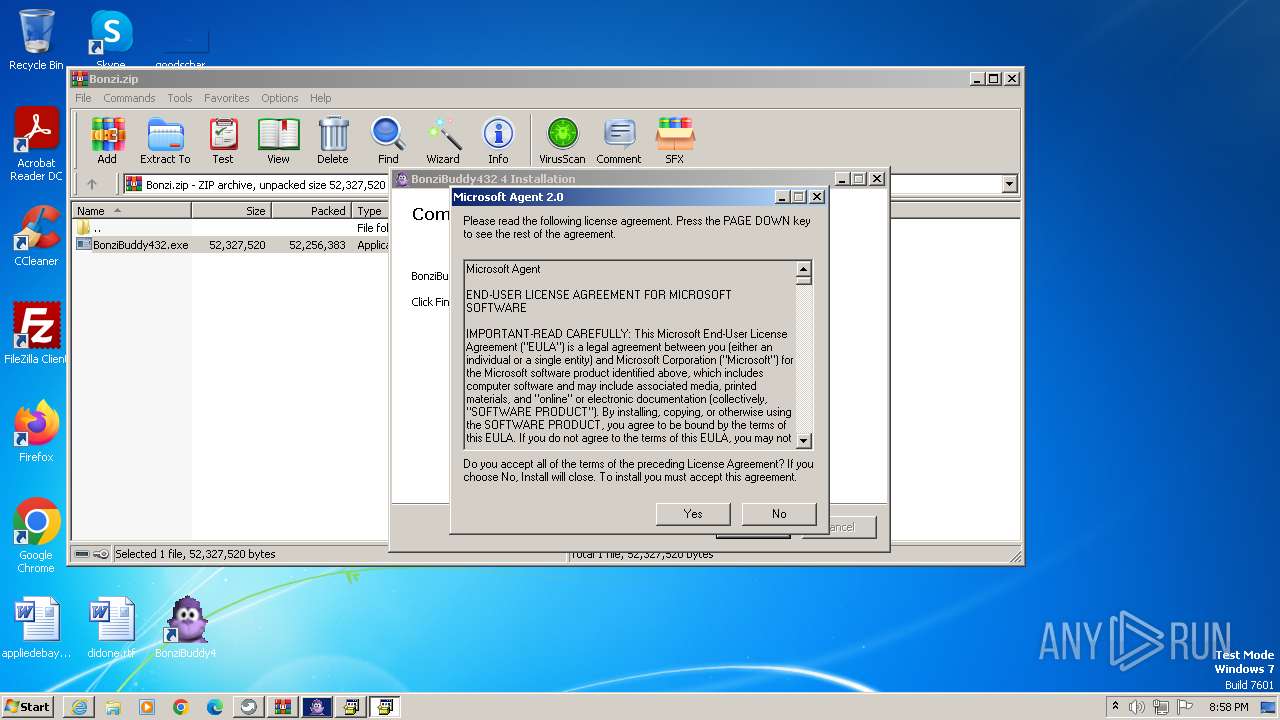
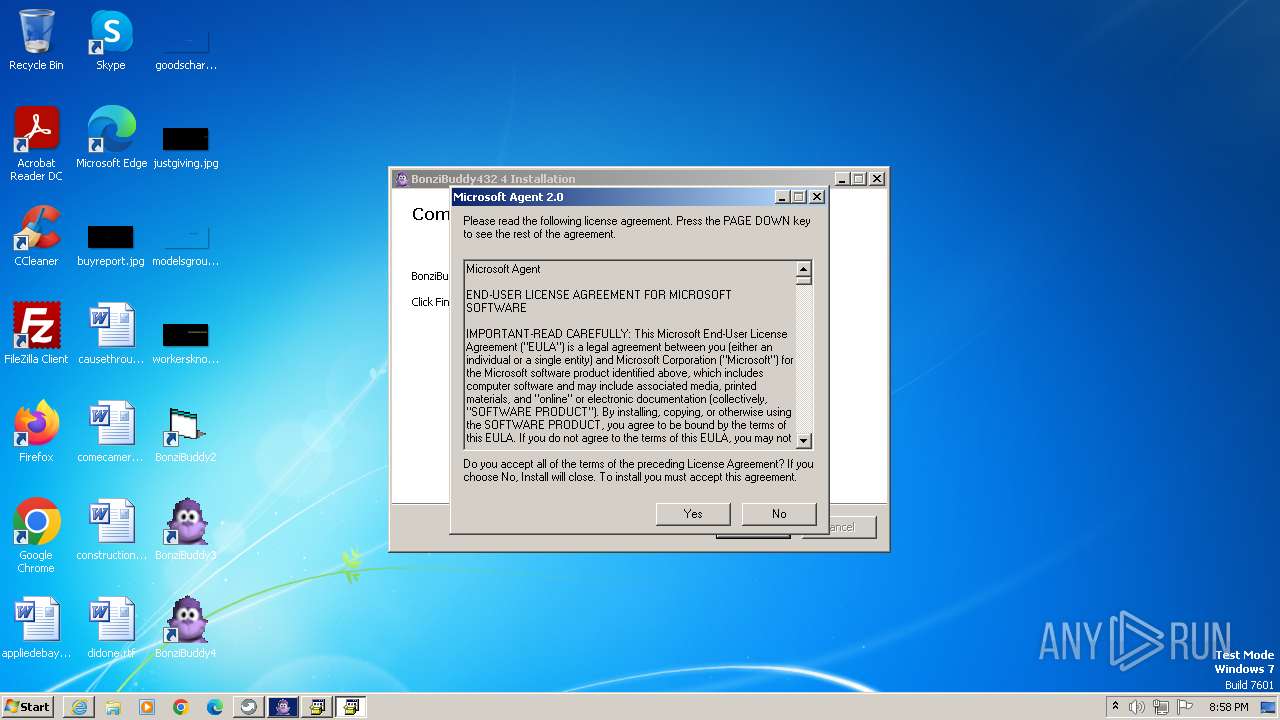
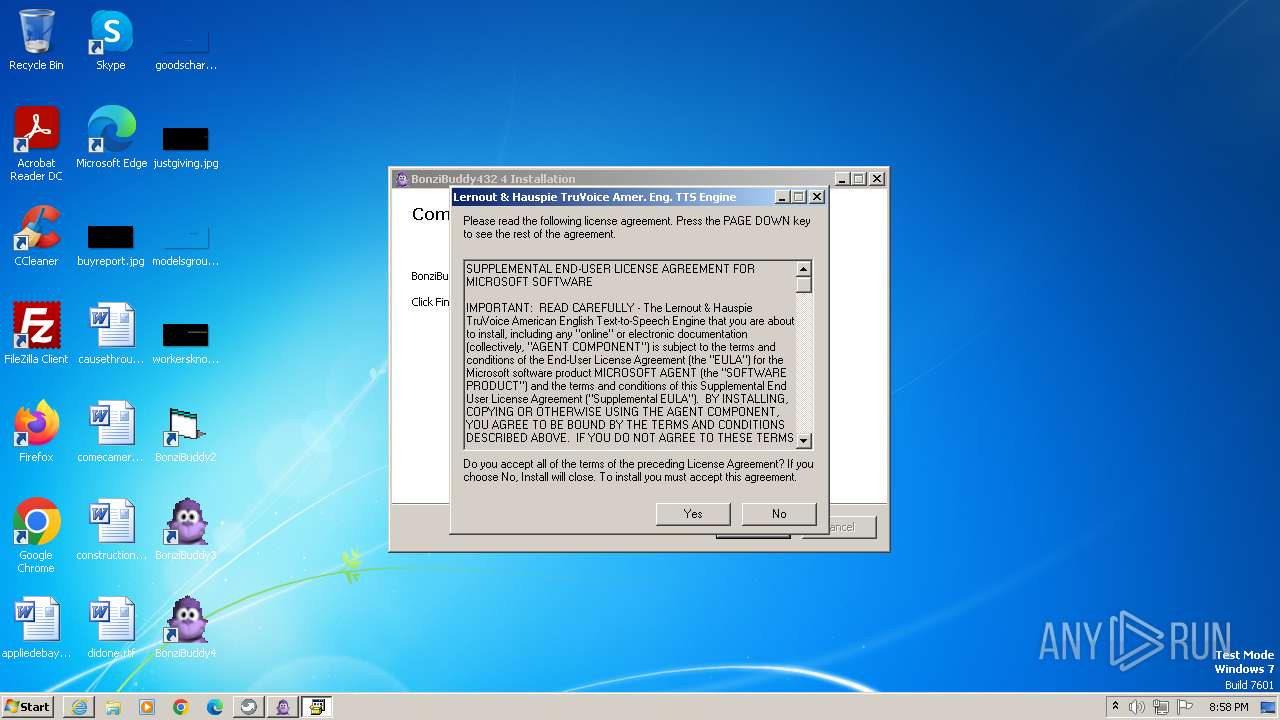
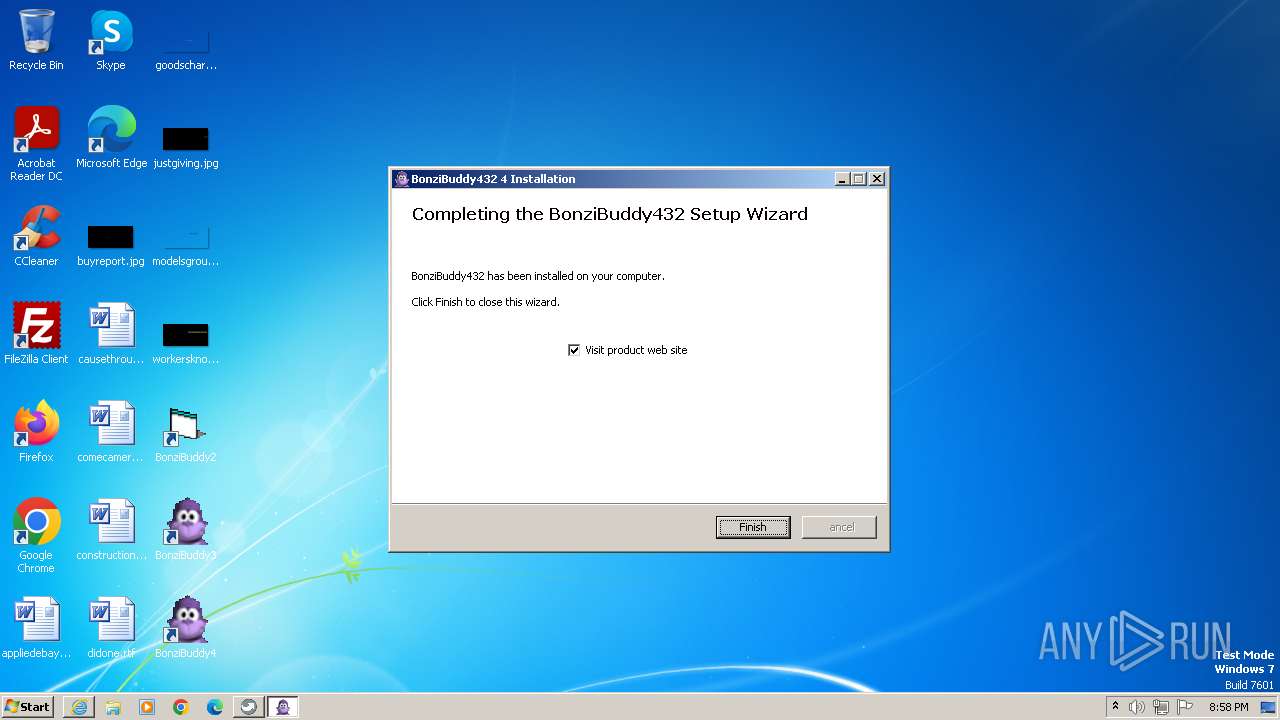
- BonziBuddy432.exe (PID: 3516)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- PortableApps.com_Platform_Setup_29.1.paf.exe (PID: 3824)
- PortableAppsUpdater.exe (PID: 2932)
The process creates files with name similar to system file names
- PortableApps.com_Platform_Setup_29.1.paf.exe (PID: 3824)
- PortableAppsUpdater.exe (PID: 2932)
Drops 7-zip archiver for unpacking
- PortableApps.com_Platform_Setup_29.1.paf.exe (PID: 3824)
Executable content was dropped or overwritten
- PortableApps.com_Platform_Setup_29.1.paf.exe (PID: 3824)
- PortableAppsUpdater.exe (PID: 2932)
- BonziBuddy432.exe (PID: 3516)
Reads the Internet Settings
- Start.exe (PID: 4036)
- PortableAppsPlatform.exe (PID: 3268)
- PortableAppsUpdater.exe (PID: 2932)
- BonziBuddy432.exe (PID: 3516)
Reads security settings of Internet Explorer
- Start.exe (PID: 4036)
- PortableAppsPlatform.exe (PID: 3268)
- PortableAppsUpdater.exe (PID: 2932)
Checks for Java to be installed
- PortableAppsPlatform.exe (PID: 3268)
Checks Windows Trust Settings
- Start.exe (PID: 4036)
- PortableAppsPlatform.exe (PID: 3268)
- PortableAppsUpdater.exe (PID: 2932)
Reads settings of System Certificates
- PortableAppsPlatform.exe (PID: 3268)
- Start.exe (PID: 4036)
- PortableAppsUpdater.exe (PID: 2932)
Starts application with an unusual extension
- PortableAppsUpdater.exe (PID: 2932)
Process drops legitimate windows executable
- BonziBuddy432.exe (PID: 3516)
Creates/Modifies COM task schedule object
- BonziBuddy432.exe (PID: 3516)
Executing commands from a ".bat" file
- BonziBuddy432.exe (PID: 3516)
Starts CMD.EXE for commands execution
- BonziBuddy432.exe (PID: 3516)
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 2164)
- WinRAR.exe (PID: 4004)
INFO
Executable content was dropped or overwritten
- iexplore.exe (PID: 3484)
- iexplore.exe (PID: 1652)
Checks supported languages
- PortableApps.com_Platform_Setup_29.1.paf.exe (PID: 3824)
- wmpnscfg.exe (PID: 4056)
- Start.exe (PID: 4036)
- PortableAppsUpdater.exe (PID: 2932)
- PortableAppsPlatform.exe (PID: 3268)
- ns7717.tmp (PID: 1432)
- 7za.exe (PID: 3952)
- BonziBuddy432.exe (PID: 3516)
- tv_enua.exe (PID: 3028)
- MSAGENT.EXE (PID: 2176)
- BonziBDY_2.EXE (PID: 3404)
- BonziBDY_4.EXE (PID: 3792)
- BonziBDY_35.EXE (PID: 2828)
- BonziBDY_35.EXE (PID: 3996)
Reads the computer name
- PortableApps.com_Platform_Setup_29.1.paf.exe (PID: 3824)
- wmpnscfg.exe (PID: 4056)
- Start.exe (PID: 4036)
- PortableAppsPlatform.exe (PID: 3268)
- PortableAppsUpdater.exe (PID: 2932)
- 7za.exe (PID: 3952)
- BonziBuddy432.exe (PID: 3516)
- BonziBDY_35.EXE (PID: 3996)
Drops the executable file immediately after the start
- iexplore.exe (PID: 1652)
- iexplore.exe (PID: 3484)
Create files in a temporary directory
- PortableApps.com_Platform_Setup_29.1.paf.exe (PID: 3824)
- PortableAppsUpdater.exe (PID: 2932)
- BonziBuddy432.exe (PID: 3516)
- 7za.exe (PID: 3952)
- BonziBDY_35.EXE (PID: 3996)
Application launched itself
- iexplore.exe (PID: 1652)
- msedge.exe (PID: 3544)
- msedge.exe (PID: 2576)
The process uses the downloaded file
- iexplore.exe (PID: 1652)
- WinRAR.exe (PID: 4000)
- msedge.exe (PID: 1780)
- WinRAR.exe (PID: 4004)
- WinRAR.exe (PID: 2164)
Manual execution by a user
- wmpnscfg.exe (PID: 4056)
- BonziBDY_35.EXE (PID: 2828)
- msedge.exe (PID: 2576)
- BonziBDY_2.EXE (PID: 3404)
- taskmgr.exe (PID: 1596)
- BonziBDY_35.EXE (PID: 3996)
- BonziBDY_4.EXE (PID: 3792)
Creates files or folders in the user directory
- PortableApps.com_Platform_Setup_29.1.paf.exe (PID: 3824)
- PortableAppsUpdater.exe (PID: 2932)
- BonziBuddy432.exe (PID: 3516)
Reads the machine GUID from the registry
- PortableApps.com_Platform_Setup_29.1.paf.exe (PID: 3824)
- Start.exe (PID: 4036)
- PortableAppsPlatform.exe (PID: 3268)
- PortableAppsUpdater.exe (PID: 2932)
- BonziBDY_35.EXE (PID: 3996)
Checks proxy server information
- PortableAppsUpdater.exe (PID: 2932)
Creates files in the program directory
- BonziBuddy432.exe (PID: 3516)
Reads mouse settings
- BonziBuddy432.exe (PID: 3516)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
110
Monitored processes
59
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --mojo-platform-channel-handle=2508 --field-trial-handle=1304,i,13738532886257080966,14882026190441312299,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 480 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=17 --mojo-platform-channel-handle=4032 --field-trial-handle=1304,i,13738532886257080966,14882026190441312299,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 920 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=30 --mojo-platform-channel-handle=4900 --field-trial-handle=1304,i,13738532886257080966,14882026190441312299,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 948 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=24 --mojo-platform-channel-handle=4052 --field-trial-handle=1304,i,13738532886257080966,14882026190441312299,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 980 | C:\Windows\system32\cmd.exe /c ""C:\Program Files\BonziBuddy432\Runtimes\CheckRuntimes.bat" " | C:\Windows\System32\cmd.exe | — | BonziBuddy432.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1168 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1564 --field-trial-handle=1312,i,527243342422278199,663410137730876332,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1196 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3220 --field-trial-handle=1304,i,13738532886257080966,14882026190441312299,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1232 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=22 --mojo-platform-channel-handle=1272 --field-trial-handle=1304,i,13738532886257080966,14882026190441312299,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1432 | "C:\Users\admin\AppData\Local\Temp\nst71B7.tmp\ns7717.tmp" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\PortableApps\PortableApps.com\App\7-Zip\7za.exe" x "C:\Users\admin\AppData\Local\Temp\nst71B7.tmp\update.7z" -o"C:\Users\admin\AppData\Local\Temp\nst71B7.tmp" -aoa | C:\Users\admin\AppData\Local\Temp\nst71B7.tmp\ns7717.tmp | — | PortableAppsUpdater.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1432 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3792 --field-trial-handle=1304,i,13738532886257080966,14882026190441312299,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
47 145
Read events
46 743
Write events
341
Delete events
61
Modification events
| (PID) Process: | (1652) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (1652) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (1652) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (1652) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1652) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1652) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1652) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1652) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1652) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1652) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
105
Suspicious files
695
Text files
1 533
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3484 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:B61EE08D408E409B82C3196DD12F4AC6 | SHA256:B9ED36A1A2A574EFBB28C574151CDD60E02C826CF1CA8CABAC2D3245CA5F12A6 | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\sf-logo-full[1].svg | image | |
MD5:535DE5A927A8EB5A004CDC0A6B6320DD | SHA256:1744FB413B91B276F5E17347382B664D6CA6C4EA4DB69825CAA97C16DD5D37C3 | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\github-sync[1].png | image | |
MD5:4A6DCE1E1233DA9CE4605000A63B81DC | SHA256:DA0649DC53EAE2E0F5982186C3D53DFBF9D11BE57B69127C6BB2DC18D11BF309 | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\sf-icon-black[1].svg | image | |
MD5:0EC28A189B84FCD3EC2EE7A376BC929C | SHA256:67285130C9EA896794BD451295DB6A03A4F5B7941CB9EFD5D5088D06F63208D7 | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\sf.sandiego-base[1].js | text | |
MD5:80F2419F055A74A6B18626ACA93E971F | SHA256:B7547012DE798D3F335199320469E3D42C57BA965D790E62BBC6FA223230DD0F | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\sf.sandiego-foundation-base[1].js | text | |
MD5:F23FBD469BB0D9569486B62E2C50D996 | SHA256:D30C030593AEE31E4BDD1A458E6739DF804F6D50012D2E3141D585B4ACF91A08 | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\v84a3a4012de94ce1a686ba8c167c359c1696973893317[1].js | text | |
MD5:DD1D068FDB5FE90B6C05A5B3940E088C | SHA256:6153D13804862B0FC1C016CF1129F34CB7C6185F2CF4BF1A3A862EECDAB50101 | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\icon[2].png | image | |
MD5:DF34C397E8559589D3C166A7901CD4F9 | SHA256:7F3357F080D67724C2F7135732C553896F9934B1A26D5083D9DB2993DE0B6748 | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:1AD370E776040B8853A93F538BFD05AB | SHA256:591F919B1A72D9C7B127865CABB15FAB417231F2492FBCA30263D4FE59D991E0 | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\icon[1].png | image | |
MD5:9330078255AA5E5875C42774A4E13EC4 | SHA256:5FD52F97E35C4DC774E5B68D48970D5BCC71CEBD7C21A81105381575A61487EA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
205
DNS requests
159
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3484 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?98084960eae7a2ec | unknown | — | — | unknown |
3484 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
3484 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?83c23cd8118a42bc | unknown | — | — | unknown |
3484 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?077c6b0ddd4f11d3 | unknown | compressed | 65.2 Kb | unknown |
3484 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?633e784b9de383ab | unknown | compressed | 65.2 Kb | unknown |
3484 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?8d4f81efd6f58e7f | unknown | compressed | 65.2 Kb | unknown |
3484 | iexplore.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
3484 | iexplore.exe | GET | 200 | 95.101.54.99:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgR%2B5rJNDRLPmf6wKNriwkmuQQ%3D%3D | unknown | binary | 503 b | unknown |
1652 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5565915fab5f2bac | unknown | — | — | unknown |
1652 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?95d95b669c097e41 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3484 | iexplore.exe | 104.18.37.111:443 | sourceforge.net | CLOUDFLARENET | — | unknown |
3484 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3484 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3484 | iexplore.exe | 104.18.40.209:443 | a.fsdn.com | CLOUDFLARENET | — | shared |
3484 | iexplore.exe | 104.16.56.101:443 | static.cloudflareinsights.com | CLOUDFLARENET | — | unknown |
3484 | iexplore.exe | 87.230.98.76:443 | d.delivery.consentmanager.net | PlusServer GmbH | DE | unknown |
3484 | iexplore.exe | 156.146.33.140:443 | cdn.consentmanager.net | Datacamp Limited | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
sourceforge.net |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
a.fsdn.com |
| whitelisted |
static.cloudflareinsights.com |
| whitelisted |
d.delivery.consentmanager.net |
| unknown |
cdn.consentmanager.net |
| malicious |
c.sf-syn.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3484 | iexplore.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
3484 | iexplore.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
2100 | msedge.exe | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
2100 | msedge.exe | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
2100 | msedge.exe | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
2100 | msedge.exe | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
2100 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
2100 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |