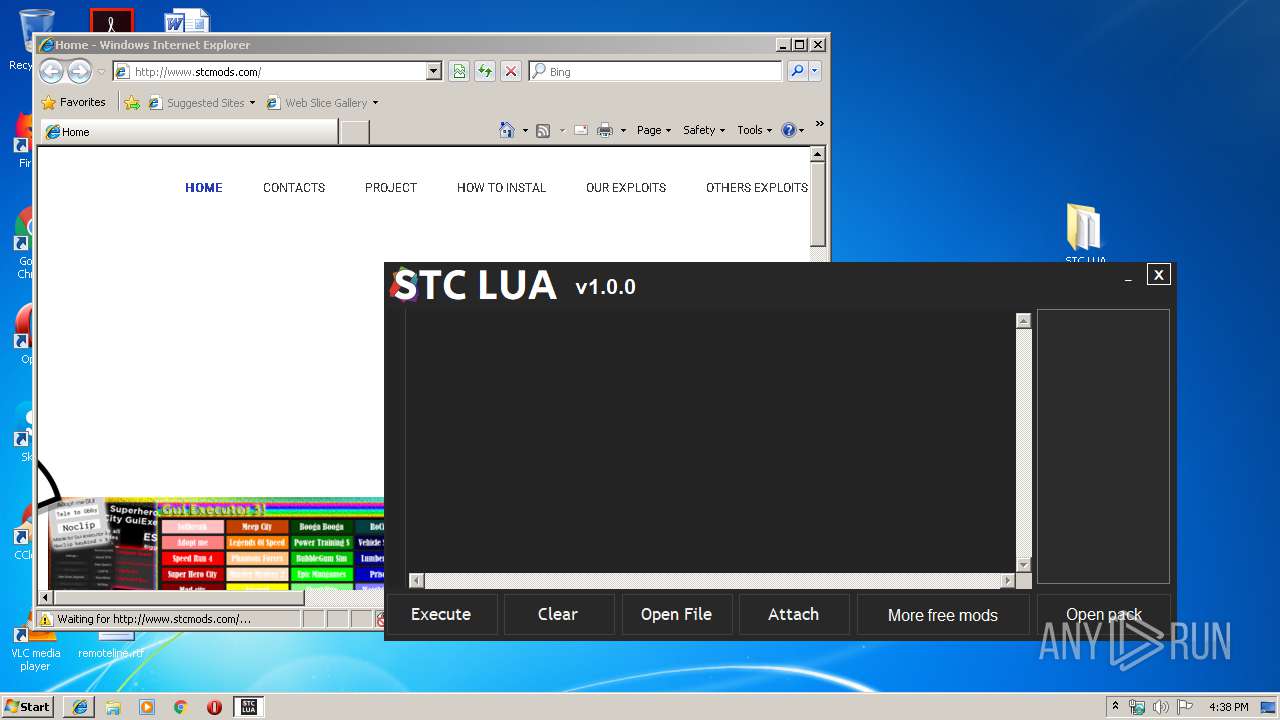
| File name: | STC LUA v1.0.0.rar |
| Full analysis: | https://app.any.run/tasks/80f48e4c-9b28-445c-ba1b-a9cf4424d496 |
| Verdict: | Suspicious activity |
| Analysis date: | September 29, 2019, 15:37:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | F311663289CC5A1A65C56E28FD8E9AB7 |
| SHA1: | A3065DE8652CE333DB122B10612C98D9AA2D611F |
| SHA256: | D9CF4E6E2769C7361375214BA2E230438098A4263BBE21E300250BA5153FFDAC |
| SSDEEP: | 6144:+YS4eLs6AMbGkCJQ+4fv1CfDbsmlDFh2LdG/:+YS4HHIzC6bftCfD4MDFoLdk |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 596)
SUSPICIOUS
Executable content was dropped or overwritten
- STC LUA v1.0.0.exe (PID: 2348)
Starts Internet Explorer
- STC LUA v1.0.0.exe (PID: 2348)
Reads Internet Cache Settings
- STC LUA v1.0.0.exe (PID: 2348)
INFO
Manual execution by user
- STC LUA v1.0.0.exe (PID: 2348)
Changes internet zones settings
- iexplore.exe (PID: 2564)
Reads internet explorer settings
- iexplore.exe (PID: 3256)
Creates files in the user directory
- iexplore.exe (PID: 3256)
Reads Internet Cache Settings
- iexplore.exe (PID: 3256)
Reads settings of System Certificates
- iexplore.exe (PID: 3256)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 527 |
|---|---|
| UncompressedSize: | 805 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2019:04:10 18:57:13 |
| PackingMethod: | Normal |
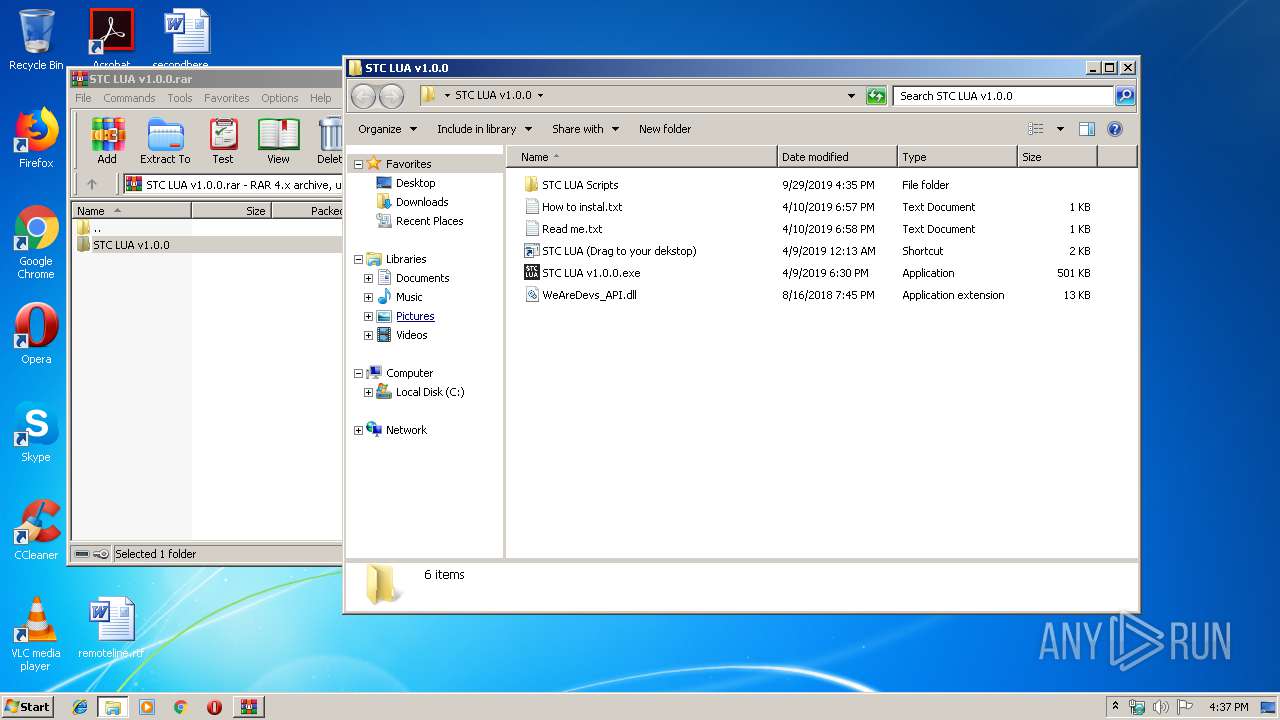
| ArchivedFileName: | STC LUA v1.0.0\How to instal.txt |
Total processes
38
Monitored processes
5
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 596 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
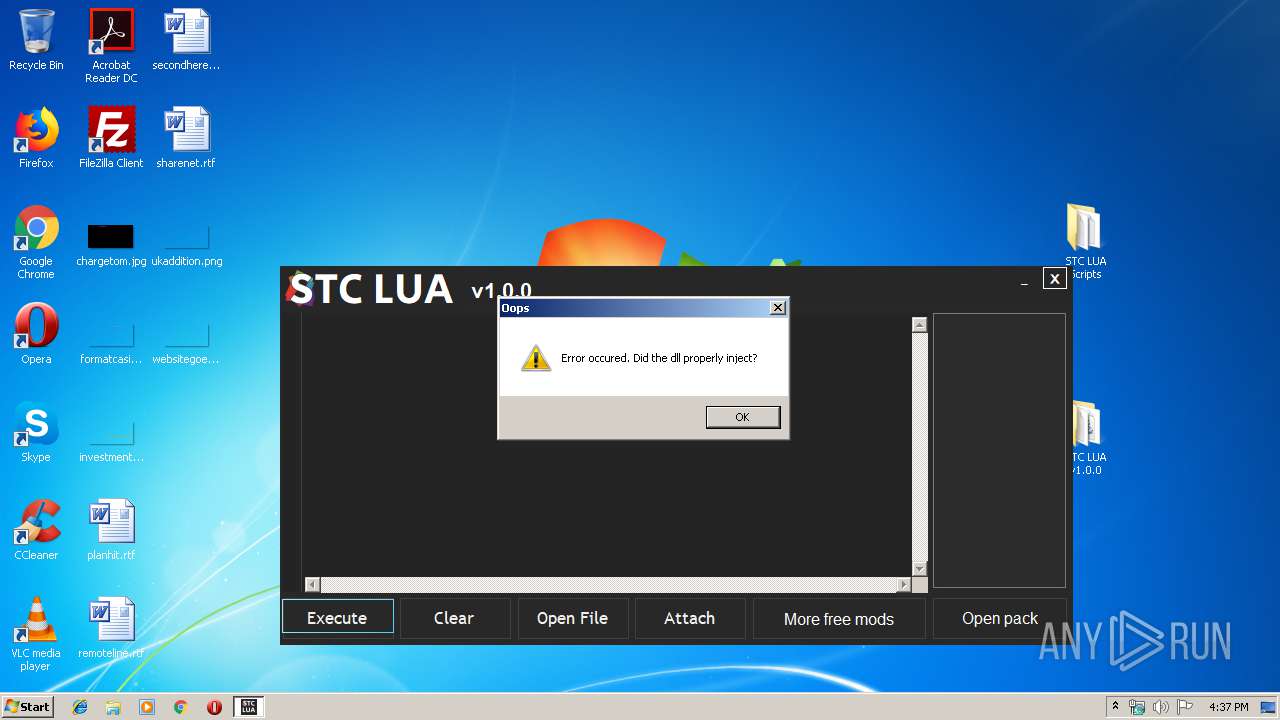
| 2348 | "C:\Users\admin\Desktop\STC LUA v1.0.0\STC LUA v1.0.0.exe" | C:\Users\admin\Desktop\STC LUA v1.0.0\STC LUA v1.0.0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: MadBreak Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2564 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | STC LUA v1.0.0.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2876 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\STC LUA v1.0.0.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3256 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2564 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 841
Read events
1 698
Write events
140
Delete events
3
Modification events
| (PID) Process: | (2876) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2876) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2876) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2876) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\STC LUA v1.0.0.rar | |||
| (PID) Process: | (2876) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2876) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2876) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2876) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (596) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (596) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
1
Suspicious files
1
Text files
50
Unknown types
29
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2876 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2876.43932\STC LUA v1.0.0\STC LUA Scripts\Unjailbreak GUI.txt | — | |
MD5:— | SHA256:— | |||
| 2876 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2876.44390\STC LUA v1.0.0\How to instal.txt | — | |
MD5:— | SHA256:— | |||
| 2876 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2876.44390\STC LUA v1.0.0\Read me.txt | — | |
MD5:— | SHA256:— | |||
| 2876 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2876.44390\STC LUA v1.0.0\STC LUA (Drag to your dekstop).lnk | — | |
MD5:— | SHA256:— | |||
| 2876 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2876.44390\STC LUA v1.0.0\STC LUA Scripts\Unjailbreak GUI.txt | — | |
MD5:— | SHA256:— | |||
| 2876 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2876.44390\STC LUA v1.0.0\STC LUA v1.0.0.exe | — | |
MD5:— | SHA256:— | |||
| 2876 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2876.44390\STC LUA v1.0.0\WeAreDevs_API.dll | — | |
MD5:— | SHA256:— | |||
| 2564 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2564 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3256 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\AEHCJ8R2\stcmods_com[1].txt | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
45
DNS requests
11
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3256 | iexplore.exe | GET | 200 | 145.14.145.69:80 | http://www.stcmods.com/css/1.css?ts=1566935947 | US | text | 1.92 Kb | shared |
3256 | iexplore.exe | GET | 200 | 145.14.145.69:80 | http://www.stcmods.com/css/common.css?ts=1566935947 | US | text | 1.73 Kb | shared |
3256 | iexplore.exe | GET | 200 | 145.14.145.69:80 | http://www.stcmods.com/gallery_gen/653cc09301108ef4d87417252416c4f2.jpg | US | image | 73.1 Kb | shared |
3256 | iexplore.exe | GET | 200 | 145.14.145.69:80 | http://www.stcmods.com/ | US | html | 2.71 Kb | shared |
3256 | iexplore.exe | GET | 200 | 172.217.23.130:80 | http://pagead2.googlesyndication.com/pagead/js/adsbygoogle.js | US | text | 35.3 Kb | whitelisted |
3256 | iexplore.exe | GET | 301 | 145.14.145.33:80 | http://stcmods.com/ | US | html | 231 b | shared |
2564 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
3256 | iexplore.exe | GET | 200 | 145.14.145.69:80 | http://www.stcmods.com/css/bootstrap.min.css | US | text | 24.1 Kb | shared |
3256 | iexplore.exe | GET | 200 | 145.14.145.69:80 | http://www.stcmods.com/fonts/glyphicons-halflings-regular.eot? | US | eot | 19.6 Kb | shared |
3256 | iexplore.exe | GET | 200 | 145.14.145.69:80 | http://www.stcmods.com/js/bootstrap.min.js | US | text | 11.4 Kb | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2348 | STC LUA v1.0.0.exe | 104.31.255.5:443 | pastebin.com | Cloudflare Inc | US | malicious |
2348 | STC LUA v1.0.0.exe | 162.159.135.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
2564 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3256 | iexplore.exe | 172.217.21.202:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3256 | iexplore.exe | 104.20.243.79:443 | embed.tawk.to | Cloudflare Inc | US | shared |
3256 | iexplore.exe | 216.58.205.238:443 | www.youtube.com | Google Inc. | US | whitelisted |
3256 | iexplore.exe | 172.217.21.238:443 | www.youtube.com | Google Inc. | US | whitelisted |
2564 | iexplore.exe | 145.14.145.69:80 | www.stcmods.com | Hostinger International Limited | US | shared |
3256 | iexplore.exe | 145.14.145.33:80 | stcmods.com | Hostinger International Limited | US | shared |
3256 | iexplore.exe | 172.217.23.130:80 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |
cdn.discordapp.com |
| shared |
www.bing.com |
| whitelisted |
stcmods.com |
| shared |
www.stcmods.com |
| shared |
pagead2.googlesyndication.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
embed.tawk.to |
| whitelisted |
www.youtube.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |