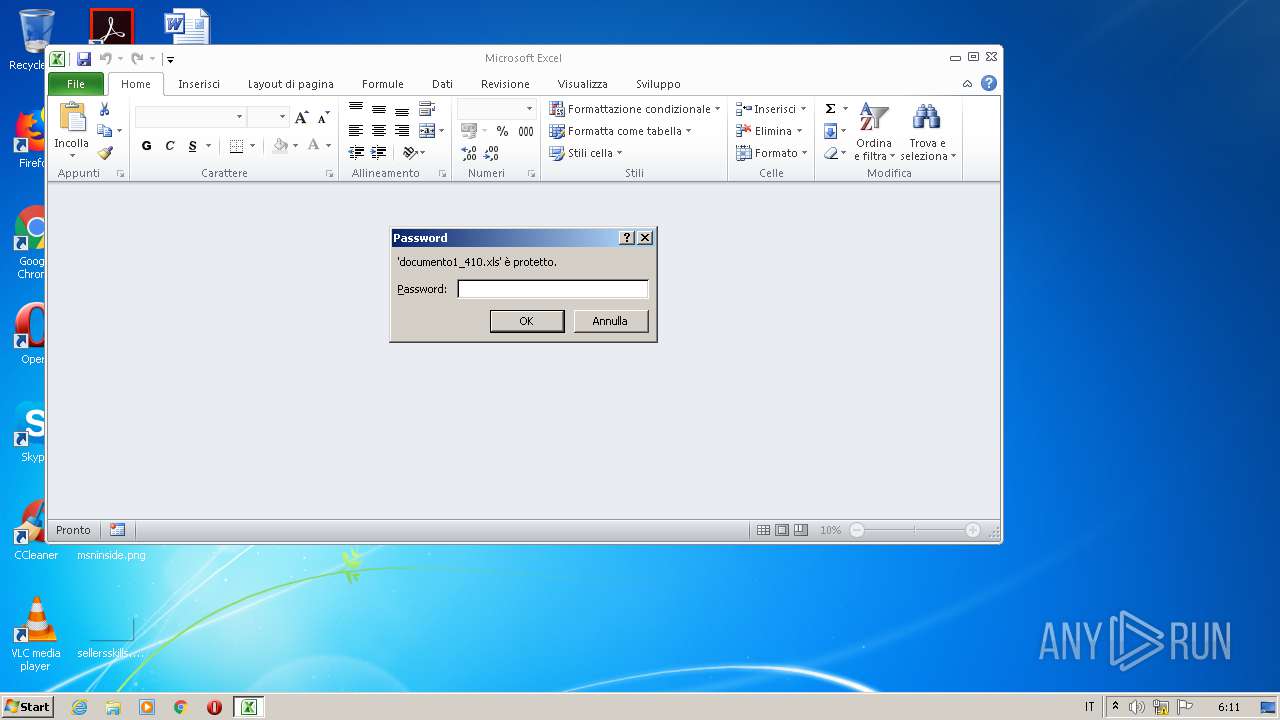
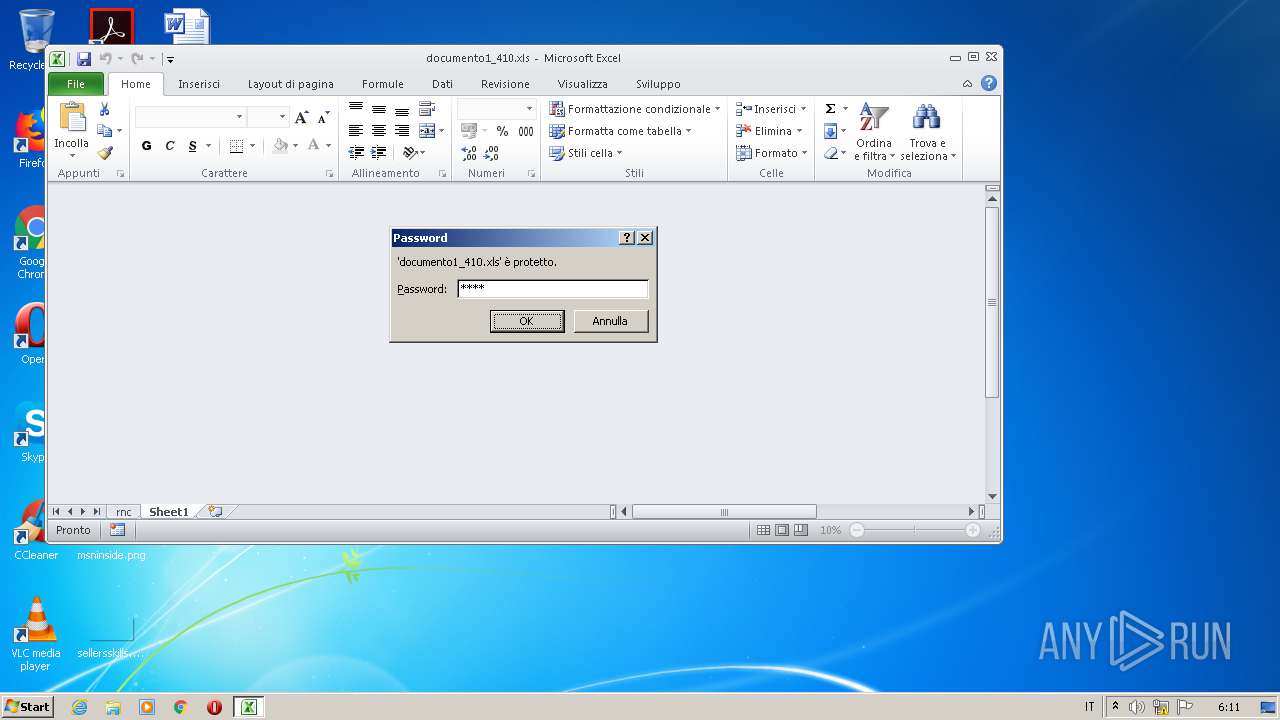
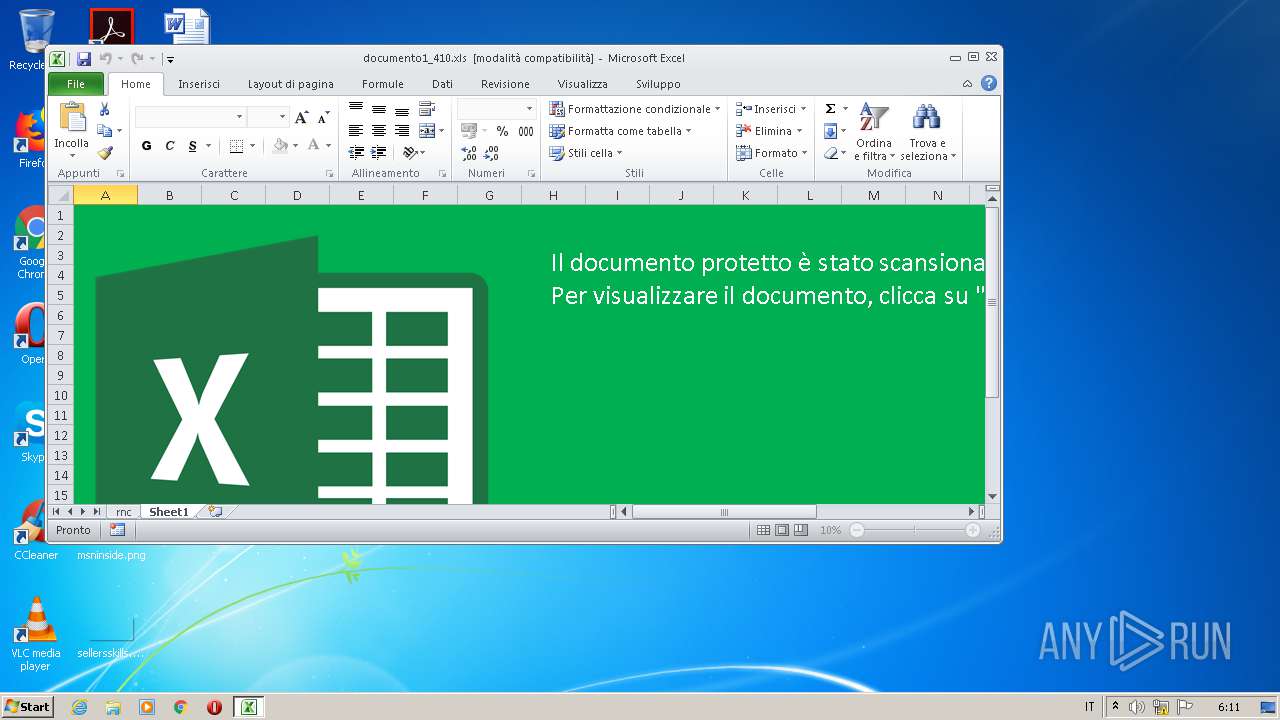
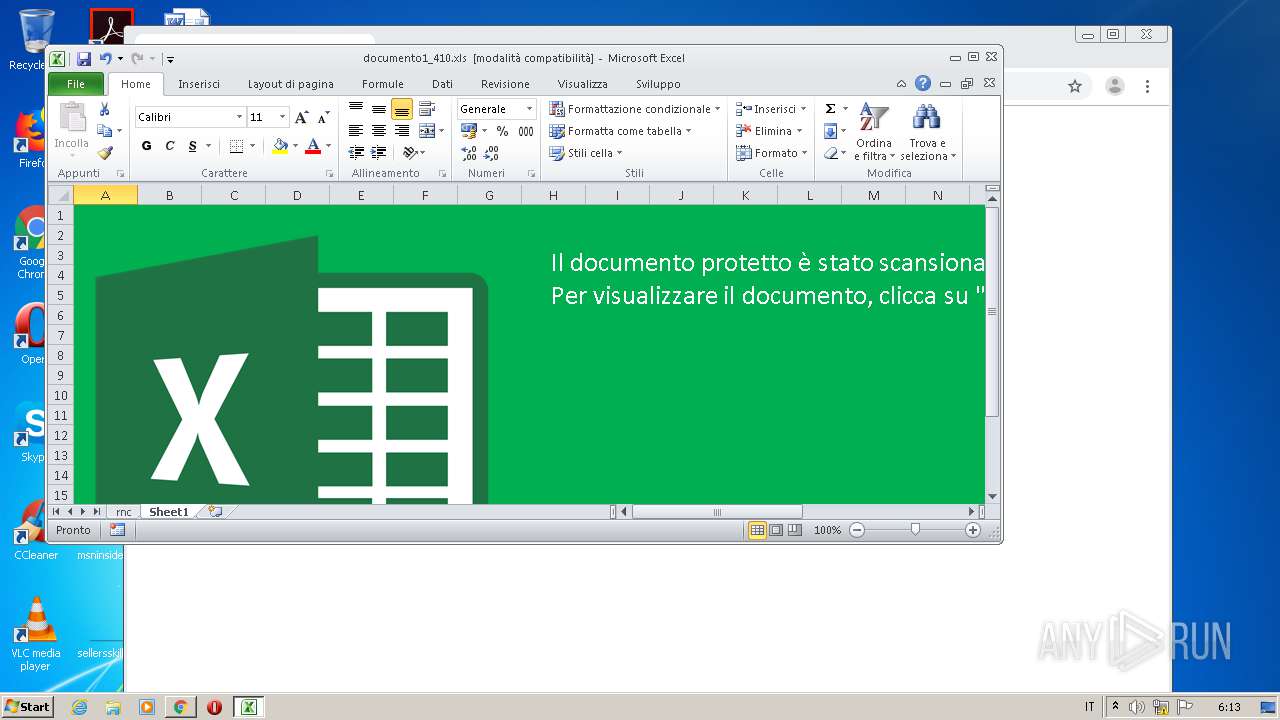
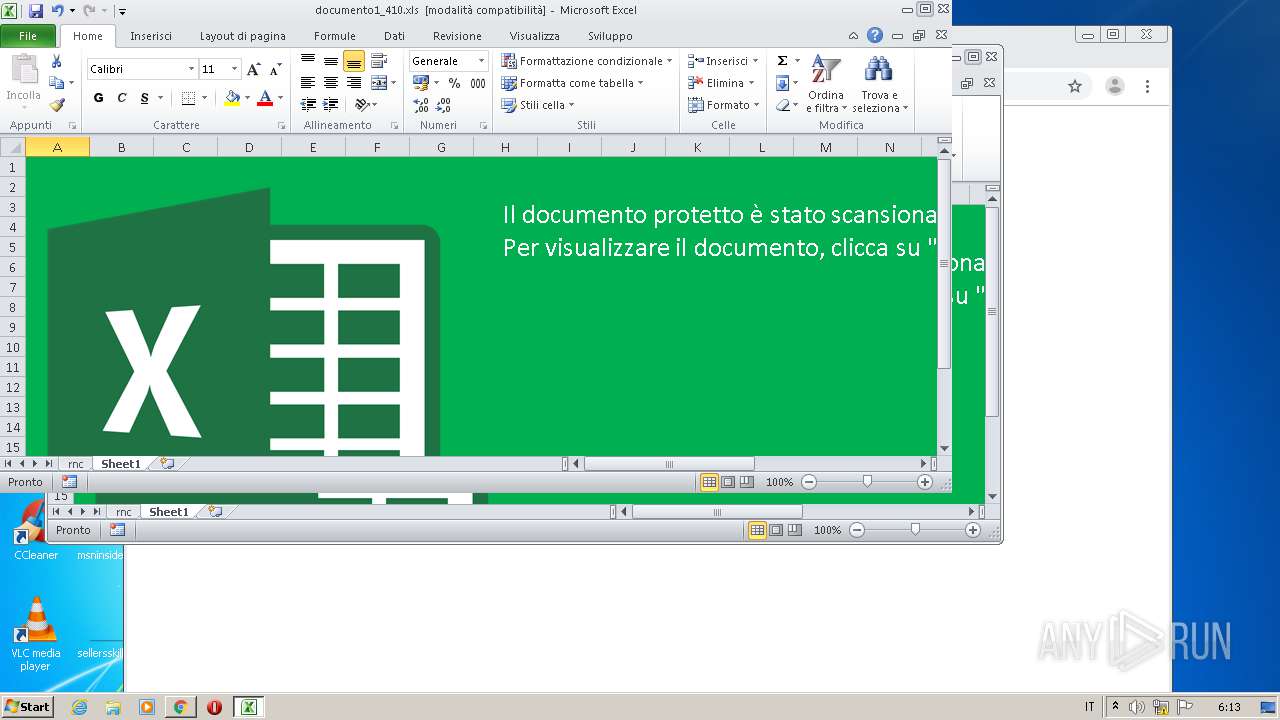
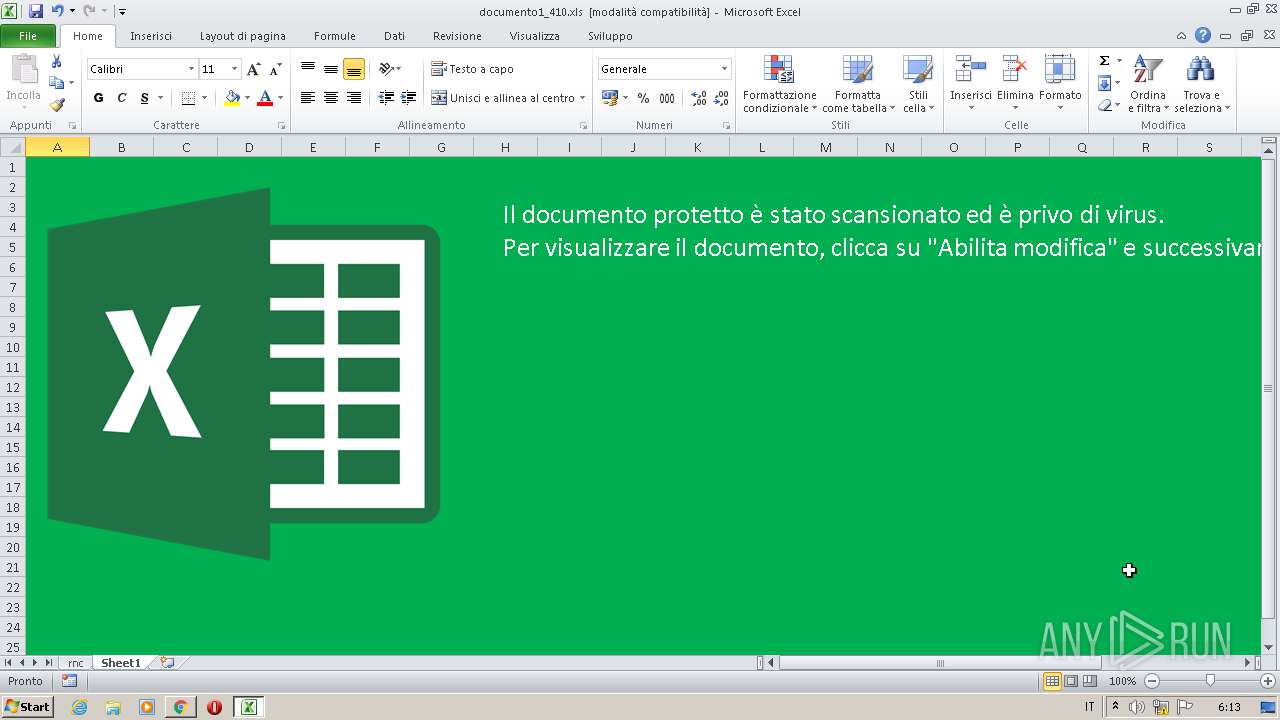
| File name: | documento1_410.xls |
| Full analysis: | https://app.any.run/tasks/e9183743-ba3c-4e8b-bc36-006cf50c3028 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2020, 04:10:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Author: dppFJMEcrkUCFZCGUe, Last Saved By: administrator, Name of Creating Application: Microsoft Excel, Create Time/Date: Tue Oct 20 00:28:19 2020, Last Saved Time/Date: Tue Oct 20 00:48:19 2020, Security: 1 |
| MD5: | E2739B11FA9EF4DDEE5F9AB41B1A56FF |
| SHA1: | A10B9A7D05F7E4F04983AED34BA3E52AAC0A8642 |
| SHA256: | D9E458B03EAA69BB9CC9A3950D38C6CC78C4AAC8DF53E0048C7D562E88B61C5F |
| SSDEEP: | 6144:uZKOXZdpjpVBrRWJ+Vl0T2q3T9UnoVEsOUqjLxjn:JOXZHpbrsJS03RUX6G |
MALICIOUS
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 2432)
SUSPICIOUS
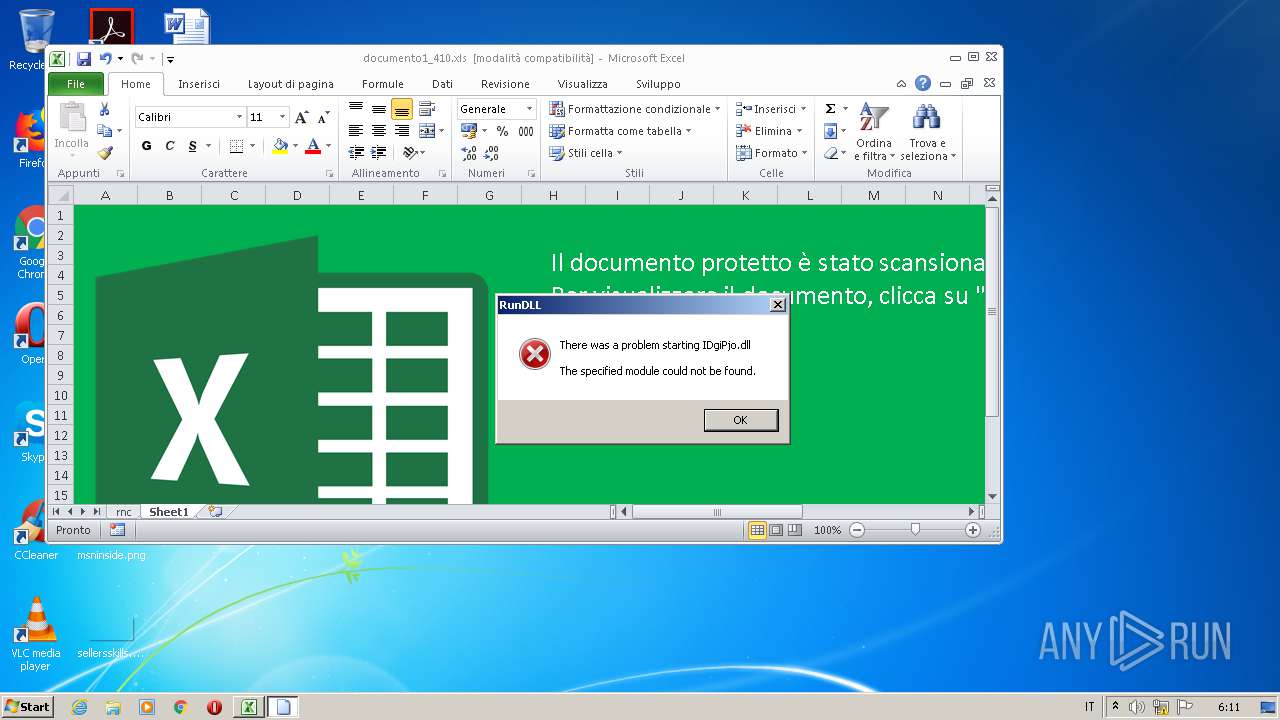
Uses RUNDLL32.EXE to load library
- EXCEL.EXE (PID: 2432)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2432)
Reads the hosts file
- chrome.exe (PID: 3840)
- chrome.exe (PID: 3696)
Reads Internet Cache Settings
- EXCEL.EXE (PID: 2432)
Manual execution by user
- chrome.exe (PID: 3840)
Creates files in the user directory
- EXCEL.EXE (PID: 2432)
Dropped object may contain TOR URL's
- chrome.exe (PID: 888)
Application launched itself
- chrome.exe (PID: 3840)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (78.9) |
|---|
EXIF
FlashPix
| Author: | dppFJMEcrkUCFZCGUe |
|---|---|
| LastModifiedBy: | administrator |
| Software: | Microsoft Excel |
| CreateDate: | 2020:10:19 23:28:19 |
| ModifyDate: | 2020:10:19 23:48:19 |
| Security: | Password protected |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
Total processes
73
Monitored processes
31
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=988,11044182080854413661,4596998670317970410,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15266733404786782799 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2168 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 444 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,11044182080854413661,4596998670317970410,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=3390891938227767839 --mojo-platform-channel-handle=2724 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 784 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,11044182080854413661,4596998670317970410,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12706139113059153015 --mojo-platform-channel-handle=2420 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 888 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,11044182080854413661,4596998670317970410,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=9684444065116908955 --mojo-platform-channel-handle=920 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1232 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,11044182080854413661,4596998670317970410,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=6333725635716713657 --mojo-platform-channel-handle=2664 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,11044182080854413661,4596998670317970410,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=10292312780266095149 --mojo-platform-channel-handle=1016 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1452 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,11044182080854413661,4596998670317970410,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=16355636525508618943 --mojo-platform-channel-handle=2548 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1500 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=988,11044182080854413661,4596998670317970410,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5344841069107381620 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2484 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1504 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,11044182080854413661,4596998670317970410,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=9745204540020078955 --mojo-platform-channel-handle=3356 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2088 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=988,11044182080854413661,4596998670317970410,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=9188600622393949180 --mojo-platform-channel-handle=3460 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 260
Read events
1 111
Write events
134
Delete events
15
Modification events
| (PID) Process: | (2432) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | 8(; |
Value: 38283B0080090000010000000000000000000000 | |||
| (PID) Process: | (2432) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2432) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2432) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2432) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2432) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2432) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2432) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2432) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2432) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
23
Text files
116
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2432 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR4088.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3840 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5F8E6395-F00.pma | — | |
MD5:— | SHA256:— | |||
| 3840 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3840 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\9de264cb-57cf-467a-a131-04d0e53affc8.tmp | — | |
MD5:— | SHA256:— | |||
| 3840 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2432 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 2432 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\documento1_410.xls.LNK | lnk | |
MD5:— | SHA256:— | |||
| 3840 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3840 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF2e2ed0.TMP | text | |
MD5:— | SHA256:— | |||
| 3840 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
57
TCP/UDP connections
25
DNS requests
24
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 82.85.147.14:80 | http://r3---sn-upnj5appu5-j5bl.gvt1.com/edgedl/release2/chrome_component/AM3bph0C5lY0rfJW1FrQdk4_86.247.200/AMawGUU2GQzt55aFY9GRU-w?cms_redirect=yes&mh=ot&mip=94.32.66.48&mm=28&mn=sn-upnj5appu5-j5bl&ms=nvh&mt=1603167112&mv=u&mvi=3&pcm2cms=yes&pl=20&shardbypass=yes | IT | — | — | whitelisted |
— | — | HEAD | 200 | 216.58.209.48:80 | http://storage.googleapis.com/update-delta/khaoiebndkojlmppeemjhbpbandiljpe/43/42/e0b8b1fb7c27acac43c236b9f6b029b07f2a3b661b5d8eed22848180aaf4f04e.crxd | US | — | — | whitelisted |
— | — | HEAD | 302 | 216.58.208.174:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/RICrvMN8bkQRllgID8xWJw_6187/H6ZPXmz_Yx1gzS8iWmCgCQ | US | — | — | whitelisted |
— | — | HEAD | 200 | 82.85.147.13:80 | http://r2---sn-upnj5appu5-j5bl.gvt1.com/edgedl/release2/chrome_component/RICrvMN8bkQRllgID8xWJw_6187/H6ZPXmz_Yx1gzS8iWmCgCQ?cms_redirect=yes&mh=K8&mip=94.32.66.48&mm=28&mn=sn-upnj5appu5-j5bl&ms=nvh&mt=1603167112&mv=u&mvi=2&pl=20&shardbypass=yes | IT | — | — | whitelisted |
— | — | GET | 302 | 216.58.208.174:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/RICrvMN8bkQRllgID8xWJw_6187/H6ZPXmz_Yx1gzS8iWmCgCQ | US | html | 481 b | whitelisted |
— | — | GET | 206 | 82.85.147.13:80 | http://r2---sn-upnj5appu5-j5bl.gvt1.com/edgedl/release2/chrome_component/RICrvMN8bkQRllgID8xWJw_6187/H6ZPXmz_Yx1gzS8iWmCgCQ?cms_redirect=yes&mh=K8&mip=94.32.66.48&mm=28&mn=sn-upnj5appu5-j5bl&ms=nvh&mt=1603167112&mv=u&mvi=2&pl=20&shardbypass=yes | IT | binary | 6.91 Kb | whitelisted |
— | — | HEAD | 200 | 216.58.209.48:80 | http://storage.googleapis.com/update-delta/gcmjkmgdlgnkkcocmoeiminaijmmjnii/9.17.0/9.16.0/092573746769772bd5e3208f6dcc3c31a029e78c61989771a8cefa8e4d829c55.crxd | US | binary | 4.33 Kb | whitelisted |
— | — | GET | 206 | 216.58.209.48:80 | http://storage.googleapis.com/update-delta/gcmjkmgdlgnkkcocmoeiminaijmmjnii/9.17.0/9.16.0/092573746769772bd5e3208f6dcc3c31a029e78c61989771a8cefa8e4d829c55.crxd | US | binary | 5.99 Kb | whitelisted |
— | — | GET | 206 | 216.58.209.48:80 | http://storage.googleapis.com/update-delta/gcmjkmgdlgnkkcocmoeiminaijmmjnii/9.17.0/9.16.0/092573746769772bd5e3208f6dcc3c31a029e78c61989771a8cefa8e4d829c55.crxd | US | binary | 9.61 Kb | whitelisted |
— | — | GET | 206 | 216.58.209.48:80 | http://storage.googleapis.com/update-delta/gcmjkmgdlgnkkcocmoeiminaijmmjnii/9.17.0/9.16.0/092573746769772bd5e3208f6dcc3c31a029e78c61989771a8cefa8e4d829c55.crxd | US | binary | 3.35 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
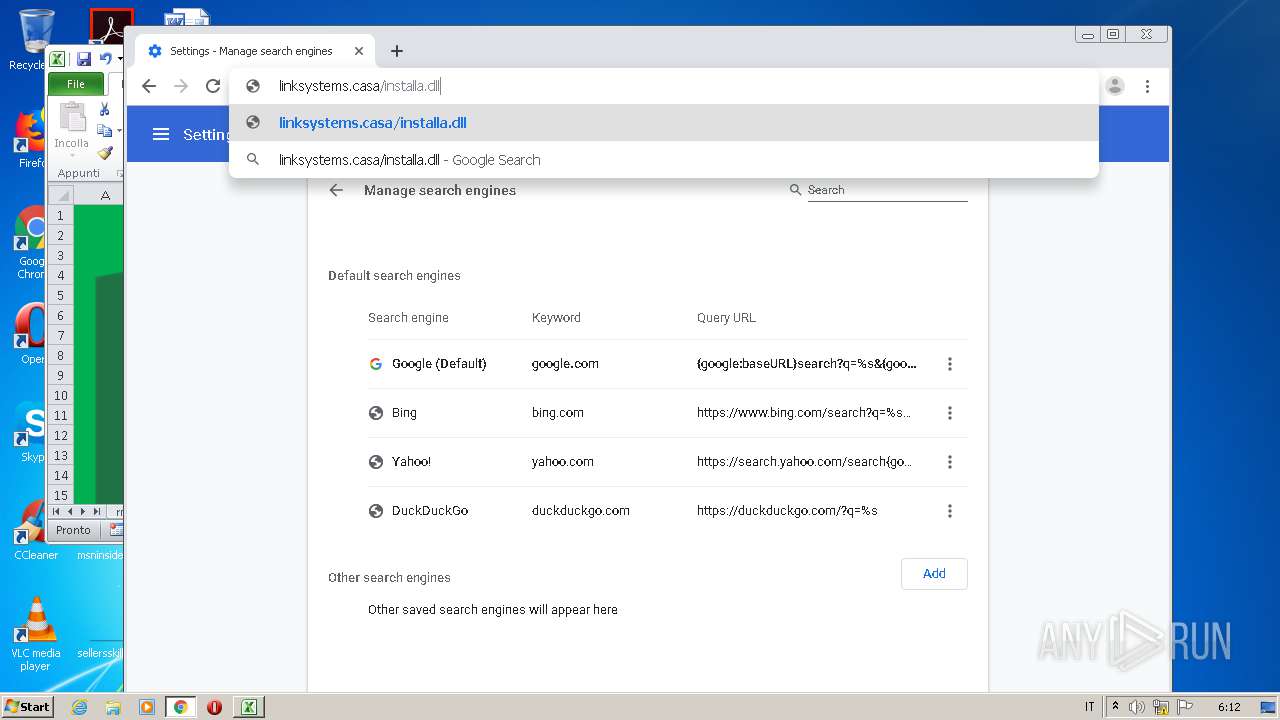
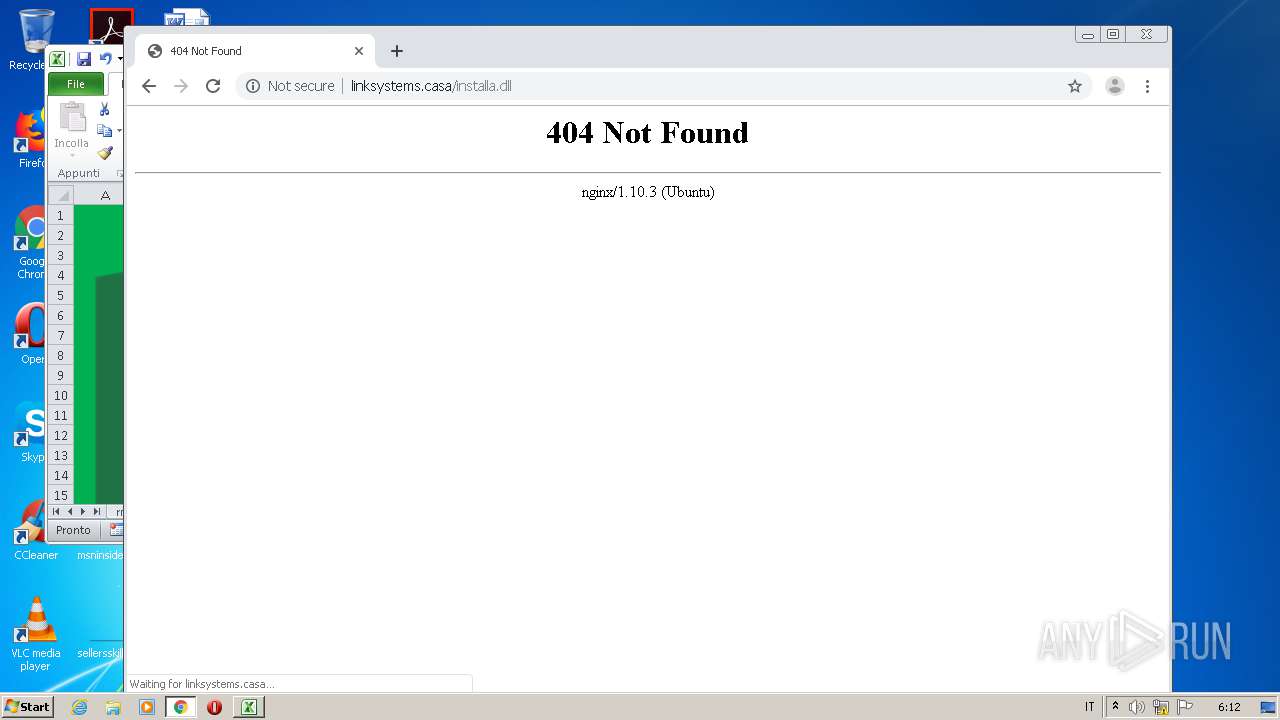
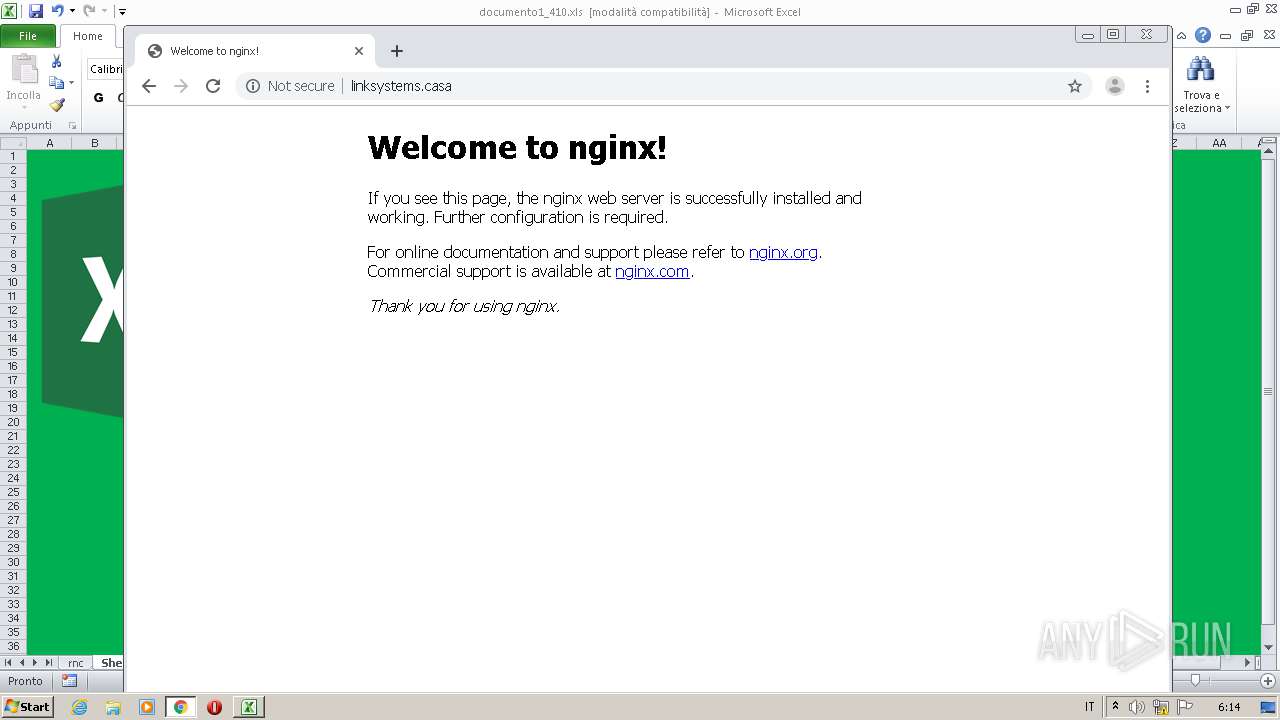
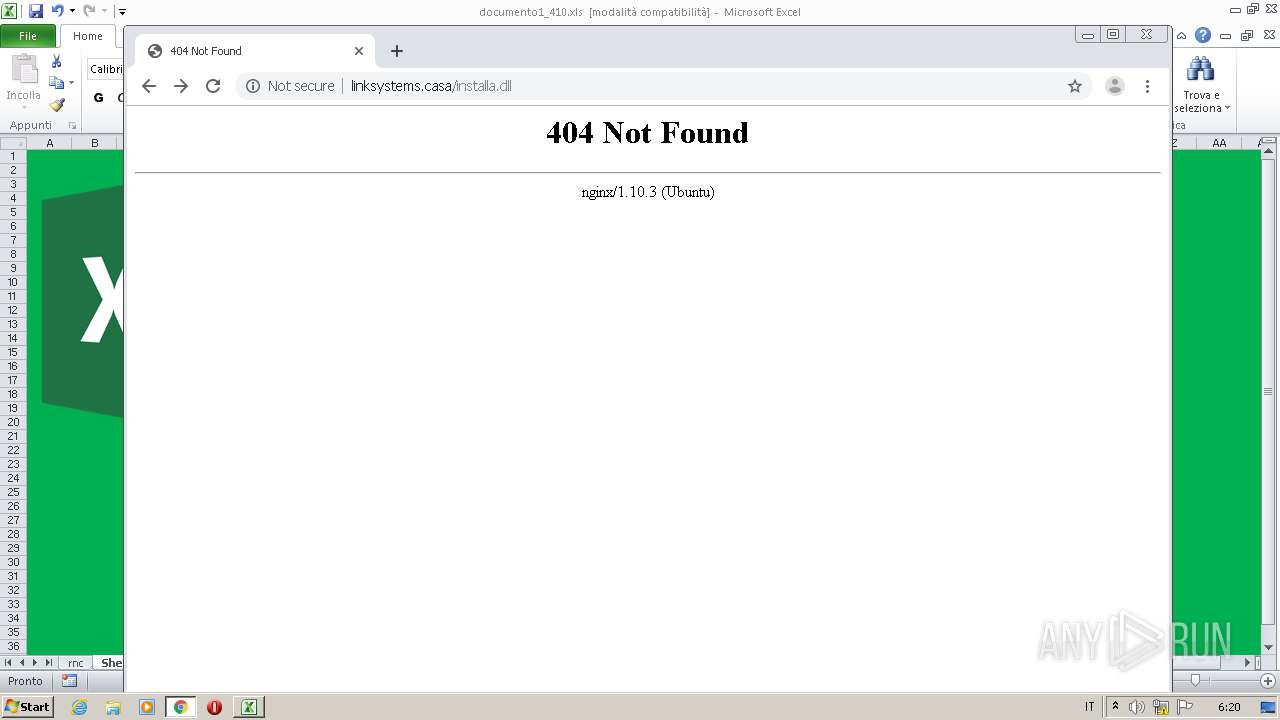
2432 | EXCEL.EXE | 109.248.203.236:80 | linksystems.casa | Business Consulting LLC | RU | suspicious |
3696 | chrome.exe | 216.58.205.67:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3696 | chrome.exe | 216.58.206.45:443 | accounts.google.com | Google Inc. | US | suspicious |
3696 | chrome.exe | 216.58.198.36:443 | www.google.com | Google Inc. | US | whitelisted |
3696 | chrome.exe | 216.58.198.10:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3696 | chrome.exe | 216.58.206.67:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3696 | chrome.exe | 216.58.205.78:443 | apis.google.com | Google Inc. | US | whitelisted |
3696 | chrome.exe | 216.58.198.14:443 | ogs.google.com | Google Inc. | US | whitelisted |
3696 | chrome.exe | 216.58.209.35:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3696 | chrome.exe | 109.248.203.236:80 | linksystems.casa | Business Consulting LLC | RU | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
linksystems.casa |
| suspicious |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com |
| whitelisted |
clients2.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3696 | chrome.exe | Potentially Bad Traffic | ET INFO Unconfigured nginx Access |