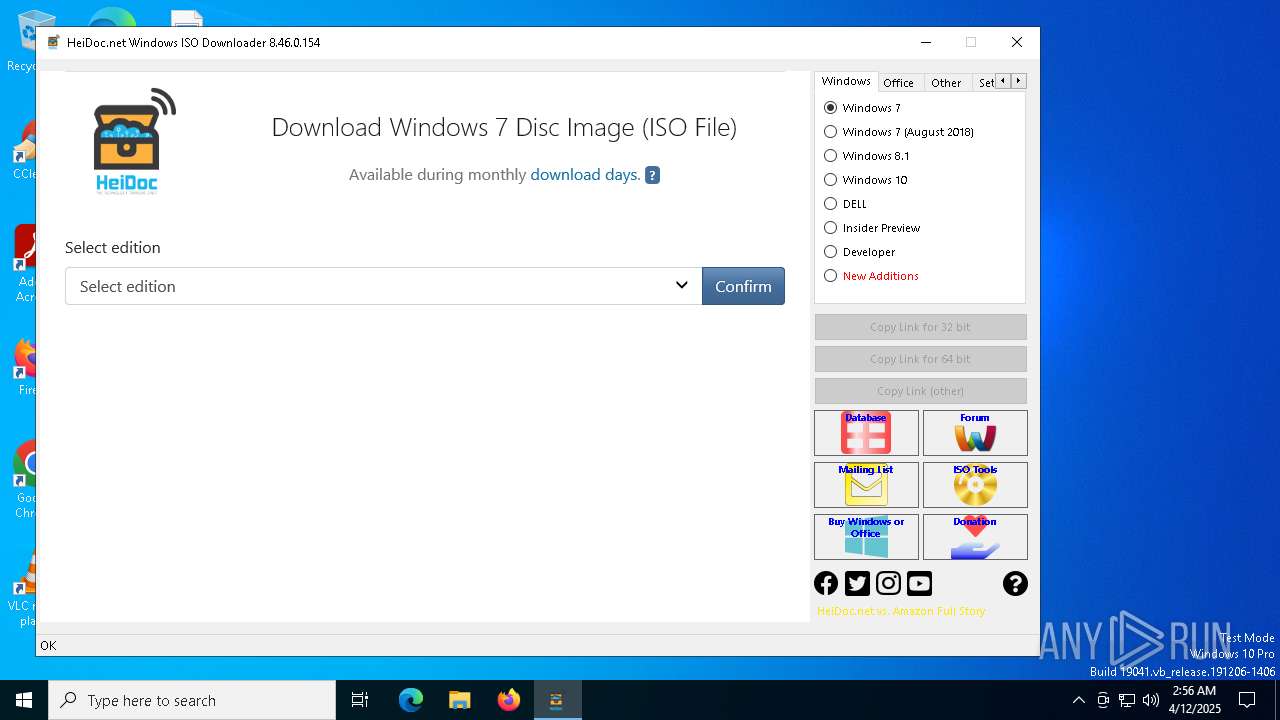
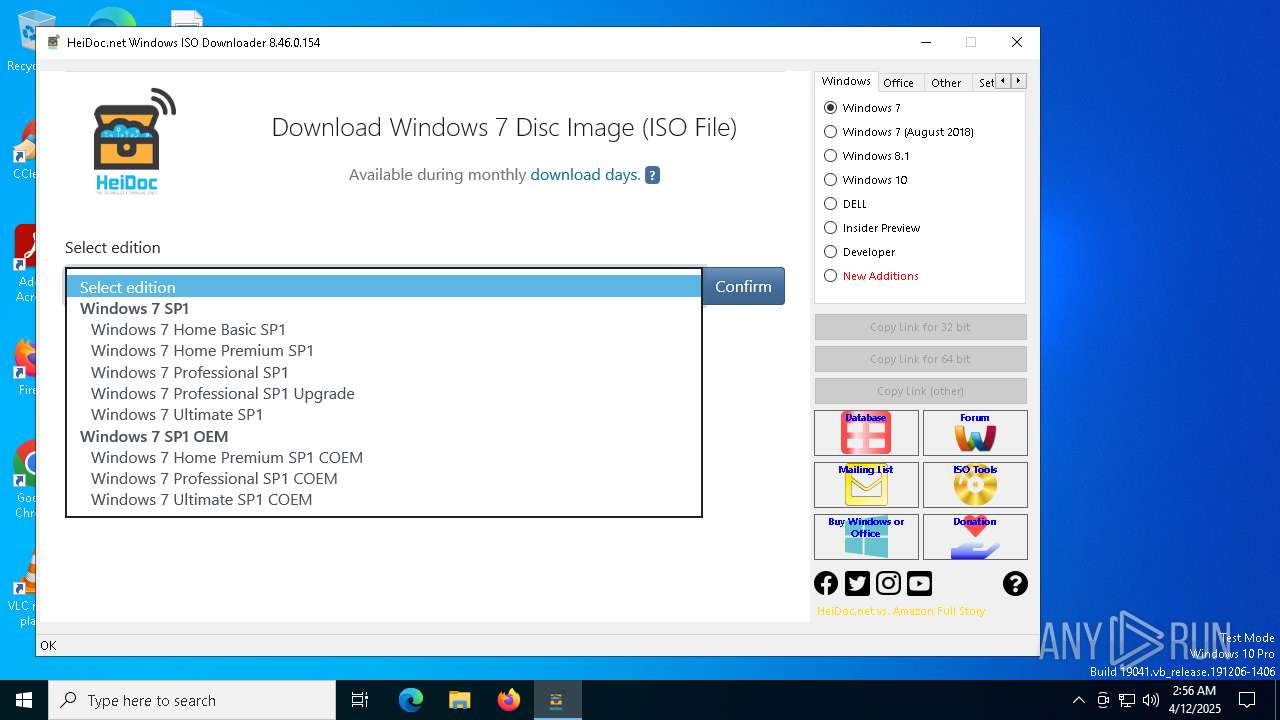
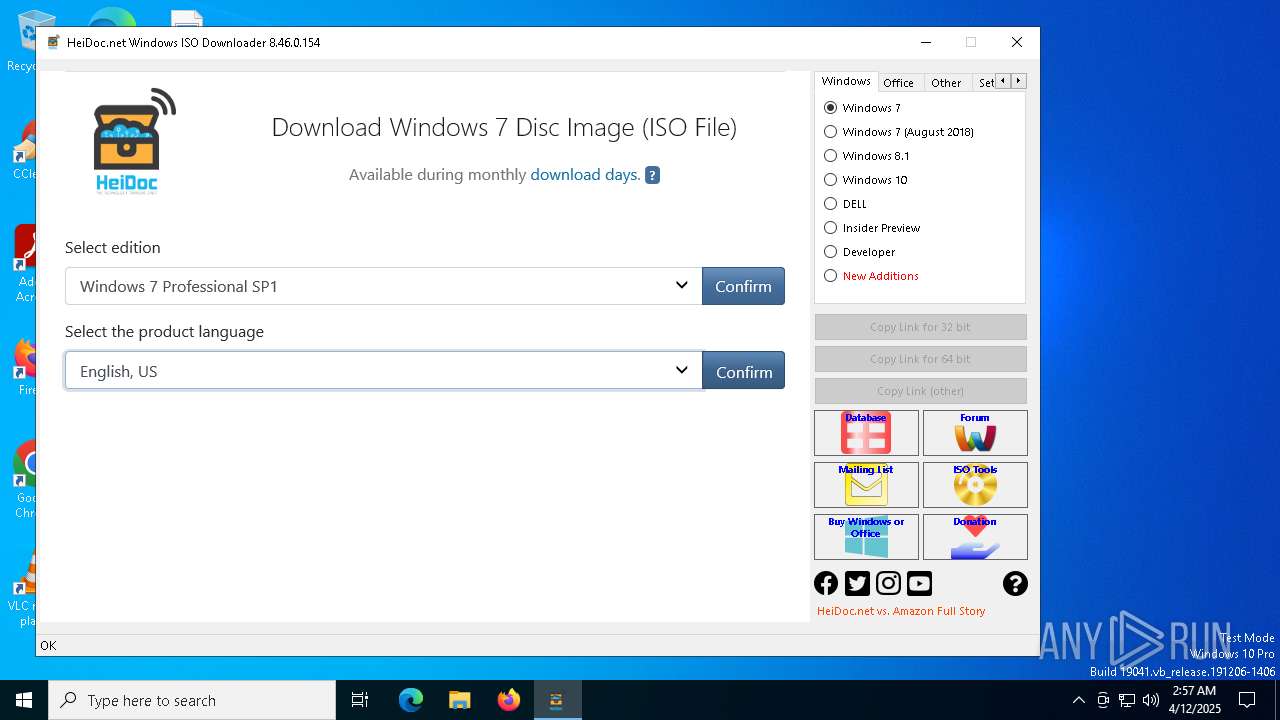
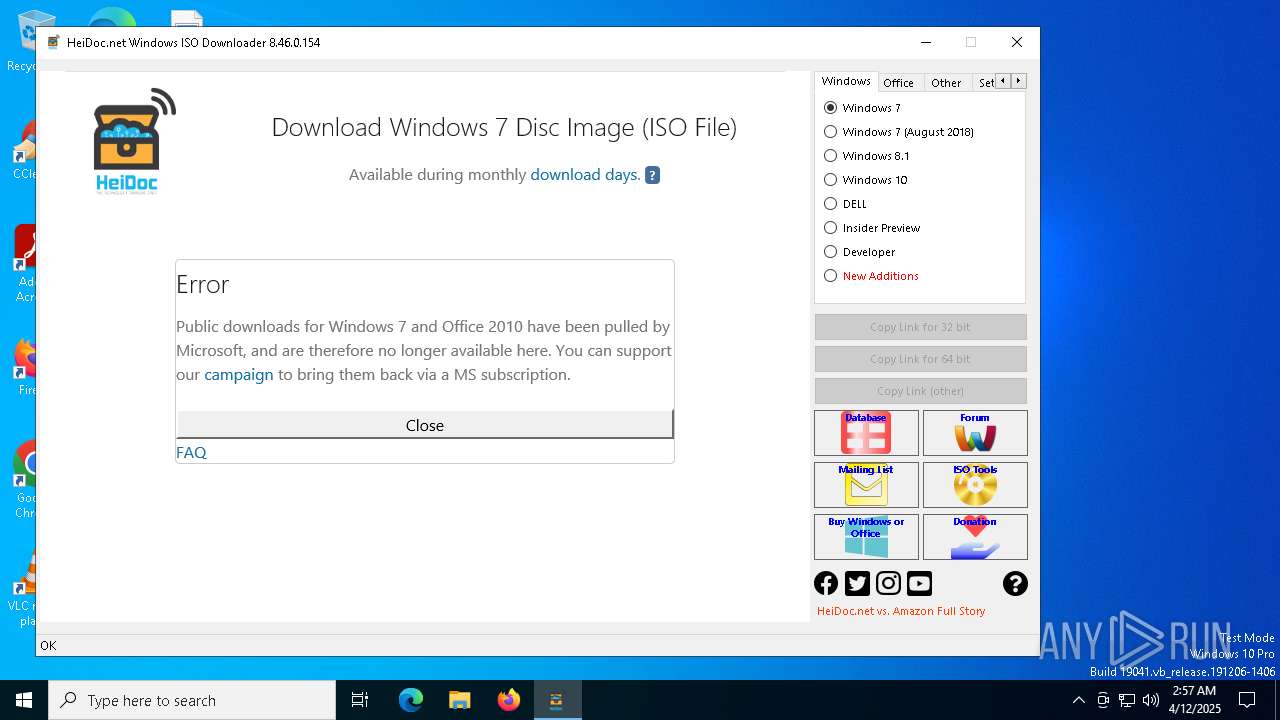
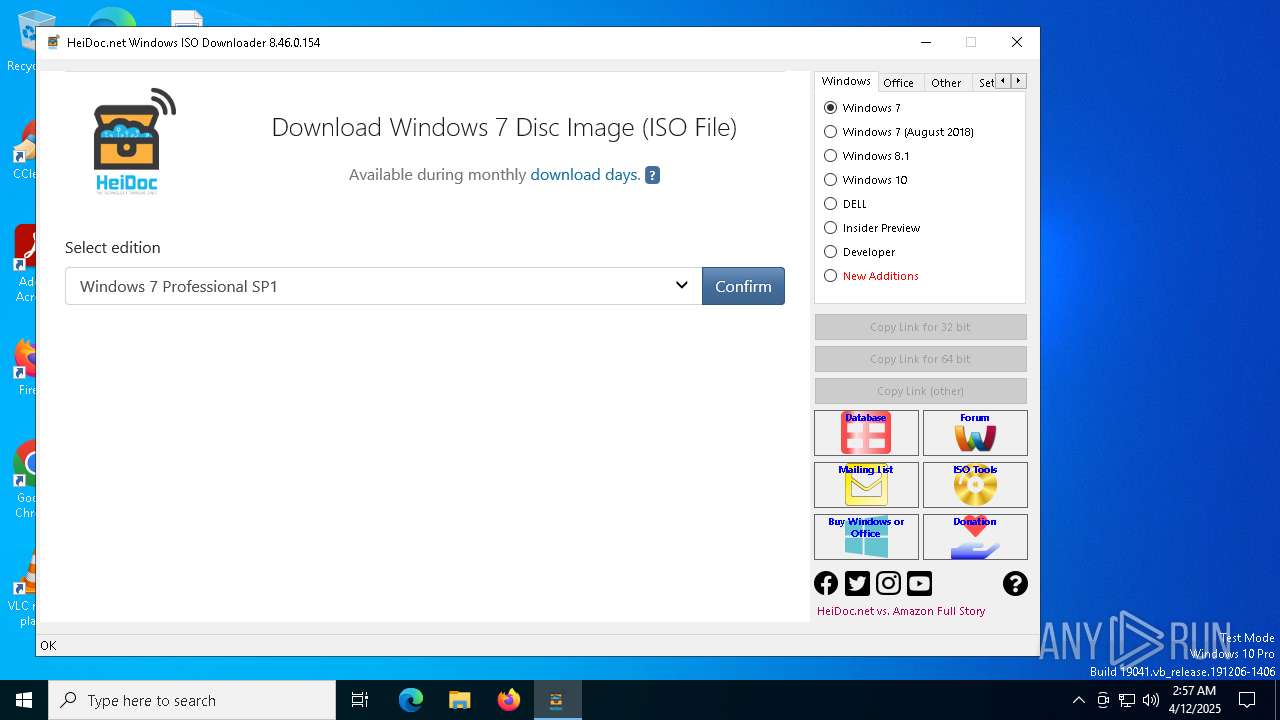
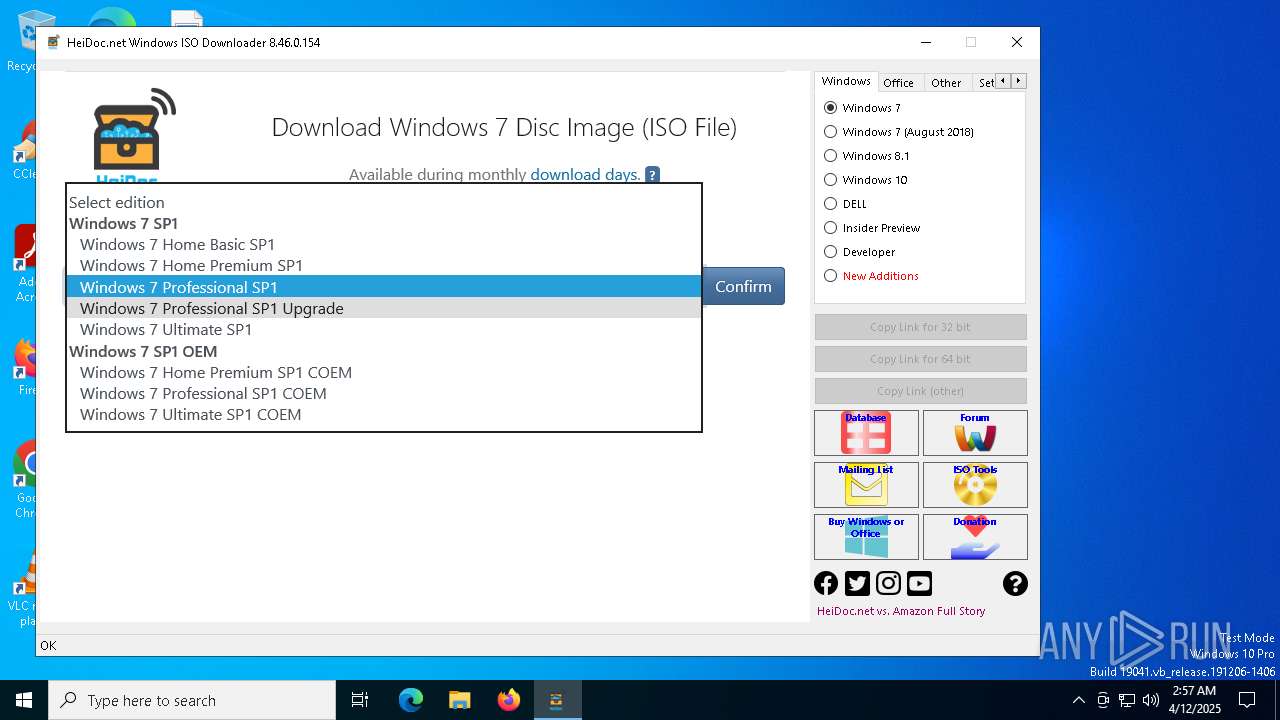
| File name: | Windows-ISO-Downloader.exe |
| Full analysis: | https://app.any.run/tasks/25ac49da-6aa9-410f-b68b-64a4920b252e |
| Verdict: | Malicious activity |
| Analysis date: | April 12, 2025, 02:56:28 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 42BE2387EA24923622219A33C504C091 |
| SHA1: | 1F4BA0EEFBF14AA351DEBE48FED9756C301FA866 |
| SHA256: | D9E52B0DBB5D3540016497C913E4186433C2ECD14E359EB841D5D93C8B021AEF |
| SSDEEP: | 98304:WI68IzIRIRIlgRnQmlGx0zcFLWoDy9G32dm/RUFVHB/mQJCyE:gXRnQm5yWoDy9GGOIlBew8 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- Windows-ISO-Downloader.exe (PID: 7476)
Reads security settings of Internet Explorer
- Windows-ISO-Downloader.exe (PID: 7476)
Reads Internet Explorer settings
- Windows-ISO-Downloader.exe (PID: 7476)
INFO
Checks proxy server information
- Windows-ISO-Downloader.exe (PID: 7476)
Reads the computer name
- Windows-ISO-Downloader.exe (PID: 7476)
Disables trace logs
- Windows-ISO-Downloader.exe (PID: 7476)
Create files in a temporary directory
- Windows-ISO-Downloader.exe (PID: 7476)
Checks supported languages
- Windows-ISO-Downloader.exe (PID: 7476)
Reads the software policy settings
- Windows-ISO-Downloader.exe (PID: 7476)
Reads the machine GUID from the registry
- Windows-ISO-Downloader.exe (PID: 7476)
Creates files or folders in the user directory
- Windows-ISO-Downloader.exe (PID: 7476)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:01:07 23:09:27+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 6998016 |
| InitializedDataSize: | 308736 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6ae7a2 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.46.0.154 |
| ProductVersionNumber: | 8.46.0.154 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | HeiDoc V.O.F. |
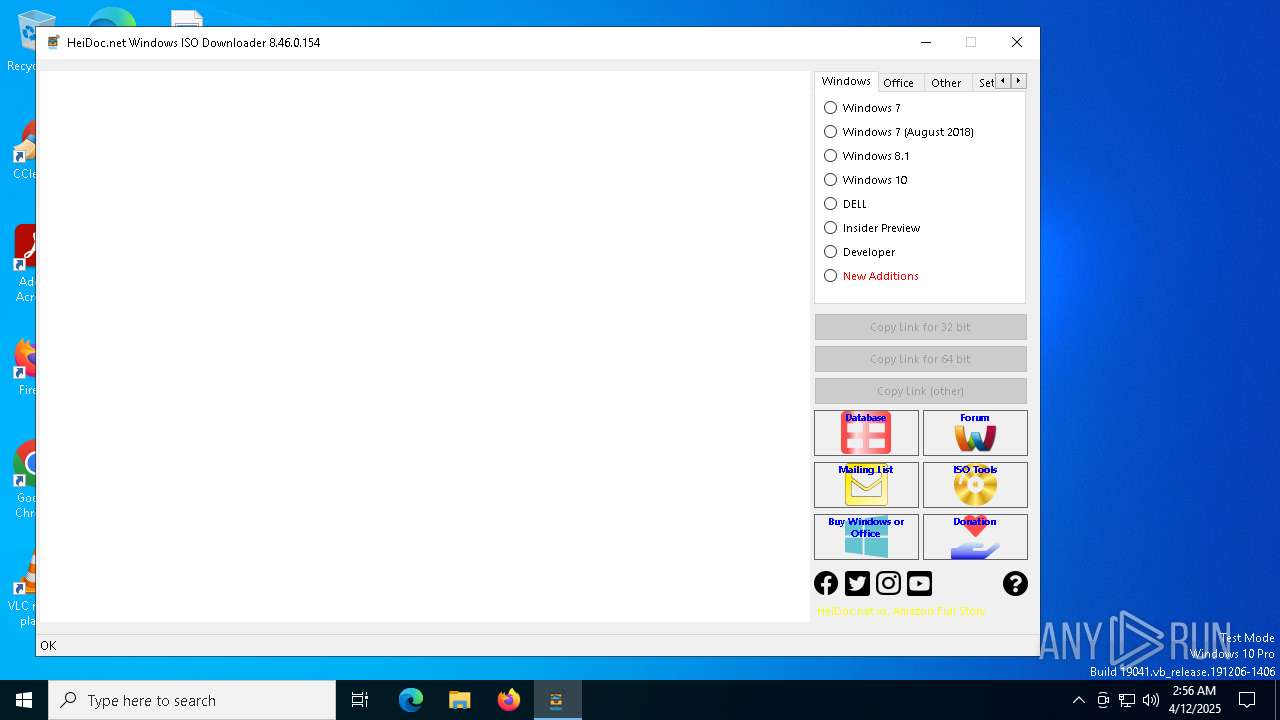
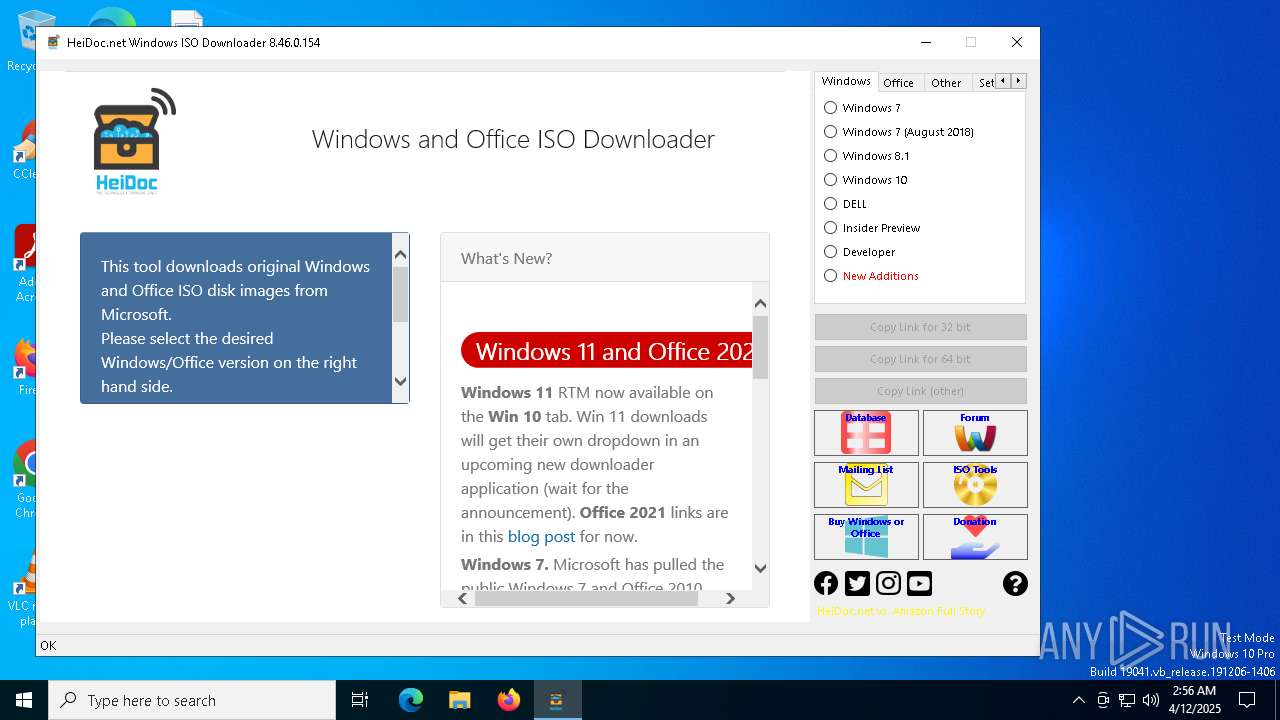
| FileDescription: | Windows ISO Downloader |
| FileVersion: | 8.46.0.0154 |
| InternalName: | Windows-ISO-Downloader.exe |
| LegalCopyright: | Copyright © 2016-2020 |
| LegalTrademarks: | - |
| OriginalFileName: | Windows-ISO-Downloader.exe |
| ProductName: | Windows ISO Downloader |
| ProductVersion: | 8.46.0.0154 |
| AssemblyVersion: | 8.46.0.154 |
Total processes
130
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7476 | "C:\Users\admin\AppData\Local\Temp\Windows-ISO-Downloader.exe" | C:\Users\admin\AppData\Local\Temp\Windows-ISO-Downloader.exe | explorer.exe | ||||||||||||
User: admin Company: HeiDoc V.O.F. Integrity Level: MEDIUM Description: Windows ISO Downloader Version: 8.46.0.0154 Modules
| |||||||||||||||
| 7580 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7612 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 069
Read events
3 042
Write events
27
Delete events
0
Modification events
| (PID) Process: | (7476) Windows-ISO-Downloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Windows-ISO-Downloader_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7476) Windows-ISO-Downloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Windows-ISO-Downloader_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7476) Windows-ISO-Downloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Windows-ISO-Downloader_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (7476) Windows-ISO-Downloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Windows-ISO-Downloader_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (7476) Windows-ISO-Downloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Windows-ISO-Downloader_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (7476) Windows-ISO-Downloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Windows-ISO-Downloader_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (7476) Windows-ISO-Downloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Windows-ISO-Downloader_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (7476) Windows-ISO-Downloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Windows-ISO-Downloader_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7476) Windows-ISO-Downloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Windows-ISO-Downloader_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7476) Windows-ISO-Downloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Windows-ISO-Downloader_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
0
Suspicious files
32
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7476 | Windows-ISO-Downloader.exe | C:\Users\admin\AppData\Local\Temp\570b93f8-dc9a-4fa6-87d8-74adff5e561c.js | binary | |
MD5:52B0A6C2004D753820BBC3E8469EC3B0 | SHA256:804CFE5038FB95F4AF2A648E436D33BFA1410B7D2F0B979335BD69B41198CB03 | |||
| 7476 | Windows-ISO-Downloader.exe | C:\Users\admin\AppData\Local\Temp\aa8dab02-62e9-4e0e-8289-400bedce47ca.css | text | |
MD5:3CD25829FBA084F9F6B743E8E07DF5CB | SHA256:1FD0CA240E45867CB52ED50910B92A6A3273E70B723F47F5F4BE9F0FDFB08756 | |||
| 7476 | Windows-ISO-Downloader.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:4A90329071AE30B759D279CCA342B0A6 | SHA256:4F544379EDA8E2653F71472AB968AEFD6B5D1F4B3CE28A5EDB14196184ED3B60 | |||
| 7476 | Windows-ISO-Downloader.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9E62DD75009A293E0AF9565AE544F23E_C994102821FFEDF565E8054DF04D5622 | binary | |
MD5:DC08A5AD0D32762310B30CF5F8FB098B | SHA256:A251334477648A8377E0A0CCC312FAAF9D698A81719E8B6D31A01B63C1A1DF20 | |||
| 7476 | Windows-ISO-Downloader.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C60C0C29522E01E6A22BD2717F20782E_D335E3B498EC872279EE731666314833 | binary | |
MD5:C2A8C69E8114F05E3D4F51C2E686CD36 | SHA256:E692C5ED9FEBA482B7FD3970C20222909BB3278BAA2F0983A5DC6FFB94CD6720 | |||
| 7476 | Windows-ISO-Downloader.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:1FBB37F79B317A9A248E7C4CE4F5BAC5 | SHA256:9BF639C595FE335B6F694EE35990BEFD2123F5E07FD1973FF619E3FC88F5F49F | |||
| 7476 | Windows-ISO-Downloader.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C60C0C29522E01E6A22BD2717F20782E_D335E3B498EC872279EE731666314833 | binary | |
MD5:D0E17F8E3C1418051E5D8D7FBABD0610 | SHA256:32B7F64AD86BAEA4B24AF865B63D8E8B1611277E2EDF572156D001B3BB1E40CC | |||
| 7476 | Windows-ISO-Downloader.exe | C:\Users\admin\AppData\Local\Temp\1450a0bf-2128-4576-936d-ac8862d29a60.css | text | |
MD5:C7E730F5C5B1884ABFDFBDCC69C1B4BA | SHA256:65A2D5BD6ADCFA48BE0D3C1DE2780421CBA0E394EB1B8F564880715512B6E707 | |||
| 7476 | Windows-ISO-Downloader.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7B5FC60CCA5D8CF767A7572C65728CD6_99D27CBA0D4B68C894F658C49157FD99 | binary | |
MD5:216AE28D2FEB1087605529FF592366AF | SHA256:EEFD501A21FC793CA61E3AB6E3DA5D17041C6A12D531D0F5CB255722EEDAFBE9 | |||
| 7476 | Windows-ISO-Downloader.exe | C:\Users\admin\AppData\Local\Temp\c66f0b72-2c48-4e5f-a358-84ee7436976e.js | binary | |
MD5:8474C4352DB320C07C6328BF16BCE6D3 | SHA256:E336E656B132BA15B9365DB9962B3B5ADFA0FA5EC2E98D8F4147DDEBA7AC0D88 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
35
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7476 | Windows-ISO-Downloader.exe | GET | 200 | 142.250.185.163:80 | http://o.pki.goog/we2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEQC9ZcgYQ%2FurORDkqLZcs5MY | unknown | — | — | whitelisted |
7476 | Windows-ISO-Downloader.exe | GET | 200 | 142.250.185.163:80 | http://o.pki.goog/we2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEQDXdO2cNvmNkhC12rwN5QK6 | unknown | — | — | whitelisted |
7476 | Windows-ISO-Downloader.exe | GET | 200 | 142.250.185.163:80 | http://o.pki.goog/we2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEE7K8N1Fqf%2FlEqTsikyBOPc%3D | unknown | — | — | whitelisted |
7476 | Windows-ISO-Downloader.exe | GET | 200 | 142.250.185.163:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
7476 | Windows-ISO-Downloader.exe | GET | 200 | 142.250.185.163:80 | http://o.pki.goog/we2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEHGvPPlOXde9CQBZ60wQP4Y%3D | unknown | — | — | whitelisted |
7476 | Windows-ISO-Downloader.exe | GET | 200 | 142.250.185.163:80 | http://o.pki.goog/we2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEQCaWeNpIFSBzAkvnnFNzwtC | unknown | — | — | whitelisted |
7476 | Windows-ISO-Downloader.exe | GET | 200 | 142.250.185.163:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
536 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7476 | Windows-ISO-Downloader.exe | 104.168.147.90:443 | www.heidoc.net | HOSTWINDS | US | whitelisted |
6544 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7476 | Windows-ISO-Downloader.exe | 142.250.184.234:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.heidoc.net |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
aa.online-metrix.net |
| whitelisted |
c.bing.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |