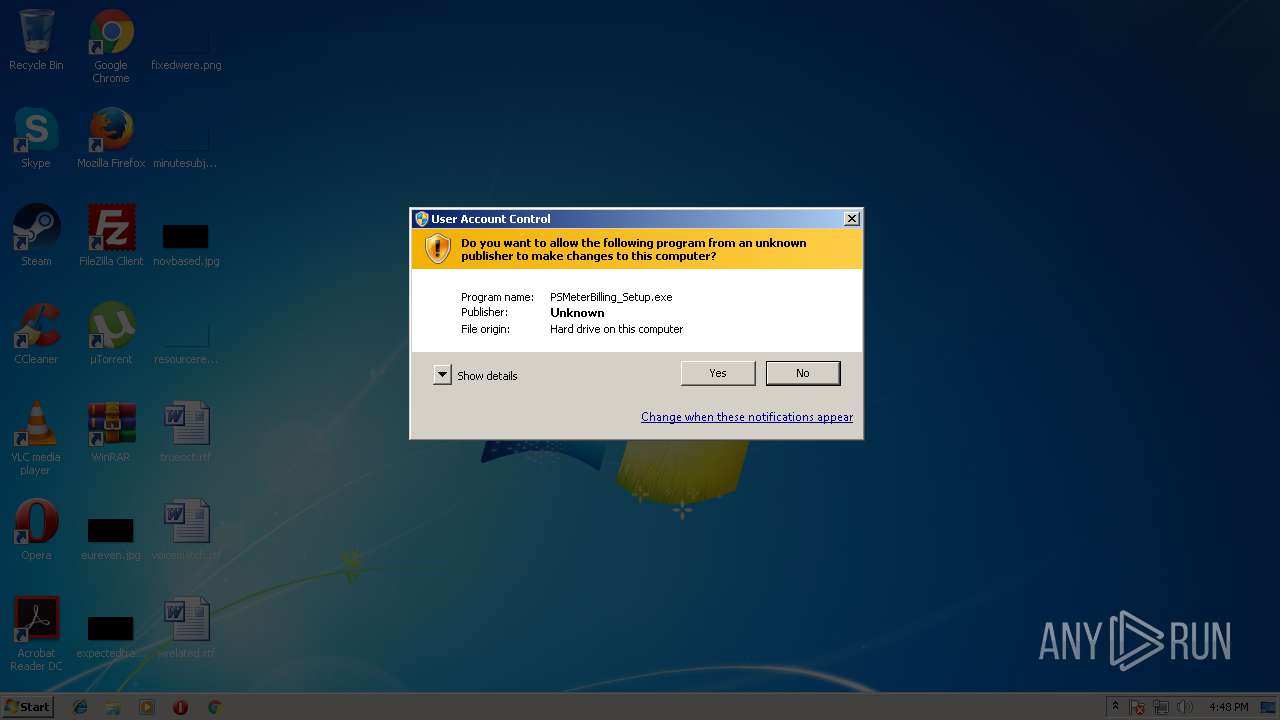
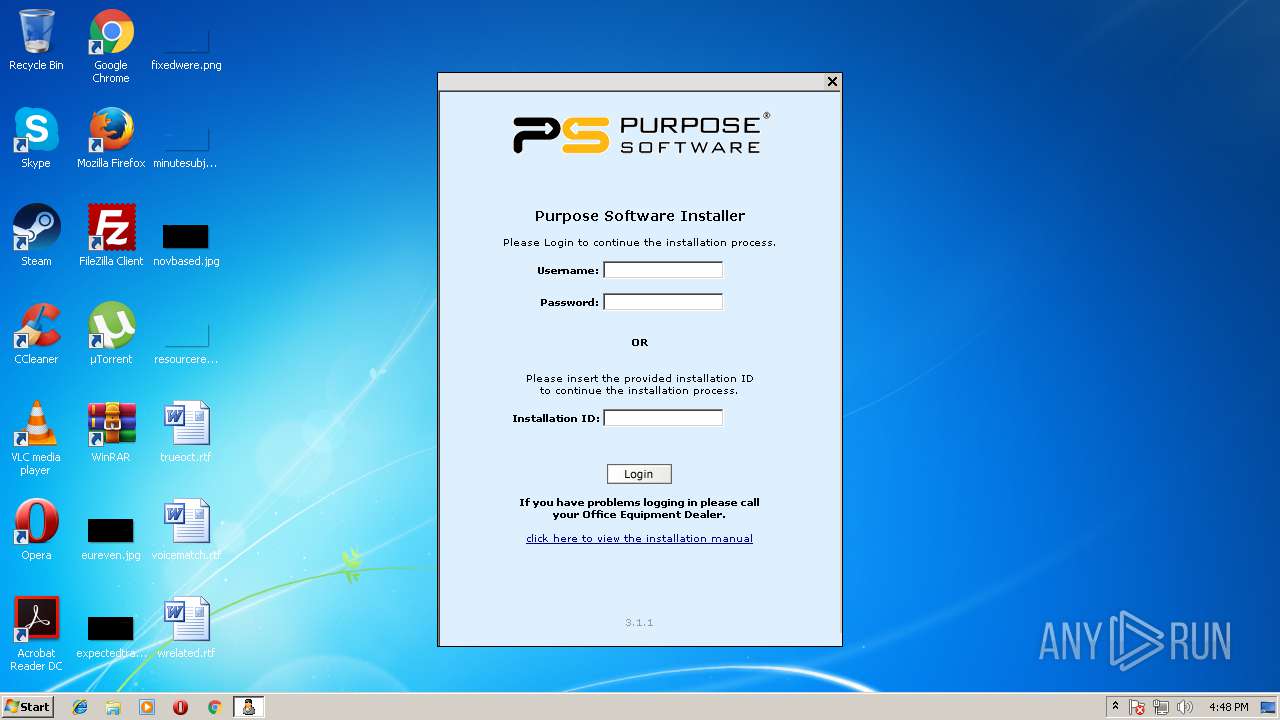
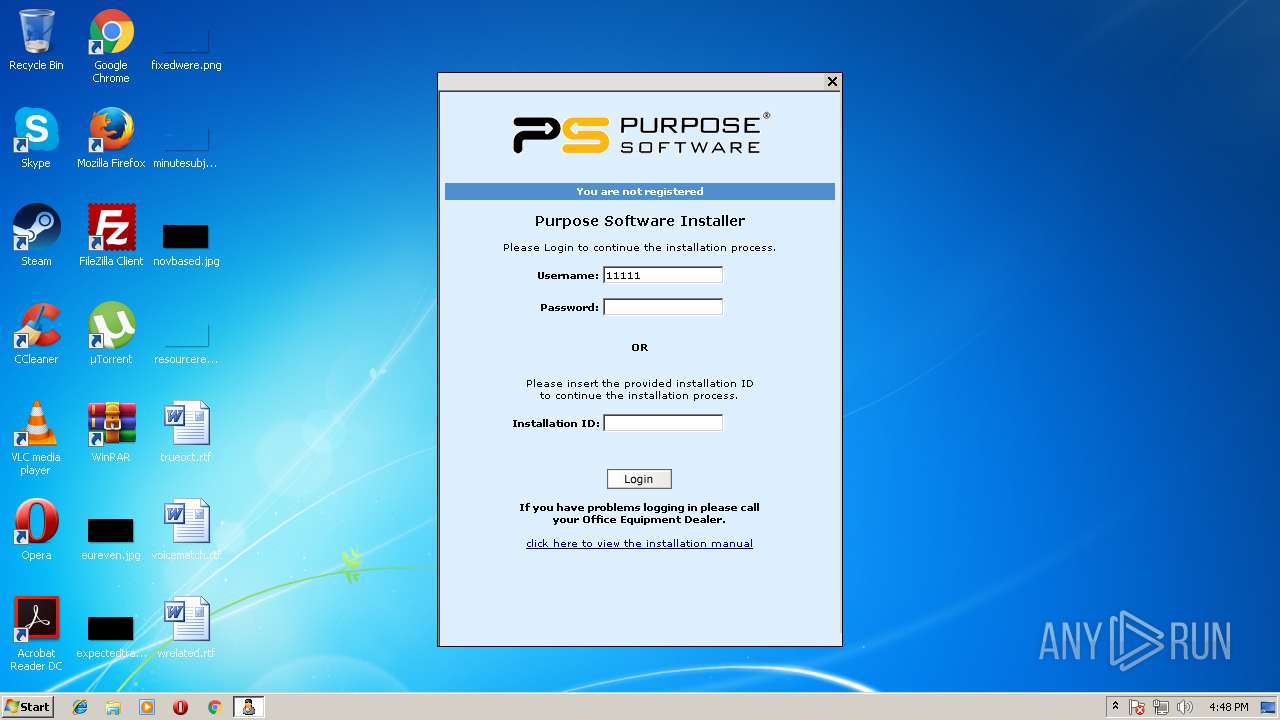
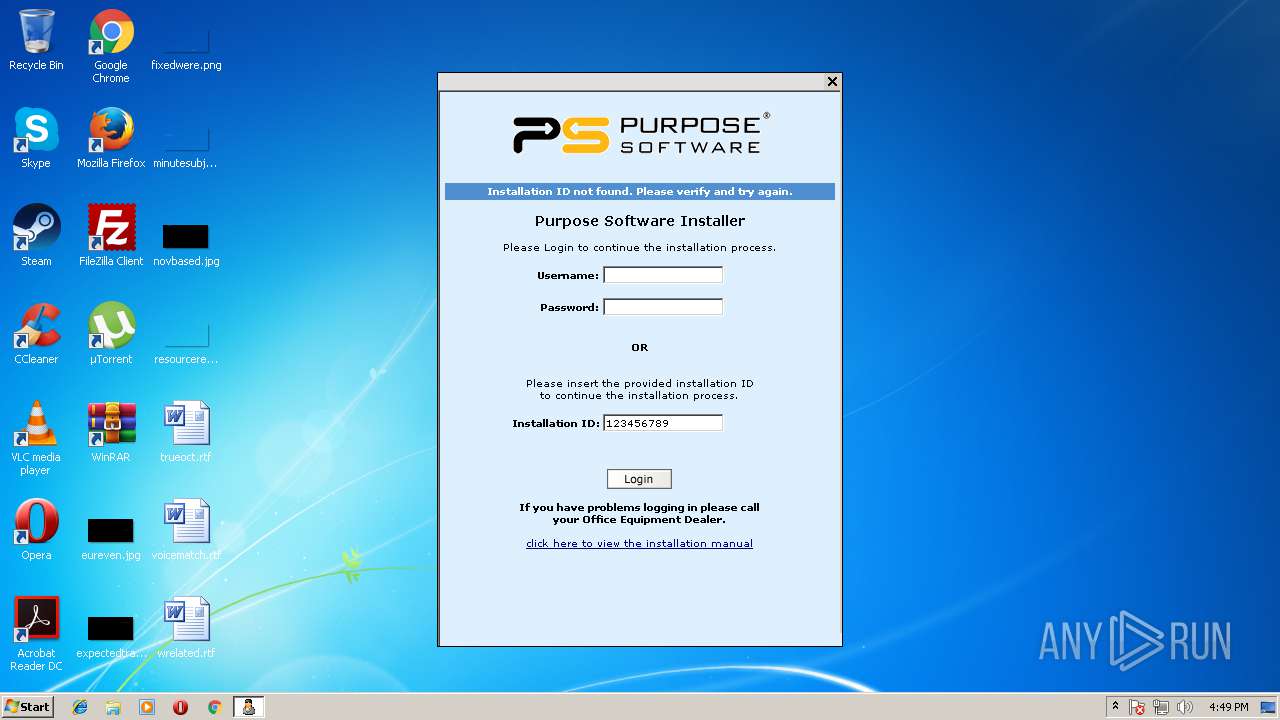
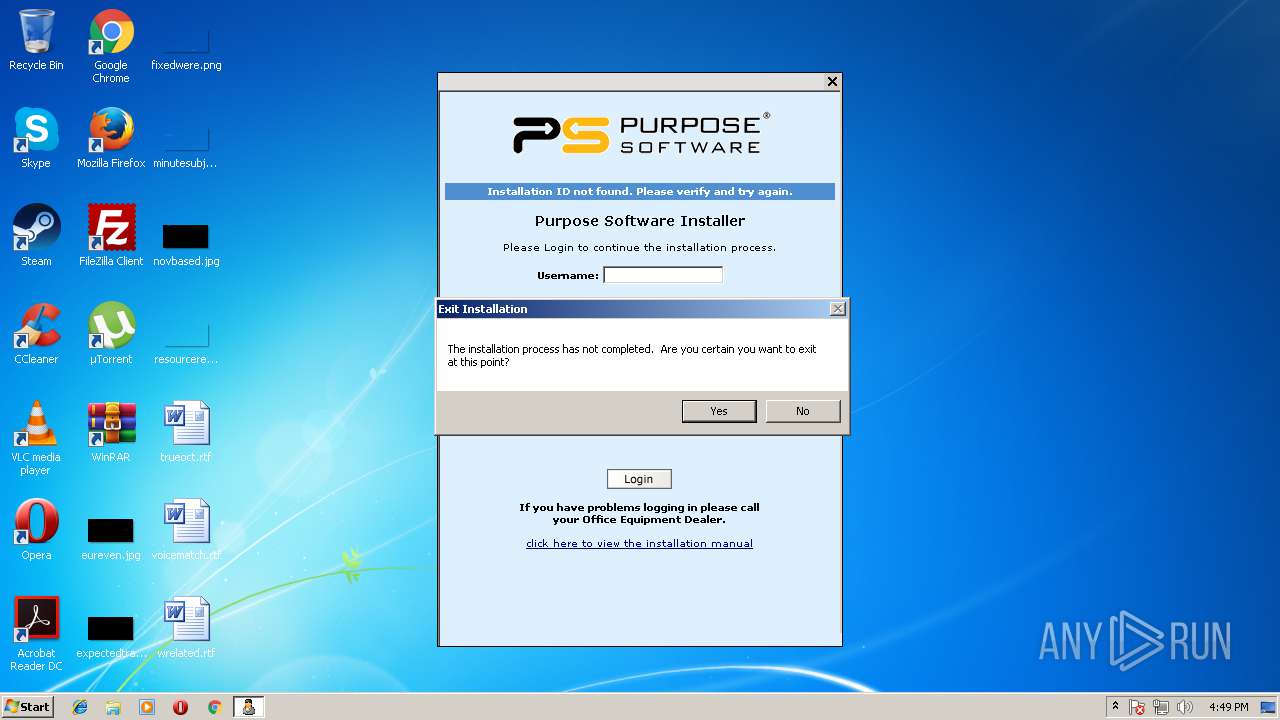
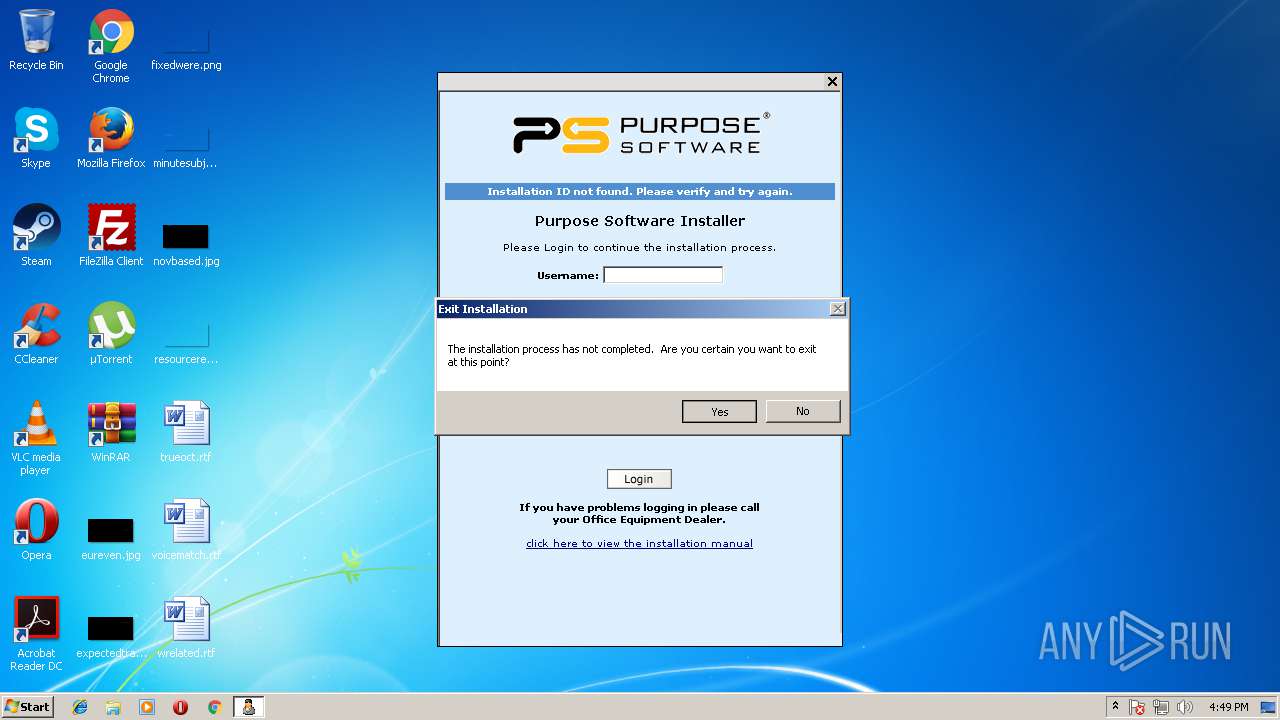
| File name: | PSMeterBilling_Setup.exe |
| Full analysis: | https://app.any.run/tasks/30d9485f-fbf2-47ec-ba61-da7e2c6208f4 |
| Verdict: | Malicious activity |
| Analysis date: | September 07, 2018, 15:47:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, RAR self-extracting archive |
| MD5: | 51AC066801A7A4D304230235E4AFE393 |
| SHA1: | 994245512D4DD6F45FA4B25CEADE4B6BF699B1FB |
| SHA256: | DA09DBAB45EB946296F2D43514B0012DA30E192E6D8A4526FB44CA8F2F11B8D3 |
| SSDEEP: | 393216:vLpDDLWKwKzN2oHj7YyoAQJNuelMs6vmEvsuke2BjnMRrpzxPsb:vLRZwgypARS/6vmXte2pnMg |
MALICIOUS
Loads dropped or rewritten executable
- Preload.exe (PID: 1540)
Application was dropped or rewritten from another process
- qmInstaller.exe (PID: 1552)
- Preload.exe (PID: 1540)
Starts NET.EXE for service management
- PSMeterBilling_Setup.exe (PID: 3020)
SUSPICIOUS
Executable content was dropped or overwritten
- PSMeterBilling_Setup.exe (PID: 3020)
- Preload.exe (PID: 1540)
Creates COM task schedule object
- Preload.exe (PID: 1540)
Low-level read access rights to disk partition
- qmInstaller.exe (PID: 1552)
Creates files in the user directory
- qmInstaller.exe (PID: 1552)
Reads Internet Cache Settings
- qmInstaller.exe (PID: 1552)
Reads internet explorer settings
- qmInstaller.exe (PID: 1552)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | WinRAR Self Extracting archive (88.2) |
|---|---|---|
| .exe | | | UPX compressed Win32 Executable (4.6) |
| .exe | | | Win32 EXE Yoda's Crypter (4.5) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.1) |
| .exe | | | Win32 Executable (generic) (0.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2004:09:08 15:51:36+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 5 |
| CodeSize: | 45056 |
| InitializedDataSize: | 8192 |
| UninitializedDataSize: | 90112 |
| EntryPoint: | 0x21bd0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 08-Sep-2004 13:51:36 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000200 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 08-Sep-2004 13:51:36 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
UPX0 | 0x00001000 | 0x00016000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
UPX1 | 0x00017000 | 0x0000B000 | 0x0000AE00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.89983 |
.rsrc | 0x00022000 | 0x00002000 | 0x00001C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.75785 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.10885 | 531 | UNKNOWN | Russian - Russia | RT_MANIFEST |
2 | 3.88998 | 1384 | UNKNOWN | Russian - Russia | RT_ICON |
3 | 4.12176 | 744 | UNKNOWN | Russian - Russia | RT_ICON |
4 | 4.68705 | 2216 | UNKNOWN | Russian - Russia | RT_ICON |
7 | 7.52713 | 556 | UNKNOWN | Russian - Russia | RT_STRING |
8 | 7.64952 | 886 | UNKNOWN | Russian - Russia | RT_STRING |
9 | 7.52107 | 530 | UNKNOWN | Russian - Russia | RT_STRING |
10 | 7.56432 | 638 | UNKNOWN | Russian - Russia | RT_STRING |
100 | 2.6902 | 62 | UNKNOWN | Russian - Russia | RT_GROUP_ICON |
101 | 7.84911 | 2998 | UNKNOWN | Russian - Russia | RT_BITMAP |
Imports
ADVAPI32.DLL |
COMCTL32.DLL |
COMDLG32.DLL |
GDI32.DLL |
KERNEL32.DLL |
OLE32.DLL |
SHELL32.DLL |
USER32.DLL |
Total processes
46
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1540 | "C:\PSMeterBilling\Preload.exe" -HOST:www.psmeterbilling.co.uk -PATH:PSMeterBilling -LOG | C:\PSMeterBilling\Preload.exe | PSMeterBilling_Setup.exe | ||||||||||||
User: admin Company: PrintMIB, LLC Integrity Level: HIGH Description: PreLoad utility for DCA installer Exit code: 0 Version: 3.01.0001 Modules
| |||||||||||||||
| 1552 | c:\PSMeterBilling\qmInstaller.exe -HOST:www.psmeterbilling.co.uk -PATH:PSMeterBilling -LOG | c:\PSMeterBilling\qmInstaller.exe | Preload.exe | ||||||||||||
User: admin Company: PrintMIB, LLC Integrity Level: HIGH Description: DCA Installer Exit code: 0 Version: 3.01.0001 Modules
| |||||||||||||||
| 2216 | "C:\Windows\system32\net.exe" stop qmMgr | C:\Windows\system32\net.exe | — | PSMeterBilling_Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2488 | C:\Windows\system32\net1 stop qmwatchdog | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3020 | "C:\Users\admin\AppData\Local\Temp\PSMeterBilling_Setup.exe" | C:\Users\admin\AppData\Local\Temp\PSMeterBilling_Setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3356 | C:\Windows\system32\net1 stop qmMgr | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3404 | "C:\Windows\system32\net.exe" stop qmwatchdog | C:\Windows\system32\net.exe | — | PSMeterBilling_Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3416 | "C:\Users\admin\AppData\Local\Temp\PSMeterBilling_Setup.exe" | C:\Users\admin\AppData\Local\Temp\PSMeterBilling_Setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
1 221
Read events
192
Write events
1 014
Delete events
15
Modification events
| (PID) Process: | (3020) PSMeterBilling_Setup.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR SFX |
| Operation: | write | Name: | C%%PSMeterBilling |
Value: C:\PSMeterBilling | |||
| (PID) Process: | (3020) PSMeterBilling_Setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3020) PSMeterBilling_Setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3020) PSMeterBilling_Setup.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-500\Software\WinRAR SFX |
| Operation: | write | Name: | C%%Program Files%WinRAR |
Value: C:\Program Files\WinRAR | |||
| (PID) Process: | (3020) PSMeterBilling_Setup.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-500\Software\WinRAR SFX |
| Operation: | write | Name: | C%%PSMeterBilling |
Value: C:\PSMeterBilling | |||
| (PID) Process: | (1540) Preload.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Dart.Tcp.1 |
| Operation: | write | Name: | |
Value: Dart Tcp Control | |||
| (PID) Process: | (1540) Preload.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Dart.Tcp.1\CLSID |
| Operation: | write | Name: | |
Value: {CA4FC24B-C65C-11D1-AA6F-000000000000} | |||
| (PID) Process: | (1540) Preload.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Dart.Tcp |
| Operation: | write | Name: | |
Value: Dart Tcp Control | |||
| (PID) Process: | (1540) Preload.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Dart.Tcp\CurVer |
| Operation: | write | Name: | |
Value: Dart.Tcp.1 | |||
| (PID) Process: | (1540) Preload.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{CA4FC24B-C65C-11D1-AA6F-000000000000} |
| Operation: | write | Name: | |
Value: Dart Tcp Control | |||
Executable files
41
Suspicious files
0
Text files
68
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3020 | PSMeterBilling_Setup.exe | C:\PSMeterBilling\PrintMIB3.mdb | — | |
MD5:— | SHA256:— | |||
| 3020 | PSMeterBilling_Setup.exe | C:\PSMeterBilling\ExtLVCTL.ocx | executable | |
MD5:6C2A11CD8ADA481897A6C225435CFA53 | SHA256:08F6949C912C95FE68CB468812EBF6DCF45D0295692ADA1759364B27295EC218 | |||
| 3020 | PSMeterBilling_Setup.exe | C:\PSMeterBilling\lgOk.gif | image | |
MD5:D96ED064F3310BA0C96A811B08408093 | SHA256:9AF6643B08D7C9F84517CB39E982EFF582A160804D7C3A30BA38D3EC0BC7508D | |||
| 3020 | PSMeterBilling_Setup.exe | C:\PSMeterBilling\MSWINSCK.OCX | executable | |
MD5:E8A2190A9E8EE5E5D2E0B599BBF9DDA6 | SHA256:80AB0B86DE58A657956B2A293BD9957F78E37E7383C86D6CD142208C153B6311 | |||
| 3020 | PSMeterBilling_Setup.exe | C:\PSMeterBilling\Mscomct2.ocx | executable | |
MD5:C1B4AF41A0370E4081D59AC99BCC929D | SHA256:2B7A1F905486736EDA8B51ADD1BC2590C2A6D9D5A9AB7565335D989F39C0EB8E | |||
| 3020 | PSMeterBilling_Setup.exe | C:\PSMeterBilling\DartZip.dll | executable | |
MD5:4AA4B6C02A7D9975B06A5E709388502C | SHA256:127FBB9412758A4CC8051DCC6F243541D4A05EFB2BF38444C5BBF9F654284461 | |||
| 3020 | PSMeterBilling_Setup.exe | C:\PSMeterBilling\DartZipLite.dll | executable | |
MD5:43F9EF17ECD013D2385D2C580DFC8D8A | SHA256:57360589101AD67FFF9666895AF6DC83348B514F5A130E011392176ED493AAC5 | |||
| 3020 | PSMeterBilling_Setup.exe | C:\PSMeterBilling\lgNotOk.gif | image | |
MD5:BFD2C64C442563832375A6B0B3CB186D | SHA256:B93AB9C87301F5BB3B3DC3CE181FDF2EB2810CBED99A69E6948EFD27C4DC4E06 | |||
| 3020 | PSMeterBilling_Setup.exe | C:\PSMeterBilling\DartWeb.dll | executable | |
MD5:65E0DB278678EAFE4BCA909EDE678C3C | SHA256:72B251A1319DA14A1F12374285D4B047CC6FB30F751CB6B5B45809E9D8675B99 | |||
| 3020 | PSMeterBilling_Setup.exe | C:\PSMeterBilling\qmgui.exe | executable | |
MD5:FB5EF93AAB9AE6EC93FF65EE99632AFE | SHA256:65FB5BDDC039ED772D13461A5673AD609AE6E4933B7130494182A58EC798FA18 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
5
DNS requests
1
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1552 | qmInstaller.exe | GET | 404 | 74.123.84.218:80 | http://www.psmeterbilling.co.uk/install/images/inputbg.gif | US | html | 4.78 Kb | malicious |
1552 | qmInstaller.exe | POST | — | 74.123.84.218:80 | http://www.psmeterbilling.co.uk/install/login.asp | US | — | — | malicious |
1552 | qmInstaller.exe | POST | 200 | 74.123.84.218:80 | http://www.psmeterbilling.co.uk/install/login.asp | US | html | 5.28 Kb | malicious |
1552 | qmInstaller.exe | GET | 200 | 74.123.84.218:80 | http://www.psmeterbilling.co.uk/install/login.asp?session=QM00001&sessiona=C4BA3647&instver=3.1.1&qmibver=3.2.6&tsclient=False&proxy=N&clientname=&varid=&groupid=&groupname=&hostmac=52:54:00:4A:AD:11&hostvm=false00 | US | html | 4.95 Kb | malicious |
1552 | qmInstaller.exe | GET | 404 | 74.123.84.218:80 | http://www.psmeterbilling.co.uk/install/images/inputbg.gif | US | html | 4.78 Kb | malicious |
1552 | qmInstaller.exe | POST | 200 | 74.123.84.218:80 | http://www.psmeterbilling.co.uk/install/login.asp | US | html | 5.31 Kb | malicious |
1552 | qmInstaller.exe | GET | — | 74.123.84.218:80 | http://www.psmeterbilling.co.uk/install/images/inputbg.gif | US | — | — | malicious |
1552 | qmInstaller.exe | GET | 200 | 74.123.84.218:80 | http://www.psmeterbilling.co.uk/install/install.css | US | text | 685 b | malicious |
1552 | qmInstaller.exe | POST | 200 | 74.123.84.218:80 | http://www.psmeterbilling.co.uk/install/login.asp | US | html | 5.28 Kb | malicious |
1552 | qmInstaller.exe | GET | — | 74.123.84.218:80 | http://www.psmeterbilling.co.uk/install/images/inputbg.gif | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1552 | qmInstaller.exe | 74.123.84.218:80 | www.psmeterbilling.co.uk | SP ISP | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.psmeterbilling.co.uk |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1552 | qmInstaller.exe | Misc activity | SUSPICIOUS [PTsecurity] Possible TrojanDownloader |