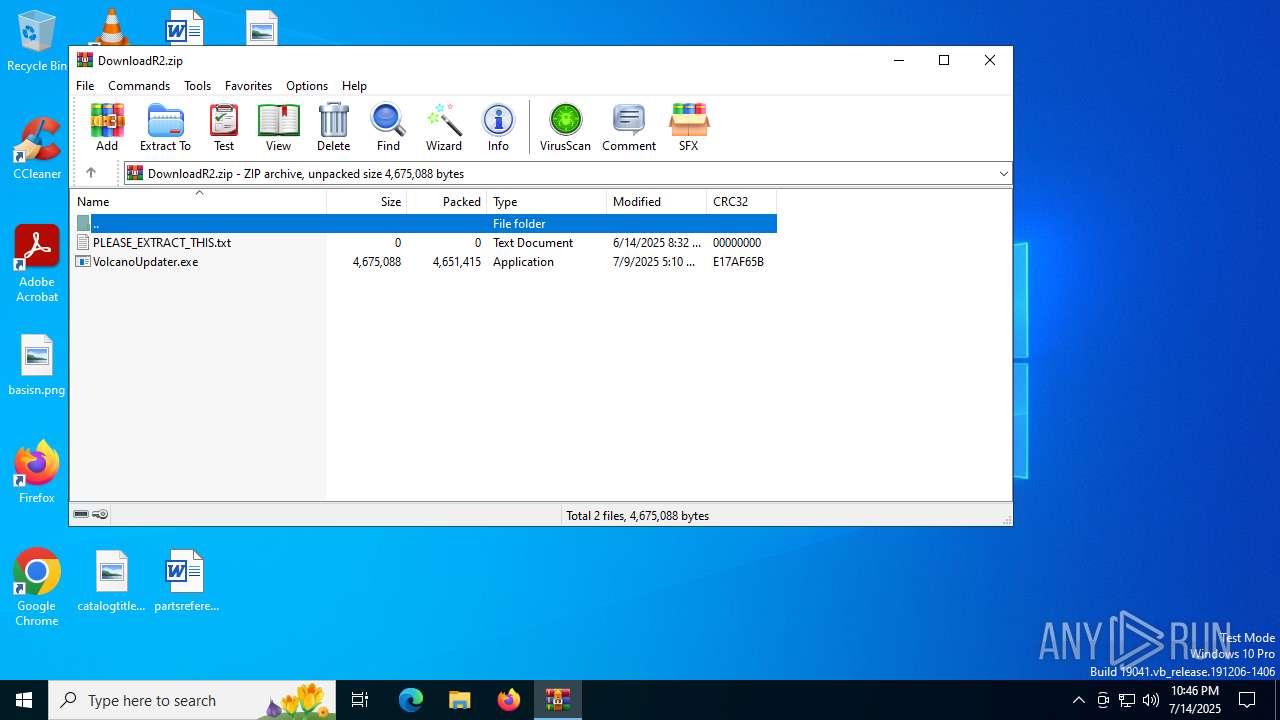
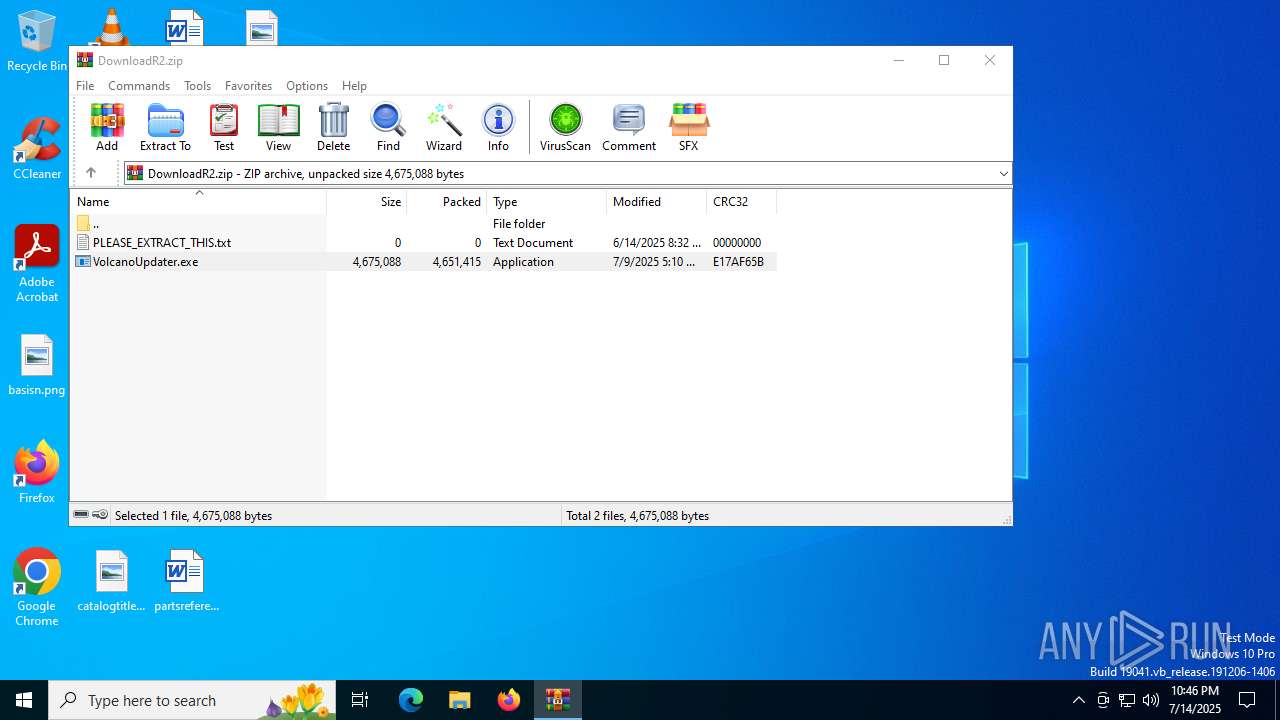
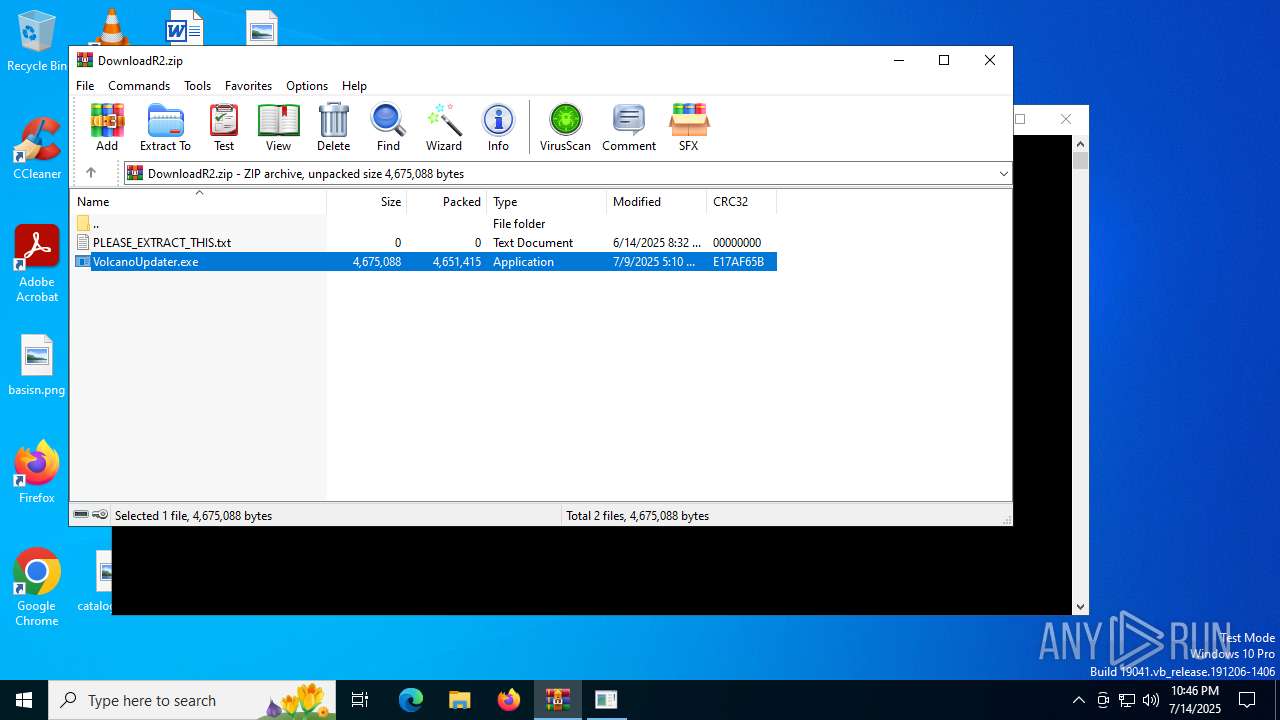
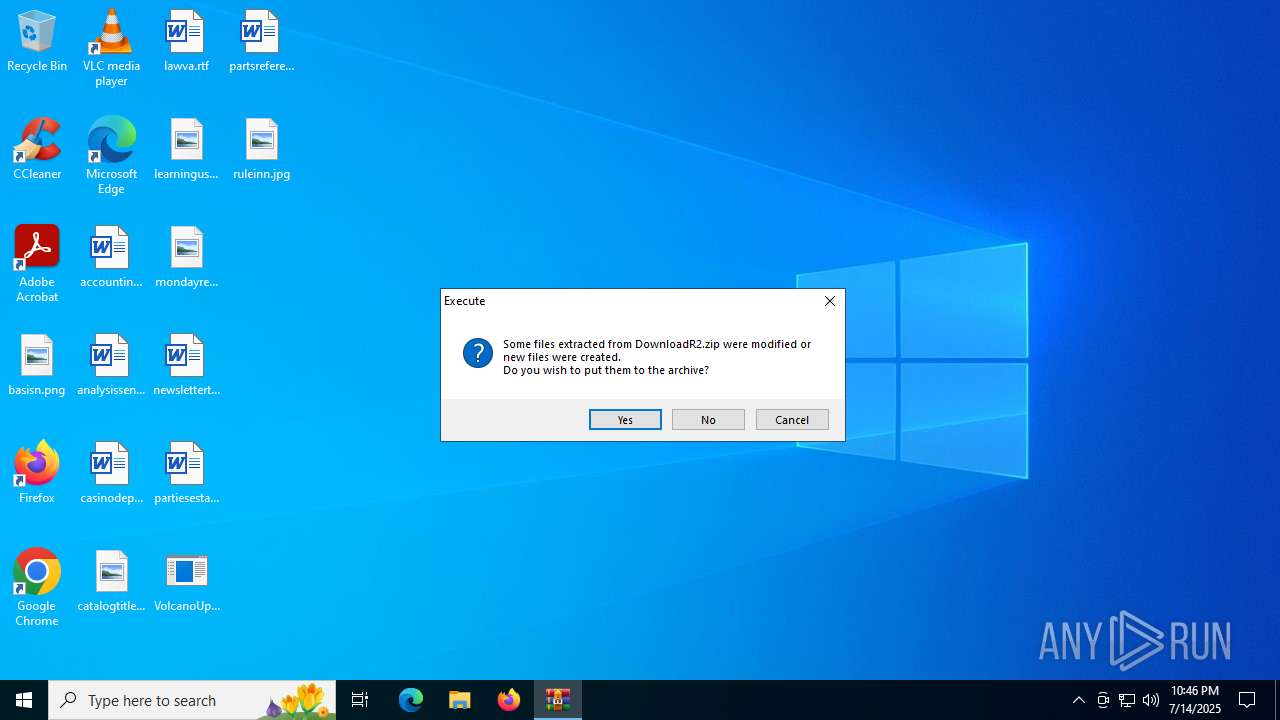
| File name: | DownloadR2.zip |
| Full analysis: | https://app.any.run/tasks/4cd27423-ca14-44f2-87c2-4c5d3cfe0aff |
| Verdict: | Malicious activity |
| Analysis date: | July 14, 2025, 22:46:35 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 1F329793E4FA72DA313D5B318CCBA7FD |
| SHA1: | 2C214E188F12183FDFAF43B7D6AF421D6BE6F702 |
| SHA256: | DA0B07E2452D9A2CDBB16838CFC886F81D7129A255CDC591EEEE8458519892B2 |
| SSDEEP: | 98304:aPxEIq02Mu7+o50HZee6YQO/qeItoFgd2DN2diPSLUEKf/4/mxvtXgtJx+R0+0Yu:jaZOWu9ce2d4 |
MALICIOUS
Generic archive extractor
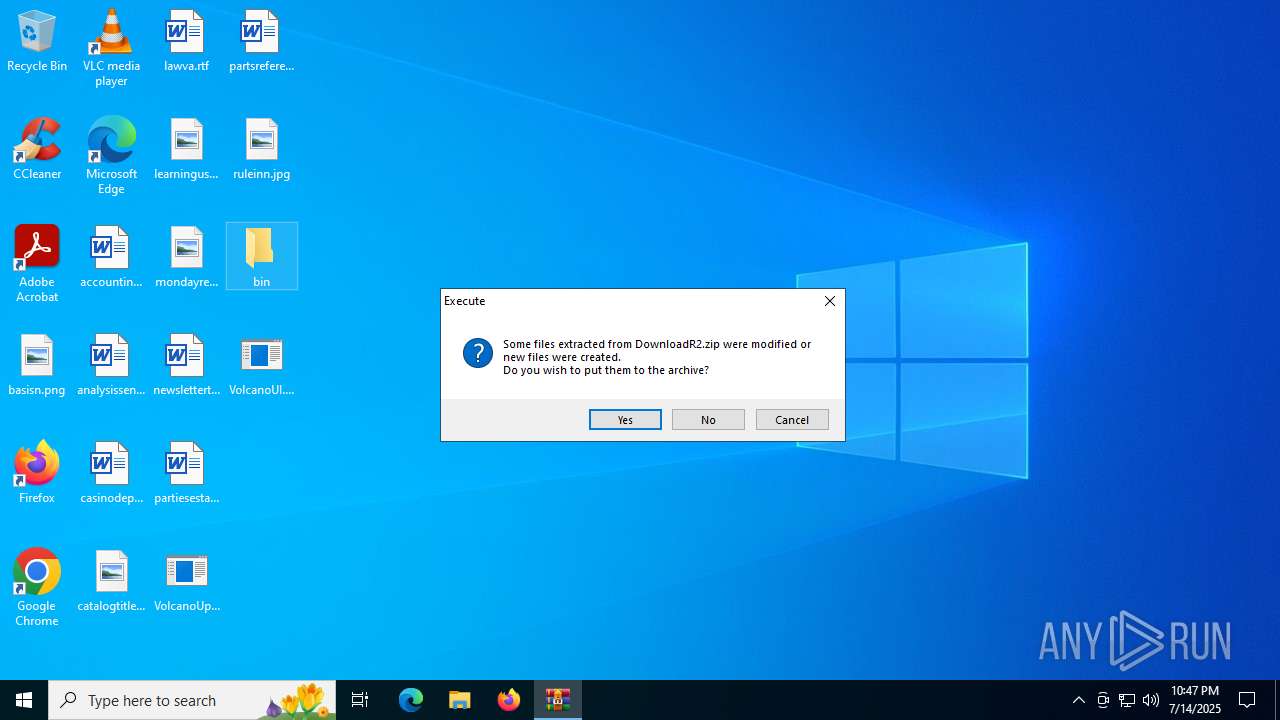
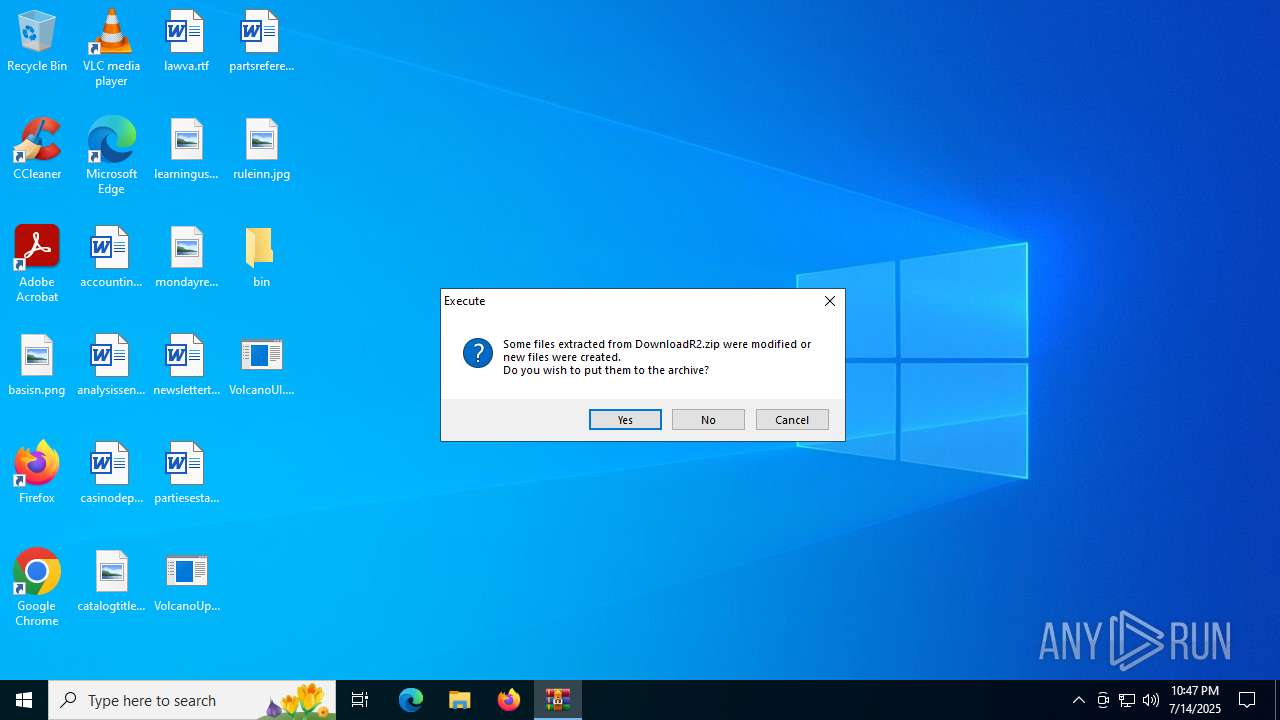
- WinRAR.exe (PID: 2532)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2532)
- VolcanoUpdater.exe (PID: 6636)
- VolcanoUpdater.exe (PID: 3672)
- VolcanoUpdater.exe (PID: 4312)
- VolcanoUpdater.exe (PID: 4552)
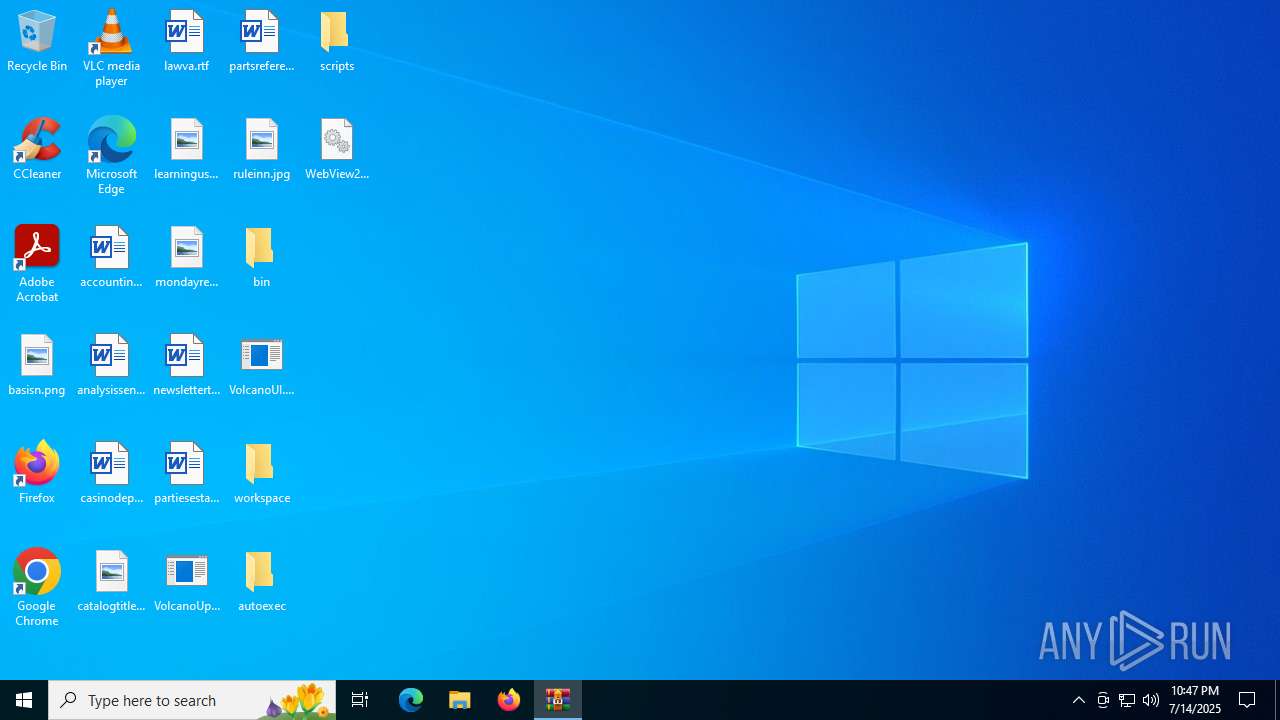
Executable content was dropped or overwritten
- VolcanoUpdater.exe (PID: 6636)
- VolcanoUI.exe (PID: 7020)
- VolcanoUpdater.exe (PID: 3672)
- VolcanoUI.exe (PID: 2512)
Reads the date of Windows installation
- VolcanoUpdater.exe (PID: 6636)
- VolcanoUpdater.exe (PID: 3672)
- VolcanoUpdater.exe (PID: 4552)
- VolcanoUpdater.exe (PID: 4312)
Reads the BIOS version
- VolcanoUpdater.exe (PID: 6636)
- VolcanoUI.exe (PID: 7020)
- VolcanoUpdater.exe (PID: 3672)
- VolcanoUI.exe (PID: 2512)
- VolcanoUpdater.exe (PID: 4552)
- VolcanoUI.exe (PID: 5284)
- VolcanoUI.exe (PID: 4932)
- VolcanoUpdater.exe (PID: 4312)
- VolcanoUI.exe (PID: 7132)
Process drops legitimate windows executable
- VolcanoUI.exe (PID: 7020)
- VolcanoUI.exe (PID: 2512)
INFO
Reads the computer name
- VolcanoUpdater.exe (PID: 6636)
- VolcanoUI.exe (PID: 7020)
- VolcanoUpdater.exe (PID: 3672)
- VolcanoUI.exe (PID: 2512)
- VolcanoUI.exe (PID: 5284)
- VolcanoUI.exe (PID: 4932)
- VolcanoUpdater.exe (PID: 4312)
- VolcanoUpdater.exe (PID: 4552)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2532)
Create files in a temporary directory
- VolcanoUpdater.exe (PID: 6636)
- VolcanoUI.exe (PID: 7020)
Checks supported languages
- VolcanoUI.exe (PID: 7020)
- VolcanoUpdater.exe (PID: 6636)
- VolcanoUpdater.exe (PID: 3672)
- VolcanoUI.exe (PID: 2512)
- VolcanoUpdater.exe (PID: 4552)
- VolcanoUI.exe (PID: 4932)
- VolcanoUpdater.exe (PID: 4312)
- VolcanoUI.exe (PID: 5284)
- VolcanoUI.exe (PID: 7132)
Process checks computer location settings
- VolcanoUpdater.exe (PID: 6636)
- VolcanoUpdater.exe (PID: 3672)
- VolcanoUpdater.exe (PID: 4312)
- VolcanoUpdater.exe (PID: 4552)
The sample compiled with english language support
- VolcanoUI.exe (PID: 7020)
- VolcanoUI.exe (PID: 2512)
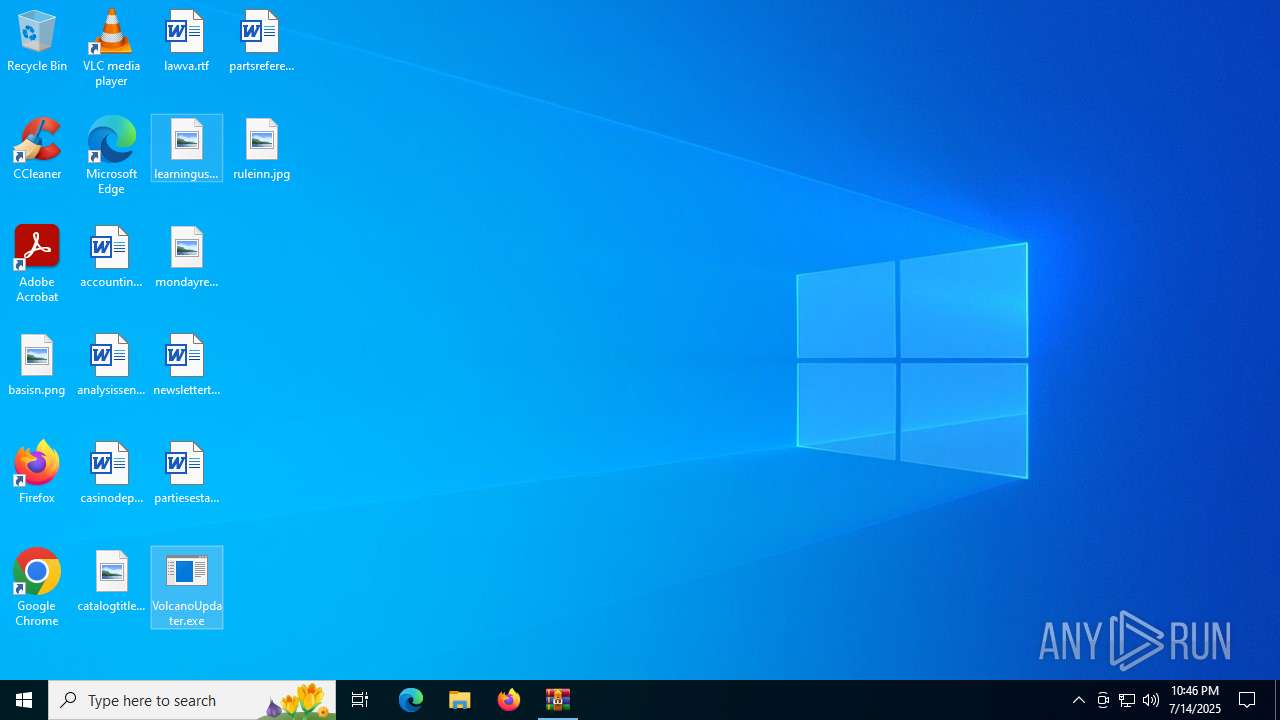
Manual execution by a user
- VolcanoUpdater.exe (PID: 3672)
- VolcanoUpdater.exe (PID: 4552)
- VolcanoUI.exe (PID: 4932)
- VolcanoUpdater.exe (PID: 4312)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:06:15 03:32:40 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | PLEASE_EXTRACT_THIS.txt |
Total processes
148
Monitored processes
16
Malicious processes
5
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | VolcanoUpdater.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | VolcanoUpdater.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2512 | "C:\Users\admin\Desktop\VolcanoUI.exe" | C:\Users\admin\Desktop\VolcanoUI.exe | VolcanoUpdater.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2532 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\DownloadR2.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3672 | "C:\Users\admin\Desktop\VolcanoUpdater.exe" | C:\Users\admin\Desktop\VolcanoUpdater.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4312 | "C:\Users\admin\Desktop\VolcanoUpdater.exe" | C:\Users\admin\Desktop\VolcanoUpdater.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4552 | "C:\Users\admin\Desktop\VolcanoUpdater.exe" | C:\Users\admin\Desktop\VolcanoUpdater.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4760 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | VolcanoUpdater.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 249
Read events
7 227
Write events
22
Delete events
0
Modification events
| (PID) Process: | (2532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\DownloadR2.zip | |||
| (PID) Process: | (2532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (2532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
8
Suspicious files
35
Text files
148
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6636 | VolcanoUpdater.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2532.1493\bin\version.txt | text | |
MD5:D49633427C94978C08790B7A247A76BC | SHA256:7D589D9FBD16FFF0A23CE254405007C8CA262F319D1512A488DEB4310844F007 | |||
| 6636 | VolcanoUpdater.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2532.1493\bin\page\assets\cameligo-BFG1Mk7z.js | text | |
MD5:E9D40B956B6BEC8A5BFFD0D94552B2F8 | SHA256:CC50FE6B6738380FDC2D31D1A2FE210EA67CB19A5F6ABBF91E0AD3A08491A1E5 | |||
| 6636 | VolcanoUpdater.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2532.1493\bin\page\assets\cpp-CLLBncYj.js | text | |
MD5:0F3FCC7CA8691D6CF4FF68B8347D18DD | SHA256:A5FB8F0E4EBFC61B3865C092BD6434A36D24EE6E62477D4ADD55A1D796CD88B4 | |||
| 6636 | VolcanoUpdater.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2532.1493\bin\page\assets\clojure-DTECt2xU.js | text | |
MD5:CBE50C2D87AFFE61EE11FAADF2F57252 | SHA256:C897D061A0F39FABC5B9204E0EA8F78FA12C37C4BE45A2749BD1119D2CBCBF68 | |||
| 6636 | VolcanoUpdater.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2532.1493\bin\page\assets\csp-5Rap-vPy.js | text | |
MD5:8CB672DB7B68FE7F3F7DFCB05AE388A5 | SHA256:C413FA2B83B1A0B1AF76E822721C4A429163B7BCD477B4DEEBD41F7C4E4C8A20 | |||
| 6636 | VolcanoUpdater.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2532.1493\bin\page\assets\coffee-CDGzqUPQ.js | text | |
MD5:72CD04F563D3C68AC724715139C7FD33 | SHA256:ADD650C5EA8D1B28C11A807ED3BF9B52A15496179CA9BC19D3900A0B577DACD5 | |||
| 6636 | VolcanoUpdater.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2532.1493\bin\page\assets\csharp-dUCx_-0o.js | text | |
MD5:5616EF1623A707EDDFB5641341DB735E | SHA256:DE87D1D2BDCEC69C9A9AB2CE355B9BC638BAC7E4078D303DF89DADCB85F58846 | |||
| 6636 | VolcanoUpdater.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2532.1493\bin\page\assets\codicon-DCmgc-ay.ttf | ttf | |
MD5:CB7F0A51C106A33FB4ABAB8C454373D8 | SHA256:0F1D5219934E96E83B8DB162D60B4D8C09B5DE1E7D38031CBAFE4A3C0F2889C9 | |||
| 6636 | VolcanoUpdater.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2532.1493\bin\page\assets\cssMode-wuhyQlOf.js | binary | |
MD5:B63088DC9449EDE74B283708F401FC0F | SHA256:019BE82D233F42BEE2CFA76DD31E3AA42D73C2F6276C7A576677BC7B005D7A38 | |||
| 6636 | VolcanoUpdater.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2532.1493\bin\page\assets\css-D3h14YRZ.js | text | |
MD5:387BF345843B2BE9BA90A6FBA1DE584E | SHA256:55CD0C924635240191C8189F4A500720E61EEE267EB2093474BF686AE5820EA6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
33
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
764 | lsass.exe | GET | 200 | 142.250.186.35:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
764 | lsass.exe | GET | 200 | 142.250.186.35:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.55.110.193:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3740 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3740 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4700 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1520 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6636 | VolcanoUpdater.exe | 172.67.175.175:443 | file.volcano.wtf | CLOUDFLARENET | US | malicious |
764 | lsass.exe | 142.250.186.35:80 | c.pki.goog | GOOGLE | US | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.55.110.193:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
file.volcano.wtf |
| malicious |
c.pki.goog |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
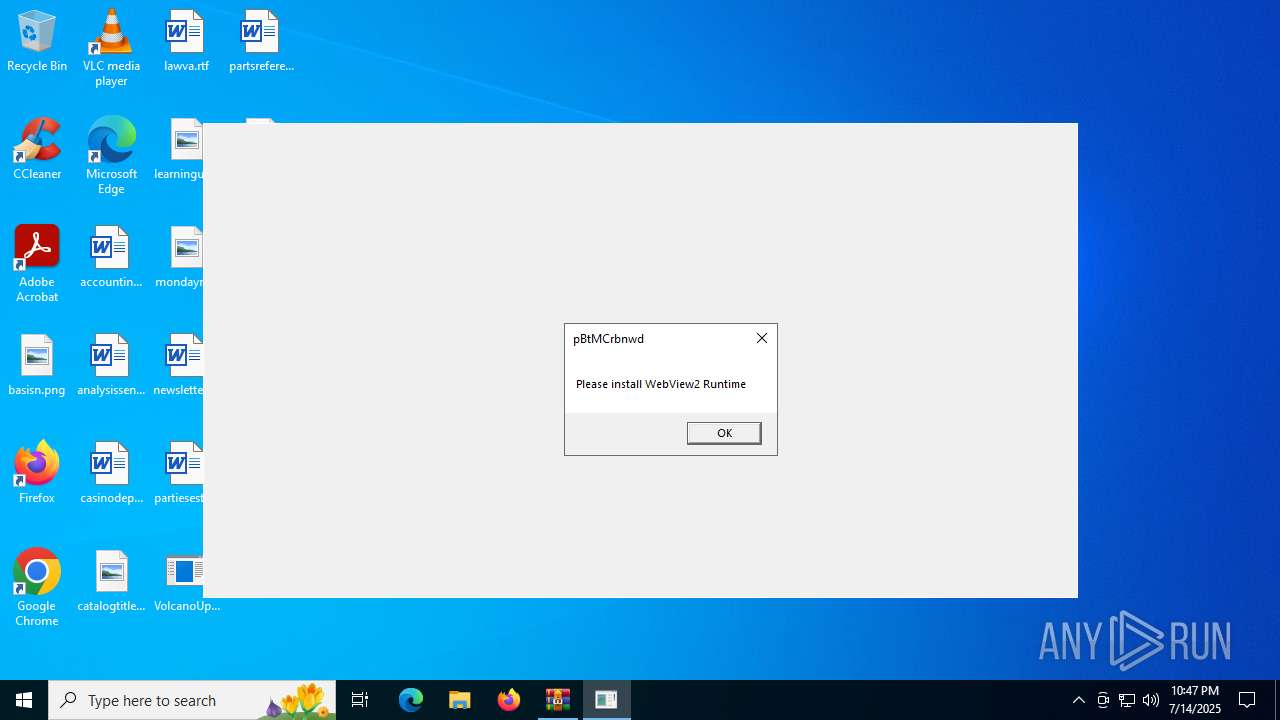
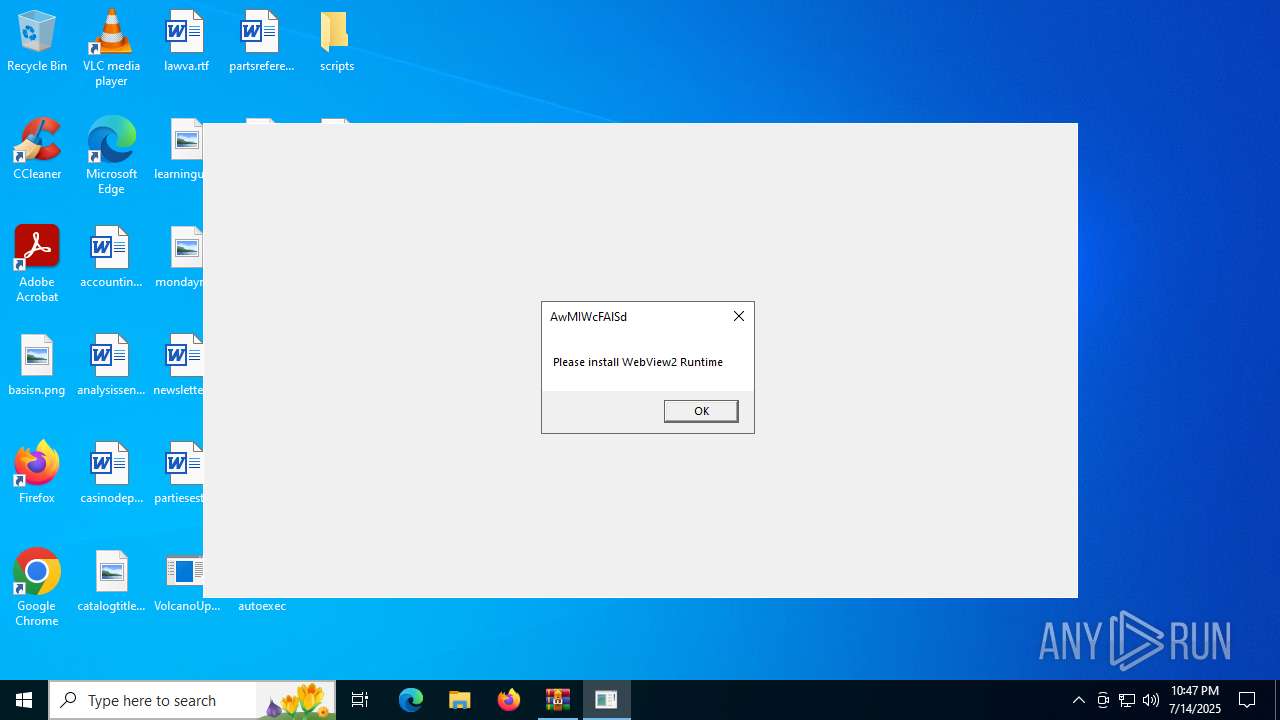
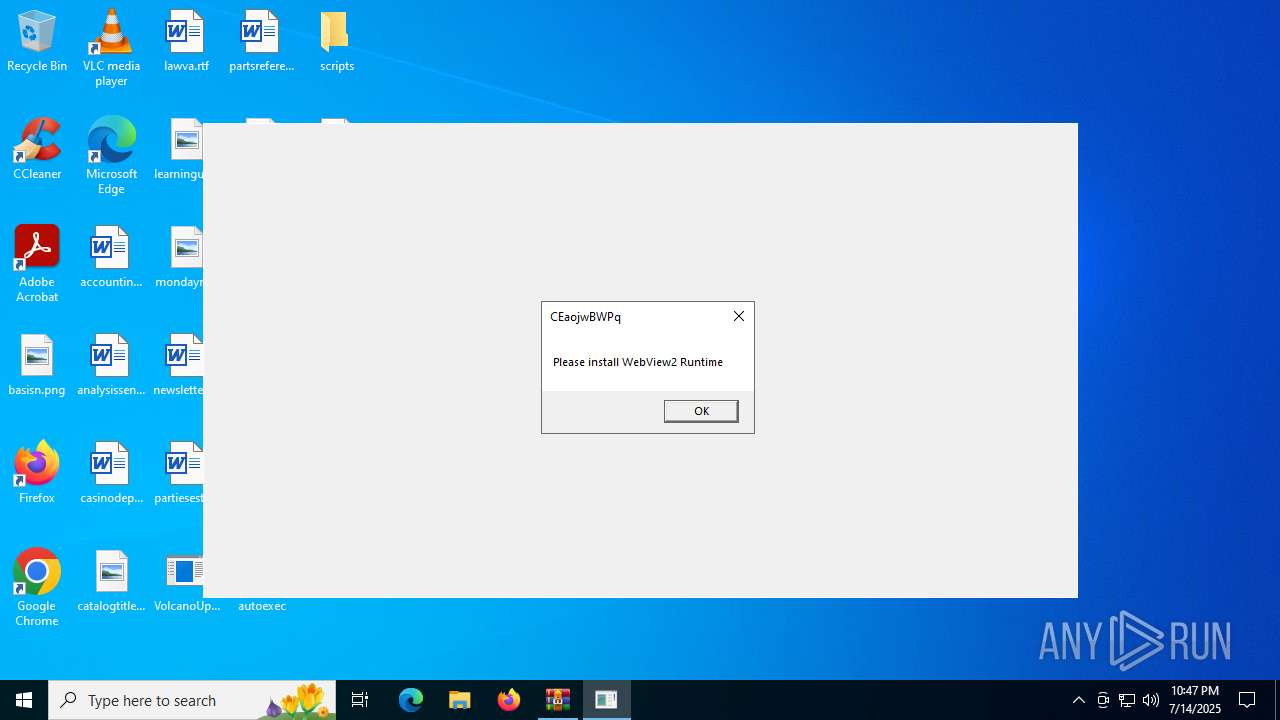
VolcanoUI.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
VolcanoUI.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
VolcanoUI.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
VolcanoUI.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
VolcanoUI.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
VolcanoUI.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
VolcanoUI.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
VolcanoUI.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|